WinSecWiki > Security Settings > Local Policies > User Rights

User Rights Assignments
Although in this section they are called user rights, these authority assignments are more commonly called privileges.
Privileges are computer level actions that you can assign to users or groups. For the sake of maintainability you should only assign privileges to groups not to individual users. Each computer has its own user rights assignments. In particular this means you should be cognizant of rights assignments on member servers which may easily differ from the rights assignments you find on your domain controllers. To centrally control user rights assignments on computers throughout your domain use group policy.
- Logon rights
- Admin equivalent rights
- Tracking user rights with the security log
- User rights in-depth
- Access this computer from the network
- Act as part of the operating system
- Add workstations to domain
- Adjust memory quotas for a process
- Allow log on locally
- Allow logon through Terminal Services
- Back up files and directories
- Bypass traverse checking
- Change the system time
- Create a pagefile
- Create a token object
- Create global objects
- Create permanent shared objects
- Debug programs
- Deny access to this computer from the network
- Deny logon as a batch job
- Deny logon as a service
- Deny logon locally
- Deny logon through Terminal Services
- Enable computer and user accounts to be trusted for delegation
- Force shutdown from a remote system
- Generate security audits
- Impersonate a client after authentication
- Increase scheduling priority
- Load and unload device drivers
- Lock pages in memory
- Log on as a batch job
- Log on as a service
- Manage auditing and security log
- Modify firmware environment values
- Perform volume maintenance tasks
- Profile single process
- Profile system performance
- Remove computer from docking station
- Replace a process level token
- Restore files and directories
- Shut down the system
- Synchronize directory service data
- Take ownership of files and other objects
Child articles:
- Logon Rights
- Admin Equivalent Rights
- Tracking User Rights with the Security Log
- User Rights In-Depth
Back to top

All things IT
User Rights Assignment Definitions
This is a list of all the User Rights Assignments available on a Windows network along with a brief description and default values. The definitions are taken from the Microsoft documentation .
Access Credential Manager as a trusted caller The Access Credential Manager as a trusted caller policy setting is used by Credential Manager during backup and restore. No accounts should have this privilege because it is assigned only to the Winlogon service. Do not modify this policy setting from the default.
Access this computer from the network The Access this computer from the network policy setting determines which users can connect to the device from the network. This capability is required by a number of network protocols, including Server Message Block (SMB)-based protocols, NetBIOS, Common Internet File System (CIFS), and Component Object Model Plus (COM+). On desktop devices or member servers, grant this right only to users and administrators. On domain controllers, grant this right only to authenticated users, enterprise domain controllers, and administrators. This setting includes the Everyone group to ensure backward compatibility. Upon Windows upgrade, after you have verified that all users and groups are correctly migrated, you should remove the Everyone group and use the Authenticated Users group instead.
Act as part of the operating system The Act as part of the operating system policy setting determines whether a process can assume the identity of any user and thereby gain access to the resources that the user is authorized to access. Typically, only low-level authentication services require this user right. Do not assign this right to any user accounts. Only assign this user right to trusted users. If a service requires this user right, configure the service to log on by using the local System account, which inherently includes this user right. Do not create a separate account and assign this user right to it.
Add workstations to domain This policy setting determines which users can add a device to a specific domain. For it to take effect, it must be assigned so that it applies to at least one domain controller. A user who is assigned this user right can add up to ten workstations to the domain. Configure this setting so that only authorized members of the IT team are allowed to add devices to the domain. By default, this setting allows access for Authenticated Users on domain controllers, and it is not defined on stand-alone servers.
Adjust memory quotas for a process This privilege determines who can change the maximum memory that can be consumed by a process. This privilege is useful for system tuning on a group or user basis. Restrict the Adjust memory quotas for a process user right to only users who require the ability to adjust memory quotas to perform their jobs. If this user right is necessary for a user account, it can be assigned to a local machine account instead of to a domain account. By default, members of the Administrators, Local Service, and Network Service groups have this right.
Allow log on locally This policy setting determines which users can start an interactive session on the device. Users must have this user right to log on over a Remote Desktop Services session that is running on a Windows-based member device or domain controller. By default, the members of the following groups have this right on domain controllers: Account Operators, Administrators, Backup Operators, Print Operators, Server Operators.
Allow log on through Terminal Services This policy setting determines which users or groups can access the logon screen of a remote device through a Remote Desktop Services connection.
Back up files and directories This user right determines which users can bypass file and directory, registry, and other persistent object permissions for the purposes of backing up the system. This user right is effective only when an application attempts access through the NTFS backup application programming interface (API) Default on domain controllers: Administrators, Backup Operators, Server Operators Default on Workstations and Server: Administrators, Backup Operators
Bypass traverse checking This policy setting determines which users (or a process that acts on behalf of the user’s account) have permission to navigate an object path in the NTFS file system or in the registry without being checked for the Traverse Folder special access permission. This user right does not allow the user to list the contents of a folder. It only allows the user to traverse folders to access permitted files or subfolders.
Change the system time This policy setting determines which users can adjust the time on the device’s internal clock.
Change the time zone This policy setting determines which users can adjust the time zone that is used by the device for displaying the local time, which includes the device’s system time plus the time zone offset.
Create a pagefile This policy setting determines which users can create and change the size of a page file. By default, members of the Administrators group have this right.
Create a token object This policy setting determines which accounts a process can use to create a token, and which accounts it can then use to gain access to local resources. This user right is used internally by the operating system. Unless it is necessary, do not assign this user right to a user, group, or process other than Local System.
Create global objects This policy setting determines which users can create global objects that are available to all sessions. Users can still create objects that are specific to their own session if they do not have this user right. A global object is an object that is created to be used by any number of processes or threads, even those not started within the user’s session. Remote Desktop Services uses global objects in its processes to facilitate connections and access. By default, members of the Administrators group have this right, as do Local Service and Network Service accounts on the supported versions of Windows. Service is included for backwards compatibility with earlier versions of Windows.
Create permanent shared objects This user right determines which accounts can be used by processes to create a directory object by using the object manager. Directory objects include Active Directory objects, files and folders, printers, registry keys, processes, and threads. Users who have this capability can create permanent shared objects, including devices, semaphores, and mutexes. By default, LocalSystem is the only account that has this right. Do not assign this right to any users.
Create symbolic links This user right determines if users can create a symbolic link from the device they are logged on to. A symbolic link is a file-system object that points to another file-system object. By default, members of the Administrators group have this right.
Debug programs This policy setting determines which users can attach to or open any process, even those they do not own. Developers who are debugging their own applications do not need to be assigned this user right. Developers who are debugging new system components need this user right. This user right provides access to sensitive and critical operating-system components. By default, members of the Administrators group have this right.
Deny access to this computer from the network This security setting determines which users are prevented from accessing a device over the network. By default, this setting is Guest on domain controllers and on stand-alone servers.
Deny log on as a batch job This policy setting determines which accounts are prevented from logging on by using a batch-queue tool to schedule and start jobs automatically in the future. The ability to log on by using a batch-queue tool is needed for any account that is used to start scheduled jobs by means of the Task Scheduler. Deny log on as a batch job prevents administrators or operators from using their personal accounts to schedule tasks.
Deny log on as a service This policy setting determines which users are prevented from logging on to the service applications on a device. A service is an application type that runs in the system background without a user interface. It provides core operating system features, such as web serving, event logging, file serving, printing, cryptography, and error reporting.
Deny log on locally This policy setting determines which users are prevented from logging on directly at the device’s console.
Deny log on through Remote Desktop Services This policy setting determines which users are prevented from logging on to the device through a Remote Desktop connection through Remote Desktop Services.
Enable computer and user accounts to be trusted for delegation This policy setting determines which users can set the Trusted for Delegation setting on a user or computer object. Security account delegation provides the ability to connect to multiple servers, and each server change retains the authentication credentials of the original client. Delegation of authentication is a capability that client and server applications use when they have multiple tiers. It allows a public-facing service to use client credentials to authenticate to an application or database service. For this configuration to be possible, the client and the server must run under accounts that are trusted for delegation. Limit this assignment as it poses a security risk. There is no reason to assign this user right to anyone on member servers and workstations that belong to a domain because it has no meaning in those contexts. It is only relevant on domain controllers and stand-alone devices.
Force shutdown from a remote system This security setting determines which users are allowed to shut down a device from a remote location on the network.
Generate security audits This policy setting determines which accounts can be used by a process to generate audit records in the security event log. The Local Security Authority Subsystem Service (LSASS) writes events to the log. You can use the information in the security event log to trace unauthorized device access. By default, this setting is Local Service and Network Service on domain controllers and stand-alone servers.
Impersonate a client after authentication This policy setting determines which programs are allowed to impersonate a user or another specified account and act on behalf of the user. Impersonation is the ability of a thread to run in a security context that is different from the context of the process that owns the thread. By default, this setting is Administrators, Local Service, Network Service, and Service on domain controllers and stand-alone servers.
Increase a process working set This policy setting determines which users can increase or decrease the size of the working set of a process. The working set of a process is the set of memory pages currently visible to the process in physical RAM. By default, standard users have this right.
Increase scheduling priority This policy setting determines which user accounts can increase the base priority class of a process. This user right is not required by administrative tools that are supplied with the operating system, but it might be required by software development tools.
Load and unload device drivers This user right is not required if a signed driver for the new hardware already exists in the driver.cab file on the device. Because device driver software runs as if it is a part of the operating system with unrestricted access to the entire computer, it is critical that only known and authorized device drivers be permitted. By default this setting is Administrators and Print Operators on domain controllers and Administrators on stand-alone servers.
Lock pages in memory This policy setting determines which accounts can use a process to keep data in physical memory, which prevents the computer from paging the data to virtual memory on a disk. Enabling this policy setting for a specific account (a user account or a process account for an application) prevents paging of the data. Thereby, the amount of memory that Windows can reclaim under pressure is limited. This could lead to performance degradation.
Log on as a batch job This policy setting determines which accounts can log on by using a batch-queue tool such as the Task Scheduler service. When you use the Add Scheduled Task Wizard to schedule a task to run under a particular user name and password, that user is automatically assigned the Log on as a batch job user right. When the scheduled time arrives, the Task Scheduler service logs on the user as a batch job instead of as an interactive user, and the task runs in the user’s security context. By default, this setting is for Administrators, Backup Operators, and Performance Log Users on domain controllers and on stand-alone servers.
Log on as a service This policy setting determines which service accounts can register a process as a service. By default this setting is Network Service on domain controllers and Network Service on stand-alone servers.
Manage auditing and security log This policy setting determines which users can specify object access audit options for individual resources such as files, Active Directory objects, and registry keys. These objects specify their system access control lists (SACL). A user who is assigned this user right can also view and clear the Security log in Event Viewer. By default this setting is Administrators on domain controllers and on stand-alone servers.
Modify an object label This privilege determines which user accounts can modify the integrity label of objects, such as files, registry keys, or processes owned by other users. By default this setting is Not defined on domain controllers and on stand-alone servers. Do not give any group this user right.
Modify firmware environment values This security setting determines who can modify firmware environment values. Firmware environment values are settings that are stored in the nonvolatile RAM of non-x86-based computers. The effect of the setting depends on the processor. On x86-based computers, the only firmware environment value that can be modified by assigning this user right is the Last Known Good Configuration setting, which should only be modified by the system. By default this setting is Administrators on domain controllers and on stand-alone servers.
Perform volume maintenance tasks This policy setting determines which users can perform volume or disk management tasks, such as defragmenting an existing volume, creating or removing volumes, and running the Disk Cleanup tool. By default this setting is Administrators on domain controllers and on stand-alone servers.
Profile single process This policy setting determines which users can view a sample performance of an application process. Typically, you do not need this user right to use the performance reporting tools included in the operating system. However, you do need this user right if the system’s monitor components are configured to collect data through Windows Management Instrumentation (WMI). This right should not be granted to individual users. It should be granted only for trusted applications that monitor other programs.
Profile system performance This security setting determines which users can use Windows performance monitoring tools to monitor the performance of system processes. By default this setting is Administrators on domain controllers and on stand-alone servers.
Remove computer from docking station This security setting determines whether a user can undock a portable device from its docking station without logging on.
Replace a process level token This policy setting determines which parent processes can replace the access token that is associated with a child process. Specifically, the Replace a process level token setting determines which user accounts can call the CreateProcessAsUser() application programming interface (API) so that one service can start another. By default this setting is Network Service and Local Service on domain controllers and on stand-alone servers.
Restore files and directories This security setting determines which users can bypass file, directory, registry, and other persistent object permissions when they restore backed up files and directories, and it determines which users can set valid security principals as the owner of an object. Users with this user right can overwrite registry settings, hide data, and gain ownership of system objects, so only assign this user right to trusted users. By default, this right is granted to the Administrators, Backup Operators, and Server Operators groups on domain controllers, and to the Administrators and Backup Operators groups on stand-alone servers.
Shut down the system This security setting determines if a user who is logged on locally to a device can shut down Windows. By default this setting is Administrators, Backup Operators, Server Operators, and Print Operators on domain controllers, and Administrators and Backup Operators on stand-alone servers.
Synchronize directory service data This policy setting determines which users and groups have authority to synchronize all directory service data, regardless of the protection for objects and properties. This privilege is required to use LDAP directory synchronization (dirsync) services. Domain controllers have this user right inherently because the synchronization process runs in the context of the System account on domain controllers. Ensure that no accounts are assigned the Synchronize directory service data user right. Only domain controllers need this privilege, which they inherently have.
Take ownership of files or other objects This policy setting determines which users can take ownership of any securable object in the device, including Active Directory objects, NTFS files and folders, printers, registry keys, services, processes, and threads. By default, the owner is the person who or the process which created the object. Owners can always change permissions to objects, even when they are denied all access to the object.
Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
What is the relationship between User Rights Assignment Policies vs. Membership of Local Groups
I just spent the better part of this morning on a support call with a vendor where we eventually resolved our issue by manually adding the service account their application was using to the following Computer Configuration/Policies/Windows Settings/Security Settings/Local Policies/User Rights Assignment policies which were being set by a Domain GPO:
- Back up files and directories
- Log on as a batch job
- Restore files and directories
After rebooting the server and getting the updated GPO our service account no longer generated the following Event 4625 - Logon Type 4 audit events when attempting to start the application:
The vendor's documentation instructed us to add the service account to the Backup Operators and Power User Local Groups - which we did. Reading the Explain tab for each one of the required User Right Assignment policies indicates that the Backup Operators have those Rights by default (TechNet seems to confirm this ). Incidentally, there's no mention of Power User being assigned those Rights that I can find so I'm not really sure why that was a requirement.
Why did we have to explicitly assign that service account those Rights ( Back up files and directories , Log on as a batch job , Restore files and directories ) when it already should of had them by virtue of being a member of the Backup Operators Local Group?
What is the relation between the User Rights Policies and the builtin Local Groups? Are User Rights Polices the constituent parts that make up the "meta"-rights of each builtin Local Groups? If so, where can I find which Rights belong to which bultin Local Groups?
As stated we resolved this issue by adding our service account to the Group Policy Object that is manually assigning a number of service accounts these specific Rights. I got the sense from the vendor's engineer that this GPO is interfering with the mapping of these constituent Rights to Local Groups. Is this hunch correct? Is assigning constituent User Rights this way a Bad Idea (TM)?
- windows-server-2008-r2
- group-policy
- windows-authentication
Members of local built-in groups (as well as domain groups) have whatever rights are assigned to the group. The default rights on a server for local built-in groups are set in the local security settings. To access the local security settings, click Start, type secpol.msc and hit enter. In the Local Security Policy editor, expand Local Policies, and click on User Rights Assignment. There you will see what groups/users are granted which rights.
The local User Rights Assignment settings can be overriden by domain group policy. If you create a domain group policy that grants certain groups/users a certain right, such as "Logon as a batch job", this will override the local policy for which users have that right.
From what you have written, here is what I am guessing happened: You had a GPO in your domain that granted certain users the rights that you mentioned. This policy did not grant these rights to local machine Backup Operators group. This policy overwrote the default policy on the server. Thus, adding the user to the Backup Operators group did not give them those rights because, due to the Domain GPO, the Backup Operators do not have them.
As to whether or not the vendor's solution is a good idea: I have found that it is usually easier to manage rights by using well-organized groups rather than granting them to individual accounts. This way, when you add a new user, you add the user to the logical groups to which he belongs, and he will immediately have all of the rights he needs rather than having to assign him each right one-by-one. That is what the Built-in groups were intended to do.
Instead of granting those three rights to an individual user, you could have granted the "Backup Operators" group those three rights in the GPO. Then adding the user to that group would have the intended effect.
I am curious why you would have a domain policy managing those rights in the first place. If the purpose was to grant certain users access to perform backup operations, it might have been a better idea to use the domain built-in Backup Operators group.
You must log in to answer this question.
- The Overflow Blog
- The reverse mullet model of software engineering
- Reshaping the future of API platforms
- Featured on Meta
- Our Partnership with OpenAI
- Imgur image URL migration: Coming soon to a Stack Exchange site near you!
Hot Network Questions
- Does Windows 10's portability limit OS features?
- What is the purpose of these fat copper coils wrapped around … something?
- Can changelings instantly change their hairstyle?
- Rafters pulling apart from center support
- Two passports, one name transliterated slightly differently
- Why did Nicodemus visit Jesus at night?
- On what basis does Frieren (Sousou no Frieren) reject the rights of Demons to exist?
- I forgot to BCC people in music promotion email
- Why wouldn't the world have advanced warning of a significant asteroid/comet strike?
- Is it more expensive to self publish or use a publisher?
- Elastic property in Voigt, Reuss and Hill approximations
- Are the threats made by members of the USA's Senate to the International Criminal Court chief prosecutor an abuse of power?
- Two minipage with horizontal lines and a vertical line
- Troubleshooting why my hammock fell
- Which type of visa should I apply for visiting Japan?
- What is the collective name of the four points in the narrative where a roll might be called for?
- Why is the empty set described as "unique" when it is a subset of every set?
- Light waves can't have a wavelength
- Why is off_t signed?
- In surreal numbers, what is the successor of all the germs in the Hardy field?
- Why did Israel invade the Gaza strip from the north and not the south?
- Are Artin-Tits groups ordered groups?
- Is it true that the U.S. President can cancel any amount of student debt without the approval from the Congress?
- Writing public libraries: Should I let the consumer of the library to enforce thread safety?
How to manage user account settings on Windows 11
Here are the steps to add, change, and remove accounts on Windows 11.
View account details
- Add more email accounts
- Change sign-in options
- Control account sync settings
- Connect to organization
- Add multiple accounts
- Delete accounts
On Windows 11 , the "Accounts" page in the Settings app allows you to review and customize many aspects of your account. You can determine the account type, switch from a Microsoft to a local account, change how you sign in, and enable many features to make the experience more secure and easier to use.
In addition, when you need to share a device with other people, you can create an account for each person so that each has a personal space they can customize, apps with their own profile, and a different area to store files.
Furthermore, if you must let a young person use a computer, you can also create a special child account type that provides parental control to monitor and protect them from content that may not be appropriate for their age.
This guide will teach you the steps to manage user accounts on your computer running the latest version of Windows 11.
How to view account details on Windows 11
On Windows 11, the "Your info" settings page includes details about your account, such as the type of account and the Microsoft account associated with the current profile. It also houses the settings to switch from a Microsoft to a local account or vice versa and the option to change the picture profile.
To view the account information on Windows 11, use these steps:
Get the Windows Central Newsletter
All the latest news, reviews, and guides for Windows and Xbox diehards.
- Open Settings .
- Click on Accounts .
- Click the Your info page on the right side.
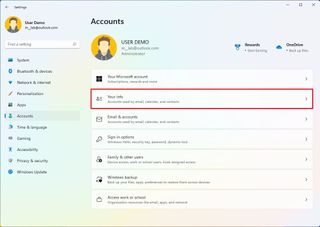
- Confirm your account details, including account type (Administrator or Standard) and whether you have a local or Microsoft account.
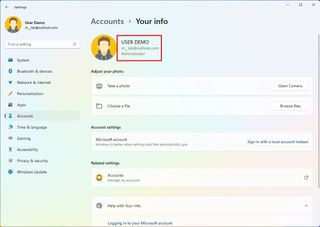
- Quick note: If the page reads "Local account" under your name, there's a link to a Microsoft account. You have a Microsoft account configuration if your email address appears on this page.
- (Optional) Under the "Related settings" section, click the "Accounts" option to access the account online to change billing details, family and security settings, and other settings.
Once you complete the steps, the "Your info" page will give various pieces of information about the account.
In the "Accounts" section, you're also going to find the "Your Microsoft account" page, but it only includes details about your Microsoft 365 subscription.
Change to local account
If you have a Microsoft account and you prefer a local account, you can use these steps to switch:
- Under the "Account settings" section, click the "Sign in with a local account instead" option.
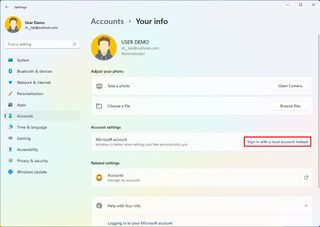
- Continue with the on-screen directions.
- If you have a Microsoft account, click the "Sign in with a local account instead" option to switch to a local account.
- Continue with the on-screen directions.
After you complete the steps, the account will no longer be associated with a Microsoft account.
You can also use the instructions outlined above to switch to a Microsoft account if you have a local account.
Change account picture
To change the account picture on Windows 11, use these steps:
- Click the Browse files button in the "Choose a file" setting.
- Quick tip: You can also use the Camera option to take a picture and set it as the new profile photo.
- Select a new image for the account.
- Click the Choose Picture button.
Once you complete the steps, the picture will apply to the account.
How to link additional emails to an account on Windows 11
You can also add other email accounts in advance, so you don't have to enter the information on other apps (such as Mail & Calendar) and services.
Add accounts for apps
To add additional email accounts on Windows 11, use these steps:
- Click the Email & accounts page on the right side.
- Under the "Accounts used by email, calendar, and contacts" section, click the Add an account button.
- Quick note: If you want to add another Microsoft account, the system will list it under the "Accounts used by other apps" section.
- Select the service provider (such as Outlook, Google, or iCloud).
After you complete the steps, the accounts will be available to set up other apps and services.
Add accounts for work
To add work accounts for apps on Windows 11, use these steps:
- Under the "Accounts used by other apps" section, click the "Add a Microsoft account" or "Add a work or school" account.
- Select the correct service.
Once you complete the steps, the account will be added, giving you quick access to work applications, such as OneDrive for Business.
How to change sign-in options on Windows 11
Windows 11 also includes the "Sign-in options" page that includes the different ways you can customize the preferences to sign into your account. For example, on this page, you can configure Windows Hello, change your local account password, and enable other features like Dynamic lock.
Change account password
If you use Windows 11 with a Microsoft account, you can only change the password online by changing your Hotmail, Live, or Outlook password. You can change the password through the Sign-in options page if you have a local account.
To change the account password on Windows 11, use these steps:
- Click the Sign-in options page on the right side.
- Under the "Ways to sign in" section, click the Password setting.
- Click the Change button.
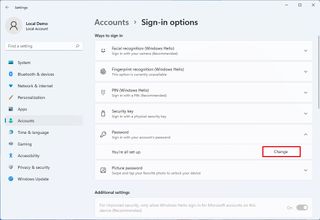
- Confirm the current password.
- Confirm the new password.
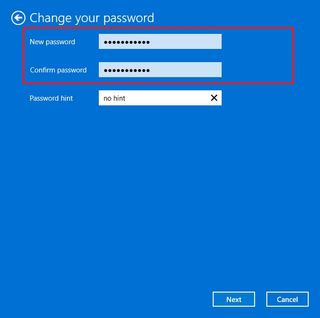
- Quick note: You can't re-use a previous password. You must enter a new password.
- Click the Next button.
- Continue with the on-screen directions (if applicable).
After you complete the steps, you can sign out and sign back in to start using the new password.
Configure or change Windows Hello authentication
On Windows 11, you have multiple ways to configure Windows Hello. You can set up facial or fingerprint recognition if you have the hardware that supports the feature. You can use a physical security key (usually used in organizations). And the most common form of authentication is the PIN option since it doesn't require special hardware and is more secure than a traditional password.
Usually, Windows 11 will prompt you to create a PIN during the initial setup, but if you are still using a password, you can use these steps to set up a Windows Hello PIN:
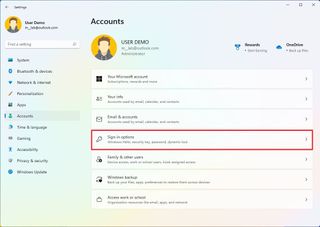
- Under the "Ways to sign in" section, click the PIN (Windows Hello) setting.
- Click the Set up button.
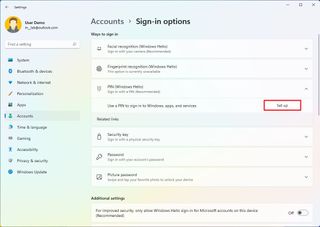
- Confirm your current password (if applicable).
- Click the OK button.
- Create a new numeric PIN that you will remember.
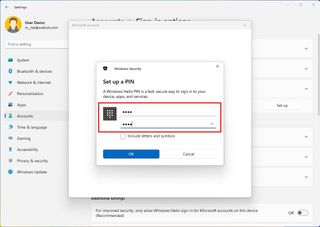
- (Optional) Under the "Additional settings" section, turn on the "For improved security, only allow Windows Hello sign-in for Microsoft accounts on this device" toggle switch.
- Quick note: This feature will turn on Windows Hello for all authentications across Windows 11, so you are never asked for your account password.
Once you complete the steps, you can start using the PIN to sign in instead of a password.
Change current PIN
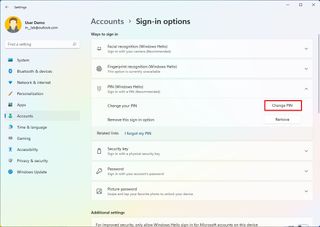
If you already have a PIN, you will only find the option to change or remove it.
To change the current account PIN, use these steps:
- Under the "Ways to sign in" section, click the PIN (Windows Hello) setting.
- Click the Change PIN button.
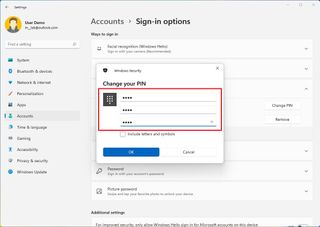
- Confirm the current PIN.
- Create a new PIN.
- Confirm the new PIN.
- (Optional) Under the "Additional settings" section, turn on the "For improved security, only allow Windows Hello sign-in for Microsoft accounts on this device" toggle switch.
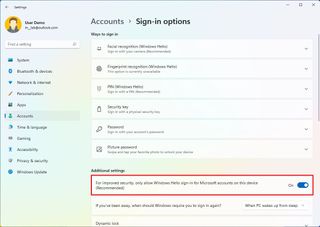
- Quick note: This feature will turn on Windows Hello for all authentications across Windows 11, so you are never asked for your account password. However, if enabled, you won't be able to remove the PIN.
After you complete the steps, the Windows Hello information will change to the new PIN.
Enable sign-in upon waking up
As part of the account settings, you can decide whether the system should prompt you for a password upon waking the device or after some time you have been away from your desk.
To require a sign-in after waking up or specific time period, use these steps:
- Under the "Additional settings" section, use the "If you've been away, when should Windows require you to sign in again?" setting to automatically select how long the system should wait before locking the account.
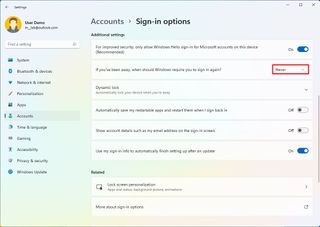
This setting replaces the "Require sign-in" option that lets you decide whether Windows 11 should ask you to sign in when the device wakes up from sleep mode. If you want to disable the option, select the Never option.
Enable Dynamic lock
"Dynamic lock" is a feature that locks your device when you step away from the room automatically. The feature uses proximity technology, meaning you'll need to connect a Bluetooth device like a phone or wearable before you can configure it. Once enabled, if you step away from the computer after 30 seconds, Windows 11 will lock the profile automatically.
To enable Dynamic lock, use these steps:
- Click on Bluetooth & devices .
- Click on Add device button.
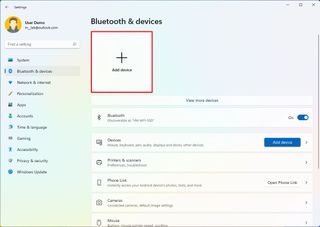
- Click on Bluetooth .
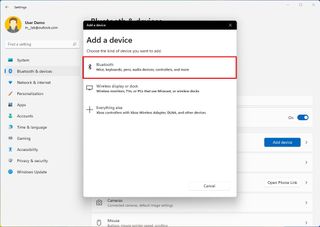
- Turn on Bluetooth on the device you want to pair.
- Select the device from the list.
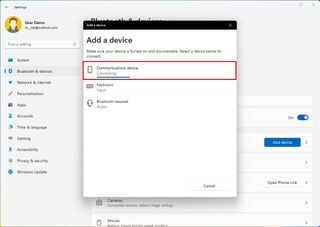
- Continue with the on-screen directions to complete the pairing.
- Click the Sign-in options page on the right side.
- Under the "Additional settings" section, click the Dynamic lock setting.
- Check the "Allow Windows to automatically lock the device when you're away" option.
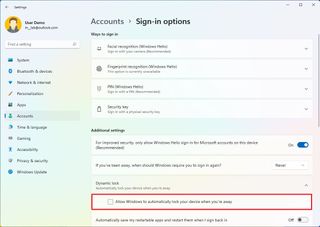
Once you complete the steps, you can step away from the desk with the Bluetooth device, and then after 30 seconds, when you return, the computer should be locked.
Stop restarting apps on startup
Some apps are able to restart automatically at startup if you don't close them before turning off the computer. If you don't like this behavior, you can disable the feature.
To prevent apps from restarting at startup, use these steps:
- Under the "Additional settings" section, turn off the "Automatically save my restartable apps and restart when I sign back in" toggle switch.
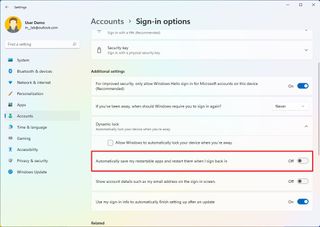
After you complete the steps, apps will no longer restart automatically on startup.
How to control account sync settings on Windows 11
On Windows 11, Microsoft is referring to the sync settings as the new "Windows Backup" feature. On this page, you can choose what folders are backed up in the cloud using OneDrive . You can decide whether the system should remember your apps so you can restore them on another installation. And you can control the settings you want to sync across devices associated with the same Microsoft account.
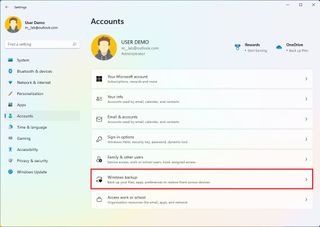
To control the sync settings on Windows 11, use the steps:
- Click the Windows backup page on the right side.
- Click the Set up syncing button for the "OneDrive folder syncing" setting.
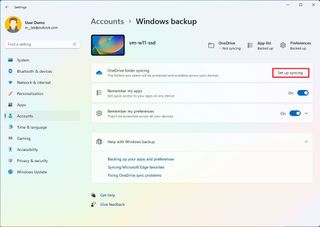
- Select the folders (Desktop, Documents, or Pictures) to upload and back up on the cloud. (You must have enough space to enable this feature.)
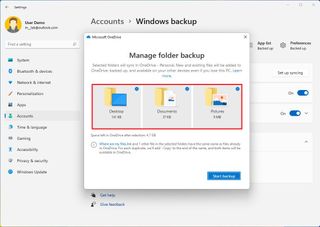
- Click the Start backup button.
- (Optional) Turn on the "Remember my apps" toggle switch if you want the system to remember the Microsoft Store app on your computer so that you can restore them later on another computer.
- Turn on the "Remember my preferences" toggle switch to allow your settings to sync across devices.
- Click the "Remember my preferences" setting.
- Check the settings you want to sync across devices, including passwords, language preferences, and other Windows settings.
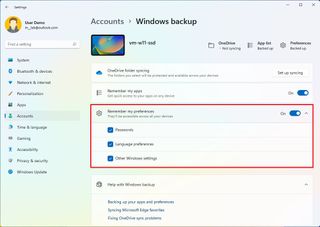
Once you complete the steps, the settings and files will sync to the cloud and across devices, depending on your configuration.
How to connect account to an organization on Windows 11
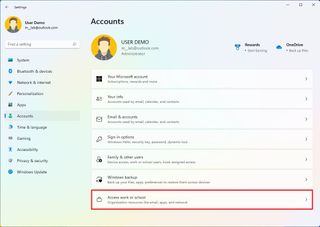
The "Access work or school" page has the settings to connect to an organization to access shared resources, such as network resources, apps, and emails. If you are part of an organization, your network administrator will provide the information.
To connect a device to the network, use these steps:
- Click the Access work or school page on the right side.
- Click the Connect button.
- Confirm your work or school account.
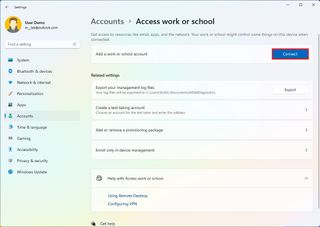
- Quick note: You can also select the option to join an Azure Active Direction or local Active Directory domain from this page.
After you complete the steps, you will have access to the organization's resources as configured by the network administrator.
How to add multiple accounts on Windows 11
Although most computers are set up for single users, Windows 11 allows you to share the device with multiple people through the "Family & other people" page, which includes the settings to add, remove, and manage multiple user accounts.
Add family members
On the page, under the "Your family" section, you can manage family members to allow each person to have their desktop, settings, apps, and a place to store files separately from everyone else.
You can have two family account types, including "Child" and "Adult," and each account type provides different features.
Create a child account
A Child account offers a controlled environment with features to keep young members safe while using apps, playing games, and browsing the internet. If you choose to create a child account, the person can use the device, personalize the desktop, work with apps, create files, and safely browse the web with Microsoft Edge.
Also, when using this account type, the organizer can control their activities, enforce limits on apps and games, control screen time, and more using the Microsoft family dashboard online.
To create a child account on Windows 11, use these steps:
- Click the Family & other users page on the right side.
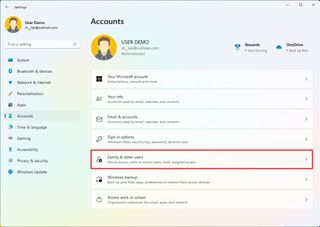
- Click the Add account in the "Add a family member" setting.
- Confirm the email address of the young person you want to add.
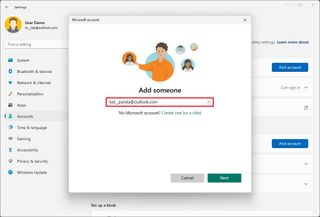
- Quick note: If the young person doesn't have an account, choose the "Create one for a child" option and continue with the on-screen directions.
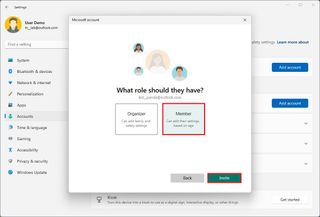
- Click the Next button.
- Select the Member option.
- Click the Invite button.
- Open the invitation email in the child's account online.
- Click the Accept Invitation button.
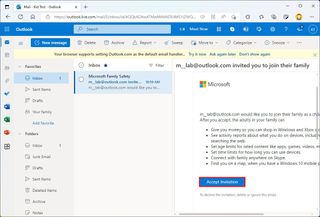
- Click the Join now button.
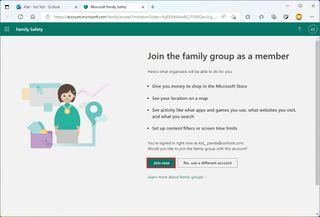
- Sign out of the main account.
- Select the child account from the Lock screen.
- Sign in with the child's Microsoft account credentials.
- Click the Skip for now option (if applicable).
- Create a PIN for the account.
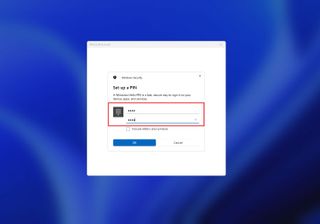
- Click the OK button.
- Continue with the on-screen directions to finish the setup.
Once you complete the steps, Windows 11 will create the account, and the user will be able to sign in immediately.
Create an adult account
When using the family settings, an adult account is the same as a traditional local account, but members can also control child accounts.
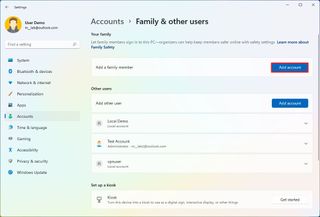
To add a new member to the family group on Windows 11, use these steps:
- Click the Add account in the "Add a family member" setting.
- Confirm the family member's email address.
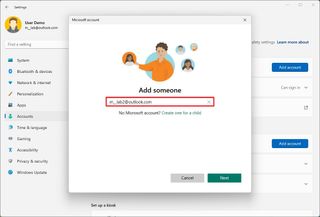
- Click the Next button.
- Select the Organizer option.
- Click the Invite button.
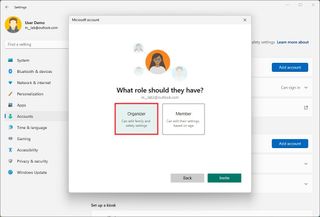
After you complete the steps, the account will be created, but the new member will need to accept the email invitation before they can use the device and manage parental control settings for child accounts.
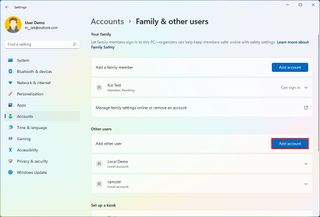
Add non-family member
On Windows 11, you can also create accounts for other people not necessarily part of your family. Using these settings, you can create a Microsoft or traditional local account.
Create a Microsoft account
Using a Microsoft account is recommended because it's easier to configure, the user can choose to sync their settings across devices, and password recovery is straightforward.
To create a profile with a Microsoft account, use these steps:
- Under the "Other users" section, click the Add account button for the "Add other user" setting.
- Confirm the email address or phone number of the new user.
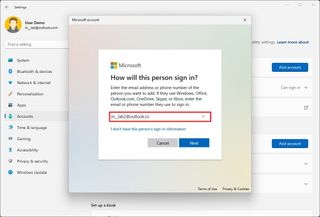
- Quick note: If the user doesn't have a Microsoft account, choose the "I don't have this person's sign-in information" option to create an account and continue with the on-screen directions.
- Click the Finish button.
Once you complete the steps, the person should be able to sign in and start using the device.
Create a local account
On Windows 11, you can still create a local account without needing a Microsoft account, also called an offline account.
To create a local account on Windows 11, use these steps:
- Click the "I don't have this person's sign-in information" option.
- Click the "Add a user without a Microsoft account" option.
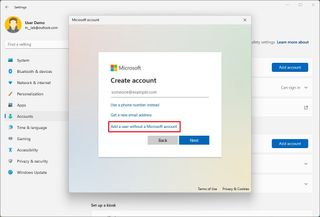
- Confirm the username.
- Create a password for the account.
- Complete the security questions to enable the reset option if you forget the password.
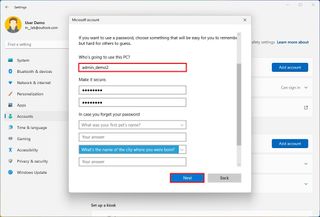
After you complete the steps, the user can log in and start using the standard local account on your Windows 11 computer.
Furthermore, the "Family & other users" page also includes an option to set up a kiosk account . This feature is usually reserved for network administrators to turn a computer into a digital sign or interactive display or turn it into a device that only runs a specific application.
Change account type
As standard user account is the recommended type for most users, but if you want to change the type to administrator .
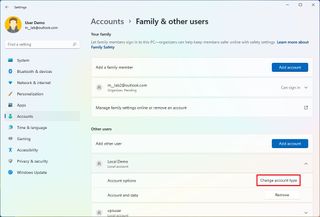
To change a user account type on Windows 11, use these steps:
- Click the Family & other users page on the right side.
- Under the "Other users" section, select the account to update.
- Click the Change account type button.
- Select the Administrator account type.
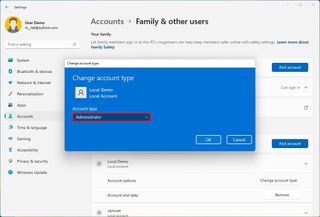
Once you complete the steps, the new account type will dictate the user's access privileges.
How to delete account on Windows 11
On Windows 11, when you no longer need an account, you can delete the profile and data, but the steps can differ depending on the account type.
Remove family account
To delete a family member account on Windows 11, use these steps:
- Under the "Your family" section, click the "Manage family settings online" option.
- Sign in with your credentials (if applicable).
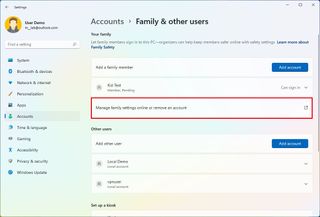
- Under the "Your family" section, click the (three-dotted) menu button in the right corner of the user account and select the "Remove from family group" option.
- Click the Remove button.
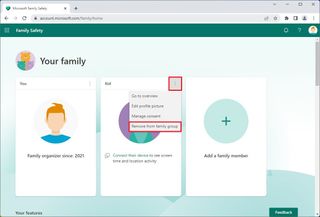
- Quick note: If you are trying to remove a child account, you may first need to choose the "Manage consent" option and remove the consent before you can remove the account from the family group.
Once you complete the steps, the account and files will be deleted from the computer.
Remove non-family account
To delete a local account on Windows 11, use these steps:
- Under the "Other users" section, select the user account and click the Remove button.
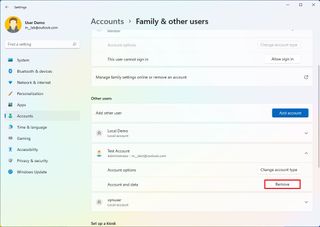
- Click the "Delete account and data" button.
After you complete the steps, the profile and files will be deleted from the device.

More resources
For more helpful articles, coverage, and answers to common questions about Windows 10 and Windows 11, visit the following resources:
- Windows 11 on Windows Central — All you need to know
- Windows 10 on Windows Central — All you need to know

Mauro Huculak is technical writer for WindowsCentral.com. His primary focus is to write comprehensive how-tos to help users get the most out of Windows 10 and its many related technologies. He has an IT background with professional certifications from Microsoft, Cisco, and CompTIA, and he's a recognized member of the Microsoft MVP community.
- 2 ASUS ROG Zephyrus G14 (2024) vs. Razer Blade 14 (2024): Which AMD gaming laptop is better for you?
- 3 Microsoft Copilot: Everything you need to know
- 4 My favorite game of all time is the cheapest it's ever been on Xbox and PC, and so is its prequel remake
- 5 Helldivers 2 CEO apologizes for Sony PSN requirement fiasco as Steam review bombing continues: "I hope we will make it up and regain the trust"
User Rights and Privileges
User rights grant specific privileges and logon rights to users and groups in your computing environment. Administrators can assign specific rights to group accounts or to individual user accounts. These rights authorize users to perform specific actions, such as logging on to a system interactively or backing up files and directories.
To ease the task of user account administration, you should assign privileges primarily to group accounts, rather than to individual user accounts. When you assign privileges to a group account, users are automatically assigned those privileges when they become a member of that group. This method of administering privileges is far easier than assigning individual privileges to each user account when the account is created.
The following table lists and describes the privileges that can be granted to a user.
Some privileges can override permissions set on an object. For example, a user logged on to a domain account as a member of the Backup Operators group has the right to perform backup operations for all domain servers. However, this requires the ability to read all files on those servers, even files on which their owners have set permissions that explicitly deny access to all users, including members of the Backup Operators group. A user right—in this case, the right to perform a backup—takes precedence over all file and directory permissions. For more information, see Backup and Recovery (https://go.microsoft.com/fwlink/?LinkID=131606).
Table Of Contents
- Access Control Overview
- Checklist: Setting Access Controls on Objects
- What Are Permissions?
- File and Folder Permissions
- Share and NTFS Permissions on a File Server
- Inherited Permissions
- How Effective Permissions Are Determined
- Determine Where to Apply Permissions
- Set, View, Change, or Remove Permissions on Files and Folders
- View Effective Permissions on Files and Folders
- Set, View, Change, or Remove Special Permissions
- Set Permissions on a Shared Resource
- Take Ownership of a File or Folder
- Audit Policies
- Define or Modify Auditing Policy Settings for an Event Category
- Apply or Modify Auditing Policy Settings for a Local File or Folder
- View the Security Log
- Understanding User Account Control
- Resources for Access Control
- Security Settings Property Page
- Select Users, Computers, or Groups Dialog Box
- Object Types Dialog Box
- Select Users, Computers, or Groups Dialog Box - Advanced Page
- Permission Entry Dialog Box
- Advanced Security Settings Properties Page - Auditing Tab
- Advanced Security Settings Properties Page - Owner Tab
- Advanced Security Settings Properties Page - Permissions Tab
- Auditing Entry Dialog Box
Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
How to add a user group in the "Shut down the system" group policy in Windows Server by CMD or PowerShell
I've read some documentation on Microsoft and other sites. Some of them suggest GPRegistryValue for registry-based policies and other recommended third-party software.
The full path of the key is: "Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment"
But in my case I cannot use other packages except CMD or PowerShell (UI not available).
- group-policy
- windows-server
- superuser.com/questions/1254253/… and blakedrumm.com/blog/set-and-check-user-rights-assignment might help you for a starting point to play with. – Vomit IT - Chunky Mess Style Nov 25, 2022 at 21:25
- This is just local security policy settings. What did you search for as this is a common task? powershell 'Local User Rights Management' – postanote Nov 25, 2022 at 21:37
Windows provides the secedit.exe tool for this and or custom code, as per the link provided in my comment to you.
Also, did you check the mspowershellgallery.com site for modules that assist with local user security policy?
Update as per '@Vomit IT - Chunky Mess Style', suggestion.
The more succinct/elegant option.
FYI --- Update for '@Vomit IT - Chunky Mess Style'. Using the PS_LSA.Wrapper
- 1 @VomitIT-ChunkyMessStyle... update provided. – postanote Nov 25, 2022 at 21:43
- Oh yeah, now you're talking!!! I saw github examples of that Indented.SecurityPolicy you suggested listed there. I like it! – Vomit IT - Chunky Mess Style Nov 25, 2022 at 21:55
- 1 Yeppers, I've got a bunch of these I've collected, refactored, and written over the years in different engagements. Even one using the underlying OS PS_LSA Windows library. – postanote Nov 25, 2022 at 22:06
- Thanks for helping me.The module of 'SecurityPolicy' is available, but when I try to find its modules "Get-Command -Module 'SecurityPolicy'" nothing is listed. Thus, I can't execute 'Add-UserRightsAssignment'. – Daniel Teodoro Nov 29, 2022 at 13:38
- If you did this Get-Command -Module 'SecurityPolicy' , and you see nothing? If so, that means it's not installed/in your PSModulePath. Did you install the module as I show in my suggested answer? If not, then you need to. Then you use Get-Module -ListAvailable to validate it's on your system. – postanote Nov 30, 2022 at 6:37
You must log in to answer this question.
Not the answer you're looking for browse other questions tagged powershell group-policy windows-server ..
- The Overflow Blog
- The reverse mullet model of software engineering
- Reshaping the future of API platforms
- Featured on Meta
- Our Partnership with OpenAI
- Imgur image URL migration: Coming soon to a Stack Exchange site near you!
Hot Network Questions
- A world where some currency loses value when handled would have a deflationary economy. What would the consequences to society be?
- Why does this vintage DRAM chip enable circuit require such a beefy resistor?
- Find the rule of a cellular automaton
- Troubleshooting why my hammock fell
- What happens when I shift gears without pressing the clutch in a manual transmission while the car is running?
- What to do when coauthor suggests me to fluff up the paper?
- Given 4 red, 3 white and 5 black balls. Picking balls one by one without replacement, find the chance that red balls are exhausted first.
- Who changes `/proc/sys/kernel/random/boot_id` in Linux (SLES)?
- Does Windows 10's portability limit OS features?
- Can I use two prepositions with the same noun when one takes the dative and the other the accusative?
- I'm exceeding 50k query rows with a child query, and no exception. Why does this work?
- Help choosing right chainset / crankset - commuter looking for a faster top speed
- Two passports, one name transliterated slightly differently
- What is the collective name of the four points in the narrative where a roll might be called for?
- What is the purpose of these fat copper coils wrapped around … something?
- Could you actually do orbital deployment?
- Why wouldn't the world have advanced warning of a significant asteroid/comet strike?
- Mt. 15:21-28 vs. Mt. 10:5 - What was Jesus doing in the region of Tyre and Sidon?
- Can we reproduce Antonio Asis circle interferences?
- Do members of the Church of Jesus Christ of Latter-day Saints believe in self-defense?
- What methods could one use to make horses a viable animal companion in the late game?
- Rafters pulling apart from center support
- Teaching job application: Should I make any references to a gap year in my employment history due to depression?
- How does 別にいいですよ mean "Its doesnt matter" or "I dont mind"?
Man or bear? Hypothetical question sparks conversation about women's safety
Women explain why they would feel safer encountering a bear in the forest than a man they didn't know. the hypothetical has sparked a broader discussion about why women fear men..

If you were alone in the woods, would you rather encounter a bear or a man? Answers to that hypothetical question have sparked a debate about why the vast majority say they would feel more comfortable choosing a bear.
The topic has been hotly discussed for weeks as men and women chimed in with their thoughts all over social media.
Screenshot HQ , a TikTok account, started the conversation, asking a group of women whether they would rather run into a man they didn't know or a bear in the forest. Out of the seven women interviewed for the piece, only one picked a man.
"Bear. Man is scary," one of the women responds.
A number of women echoed the responses given in the original video, writing in the comments that they, too, would pick a bear over a man. The hypothetical has people split, with some expressing their sadness over the state of the world and others cracking jokes. Some men were flabbergasted.
Here's what we know.
A bear is the safer choice, no doubt about it, many say
There were a lot of responses, more than 65,000, under the original post. Many wrote that they understood why the women would choose a bear.
"No one’s gonna ask me if I led the bear on or give me a pamphlet on bear attack prevention tips," @celestiallystunning wrote.
@Brennduhh wrote: "When I die leave my body in the woods, the wolves will be gentler than any man."
"I know a bear's intentions," another woman wrote. "I don't know a man's intentions. no matter how nice they are."
Other TikTok users took it one step further, posing the hypothetical question to loved ones. Meredith Steele, who goes by @babiesofsteele , asked her husband last week whether he would rather have their daughter encounter a bear or a man in the woods. Her husband said he "didn't like either option" but said he was leaning toward the bear.
"Maybe it's a friendly bear," he says.
Diana, another TikTok user , asked her sister-in-law what she would choose and was left speechless.
"I asked her the question, you know, just for giggles. She was like, 'You know, I would rather it be a bear because if the bear attacks me, and I make it out of the woods, everybody’s gonna believe me and have sympathy for me," she said. "But if a man attacks me and I make it out, I’m gonna spend my whole life trying to get people to believe me and have sympathy for me.'"
Bear vs. man debate stirs the pot, woman and some men at odds
The hypothetical has caused some tension, with some women arguing that men will never truly understand what it's like to be a woman or the inherent dangers at play.
Social media users answered this question for themselves, producing memes, spoken word poetry and skits in the days and weeks since.
So, what would you choose?
Advertisement
Supported by
Congress Passed a Bill That Could Ban TikTok. Now Comes the Hard Part.
President Biden has signed the bill to force a sale of the video app or ban it. Now the law faces court challenges, a shortage of qualified buyers and Beijing’s hostility.
- Share full article

By Sapna Maheshwari and David McCabe
Sapna Maheshwari reported from New York, and David McCabe from Washington.
A bill that would force a sale of TikTok by its Chinese owner, ByteDance — or ban it outright — was passed by the Senate on Tuesday and signed into law Wednesday by President Biden.
Now the process is likely to get even more complicated.
Congress passed the measure citing national security concerns because of TikTok’s Chinese ties. Both lawmakers and security experts have said there are risks that the Chinese government could lean on ByteDance for access to sensitive data belonging to its 170 million U.S. users or to spread propaganda.
The law would allow TikTok to continue to operate in the United States if ByteDance sold it within 270 days, or about nine months, a time frame that the president could extend to a year.
The measure is likely to face legal challenges, as well as possible resistance from Beijing, which could block the sale or export of the technology. It’s also unclear who has the resources to buy TikTok, since it will carry a hefty price tag.
The issue could take months or even years to settle, during which the app would probably continue to function for U.S. consumers.
“It’s going to be a royal mess,” said Anupam Chander, a visiting scholar at the Institute for Rebooting Social Media at Harvard and an expert on the global regulation of new technologies.
TikTok pledged to challenge the law. “Rest assured, we aren’t going anywhere,” its chief executive, Shou Chew, said in a video posted to the platform. “We are confident, and we will keep fighting for your rights in the courts.”
Here’s what to expect next.
TikTok’s Day in Court
TikTok is likely to start by challenging the measure in the courts.
“I think that’s the one certainty: There will be litigation,” said Jeff Kosseff, an associate professor of cybersecurity law at the Naval Academy.
TikTok’s case will probably lean on the First Amendment, legal experts said. The company is expected to argue that a forced sale could violate its users’ free speech rights because a new owner could change the app’s content policies and reshape what users are able to freely share on the platform.
“Thankfully, we have a Constitution in this country, and people’s First Amendment rights are very important,” Michael Beckerman, TikTok’s vice president of public policy, said in an interview with a creator on the platform last week. “We’ll continue to fight for you and all the other users on TikTok.”
Other groups, like the American Civil Liberties Union, which has been a vocal opponent of the bill, may also join the legal fight. A spokeswoman for the A.C.L.U. said on Tuesday that the group was still weighing its role in potential litigation challenging the law.
The government will probably need to make a strong case that ByteDance’s ownership of TikTok makes it necessary to limit speech because of national security concerns, the legal experts said.
TikTok already has a strong record in similar First Amendment battles. When he was president, Donald J. Trump tried to force a sale or ban of the app in 2020, but federal judges blocked the effort because it would have had the effect of shutting down a “platform for expressive activity.” Montana tried to ban TikTok in the state last year because of the app’s Chinese ownership, but a different federal judge ruled against the state law for similar reasons.
Only one narrower TikTok restriction has survived a court challenge. The governor of Texas announced a ban of the app on state government devices and networks in 2022 because of its Chinese ownership and related data privacy concerns. Professors at public universities challenged the ban in court last year, saying it blocked them from doing research on the app. A federal judge upheld the state ban in December, finding it was a “reasonable restriction” in light of Texas’ concerns and the narrow scope affecting only state employees.
Small Buyer Pool
Analysts estimate that the price for the U.S. portion of TikTok could be tens of billions of dollars.
ByteDance itself is one of the world’s most valuable start-ups , with an estimated worth of $225 billion, according to CB Insights, a firm that tracks venture capital and start-ups.
The steep price tag would limit the list of who could afford TikTok. Tech giants like Meta or Google would probably be blocked from an acquisition because of antitrust concerns.
Private equity firms or other investors could form a group to raise enough money to buy TikTok. Former Treasury Secretary Steven Mnuchin said in March that he wanted to build such a group. And anyone who can pony up the money still has to pass muster with the U.S. government, which needs to sign off on any purchase.
Few others have expressed public interest in buying the app.
The last time the government tried to force ByteDance to sell TikTok in 2020, the company held talks with Microsoft and the software company Oracle. (Oracle and Walmart ultimately appeared to reach an agreement with ByteDance, but the deal never materialized .)
A Complicated Divestment
Even if TikTok approaches a sale, the process of separating TikTok from ByteDance is likely to be messy.
The legislation prohibits any connection between ByteDance and TikTok after a sale. Yet TikTok employees use ByteDance software in their communications, and the company’s employees are global, with executives in Singapore, Dublin, Los Angeles and Mountain View, Calif.
It’s unclear if ByteDance would consider selling TikTok’s entire global footprint or just its U.S. operations, where the company has nearly 7,000 employees.
Breaking off just the U.S. portion of TikTok could prove particularly challenging. The app's recommendation algorithm, which figures out what users like and serves up content, is key to the success of the app. But Chinese engineers work on that algorithm, which ByteDance owns.
During Mr. Trump’s attempt to force a sale in 2020, the Chinese government issued export restrictions that appeared to require its regulators to grant permission before ByteDance algorithms could be sold or licensed to outsiders.
The uncertainty around the export of the algorithm and other ByteDance technology could also deter interested buyers.
China’s Unpredictable Role
The Chinese government could also try to block a TikTok sale.
Chinese officials criticized a similar bill after the House passed it in March, although they have not yet said whether they would block a divestment. About a year ago, China’s commerce ministry said it would “firmly oppose” a sale of the app by ByteDance.
Chinese export regulations appear to cover TikTok’s content recommendation algorithm, giving Beijing a say in whether ByteDance could sell or license the app’s most valuable feature.
It “is not a foregone conclusion by any means” that China will allow a sale, said Lindsay Gorman, a senior fellow at the German Marshall Fund who specializes in emerging tech and China.
China may retaliate against American companies. On Friday, China’s Cyberspace Administration asked Apple to remove Meta’s WhatsApp and Threads from its App Store, according to the iPhone manufacturer. The Chinese government cited national security reasons in making the demand.
Sapna Maheshwari reports on TikTok, technology and emerging media companies. She has been a business reporter for more than a decade. Contact her at [email protected] . More about Sapna Maheshwari
David McCabe covers tech policy. He joined The Times from Axios in 2019. More about David McCabe
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
user rights
- 6 contributors
Use user rights only to refer to Windows security policies that apply to individual user accounts or administrative groups. The system administrator manages user rights through the User Rights Assignment snap-in. User rights are assigned, not granted or allowed .
When you refer to a named user right, use sentence-style capitalization and bold formatting for the name itself.
If an operation requires that the user be signed in to an account that's a member of a specific administrative group, refer to the group instead of to the associated user rights.
Don't use privilege as a synonym for user right .
Examples You must have the Perform volume maintenance tasks user right to perform this task. You must be signed in as a member of the Administrators group to perform this task.
See also permissions , rights
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback .
Submit and view feedback for
Additional resources

COMMENTS
All editions can use Option Three below. 1 Press the Win + R keys to open Run, type secpol.msc into Run, and click/tap on OK to open Local Security Policy. 2 Expand open Local Policies in the left pane of Local Security Policy, and click/tap on User Rights Assignment. (see screenshot below step 3)
User rights are managed in Group Policy under the User Rights Assignment item. Each user right has a constant name and a Group Policy name associated with it. The constant names are used when referring to the user right in log events. You can configure the user rights assignment settings in the following location within the Group Policy ...
undefined. User Rights Assignment is one of those meat and potatoes features of the operating system that we all have a cursory understanding of but rarely think about in depth. User rights include logon rights and permissions. Logon rights control who is authorized to log on to a device and how they can log on.
In the console tree, click Computer Configuration, select Windows Settings, and then select Security Settings. Do one of the following: Select Account Policies to edit the Password Policy or Account Lockout Policy. Select Local Policies to edit an Audit Policy, a User Rights Assignment, or Security Options. In the details pane, double-click the ...
The User Rights Assignment section of Windows Policy is where you get to manage this stuff. To see for yourself, open the default domain controllers Group Policy Object (GPO) or run gpedit.msc. With the policy management window open, navigate to Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment.
User Rights Assignments. Although in this section they are called user rights, these authority assignments are more commonly called privileges. Privileges are computer level actions that you can assign to users or groups. For the sake of maintainability you should only assign privileges to groups not to individual users.
Local Policies/User Rights Assignment. User rights assignments are settings applied to the local device. They allow users to perform various system tasks, such as local logon, remote logon, accessing the server from network, shutting down the server, and so on. In this section, I will explain the most important settings and how they should be ...
This is a list of all the User Rights Assignments available on a Windows network along with a brief description and default values. The definitions are taken from the Microsoft documentation. Access Credential Manager as a trusted caller. The Access Credential Manager as a trusted caller policy setting is used by Credential Manager during ...
If you're asking for User Rights Assignment on a single computer, look for Local Security Policy. If you're asking for User Rights Assignment as a group policy, well, it shows up just fine in my console. Are you using RSAT (Remote Server Administration Tools)? I'm using the RSAT available for Windows 10.
The default rights on a server for local built-in groups are set in the local security settings. To access the local security settings, click Start, type secpol.msc and hit enter. In the Local Security Policy editor, expand Local Policies, and click on User Rights Assignment. There you will see what groups/users are granted which rights.
User rights govern the methods by which a user can log on to a system. User rights are applied at the local device level, and they allow users to perform tas...
User rights permissions control access to computer and domain resources, and they can override permissions that have been set on specific objects. User rights are managed in Group Policy under the User Rights Assignment item. Each user right has a constant name and a Group Policy name associated with it. The constant names are used when ...
I want to edit security settings of user rights assignment of local security policy using powershell or cmd. Eg: policy = "change the system time". default_security_settings = "local service,Administrators". i want to remove everything except Administrators. i have tried ntrights command, but seems like not working Any command will be appreciated.
User Rights Assignment. Specify the users or groups that have sign-in rights or privileges on a device. Security Options. Specify security settings for the computer, such as Administrator and Guest Account names; access to floppy disk drives and CD-ROM drives; installation of drivers; sign-in prompts; and so on.
To create a local account on Windows 11, use these steps: Open Settings. Click on Accounts. Click the Family & other users page on the right side. (Image credit: Future) Under the "Other users ...
User Rights and Privileges. User rights grant specific privileges and logon rights to users and groups in your computing environment. Administrators can assign specific rights to group accounts or to individual user accounts. These rights authorize users to perform specific actions, such as logging on to a system interactively or backing up ...
Find-Module -Name '*sec*pol*' # Results <# Version Name Repository Description ----- ---- ----- ----- 2.10.0.0 SecurityPolicyDsc PSGallery This module is a wrapper around secedit.exe which provides the ability to configure user rights assignments 1.3.2 Indented.SecurityPolicy PSGallery Security management functions and resources 0.0.12 ...
"Bear. Man is scary," one of the women responds. A number of women echoed the responses given in the original video, writing in the comments that they, too, would pick a bear over a man.
Study with Quizlet and memorize flashcards containing terms like Account policies settings are located in which of the following? a.local security policy b.NAP c.remote policy d.EFS security policy, The most common use for AppLocker is malware prevention. True False, Applications that are not designed for Windows 10 and that require administrative privileges do not properly request elevated ...
The Enable computer and user accounts to be trusted for delegation user right should be assigned only if there's a clear need for its functionality. When you assign this right, you should investigate the use of constrained delegation to control what the delegated accounts can do. On domain controllers, this right is assigned to the ...
This document has four sections identified below. It will familiarize you with user rights and roles in terms of adding users to your project. Section 1: User Rights Glossary - this chart defines all the user rights that are available to be assigned for each project user, either directly or through the use of user roles (described next).
Which advanced audit policy setting tracks when tasks are performed that require a user-rights assignment, such as changing the system time? Account Management Object Access Privilege Use Detailed Tracking. Privilege Use. Newer Windows applications use a Manifest to describe the structure of the application.
For domain controllers, assign the Allow log on locally user right only to the Administrators group. For other server roles, you may choose to add Backup Operators in addition to Administrators. For end-user computers, you should also assign this right to the Users group. Alternatively, you can assign groups such as Account Operators, Server ...
The company is expected to argue that a forced sale could violate its users' free speech rights because a new owner could change the app's content policies and reshape what users are able to ...
Medicare.gov Care Compare is a new tool that helps you find and compare the quality of Medicare-approved providers near you. You can search for nursing homes, doctors, hospitals, hospice centers, and more. Learn how to use Care Compare and make informed decisions about your health care. Official Medicare site.
In this article. Use user rights only to refer to Windows security policies that apply to individual user accounts or administrative groups. The system administrator manages user rights through the User Rights Assignment snap-in. User rights are assigned, not granted or allowed. When you refer to a named user right, use sentence-style capitalization and bold formatting for the name itself.