Harvey Cushing/John Hay Whitney Medical Library
- Collections
- Research Help

YSN Doctoral Programs: Steps in Conducting a Literature Review
- Biomedical Databases
- Global (Public Health) Databases
- Soc. Sci., History, and Law Databases
- Grey Literature
- Trials Registers
- Data and Statistics
- Public Policy
- Google Tips
- Recommended Books
- Steps in Conducting a Literature Review
What is a literature review?
A literature review is an integrated analysis -- not just a summary-- of scholarly writings and other relevant evidence related directly to your research question. That is, it represents a synthesis of the evidence that provides background information on your topic and shows a association between the evidence and your research question.
A literature review may be a stand alone work or the introduction to a larger research paper, depending on the assignment. Rely heavily on the guidelines your instructor has given you.
Why is it important?
A literature review is important because it:
- Explains the background of research on a topic.
- Demonstrates why a topic is significant to a subject area.
- Discovers relationships between research studies/ideas.
- Identifies major themes, concepts, and researchers on a topic.
- Identifies critical gaps and points of disagreement.
- Discusses further research questions that logically come out of the previous studies.
APA7 Style resources
APA Style Blog - for those harder to find answers
1. Choose a topic. Define your research question.
Your literature review should be guided by your central research question. The literature represents background and research developments related to a specific research question, interpreted and analyzed by you in a synthesized way.
- Make sure your research question is not too broad or too narrow. Is it manageable?
- Begin writing down terms that are related to your question. These will be useful for searches later.
- If you have the opportunity, discuss your topic with your professor and your class mates.
2. Decide on the scope of your review
How many studies do you need to look at? How comprehensive should it be? How many years should it cover?
- This may depend on your assignment. How many sources does the assignment require?
3. Select the databases you will use to conduct your searches.
Make a list of the databases you will search.
Where to find databases:
- use the tabs on this guide
- Find other databases in the Nursing Information Resources web page
- More on the Medical Library web page
- ... and more on the Yale University Library web page
4. Conduct your searches to find the evidence. Keep track of your searches.
- Use the key words in your question, as well as synonyms for those words, as terms in your search. Use the database tutorials for help.
- Save the searches in the databases. This saves time when you want to redo, or modify, the searches. It is also helpful to use as a guide is the searches are not finding any useful results.
- Review the abstracts of research studies carefully. This will save you time.
- Use the bibliographies and references of research studies you find to locate others.
- Check with your professor, or a subject expert in the field, if you are missing any key works in the field.
- Ask your librarian for help at any time.
- Use a citation manager, such as EndNote as the repository for your citations. See the EndNote tutorials for help.
Review the literature
Some questions to help you analyze the research:
- What was the research question of the study you are reviewing? What were the authors trying to discover?
- Was the research funded by a source that could influence the findings?
- What were the research methodologies? Analyze its literature review, the samples and variables used, the results, and the conclusions.
- Does the research seem to be complete? Could it have been conducted more soundly? What further questions does it raise?
- If there are conflicting studies, why do you think that is?
- How are the authors viewed in the field? Has this study been cited? If so, how has it been analyzed?
Tips:
- Review the abstracts carefully.
- Keep careful notes so that you may track your thought processes during the research process.
- Create a matrix of the studies for easy analysis, and synthesis, across all of the studies.
- << Previous: Recommended Books
- Last Updated: Jan 4, 2024 10:52 AM
- URL: https://guides.library.yale.edu/YSNDoctoral

Research Process :: Step by Step
- Introduction
- Select Topic
- Identify Keywords
- Background Information
- Develop Research Questions
- Refine Topic
- Search Strategy
- Popular Databases
- Evaluate Sources
- Types of Periodicals
- Reading Scholarly Articles
- Primary & Secondary Sources
- Organize / Take Notes
- Writing & Grammar Resources
- Annotated Bibliography
- Literature Review
- Citation Styles
- Paraphrasing
- Privacy / Confidentiality
- Research Process
- Selecting Your Topic
- Identifying Keywords
- Gathering Background Info
- Evaluating Sources

Organize the literature review into sections that present themes or identify trends, including relevant theory. You are not trying to list all the material published, but to synthesize and evaluate it according to the guiding concept of your thesis or research question.
What is a literature review?
A literature review is an account of what has been published on a topic by accredited scholars and researchers. Occasionally you will be asked to write one as a separate assignment, but more often it is part of the introduction to an essay, research report, or thesis. In writing the literature review, your purpose is to convey to your reader what knowledge and ideas have been established on a topic, and what their strengths and weaknesses are. As a piece of writing, the literature review must be defined by a guiding concept (e.g., your research objective, the problem or issue you are discussing, or your argumentative thesis). It is not just a descriptive list of the material available, or a set of summaries
A literature review must do these things:
- be organized around and related directly to the thesis or research question you are developing
- synthesize results into a summary of what is and is not known
- identify areas of controversy in the literature
- formulate questions that need further research
Ask yourself questions like these:
- What is the specific thesis, problem, or research question that my literature review helps to define?
- What type of literature review am I conducting? Am I looking at issues of theory? methodology? policy? quantitative research (e.g. on the effectiveness of a new procedure)? qualitative research (e.g., studies of loneliness among migrant workers)?
- What is the scope of my literature review? What types of publications am I using (e.g., journals, books, government documents, popular media)? What discipline am I working in (e.g., nursing psychology, sociology, medicine)?
- How good was my information seeking? Has my search been wide enough to ensure I've found all the relevant material? Has it been narrow enough to exclude irrelevant material? Is the number of sources I've used appropriate for the length of my paper?
- Have I critically analyzed the literature I use? Do I follow through a set of concepts and questions, comparing items to each other in the ways they deal with them? Instead of just listing and summarizing items, do I assess them, discussing strengths and weaknesses?
- Have I cited and discussed studies contrary to my perspective?
- Will the reader find my literature review relevant, appropriate, and useful?
Ask yourself questions like these about each book or article you include:
- Has the author formulated a problem/issue?
- Is it clearly defined? Is its significance (scope, severity, relevance) clearly established?
- Could the problem have been approached more effectively from another perspective?
- What is the author's research orientation (e.g., interpretive, critical science, combination)?
- What is the author's theoretical framework (e.g., psychological, developmental, feminist)?
- What is the relationship between the theoretical and research perspectives?
- Has the author evaluated the literature relevant to the problem/issue? Does the author include literature taking positions she or he does not agree with?
- In a research study, how good are the basic components of the study design (e.g., population, intervention, outcome)? How accurate and valid are the measurements? Is the analysis of the data accurate and relevant to the research question? Are the conclusions validly based upon the data and analysis?
- In material written for a popular readership, does the author use appeals to emotion, one-sided examples, or rhetorically-charged language and tone? Is there an objective basis to the reasoning, or is the author merely "proving" what he or she already believes?
- How does the author structure the argument? Can you "deconstruct" the flow of the argument to see whether or where it breaks down logically (e.g., in establishing cause-effect relationships)?
- In what ways does this book or article contribute to our understanding of the problem under study, and in what ways is it useful for practice? What are the strengths and limitations?
- How does this book or article relate to the specific thesis or question I am developing?
Text written by Dena Taylor, Health Sciences Writing Centre, University of Toronto
http://www.writing.utoronto.ca/advice/specific-types-of-writing/literature-review
- << Previous: Annotated Bibliography
- Next: Step 5: Cite Sources >>
- Last Updated: May 3, 2024 1:54 PM
- URL: https://libguides.uta.edu/researchprocess
University of Texas Arlington Libraries 702 Planetarium Place · Arlington, TX 76019 · 817-272-3000
- Internet Privacy
- Accessibility
- Problems with a guide? Contact Us.
How To Write An A-Grade Literature Review
3 straightforward steps (with examples) + free template.
By: Derek Jansen (MBA) | Expert Reviewed By: Dr. Eunice Rautenbach | October 2019
Quality research is about building onto the existing work of others , “standing on the shoulders of giants”, as Newton put it. The literature review chapter of your dissertation, thesis or research project is where you synthesise this prior work and lay the theoretical foundation for your own research.
Long story short, this chapter is a pretty big deal, which is why you want to make sure you get it right . In this post, I’ll show you exactly how to write a literature review in three straightforward steps, so you can conquer this vital chapter (the smart way).
Overview: The Literature Review Process
- Understanding the “ why “
- Finding the relevant literature
- Cataloguing and synthesising the information
- Outlining & writing up your literature review
- Example of a literature review
But first, the “why”…
Before we unpack how to write the literature review chapter, we’ve got to look at the why . To put it bluntly, if you don’t understand the function and purpose of the literature review process, there’s no way you can pull it off well. So, what exactly is the purpose of the literature review?
Well, there are (at least) four core functions:
- For you to gain an understanding (and demonstrate this understanding) of where the research is at currently, what the key arguments and disagreements are.
- For you to identify the gap(s) in the literature and then use this as justification for your own research topic.
- To help you build a conceptual framework for empirical testing (if applicable to your research topic).
- To inform your methodological choices and help you source tried and tested questionnaires (for interviews ) and measurement instruments (for surveys ).
Most students understand the first point but don’t give any thought to the rest. To get the most from the literature review process, you must keep all four points front of mind as you review the literature (more on this shortly), or you’ll land up with a wonky foundation.
Okay – with the why out the way, let’s move on to the how . As mentioned above, writing your literature review is a process, which I’ll break down into three steps:
- Finding the most suitable literature
- Understanding , distilling and organising the literature
- Planning and writing up your literature review chapter
Importantly, you must complete steps one and two before you start writing up your chapter. I know it’s very tempting, but don’t try to kill two birds with one stone and write as you read. You’ll invariably end up wasting huge amounts of time re-writing and re-shaping, or you’ll just land up with a disjointed, hard-to-digest mess . Instead, you need to read first and distil the information, then plan and execute the writing.

Step 1: Find the relevant literature
Naturally, the first step in the literature review journey is to hunt down the existing research that’s relevant to your topic. While you probably already have a decent base of this from your research proposal , you need to expand on this substantially in the dissertation or thesis itself.
Essentially, you need to be looking for any existing literature that potentially helps you answer your research question (or develop it, if that’s not yet pinned down). There are numerous ways to find relevant literature, but I’ll cover my top four tactics here. I’d suggest combining all four methods to ensure that nothing slips past you:
Method 1 – Google Scholar Scrubbing
Google’s academic search engine, Google Scholar , is a great starting point as it provides a good high-level view of the relevant journal articles for whatever keyword you throw at it. Most valuably, it tells you how many times each article has been cited, which gives you an idea of how credible (or at least, popular) it is. Some articles will be free to access, while others will require an account, which brings us to the next method.
Method 2 – University Database Scrounging
Generally, universities provide students with access to an online library, which provides access to many (but not all) of the major journals.
So, if you find an article using Google Scholar that requires paid access (which is quite likely), search for that article in your university’s database – if it’s listed there, you’ll have access. Note that, generally, the search engine capabilities of these databases are poor, so make sure you search for the exact article name, or you might not find it.
Method 3 – Journal Article Snowballing
At the end of every academic journal article, you’ll find a list of references. As with any academic writing, these references are the building blocks of the article, so if the article is relevant to your topic, there’s a good chance a portion of the referenced works will be too. Do a quick scan of the titles and see what seems relevant, then search for the relevant ones in your university’s database.
Method 4 – Dissertation Scavenging
Similar to Method 3 above, you can leverage other students’ dissertations. All you have to do is skim through literature review chapters of existing dissertations related to your topic and you’ll find a gold mine of potential literature. Usually, your university will provide you with access to previous students’ dissertations, but you can also find a much larger selection in the following databases:
- Open Access Theses & Dissertations
- Stanford SearchWorks
Keep in mind that dissertations and theses are not as academically sound as published, peer-reviewed journal articles (because they’re written by students, not professionals), so be sure to check the credibility of any sources you find using this method. You can do this by assessing the citation count of any given article in Google Scholar. If you need help with assessing the credibility of any article, or with finding relevant research in general, you can chat with one of our Research Specialists .
Alright – with a good base of literature firmly under your belt, it’s time to move onto the next step.
Need a helping hand?
Step 2: Log, catalogue and synthesise
Once you’ve built a little treasure trove of articles, it’s time to get reading and start digesting the information – what does it all mean?
While I present steps one and two (hunting and digesting) as sequential, in reality, it’s more of a back-and-forth tango – you’ll read a little , then have an idea, spot a new citation, or a new potential variable, and then go back to searching for articles. This is perfectly natural – through the reading process, your thoughts will develop , new avenues might crop up, and directional adjustments might arise. This is, after all, one of the main purposes of the literature review process (i.e. to familiarise yourself with the current state of research in your field).
As you’re working through your treasure chest, it’s essential that you simultaneously start organising the information. There are three aspects to this:
- Logging reference information
- Building an organised catalogue
- Distilling and synthesising the information
I’ll discuss each of these below:
2.1 – Log the reference information
As you read each article, you should add it to your reference management software. I usually recommend Mendeley for this purpose (see the Mendeley 101 video below), but you can use whichever software you’re comfortable with. Most importantly, make sure you load EVERY article you read into your reference manager, even if it doesn’t seem very relevant at the time.
2.2 – Build an organised catalogue
In the beginning, you might feel confident that you can remember who said what, where, and what their main arguments were. Trust me, you won’t. If you do a thorough review of the relevant literature (as you must!), you’re going to read many, many articles, and it’s simply impossible to remember who said what, when, and in what context . Also, without the bird’s eye view that a catalogue provides, you’ll miss connections between various articles, and have no view of how the research developed over time. Simply put, it’s essential to build your own catalogue of the literature.
I would suggest using Excel to build your catalogue, as it allows you to run filters, colour code and sort – all very useful when your list grows large (which it will). How you lay your spreadsheet out is up to you, but I’d suggest you have the following columns (at minimum):
- Author, date, title – Start with three columns containing this core information. This will make it easy for you to search for titles with certain words, order research by date, or group by author.
- Categories or keywords – You can either create multiple columns, one for each category/theme and then tick the relevant categories, or you can have one column with keywords.
- Key arguments/points – Use this column to succinctly convey the essence of the article, the key arguments and implications thereof for your research.
- Context – Note the socioeconomic context in which the research was undertaken. For example, US-based, respondents aged 25-35, lower- income, etc. This will be useful for making an argument about gaps in the research.
- Methodology – Note which methodology was used and why. Also, note any issues you feel arise due to the methodology. Again, you can use this to make an argument about gaps in the research.
- Quotations – Note down any quoteworthy lines you feel might be useful later.
- Notes – Make notes about anything not already covered. For example, linkages to or disagreements with other theories, questions raised but unanswered, shortcomings or limitations, and so forth.
If you’d like, you can try out our free catalog template here (see screenshot below).
2.3 – Digest and synthesise
Most importantly, as you work through the literature and build your catalogue, you need to synthesise all the information in your own mind – how does it all fit together? Look for links between the various articles and try to develop a bigger picture view of the state of the research. Some important questions to ask yourself are:
- What answers does the existing research provide to my own research questions ?
- Which points do the researchers agree (and disagree) on?
- How has the research developed over time?
- Where do the gaps in the current research lie?
To help you develop a big-picture view and synthesise all the information, you might find mind mapping software such as Freemind useful. Alternatively, if you’re a fan of physical note-taking, investing in a large whiteboard might work for you.
Step 3: Outline and write it up!
Once you’re satisfied that you have digested and distilled all the relevant literature in your mind, it’s time to put pen to paper (or rather, fingers to keyboard). There are two steps here – outlining and writing:
3.1 – Draw up your outline
Having spent so much time reading, it might be tempting to just start writing up without a clear structure in mind. However, it’s critically important to decide on your structure and develop a detailed outline before you write anything. Your literature review chapter needs to present a clear, logical and an easy to follow narrative – and that requires some planning. Don’t try to wing it!
Naturally, you won’t always follow the plan to the letter, but without a detailed outline, you’re more than likely going to end up with a disjointed pile of waffle , and then you’re going to spend a far greater amount of time re-writing, hacking and patching. The adage, “measure twice, cut once” is very suitable here.
In terms of structure, the first decision you’ll have to make is whether you’ll lay out your review thematically (into themes) or chronologically (by date/period). The right choice depends on your topic, research objectives and research questions, which we discuss in this article .
Once that’s decided, you need to draw up an outline of your entire chapter in bullet point format. Try to get as detailed as possible, so that you know exactly what you’ll cover where, how each section will connect to the next, and how your entire argument will develop throughout the chapter. Also, at this stage, it’s a good idea to allocate rough word count limits for each section, so that you can identify word count problems before you’ve spent weeks or months writing!
PS – check out our free literature review chapter template…
3.2 – Get writing
With a detailed outline at your side, it’s time to start writing up (finally!). At this stage, it’s common to feel a bit of writer’s block and find yourself procrastinating under the pressure of finally having to put something on paper. To help with this, remember that the objective of the first draft is not perfection – it’s simply to get your thoughts out of your head and onto paper, after which you can refine them. The structure might change a little, the word count allocations might shift and shuffle, and you might add or remove a section – that’s all okay. Don’t worry about all this on your first draft – just get your thoughts down on paper.

Once you’ve got a full first draft (however rough it may be), step away from it for a day or two (longer if you can) and then come back at it with fresh eyes. Pay particular attention to the flow and narrative – does it fall fit together and flow from one section to another smoothly? Now’s the time to try to improve the linkage from each section to the next, tighten up the writing to be more concise, trim down word count and sand it down into a more digestible read.
Once you’ve done that, give your writing to a friend or colleague who is not a subject matter expert and ask them if they understand the overall discussion. The best way to assess this is to ask them to explain the chapter back to you. This technique will give you a strong indication of which points were clearly communicated and which weren’t. If you’re working with Grad Coach, this is a good time to have your Research Specialist review your chapter.
Finally, tighten it up and send it off to your supervisor for comment. Some might argue that you should be sending your work to your supervisor sooner than this (indeed your university might formally require this), but in my experience, supervisors are extremely short on time (and often patience), so, the more refined your chapter is, the less time they’ll waste on addressing basic issues (which you know about already) and the more time they’ll spend on valuable feedback that will increase your mark-earning potential.
Literature Review Example
In the video below, we unpack an actual literature review so that you can see how all the core components come together in reality.
Let’s Recap
In this post, we’ve covered how to research and write up a high-quality literature review chapter. Let’s do a quick recap of the key takeaways:
- It is essential to understand the WHY of the literature review before you read or write anything. Make sure you understand the 4 core functions of the process.
- The first step is to hunt down the relevant literature . You can do this using Google Scholar, your university database, the snowballing technique and by reviewing other dissertations and theses.
- Next, you need to log all the articles in your reference manager , build your own catalogue of literature and synthesise all the research.
- Following that, you need to develop a detailed outline of your entire chapter – the more detail the better. Don’t start writing without a clear outline (on paper, not in your head!)
- Write up your first draft in rough form – don’t aim for perfection. Remember, done beats perfect.
- Refine your second draft and get a layman’s perspective on it . Then tighten it up and submit it to your supervisor.

Psst… there’s more!
This post is an extract from our bestselling short course, Literature Review Bootcamp . If you want to work smart, you don't want to miss this .
You Might Also Like:

38 Comments
Thank you very much. This page is an eye opener and easy to comprehend.
This is awesome!
I wish I come across GradCoach earlier enough.
But all the same I’ll make use of this opportunity to the fullest.
Thank you for this good job.
Keep it up!
You’re welcome, Yinka. Thank you for the kind words. All the best writing your literature review.
Thank you for a very useful literature review session. Although I am doing most of the steps…it being my first masters an Mphil is a self study and one not sure you are on the right track. I have an amazing supervisor but one also knows they are super busy. So not wanting to bother on the minutae. Thank you.
You’re most welcome, Renee. Good luck with your literature review 🙂
This has been really helpful. Will make full use of it. 🙂
Thank you Gradcoach.
Really agreed. Admirable effort
thank you for this beautiful well explained recap.
Thank you so much for your guide of video and other instructions for the dissertation writing.
It is instrumental. It encouraged me to write a dissertation now.
Thank you the video was great – from someone that knows nothing thankyou
an amazing and very constructive way of presetting a topic, very useful, thanks for the effort,
It is timely
It is very good video of guidance for writing a research proposal and a dissertation. Since I have been watching and reading instructions, I have started my research proposal to write. I appreciate to Mr Jansen hugely.
I learn a lot from your videos. Very comprehensive and detailed.
Thank you for sharing your knowledge. As a research student, you learn better with your learning tips in research
I was really stuck in reading and gathering information but after watching these things are cleared thanks, it is so helpful.
Really helpful, Thank you for the effort in showing such information
This is super helpful thank you very much.
Thank you for this whole literature writing review.You have simplified the process.
I’m so glad I found GradCoach. Excellent information, Clear explanation, and Easy to follow, Many thanks Derek!
You’re welcome, Maithe. Good luck writing your literature review 🙂
Thank you Coach, you have greatly enriched and improved my knowledge
Great piece, so enriching and it is going to help me a great lot in my project and thesis, thanks so much
This is THE BEST site for ANYONE doing a masters or doctorate! Thank you for the sound advice and templates. You rock!
Thanks, Stephanie 🙂
This is mind blowing, the detailed explanation and simplicity is perfect.
I am doing two papers on my final year thesis, and I must stay I feel very confident to face both headlong after reading this article.
thank you so much.
if anyone is to get a paper done on time and in the best way possible, GRADCOACH is certainly the go to area!
This is very good video which is well explained with detailed explanation
Thank you excellent piece of work and great mentoring
Thanks, it was useful
Thank you very much. the video and the information were very helpful.
Good morning scholar. I’m delighted coming to know you even before the commencement of my dissertation which hopefully is expected in not more than six months from now. I would love to engage my study under your guidance from the beginning to the end. I love to know how to do good job
Thank you so much Derek for such useful information on writing up a good literature review. I am at a stage where I need to start writing my one. My proposal was accepted late last year but I honestly did not know where to start
Like the name of your YouTube implies you are GRAD (great,resource person, about dissertation). In short you are smart enough in coaching research work.
This is a very well thought out webpage. Very informative and a great read.
Very timely.
I appreciate.
Very comprehensive and eye opener for me as beginner in postgraduate study. Well explained and easy to understand. Appreciate and good reference in guiding me in my research journey. Thank you
Thank you. I requested to download the free literature review template, however, your website wouldn’t allow me to complete the request or complete a download. May I request that you email me the free template? Thank you.
Submit a Comment Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
- Print Friendly
Research Methods
- Getting Started
- Literature Review Research
- Research Design
- Research Design By Discipline
- SAGE Research Methods
- Teaching with SAGE Research Methods
Literature Review
- What is a Literature Review?
- What is NOT a Literature Review?
- Purposes of a Literature Review
- Types of Literature Reviews
- Literature Reviews vs. Systematic Reviews
- Systematic vs. Meta-Analysis
Literature Review is a comprehensive survey of the works published in a particular field of study or line of research, usually over a specific period of time, in the form of an in-depth, critical bibliographic essay or annotated list in which attention is drawn to the most significant works.
Also, we can define a literature review as the collected body of scholarly works related to a topic:
- Summarizes and analyzes previous research relevant to a topic
- Includes scholarly books and articles published in academic journals
- Can be an specific scholarly paper or a section in a research paper
The objective of a Literature Review is to find previous published scholarly works relevant to an specific topic
- Help gather ideas or information
- Keep up to date in current trends and findings
- Help develop new questions
A literature review is important because it:
- Explains the background of research on a topic.
- Demonstrates why a topic is significant to a subject area.
- Helps focus your own research questions or problems
- Discovers relationships between research studies/ideas.
- Suggests unexplored ideas or populations
- Identifies major themes, concepts, and researchers on a topic.
- Tests assumptions; may help counter preconceived ideas and remove unconscious bias.
- Identifies critical gaps, points of disagreement, or potentially flawed methodology or theoretical approaches.
- Indicates potential directions for future research.
All content in this section is from Literature Review Research from Old Dominion University
Keep in mind the following, a literature review is NOT:
Not an essay
Not an annotated bibliography in which you summarize each article that you have reviewed. A literature review goes beyond basic summarizing to focus on the critical analysis of the reviewed works and their relationship to your research question.
Not a research paper where you select resources to support one side of an issue versus another. A lit review should explain and consider all sides of an argument in order to avoid bias, and areas of agreement and disagreement should be highlighted.
A literature review serves several purposes. For example, it
- provides thorough knowledge of previous studies; introduces seminal works.
- helps focus one’s own research topic.
- identifies a conceptual framework for one’s own research questions or problems; indicates potential directions for future research.
- suggests previously unused or underused methodologies, designs, quantitative and qualitative strategies.
- identifies gaps in previous studies; identifies flawed methodologies and/or theoretical approaches; avoids replication of mistakes.
- helps the researcher avoid repetition of earlier research.
- suggests unexplored populations.
- determines whether past studies agree or disagree; identifies controversy in the literature.
- tests assumptions; may help counter preconceived ideas and remove unconscious bias.
As Kennedy (2007) notes*, it is important to think of knowledge in a given field as consisting of three layers. First, there are the primary studies that researchers conduct and publish. Second are the reviews of those studies that summarize and offer new interpretations built from and often extending beyond the original studies. Third, there are the perceptions, conclusions, opinion, and interpretations that are shared informally that become part of the lore of field. In composing a literature review, it is important to note that it is often this third layer of knowledge that is cited as "true" even though it often has only a loose relationship to the primary studies and secondary literature reviews.
Given this, while literature reviews are designed to provide an overview and synthesis of pertinent sources you have explored, there are several approaches to how they can be done, depending upon the type of analysis underpinning your study. Listed below are definitions of types of literature reviews:
Argumentative Review This form examines literature selectively in order to support or refute an argument, deeply imbedded assumption, or philosophical problem already established in the literature. The purpose is to develop a body of literature that establishes a contrarian viewpoint. Given the value-laden nature of some social science research [e.g., educational reform; immigration control], argumentative approaches to analyzing the literature can be a legitimate and important form of discourse. However, note that they can also introduce problems of bias when they are used to to make summary claims of the sort found in systematic reviews.
Integrative Review Considered a form of research that reviews, critiques, and synthesizes representative literature on a topic in an integrated way such that new frameworks and perspectives on the topic are generated. The body of literature includes all studies that address related or identical hypotheses. A well-done integrative review meets the same standards as primary research in regard to clarity, rigor, and replication.
Historical Review Few things rest in isolation from historical precedent. Historical reviews are focused on examining research throughout a period of time, often starting with the first time an issue, concept, theory, phenomena emerged in the literature, then tracing its evolution within the scholarship of a discipline. The purpose is to place research in a historical context to show familiarity with state-of-the-art developments and to identify the likely directions for future research.
Methodological Review A review does not always focus on what someone said [content], but how they said it [method of analysis]. This approach provides a framework of understanding at different levels (i.e. those of theory, substantive fields, research approaches and data collection and analysis techniques), enables researchers to draw on a wide variety of knowledge ranging from the conceptual level to practical documents for use in fieldwork in the areas of ontological and epistemological consideration, quantitative and qualitative integration, sampling, interviewing, data collection and data analysis, and helps highlight many ethical issues which we should be aware of and consider as we go through our study.
Systematic Review This form consists of an overview of existing evidence pertinent to a clearly formulated research question, which uses pre-specified and standardized methods to identify and critically appraise relevant research, and to collect, report, and analyse data from the studies that are included in the review. Typically it focuses on a very specific empirical question, often posed in a cause-and-effect form, such as "To what extent does A contribute to B?"
Theoretical Review The purpose of this form is to concretely examine the corpus of theory that has accumulated in regard to an issue, concept, theory, phenomena. The theoretical literature review help establish what theories already exist, the relationships between them, to what degree the existing theories have been investigated, and to develop new hypotheses to be tested. Often this form is used to help establish a lack of appropriate theories or reveal that current theories are inadequate for explaining new or emerging research problems. The unit of analysis can focus on a theoretical concept or a whole theory or framework.
* Kennedy, Mary M. "Defining a Literature." Educational Researcher 36 (April 2007): 139-147.
All content in this section is from The Literature Review created by Dr. Robert Larabee USC
Robinson, P. and Lowe, J. (2015), Literature reviews vs systematic reviews. Australian and New Zealand Journal of Public Health, 39: 103-103. doi: 10.1111/1753-6405.12393

What's in the name? The difference between a Systematic Review and a Literature Review, and why it matters . By Lynn Kysh from University of Southern California

Systematic review or meta-analysis?
A systematic review answers a defined research question by collecting and summarizing all empirical evidence that fits pre-specified eligibility criteria.
A meta-analysis is the use of statistical methods to summarize the results of these studies.
Systematic reviews, just like other research articles, can be of varying quality. They are a significant piece of work (the Centre for Reviews and Dissemination at York estimates that a team will take 9-24 months), and to be useful to other researchers and practitioners they should have:
- clearly stated objectives with pre-defined eligibility criteria for studies
- explicit, reproducible methodology
- a systematic search that attempts to identify all studies
- assessment of the validity of the findings of the included studies (e.g. risk of bias)
- systematic presentation, and synthesis, of the characteristics and findings of the included studies
Not all systematic reviews contain meta-analysis.
Meta-analysis is the use of statistical methods to summarize the results of independent studies. By combining information from all relevant studies, meta-analysis can provide more precise estimates of the effects of health care than those derived from the individual studies included within a review. More information on meta-analyses can be found in Cochrane Handbook, Chapter 9 .
A meta-analysis goes beyond critique and integration and conducts secondary statistical analysis on the outcomes of similar studies. It is a systematic review that uses quantitative methods to synthesize and summarize the results.
An advantage of a meta-analysis is the ability to be completely objective in evaluating research findings. Not all topics, however, have sufficient research evidence to allow a meta-analysis to be conducted. In that case, an integrative review is an appropriate strategy.
Some of the content in this section is from Systematic reviews and meta-analyses: step by step guide created by Kate McAllister.
- << Previous: Getting Started
- Next: Research Design >>
- Last Updated: Aug 21, 2023 4:07 PM
- URL: https://guides.lib.udel.edu/researchmethods
- University of Texas Libraries
Literature Reviews
- What is a literature review?
- Steps in the Literature Review Process
- Define your research question
- Determine inclusion and exclusion criteria
- Choose databases and search
- Review Results
- Synthesize Results
- Analyze Results
- Librarian Support
What is a Literature Review?
A literature or narrative review is a comprehensive review and analysis of the published literature on a specific topic or research question. The literature that is reviewed contains: books, articles, academic articles, conference proceedings, association papers, and dissertations. It contains the most pertinent studies and points to important past and current research and practices. It provides background and context, and shows how your research will contribute to the field.
A literature review should:
- Provide a comprehensive and updated review of the literature;
- Explain why this review has taken place;
- Articulate a position or hypothesis;
- Acknowledge and account for conflicting and corroborating points of view
From S age Research Methods
Purpose of a Literature Review
A literature review can be written as an introduction to a study to:
- Demonstrate how a study fills a gap in research
- Compare a study with other research that's been done
Or it can be a separate work (a research article on its own) which:
- Organizes or describes a topic
- Describes variables within a particular issue/problem
Limitations of a Literature Review
Some of the limitations of a literature review are:
- It's a snapshot in time. Unlike other reviews, this one has beginning, a middle and an end. There may be future developments that could make your work less relevant.
- It may be too focused. Some niche studies may miss the bigger picture.
- It can be difficult to be comprehensive. There is no way to make sure all the literature on a topic was considered.
- It is easy to be biased if you stick to top tier journals. There may be other places where people are publishing exemplary research. Look to open access publications and conferences to reflect a more inclusive collection. Also, make sure to include opposing views (and not just supporting evidence).
Source: Grant, Maria J., and Andrew Booth. “A Typology of Reviews: An Analysis of 14 Review Types and Associated Methodologies.” Health Information & Libraries Journal, vol. 26, no. 2, June 2009, pp. 91–108. Wiley Online Library, doi:10.1111/j.1471-1842.2009.00848.x.
Meryl Brodsky : Communication and Information Studies
Hannah Chapman Tripp : Biology, Neuroscience
Carolyn Cunningham : Human Development & Family Sciences, Psychology, Sociology
Larayne Dallas : Engineering
Janelle Hedstrom : Special Education, Curriculum & Instruction, Ed Leadership & Policy
Susan Macicak : Linguistics
Imelda Vetter : Dell Medical School
For help in other subject areas, please see the guide to library specialists by subject .
Periodically, UT Libraries runs a workshop covering the basics and library support for literature reviews. While we try to offer these once per academic year, we find providing the recording to be helpful to community members who have missed the session. Following is the most recent recording of the workshop, Conducting a Literature Review. To view the recording, a UT login is required.
- October 26, 2022 recording
- Last Updated: Oct 26, 2022 2:49 PM
- URL: https://guides.lib.utexas.edu/literaturereviews


Research Process Guide
- Step 1 - Identifying and Developing a Topic
- Step 2 - Narrowing Your Topic
- Step 3 - Developing Research Questions
- Step 4 - Conducting a Literature Review
- Step 5 - Choosing a Conceptual or Theoretical Framework
- Step 6 - Determining Research Methodology
- Step 6a - Determining Research Methodology - Quantitative Research Methods
- Step 6b - Determining Research Methodology - Qualitative Design
- Step 7 - Considering Ethical Issues in Research with Human Subjects - Institutional Review Board (IRB)
- Step 8 - Collecting Data
- Step 9 - Analyzing Data
- Step 10 - Interpreting Results
- Step 11 - Writing Up Results
Step 4: Conducting a Literature Review

In order to understand your topic, before you conduct your research, it is extremely important to immerse yourself in the research that has been done on your topic and the topics that might be adjacent to your particular research interest or questions. “a researcher cannot perform significant research without first understanding the literature in the field” (Boote & Beile, 2005, p. 3). Essentially, When writing a thesis or research proposal, the review of the literature would be your Chapter 2 .
Frankly, the literature review is often the first major challenge of the writing process. Sometimes, the task to review and synthesize all of the previous research on and around your topic can feel overwhelming. Although the literature review is foundational to situate your research within the body of literature on your topic, there is almost no literature on the challenges and pitfalls of writing a literature review (Randolph, 2009).
Boote and Beile (2005) reveal through their research on dissertation writing, that although a sophisticated literature review is essential for substantial research, they are often poorly written and lack organizational structure and conceptual relevance. So, the question is, how can you write a literature that is well-organized, comprehensive and situate your research within the literature?
Onweugbuzie et al. (2012) identify 23 core components of an effective literature review in their research and are referred to as the standard checklist for most empirical researchers. The list includes the following:
- What has been researched and what needs to be in the future.
- Identify variables within the literature that are relevant to your study.
- Identify the relationship between theory and practice within the literature.
- Discuss the quality of research with particular emphasis on the exemplary studies.
- Examine the methodologies and research design used throughout the literature, and evaluate the efficacy.
- Pay attention to any contradictions within the literature and
- Make sure to not replicate studies that have already been completed, however, if there are similarities, identify how your study and variables examined are important, different, and relevant.
How to complete a literature review
Fair Warning: The literature review is often time-consuming and can feel like an endless process. Don’t Give Up! It is the first major hurdle of the research proposal process. Once you have completed the literature review, you will have a good idea of what is significant, relevant and novel about your research. The key is to spend time reading, recording important findings, and organizing the scholarly literature on (and around) your topic.
At this point, it is important to distinguish between scholarly literature and other sources. You need to keep in mind that you are only reviewing scholarly literature, which includes sources and studies that have a clear methodology, empirical evidence, results and conclusions. These studies are PEER-REVIEWED, meaning, contemporaries in the field have reviewed the research methods and findings of the literature, and found them relevant, significant, authentic and valid (Wakefield, 2015).
Where do you begin? Great question.
According to Randolph (2009), the goal of a literature review is to integrate and generalize findings across studies, debate findings within a field, resolve the debate, and discuss the language specific to the field. For a meta-analysis, which is a common strategy for a literature review, the goal is largely to integrate quantitative findings across the research on the topic. For other strategies to complete the literature review, the goals may be to critically analyze previous studies, identify central themes or issues within the existing literature or analyze an argument in the field (Randolph, 2009). In literature reviews for dissertation, the goal is to largely interrogate and analyze the current findings to find weaknesses or contradictions in order to place your study within the context of the current literature and to justify your study’s relevance. So in essence, the goals of literature review, regardless of the strategy, are not only to deal with the central theme across the literature and to present a thematic analysis of that literature, but also, and perhaps more importantly, it is to focus on whether the body of knowledge is credible, reliable and valid based on the methodological approaches and outcomes of the literature in the field (Wakefield, 2015).
A few initial steps are:
- Develop a list of key words and phrases that relate to your topic and questions (Denney & Tewksbury, 2013).
- Search for relevant sources using useful databases found in Kean University’s Library :
- Kean University’s WorldCat Discovery single-search application
- ERIC (education)
- JSTOR (multidisciplinary)
- Project Muse (humanities and social science)
- Web of Science (citation searching)
- Google Scholar
- Set up an account with a bibliographic citation manager like EndNote Online (access provided by Kean University) or a freely available option such as Zotero. The EndNote Online Guide provides separate on-campus and off-campus account registration instructions. A bibliographic citation manager will not only help you manage and organize your sources, but it will also help you format your references in various citation styles.
- Take advantage of research support options provided by Kean’s librarians, including workshops , appointments with a librarian , and 24/7 Chat .
If you identify a source (article or book) that is not available through Kean University’s library collections, you may submit an Interlibrary Loan request. Book or article records found in the WorldCat Discovery database will feature an Interlibrary Loan request option. However, you may also utilize the Interlibrary Loan form .
You may also use the VALE Reciprocal Borrowing Program , which enables Kean University students and faculty to check out books from libraries at other New Jersey colleges and universities. To participate in this program, a researcher must first obtain a signed "VALE Reciprocal Borrowing Application Form" from the Nancy Thompson Learning Commons before they can borrow at one of the participating libraries .
What are the sources that are appropriate for a literature review? According to Garrard (2009) and others scientific or empirical research refers to the:
…theoretical and research publications in scientific journals, reference books, government practice, policy statements, and other materials about the theory, practice, and results of scientific inquiry. These materials and publications are produced by individuals or groups in universities, foundations, government research laboratories, and other nonprofit or for-profit organizations (p.4). Onwuegbuzie et al. (2010; as cited in Onwuegbuzie et al., 2012) goes further and describes the literature that could be included in a literature review, “research articles,… essays, article reviews, monographs, dissertations, books, Internet websites, video, interview transcripts, encyclopedias, company reports, trade catalogues, government documents, congressional/parliamentary bills…” (p. 7). However, Onwuegbuzie et al. (2012) builds on this definition, by saying that a literature review is largely, “a systematic, explicit, and reproducible method for identifying, evaluating, and synthesizing the existing body of completed and recorded work produced by researchers, scholars and practitioners” (p.3).
So, what does this mean for you, the researcher and author of the literature review? You want to use multiple source types. Additionally, stick to the parameters laid out by Onwuegbuzie et al. (2012) in that the literature reviewed should be an evaluation and synthesis of the existing work completed by “researchers, scholars and practitioners.” The list of sources should be semi-exhaustive and representative of the field.
Next, you should:
3. Evaluate and select your sources. Read the abstract first to see if the source is relevant to your topic (Wakefield, 2015; Denney & Tewksbury, 2013; Randolph, 2009).
- Is this source peer-reviewed?
- Is this source presenting empirical evidence, meeting the threshold for scholarly research?
- Is this topic relevant to my research topic/questions?
Organizing your Literature Review:
Outline your literature review- how do you want it organized? You are “synthesizing” the literature as your purpose here. What structure works best for your topic and study? The most common formats are (Randolph, 2009; Onwuegbuzie et al., 2012):
- Historical format - literature is reviewed chronologically.This method is preferred when there is a goal of analyzing the progression of research methods, theories or practices over time.
- Conceptual format - centered arounds the propositions in research rationale or a theoretical- centered review which is organized according to the theories in the literature.
- Methodological format - this involves the discussion of methodology as in an imperial paper including an introduction, method, results and discussion. This approach is most commonly used in meta- analytical reports.
Let’s talk about synthesis.
A literature review is not only a review of the empirical research, but it is also evaluation and synthesis of the research. Boote and Beile (2005) have created a five- category list for evaluating a literature review. The categories are coverage, synthesis, methodology, significance, and rhetoric .
- You need to create a justified criteria for including and excluding studies from your review
- You need to discuss what has been done in the field and what still needs to be done.
- Place the topic or problem within the greater context of scholarly literature.
- Place the topic or problem within the historical context.
- Discuss the subject vocabulary.
- Articulate the important variables and phenomena that are relevant to the topic.
- Synthesize and discuss a new perspective on the literature.
- Identify the main methods and research techniques that have been used in the field as well as their advantages/disadvantages.
- Relate ideas and theories to research methodologies.
- Rationalize the practical significance of the research problem.
- Rationalize the scholarly significance of the research problem.
- Write in coherent language and be sure the organization/ structure of the review makes sense.
Synthesis is difficult - you need to articulate what this literature means for your research and/or how does the literature inform the purpose, impact, methodology of your study? Rather than summarizing, the idea behind synthesis is taking the information you have discussed and drawing your own conclusions, making connections between the literature and your study.
Boote, D. N., & Beile, P. (2005). Scholars before researchers: On the centrality of the dissertation literature review in research preparation. Educational Researcher, 34 (6), 3-15. https://www.jstor.org/stable/3699805
Denney, A. S., & Tewksbury, R. (2013). How to write a literature review. Journal of Criminal Justice Education, 24 (2), 218-234. https://doi-org.kean.idm.oclc.org/10.1080/10511253.2012.730617
Garrard, J. (2009). Health sciences literature review made easy: The matrix method. Jones and Bartlett.
Onwuegbuzie, A. J., Leech, N. L., & Collins, K. M. (2012). Qualitative analysis techniques for the review of the literature. Qualitative Report, 17( 28), 1-28.
Randolph, J. (2009). A guide to writing the dissertation literature review. Practical Assessment, Research, and Evaluation, 14 (1), 13.
Wakefield, A. (2015). Synthesising the literature as part of a literature review. Nursing Standard, 29 (29), 44-51. https://doi.org/10.7748/ns.29.29.44.e8957
- Last Updated: Jun 29, 2023 1:35 PM
- URL: https://libguides.kean.edu/ResearchProcessGuide

Graduate Research: Guide to the Literature Review
- "Literature review" defined
- Research Communication Graphic
- Literature Review Steps
- Search techniques
- Finding Additional "Items
- Evaluating information
- Citing Styles
- Ethical Use of Information
- Research Databases This link opens in a new window
- Get Full Text
- Reading a Scholarly Article
- Author Rights
- Selecting a publisher
Introduction to Research Process: Literature Review Steps
When seeking information for a literature review or for any purpose, it helps to understand information-seeking as a process that you can follow. 5 Each of the six (6) steps has its own section in this web page with more detail. Do (and re-do) the following six steps:
1. Define your topic. The first step is defining your task -- choosing a topic and noting the questions you have about the topic. This will provide a focus that guides your strategy in step II and will provide potential words to use in searches in step III.
2. Develop a strategy. Strategy involves figuring out where the information might be and identifying the best tools for finding those types of sources. The strategy section identifies specific types of research databases to use for specific purposes.
3. Locate the information . In this step, you implement the strategy developed in II in order to actually locate specific articles, books, technical reports, etc.
4. Use and Evaluate the information. Having located relevant and useful material, in step IV you read and analyze the items to determine whether they have value for your project and credibility as sources.
5. Synthesize. In step V, you will make sense of what you've learned and demonstrate your knowledge. You will thoroughly understand, organize and integrate the information --become knowledgeable-- so that you are able to use your own words to support and explain your research project and its relationship to existing research by others.
6. Evaluate your work. At every step along the way, you should evaluate your work. However, this final step is a last check to make sure your work is complete and of high quality.
Continue below to begin working through the process.
5. Eisenberg, M. B., & Berkowitz, R. E. (1990). Information Problem-Solving: the Big Six Skills Approach to Library & Information Skills Instruction . Norwood, NJ: Ablex Publishing.
1. Define your topic.
I. Define your topic
A. Many students have difficulty selecting a topic. You want to find a topic you find interesting and will enjoy learning more about.
B. Students often select a topic that is too broad. You may have a broad topic in mind initially and will need to narrow it.
1. To help narrow a broad topic :
a. Brainstorm.
1). Try this technique for brainstorming to narrow your focus.
a) Step 1. Write down your broad topic.
b) Step 2. Write down a "specific kind" or "specific aspect" of the topic you identified in step 1.
c) Step 3. Write down an aspect --such as an attribute or behavior-- of the "specific kind" you identified in step 2.
d) Step 4. Continue to add levels of specificity as needed to get to a focus that is manageable. However, you may want to begin researching the literature before narrowing further to give yourself the opportunity to explore what others are doing and how that might impact the direction that you take for your own research.
2) Three examples of using the narrowing technique. These examples start with very, very broad topics, so the topic at step 3 or 4 in these examples would be used for a preliminary search in the literature in order to identify a more specific focus. Greater specificity than level 3 or 4 will ultimately be necessary for developing a specific research question. And we may discover in our preliminary research that we need to alter the direction that we originally were taking.
a) Example 1.
Step 1. information security
Step 2. protocols
Step 3. handshake protocol
Brainstorming has brought us to focus on the handshake protocol.
b) Example 2.
Step 1. information security
Step 2. single sign-on authentication
Step 3. analyzing
Step 4. methods
Brainstorming has brought us to focus on methods for analyzing the security of single sign-on authentication
c) Example 3. The diagram below is an example using the broad topic of "software" to show two potential ways to begin to narrow the topic.
C. Once you have completed the brainstorming process and your topic is more focused, you can do preliminary research to help you identify a specific research question .
1) Examine overview sources such as subject-specific encyclopedias and textbooks that are likely to break down your specific topic into sub-topics and to highlight core issues that could serve as possible research questions. [See section II. below on developing a strategy to learn how to find these encyclopedias]
2). Search the broad topic in a research database that includes scholarly journals and professional magazines (to find technical and scholarly articles) and scan recent article titles for ideas. [See section II. below on developing a strategy to learn how to find trade and scholarly journal articles]
D. Once you have identified a research question or questions, ask yourself what you need to know to answer the questions. For example,
1. What new knowledge do I need to gain?
2. What has already been answered by prior research of other scholars?
E. Use the answers to the questions in C. to identify what words to use to describe the topic when you are doing searches.
1. Identify key words
a. For example , if you are investigating "security audits in banking", key terms to combine in your searches would be: security, audits, banking.
2. Create a list of alternative ways of referring to a key word or phrase
a.For example , "information assurance" may be referred to in various ways such as: "information assurance," "information security," and "computer security."
b. Use these alternatives when doing searches.
3. As you are searching, pay attention to how others are writing about the topic and add new words or phrases to your searches if appropriate.
2. Develop a strategy.
II. Develop a strategy for finding the information.
A. Start by considering what types of source might contain the information you need . Do you need a dictionary for definitions? a directory for an address? the history of a concept or technique that might be in a book or specialized encyclopedia? today's tech news in an online tech magazine or newspaper? current research in a journal article? background information that might be in a specialized encyclopedia? data or statistics from a specific organization or website? Note that you will typically have online access to these source types.
B. This section provides a description of some of the common types of information needed for research.
1. For technical and business analysis , look for articles in technical and trade magazines . These articles are written by information technology professionals to help other IT professionals do their jobs better. Content might include news on new developments in hardware or software, techniques, tools, and practical advice. Technical journals are also likely to have product ads relevant to information technology workers and to have job ads. Examples iof technical magazines include Network Computing and IEEE Spectrum .
2. To read original research studies , look for articles in scholarly journals and conference proceedings . They will provide articles written by information technology professionals who are reporting original research; that is, research that has been done by the authors and is being reported for the first time. The audience for original research articles is other information technology scholars and professionals. Examples of scholarly journals include Journal of Applied Security Research , Journal of Management Information Systems , IEEE Transactions on Computers , and ACM Transactions on Information and System Security .
3. For original research being reported to funding agencies , look for technical reports on agency websites. Technical reports are researcher reports to funding agencies about progress on or completion of research funded by the agency.
4. For in-depth, comprehensive information on a topic , look for book-length volumes . All chapters in the book might be written by the same author(s) or might be a collection of separate papers written by different authors.
5. To learn about an unfamiliar topic , use textbooks , specialized encyclopedias and handbooks to get get overviews of topics, history/background, and key issues explained.
6. For instructions for hardware, software, networking, etc., look for manuals that provide step-by-step instructions.
7. For technical details about inventions (devices, instruments, machines), look for patent documents .
C. NOTE - In order to search for and find original research studies, it will help if you understand how information is produced, packaged and communicated within your profession. This is explained in the tab "Research Communication: Graphic."
3. Locate the information.
III. Locate the information
A. Use search tools designed to find the sources you want. Types of sources were described in section II. above.
Always feel free to Ask a librarian for assistance when you have questions about where and how locate the information you need.
B. Evaluate the search results (no matter where you find the information)
1. Evaluate the items you find using at least these 5 criteria:
a. accuracy -- is the information reliable and error free?
1) Is there an editor or someone who verifies/checks the information?
2) Is there adequate documentation: bibliography, footnotes, credits?
3) Are the conclusions justified by the information presented?
b. authority -- is the source of the information reputable?
1) How did you find the source of information: an index to edited/peer-reviewed material, in a bibliography from a published article, etc.?
2) What type of source is it: sensationalistic, popular, scholarly?
c. objectivity -- does the information show bias?
1) What is the purpose of the information: to inform, persuade, explain, sway opinion, advertise?
2) Does the source show political or cultural biases?
d. currency -- is the information current? does it cover the time period you need?
e. coverage -- does it provide the evidence or information you need?
2. Is the search producing the material you need? -- the right content? the right quality? right time period? right geographical location? etc. If not, are you using
a. the right sources?
b. the right tools to get to the sources?
c. are you using the right words to describe the topic?
3. Have you discovered additional terms that should be searched? If so, search those terms.
4. Have you discovered additional questions you need to answer? If so, return to section A above to begin to answer new questions.

4. Use and evaluate the information.
IV. Use the information.
A. Read, hear or view the source
1. Evaluate: Does the material answer your question(s)? -- right content? If not, return to B.
2. Evaluate: Is the material appropriate? -- right quality? If not, return to B.
B. Extract the information from the source : copy/download information, take notes, record citation, keep track of items using a citation manager.
1. Note taking (these steps will help you when you begin to write your thesis and/or document your project.):
a. Write the keywords you use in your searches to avoid duplicating previous searches if you return to search a research database again. Keeping track of keywords used will also save you time if your search is interrupted or you need return and do the search again for some other reason. It will help you remember which search terms worked successfully in which databases
b. Write the citations or record the information needed to cite each article/document you plan to read and use, or make sure that any saved a copy of the article includes all the information needed to cite it. Some article pdf files may not include all of the information needed to cite, and it's a waste of your valuable time to have to go back to search and find the items again in order to be able to cite them. Using citation management software such as EndNote will help keep track of citations and help create bibliographies for your research papers.
c. Write a summary of each article you read and/or why you want to use it.
5. Synthesize.
V. Synthesize.
A. Organize and integrate information from multiple sources
B. Present the information (create report, speech, etc. that communicates)
C. Cite material using the style required by your professor or by the venue (conference, publication, etc.). For help with citation styles, see Guide to Citing Sources . A link to the citing guide is also available in the "Get Help" section on the left side of the Library home page
6. Evaluate your work.
VI. Evaluate the paper, speech, or whatever you are using to communicate your research.
A. Is it effective?
B. Does it meet the requirements?
C. Ask another student or colleague to provide constructive criticism of your paper/project.
- << Previous: Research Communication Graphic
- Next: Search techniques >>
- Last Updated: Apr 15, 2024 3:27 PM
- URL: https://library.dsu.edu/graduate-research

Systematic Review
- Library Help
- What is a Systematic Review (SR)?
Steps of a Systematic Review
- Framing a Research Question
- Developing a Search Strategy
- Searching the Literature
- Managing the Process
- Meta-analysis
- Publishing your Systematic Review
Forms and templates

Image: David Parmenter's Shop
- PICO Template
- Inclusion/Exclusion Criteria
- Database Search Log
- Review Matrix
- Cochrane Tool for Assessing Risk of Bias in Included Studies
• PRISMA Flow Diagram - Record the numbers of retrieved references and included/excluded studies. You can use the Create Flow Diagram tool to automate the process.
• PRISMA Checklist - Checklist of items to include when reporting a systematic review or meta-analysis
PRISMA 2020 and PRISMA-S: Common Questions on Tracking Records and the Flow Diagram
- PROSPERO Template
- Manuscript Template
- Steps of SR (text)
- Steps of SR (visual)
- Steps of SR (PIECES)
Adapted from A Guide to Conducting Systematic Reviews: Steps in a Systematic Review by Cornell University Library
Source: Cochrane Consumers and Communications (infographics are free to use and licensed under Creative Commons )
Check the following visual resources titled " What Are Systematic Reviews?"
- Video with closed captions available
- Animated Storyboard
- << Previous: What is a Systematic Review (SR)?
- Next: Framing a Research Question >>
- Last Updated: Apr 19, 2024 12:47 PM
- URL: https://lib.guides.umd.edu/SR
Intelligent environments and assistive technologies for assisting visually impaired people: a systematic literature review
- Published: 03 May 2024
Cite this article

- Leandro Rossetti de Souza 1 ,
- Rosemary Francisco 2 na1 ,
- João Elison da Rosa Tavares 1 na1 &
- Jorge Luis Victória Barbosa 1 na1
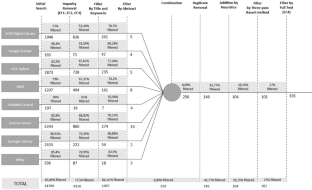
Intelligent environments (IE) refer to physical spaces imbued with pervasive and seamless intelligence, created to proactively support individuals in their daily routines. Developments in technologies such as the internet of things (IoT) and artificial intelligence (AI) have taken these environments from theoretical notions to practical realities. Simultaneously, the field of ambient assisted living (AAL) has made significant strides. Evolving from AT, AAL represents an application of IE that specifically seeks to enable individuals-especially those with disabilities or the elderly-to lead healthier, more independent, and dignified lives through the assistance of technology integrated within their living environments. The confluence of IE and AAL has led to the rise of innovative solutions aimed at enhancing the lives of individuals with special needs, such as the visually impaired people (VIP). This research presents a systematic literature review investigating the utilization of IE, underpinned by AAL principles, in supporting VIPs. Initially, a pool of 14,760 studies was obtained from 9 databases, all published up to December 2022. After applying specific inclusion and exclusion criteria, this pool was reduced to 101 articles. Each of these articles was reviewed, analyzed, and categorized into four functional and operating principle categories to address five research questions. The study proposes multiple taxonomies as an approach to holistically synthesize the various technologies and devices categorized in the reviewed articles. Emerging research challenges and trends in this domain are highlighted, with a substantial trend being the escalating use of deep learning (DL) techniques. These techniques have been pivotal in the development of systems focused on object detection, path recognition, and navigation for devices, particularly smartphones, geared towards enhancing the lives of VIPs.
This is a preview of subscription content, log in via an institution to check access.
Access this article
Price includes VAT (Russian Federation)
Instant access to the full article PDF.
Rent this article via DeepDyve
Institutional subscriptions
Cook, D.J., Augusto, J.C., Jakkula, V.R.: Ambient intelligence: technologies, applications, and opportunities. Pervasive Mob. Comput. 5 (4), 277–298 (2009)
Article Google Scholar
Dohr, A., Modre-Opsrian, R., Drobics, M., Hayn, D., Schreier, G.: The internet of things for ambient assisted living. IEEE J. Inf. Technol. Biomed. 14 (2), 277–284 (2010)
Google Scholar
A.I.T.A: Assistive Technology Industry Association. Assistive Technology Industry Association (2022). https://www.atia.org/
Cook, A.M., Polgar, J.M.: Assistive Technologies: Principles and Practice, 2nd edn. Mosby, St. Louis (2002)
Schneiderman, B.: The Science of Human–Computer Interaction: A Multidisciplinary Approach. CRC Press, Boca Raton (2012)
Report, W.H.O.: World Report on Vision. World Health Organization (2019). https://www.who.int/publications/i/item/9789241516570
Organization, W.H.: Visual impairment and blindness. Accessed 15 July 2023 (2023). http://www.who.int/news-room/fact-sheets/detail/visual-impairment-and-blindness
Organization, W.H., Fund, U.N.C.: Global Report on Assistive Technology. WHO and UNICEF (2022)
Thordardottir, B., Fänge, A.M., Lethin, C., Gatta, D.R., Chiatti, C.: Acceptance and use of innovative assistive technologies among people with cognitive impairment and their caregivers: a systematic review. Biomed. Res. Int. (2019)
Priscila, C., Cristina, S., Karina, C., Alexandra, B.: A systematic literature review on devices and systems for ambient assisted living: solutions and trends from different user perspectives. In: 2018 International Conference on eDemocracy e Government (ICEDEG), pp. 59–66 (2018). https://doi.org/10.1109/ICEDEG.2018.8372367
Kuriakose, B., Shrestha, R., Sandnes, F.E.: Tools and technologies for blind and visually impaired navigation support: a review. IETE Tech. Rev. 39 (1), 3–18 (2022). https://doi.org/10.1080/02564602.2020.1819893
Rute, B., Isabel, M.A., Joao, P., Goncalves, S.A., Pacheco, R.N.: Methodological quality of user-centered usability evaluation of ambient assisted living solutions: a systematic literature review. Int. J. Environ. Res. Public Health (2021). https://doi.org/10.3390/ijerph182111507
Ashraf, M.M., Hasan, N., Lewis, L., Hasan, M.R., Ray, P.: A systematic literature review of the application of information communication technology for visually impaired people. Int. J. Disabil. Manag. 11 , 1–18 (2017)
Jovanovic, M., Mitrov, G., Zdravevski, E., Lameski, P., Colantonio, S., Kampel, M., Tellioglu, H., Florez-Revuelta, F.: Ambient assisted living: scoping review of artificial intelligence models, domains, technology, and concerns. J. Med. Internet Res. 24 (11), 36553 (2022). https://doi.org/10.2196/36553
Kitchenham, B.A., Charters, S.: Guidelines for performing systematic literature reviews in software engineering. Tech. Rep. EBSE 2007-001. Keele University and Durham University Joint Report (2007)
Kitchenham, B., Pretorius, R., Budgen, D., Brereton, O.P., Turner, M., Niazi, M., Linkman, S.: Systematic literature reviews in software engineering—a tertiary study. Inf. Softw. Technol. 52 (8), 792–805 (2010)
Petticrew, M., Roberts, H.: Systematic Reviews in the Social Sciences: A Practical Guide, p. 352. Blackwell, Oxford (2006)
Book Google Scholar
Sadia, Z., Muhammad, A., Bin, A.M., Tauqeer, F., Munir, A., Adnan, K.M.: Assistive devices analysis for visually impaired persons: a review on taxonomy. IEEE Access 10 , 13354–13366 (2022). https://doi.org/10.1109/ACCESS.2022.3146728
Tzovaras, D., Nikolakis, G., Fergadis, G., Malassiotis, S., Stavrakis, M.: Virtual environments for the training of the visually impaired. In: Universal Access and Assistive Technology, pp. 151–160. Springer, London (2002)
Shinohara, K.: Designing assistive technology for blind users. In: Proceedings of the 8th International ACM SIGACCESS Conference on Computers and Accessibility, pp. 293–294 (2006)
Coroama, V.: Experiences from the design of a ubiquitous computing system for the blind. In: CHI’06 Extended Abstracts on Human Factors in Computing Systems, pp. 664–669 (2006)
White, G.R., Fitzpatrick, G., McAllister, G.: Toward accessible 3d virtual environments for the blind and visually impaired. In: Proceedings of the 3rd International Conference on Digital Interactive Media in Entertainment and Arts, pp. 134–141 (2008)
Narasimhan, P., Gandhi, R., Rossi, D.: Smartphone-based assistive technologies for the blind. In: Proceedings of the 2009 International Conference on Compilers, Architecture, and Synthesis for Embedded Systems, pp. 223–232 (2009)
José, J., Farrajota, M., Rodrigues, J.M.F., Buf, J.M.H.: The smartvision local navigation aid for blind and visually impaired persons. Int. J. Digit. Content Technol. Appl. 5 (5), 362–375 (2011)
Bălan, O., Moldoveanu, A., Moldoveanu, F., Morar, A., Asavei, V.: Assistive it for visually imapired people. J. Inf. Syst. Oper. Manag. 7 (2), 391–404 (2013)
Augusto, J.C., Callaghan, V., Cook, D., Kameas, A., Satoh, I.: Intelligent environments: a manifesto. HCIS 3 (1), 1–18 (2013)
Dunai, L.D., Lengua, I.L., Tortajada, I., Simon, F.B.: Obstacle detectors for visually impaired people. In: 2014 International Conference on Optimization of Electrical and Electronic Equipment (OPTIM), pp. 809–816. IEEE (2014)
Kinoe, Y., Noguchi, A.: Qualitative study for the design of assistive technologies for improving quality of life of visually impaired. In: International Conference on Human Interface and the Management of Information, pp. 602–613. Springer (2014)
Mahmud, N., Saha, R., Zafar, R., Bhuian, M., Sarwar, S.: Vibration and voice operated navigation system for visually impaired person. In: 2014 International Conference on Informatics, Electronics & Vision (ICIEV), pp. 1–5. IEEE (2014)
Csapó, Á., Wersényi, G., Nagy, H., Stockman, T.: A survey of assistive technologies and applications for blind users on mobile platforms: a review and foundation for research. J. Multimodal User Interfaces 9 (4), 275–286 (2015)
Paredes, H., Fernandes, H., Sousa, A., Fernandes, L., Koch, F., Fortes, R., Filipe, V., Barroso, J.: Exploring smart environments through human computation for enhancing blind navigation. In: International Workshop on Multiagent Foundations of Social Computing, pp. 66–76. Springer (2015)
Owayjan, M., Hayek, A., Nassrallah, H., Eldor, M.: Smart assistive navigation system for blind and visually impaired individuals. In: 2015 International Conference on Advances in Biomedical Engineering (ICABME), pp. 162–165. IEEE (2015)
Sato, S., Yamashita, A., Matsubayashi, K.: A positioning system with rfid tags and qzss for navigating the visually impaired. In: 2016 Fifth ICT International Student Project Conference (ICT-ISPC), pp. 129–132. IEEE (2016)
Poggi, M., Mattoccia, S.: A wearable mobility aid for the visually impaired based on embedded 3d vision and deep learning. In: 2016 IEEE Symposium on Computers and Communication (ISCC), pp. 208–213. IEEE (2016)
Sivan, S., Darsan, G.: Computer vision based assistive technology for blind and visually impaired people. In: Proceedings of the 7th International Conference on Computing Communication and Networking Technologies, pp. 1–8 (2016)
Sharma, A.: Computer vision guided navigation system for visually impaired. PhD thesis, National Institute of Technology (2016)
Aggravi, M., Salvietti, G., Prattichizzo, D.: Haptic assistive bracelets for blind skier guidance. In: Proceedings of the 7th Augmented Human International Conference 2016, pp. 1–4 (2016)
Filgueiras, T.S., Lima, A.C.O., Baima, R.L., Oka, G.T.R., Cordovil, L.A.Q., Bastos, M.P.: Vibrotactile sensory substitution on personal navigation: Remotely controlled vibrotactile feedback wearable system to aid visually impaired. In: 2016 IEEE International Symposium on Medical Measurements and Applications (MeMeA), pp. 1–5. IEEE (2016)
Liu, K.-C., Wu, C.-H., Tseng, S.-Y., Tsai, Y.-T.: Voice helper: a mobile assistive system for visually impaired persons. In: 2015 IEEE International Conference on Computer and Information Technology; Ubiquitous Computing and Communications; Dependable, Autonomic and Secure Computing; Pervasive Intelligence and Computing, pp. 1400–1405. IEEE (2015)
Tao, Y., Ding, L., Ganz, A.: Indoor navigation validation framework for visually impaired users. IEEE Access 5 , 21763–21773 (2017)
Kallara, S.B., Raj, M., Raju, R., Mathew, N.J., Padmaprabha, V., Divya, D.: Indriya—a smart guidance system for the visually impaired. In: 2017 International Conference on Inventive Computing and Informatics (ICICI), pp. 26–29. IEEE (2017)
Saleh, K., Zeineldin, R.A., Hossny, M., Nahavandi, S., El-Fishawy, N.A.: Navigational path detection for the visually impaired using fully convolutional networks. In: 2017 IEEE International Conference on Systems, Man, and Cybernetics (SMC), pp. 1399–1404. IEEE (2017)
Götzelmann, T., Kreimeier, J.: Optimization of navigation considerations of people with visual impairments through ambient intelligence: a case study. In: Proceedings of the 13th ACM International Conference on PErvasive Technologies Related to Assistive Environments, pp. 1–6 (2020)
Hudec, M., Smutny, Z.: Rudo: a home ambient intelligence system for blind people. Sensors 17 (8), 1926 (2017)
Khder, M.A., AlZaqebah, M.A., Abazeed, A., Saifi, M.A.: Smart shoes for visually impaired/blind people. ICSF 2017 Kingdom of Bahrain, p. 479 (2017)
Billah, S.M., Ashok, V., Porter, D.E., Ramakrishnan, I.: Ubiquitous accessibility for people with visual impairments: are we there yet? In: Proceedings of the 2017 Chi Conference on Human Factors in Computing Systems, pp. 5862–5868 (2017)
Bine, L.M.S., Costa, Y.M., Aylon, L.B.R.: Automata classification with convolutional neural networks for use in assistive technologies for the visually impaired. In: Proceedings of the 11th PErvasive Technologies Related to Assistive Environments Conference, pp. 157–164 (2018)
Mahida, P.T., Shahrestani, S., Cheung, H.: Comparision of pathfinding algorithms for visually impaired people in iot based smart buildings. In: 2018 28th International Telecommunication Networks and Applications Conference (ITNAC), pp. 1–3. IEEE (2018)
Hashimoto, Y., Takagi, N.: Development of audio-tactile graphic system aimed at facilitating access to visual information for blind people. In: 2018 IEEE International Conference on Systems, Man, and Cybernetics (SMC), pp. 2283–2288. IEEE (2018)
Díaz, J.E., Márquez, J.L., Sánchez, M., Sánchez-Aguilera, J.M., Sánchez, M.A., Bajo, J.: Diami: Distributed intelligent environment for blind musicians. In: International Work-Conference on Artificial Neural Networks, pp. 475–482. Springer (2009)
Dutta, S., Barik, M.S., Chowdhury, C., Gupta, D.: Divya-dristi: a smartphone based campus navigation system for the visually impaired. In: 2018 Fifth International Conference on Emerging Applications of Information Technology (EAIT), pp. 1–3. IEEE (2018)
Shih, M.-L., Chen, Y.-C., Tung, C.-Y., Sun, C., Cheng, C.-J., Chan, L., Varadarajan, S., Sun, M.: Dlwv2: a deep learning-based wearable vision-system with vibrotactile-feedback for visually impaired people to reach objects. In: 2018 IEEE/RSJ International Conference on Intelligent Robots and Systems (IROS), pp. 1–9. IEEE (2018)
Aljahdali, M., Abokhamees, R., Bensenouci, A., Brahimi, T., Bensenouci, M.-A.: Iot based assistive walker device for frail & visually impaired people. In: 2018 15th Learning and Technology Conference (L &T), pp. 171–177. IEEE (2018)
Martillano, D.A., Chowdhury, A.F.D., Dellosa, J.C.M., Murcia, A.A., Mangoma, R.J.P.: Pindots: an assistive six-dot braille cell keying device on basic notation writing for visually impaired students with iot technology. In: Proceedings of the 2018 2nd International Conference on Education and E-Learning, pp. 41–47 (2018)
Suda, S., Ohnishi, K., Iwazaki, Y., Asami, T.: Robustness of machine learning pedestrian signal detection applied to pedestrian guidance device for persons with visual impairment. In: 2018 12th France-Japan and 10th Europe-Asia Congress on Mechatronics, pp. 116–121. IEEE (2018)
Sowmiya, S., Valarmathi, K., Sathyavenkateshwaren, S., Gobinath, M., Thillaisivakavi, S.: Snag detection robot for visually impaired steering and blind individuals. In: 2018 International Conference on Inventive Research in Computing Applications (ICIRCA), pp. 167–171. IEEE (2018)
Reda, M.M., Mohammed, N.G., Seoud, R.A.A.A.A.: Svbicomm: sign-voice bidirectional communication system for normal,“deaf/dumb” and blind people based on machine learning. In: 2018 1st International Conference on Computer Applications & Information Security (ICCAIS), pp. 1–8. IEEE (2018)
Wahidin, H., Waycott, J., Baker, S.: The challenges in adopting assistive technologies in the workplace for people with visual impairments. In: Proceedings of the 30th Australian Conference on Computer–Human Interaction, pp. 432–442 (2018)
Ahmed, T., Kapadia, A., Potluri, V., Swaminathan, M.: Up to a limit? Privacy concerns of bystanders and their willingness to share additional information with visually impaired users of assistive technologies. In: Proceedings of the ACM on Interactive, Mobile, Wearable and Ubiquitous Technologies, vol. 2(3), pp. 1–27 (2018)
Chang, W.-J., Yu, Y.-X., Chen, J.-H., Zhang, Z.-Y., Ko, S.-J., Yang, T.-H., Hsu, C.-H., Chen, L.-B., Chen, M.-C.: A deep learning based wearable medicines recognition system for visually impaired people. In: 2019 IEEE International Conference on Artificial Intelligence Circuits and Systems (AICAS), pp. 207–208. IEEE (2019)
Vasanth, K., Macharla, M., Varatharajan, R.: A self assistive device for deaf & blind people using iot. J. Med. Syst. 43 (4), 1–8 (2019)
Lin, W.-J., Su, M.-C., Cheng, W.-Y., Cheng, W.-Y.: An assist system for visually impaired at indoor residential environment using faster-rcnn. In: 2019 8th International Congress on Advanced Applied Informatics (IIAI-AAI), pp. 1071–1072. IEEE (2019)
Croce, D., Giarre, L., Pascucci, F., Tinnirello, I., Galioto, G.E., Garlisi, D., Valvo, A.L.: An indoor and outdoor navigation system for visually impaired people. IEEE Access 7 , 170406–170418 (2019)
Noman, M., Shehieb, W., Sharif, T.: Assistive technology for integrating the visually-impaired in mainstream education and society. In: 2019 Advances in Science and Engineering Technology International Conferences (ASET), pp. 1–5. IEEE (2019)
Nasralla, M.M., Rehman, I.U., Sobnath, D., Paiva, S.: Computer vision and deep learning-enabled uavs: proposed use cases for visually impaired people in a smart city. In: International Conference on Computer Analysis of Images and Patterns, pp. 91–99. Springer (2019)
Shekhar, S., Chhokra, A., Sun, H., Gokhale, A., Dubey, A., Koutsokos, X.: Supporting fog/edge-based cognitive assistance iot services for the visually impaired. In: Proceedings of the International Conference on Internet of Things Design and Implementation, pp. 275–276 (2019)
Mascetti, S., Ahmetovic, D., Bernareggi, C.: Research to market transition of mobile assistive technologies for people with visual impairments. In: The 21st International ACM SIGACCESS Conference on Computers and Accessibility, pp. 440–445 (2019)
Grewe, L., Stevenson, G.: Seeing eye drone: a deep learning, vision-based uav for assisting the visually impaired with mobility. In: Proceedings of the ACM Turing Celebration Conference-China, pp. 1–5 (2019)
Alghamdi, S.: Shopping and tourism for blind people using rfid as an application of iot. In: 2019 2nd International Conference on Computer Applications & Information Security (ICCAIS), pp. 1–4. IEEE (2019)
Salat, S., Habib, M.A.: Smart electronic cane for the assistance of visually impaired people. In: 2019 IEEE International WIE Conference on Electrical and Computer Engineering (WIECON-ECE), pp. 1–4. IEEE (2019)
Rai, A., Maurya, A., Ranjan, A., Gupta, R., et al.: Smart traveler-for visually impaired people. In: International Conference on Information Management & Machine Intelligence, pp. 653–662. Springer (2019)
Kose, U., Vasant, P.: Better campus life for visually impaired university students: intelligent social walking system with beacon and assistive technologies. Wirel. Netw. 26 (7), 4789–4803 (2020)
Son, H., Krishnagiri, D., Jeganathan, V.S., Weiland, J.: Crosswalk guidance system for the blind. In: 2020 42nd Annual International Conference of the IEEE Engineering in Medicine & Biology Society (EMBC), pp. 3327–3330. IEEE (2020)
Mahida, P., Shahrestani, S., Cheung, H.: Deep learning-based positioning of visually impaired people in indoor environments. Sensors 20 (21), 6238 (2020)
Sarkar, T., Patel, A., Arjunan, S.P.: Design and development of a smart eye wearable for the visually impaired. In: International Conference on Information, Communication and Computing Technology, pp. 208–221. Springer (2020)
Shafique, K., Khawaja, B.A., Sabir, F., Qazi, S., Mustaqim, M.: Internet of things (iot) for next-generation smart systems: a review of current challenges, future trends and prospects for emerging 5g-iot scenarios. IEEE Access 8 , 23022–23040 (2020)
Chang, W.-J., Chen, L.-B., Hsu, C.-H., Chen, J.-H., Yang, T.-C., Lin, C.-P.: Medglasses: a wearable smart-glasses-based drug pill recognition system using deep learning for visually impaired chronic patients. IEEE Access 8 , 17013–17024 (2020)
Khan, M., Khan, D., Bazai, S., Ahmed, S., Khan, H., Ejaz, N.: ullah n (2020) motion based smart assistant for visually impaired people. Indian J. Sci. Technol. 13 (16), 1612–1618 (2020)
Khairnar, D.P., Karad, R.B., Kapse, A., Kale, G., Jadhav, P.: Partha: a visually impaired assistance system. In: 2020 3rd International Conference on Communication System, Computing and IT Applications (CSCITA), pp. 32–37. IEEE (2020)
Connier, J., Zhou, H., De Vaulx, C., Li, J.-J., Shi, H., Vaslin, P., Hou, K.M.: Perception assistance for the visually impaired through smart objects: concept, implementation, and experiment scenario. IEEE Access 8 , 46931–46945 (2020)
Akter, T., Ahmed, T., Kapadia, A., Swaminathan, S.M.: Privacy considerations of the visually impaired with camera based assistive technologies: misrepresentation, impropriety, and fairness. In: The 22nd International ACM SIGACCESS Conference on Computers and Accessibility, pp. 1–14 (2020)
Terreran, M., Tramontano, A.G., Lock, J.C., Ghidoni, S., Bellotto, N.: Real-time object detection using deep learning for helping people with visual impairments. In: 2020 IEEE 4th International Conference on Image Processing, Applications and Systems (IPAS), pp. 89–95. IEEE (2020)
Lin, J.-Y., Chiang, C.-L., Wu, M.-J., Yao, C.-C., Chen, M.-C.: Smart glasses application system for visually impaired people based on deep learning. In: 2020 Indo-Taiwan 2nd International Conference on Computing, Analytics and Networks (Indo-Taiwan ICAN), pp. 202–206. IEEE (2020)
Al-Haider, A.J., Al-Sharshani, S.M., Al-Sheraim, H.S., Subramanian, N., Al-Maadeed, S., Chaari, M.: Smart medicine planner for visually impaired people. In: 2020 IEEE International Conference on Informatics, IoT, and Enabling Technologies (ICIoT), pp. 361–366. IEEE (2020)
Gamal, O., Thakkar, S., Roth, H.: Towards intelligent assistive system for visually impaired people: outdoor navigation system. In: 2020 24th International Conference on System Theory, Control and Computing (ICSTCC), pp. 390–397. IEEE (2020)
Poornima, J., Vishnupriyan, J., Vijayadhasan, G.K., Ettappan, M.: Voice assisted smart vision stick for visually impaired. Int. J. Control Autom. 13 (2), 512–519 (2020)
Rao, S.U., Ranganath, S., Ashwin, T., Reddy, G.R.M., et al.: A google glass based real-time scene analysis for the visually impaired. IEEE Access 9 , 166351–166369 (2021)
Wang, Z., Li, H., Chen, J., Chai, X., Zhai, Z.: A wearable vision-to-audio sensory substitution system based on deep learning for the visually impaired. In: 2021 International Conference on Digital Society and Intelligent Systems (DSInS), pp. 283–286. IEEE (2021)
Khan, A., Khusro, S.: An insight into smartphone-based assistive solutions for visually impaired and blind people: issues, challenges and opportunities. Univ. Access Inf. Soc. 20 (2), 265–298 (2021)
Rodrigo-Salazar, L., González-Carrasco, I., Garcia-Ramirez, A.R.: An iot-based contribution to improve mobility of the visually impaired in smart cities. Computing 103 (6), 1233–1254 (2021)
Parikh, N., Shah, I., Vahora, S.: Android smartphone based visual object recognition for visually impaired using deep learning. In: 2018 International Conference on Communication and Signal Processing (ICCSP), pp. 0420–0425. IEEE (2018)
Beingolea, J.R., Zea-Vargas, M.A., Huallpa, R., Vilca, X., Bolivar, R., Rendulich, J.: Assistive devices: technology development for the visually impaired. Designs 5 (4), 75 (2021)
Mejía, P., Martini, L.C., Grijalva, F., Zambrano, A.M.: Casvi: computer algebra system aimed at visually impaired people. experiments. IEEE Access 9 , 157021–157034 (2021)
Rao, S., Singh, V.M.: Computer vision and iot based smart system for visually impaired people. In: 2021 11th International Conference on Cloud Computing, Data Science & Engineering (Confluence), pp. 552–556. IEEE (2021)
Mohamed, E., Sirlantzis, K., Howells, G.: Indoor/outdoor semantic segmentation using deep learning for visually impaired wheelchair users. IEEE Access 9 , 147914–147932 (2021)
Kanna, S.B., Kumar, T.G., Niranjan, C., Prashanth, S., Gini, J.R., Harikumar, M.: Low cost smart navigation system for the blind. In: 2021 7th International Conference on Advanced Computing and Communication Systems (ICACCS), vol. 1, pp. 466–471. IEEE (2021)
Abdel-Jaber, H., Albazar, H., Abdel-Wahab, A., El Amir, M., Alqahtani, A., Alobaid, M.: Mobile based iot solution for helping visual impairment users. Adv. Internet Things 11 (4), 141–152 (2021)
Denić, D., Aleksov, P., Vučković, I.: Object recognition with machine learning for people with visual impairment. In: 2021 15th International Conference on Advanced Technologies, Systems and Services in Telecommunications (TELSIKS), pp. 389–392. IEEE (2021)
Kumar, P., Inchara, K., Lekhashree, S., Likhith, C., Pavan, U.: Real time assistive shoe for visually impaired people. In: 2021 6th International Conference for Convergence in Technology (I2CT), pp. 1–5. IEEE (2021)
Mukhiddinov, M., Cho, J.: Smart glass system using deep learning for the blind and visually impaired. Electronics 10 (22), 2756 (2021)
Rahman, M.W., Tashfia, S.S., Islam, R., Hasan, M.M., Sultan, S.I., Mia, S., Rahman, M.M.: The architectural design of smart blind assistant using iot with deep learning paradigm. Internet Things 13 , 100344 (2021)
Kuriakose, B., Shrestha, R., Eika Sandnes, F.: Towards independent navigation with visual impairment: a prototype of a deep learning and smartphone-based assistant. In: The 14th PErvasive Technologies Related to Assistive Environments Conference, pp. 113–114 (2021)
Oliveira, J.D.: Using interactive agents to provide daily living assistance for visually impaired people. Master’s thesis, Pontifícia Universidade Católica do Rio Grande do Sul (2021)
Saha, S., Shakal, F.H., Mahmood, M.: Visual, navigation and communication aid for visually impaired person. Int. J. Electr. Comput. Eng. 11 (2), 1276 (2021)
Pachodiwale, Z.A., Brahmankar, Y., Parakh, N., Patel, D., Eirinaki, M.: Viva: a virtual assistant for the visually impaired. In: International Conference on Human–Computer Interaction, pp. 444–460. Springer (2021)
Hudec, M., Smutny, Z.: Ambient intelligence system enabling people with blindness to develop electrotechnical components and their drivers. IEEE Access 10 , 8539–8565 (2022)
Ashiq, F., Asif, M., Ahmad, M.B., Zafar, S., Masood, K., Mahmood, T., Mahmood, M.T., Lee, I.H.: Cnn-based object recognition and tracking system to assist visually impaired people. IEEE Access 10 , 14819–14834 (2022)
Mallikarjuna, G.C., Hajare, R., Pavan, P.: Cognitive iot system for visually impaired: machine learning approach. Mater. Today Proc. 49 , 529–535 (2022)
Durgadevi, S., Komathi, C., Thirupurusundari, K., Haresh, S., Harishanker, A.: Iot based assistive system for visually impaired and aged people. In: 2022 2nd International Conference on Power Electronics & IoT Applications in Renewable Energy and Its Control (PARC), pp. 1–4. IEEE (2022)
Wang, X., Calderon, J., Khoshavi, N., Jaimes, L.G.: Path and floor detection in outdoor environments for fall prevention of the visually impaired population. In: 2022 IEEE 19th Annual Consumer Communications & Networking Conference (CCNC), pp. 1–6. IEEE (2022)
Masud, U., Saeed, T., Malaikah, H.M., Islam, F.U., Abbas, G.: Smart assistive system for visually impaired people obstruction avoidance through object detection and classification. IEEE Access 10 , 13428–13441 (2022)
Yang, Z., Yang, L., Kong, L., Wei, A., Leaman, J., Brooks, J., Li, B.: Seeway: vision-language assistive navigation for the visually impaired. In: 2022 IEEE International Conference on Systems, Man, and Cybernetics, pp. 52–58 (2022). https://doi.org/10.1109/SMC53654.2022.9945087
Ntakolia, C., Dimas, G., Iakovidis, D.: User-centered system design for assisted navigation of visually impaired individuals in outdoor cultural environments. Univers. Access Inf. Soc. 21 , 1–26 (2022). https://doi.org/10.1007/s10209-020-00764-1
López, A.F., Ohmura, R.: Public transport guiding system for visually impaired users easy to deploy, maintain and extend. In: 2022 IEEE International Smart Cities Conference (ISC2), pp. 1–7 (2022). https://doi.org/10.1109/ISC255366.2022.9922280
Roy, T., Boppana, L.: Interactive web-based image and graph analysis using sonification for the blind. In: 2022 IEEE Region 10 Symposium (TENSYMP), pp. 1–6 (2022). https://doi.org/10.1109/TENSYMP54529.2022.9864411
Fathi, K., Darvishy, A., Venn, H.W.: Augmented reality for the visually impaired: navigation aid and scene semantics for indoor use cases. In: 2022 IEEE 12th International Conference on Consumer Electronics (ICCE-Berlin), pp. 1–6 (2022). https://doi.org/10.1109/ICCE-Berlin56473.2022.9937109
Huang, C.-Y., Wu, C.-K., Liu, P.-Y.: Assistive technology in smart cities: a case of street crossing for the visually-impaired. Technol. Soc. 68 , 101805 (2022). https://doi.org/10.1016/j.techsoc.2021.101805
Feitl, S., Kreimeier, J., Götzelmann, T.: Accessible electrostatic surface haptics: towards an interactive audiotactile map interface for people with visual impairments. In: ND, pp. 522–531. Association for Computing Machinery, New York, NY, USA (2022). https://doi.org/10.1145/3529190.3534781
Rana, L., Rehman, A.U., Javaid, S., Ali, T.M.: A novel model-driven approach for visual impaired people assistance optic ally. In: 2022 Third International Conference on Latest Trends in Electrical Engineering and Computing Technologies (INTELLECT), pp. 1–8 (2022). https://doi.org/10.1109/INTELLECT55495.2022.9969400
Ahmed, E., Yaqoob, I., Gani, A., Imran, M.: Guizani: internet-of-things-based smart environments: state of the art, taxonomy, and open research challenges. IEEE Wirel. Commun. 23 (5), 10–16 (2016)
Download references
The authors did not receive support from any organization for the submitted work.
Author information
Rosemary Francisco, João Elison da Rosa Tavares and Jorge Luis Victória Barbosa have contributed equally to this work.
Authors and Affiliations
Applied Computing Graduate Program (PPGCA), University of Vale do Rio dos Sinos (UNISINOS), Unisinos Avenue, 950, São Leopoldo, RS, 93022-750, Brazil
Leandro Rossetti de Souza, João Elison da Rosa Tavares & Jorge Luis Victória Barbosa
Unisinos Business School, University of Vale do Rio dos Sinos (UNISINOS), Unisinos Avenue, 950, São Leopoldo, RS, 93022-750, Brazil
Rosemary Francisco
You can also search for this author in PubMed Google Scholar
Contributions
R. F. This author contributed equally to this work. J. E. R. T.: This author contributed equally to this work. J. L. V. B.: This author contributed equally to this work.
Corresponding author
Correspondence to Leandro Rossetti de Souza .
Ethics declarations
Conflict of interest.
The authors have no Conflict of interest to declare that are relevant to the content of this article.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
Reprints and permissions
About this article
Souza, L.R.d., Francisco, R., Rosa Tavares, J.E.d. et al. Intelligent environments and assistive technologies for assisting visually impaired people: a systematic literature review. Univ Access Inf Soc (2024). https://doi.org/10.1007/s10209-024-01117-y
Download citation
Accepted : 12 April 2024
Published : 03 May 2024
DOI : https://doi.org/10.1007/s10209-024-01117-y
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Intelligent environments (IE)
- Ambient-assisted living (AAL)
- Internet of things (IoT)
- Visually impaired people (VIP)
Advertisement
- Find a journal
- Publish with us
- Track your research
Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
- My Account Login
- Explore content
- About the journal
- Publish with us
- Sign up for alerts
- Open access
- Published: 03 May 2024
Unlocking the potential of blockchain technology in enhancing the fisheries supply chain: an exploration of critical adoption barriers in China
- Ubair Nisar 1 ,
- Zhixin Zhang 1 ,
- Bronwyn P. Wood 2 ,
- Shadab Ahmad 3 ,
- Ehsan Ellahi 1 ,
- Syed Ijaz Ul Haq 4 ,
- Mohamad Alnafissa 5 &
- Elsayed Fathi Abd-Allah 6
Scientific Reports volume 14 , Article number: 10167 ( 2024 ) Cite this article
Metrics details
- Mathematics and computing
- Ocean sciences
The application of blockchain technology holds significant potential for improving efficiency, resilience, and transparency within the Fisheries Supply Chain (FSC). This study addresses the critical barriers hindering the adoption of blockchain technology (BT) in the Chinese FSC, recognizing the unique challenges posed by its intricacies. Through a comprehensive literature review, fourteen Critical Barrier Factors (CBFs) were identified, and a grey Delphi method was employed to distill this set. Five pivotal CBFs emerged, including "Regulatory Compliance," "Cost of Implementation," and "Complex Supply Chain Network". A subsequent grey Decision-Making Trial and Evaluation Laboratory (DEMATEL) analysis revealed the causal relationships among these factors, categorizing them into effect and cause groups. "Regulatory Compliance," "Cost of Implementation," and "Complex Supply Chain Network" were identified as primary influencing factors demanding attention for effective BT integration in the FSC. The findings serve as a valuable resource for FSC stakeholders, assisting in prioritizing efforts to address these barriers. The discerned causal relationships provide guidance for managers in optimizing resource allocation. Ultimately, this research advocates for the adoption of blockchain technology in the fisheries supply chain to enhance overall performance and operational efficiency.
Introduction
The Chinese fisheries supply chain plays a pivotal role in both fulfilling China's domestic seafood consumption needs and facilitating its active participation in the global seafood trade. As one of the world's foremost producers and consumers of seafood, China's fisheries supply chain operates as a multifaceted and ever-evolving network. It involves a diverse array of stakeholders, ranging from fishermen and aquaculture farmers to processors, distributors, and exporters. China's fisheries sector encompasses a vast spectrum of aquatic products, encompassing a diverse range of fish species, shellfish, and aquatic plants. The current major crisis China is facing is ever-increasing seafood demand, water scarcity, and cultivable land resources. In order to overcome these problems, the best solution is intensive sustainable aquaculture and efficient supply chain management 1 . This comprehensive portfolio solidifies China's position as a key player in the worldwide seafood industry. The significance of this supply chain extends not solely to meeting the demands of China's vast population but also to its substantial exports of seafood products to international markets. China as a nation reduces the impact of future uncertainties by improving its supply chain management and logistics networking 2 .
Blockchain technology has garnered significant attention in recent years, drawing interest from both researchers and professionals across various industries 3 . Blockchain, as a decentralized peer-to-peer platform, presents a particularly promising prospect for implementation within complex food supply chains. The blockchain technology model named Deep Improving Commute Experience (DeepICE) demonstrate the superior performance of proposed model compared to existing approaches 4 . Unlike many other industries, the food production sector operates within intricate value chains that necessitate heightened attention to handling and storage. The utilization of blockchain technology has the potential to greatly enhance the trustworthiness, effectiveness, and protection of data shared among participants in supply chain networks 5 . Factors such as transportation and temperature can significantly impact the quality and freshness of food products 6 . The primary factor that positions Blockchain as the pivotal tool of our times lies in its distinctive attributes. These include the instantaneous exchange of information, robust cybersecurity, transparency, dependability, traceability, and enhanced visibility, all of which contribute to the optimization of supply chain operations 7 . In the fisheries industry, blockchain technology can be leveraged to record data from specialized IoT devices, such as intelligent sensors. These sensors capture vital information from the moment of product capture all the way through to the final delivery to the end customer. The data they provide, particularly regarding factors like temperature, is crucial for monitoring the condition of transported products. Beyond the utilization of blockchain technology, there is a requisite for additional adaptable sensors. These sensors not only facilitate precise and accurate detection of crucial changes in environmental parameters but also offer promising resolutions for various challenges, including enhanced precision in agri-food processing, grading, and inspection 8 . Blockchain technology can play a vital role in ensuring the integrity of transportation, handling, and storage processes, including tamper-proof checks and maintaining a comprehensive product history, among other applications 9 . Leveraging effective blockchain adoption (BCA) alongside enhanced knowledge management (KM) within organizational and production processes has emerged as a potent combination for elevating sustainable organizational performance (SOP) 10 .
In today's rapidly changing global landscape, supply chains (SCs) encounter numerous challenges. One major issue is the difficulty in accurately forecasting demand due to historical demand data being unreliable 11 , 12 . Additionally, inadequate communication among various players within the supply chain leads to limited visibility and an increased risk of unexpected problems arising 13 . The modern supply chain is often lengthy and intricate, which can result in the bullwhip effect caused by poor communication between different entities. This negatively impacts overall supply chain operations, emphasizing the necessity to rethink how information is utilized for more effective and efficient supply chain coordination and performance improvement 14 . The fast-paced nature of today's business environment adds further complexity to supply chain collaboration 15 , especially when considering the diversity of social and organizational cultures. End-to-end supply chains encompass multi-tier supply chains (MTSCs), involving the collection and analysis of vast amounts of data. This demands a transparent workflow for sharing information across all levels of the MTSC. Consequently, collaboration becomes a crucial component in addressing the current challenges faced by supply chains. Furthermore, this technology has the potential to alleviate various supply chain challenges, including issues related to data loss, transparency, accuracy, and dependable communication. Blockchain technology is viewed as a valuable tool for rebuilding trust among supply chain partners by providing a secure and credible platform for sharing information. As a result, blockchain technology is considered a significant emerging trend that is poised to have a substantial impact on both business and society in the years ahead 16 . Lately, sustainability has taken the forefront as the primary research focus, encompassing aspects such as compliance with environmental protection regulations, the integration of eco-friendly technologies, regulatory obligations, and the implementation of agile supply chain strategies 17 .
Following the advent of Industry 4.0, emerging economies are currently undergoing a progressive shift in technology adoption 18 . This transformation can be effectively orchestrated through the implementation of Industry 3.5 strategies, as opposed to strict adherence to the lofty objectives of Industry 4.0. Industry 3.5 represents a balanced approach that integrates elements from both Industry 4.0 and Industry 3.0, leveraging recent advancements in information and communication technologies 19 . Although there is increasing enthusiasm for Blockchain Innovation (BI), there is a scarcity of research concerning its determinants 20 . Blockchain technology is strategically positioned to pave the way for innovative business models and has the potential to spearhead such advancements 21 . Traditionally, blockchain is described as a secure ledger of historical transactions, organized into blocks, arranged chronologically, and distributed across multiple servers to establish a streamlined provenance 22 . It facilitates peer-to-peer transactions and offers significant enhancements in terms of transparency, accountability, security, efficiency, and cost reduction 23 . Additionally, blockchain technology guarantees data immutability, traceability, and the implementation of smart contracts, fostering high-trust environments without the need for intermediaries 24 . In the realm of technological research, scholars have primarily concentrated on the significance of fostering technological innovation within the supply industry for economic development 25 .
Furthermore, the blockchain-based system eliminates the need for intermediaries from both public and private institutions, resulting in a significant reduction in transaction costs. Participants in the blockchain-based system place their trust in computer code rather than relying solely on themselves, ensuring a highly secure and foolproof process 26 . Blockchain technology introduces traceability into the FSC while smart contracts facilitate seamless operations within the agri-business sector. Additionally, the blockchain-based system enhances the sustainability of supply chain operations by meticulously tracking compliance for each activity 27 , 28 . Although blockchain technology holds great promise for revolutionizing FSC, its practical adoption is still in its nascent stages 21 , 29 . Much like technology-focused nations, China is keen on harnessing the potential of blockchain to meet its growing demands and requirements. Therefore, there is a need to investigate the current barriers to blockchain adoption. Consequently, the objectives of this research can be succinctly summarized as follows:
Identify the barriers to blockchain adoption in the Chinese Fisheries Supply Chain (FSC).
Develop a model to analyze how these barriers relate to each other and establish a hierarchy.
Assess the strength of causal relationships among the identified factors and categorize them accordingly.
The primary aim of the study is to identify the barriers hindering the adoption of blockchain technology (BT) in the FSC and to discover the cause-and-effect relationships between these barriers. The Goal of the study is to provide valuable insights that can assist decision-makers at government policy and company levels in taking effective actions to address these obstacles and promote the successful implementation of BT in the sector. While some prior research has indeed identified barriers to BT adoption, the study goes a step further by establishing the causal connections between these barriers, thereby offering practical guidance to practitioners on where to concentrate their efforts when implementing blockchain. To achieve the research objectives, we conducted a comprehensive literature review to identify the most significant barriers to adopting BT in FSC. Recognizing these significant barriers is crucial for facilitating BT adoption in this context. However, the obstacles identified are substantial and cannot all be tackled simultaneously. Therefore, to ensure the successful integration of BT in supply chains, the study recognized the need to construct a causal relationship map. This map serves as a systematic approach to address these barriers in a prioritized manner. Furthermore, when organizations understand the cause-and-effect relationships among these apparent barriers, they can allocate their resources more efficiently in mitigating these challenges. One distinctive contribution of our study, particularly relevant to the context of a developing economy like China, is the identification of this causal structure of BT implementation barriers in the suppl chain of fisheries sector.
Literature review
Blockchain and supply chain.
A supply chain is a highly intricate, adaptable network that spans various stages, geographical locations, financial systems, and entities. The dynamics of a supply chain vary based on product type and market conditions 30 , 31 . Supply chain systems encompass networks of facilities and distribution entities, including suppliers, manufacturers, distributors, and retailers. These systems execute the functions of procuring raw materials, transforming them into intermediates and finished products, and distributing the final products to customers. This process is achieved through the control of both information flow and material flow 32 . These networks typically involve multiple partners, such as manufacturing facilities, distribution centers, suppliers, logistics providers, and couriers 33 , contributing to their growing complexity. Several factors have contributed to this complexity, including sustainability concerns, globalization, trade liberalization, reduced trade costs, and the integration of new technologies. Effective management of supply chain networks is critical for maintaining organizational competitiveness 30 , 34 . It is imperative to advance technological solutions aimed at addressing challenges within the cold chain concerning perishable commodities 35 .
In recent times, blockchain technology has garnered significant attention from both researchers and practitioners for its potential role within supply chains. It offers various benefits, including the use of smart contracts, product traceability, enforcement tracking, inventory management, transaction and settlement facilitation, and data immutability 36 . To attain optimal efficiency in the product flow within a supply chain, it is imperative to pioneer the development of novel technologies that can mitigate losses 37 . Existing literature has identified numerous applications of blockchain within supply chain management. An extensive literature review focusing on blockchain-based applications within the Agricultural Supply Chain (ASC) 21 . Their research findings shed light on the various uses of blockchain in ASC, encompassing traceability, sustainable water management, agri-food manufacturing, and information security. A survey was conducted to gauge the landscape of blockchain research in agriculture 38 . They observed that the adoption of blockchain in this sector is still in its early stages. The authors categorized existing blockchain-based research into four dimensions: traceability, architecture, information systems, and other miscellaneous applications. In a related context 39 , advocated the incorporation of blockchain technology for ensuring food safety, particularly when coupled with Radio-Frequency Identification (RFID) technology. Subsequently, in 2017, Tian proposed a traceability mechanism for the Agricultural Supply Chain (ASC) by harnessing the combined power of blockchain and the Internet of Things (IoT). Additionally, Yadav and Singh introduced a framework designed to address specific challenges faced by farmers in the Indian context. They proposed the use of a blockchain-based mobile application as a solution to these challenges 40 .
Existing studies in the SC perspective regarding blockchain applications are categorized into four major types: "conceptual", "descriptive", "predictive," and "prescriptive" research. For instance 41 , studied BT and identified the potential areas of BT contribution to performance from a SC perspective. Further, they also highlighted the scope for future research, from which the motivation for this study was derived, of highlighting on BT barriers and their interrelationships. Reference 42 proposed blockchain based system architecture and found that BT can decrease the complexity of the management of SC. A literature review was conducted review and pinpointed privacy and security as the central hurdles in the implementation of blockchain technology 43 . Lu conducted a review focusing on blockchain technology (BT), identifying its essential components, its role in data management, security enhancement, BT-based Internet of Things (IoT), and primary applications 44 . Furthermore, Lu discussed emerging trends and the associated challenges in the field of BT. A review of blockchain technology was carried out, emphasizing the potential benefits of immutable distributed ledgers in supply chain operations 28 . Finally, 45 explored challenges related to blockchain-enabled IoT and investigated how blockchain technology can enhance the performance of the Internet of Things.
A study was conducted on blockchain trends within the Agricultural Supply Chain (ASC) and explored the associated challenges hindering its widespread adoption. These challenges encompass factors such as the absence of government regulation, uncertainties regarding regulatory frameworks, inadequate training resources, and related issues 46 . Kamble 47 delved into the subject of blockchain-based traceability mechanisms for the food-retail Supply Chain (SC) in India. Simultaneously, undertook an analysis of the hurdles encountered when applying blockchain to food traceability 48 . One notable challenge lies in the lack of control over sensors that feed data into the blockchain system. This makes it challenging to detect fraudulent manipulations of such sensors. The adoption of blockchain in ASC is further complicated by a range of other obstacles, including the shortage of skilled professionals, regulatory gaps, limited system storage capacity, throughput and latency issues, scalability concerns, privacy considerations, and the associated high costs 21 . The concept of using blockchain for land registration in the Indian context, emphasizing the potential benefits of authenticity and tamper-proof record-keeping was explored 49 . However, they also acknowledged various implementation challenges, including the substantial initial investment required, regulatory uncertainties, and security-related concerns.
Blockchain fisheries adoption
The rapid pace of technological innovation has made the swift adoption of information communication technologies a critical objective for businesses. The fisheries industry is notably complex due to the multitude of products, processes, individuals, and organizations it encompasses 50 . For instance, Ireland's fishing sector comprises distinct segments like refrigerated seawater pelagic, beam trawler, polyvalent, specific, and aquaculture, each focusing on different types of aquatic species and products. In Ireland, aquaculture primarily revolves around salmon farming, and fish processing involves numerous companies, with many generating revenues exceeding €1 million. The industry predominantly consists of whitefish, pelagic, and shellfish operators, with whitefish, shellfish, and smoked salmon processors being particularly prominent. This intricate structure is a consequence of the globalization, distribution, and consumption patterns in the food production sector 50 , 51 . To tackle the intricacies of supply chain management in this context, various solutions have been proposed, including vigilant information systems and blockchain technology 9 .
Numerous theories have emerged over time to explain the factors driving the adoption of information technology. These theories often examine user behavior, such as the Technology Acceptance Model (TAM), Task-Technology Fit (TTF) theory, Diffusion of Innovation (DOI) theory, Theory of Reasoned Action (TRA), Theory of Planned Behavior (TPB), Unified Theory of Acceptance and Use of Technology (UTAUT), and Social Cognitive Theory (SCT) 36 . Other models include the Perceived e-Readiness Model and Assimilation Theory 52 . In 1990, the Technology-Organization-Environment (TOE) model was introduced, identifying three distinct areas within an organization's context that influence the adoption and implementation of technological innovations: the technological context, organizational context, and environmental context 53 . The technological context encompasses both internal and external technologies relevant to the firm, including factors like complexity, relative advantage, privacy, security, and compatibility, all of which have been shown to impact information technology adoption 36 , 53 . The organizational context considers the firm's scope, size, managerial structure, top management support, prior IT experience, innovativeness, information intensity, and organizational readiness 53 .
Applications
Our research contributes by systematically identifying and categorizing fourteen specific Critical Barrier Factors (CBFs) through an extensive literature review and the use of the grey Delphi method. This establishes a structured foundation for understanding the hurdles that impede the successful integration of blockchain technology in fisheries supply chains. The work will provide valuable insights into the challenges associated with the adoption of blockchain technology in emerging economies within the fisheries industry. By highlighting the multifaceted nature of these challenges, including logistical complexities, financial constraints, and regulatory intricacies, the study contributes to a nuanced understanding of the specific hurdles faced by these regions. The study also delves into the intricate challenges posed by regulatory compliance in the seafood industry. By recommending strategies such as open communication, integration of compliance features into blockchain design, and leveraging smart contracts, the article contributes practical insights for overcoming regulatory hurdles in the adoption of blockchain technology. Recognizing the unique socio-economic and regulatory environment of China, the study identifies specific barriers that can hinder the seamless integration of blockchain across the entire supply chain. This contextual understanding contributes to the development of tailored strategies for overcoming challenges in this specific market.
Methodology
This study follows a three-phase research framework to accomplish its stated research objectives as shown in Fig. 1 . Initial CBF Identification : the first phase commences with a systematic literature review aimed at identifying the preliminary Critical Barrier Factors (CBFs) associated with the Blockchain-based FSC. To achieve this, a comprehensive review of existing literature is conducted using the Scopus database. Scopus is chosen due to its recognition as one of the largest repositories of peer-reviewed articles in the fields of science and social sciences. Through this systematic review, the initial set of CBFs for blockchain adoption within the FSC is established. Expert Involvement and CBF Finalization : the second phase involves the utilization of the grey Delphi method to finalize the identified CBFs for blockchain adoption within the FSC. Expert input plays a pivotal role in this phase, facilitating the refinement and selection of the most relevant CBFs. This expert-driven approach ensures a comprehensive and informed understanding of the critical factors. Causal Relationship Development : subsequent to the finalization of the CBFs for blockchain adoption, the third phase employs the grey Decision-Making Trial and Evaluation Laboratory (DEMATEL) technique to construct causal interrelationships among these factors. Various techniques, including Interpretive Structural Modelling (ISM), Total Interpretive Structural Modelling (TISM), Analytic Network Process (ANP), and DEMATEL, have been utilized in the literature to explore causal relationships 54 . While ISM and TISM reveal structural linkages between CBFs, they do not quantify the strength of these relationship 16 . The DEMATEL approach, however, provides a means to measure the strength of each relationship. To address potential subjectivity and vagueness in expert input, this study combines grey theory with DEMATEL, aiming to enhance the precision and reliability of the causal relationships among the CBFs 55 .
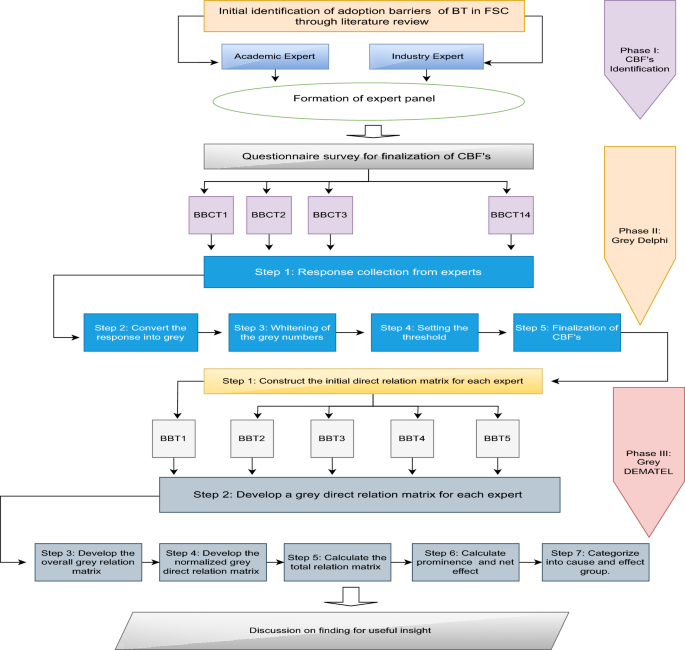
Proposed framework for CBFs of blockchain adoption in FSC.
Grey Delphi and Grey DEMATEL are particularly well-suited for handling situations with uncertain and incomplete information. In the context of our study on the adoption barriers of blockchain technology in the Chinese Fisheries Supply Chain, the presence of uncertainties warranted a methodology that could effectively manage and process imperfect information. Grey systems theory provides a flexible framework that allows for the incorporation of uncertainties in decision-making processes. Given the dynamic and complex nature of the barriers within the supply chain, we found Grey Delphi and Grey DEMATEL to be suitable for modeling and evaluating the interactions among critical barrier factors. The choice of Grey Delphi and Grey DEMATEL has been successfully applied in prior studies involving complex decision-making scenarios. This includes situations where there is a need to evaluate and prioritize factors within supply chains, making them relevant and applicable to our investigation in the Chinese Fisheries Supply Chain. Grey systems theory allows for a more straightforward interpretation of results, which is essential for conveying findings to a diverse audience, including stakeholders and practitioners in the fisheries industry. This aligns with our objective to ensure that the outcomes of our study are accessible and actionable.
The data collection protocol for this research is a methodically structured process aimed at acquiring high-quality input from a diverse group of experts in supply chain management and blockchain technology. The initial step involved a careful selection of experts, considering variations in professional backgrounds, experiences, and educational qualifications to ensure a comprehensive perspective. After identifying potential participants, informed consent was obtained, outlining the purpose, confidentiality, and voluntary nature of their involvement. To gather relevant and insightful information, tailored questionnaires were designed for the Grey Delphi and Decision-Making Trial and Evaluation Laboratory (DEMATEL) methodologies. These questionnaires are crafted to elicit detailed responses on critical barrier factors affecting the adoption of blockchain technology in the Chinese Fisheries Supply Chain. Descriptive data, including the designation, work experience, country of residence, educational background, and gender of each expert, was collected to provide context and potentially identify patterns within the expert panel. Furthermore, the participants' history of engagement in Grey Delphi, DEMATEL, or both was recorded, allowing for an understanding of their familiarity with the methodologies. Similarly, the distribution of electronic questionnaires is conducted systematically, with periodic reminders to ensure timely and complete responses. In cases where additional clarification or insights are needed, follow-up interviews were conducted in a structured manner. Data validation is a crucial step to ensure the accuracy and reliability of the collected information. Cross-referencing responses and addressing any discrepancies or outliers enhances the integrity of the dataset. Subsequently, the collected data undergoes rigorous analysis, involving Grey Delphi iterations and DEMATEL analysis. These methodologies are employed to quantify qualitative responses and construct a matrix of pairwise comparisons, facilitating a robust examination of critical barrier factors in the adoption of blockchain technology within the Chinese Fisheries Supply Chain. Finally, the aggregated findings were presented in a clear and comprehensive manner, adhering to scientific standards. This meticulous data collection protocol ensures the credibility and validity of the research outcomes, contributing to a nuanced understanding of the complexities surrounding blockchain technology adoption in the fisheries supply chain context. The expert details are provided in Table 1 .
Preliminaries
To address the issue of uncertainties inherent in expert input for Multiple Criteria Decision Making (MCDM) methods, this study incorporates the theory of grey systems 56 , a methodology widely used across various domains. Specifically, this research combines grey systems theory with Delphi and DEMATEL techniques to handle subjective data provided by expert panels.
In the grey systems framework, information is categorized into three distinct groups: fully certain information is denoted as white, inadequate information is represented as grey, and absolute unknown information is indicated as black 57 . In this study, the concept of interval grey numbers from the grey system theory has been applied. As a result, the essential definitions and operations of interval grey numbers are provided as follows:
Definition 1
Suppose \(\otimes\) G implies the interval grey number that could be expressed as:
where, \(\underset{\_}{{\text{G}}}\) shows the lower limit and \(\overline{{\text{G}} }\) depicts the upper limits of the information \(\otimes\) G.
Definition 2
The fundamental mathematical operations on the interval grey numbers are provided as follows:
Addition of two interval grey number is expressed as Eq. ( 2 ):
Subtraction of interval grey number is expressed as Eq. ( 3 ):
Multiplication of interval grey number is expressed as Eq. ( 4 ):
Division of interval grey number is expressed as Eq. ( 5 ):
Definition 3
Usually, the whitenisation value (crisp value) of the interval grey number \(\otimes {G}_{i}=\left[\underline{G},\overline{G }\right]\) is done with \(\otimes\) and could be done through Eq. ( 6 ).
where, a is the coefficient of whitenisation and the commonly used value for a is 0.5, considering the equal weight mean whitenisation.
Grey Delphi
Dalkey and Helmer 58 introduced the Delphi approach, a widely used survey methodology designed to aggregate expert opinions on a particular issue with the goal of achieving a collective consensus 59 . However, the traditional Delphi method has certain drawbacks, including the need for multiple rounds to reach a consensus, susceptibility to subjectivity, and potential expert biases. To address these limitations, the integration of grey theory is proposed 60 . Consequently, the combination of Delphi and grey set theories results in the creation of the grey Delphi approach. The following outlines the key steps involved in implementing the grey Delphi method:
Step 1: identifying the obstacles to blockchain adoption within the Fisheries Supply Chain (FSC).
This stage encompasses the recognition of possible adoption hindrances within the FSC by conducting a thorough literature review. Utilizing these identified Critical Barrier Factors (CBFs), a questionnaire is then crafted to gather expert input and data.
Step 2: Response compilation from experts.
Gathering responses from experts involves distributing the constructed questionnaire to these individuals, who are requested to furnish their answers using a linguistic scale. The linguistic scales and corresponding grey numbers for each scale can be found in Table 2 .
Step 3: Comprehensive evaluation using grey number.
Comprehensive assessment employing grey numbers is carried out by converting the responses into corresponding grey numbers. These grey numbers serve as the basis for consolidating the feedback provided by the panel of experts, which, in this context, consists of k members. The evaluation of the factor \(\otimes {{\text{G}}}_{{\text{i}}}\) is as follows:
where \(\otimes {{\text{G}}}_{{\text{i}}}\) i is the overall evaluation of adoption factors and \(\otimes {{\text{G}}}_{{\text{i}}}^{{\text{h}}}\) denotes the hth expert’s evaluation of CSF ‘i’ of blockchain adoption barrier.
Step 4: Whitening of the grey number.
The grey number having the interval \(\left(\otimes {{\text{G}}}_{{\text{i}}}=[\underset{\_}{{\text{G}}},\overline{{\text{G}} }]=\left[{{\text{G}}}^{{{\prime}}}\in {\text{G}}\mid \underset{\_}{{\text{G}}}\le {{\text{G}}}^{{{\prime}}}\le \underset{\_}{{\text{G}}}\right]\right)\) and their equivalent whitenisation value is \(\widetilde{\otimes }\) . The whitenisation of grey numbers is obtained through Eq. ( 6 ) as mentioned in preliminary section.
Step 5: Setting threshold limit and CBFs selection.
The final step of the grey Delphi method involves selecting and rejecting CBFs. In order to determine the significance of the factor, an overall score is calculated and compared to a threshold value \((\uplambda )\) . If the value of \(\widetilde{\otimes }\ge\uplambda\) , then the factor is selected; otherwise, it is rejected. The accepted CBF’s are shown in Fig. 2 .
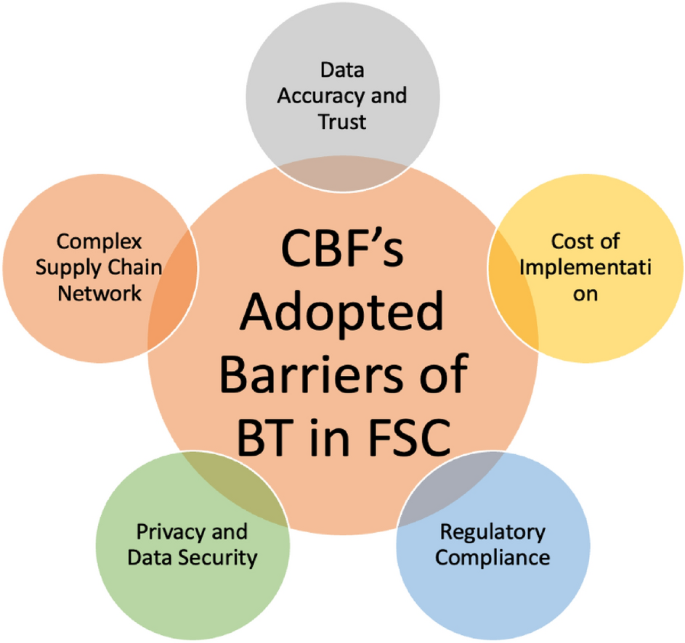
CBFs of BT adoption barriers in FSC.
Grey DEMATEL
A grey DEMATEL approach combines grey theory and DEMATEL to address the incomplete information, subjectivities, and biases in expert input. Furthermore, this method can improve the accuracy of the observations. Following is the stepwise procedure for grey DEMATEL.
Step 1: Construct the initial direct-relation matrix.
Develop an initial direct relation matrix of CBFs (c = {ci|i = 1, 2,, n}) of blockchain adoption barriers n FSC, utilizing the five-point grey linguistic scale (refer to Table 3 ), from “No Influence” to “Very High influence” by k experts through pair-wise comparisons.
Step 2: Develop a grey direct-relation matrix.
The linguistic term is substituted with the corresponding grey number to convert the obtained initial direct relationship matrix into a grey initial direct relationship matrix. As K-number of experts provided their responses, the K grey direct relationship matrix X1, X2, X3…, XK is obtained. The direct-relation grey matrix is represented as follows by Eq. ( 8 ):
The element of [X], \(\otimes {{\text{x}}}_{{\text{ijk}}}=\left(\underset{\_}{\otimes }{{\text{x}}}_{{\text{ijk}}},\overline{\otimes }{{\text{x}} }_{{\text{ijk}}}\right)\) , shows the influence of CBF ‘i’ on CBF ‘j’ by the kth expert. The x ijk represents the lower and xijk the upper limit of grey values.
Step 3: Develop the overall grey relation matrix.
To formulate the overall grey relation matrix, all grey direct relation matrices were combined by using Eq. ( 9 ).
Step 4: Express the normalized grey direct-relation matrix. In order to transform the grey relation matrix into a normalized grey direct-relation matrix N,
Equations ( 4 )–( 6 ) are used.
Step 5: Calculate the total relation matrix.
The total relation matrix “T” is obtained from the normalized grey direct-relation matrix by using Eq. ( 13 ).
where “I” is the grey identity matrix.
Step 6: Compute the causal parameters.
The Eqs. ( 14 ) and ( 15 ) are used to determine the causal parameter:
The R i shows the influence of the CSF “i”, which infers the overall influence of CBFs, and the Cj represents the influence received by “j” by the other CBFs.
Step 7: Calculate the prominence (Pi) and net effect (Ei)
The prominence (Pi) and net effect (Ei) score of the CBFs is determined using expressions ( 16 ) and ( 17 ):
The causal relationship diagram is constructed using the prominence (Pi) and net effect (Ei) scores. A positive Ei value indicates that a CBF causes an effect on the system, while a negative Ei value signifies its impact on the CBF itself.
Identifying obstacles in implementing blockchain technology within the fisheries supply chain
The literature review uncovered several challenges hindering the effective implementation of blockchain technology (BT) in fisheries within the context of supply chains (SCs). To identify relevant scholarly articles, the study relied on the Scopus database, a renowned repository of scientific literature. A targeted search in the Scopus database using keywords such as 'fisheries supply chain management,' 'fish- supply chain' 'blockchain technology,' 'supply chain obstacles,' 'challenges,' and 'barriers were conducted. The search query is created by using Boolean operators to combine these keywords. Subsequently, these queries are executed in the Scopus database to locate relevant articles. Following this relevant academic works were selected based on an initial assessment of the article's abstract and title. Subsequently, an exhaustive examination of the existing literature, resulting in the identification of fourteen specific Critical Barrier Factors (CBFs) that impede the successful integration of blockchain technology into supply chains were conducted. These obstacles can be found in Table 4 .
After initially identifying the Critical Barrier Factors (CBFs) for the adoption of blockchain technology in FSC, the grey Delphi method with the assistance of experts were applied. To ensure a well-rounded perspective, experts from both academia and industry were selected 16 . The study assembled a group of professionals from the FSC and technology development sectors, each of whom possessed a minimum of five years of experience in FSC management. Additionally, the work enlisted academic experts specializing in FSC, technology management, or technology transfer, who were affiliated with respected academic institutions. The selection of these experts was based on their demonstrated expertise and knowledge in the field of FSC. As a result, a total of 9 valid responses were collected, which are presented in Table 5 .
Following the collection of feedback from the panel of experts, the transformation of the linguistic values into numerical representations was done using Table 2 . The resulting grey matrix is displayed in Table 6 . This table serves as the numerical foundation for the subsequent application of the Grey Delphi method, facilitating a systematic and quantitative analysis of expert opinions on the critical barriers influencing the adoption of blockchain technology in the Chinese Fisheries Supply Chain.
To further analyze and prioritize these obstacles, the study calculated the overall grey weight using Eq. ( 1 ) and subsequently converted it into a crisp number using Eq. ( 2 ). The precise numerical data were instrumental in determining whether to include or exclude obstacles from this subsequent study. Obstacles with a crisp value exceeding 3.5 were included, while those below this threshold were excluded 82 , 83 . Detailed measurements of both grey and crisp weight, along with corresponding decisions, are provided in Table 7 . This table provides a comprehensive overview of the outcomes of the Grey Delphi method, aiding in the identification and classification of critical barriers with a strategic decision-making process. The decisions to either select or reject each obstacle, along with their respective crisp weights, guide the subsequent steps in addressing and mitigating the barriers to the adoption of blockchain technology in the Chinese Fisheries Supply Chain.
In this way, the work identified five significant obstacles associated with the adoption of blockchain technology in emerging economies. Additionally, the confirmed barriers to embracing blockchain technology are detailed in Table 8 . These barriers highlight the multifaceted challenges faced by the fisheries industry in adopting blockchain technology, ranging from logistical complexities to financial constraints and regulatory intricacies. The detailed descriptions provide a nuanced understanding of each identified obstacle, forming a foundation for targeted strategies and interventions to enhance blockchain adoption in the Fisheries Supply Chain. Additionally, Fig. 2 visually represents the confirmed barriers, offering a graphical depiction of their significance and interrelationships.
DEMATEL analysis
The Decision-Making Trial and Evaluation Laboratory (DEMATEL) is recognized as a valuable approach for pinpointing the cause-and-effect relationships within intricate systems. DEMATEL enables the assessment of interlinked factors and the identification of critical elements by constructing a visual structural model 84 . DEMATEL analysis is a powerful technique for understanding and managing complex systems, and it has been applied in various fields to solve problems and improve decision-making processes. The study conducted an analysis using grey DEMATEL to explore the causal relationships among Critical Barrier Factors (CBFs) in the adoption of blockchain technology in FSC. To guide the experts through the research process, we initially outlined the study's objectives. The experts were then asked to assess how one CBF influences another, using a linguistic scale in the form of a direct-relationship matrix. We converted the original direct relationship matrices into grey relationship matrices using grey numbers. With input from six experts, we obtained six grey initial relationship matrices, which were subsequently combined to form a global grey relation matrix presented in Table 9 .
Initially, the expert panel provided the Initial Direct Relationship Matrix (IDRM). Among these experts, six possess expertise in fisheries supply chain management, technology adoption, and Blockchain. Using Eq. ( 1 ), overall direct relationship matrix was created, which is presented in Table 5 . Subsequently, we transformed the IDRM into a Normalized Relationship Matrix (NRM) using Eqs. ( 2 ) and ( 3 ), and the resulting NRM is displayed in Table 10 . Equation ( 4 ) was used to convert the obtained Normalized Relationship Matrix (NRM) into a total relationship matrix (T), and the resulting matrix is displayed in Table 11 .
The work calculated a threshold value to identify significant relationships among the barriers. This threshold is determined by adding the average and standard deviation of the T matrix. It helps differentiate the structure and aids in developing the causal map. If the values in Table 11 's T matrix exceed this threshold, a causal map is drawn. This cause-and-effect map not only helps assess the importance of one barrier over another but also filters out minor effects. The causal map for blockchain technology adoption barriers, constructed using the T matrix in Table 11 , is shown in Fig. 3 . Additionally, the map distinguishes cause-and-effect barriers with different colors.
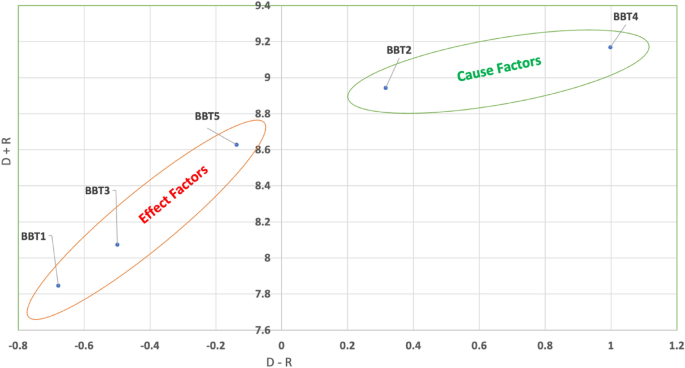
Causal relationship map among barriers of BT adoption in the fisheries supply chain.
Later the row-wise summation (R) and column-wise summation (C) in the total relationship matrix T were calculated using Eqs. ( 5 ) and ( 6 ), which are displayed in Table 12 . Additionally, the prominence scores and effect scores with the assistance of Eqs. ( 7 ) and ( 8 ), respectively were determined.
The DEMATEL method was used to determine the order of importance for each barrier. The degree of influence between the identified constructs is indicated by the relationship intensity, while (D—R) signifies the criteria for the cause-and-effect grouping. However, the central strength of these constructs is represented by the (D + R) value. Typically, the cause group construct operates independently and propels the effect group construct, as observed in the study by 85 . The critical order of the barriers is as follows: ' Regulatory compliance ' is ranked highest, followed by 'Data accuracy and trust,' ‘Privacy and data security,' 'Cost of implementation,' and finally, ' Complex supply chain network.' The importance order of each barrier is illustrated in Fig. 4 .
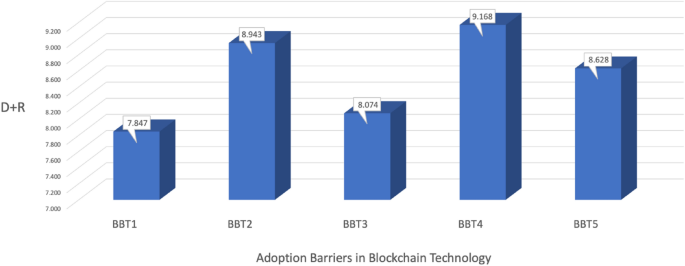
Ranking of the barriers to BT implementation in the fisheries supply chain.
Sensitivity analysis
Conducting a sensitivity analysis involves assessing the robustness of results. In this context, the approach employed includes altering the weighting assigned to one expert's input while maintaining uniform weightings for the remaining experts. Various methods can be employed for this purpose, such as adjusting the weight levels attributed to individual experts or different barriers. In this study, archetypal sensitivity analysis is utilized, wherein distinct weightings are assigned to experts. To illustrate, initially, the weight assigned to Expert 1 was set at 0.2, while the other experts were given a weight of 0.1. To conduct sensitivity analysis, nine distinct total relationship matrices were generated by multiplying the weights assigned to various experts as outlined in Table 6 and similar matrices. Subsequently, average relationship matrices were calculated, leading to the establishment of cause-effect relationships among different barriers. The weights assigned to the nine experts and the ranking of diverse barriers during the sensitivity analysis are presented in Tables 13 and 14 . From the table, it is clear that there was no major change in barrier rankings after sensitivity analysis. The same rank order for cause-effect barriers for each expert was obtained, accepting minor rank value variation. Therefore, the sensitivity analysis confirms the robustness of obtained results.
The complexity of the fisheries supply chain emerged as a prominent barrier, given the involvement of numerous intermediaries. To overcome this, it is crucial to comprehensively map the supply chain network, streamline processes, establish interoperability standards, select scalable blockchain solutions, and implement permissioned networks. Ensuring data accuracy and trust is essential, and mechanisms for data validation and verification within the blockchain should be implemented. Additionally, strategies such as robust supplier onboarding procedures and secure authentication mechanisms can enhance data accuracy and trust. Implementing blockchain technology involves various costs, posing a financial barrier, especially for small and medium-sized fisheries enterprises. To address this challenge, a comprehensive cost–benefit analysis is crucial, and a phased implementation approach, collaboration with stakeholders, exploration of open-source blockchain solutions, and seeking government grants and incentives can help alleviate the financial burden. Regulatory compliance is a significant barrier in the seafood industry, subject to diverse and evolving regulations. Open communication with regulatory authorities, integration of compliance features into blockchain design, and leveraging smart contracts for automated compliance checks are recommended strategies. Robust data privacy and security measures, comprehensive auditing, and reporting tools are crucial for compliance. While blockchain offers transparency, protecting sensitive information is equally important, necessitating strong data privacy and security measures. The DEMATEL analysis revealed causal relationships among the identified barriers, with 'Regulatory Compliance' emerging as the most influential barrier, followed by 'Cost of Implementation' and 'Complex Supply Chain Network.' Overcoming these barriers requires a multifaceted approach considering technology, compliance, financial aspects, and data security, and collaboration among stakeholders, ongoing monitoring, and adaptation to changing regulations are instrumental in addressing these challenges, offering valuable insights for industry players, policymakers, and researchers seeking to enhance transparency, traceability, and sustainability within the fisheries supply chain through blockchain technology.
However, China faces specific barriers that are influenced by its unique socio-economic and regulatory environment. The country's complex supply chain network (BBCT1) is a distinctive challenge due to the sheer scale and diversity of its fisheries industry. This complexity can hinder the seamless integration of blockchain across the entire supply chain 61 . Additionally, regulatory compliance (BBCT7) is a significant concern in China, given the government's active involvement in shaping the technology landscape 86 . China's regulatory framework may require adjustments and alignment with blockchain technology adoption.
On the other hand, China's comparatively strong emphasis on technology development and innovation might serve as an advantage in addressing these barriers. China's rapid progress in technology adoption and its large market size can potentially accelerate the resolution of these challenges 65 . Nevertheless, it remains essential for both China and the global fisheries industry to address these shared and unique barriers effectively to harness the full potential of blockchain technology for enhanced sustainability and food security in the fisheries supply chain.
Effect CBF’s
The study categorized the identified barriers as 'effect barriers' and 'cause barriers.' The group of 'effect barriers' comprises three key barriers: 'Regulatory Compliance,' 'Cost of Implementation,' and 'Complex Supply Chain Network.' These barriers demand greater attention, as they exert influence on other significant barriers. The most influential barrier is regulatory compliance. Regulatory compliance serves as a significant obstacle to the widespread adoption of blockchain technology within the fisheries supply chain. This barrier arises from the complex and dynamic nature of regulations governing the fishing industry, which vary across regions and evolve over time. Blockchain implementation in this context requires alignment with diverse legal frameworks, making it a complex and resource-intensive endeavor. Additionally, ensuring transparency and traceability in compliance with these regulations through blockchain technology can be challenging, further impeding its adoption. Addressing these regulatory hurdles is crucial for realizing the full potential of blockchain in enhancing transparency and sustainability within the fisheries supply chain.
Overcoming the barrier of regulatory compliance in blockchain adoption within the fisheries supply chain entails a multifaceted approach. This involves establishing open lines of communication with regulatory bodies and industry stakeholders to align blockchain strategies with existing regulations. Leveraging expertise in fisheries regulations for tailored solutions, developing adaptable blockchain systems to accommodate evolving compliance requirements, implementing robust data security measures, and utilizing smart contracts for automated compliance checks are crucial steps. Furthermore, maintaining comprehensive audit trails, educating stakeholders, conducting pilot programs to showcase benefits, engaging in advocacy efforts for regulatory reforms, and continuously monitoring and adapting blockchain solutions to changing regulations are essential components of this comprehensive approach.
The next effect barriers is cost of implementation. To overcome this barrier in the fisheries supply chain, a strategic approach is essential. This involves conducting a comprehensive cost–benefit analysis to highlight blockchain's potential to enhance transparency, reduce fraud, improve traceability, and enable better decision-making in the supply chain. Implementing a phased approach, starting with smaller-scale pilot projects, allows for a thorough assessment of costs and benefits before full-scale deployment. Collaboration with supply chain stakeholders can distribute financial burdens, while exploring open source blockchain solutions and leveraging third-party providers can reduce expenses. Investigating government grants and incentives, adopting lean development practices, investing in staff training, and continuously monitoring ROI help ensure that the benefits of blockchain outweigh initial implementation costs.
The final effect barrier is complex supply chain network and to overcome this barrier it begins with mapping the entire network comprehensively, encompassing stakeholders, processes, and data flows to gain a clear understanding of the complexity. Identifying opportunities to simplify or streamline processes helps reduce unnecessary intricacies. The establishment of interoperability standards ensures seamless communication between various systems and the blockchain, mitigating integration challenges. Choosing a scalable blockchain solution accommodates network growth, while implementing permissioned networks enhances control and security. Ensuring data consistency and standardization, along with education and training, fosters effective adaptation. Pilot projects validate compatibility and effectiveness, expert consultation tailors solutions, and continuous improvement and collaboration across stakeholders collectively address the intricacies of the supply chain, promoting successful blockchain adoption.
Cause CBF’s
The cause barrier group includes ‘Regulatory Compliance’ and ‘Data Accuracy and Trust’. Amongst the two, the most cause barrier is regulatory compliance which can be overcome by considering a multifaceted approach. Engage in open communication with regulatory authorities to understand their specific requirements. Leverage regulatory expertise by consulting specialists in fisheries regulations and integrate compliance into the blockchain's design. Utilize smart contracts to automate and monitor compliance and implement robust data privacy and security measures. Integrate auditing tools, explore regulatory sandboxes, and collaborate with stakeholders. Stay updated on evolving regulations, educate your team, maintain transparency with regulators, and engage in advocacy efforts for blockchain-friendly reforms. These strategies collectively enable compliance while harnessing blockchain's potential for transparency and traceability. In order to overcome the data accuracy and trust there is a need to engage in open communication with regulatory authorities to understand their specific requirements 62 . Leverage regulatory expertise by consulting specialists in fisheries regulations and integrate compliance into the blockchain's design 31 . Utilize smart contracts to automate and monitor compliance and implement robust data privacy and security measures. Integrate auditing tools, explore regulatory sandboxes, and collaborate with stakeholders. Stay updated on evolving regulations, educate your team, maintain transparency with regulators, and engage in advocacy efforts for blockchain-friendly reforms. These strategies collectively enable compliance while harnessing blockchain's potential for transparency and traceability.
Managerial and policy implications
The findings of our research carry significant implications for decision-makers engaged in the implementation of Sustainable Fisheries Supply Chain Management (SFSCM). The study has yielded several managerial recommendations. The impact group can be readily influenced by the cause group, underscoring the importance of managers directing their attention primarily towards addressing causal barriers when integrating SFSCM practices into their conventional supply chains. This research aids managers in delineating barriers that demand heightened focus within their respective industries, distinguishing between those of greater and lesser significance. The hierarchical classification of barriers in the cause and effect groups provides valuable assistance to managers and decision-makers in formulating strategic policies during the implementation of SSCM. The outcomes of this research framework have the potential to motivate decision-makers and industrial managers to embrace SFSCM practices that are pivotal for sustainable development and exert the most substantial influence on the transformation of traditional supply chains in the fisheries sector. Managers can view this framework as a benchmark for enhancing traditional supply chains, thereby fostering improvements in environmental, social, and economic sustainability.
Based on the findings of the research on blockchain technology barriers in fisheries supply chains, several key policy implications emerge. Government entities should focus on nurturing trust within the industry by facilitating industry group discussions and educational programs to enhance awareness and understanding of blockchain technology (BT). Moreover, improving information infrastructure, including data security standards, can alleviate concerns regarding privacy and data security. Policymakers can incentivize BT adoption through tax benefits and grants, foster partnerships with technology providers to address technical hurdles, and enforce transparency and accountability measures within the supply chain. Cost mitigation options, particularly for small and medium-sized enterprises (SMEs), and the promotion of a culture of information sharing can further reduce adoption barriers. Implementing performance metrics and supporting research and development initiatives are essential steps in creating an enabling environment for successful BT adoption, ultimately enhancing transparency, efficiency, and sustainability in the fisheries sector.
The work also has significant policy implications for businesses and industry leaders. To overcome primary barriers such as information sharing readiness and trust issues, executives can invest in relationship-building efforts, align incentives, and consider co-investing in blockchain technology (BT) initiatives. Leveraging third-party technologies and training programs can help businesses source expertise and address these hurdles effectively. Furthermore, formal business case evaluations of BT adoption, articulating its net benefits, can encourage companies to shift their information policies and corporate culture towards more openness and collaboration. These findings offer valuable insights for policymakers and business leaders to proactively anticipate and mitigate potential implementation challenges, fostering a climate of innovation and cooperation within fisheries supply chains. This approach can ultimately lead to improved data and knowledge sharing, creating win–win outcomes across supply chains, enhancing food security, and promoting sustainability in the industry.
Conclusion and future work
The comprehensive exploration of challenges and barriers associated with implementing blockchain technology in fisheries supply chains reveals a complex landscape that demands nuanced strategies for successful integration. Drawing upon an extensive literature review and utilizing the Scopus database, this study employed the grey Delphi method, with input from both academic and industry experts, to identify fourteen Critical Barrier Factors (CBFs). These factors represent key obstacles hindering the effective assimilation of blockchain technology into supply chains, forming the foundation for further analysis. The study sheds light on five significant obstacles specifically linked to the adoption of blockchain technology in emerging economies within the fisheries industry. These obstacles underscore the multifaceted challenges faced by fisheries, encompassing logistical complexities, financial constraints, and regulatory intricacies. The Decision-Making Trial and Evaluation Laboratory (DEMATEL) method, employed to explore causal relationships among CBFs, generated valuable insights. Regulatory compliance emerged as the most pivotal, followed by data accuracy and trust, privacy and data security, the cost of implementation, and the complexity of the supply chain network. DEMATEL not only identifies critical barriers but also unravels their intricate relationships. This nuanced understanding provides actionable guidance for policymakers, industry practitioners, and researchers, facilitating the formulation of targeted interventions and strategies crucial for the successful adoption of blockchain technology in fisheries supply chains.
Regulatory compliance poses a formidable challenge, given the diverse and evolving nature of regulations in the seafood industry. Recommended strategies include open communication with regulatory authorities, integration of compliance features into blockchain design, and the use of smart contracts for automated compliance checks. Robust data privacy and security measures, comprehensive auditing, and reporting tools are emphasized for achieving compliance. The unique socio-economic and regulatory environment of China introduces specific barriers, necessitating tailored approaches to enable seamless integration of blockchain across the entire supply chain. The study categorizes barriers as 'efffect' and 'cause,' with regulatory compliance identified as the most influential due to the dynamic nature of fishing industry regulations. Addressing regulatory hurdles is crucial for unlocking the full potential of blockchain in enhancing transparency and sustainability within fisheries supply chains.
To overcome the challenges associated with the complex supply chain network, the study recommends a collaborative approach involving comprehensive mapping, simplification of processes, establishment of interoperability standards, selection of scalable blockchain solutions, implementation of permissioned networks, ensuring data consistency and standardization, and continuous improvement through stakeholder collaboration. The research highlights regulatory compliance and data accuracy and trust as the most cause barriers in the implementation of Sustainable Fisheries Supply Chain Management (SFSCM). To address these, managers are advised to engage in open communication with regulatory authorities, leverage regulatory expertise, integrate compliance into blockchain design, use smart contracts, employ auditing tools, explore regulatory sandboxes, and collaborate with stakeholders. Staying updated on evolving regulations, maintaining transparency, and advocating for blockchain-friendly reforms are also recommended strategies.
The study, while comprehensive in its examination of blockchain technology (BT) adoption barriers within the fisheries supply chain, is not without its limitations. Firstly, the barriers were initially identified and refined based on a combination of literature survey and expert opinions. Although extensive efforts were made to encompass a wide spectrum of perspectives, it is possible that certain potential barriers may have been inadvertently overlooked in the selection and review process. Additionally, the evaluation heavily relies on expert feedback, which, despite the study’s design efforts to minimize bias, may still introduce some degree of subjectivity.
To mitigate these limitations, future research endeavors should consider broader validation and refinement processes to enhance this collective understanding of BT barriers. Firstly, researchers should delve into the dynamic nature of regulatory compliance, given its influential role in obstructing the adoption of blockchain technology in the fisheries supply chain. A more in-depth investigation into the evolving regulatory landscape, both globally and regionally, could provide a nuanced understanding of the challenges posed and contribute to the development of adaptive strategies. This could involve exploring the feasibility and effectiveness of technological solutions, such as smart contracts, in automating compliance checks and adapting to regulatory changes in real-time. Secondly, future work should focus on refining and expanding the strategies proposed for overcoming the financial barriers associated with implementing blockchain technology, particularly for small and medium-sized fisheries enterprises. Further research can investigate the long-term cost-effectiveness of different blockchain solutions, the scalability of open-source options, and the potential impact of government grants and incentives. Additionally, exploring innovative financing models and collaborations within the industry could contribute to more sustainable and feasible financial approaches. Addressing the unique challenges faced by the fisheries industry in emerging economies, especially in China, requires specific attention in future research. Tailored strategies for navigating the socio-economic and regulatory landscape of these regions can be developed to facilitate the seamless integration of blockchain technology across the entire supply chain. Comparative studies between emerging and developed economies could provide valuable insights into the contextual variations influencing blockchain adoption.
Data availability
The datasets used and analyzed during the current study are available from the corresponding author on reasonable request.
Nisar, U., Peng, D., Mu, Y. & Sun, Y. A solution for sustainable utilization of aquaculture waste: A comprehensive review of biofloc technology and aquamimicry. Front. Nutr. 8 , 1 (2022).
Nisar, U., Zhang, Z., Cui, Z., Mu, Y. & Zhang, H. Impact of COVID-19 on fish and crustacean export from China with building resilient food system through China’s lens. Front. Sustain. Food Syst. 7 , 1 (2023).
Schmidt, C. G. & Wagner, S. M. Blockchain and supply chain relations: A transaction cost theory perspective. J. Purch. Supply Manag. 25 , 100552 (2019).
Article Google Scholar
Yang, J. et al. Improving commute experience for private car users via blockchain-enabled multitask learning. IEEE Internet Things J. 10 , 21656–21669 (2023).
Wang, Z.-J. et al. Blockchain adoption in sustainable supply chains for Industry 5.0: A multistakeholder perspective. J. Innov. Knowl. 8 , 100425 (2023).
Duan, J., Zhang, C., Gong, Y., Brown, S. & Li, Z. A content-analysis based literature review in blockchain adoption within food supply chain. Int. J. Environ. Res. Public. Health 17 , 1784 (2020).
Article PubMed PubMed Central Google Scholar
Aslam, J., Saleem, A., Khan, N. T. & Kim, Y. B. Factors influencing blockchain adoption in supply chain management practices: A study based on the oil industry. J. Innov. Knowl. 6 , 124–134 (2021).
Xu, J., Yang, Z., Wang, Z., Li, J. & Zhang, X. Flexible sensing enabled packaging performance optimization system (FS-PPOS) for lamb loss reduction control in E-commerce supply chain. Food Control 145 , 109394 (2023).
Mondragon, A. E. C., Mondragon, C. E. C. & Coronado, E. S. Feasibility of internet of things and agnostic blockchain technology solutions: a case in the fisheries supply chain. In 2020 IEEE 7th International Conference on Industrial Engineering and Applications (ICIEA) 504–508 (IEEE, 2020).
Sun, Y., Shahzad, M. & Razzaq, A. Sustainable organizational performance through blockchain technology adoption and knowledge management in China. J. Innov. Knowl. 7 , 100247 (2022).
Siddiqui, R., Azmat, M., Ahmed, S. & Kummer, S. A hybrid demand forecasting model for greater forecasting accuracy: the case of the pharmaceutical industry. In Supply Chain Forum: An International Journal vol. 23 124–134 (Taylor & Francis, 2022).
Perera, H. N., Hurley, J., Fahimnia, B. & Reisi, M. The human factor in supply chain forecasting: A systematic review. Eur. J. Oper. Res. 274 , 574–600 (2019).
Article MathSciNet Google Scholar
Tliche, Y., Taghipour, A., Mahfod-Leroux, J. & Vosooghidizaji, M. Collaborative bullwhip effect-oriented bi-objective optimization for inference-based weighted moving average forecasting in decentralized supply chain. Int. J. Inf. Syst. Supply Chain Manag. 16 , (2023).
Ojha, D., Sahin, F., Shockley, J. & Sridharan, S. V. Is there a performance tradeoff in managing order fulfillment and the bullwhip effect in supply chains? The role of information sharing and information type. Int. J. Prod. Econ. 208 , 529–543 (2019).
Huang, Y., Han, W. & Macbeth, D. K. The complexity of collaboration in supply chain networks. Supply Chain Manag. Int. J. 25 , 393–410 (2020).
Khan, S., Khan, M. I. & Haleem, A. Evaluation of barriers in the adoption of halal certification: A fuzzy DEMATEL approach. J. Model. Manag. 14 , 153–174 (2019).
Shahzad, M., Qu, Y., Rehman, S. U. & Zafar, A. U. Adoption of green innovation technology to accelerate sustainable development among manufacturing industry. J. Innov. Knowl. 7 , 100231 (2022).
Drath, R. & Horch, A. Industrie 4.0: Hit or hype?[industry forum]. IEEE Ind. Electron. Mag. 8 , 56–58 (2014).
Chien, C.-F., Chou, C.-W. & Yu, H.-C. A novel route selection and resource allocation approach to improve the efficiency of manual material handling system in 200-mm wafer fabs for industry 3.5. IEEE Trans. Autom. Sci. Eng. 13 , 1567–1580 (2016).
Nguyen, P. T. & Nguyen, L. T. M. A multi-country analysis of policy uncertainty and Blockchain Innovation. J. Innov. Knowl. 8 , 100379 (2023).
Zhao, G. et al. Blockchain technology in agri-food value chain management: A synthesis of applications, challenges and future research directions. Comput. Ind. 109 , 83–99 (2019).
Angelis, J. & Ribeiro da Silva, E. Blockchain adoption: A value driver perspective. Bus. Horiz. 62 , 307–314 (2019).
Kshetri, N. 1 Blockchain’s roles in meeting key supply chain management objectives. Int. J. Inf. Manag. 39 , 80–89 (2018).
Kouhizadeh, M., Saberi, S. & Sarkis, J. Blockchain technology and the sustainable supply chain: Theoretically exploring adoption barriers. Int. J. Prod. Econ. 231 , 107831 (2021).
Hu, F. et al. Research on the evolution of China’s photovoltaic technology innovation network from the perspective of patents. Energy Strategy Rev. 51 , 101309 (2024).
Longo, F., Nicoletti, L., Padovano, A., d’Atri, G. & Forte, M. Blockchain-enabled supply chain: An experimental study. Comput. Ind. Eng. 136 , 57–69 (2019).
Saberi, S., Kouhizadeh, M., Sarkis, J. & Shen, L. Blockchain technology and its relationships to sustainable supply chain management. Int. J. Prod. Res. 57 , 2117–2135 (2019).
Helo, P. & Hao, Y. Blockchains in operations and supply chains: A model and reference implementation. Comput. Ind. Eng. 136 , 242–251 (2019).
Ge, L. et al. Blockchain for Agriculture and Food: Findings from the Pilot Study . (Wageningen Economic Research, 2017).
Saberi, S., Kouhizadeh, M. & Sarkis, J. Blockchains and the supply chain: Findings from a broad study of practitioners. IEEE Eng. Manag. Rev. 47 , 95–103 (2019).
Wamba, S. F. & Queiroz, M. M. Blockchain in the Operations and Supply Chain Management: Benefits, Challenges and Future Research Opportunities . International Journal of Information Management vol. 52 102064 (Elsevier, 2020).
Li, Q.-K. & Lin, H. H∞ Consensus for Multi-Agent Based Supply Chain Systems under Switching Topology and Uncertain Demands.
Kumar Bhardwaj, A., Garg, A. & Gajpal, Y. Determinants of blockchain technology adoption in supply chains by small and medium enterprises (SMEs) in India. Math. Probl. Eng. 2021 , 1–14 (2021).
Allen, D. W., Berg, C., Davidson, S., Novak, M. & Potts, J. International policy coordination for blockchain supply chains. Asia Pac. Policy Stud. 6 , 367–380 (2019).
Huang, W., Wang, X., Zhang, J., Xia, J. & Zhang, X. Improvement of blueberry freshness prediction based on machine learning and multi-source sensing in the cold chain logistics. Food Control 145 , 109496 (2023).
Alazab, M., Alhyari, S., Awajan, A. & Abdallah, A. B. Blockchain technology in supply chain management: an empirical study of the factors affecting user adoption/acceptance. Clust. Comput. 24 , 83–101 (2021).
Huang, W. et al. Flexible sensing enabled agri-food cold chain quality control: A review of mechanism analysis, emerging applications, and system integration. Trends Food Sci. Technol. 133 , 189–204 (2023).
Article CAS Google Scholar
Yadav, V. S. & Singh, A. R. Use of blockchain to solve select issues of Indian farmers. in AIP Conference Proceedings vol. 2148 (AIP Publishing, 2019).
Tian, F. An agri-food supply chain traceability system for China based on RFID & blockchain technology. in 2016 13th international conference on service systems and service management (ICSSSM) 1–6 (IEEE, 2016).
Yadav, V. S. & Singh, A. R. A systematic literature review of blockchain technology in agriculture. in Proceedings of the international conference on industrial engineering and operations management 973–981 (IEOM Society International Southfield, MI, USA, 2019).
Cole, R., Stevenson, M. & Aitken, J. Blockchain technology: implications for operations and supply chain management. Supply Chain Manag. Int. J. 24 , 469–483 (2019).
Wang, B., Luo, W., Zhang, A., Tian, Z. & Li, Z. Blockchain-enabled circular supply chain management: A system architecture for fast fashion. Comput. Ind. 123 , 103324 (2020).
Mohanta, B. K., Jena, D., Panda, S. S. & Sobhanayak, S. Blockchain technology: A survey on applications and security privacy Challenges. Internet Things 8 , 100107 (2019).
Lu, Y. The blockchain: State-of-the-art and research challenges. J. Ind. Inf. Integr. 15 , 80–90 (2019).
Google Scholar
Reyna, A., Martín, C., Chen, J., Soler, E. & Díaz, M. On blockchain and its integration with IoT. Challenges and opportunities. Future Gener. Comput. Syst. 88 , 173–190 (2018).
Kamilaris, A., Fonts, A. & Prenafeta-Boldύ, F. X. The rise of blockchain technology in agriculture and food supply chains. Trends Food Sci. Technol. 91 , 640–652 (2019).
Kamble, S. S., Gunasekaran, A. & Sharma, R. Modeling the blockchain enabled traceability in agriculture supply chain. Int. J. Inf. Manag. 52 , 101967 (2020).
Galvez, J. F., Mejuto, J. C. & Simal-Gandara, J. Future challenges on the use of blockchain for food traceability analysis. TrAC Trends Anal. Chem. 107 , 222–232 (2018).
Thakur, V., Doja, M. N., Dwivedi, Y. K., Ahmad, T. & Khadanga, G. Land records on blockchain for implementation of land titling in India. Int. J. Inf. Manag. 52 , 101940 (2020).
Pedroza-Gutiérrez, C. & Hernández, J. M. Social networks and supply chain management in fish trade. Sage Open 10 , 2158244020931815 (2020).
Lin, C.-F. Blockchainizing food law: Implications for food safety, traceability, and sustainability. in Conference on Food Law and Policy: Food Safety and Technology Governance, Taipei (2019).
Clohessy, T., Treiblmaier, H., Acton, T. & Rogers, N. Antecedents of blockchain adoption: An integrative framework. Strateg. Change 29 , 501–515 (2020).
Oliveira, T. & Martins, M. F. Literature review of information technology adoption models at firm level. Electron. J. Inf. Syst. Eval. 14 , 110–121 (2011).
Katiyar, R., Barua, M. K. & Meena, P. L. Analysing the interactions among the barriers of supply chain performance measurement: an ISM with fuzzy MICMAC approach. Glob. Bus. Rev. 19 , 48–68 (2018).
Sufiyan, M., Haleem, A., Khan, S. & Khan, M. I. Evaluating food supply chain performance using hybrid fuzzy MCDM technique. Sustain. Prod. Consum. 20 , 40–57 (2019).
Ju-Long, D. Control problems of grey systems. Syst. Control Lett. 1 , 288–294 (1982).
Yang, Z., Guo, X., Sun, J. & Zhang, Y. Contextual and organizational factors in sustainable supply chain decision making: Grey relational analysis and interpretative structural modeling. Environ. Dev. Sustain. 23 , 12056–12076 (2021).
Singh, R., Khan, S. & Dsilva, J. A framework for assessment of critical factor for circular economy practice implementation. J. Model. Manag. 18 , 1476–1497 (2023).
Dalkey, N. & Helmer, O. An experimental application of the Delphi method to the use of experts. Manag. Sci. 9 , 458–467 (1963).
Khan, S., Haleem, A. & Khan, M. I. Risk management in Halal supply chain: an integrated fuzzy Delphi and DEMATEL approach. J. Model. Manag. 16 , 172–214 (2021).
Iansiti, M. & Lakhani, K. R. The truth about blockchain. Harv. Bus. Rev. 95 , 118–127 (2017).
Lone, A. H. & Naaz, R. Applicability of Blockchain smart contracts in securing Internet and IoT: A systematic literature review. Comput. Sci. Rev. 39 , 100360 (2021).
Tsang, Y. P. et al. An Internet of Things (IoT)-based risk monitoring system for managing cold supply chain risks. Ind. Manag. Data Syst. 118 , 1432–1462 (2018).
Saberi, S., Kouhizadeh, M. & Sarkis, J. Blockchain technology: A panacea or pariah for resources conservation and recycling?. Resour. Conserv. Recycl. 130 , 80–81 (2018).
Kamilaris, A. & Prenafeta-Boldú, F. X. Deep learning in agriculture: A survey. Comput. Electron. Agric. 147 , 70–90 (2018).
Rana, R. L., Tricase, C. & De Cesare, L. Blockchain technology for a sustainable agri-food supply chain. Br. Food J. 123 , 3471–3485 (2021).
Teodorescu, M. & Korchagina, E. Applying blockchain in the modern supply chain management: Its implication on open innovation. J. Open Innov. Technol. Mark. Complex. 7 , 80 (2021).
Yadav, V. S., Singh, A. R., Raut, R. D. & Govindarajan, U. H. Blockchain technology adoption barriers in the Indian agricultural supply chain: an integrated approach. Resour. Conserv. Recycl. 161 , 104877 (2020).
Biswas, B. & Gupta, R. Analysis of barriers to implement blockchain in industry and service sectors. Comput. Ind. Eng. 136 , 225–241 (2019).
Wang, Y., Singgih, M., Wang, J. & Rit, M. Making sense of blockchain technology: How will it transform supply chains?. Int. J. Prod. Econ. 211 , 221–236 (2019).
Morkunas, V. J., Paschen, J. & Boon, E. How blockchain technologies impact your business model. Bus. Horiz. 62 , 295–306 (2019).
Boutkhoum, O. et al. Analysis and evaluation of barriers influencing blockchain implementation in Moroccan sustainable supply chain management: an integrated IFAHP-DEMATEL framework. Mathematics 9 , 1601 (2021).
Khan, S., Haleem, A. & Khan, M. I. A grey-based framework for circular supply chain management: A forward step towards sustainability. Manag. Environ. Qual. Int. J. 33 , 1476–1501 (2022).
Mangla, S. K. et al. Barriers to effective circular supply chain management in a developing country context. Prod. Plan. Control 29 , 551–569 (2018).
Zheng, Z., Xie, S., Dai, H.-N., Chen, X. & Wang, H. Blockchain challenges and opportunities: A survey. Int. J. Web Grid Serv. 14 , 352–375 (2018).
Falcone, E. C., Steelman, Z. R. & Aloysius, J. A. Understanding managers’ reactions to blockchain technologies in the supply chain: The reliable and unbiased software agent. J. Bus. Logist. 42 , 25–45 (2021).
Kurpjuweit, S., Schmidt, C. G., Klöckner, M. & Wagner, S. M. Blockchain in additive manufacturing and its impact on supply chains. J. Bus. Logist. 42 , 46–70 (2021).
Lacity, M. C. Addressing key challenges to making enterprise blockchain applications a reality. MIS Q. Exec. 17 , 201–222 (2018).
Wang, Y., Han, J. H. & Beynon-Davies, P. Understanding blockchain technology for future supply chains: A systematic literature review and research agenda. Supply Chain Manag. Int. J. 24 , 62–84 (2018).
OuYang, X., Zhu, X., Ye, L. & Yao, J. Preliminary applications of blockchain technique in large consumers direct power trading. Proc. CSEE 37 , 3737–3745 (2017).
Kumar, S. et al. Integrated blockchain and internet of things in the food supply chain: Adoption barriers. Technovation 118 , 102589 (2022).
Chen, Z. & Pak, M. A Delphi analysis on green performance evaluation indices for ports in China. Marit. Policy Manag. 44 , 537–550 (2017).
Vuran, M. C., Salam, A., Wong, R. & Irmak, S. Internet of underground things in precision agriculture: Architecture and technology aspects. Ad Hoc Netw. 81 , 160–173 (2018).
Si, S.-L., You, X.-Y., Liu, H.-C. & Zhang, P. DEMATEL technique: A systematic review of the state-of-the-art literature on methodologies and applications. Math. Probl. Eng. 2018 , e3696457 (2018).
Hori, S. & Shimizu, Y. Designing methods of human interface for supervisory control systems. Control Eng. Pract. 7 , 1413–1419 (1999).
Feng, Q., He, D., Zeadally, S., Khan, M. K. & Kumar, N. A survey on privacy protection in blockchain system. J. Netw. Comput. Appl. 126 , 45–58 (2019).
Download references
The authors would like to extend their sincere appreciation to the Researchers Supporting Project Number (RSPD2024R932), King Saud University, Riyadh, Saudi Arabia.
Author information
Authors and affiliations.
School of Economics, Shandong University of Technology, Zibo, Shandong, People’s Republic of China
Ubair Nisar, Zhixin Zhang & Ehsan Ellahi
College of Business and Economics, United Arab Emirates University, Al Ain, UAE
Bronwyn P. Wood
School of Mechanical Engineering, Shandong University of Technology, Zibo, China
Shadab Ahmad
College of Agricultural Engineering and Food Science, Shandong University of Technology, Zibo, China
Syed Ijaz Ul Haq
Department of Agricultural Economics, College of Food and Agricultural Sciences, King Saud University, P.O. Box. 2460, 11451, Riyadh, Saudi Arabia
Mohamad Alnafissa
Plant Production Department, College of Food and Agricultural Sciences, King Saud University, P.O. Box. 2460, 11451, Riyadh, Saudi Arabia
Elsayed Fathi Abd-Allah
You can also search for this author in PubMed Google Scholar
Contributions
All authors contributed to the study conception and design. Funding acquisition was managed by UN. Material preparation, data collection and analysis were performed by UN. Figures were designed in Adobe Illustrator by ZZ and BPW. The first draft of the manuscript was written by UN. BPW, SA and EE commented on previous versions of the manuscript. The funding was provided by E.F.A.. All authors read and approved the final manuscript.
Corresponding authors
Correspondence to Zhixin Zhang or Bronwyn P. Wood .
Ethics declarations
Competing interests.
The authors declare no competing interests.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Cite this article.
Nisar, U., Zhang, Z., Wood, B.P. et al. Unlocking the potential of blockchain technology in enhancing the fisheries supply chain: an exploration of critical adoption barriers in China. Sci Rep 14 , 10167 (2024). https://doi.org/10.1038/s41598-024-59167-4
Download citation
Received : 18 December 2023
Accepted : 08 April 2024
Published : 03 May 2024
DOI : https://doi.org/10.1038/s41598-024-59167-4
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Supply chain sustainability
- Critical barrier
By submitting a comment you agree to abide by our Terms and Community Guidelines . If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies
Sign up for the Nature Briefing: Anthropocene newsletter — what matters in anthropocene research, free to your inbox weekly.

IMAGES
VIDEO
COMMENTS
Examples of literature reviews. Step 1 - Search for relevant literature. Step 2 - Evaluate and select sources. Step 3 - Identify themes, debates, and gaps. Step 4 - Outline your literature review's structure. Step 5 - Write your literature review.
This is why the literature review as a research method is more relevant than ever. Traditional literature reviews often lack thoroughness and rigor and are conducted ad hoc, rather than following a specific methodology. Therefore, questions can be raised about the quality and trustworthiness of these types of reviews.
A literature review is an integrated analysis-- not just a summary-- of scholarly writings and other relevant evidence related directly to your research question.That is, it represents a synthesis of the evidence that provides background information on your topic and shows a association between the evidence and your research question.
Literature Review and Research Design by Dave Harris This book looks at literature review in the process of research design, and how to develop a research practice that will build skills in reading and writing about research literature--skills that remain valuable in both academic and professional careers. Literature review is approached as a process of engaging with the discourse of scholarly ...
In writing the literature review, your purpose is to convey to your reader what knowledge and ideas have been established on a topic, and what their strengths and weaknesses are. As a piece of writing, the literature review must be defined by a guiding concept (e.g., your research objective, the problem or issue you are discussing, or your ...
Literature reviews establish the foundation of academic inquires. However, in the planning field, we lack rigorous systematic reviews. In this article, through a systematic search on the methodology of literature review, we categorize a typology of literature reviews, discuss steps in conducting a systematic literature review, and provide suggestions on how to enhance rigor in literature ...
A literature review is an integral part of both research and education. It is the first and foremost step in research. There are different types of literature reviews with varying degrees of rigor in methodology, ranging from scoping reviews to systematic reviews.
Step One: Decide on your areas of research: Before you begin to search for articles or books, decide beforehand what areas you are going to research. Make sure that you only get articles and books in those areas, even if you come across fascinating books in other areas. A literature review I am currently working on, for example, explores ...
As mentioned above, writing your literature review is a process, which I'll break down into three steps: Finding the most suitable literature. Understanding, distilling and organising the literature. Planning and writing up your literature review chapter. Importantly, you must complete steps one and two before you start writing up your chapter.
Literature Review is a comprehensive survey of the works published in a particular field of study or line of research, usually over a specific period of time, in the form of an in-depth, critical bibliographic essay or annotated list in which attention is drawn to the most significant works. Also, we can define a literature review as the ...
A literature or narrative review is a comprehensive review and analysis of the published literature on a specific topic or research question. The literature that is reviewed contains: books, articles, academic articles, conference proceedings, association papers, and dissertations. It contains the most pertinent studies and points to important ...
How to complete a literature review. Fair Warning: The literature review is often time-consuming and can feel like an endless process. Don't Give Up! It is the first major hurdle of the research proposal process. Once you have completed the literature review, you will have a good idea of what is significant, relevant and novel about your ...
Abstract. Performing a literature review is a critical first step in research to understanding the state-of-the-art and identifying gaps and challenges in the field. A systematic literature review is a method which sets out a series of steps to methodically organize the review. In this paper, we present a guide designed for researchers and in ...
In the field of research, the term method represents the specific approaches and procedures that the researcher systematically utilizes that are manifested in the research design, sampling design, data collec-tion, data analysis, data interpretation, and so forth. The literature review represents a method because the literature reviewer chooses ...
This explicit methodology description is essential since many academic journals list SotA reviews as an accepted type of literature review. For instance, Educational Research Review , the American Academy of Pediatrics , and Thorax all lists SotA reviews as one of the types of knowledge syntheses they accept . However, while SotA reviews are ...
When seeking information for a literature review or for any purpose, it helps to understand information-seeking as a process that you can follow. 5 Each of the six (6) steps has its own section in this web page with more detail. Do (and re-do) the following six steps: 1. Define your topic.
Literature search. Fink has defined research literature review as a "systematic, explicit and reproducible method for identifying, evaluating, and synthesizing the existing body of completed and recorded work produced by researchers, scholars and practitioners."[]Review of research literature can be summarized into a seven step process: (i) Selecting research questions/purpose of the ...
Literature reviews allow scientists to argue that they are expanding current. expertise - improving on what already exists and filling the gaps that remain. This paper demonstrates the literatu ...
9.3. Types of Review Articles and Brief Illustrations. EHealth researchers have at their disposal a number of approaches and methods for making sense out of existing literature, all with the purpose of casting current research findings into historical contexts or explaining contradictions that might exist among a set of primary research studies conducted on a particular topic.
This. paper discusses literature review as a methodology for conducting research and o ffers an overview of different. types of reviews, as well as some guidelines to how to both conduct and ...
Image by TraceyChandler. Steps to conducting a systematic review. Quick overview of the process: Steps and resources from the UMB HSHSL Guide. YouTube video (26 min); Another detailed guide on how to conduct and write a systematic review from RMIT University; A roadmap for searching literature in PubMed from the VU Amsterdam; Alexander, P. A. (2020).
Method details Overview. A Systematic Literature Review (SLR) is a research methodology to collect, identify, and critically analyze the available research studies (e.g., articles, conference proceedings, books, dissertations) through a systematic procedure [12].An SLR updates the reader with current literature about a subject [6].The goal is to review critical points of current knowledge on a ...
Recent advancements in manual sampling and mapping methods of LCZs reviews the progress of LCZs research methods applied in UHI research. ... method comprises six main steps, ... Literature Review ...
In accordance with the guidelines proposed by , this review incorporates the following steps: (1) Define research questions; (2) Establish search process; (3) Determine criteria for text selection; (4) Execute analysis and classification of selected texts. The subsequent subsections will detail these processes.
Reasons for inclusion and exclusion should be recorded. Step 3: Assessing the quality of studies. Study quality assessment is relevant to every step of a review. Question formulation (Step 1) and study selection criteria (Step 2) should describe the minimum acceptable level of design.
Our research contributes by systematically identifying and categorizing fourteen specific Critical Barrier Factors (CBFs) through an extensive literature review and the use of the grey Delphi method.