Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
- Explore content
- About the journal
- Publish with us
- Sign up for alerts
- Open access
- Published: 17 May 2023

A holistic and proactive approach to forecasting cyber threats
- Zaid Almahmoud 1 ,
- Paul D. Yoo 1 ,
- Omar Alhussein 2 ,
- Ilyas Farhat 3 &
- Ernesto Damiani 4 , 5
Scientific Reports volume 13 , Article number: 8049 ( 2023 ) Cite this article
5583 Accesses
9 Citations
2 Altmetric
Metrics details
- Computer science
- Information technology
Traditionally, cyber-attack detection relies on reactive, assistive techniques, where pattern-matching algorithms help human experts to scan system logs and network traffic for known virus or malware signatures. Recent research has introduced effective Machine Learning (ML) models for cyber-attack detection, promising to automate the task of detecting, tracking and blocking malware and intruders. Much less effort has been devoted to cyber-attack prediction, especially beyond the short-term time scale of hours and days. Approaches that can forecast attacks likely to happen in the longer term are desirable, as this gives defenders more time to develop and share defensive actions and tools. Today, long-term predictions of attack waves are mostly based on the subjective perceptiveness of experienced human experts, which can be impaired by the scarcity of cyber-security expertise. This paper introduces a novel ML-based approach that leverages unstructured big data and logs to forecast the trend of cyber-attacks at a large scale, years in advance. To this end, we put forward a framework that utilises a monthly dataset of major cyber incidents in 36 countries over the past 11 years, with new features extracted from three major categories of big data sources, namely the scientific research literature, news, blogs, and tweets. Our framework not only identifies future attack trends in an automated fashion, but also generates a threat cycle that drills down into five key phases that constitute the life cycle of all 42 known cyber threats.
Similar content being viewed by others
Detecting hallucinations in large language models using semantic entropy
Deep-learning-enabled antibiotic discovery through molecular de-extinction

Highly accurate protein structure prediction with AlphaFold
Introduction.
Running a global technology infrastructure in an increasingly de-globalised world raises unprecedented security issues. In the past decade, we have witnessed waves of cyber-attacks that caused major damage to governments, organisations and enterprises, affecting their bottom lines 1 . Nevertheless, cyber-defences remained reactive in nature, involving significant overhead in terms of execution time. This latency is due to the complex pattern-matching operations required to identify the signatures of polymorphic malware 2 , which shows different behaviour each time it is run. More recently, ML-based models were introduced relying on anomaly detection algorithms. Although these models have shown a good capability to detect unknown attacks, they may classify benign behaviour as abnormal 3 , giving rise to a false alarm.
We argue that data availability can enable a proactive defense, acting before a potential threat escalates into an actual incident. Concerning non-cyber threats, including terrorism and military attacks, proactive approaches alleviate, delay, and even prevent incidents from arising in the first place. Massive software programs are available to assess the intention, potential damages, attack methods, and alternative options for a terrorist attack 4 . We claim that cyber-attacks should be no exception, and that nowadays we have the capabilities to carry out proactive, low latency cyber-defenses based on ML 5 .
Indeed, ML models can provide accurate and reliable forecasts. For example, ML models such as AlphaFold2 6 and RoseTTAFold 7 can predict a protein’s three-dimensional structure from its linear sequence. Cyber-security data, however, poses its unique challenges. Cyber-incidents are highly sensitive events and are usually kept confidential since they affect the involved organisations’ reputation. It is often difficult to keep track of these incidents, because they can go unnoticed even by the victim. It is also worth mentioning that pre-processing cyber-security data is challenging, due to characteristics such as lack of structure, diversity in format, and high rates of missing values which distort the findings.
When devising a ML-based method, one can rely on manual feature identification and engineering, or try and learn the features from raw data. In the context of cyber-incidents, there are many factors ( i.e. , potential features) that could lead to the occurrence of an attack. Wars and political conflicts between countries often lead to cyber-warfare 8 , 9 . The number of mentions of a certain attack appearing in scientific articles may correlate well with the actual incident rate. Also, cyber-attacks often take place on holidays, anniversaries and other politically significant dates 5 . Finding the right features out of unstructured big data is one of the key strands of our proposed framework.
The remainder of the paper is structured as follows. The “ Literature review ” section presents an overview of the related work and highlights the research gaps and our contributions. The “ Methods ” section describes the framework design, including the construction of the dataset and the building of the model. The “ Results ” section presents the validation results of our model, the trend analysis and forecast, and a detailed description of the developed threat cycle. Lastly, the “ Discussion ” section offers a critical evaluation of our work, highlighting its strengths and limitations, and provides recommendations for future research.
Literature review
In recent years, the literature has extensively covered different cyber threats across various application domains, and researchers have proposed several solutions to mitigate these threats. In the Social Internet of Vehicles (SIoV), one of the primary concerns is the interception and tampering of sensitive information by attackers 10 . To address this, a secure authentication protocol has been proposed that utilises confidential computing environments to ensure the privacy of vehicle-generated data. Another application domain that has been studied is the privacy of image data, specifically lane images in rural areas 11 . The proposed methodology uses Error Level Analysis (ELA) and artificial neural network (ANN) algorithms to classify lane images as genuine or fake, with the U-Net model for lane detection in bona fide images. The final images are secured using the proxy re-encryption technique with RSA and ECC algorithms, and maintained using fog computing to protect against forgery.
Another application domain that has been studied is the security of Wireless Mesh Networks (WMNs) in the context of the Internet of Things (IoT) 12 . WMNs rely on cooperative forwarding, making them vulnerable to various attacks, including packet drop/modification, badmouthing, on-off, and collusion attacks. To address this, a novel trust mechanism framework has been proposed that differentiates between legitimate and malicious nodes using direct and indirect trust computation. The framework utilises a two-hop mechanism to observe the packet forwarding behaviour of neighbours, and a weighted D-S theory to aggregate recommendations from different nodes. While these solutions have shown promising results in addressing cyber threats, it is important to anticipate the type of threat that may arise to ensure that the solutions can be effectively deployed. By proactively identifying and anticipating cyber threats, organisations can better prepare themselves to protect their systems and data from potential attacks.
While we are relatively successful in detecting and classifying cyber-attacks when they occur 13 , 14 , 15 , there has been a much more limited success in predicting them. Some studies exist on short-term predictive capability 16 , 17 , 18 , 19 , 20 , 21 , 22 , 23 , 24 , 25 , 26 , such as predicting the number or source of attacks to be expected in the next hours or days. The majority of this work performs the prediction in restricted settings ( e.g. , against a specific entity or organisation) where historical data are available 18 , 19 , 25 . Forecasting attack occurrences has been attempted by using statistical methods, especially when parametric data distributions could be assumed 16 , 17 , as well as by using ML models 20 . Other methods adopt a Bayesian setting and build event graphs suitable for estimating the conditional probability of an attack following a given chain of events 21 . Such techniques rely on libraries of predefined attack graphs: they can identify the known attack most likely to happen, but are helpless against never-experienced-before, zero-day attacks.
Other approaches try to identify potential attackers by using network entity reputation and scoring 26 . A small but growing body of research explores the fusion of heterogeneous features (warning signals) to forecast cyber-threats using ML. Warning signs may include the number of mentions of a victim organisation on Twitter 18 , mentions in news articles about the victim entity 19 , and digital traces from dark web hacker forums 20 . Our literature review is summarised in Table 1 .
Forecasting the cyber-threats that will most likely turn into attacks in the medium and long term is of significant importance. It not only gives to cyber-security agencies the time to evaluate the existing defence measures, but also assists them in identifying areas where to develop preventive solutions. Long-term prediction of cyber-threats, however, still relies on the subjective perceptions of human security experts 27 , 28 . Unlike a fully automated procedure based on quantitative metrics, the human-based approach is prone to bias based on scientific or technical interests 29 . Also, quantitative predictions are crucial to scientific objectivity 30 . In summary, we highlight the following research gaps:
Current research primarily focuses on detecting ( i.e. , reactive) rather than predicting cyber-attacks ( i.e. , proactive).
Available predictive methods for cyber-attacks are mostly limited to short-term predictions.
Current predictive methods for cyber-attacks are limited to restricted settings ( e.g. , a particular network or system).
Long-term prediction of cyber-attacks is currently performed by human experts, whose judgement is subjective and prone to bias and disagreement.
Research contributions
Our objective is to fill these research gaps by a proactive, long-term, and holistic approach to attack prediction. The proposed framework gives cyber-security agencies sufficient time to evaluate existing defence measures while also providing objective and accurate representation of the forecast. Our study is aimed at predicting the trend of cyber-attacks up to three years in advance, utilising big data sources and ML techniques. Our ML models are learned from heterogeneous features extracted from massive, unstructured data sources, namely, Hackmageddon 9 , Elsevier 31 , Twitter 32 , and Python APIs 33 . Hackmageddon provides more than 15, 000 records of global cyber-incidents since the year 2011, while Elsevier API offers access to the Scopus database, the largest abstract and citation database of peer-reviewed literature with over 27,000,000 documents 34 . The number of relevant tweets we collected is around 9 million. Our study covers 36 countries and 42 major attack types. The proposed framework not only provides the forecast and categorisation of the threats, but also generates a threat life-cycle model, whose the five key phases underlie the life cycle of all 42 known cyber-threats. The key contribution of this study consists of the following:
A novel dataset is constructed using big unstructured data ( i.e. , Hackmageddon) including news and government advisories, in addition to Elsevier, Twitter, and Python API. The dataset comprises monthly counts of cyber-attacks and other unique features, covering 42 attack types across 36 countries.
Our proactive approach offers long-term forecasting by predicting threats up to 3 years in advance.
Our approach is holistic in nature, as it does not limit itself to specific entities or regions. Instead, it provides projections of attacks across 36 countries situated in diverse parts of the world.
Our approach is completely automated and quantitative, effectively addressing the issue of bias in human predictions and providing a precise forecast.
By analysing past and predicted future data, we have classified threats into four main groups and provided a forecast of 42 attacks until 2025.
The first threat cycle is proposed, which delineates the distinct phases in the life cycle of 42 cyber-attack types.
The framework of forecasting cyber threats
The architecture of our framework for forecasting cyber threats is illustrated in Fig. 1 . As seen in the Data Sources component (l.h.s), to harness all the relevant data and extract meaningful insights, our framework utilises various sources of unstructured data. One of our main sources is Hackmageddon, which includes massive textual data on major cyber-attacks (approx. 15,334 incidents) dating back to July 2011. We refer to the monthly number of attacks in the list as the Number of Incidents (NoI). Also, Elsevier’s Application Programming Interface (API) gives access to a very large corpus of scientific articles and data sets from thousands of sources. Utilising this API, we obtained the Number of Mentions (NoM) ( e.g. , monthly) of each attack that appeared in the scientific publications. This NoM data is of particular importance as it can be used as the ground truth for attack types that do not appear in Hackmageddon. During the preliminary research phase, we examined all the potentially relevant features and noticed that wars/political conflicts are highly correlated to the number of cyber-events. These data were then extracted via Twitter API as Armed Conflict Areas/Wars (ACA). Lastly, as attacks often take place around holidays, Python’s holidays package was used to obtain the number of public holidays per month for each country, which is referred to as Public Holidays (PH).
To ensure the accuracy and quality of Hackmageddon data, we validated it using the statistics from official sources across government, academia, research institutes and technology organisations. For a ransomware example, the Cybersecurity & Infrastructure Security Agency stated in their 2021 trend report that cybersecurity authorities in the United States, Australia, and the United Kingdom observed an increase in sophisticated, high-impact ransomware incidents against critical infrastructure organisations globally 35 . The WannaCry attack in the dataset was also validated with Ghafur et al ’s 1 statement in their article: “WannaCry ransomware attack was a global epidemic that took place in May 2017”.
An example of an entry in the Hackmageddon dataset is shown in Table 2 . Each entry includes the incident date, the description of the attack, the attack type, and the target country. Data pre-processing (Fig. 1 ) focused on noise reduction through imputing missing values ( e.g. , countries), which were often observed in the earlier years. We were able to impute these values from the description column or occasionally, by looking up the entity location using Google.
The textual data were quantified via our Word Frequency Counter (WFC), which counted the number of each attack type per month as in Table 3 . Cumulative Aggregation (CA) obtained the number of attacks for all countries combined and an example of a data entry after transformation includes the month, and the number of attacks against each country (and all countries combined) for each attack type. By adding features such as NoM, ACA, and PH, we ended up having additional features that we appended to the dataset as shown in Table 4 . Our final dataset covers 42 common types of attacks in 36 countries. The full list of attacks is provided in Table 5 . The list of the countries is given in Supplementary Table S1 .
To analyse and investigate the main characteristics of our data, an exploratory analysis was conducted focusing on the visualisation and identification of key patterns such as trend and seasonality, correlated features, missing data and outliers. For seasonal data, we smoothed out the seasonality so that we could identify the trend while removing the noise in the time series 36 . The smoothing type and constants were optimised along with the ML model (see Optimisation for details). We applied Stochastic selection of Features (SoF) to find the subset of features that minimises the prediction error, and compared the univariate against the multivariate approach.
For the modelling, we built a Bayesian encoder-decoder Long Short-Term Memory (B-LSTM) network. B-LSTM models have been proposed to predict “perfect wave” events like the onset of stock market “bear” periods on the basis of multiple warning signs, each having different time dynamics 37 . Encoder-decoder architectures can manage inputs and outputs that both consist of variable-length sequences. The encoder stage encodes a sequence into a fixed-length vector representation (known as the latent representation). The decoder prompts the latent representation to predict a sequence. By applying an efficient latent representation, we train the model to consider all the useful warning information from the input sequence - regardless of its position - and disregard the noise.
Our Bayesian variation of the encoder-decoder LSTM network considers the weights of the model as random variables. This way, we extract epistemic uncertainty via (approximate) Bayesian inference, which quantifies the prediction error due to insufficient information 38 . This is an important parameter, as epistemic uncertainty can be reduced by better intelligence, i.e. , by acquiring more samples and new informative features. Details are provided in “ Bayesian long short-term memory ” section.
Our overall analytical platform learns an operational model for each attack type. Here, we evaluated the model’s performance in predicting the threat trend 36 months in advance. A newly modified symmetric Mean Absolute Percentage Error (M-SMAPE) was devised as the evaluation metric, where we added a penalty term that accounts for the trend direction. More details are provided in the “ Evaluation metrics ” section.
Feature extraction
Below, we provide the details of the process that transforms raw data into numerical features, obtaining the ground truth NoI and the additional features NoM, ACA and PH.
NoI: The number of daily incidents in Hackmageddon was transformed from the purely unstructured daily description of attacks along with the attack and country columns, to the monthly count of incidents for each attack in each country. Within the description, multiple related attacks may appear, which are not necessarily in the attack column. Let \(E_{x_i}\) denote the set of entries during the month \(x_i\) in Hackmageddon dataset. Let \(a_j\) and \(c_k\) denote the j th attack and k th country. Then NoI can be expressed as follows:
where \(Z(a_j,c_k,e)\) is a function that evaluates to 1 if \(a_j\) appears either in the description or in the attack columns of entry e and \(c_k\) appears in the country column of e . Otherwise, the function evaluates to 0. Next, we performed CA to obtain the monthly count of attacks in all countries combined for each attack type as follows:
NoM: We wrote a Python script to query Elsevier API for the number of mentions of each attack during each month 31 . The search covers the title, abstract and keywords of published research papers that are stored in Scopus database 39 . Let \(P_{x_i}\) denote the set of research papers in Scopus published during the month \(x_i\) . Also, let \(W_{p}\) denote the set of words in the title, abstract and keywords of research paper p . Then NoM can be expressed as follows:
where \(U(w,a_j)\) evaluates to 1 if \(w=a_j\) , and to 0 otherwise.
ACA: Using Twitter API in Python 32 , we wrote a query to obtain the number of tweets with keywords related to political conflicts or military attacks associated with each country during each month. The keywords used for each country are summarised in Supplementary Table S2 , representing our query. Formally, let \(T_{x_i}\) denote the set of all tweets during the month \(x_i\) . Then ACA can be expressed as follows:
where \(Q(t,c_k)\) evaluates to 1 if the query in Supplementary Table S2 evaluates to 1 given t and \(c_k\) . Otherwise, it evaluates to 0.
PH: We used the Python holidays library 33 to count the number of days that are considered public holidays in each country during each month. More formally, this can be expressed as follows:
where \(H(d,c_k)\) evaluates to 1 if the day d in the country \(c_k\) is a public holiday, and to 0 otherwise. In ( 4 ) and ( 5 ), CA was used to obtain the count for all countries combined as in ( 2 ).
Data integration
Based on Eqs. ( 1 )–( 5 ), we obtain the following columns for each month:
NoI_C: The number of incidents for each attack type in each country ( \(42 \times 36\) columns) [Hackmageddon].
NoI: The total number of incidents for each attack type (42 columns) [Hackmageddon].
NoM: The number of mentions of each attack type in research articles (42 columns) [Elsevier].
ACA_C: The number of tweets about wars and conflicts related to each country (36 columns) [Twitter].
ACA: The total number of tweets about wars and conflicts (1 column) [Twitter].
PH_C: The number of public holidays in each country (36 columns) [Python].
PH: The total number of public holidays (1 column) [Python].
In the aforementioned list of columns, the name enclosed within square brackets denotes the source of data. By matching and combining these columns, we derive our monthly dataset, wherein each row represents a distinct month. A concrete example can be found in Tables 3 and 4 , which, taken together, constitute a single observation in our dataset. The dataset can be expanded through the inclusion of other monthly features as supplementary columns. Additionally, the dataset may be augmented with further samples as additional monthly records become available. Some suggestions for extending the dataset are provided in the “ Discussion ” section.
Data smoothing
We tested multiple smoothing methods and selected the one that resulted in the model with the lowest M-SMAPE during the hyper-parameter optimisation process. The methods we tested include exponential smoothing (ES), double exponential smoothing (DES) and no smoothing (NS). Let \(\alpha \) be the smoothing constant. Then the ES formula is:
where \(D(x_{i})\) denotes the original data at month \(x_{i}\) . For the DES formula, let \(\alpha \) and \(\beta \) be the smoothing constants. We first define the level \(l(x_{i})\) and the trend \(\tau (x_{i})\) as follows:
then, DES is expressed as follows:
The smoothing constants ( \(\alpha \) and \(\beta \) ) in the aforementioned methods are chosen as the predictive results of the ML model that gives the lowest M-SMAPE during the hyper-parameter optimisation process. Supplementary Fig. S5 depicts an example for the DES result.
Bayesian long short-term memory
LSTM is a type of recurrent neural network (RNN) that uses lagged observations to forecast the future time steps 30 . It was introduced as a solution to the so-called vanishing/exploding gradient problem of traditional RNNs 40 , where the partial derivative of the loss function may suddenly approach zero at some point of the training. In LSTM, the input is passed to the network cell, which combines it with the hidden state and cell state values from previous time steps to produce the next states. The hidden state can be thought of as a short-term memory since it stores information from recent periods in a weighted manner. On the other hand, the cell state is meant to remember all the past information from previous intervals and store them in the LSTM cell. The cell state thus represents the long-term memory.
LSTM networks are well-suited for time-series forecasting, due to their proficiency in retaining both long-term and short-term temporal dependencies 41 , 42 . By leveraging their ability to capture these dependencies within cyber-attack data, LSTM networks can effectively recognise recurring patterns in the attack time-series. Moreover, the LSTM model is capable of learning intricate temporal patterns in the data and can uncover inter-correlations between various variables, making it a compelling option for multivariate time-series analysis 43 .
Given a sequence of LSTM cells, each processing a single time-step from the past, the final hidden state is encoded into a fixed-length vector. Then, a decoder uses this vector to forecast future values. Using such architecture, we can map a sequence of time steps to another sequence of time steps, where the number of steps in each sequence can be set as needed. This technique is referred to as encoder-decoder architecture.
Because we have relatively short sequences within our refined data ( e.g. , 129 monthly data points over the period from July 2011 to March 2022), it is crucial to extract the source of uncertainty, known as epistemic uncertainty 44 , which is caused by lack of knowledge. In principle, epistemic uncertainty can be reduced with more knowledge either in the form of new features or more samples. Deterministic (non-stochastic) neural network models are not adequate to this task as they provide point estimates of model parameters. Rather, we utilise a Bayesian framework to capture epistemic uncertainty. Namely, we adopt the Monte Carlo dropout method proposed by Gal et al. 45 , who showed that the use of non-random dropout neurons during ML training (and inference) provides a Bayesian approximation of the deep Gaussian processes. Specifically, during the training of our LSTM encoder-decoder network, we applied the same dropout mask at every time-step (rather than applying a dropout mask randomly from time-step to time-step). This technique, known as recurrent dropout is readily available in Keras 46 . During the inference phase, we run trained model multiple times with recurrent dropout to produce a distribution of predictive results. Such prediction is shown in Fig. 4 .
Figure 2 shows our encoder-decoder B-LSTM architecture. The hidden state and cell state are denoted respectively by \(h_{i}\) and \(C_{i}\) , while the input is denoted by \(X_{i}\) . Here, the length of the input sequence (lag) is a hyper-parameter tuned to produce the optimal model, where the output is a single time-step. The number of cells ( i.e. , the depth of each layer) is tuned as a hyper-parameter in the range between 25 and 200 cells. Moreover, we used one or two layers, tuning the number of layers to each attack type. For the univariate model we used a standard Rectified Linear Unit (ReLU) activation function, while for the multivariate model we used a Leaky ReLU. Standard ReLU computes the function \(f(x)=max(0,x)\) , thresholding the activation at zero. In the multivariate case, zero-thresholding may generate the same ReLU output for many input vectors, making the model convergence slower 47 . With Leaky ReLU, instead of defining ReLU as zero when \(x < 0\) , we introduce a negative slope \(\alpha =0.2\) . Additionally, we used recurrent dropout ( i.e. , arrows in red as shown in Fig. 2 ), where the probability of dropping out is another hyper-parameter that we tune as described above, following Gal’s method 48 . The tuned dropout value is maintained during the testing and prediction as previously mentioned. Once the final hidden vector \(h_{0}\) is produced by the encoder, the Repeat Vector layer is used as an adapter to reshape it from the bi-dimensional output of the encoder ( e.g. , \(h_{0}\) ) to the three-dimensional input expected by the decoder. The decoder processes the input and produces the hidden state, which is then passed to a dense layer to produce the final output.
Each time-step corresponds to a month in our model. Since the model is learnt to predict a single time-step (single month), we use a sliding window during the prediction phase to forecast 36 (monthly) data points. In other words, we predict a single month at each step, and the predicted value is fed back for the prediction of the following month. This concept is illustrated in the table shown in Fig. 2 . Utilising a single time-step in the model’s output minimises the size of the sliding window, which in turn allows for training with as many observations as possible with such limited data.
The difference between the univariate and multivariate B-LSTMs is that the latter carries additional features in each time-step. Thus, instead of passing a scalar input value to the network, we pass a vector of features including the ground truth at each time-step. The model predicts a vector of features as an output, from which we retrieve the ground truth, and use it along with the other predicted features as an input to predict the next time-step.
Evaluation metrics
The evaluation metric SMAPE is a percentage (or relative) error based accuracy measure that judges the prediction performance purely on how far the predicted value is from the actual value 49 . It is expressed by the following formula:
where \(F_{t}\) and \(A_{t}\) denote the predicted and actual values at time t . This metric returns a value between 0% and 100%. Given that our data has zero values in some months ( e.g. , emerging threats), the issue of division by zero may arise, a problem that often emerges when using standard MAPE (Mean Absolute Percentage Error). We find SMAPE to be resilient to this problem, since it has both the actual and predicted values in the denominator.
Recall that our model aims to predict a curve (corresponding to multiple time steps). Using plain SMAPE as the evaluation metric, the “best” model may turn out to be simply a straight line passing through the same points of the fluctuating actual curve. However, this is undesired in our case since our priority is to predict the trend direction (or slope) over its intensity or value at a certain point. We hence add a penalty term to SMAPE that we apply when the height of the predicted curve is relatively smaller than that of the actual curve. This yields the modified SMAPE (M-SMAPE). More formally, let I ( V ) be the height of the curve V , calculated as follows:
where n is the curve width or the number of data points. Let A and F denote the actual and predicted curves. We define M-SMAPE as follows:
where \(\gamma \) is a penalty constant between 0 and 1, and d is another constant \(\ge \) 1. In our experiment, we set \(\gamma \) to 0.3, and d to 3, as we found these to be reasonable values by trial and error. We note that the range of possible values of M-SMAPE is between 0% and (100 + 100 \(\gamma \) )% after this modification. By running multiple experiments we found out that the modified evaluation metric is more suitable for our scenario, and therefore was adopted for the model’s evaluation.
Optimisation
On average, our model was trained on around 67% of the refined data, which is equivalent to approximately 7.2 years. We kept the rest, approximately 33% (3 years + lag period), for validation. These percentages may slightly differ for different attack types depending on the optimal lag period selected.
For hyper-parameter optimisation, we performed a random search with 60 iterations, to obtain the set of features, smoothing methods and constants, and model’s hyper-parameters that results in the model with the lowest M-SMAPE. Random search is a simple and efficient technique for hyper-parameter optimisation, with advantages including efficiency, flexibility, robustness, and scalability. The technique has been studied extensively in the literature and was found to be superior to grid search in many cases 50 . For each set of hyper-parameters, the model was trained using the mean squared error (MSE) as the loss function, and while using ADAM as the optimisation algorithm 51 . Then, the model was validated by forecasting 3 years while using M-SMAPE as the evaluation metric, and the average performance was recorded over 3 different seeds. Once the set of hyper-parameters with the minimum M-SMAPE was obtained, we used it to train the model on the full data, after which we predicted the trend for the next 3 years (until March, 2025).
The first group of hyper-parameters is the subset of features in the case of the multivariate model. Here, we experimented with each of the 3 features separately (NoM, ACA or PH) along with the ground truth (NoI), in addition to the combination of all features. The second group is the smoothing methods and constants. The set of methods includes ES, DES and NS, as previously discussed. The set of values for the smoothing constant \(\alpha \) ranges from 0.05 to 0.7 while the set of values for the smoothing constant \(\beta \) (for DES) ranges from 0.3 to 0.7. Next is the optimisation of the lag period with values that range from 1 to 12 months. This is followed by the model’s hyper-parameters which include the learning rate with values that range from \(6\times 10^{-4}\) to \(1\times 10^{-2}\) , the number of epochs with values between 30 and 200, the number of layers in the range 1 to 2, the number of units in the range 25 to 200, and the recurrent dropout value between 0.2 and 0.5. The range of these values was obtained from the literature and the online code repositories 52 .
Validation and comparative analysis
The results of our model’s validation are provided in Fig. 3 and Table 5 . As shown in Fig. 3 , the predicted data points are well aligned with the ground truth. Our models successfully predicted the next 36 months of all the attacks’ trends with an average M-SMAPE of 0.25. Table 5 summarises the validation results of univariate and multivariate approaches using B-LSTM. The results show that with approximately 69% of all the attack types, the multivariate approach outperformed the univariate approach. As seen in Fig. 3 , the threats that have a consistent increasing or emerging trend seemed to be more suitable for the univariate approach, while threats that have a fluctuating or decreasing trend showed less validation error when using the multivariate approach. The feature of ACA resulted in the best model for 33% of all the attack types, which makes it among the three most informative features that can boost the prediction performance. The PH accounts for 17% of all the attacks followed by NoM that accounts for 12%.
We additionally compared the performance of the proposed model B-LSTM with other models namely LSTM and ARIMA. The comparison covers the univariate and multivariate approaches of LSTM and B-LSTM, with two features in the case of multivariate approach namely NoI and NoM. The comparison is in terms of the Mean Absolute Percentage Error (MAPE) when predicting four common attack types, namely DDoS, Password Attack, Malware, and Ransomware. A comparison table is provided in Supplementary Table S3 . The results illustrate the superiority of the B-LSTM model for most of the attack types.
Trends analysis
The forecast of each attack trend until the end of the first quarter of 2025 is given in Supplementary Figs. S1 – S4 . By visualising the historical data of each attack as well as the prediction for the next three years, we were able to analyse the overall trend of each attack. The attacks generally follow 4 types of trends: (1) rapidly increasing, (2) overall increasing, (3) emerging and (4) decreasing. The names of attacks for each category are provided in Fig. 4 .
The first trend category is the rapidly increasing trend (Fig. 4 a—approximately 40% of the attacks belong to this trend. We can see that the attacks belonging to this category have increased dramatically over the past 11 years. Based on the model’s prediction, some of these attacks will exhibit a steep growth until 2025. Examples include session hijacking, supply chain, account hijacking, zero-day and botnet. Some of the attacks under this category have reached their peak, have recently started stabilising, and will probably remain steady over the next 3 years. Examples include malware, targeted attack, dropper and brute force attack. Some attacks in this category, after a recent increase, are likely to level off in the next coming years. These are password attack, DNS spoofing and vulnerability-related attacks.
The second trend category is the overall increasing trend as seen in Fig. 4 b. Approximately 31% of the attacks seem to follow this trend. The attacks under this category have a slower rate of increase over the years compared to the attacks in the first category, with occasional fluctuations as can be observed in the figure. Although some of the attacks show a slight recent decline ( e.g. , malvertising, keylogger and URL manipulation), malvertising and keylogger are likely to recover and return to a steady state while URL manipulation is projected to continue a smooth decline. Other attacks typical of “cold” cyber-warfare like Advanced Persistent Threats (APT) and rootkits are already recovering from a small drop and will likely to rise to a steady state by 2025. Spyware and data breach have already reached their peak and are predicted to decline in the near future.
Next is the emerging trend as shown in Fig. 4 c. These are the attacks that started to grow significantly after the year 2016, although many of them existed much earlier. In our study, around 17% of the attacks follow this trend. Some attacks have been growing steeply and are predicted to continue this trend until 2025. These are Internet of Things (IoT) device attack and deepfake. Other attacks have also been increasing rapidly since 2016, however, are likely to slow down after 2022. These include ransomware and adversarial attacks. Interestingly, some attacks that emerged after 2016 have already reached the peak and recently started a slight decline ( e.g. , cryptojacking and WannaCry ransomware attack). It is likely that WannaCry will become relatively steady in the coming years, however, cryptojacking will probably continue to decline until 2025 thanks to the rise of proof-of-stake consensus mechanisms 53 .
The fourth and last trend category is the decreasing trend (Fig. 4 d—only 12% of the attacks follow this trend. Some attacks in this category peaked around 2012, and have been slowly decreasing since then ( e.g. , SQL Injection and defacement). The drive-by attack also peaked in 2012, however, had other local peaks in 2016 and 2018, after which it declined noticeably. Cross-site scripting (XSS) and pharming had their peak more recently compared to the other attacks, however, have been smoothly declining since then. All the attacks under this category are predicted to become relatively stable from 2023 onward, however, they are unlikely to disappear in the next 3 years.
The threat cycle
This large-scale analysis involving the historical data and the predictions for the next three years enables us to come up with a generalisable model that traces the evolution and adoption of the threats as they pass through successive stages. These stages are named by the launch, growth, maturity, trough and stability/decline. We refer to this model as The Threat Cycle (or TTC), which is depicted in Fig. 5 . In the launch phase, few incidents start appearing for a short period. This is followed by a sharp increase in terms of the number of incidents, growth and visibility as more and more cyber actors learn and adopt this new attack. Usually, the attacks in the launch phase are likely to have many variants as observed in the case of the WannaCry attack in 2017. At some point, the number of incidents reaches a peak where the attack enters the maturity phase, and the curve becomes steady for a while. Via the trough (when the attack experiences a slight decline as new security measures seem to be very effective), some attacks recover and adapt to the security defences, entering the slope of plateau, while others continue to smoothly decline although they do not completely disappear ( i.e. , slope of decline). It is worth noting that the speed of transition between the different phases may vary significantly between the attacks.
As seen in Fig. 5 , the attacks are placed on the cycle based on the slope of their current trend, while considering their historical trend and prediction. In the trough phase, we can see that the attacks will either follow the slope of plateau or the slope of decline. Based on the predicted trend in the blue zone in Fig. 4 , we were able to indicate the future direction for some of the attacks close to the split point of the trough using different colours (blue or red). Brute force, malvertising, the Distributed Denial-of-Service attack (DDoS), insider threat, WannaCry and phishing are denoted in blue meaning that these are likely on their way to the slope of plateau. In the first three phases, it is usually unclear and difficult to predict whether a particular attack will reach the plateau or decline, thus, denoted in grey.
There are some similarities and differences between TTC and the well-known Gartner hype cycle (GHC) 54 . A standard GHC is shown in a vanishing green colour in Fig. 5 . As TTC is specific to cyber threats, it has a much wider peak compared to GHC. Although both GHC and TTC have a trough phase, the threats decline slightly (while significant drop in GHC) as they exit their maturity phase, after which they recover and move to stability (slope of plateau) or decline.
Many of the attacks in the emerging category are observed in the growth phase. These include IoT device attack, deepfake and data poisoning. While ransomwares (except WannaCry) are in the growth phase, WannaCry already reached the trough, and is predicted to follow the slope of plateau. Adversarial attack has just entered the maturity stage, and cryptojacking is about to enter the trough. Although adversarial attack is generally regarded as a growing threat, interestingly, this machine-based prediction and introspection shows that it is maturing. The majority of the rapidly increasing threats are either in the growth or in the maturity phase. The attacks in the growth phase include session hijacking, supply chain, account hijacking, zero-day and botnet. The attacks in the maturity phase include malware, targeted attack, vulnerability-related attacks and Man-In-The-Middle attack (MITM). Some rapidly increasing attacks such as phishing, brute force, and DDoS are in the trough and are predicted to enter the stability. We also observe that most of the attacks in the category of overall increasing threats have passed the growth phase and are mostly branching to the slope of plateau or the slope of decline, while few are still in the maturity phase ( e.g. , spyware). All of the decreasing threats are on the slope of decline. These include XSS, pharming, drive-by, defacement and SQL injection.
Highlights and limitations
This study presents the development of a ML-based proactive approach for long-term prediction of cyber-attacks offering the ability to communicate effectively with the potential attacks and the relevant security measures in an early stage to plan for the future. This approach can contribute to the prevention of an incident by allowing more time to develop optimal defensive actions/tools in a contested cyberspace. Proactive approaches can also effectively reduce uncertainty when prioritising existing security measures or initiating new security solutions. We argue that cyber-security agencies should prioritise their resources to provide the best possible support in preventing fastest-growing attacks that appear in the launch phase of TTC or the attacks in the categories of the rapidly increasing or emerging trend as in Fig. 4 a and c based on the predictions in the coming years.
In addition, our fully automated approach is promising to overcome the well-known issues of human-based analysis, above all expertise scarcity. Given the absence of the possibility of analysing with human’s subjective bias while following a purely quantitative procedure and data, the resulting predictions are expected to have lower degree of subjectivity, leading to consistencies within the subject. By fully automating this analytic process, the results are reproducible and can potentially be explainable with help of the recent advancements in Explainable Artificial Intelligence.
Thanks to the massive data volume and wide geographic coverage of the data sources we utilised, this study covers every facet of today’s cyber-attack scenario. Our holistic approach performs the long-term prediction on the scale of 36 countries, and is not confined to a specific region. Indeed, cyberspace is limitless, and a cyber-attack on critical infrastructure in one country can affect the continent as a whole or even globally. We argue that our Threat Cycle (TTC) provides a sound basis to awareness of and investment in new security measures that could prevent attacks from taking place. We believe that our tool can enable a collective defence effort by sharing the long-term predictions and trend analysis generated via quantitative processes and data and furthering the analysis of its regional and global impacts.
Zero-day attacks exploit a previously unknown vulnerability before the developer has had a chance to release a patch or fix for the problem 55 . Zero-day attacks are particularly dangerous because they can be used to target even the most secure systems and go undetected for extended periods of time. As a result, these attacks can cause significant damage to an organisation’s reputation, financial well-being, and customer trust. Our approach takes the existing research on using ML in the field of zero-day attacks to another level, offering a more proactive solution. By leveraging the power of deep neural networks to analyse complex, high-dimensional data, our approach can help agencies to prepare ahead of time, in-order to prevent the zero-day attack from happening at the first place, a problem that there is no existing fix for it despite our ability to detect it. Our results in Fig. 4 a suggest that zero-day attack is likely to continue a steep growth until 2025. If we know this information, we can proactively invest on solutions to prevent it or slow down its rise in the future, since after all, the ML detection approaches may not be alone sufficient to reduce its effect.
A limitation of our approach is its reliance on a restricted dataset that encompasses data since 2011 only. This is due to the challenges we encountered in accessing confidential and sensitive information. Extending the prediction phase requires the model to make predictions further into the future, where there may be more variability and uncertainty. This could lead to a decrease in prediction accuracy, especially if the underlying data patterns change over time or if there are unforeseen external factors that affect the data. While not always the case, this uncertainty is highlighted by the results of the Bayesian model itself as it expresses this uncertainty through the increase of the confidence interval over time (Fig. 3 a and b). Despite incorporating the Bayesian model to tackle the epistemic uncertainty, our model could benefit substantially from additional data to acquire a comprehensive understanding of past patterns, ultimately improving its capacity to forecast long-term trends. Moreover, an augmented dataset would allow ample opportunity for testing, providing greater confidence in the model’s resilience and capability to generalise.
Further enhancements can be made to the dataset by including pivotal dates (such as anniversaries of political events and war declarations) as a feature, specifically those that experience a high frequency of cyber-attacks. Additionally, augmenting the dataset with digital traces that reflect the attackers’ intentions and motivations obtained from the dark web would be valuable. Other informative features could facilitate short-term prediction, specifically to forecast the on-set of each attack.
Future work
Moving forward, future research can focus on augmenting the dataset with additional samples and informative features to enhance the model’s performance and its ability to forecast the trend in the longer-term. Also, the work opens a new area of research that focuses on prognosticating the disparity between the trend of cyber-attacks and the associated technological solutions and other variables, with the aim of guiding research investment decisions. Subsequently, TTC could be improved by adopting another curve model that can visualise the current development of relevant security measures. The threat trend categories (Fig. 4 ) and TTC (Fig. 5 ) show how attacks will be visible in the next three years and more, however, we do not know where the relevant security measures will be. For example, data poisoning is an AI-targeted adversarial attack that attempts to manipulate the training dataset to control the prediction behaviour of a machine-learned model. From the scientific literature data ( e.g. , Scopus), we could analyse the published articles studying the data poisoning problem and identify the relevant keywords of these articles ( e.g. , Reject on Negative Impact (RONI) and Probability of Sufficiency (PS)). RONI and PS are typical methods used for detecting poisonous data by evaluating the effect of individual data points on the performance of the trained model. Likewise, the features that are informative, discriminating or uncertainty-reducing for knowing how the relevant security measures evolve exist within such online sources in the form of author’s keywords, number of citations, research funding, number of publications, etc .
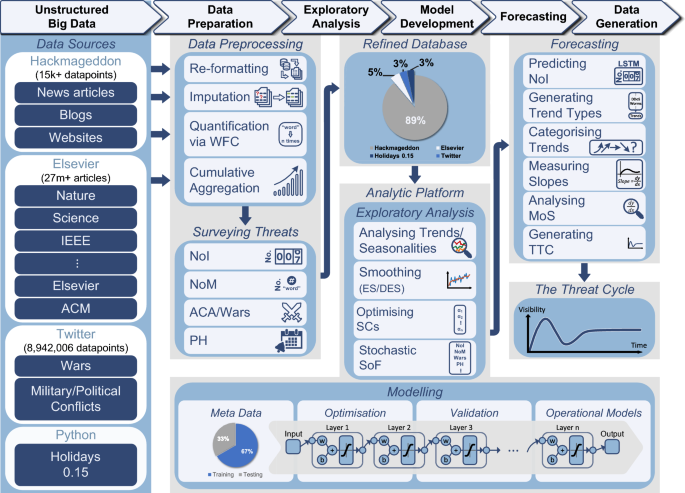
The workflow and architecture of forecasting cyber threats. The ground truth of Number of Incidents (NoI) was extracted from Hackmageddon which has over 15,000 daily records of cyber incidents worldwide over the past 11 years. Additional features were obtained including the Number of Mentions (NoM) of each attack in the scientific literature using Elsevier API which gives access to over 27 million documents. The number of tweets about Armed Conflict Areas/Wars (ACA) was also obtained using Twitter API for each country, with a total of approximately 9 million tweets. Finally, the number of Public Holidays (PH) in each country was obtained using the holidays library in Python. The data preparation phase includes data re-formatting, imputation and quantification using Word Frequency Counter (WFC) to obtain the monthly occurrence of attacks per country and Cumulative Aggregation (CA) to obtain the sum for all countries. The monthly NoM, ACA and PHs were quantified and aggregated using CA. The numerical features were then combined and stored in the refined database. The percentages in the refined database are based on the contribution of each data source. In the exploratory analysis phase, the analytic platform analyses the trend and performs data smoothing using Exponential Smoothing (ES), Double Exponential Smoothing (DES) and No Smoothing (NS). The smoothing methods and Smoothing Constants (SCs) were chosen for each attack followed by the Stochastic Selection of Features (SoF). In the model development phase, the meta data was partitioned into approximately 67% for training and 33% for testing. The models were learned using the encoder-decoder architecture of the Bayesian Long Short-Term Memory (B-LSTM). The optimisation component finds the set of hyper-parameters that minimises the error (i.e., M-SMAPE), which is then used for learning the operational models. In the forecasting phase, we used the operational models to predict the next three years’ NoIs. Analysing the predicted data, trend types were identified and attacks were categorised into four different trends. The slope of each attack was then measured and the Magnitude of Slope (MoS) was analysed. The final output is The Threat Cycle (TTC) illustrating the attacks trend, status, and direction in the next 3 years.
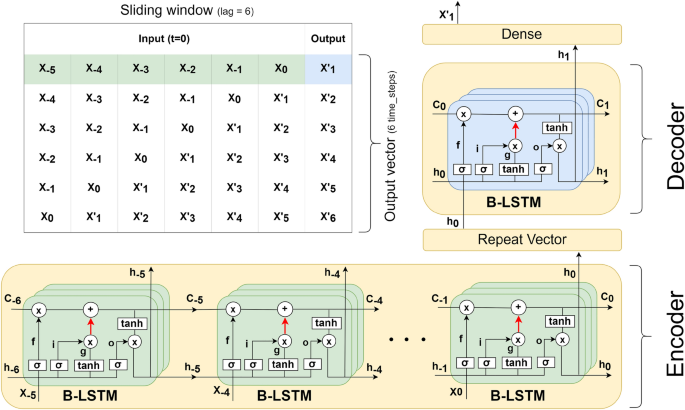
The encoder-decoder architecture of Bayesian Long Short-Term Memory (B-LSTM). \(X_{i}\) stands for the input at time-step i . \(h_{i}\) stands for the hidden state, which stores information from the recent time steps (short-term). \(C_{i}\) stands for the cell state, which stores all processed information from the past (long-term). The number of input time steps in the encoder is a variable tuned as a hyper-parameter, while the output in the decoder is a single time-step. The depth and number of layers are another set of hyper-parameters tuned during the model optimisation. The red arrows indicate a recurrent dropout maintained during the testing and prediction. The figure shows an example for an input with time lag=6 and a single layer. The final hidden state \(h_{0}\) produced by the encoder is passed to the Repeat Vector layer to convert it from 2 dimensional output to 3 dimensional input as expected by the decoder. The decoder processes the input and produces the final hidden state \(h_{1}\) . This hidden state is finally passed to a dense layer to produce the output. The table illustrates the concept of sliding window method used to forecast multiple time steps during the testing and prediction (i.e., using the output at a time-step as an input to forecast the next time-step). Using this concept, we can predict as many time steps as needed. In the table, an output vector of 6 time steps was predicted.
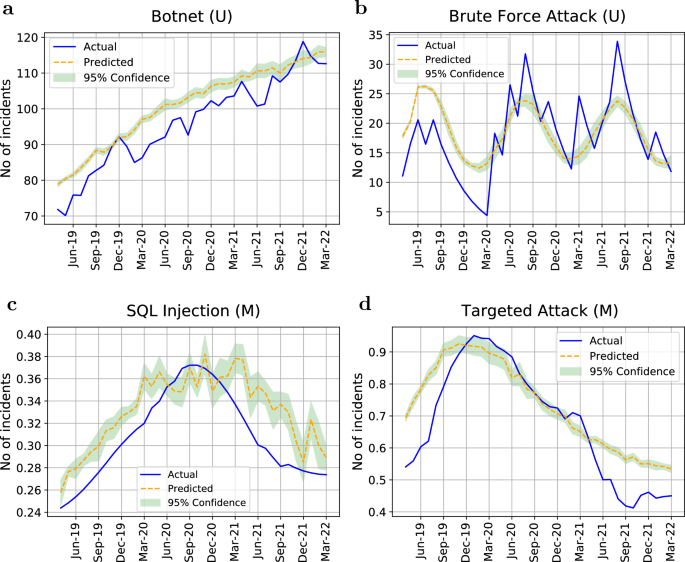
The B-LSTM validation results of predicting the number of attacks from April, 2019 to March, 2022. (U) indicates an univariate model while (M) indicates a multivariate model. ( a ) Botnet attack with M-SMAPE=0.03. ( b ) Brute force attack with M-SMAPE=0.13. ( c ) SQL injection attack with M-SMAPE=0.04 using the feature of NoM. ( d ) Targeted attack with M-SMAPE=0.06 using the feature of NoM. Y axis is normalised in the case of multivariate models to account for the different ranges of feature values.
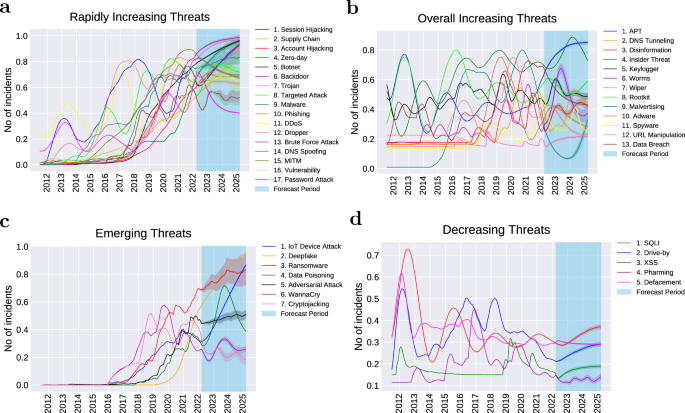
A bird’s eye view of threat trend categories. The period of the trend plots is between July, 2011 and March, 2025, with the period between April, 2022 and March, 2025 forecasted using B-LSTM. ( a ) Among rapidly increasing threats, as observed in the forecast period, some threats are predicted to continue a sharp increase until 2025 while others will probably level off. ( b ) Threats under this category have overall been increasing while fluctuating over the past 11 years. Recently, some of the overall increasing threats slightly declined however many of those are likely to recover and level off by 2025. ( c ) Emerging threats that began to appear and grow sharply after the year 2016, and are expected to continue growing at this increasing rate, while others are likely to slow down or stabilise by 2025. ( d ) Decreasing threats that peaked in the earlier years and have slowly been declining since then. This decreasing group are likely to level off however probably will not disappear in the coming 3 years. The Y axis is normalised to account for the different ranges of values across different attacks. The 95% confidence interval is shown for each threat prediction.
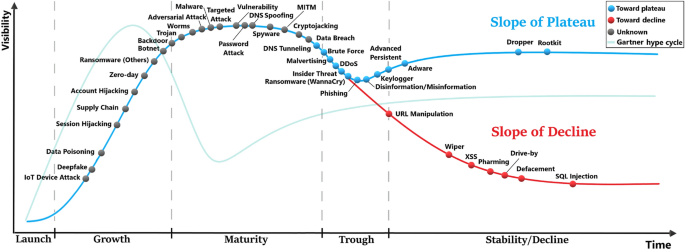
The threat cycle (TTC). The attacks go through 5 stages, namely, launch, growth, maturity trough, and stability/decline. A standard Gartner hype cycle (GHC) is shown with a vanishing green colour for a comparison to TTC. Both GHC and TTC have a peak, however, TTC’s peak is much wider with a slightly less steep curve during the growth stage. Some attacks in TTC do not recover after the trough and slide into the slope of decline. TTC captures the state of each attack in 2022, where the colour of each attack indicates which slope it would follow (e.g., plateau or decreasing) based on the predictive results until 2025. Within the trough stage, the attacks (in blue dot) are likely to arrive at the slope of plateau by 2025. The attacks (in red dot) will probably be on the slope of decline by 2025. The attacks with unknown final destination are coloured in grey.
Data availability
As requested by the journal, the data used in this paper is available to editors and reviewers upon request. The data will be made publicly available and can be accessed at the following link after the paper is published. https://github.com/zaidalmahmoud/Cyber-threat-forecast .
Ghafur, S. et al. A retrospective impact analysis of the wannacry cyberattack on the NHS. NPJ Digit. Med. 2 , 1–7 (2019).
Article Google Scholar
Alrzini, J. R. S. & Pennington, D. A review of polymorphic malware detection techniques. Int. J. Adv. Res. Eng. Technol. 11 , 1238–1247 (2020).
Google Scholar
Lazarevic, A., Ertoz, L., Kumar, V., Ozgur, A. & Srivastava, J. A comparative study of anomaly detection schemes in network intrusion detection. In: Proceedings of the 2003 SIAM International Conference on Data Mining , 25–36 (SIAM, 2003).
Kebir, O., Nouaouri, I., Rejeb, L. & Said, L. B. Atipreta: An analytical model for time-dependent prediction of terrorist attacks. Int. J. Appl. Math. Comput. Sci. 32 , 495–510 (2022).
MATH Google Scholar
Anticipating cyber attacks: There’s no abbottabad in cyber space. Infosecurity Magazine https://www.infosecurity-magazine.com/white-papers/anticipating-cyber-attacks (2015).
Jumper, J. et al. Highly accurate protein structure prediction with alphafold. Nature 596 , 583–589 (2021).
Article ADS CAS PubMed PubMed Central Google Scholar
Baek, M. et al. Accurate prediction of protein structures and interactions using a three-track neural network. Science 373 , 871–876 (2021).
Gibney, E. et al. Where is russia’s cyberwar? researchers decipher its strategy. Nature 603 , 775–776 (2022).
Article ADS CAS PubMed Google Scholar
Passeri, P. Hackmageddon data set. Hackmageddon https://www.hackmageddon.com (2022).
Chen, C.-M. et al. A provably secure key transfer protocol for the fog-enabled social internet of vehicles based on a confidential computing environment. Veh. Commun. 39 , 100567 (2023).
Nagasree, Y. et al. Preserving privacy of classified authentic satellite lane imagery using proxy re-encryption and UAV technologies. Drones 7 , 53 (2023).
Kavitha, A. et al. Security in IoT mesh networks based on trust similarity. IEEE Access 10 , 121712–121724 (2022).
Salih, A., Zeebaree, S. T., Ameen, S., Alkhyyat, A. & Shukur, H. M A survey on the role of artificial intelligence, machine learning and deep learning for cybersecurity attack detection. In: 2021 7th International Engineering Conference “Research and Innovation amid Global Pandemic” (IEC) , 61–66 (IEEE, 2021).
Ren, K., Zeng, Y., Cao, Z. & Zhang, Y. Id-rdrl: A deep reinforcement learning-based feature selection intrusion detection model. Sci. Rep. 12 , 1–18 (2022).
Liu, X. & Liu, J. Malicious traffic detection combined deep neural network with hierarchical attention mechanism. Sci. Rep. 11 , 1–15 (2021).
Werner, G., Yang, S. & McConky, K. Time series forecasting of cyber attack intensity. In Proceedings of the 12th Annual Conference on Cyber and Information Security Research , 1–3 (2017).
Werner, G., Yang, S. & McConky, K. Leveraging intra-day temporal variations to predict daily cyberattack activity. In 2018 IEEE International Conference on Intelligence and Security Informatics (ISI) , 58–63 (IEEE, 2018).
Okutan, A., Yang, S. J., McConky, K. & Werner, G. Capture: cyberattack forecasting using non-stationary features with time lags. In 2019 IEEE Conference on Communications and Network Security (CNS) , 205–213 (IEEE, 2019).
Munkhdorj, B. & Yuji, S. Cyber attack prediction using social data analysis. J. High Speed Netw. 23 , 109–135 (2017).
Goyal, P. et al. Discovering signals from web sources to predict cyber attacks. arXiv preprint arXiv:1806.03342 (2018).
Qin, X. & Lee, W. Attack plan recognition and prediction using causal networks. In 20th Annual Computer Security Applications Conference , 370–379 (IEEE, 2004).
Husák, M. & Kašpar, J. Aida framework: real-time correlation and prediction of intrusion detection alerts. In: Proceedings of the 14th international conference on availability, reliability and security , 1–8 (2019).
Liu, Y. et al. Cloudy with a chance of breach: Forecasting cyber security incidents. In: 24th USENIX Security Symposium (USENIX Security 15) , 1009–1024 (2015).
Malik, J. et al. Hybrid deep learning: An efficient reconnaissance and surveillance detection mechanism in sdn. IEEE Access 8 , 134695–134706 (2020).
Bilge, L., Han, Y. & Dell’Amico, M. Riskteller: Predicting the risk of cyber incidents. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security , 1299–1311 (2017).
Husák, M., Bartoš, V., Sokol, P. & Gajdoš, A. Predictive methods in cyber defense: Current experience and research challenges. Futur. Gener. Comput. Syst. 115 , 517–530 (2021).
Stephens, G. Cybercrime in the year 2025. Futurist 42 , 32 (2008).
Adamov, A. & Carlsson, A. The state of ransomware. Trends and mitigation techniques. In EWDTS , 1–8 (2017).
Shoufan, A. & Damiani, E. On inter-rater reliability of information security experts. J. Inf. Secur. Appl. 37 , 101–111 (2017).
Cha, Y.-O. & Hao, Y. The dawn of metamaterial engineering predicted via hyperdimensional keyword pool and memory learning. Adv. Opt. Mater. 10 , 2102444 (2022).
Article CAS Google Scholar
Elsevier research products apis. Elsevier Developer Portal https://dev.elsevier.com (2022).
Twitter api v2. Developer Platform https://developer.twitter.com/en/docs/twitter-api (2022).
holidays 0.15. PyPI. The Python Package Index https://pypi.org/project/holidays/ (2022).
Visser, M., van Eck, N. J. & Waltman, L. Large-scale comparison of bibliographic data sources: Scopus, web of science, dimensions, crossref, and microsoft academic. Quant. Sci. Stud. 2 , 20–41 (2021).
2021 trends show increased globalized threat of ransomware. Cybersecurity and Infrastructure Security Agency https://www.cisa.gov/uscert/ncas/alerts/aa22-040a (2022).
Lai, K. K., Yu, L., Wang, S. & Huang, W. Hybridizing exponential smoothing and neural network for financial time series predication. In International Conference on Computational Science , 493–500 (Springer, 2006).
Huang, B., Ding, Q., Sun, G. & Li, H. Stock prediction based on Bayesian-lstm. In Proceedings of the 2018 10th International Conference on Machine Learning and Computing , 128–133 (2018).
Mae, Y., Kumagai, W. & Kanamori, T. Uncertainty propagation for dropout-based Bayesian neural networks. Neural Netw. 144 , 394–406 (2021).
Article PubMed Google Scholar
Scopus preview. Scopus https://www.scopus.com/home.uri (2022).
Jia, P., Chen, H., Zhang, L. & Han, D. Attention-lstm based prediction model for aircraft 4-d trajectory. Sci. Rep. 12 (2022).
Chandra, R., Goyal, S. & Gupta, R. Evaluation of deep learning models for multi-step ahead time series prediction. IEEE Access 9 , 83105–83123 (2021).
Gers, F. A., Schmidhuber, J. & Cummins, F. Learning to forget: Continual prediction with lstm. Neural Comput. 12 , 2451–2471 (2000).
Article CAS PubMed Google Scholar
Sagheer, A. & Kotb, M. Unsupervised pre-training of a deep lstm-based stacked autoencoder for multivariate time series forecasting problems. Sci. Rep. 9 , 1–16 (2019).
Article ADS Google Scholar
Swiler, L. P., Paez, T. L. & Mayes, R. L. Epistemic uncertainty quantification tutorial. In Proceedings of the 27th International Modal Analysis Conference (2009).
Gal, Y. & Ghahramani, Z. Dropout as a bayesian approximation: Representing model uncertainty in deep learning. arXiv preprint arXiv:1506.02142v6 (2016).
Chollet, F. Deep Learning with Python , 2 edn. (Manning Publications, 2017).
Xu, J., Li, Z., Du, B., Zhang, M. & Liu, J. Reluplex made more practical: Leaky relu. In 2020 IEEE Symposium on Computers and Communications (ISCC) , 1–7 (IEEE, 2020).
Gal, Y., Hron, J. & Kendall, A. Concrete dropout. Adv. Neural Inf. Process. Syst. 30 (2017).
Shcherbakov, M. V. et al. A survey of forecast error measures. World Appl. Sci. J. 24 , 171–176 (2013).
Bergstra, J. & Bengio, Y. Random search for hyper-parameter optimization. J. Mach. Learn. Res. 13 (2012).
Kingma, D. P. & Ba, J. Adam: A method for stochastic optimization. arXiv preprint arXiv:1412.6980 (2014).
Krizhevsky, A., Sutskever, I. & Hinton, G. E. Imagenet classification with deep convolutional neural networks. Commun. ACM 60 , 84–90 (2017).
Shifferaw, Y. & Lemma, S. Limitations of proof of stake algorithm in blockchain: A review. Zede J. 39 , 81–95 (2021).
Dedehayir, O. & Steinert, M. The hype cycle model: A review and future directions. Technol. Forecast. Soc. Chang. 108 , 28–41 (2016).
Abri, F., Siami-Namini, S., Khanghah, M. A., Soltani, F. M. & Namin, A. S. Can machine/deep learning classifiers detect zero-day malware with high accuracy?. In 2019 IEEE International Conference on Big Data (Big Data) , 3252–3259 (IEEE, 2019).
Download references
Acknowledgements
The authors are grateful to the DASA’s machine learning team for their invaluable discussions and feedback, and special thanks to the EBTIC, British Telecom’s (BT) cyber security team for their constructive criticism on this work.
Author information
Authors and affiliations.
Department of Computer Science and Information Systems, University of London, Birkbeck College, London, United Kingdom
Zaid Almahmoud & Paul D. Yoo
Huawei Technologies Canada, Ottawa, Canada
Omar Alhussein
Department of Electrical and Computer Engineering, University of Waterloo, Waterloo, Canada
Ilyas Farhat
Department of Computer Science, Università degli Studi di Milano, Milan, Italy
Ernesto Damiani
Center for Cyber-Physical Systems (C2PS), Khalifa University, Abu Dhabi, United Arab Emirates
You can also search for this author in PubMed Google Scholar
Contributions
Z.A., P.D.Y, I.F., and E.D. were in charge of the framework design and theoretical analysis of the trend analysis and TTC. Z.A., O.A., and P.D.Y. contributed to the B-LSTM design and experiments. O.A. proposed the concepts of B-LSTM. All of the authors contributed to the discussion of the framework design and experiments, and the writing of this paper. P.D.Y. proposed the big data approach and supervised the whole project.
Corresponding author
Correspondence to Paul D. Yoo .
Ethics declarations
Competing interests.
The authors declare no competing interests.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Supplementary Information
Supplementary information., rights and permissions.
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Cite this article.
Almahmoud, Z., Yoo, P.D., Alhussein, O. et al. A holistic and proactive approach to forecasting cyber threats. Sci Rep 13 , 8049 (2023). https://doi.org/10.1038/s41598-023-35198-1
Download citation
Received : 21 December 2022
Accepted : 14 May 2023
Published : 17 May 2023
DOI : https://doi.org/10.1038/s41598-023-35198-1
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
This article is cited by
Integrating ai-driven threat intelligence and forecasting in the cyber security exercise content generation lifecycle.
- Alexandros Zacharis
- Vasilios Katos
- Constantinos Patsakis
International Journal of Information Security (2024)
By submitting a comment you agree to abide by our Terms and Community Guidelines . If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies
Sign up for the Nature Briefing: AI and Robotics newsletter — what matters in AI and robotics research, free to your inbox weekly.

NDSS Symposium 2023: 30 Years of Cutting Edge Network Security Research

The Network and Distributed Systems Security (NDSS) Symposium reaches an important milestone this year, with the 30th edition of the event taking place from 27 February to 3 March 2023 in San Diego, USA. The Internet Society hosted the initial Privacy and Security Research Group (PSRG) Workshop on Network and Distributed System Security 10-12 February 1993. This evolved into the Network and Distributed Systems Security Symposium and has been proudly hosted by the Internet Society in San Diego in the 30 years since.
An incubator of ideas, the NDSS Symposium brings together leading academics, industry researchers, students, and security practitioners to discuss top-tier, peer-reviewed research and exchange ideas. The recordings of every paper presentation and the papers themselves are made available online for anyone to view to support collaborative research.
The Symposium continues to be one of the top conferences for computer and network security research, and more than 560 attendees are expected to participate both in-person and virtually. NDSS 2023 has a full agenda featuring 2 keynotes, 94 accepted papers, 40 posters, and a 30th anniversary retrospective from Tuesday, 28 February to Thursday, 2 March 2023. In addition, there will be eight co-located events on the Monday before, and the Friday after, the main symposium focusing on specific areas of network security research.
Featured Keynotes
The Symposium is honored to have two distinguished speakers providing the keynotes. Richard Ford (Praetorian) will open the symposium on Tuesday with a talk focused on ChatGPT, what this means for machine learning for cybersecurity and privacy, and whether this will benefit defenders or provide new vectors for attackers. Nina Taft (Google) will provide the Wednesday keynote that will discuss the challenges faced by developers with respect to continually evolving privacy laws, policies and user preferences, and the use of Natural Language Processing techniques that can automatically analyze privacy polices to help address this.
Co-Located Events
Throughout the week, there will be eight co-located events:
- The inaugural Symposium on Vehicle Security and Privacy ( VehicleSec 2023 ) builds upon the Automotive and Autonomous Vehicle Security (AutoSec) Workshop that has previously been held during the NDSS Symposium for the past four years. The workshop will discuss the security and privacy issues related to the on-board systems of ground, aerial, underwater and space vehicles, their supporting infrastructures, and associated technologies.
- The inaugural Workshop on Security of Space and Satellite Systems ( SpaceSec 2023 ) will be the first academic workshop co-located with the NDSS Symposium dedicated to the security of satellite systems. It aims to raise awareness of attack vectors and vulnerabilities in the light of major attacks on the ViaSat network and ongoing disruptions of the Global Navigation Satellite System (GNSS).
- The 2nd International Workshop on Ethics in Computer Security ( EthiCS 2023 ) will discuss the increasingly important question of ethics in computer security research. There are often unclear guidelines and review processes, and this workshop aims to provide an international forum for raising awareness and exchanging perspectives to support the development of new guidelines for future ethical security research.
- The Usable Security and Privacy Symposium ( USEC 2023 ) has grown out of the Usable Security and Privacy workshop first held alongside the NDSS Symposium in 2014. This co-located symposium considers how users approach and behave with respect to security and privacy, and how systems can be better designed to reflect this.
- The Workshop on Security Operation Centers (SOC) Operations and Construction ( WOSEC 2023 ) is another new workshop to co-locate with the NDSS Symposium and provides a forum where the Security Operation Center (SOCs) operational community can interact with the researchers to discuss requirements and development new tools and practices in this young field.
- The Workshop on Learning from Authoritative Security Experiment Results ( LASER 2023 ) is the latest in a series of workshops that focus on learning from cybersecurity experiments. This workshop will cover topics that include social media misinformation, privacy considerations of the Hybrid Broadcast Broadband TV (HbbTV) protocol, and tracing user location on instant messaging.
- The Workshop on Measurements, Attacks, and Defenses for the Web ( MADWeb 2023 ) evaluates the security aspects of web browsers and apps with the aim of improving browser architectures, security policies, privacy enhancing techniques, and measurements for the purposes of studying illegal activities.
- The Workshop on Binary Analysis Research ( BAR 2023 ) aims to bring together research on the growing field of binary code analysis, which is needed to analyze embedded devices and closed-source commercial and legacy software for potential cyberthreats.
Academic Papers
The main NDSS Symposium kicks off on Tuesday and runs until Thursday, mostly being organized into three parallel tracks. With so many high-quality papers being presented, it’s impossible to preview them all, but we’d like to highlight a few that have particularly drawn our attention:
Tuesday, 28 February 2023
- Faster Secure Comparisons with Offline Phase for Efficient Private Set Intersection (Session 1C: Privacy and Anonymity) – discussing a new efficient, fast, and private approach to a Private Section Intersection (PSI) protocol.
- DiffCSP: Finding Browser Bugs in Content Security Policy Enforcement through Differential Testing (Session 2A: Software Security II) – presenting the first differential testing framework to find Content Security Policy (CSP) enforcement bugs involving JavaScript execution.
- Drone Security and the Mysterious Case of DJI’s DroneID (Session 2A: Software Security II) – an analysis of the security and privacy of DJI drones, investigating how an attacker can eavesdrop on over-the-air data traffic.
- On the Anonymity of Peer-To-Peer Network Anonymity Schemes Used by Cryptocurrencies (Session 2C: Privacy and Anonymity II) – possible solutions for cryptocurrency systems that can be subjected to de-anonymization attacks by exploiting the network-level communication on their peer-to-peer network, allowing adversaries to observe transactions being exchanged and infer the parties involved.
- Thwarting Smartphone SMS Attacks at the Radio Interface Layer (Session 2C: Privacy and Anonymity II) – the short message service (SMS) can be readily exploited to compromise unsuspecting remote victims. An inline defense mechanism called RILDEFENDER has been developed that integrates into the radio interface layer of Android smartphones.
- FUZZILLI: Fuzzing for JavaScript JIT Compiler Vulnerabilities (Session 3A: Fuzzing) – presenting the first fuzzer that focuses on JavaScript just-in-time compiler vulnerabilities.
- BARS: Local Robustness Certification for Deep Learning based Traffic Analysis Systems (Session 3B: ML and AI III) – a proposed certification framework for deep learning-based traffic analysis systems based on boundary-adaptive randomized smoothing.
Wednesday, 1 March 2023
- Automata-Based Automated Detection of State Machine Bugs in Protocol Implementations (Session 4A: Network Protocols) – an automated black-box technique for detecting state machine bugs in implementations of stateful network protocols.
- Real Threshold ECDSA (Session 4B: Blockchains I) – a proposed solution to mitigate denial-of-service vulnerabilities prevalent in existing ECDSA scheme that makes the assumption of honest signatories.
- MyTEE: Own the Trusted Execution Environment on Embedded Devices (Session 4C: Mobile Security and Privacy) – MyTEE is a trusted execution environment (TEE) that can be used in worst-case environments where major hardware security primitives are absent.
- Parakeet: Practical Key Transparency for End-to-End Encrypted Messaging (Session 5C: Keys and Certification) – a solution for ensuring that key servers honestly serve public keys to users.
- OBI: a multi-path oblivious RAM for forward-and-backward-secure searchable encryption (Session 5C: Keys and Certification) – dynamic searchable encryption (DSE) is a user-cloud protocol for searching over outsourced encrypted data, but it can be inefficient to fetch/insert a large set of data blocks which OBI aims to address.
Thursday, 2 March 2023
- SoundLock: A Novel User Authentication Scheme for VR Devices Using Auditory-Pupillary Response (Session 6A: Cyber-Physical Systems Security I) – improving the security of virtual reality devices.
- Access Your Tesla without Your Awareness: Compromising Keyless Entry System of Model 3 (Session 7A: Cyber-Physical Systems Security II) – a detailed security analysis of Tesla key cards and phone keys, including the possibility of man-in-the-middle attacks.
- Tactics, Threats & Targets: Modeling Disinformation and its Mitigation (Session 7B: Web Security II) – development of cybersecurity-inspired framework to characterize the threat of disinformation.
- Detecting Unknown Encrypted Malicious Traffic in Real Time via Flow Interaction Graph Analysis (Session 7C: Cyber Attacks) – presents HyperVision, a realtime unsupervised machine learning-based system that can detect malicious traffic within encrypted flows.
- A Systematic Study of the Consistency of Two-Factor Authentication User Journeys on Top-Ranked Websites (Session 8C: Usable Security and Privacy) – a study of the user experience of two-factor authentication on top-ranked websites, and how this can be improved.
30th Anniversary: An Overview of Achievements and Success
Last but not least, on Wednesday afternoon an NDSS Symposium 30th Anniversary session will celebrate the achievements and successes of NDSS over the years.
Volunteer Led
The Internet Society would also like to take this opportunity to thank all the volunteer members of the 2023 Program Committee , the Organizing Committee , and the Steering Group , who have worked hard to pull together another high-quality event. We look forward to seeing you all in San Diego!
More Information Check out the full NDSS Symposium 2023 program . Advance registration is now closed but on-site registration is possible from 27 February.
Follow NDSS Symposium on Twitter , Facebook , LinkedIn , and Youtube !
Image copyright: ©Wes Hardaker
Disclaimer: Viewpoints expressed in this post are those of the author and may or may not reflect official Internet Society positions.
Recent Posts
- What Makes The Internet? People Coming Together
The Wellness Side of the Run the Internet Challenge
Run the internet with us: a 7-day movement challenge, bill s-210 threatens canadians’ access to the internet .
- It Takes a Community to Defend the Internet
Related articles
Run the Internet for a healthier you and a healthier Internet. Join the challenge today!
Join the Run the Internet challenge from 5-11 June 2024 to support a globally connected Internet—for all of us.
Canadian Bill S-210 threatens to break the Internet in Canada and fragment Canadians' access. Help spread the word that...
Help | Advanced Search
Computer Science > Cryptography and Security
Title: quantum cryptography for enhanced network security: a comprehensive survey of research, developments, and future directions.
Abstract: With the ever-growing concern for internet security, the field of quantum cryptography emerges as a promising solution for enhancing the security of networking systems. In this paper, 20 notable papers from leading conferences and journals are reviewed and categorized based on their focus on various aspects of quantum cryptography, including key distribution, quantum bit commitment, post quantum cryptography, and counterfactual quantum key distribution. The paper explores the motivations and challenges of employing quantum cryptography, addressing security and privacy concerns along with existing solutions. Secure key distribution, a critical component in ensuring the confidentiality and integrity of transmitted information over a network, is emphasized in the discussion. The survey examines the potential of quantum cryptography to enable secure key exchange between parties, even when faced with eavesdropping, and other applications of quantum cryptography. Additionally, the paper analyzes the methodologies, findings, and limitations of each reviewed study, pinpointing trends such as the increasing focus on practical implementation of quantum cryptography protocols and the growing interest in postquantum cryptography research. Furthermore, the survey identifies challenges and open research questions, including the need for more efficient quantum repeater networks, improved security proofs for continuous variable quantum key distribution, and the development of quantum resistant cryptographic algorithms.
| Subjects: | Cryptography and Security (cs.CR) |
| Cite as: | [cs.CR] |
| (or [cs.CR] for this version) | |
| Focus to learn more arXiv-issued DOI via DataCite |
Submission history
Access paper:.
- Other Formats
References & Citations
- Google Scholar
- Semantic Scholar
BibTeX formatted citation
Bibliographic and Citation Tools
Code, data and media associated with this article, recommenders and search tools.
- Institution
arXivLabs: experimental projects with community collaborators
arXivLabs is a framework that allows collaborators to develop and share new arXiv features directly on our website.
Both individuals and organizations that work with arXivLabs have embraced and accepted our values of openness, community, excellence, and user data privacy. arXiv is committed to these values and only works with partners that adhere to them.
Have an idea for a project that will add value for arXiv's community? Learn more about arXivLabs .
- IEEE Xplore Digital Library
- IEEE Standards
- IEEE Spectrum Online
- More IEEE Sites

CALL FOR PAPERS
The IEEE Conference on Communications and Network Security (CNS) is a premier forum for cybersecurity researchers, engineers, practitioners, and policy makers to exchange ideas, techniques and tools related to all practical and theoretical aspects of communications and network security. The conference seeks submissions from academia, industry, and government presenting novel research results in communications and network security.
Particular topics of interest include, but are not limited to:
- Anonymity and privacy technologies
- Biometric authentication and identity management
- Cyber crimes, forensics, and defenses
- Data security
- Game-theoretic and information-theoretic security technologies
- Implementation and evaluation of networked security systems
- Intrusion detection, prevention, and response
- Key management, public key infrastructures, certification revocation, authentication, and access control
- Software and language-based security
- Security metrics and models
- Physical-layer and cross-layer security technologies
- Machine learning security
- Security in Internet of Things, cyber-physical systems, and critical infrastructures (smart grids, transportation systems, etc.)
- Security in wireless, cellular, ad hoc, mesh, sensor networks and technologies
- Security for mobile and wearable devices
- Security of blockchain and its applications
- Security in cloud and edge computing, crowdsourcing, peer-to-peer and overlay networks
- Security for future Internet architectures and designs
- Security for software-defined and data center networks
- Security in autonomous vehicles, UAVs/UAS, drones, etc.
- Security of social networks, metaverse/virtual/augmented reality-based networks/systems
- Social, economic, and policy issues of trust, security, and privacy
- Traffic analysis
- Usable security and privacy
- Web security
Accepted and presented technical papers will be published in the 2023 IEEE CNS Proceedings and submitted to IEEE Xplore® as well as other Abstracting and Indexing (A&I) databases. See the website for detailed instructions and submission rules and regulations and for author requirements for accepted papers.
Submission deadline: 12 June 2023 18 June 2023 (AoE)
Submit a paper
Information
- Author Services
Initiatives
You are accessing a machine-readable page. In order to be human-readable, please install an RSS reader.
All articles published by MDPI are made immediately available worldwide under an open access license. No special permission is required to reuse all or part of the article published by MDPI, including figures and tables. For articles published under an open access Creative Common CC BY license, any part of the article may be reused without permission provided that the original article is clearly cited. For more information, please refer to https://www.mdpi.com/openaccess .
Feature papers represent the most advanced research with significant potential for high impact in the field. A Feature Paper should be a substantial original Article that involves several techniques or approaches, provides an outlook for future research directions and describes possible research applications.
Feature papers are submitted upon individual invitation or recommendation by the scientific editors and must receive positive feedback from the reviewers.
Editor’s Choice articles are based on recommendations by the scientific editors of MDPI journals from around the world. Editors select a small number of articles recently published in the journal that they believe will be particularly interesting to readers, or important in the respective research area. The aim is to provide a snapshot of some of the most exciting work published in the various research areas of the journal.
Original Submission Date Received: .
- Active Journals
- Find a Journal
- Proceedings Series
- For Authors
- For Reviewers
- For Editors
- For Librarians
- For Publishers
- For Societies
- For Conference Organizers
- Open Access Policy
- Institutional Open Access Program
- Special Issues Guidelines
- Editorial Process
- Research and Publication Ethics
- Article Processing Charges
- Testimonials
- Preprints.org
- SciProfiles
- Encyclopedia

Article Menu

- Subscribe SciFeed
- Recommended Articles
- PubMed/Medline
- Google Scholar
- on Google Scholar
- Table of Contents
Find support for a specific problem in the support section of our website.
Please let us know what you think of our products and services.
Visit our dedicated information section to learn more about MDPI.
JSmol Viewer
A critical cybersecurity analysis and future research directions for the internet of things: a comprehensive review.

1. Introduction
- There is a lack of comprehensive security solutions for IoT devices. The number of devices and the different applications that they are used for having resulted in a complex ecosystem that is hard to secure. This complexity is exacerbated by the limited computational resources of many IoT devices, which makes it difficult to implement advanced security solutions.
- There is a lack of protocol standardization in IoT device security. The lack of universal security measures makes it easier for attackers to exploit vulnerabilities, resulting in a higher risk of security breaches. Without a common taxonomy, it becomes difficult to ensure the security of an IoT ecosystem, which consists of several different types of devices, communication protocols, and applications.
- There is a need for research to identify new security risks that arise from the integration of IoT devices with other systems, such as layer-based services. The integration of IoT devices with diverse systems introduces new vulnerabilities, which need to be identified and addressed.
- There is a need for more research on access control driven anomalies and countermeasures related to IoT devices. The massive deployment of these devices has led to the collection of vast amounts of data, and it is essential to ensure that this data is protected from unauthorized access and misuse.
2. General Design, Components, and Protocols for the Internet of Things
2.1. observation layer, 2.2. network layer, 2.3. application layer, 3. potential security issues with the internet of things, data, network and device security, 4. what distinguishes iot anomaly detection from it security.
- Microcontroller or microprocessor with low power consumption and wireless connectivity (e.g., Wi-Fi, Bluetooth, and Zigbee);
- Sensors and actuators for data acquisition and control;
- Power source (e.g., battery, energy harvesting, and power adapter);
- Memory and storage for data and software;
- Security features (e.g., secure boot, encryption, and access control).
- Wireless communication protocols (e.g., Wi-Fi, Bluetooth, Zigbee, and LoRaWAN);
- Network topology (e.g., star, mesh, and point-to-point);
- Gateway or edge device for data aggregation and processing;
- Cloud or server infrastructure for data storage and analysis;
- Security protocols (e.g., SSL/TLS, VPN, firewalls, and intrusion detection/prevention).
- Operating System (e.g., embedded Linux, FreeRTOS, and Zephyr);
- Middleware (e.g., MQTT, CoAP, and AMQP);
- Database (e.g., Apache Cassandra, MongoDB, and InfluxDB);
- Application Development Tools (applied) (e.g., software development kits (SDKs) and integrated development environments (IDEs).
5. Classification of Internet of Things Access Control
5.1. cryptographic paradigm in iot.
- An “always-on” interoperability method is preferable to the periodic activation and deactivation of communication networks when an IoT system application has to transfer data often.
- Data from IoT devices should be gathered as efficiently as possible and compressed before being sent over the network. Coordinating several IoT Services delivered by a single communications module within a single IoT device application is essential for making efficient use of the network.
- To avoid seeming as though they are all functioning unison, application software operating on IoT devices should utilize a random pattern to request network connection.
- The data should be encrypted from edge to edge using the IoT system software.
- Before beginning any data transfer, the IoT device application must verify that it can communicate with the IoT platform. The level of security provided by the encryption technique should be commensurate with the IoT Service.
- The application running on the IoT device should not have to constantly reestablish the modem’s network connection.
- When an Internet of Things device framework does not require constant information exchange and therefore may function with some delay in its IoT Service.
- The Internet of Things device application must include “temporal resynchronization” capability, both for local and distant connections.
5.1.1. Symmetric Ciphering
Block cipher methods, data encryption standard (des), advanced encryption standard (aes), stream cipher methods, 5.1.2. asymmetric ciphering, rivest–shamir–adleman (rsa) crypto algorithm, digital signature standards (dss), elliptical curve cryptography (ecc), ntruencrypt, 5.1.3. ciphering protocols, internet protocol security (ipsec), secure/multipurpose internet mail extensions (s/mime), transport layer security (tls), secure shell protocol (ssh), 5.1.4. hashing (integrity), 6. roadmap for securing iot devices, 6.1. how can artificial intelligence (ai) and machine learning (ml) change iot security, 6.2. risk factors, 6.3. future directions: decisive remarks, 7. conclusions and our recommendations, author contributions, institutional review board statement, informed consent statement, data availability statement, acknowledgments, conflicts of interest.
- Das, A.; Yashkova, O. Market Analysis Perspective: Worldwide Internet of Things, 2022—Infrastructure and the Intelligent Edge. (IDC) from IDC: The Premier Global Market Intelligence Company. October 2022. Available online: https://www.idc.com/getdoc.jsp?containerId=US49735922 (accessed on 15 January 2023).
- Alaba, F.A.; Othman, M.; Hashem, I.A.; Alotaibi, F. Internet of Things security: A survey. J. Netw. Comput. Appl. 2017 , 88 , 10–28. [ Google Scholar ] [ CrossRef ]
- Wani, A.R.; Gupta, S.K.; Khanam, Z.; Rashid, M.; Alshamrani, S.S.; Baz, M. A novel approach for securing data against adversary attacks in UAV embedded HetNet using identity based authentication scheme. IET Intell. Transp. Syst. Early View 2022 , 1–19. [ Google Scholar ] [ CrossRef ]
- CONNECT. Fast Innovation Requires Fast IT. Building the Internet of Things. December 2022. Available online: https://www.cisco.com/c/dam/global/en_ph/assets/ciscoconnect/pdf/bigdata/jim_green_cisco_connect.pdf (accessed on 5 January 2023).
- NIST. Cybersecurity Framework. Cybersecurity Framework Version 1.1. 12 November 2013. Available online: https://www.nist.gov/cyberframework (accessed on 5 January 2023).
- Cao, C.; Tang, Y.; Huang, D.; Gan, W.; Zhang, C. IIBE: An Improved Identity-Based Encryption Algorithm for WSN Security. Secur. Commun. Netw. 2021 , 2021 , 1–8. [ Google Scholar ] [ CrossRef ]
- Yu, H.J.; Kim, C.H.; Im, S.S.; Oh, S.H. ZigBee Authentication Protocol with Enhanced User Convenience and Safety. J. Inf. Secur. 2022 , 22 , 81–92. [ Google Scholar ] [ CrossRef ]
- Sofi, A. Bluetooth Protocol in Internet of Things (IoT), Security Challenges and a Comparison with Wi-Fi Protocol: A Review. Int. J. Eng. Tech. Res. 2016 , 5 , 1–7. [ Google Scholar ] [ CrossRef ]
- Barua, A.; Al Alamin, M.A.; Hossain, M.S.; Hossain, E. Security and Privacy Threats for Bluetooth Low Energy in IoT and Wearable Devices: A Comprehensive Survey. IEEE Open J. Commun. Soc. 2022 , 3 , 251–281. [ Google Scholar ] [ CrossRef ]
- Aloufi, K.S. 6LoWPAN Stack Model Configuration for IoT Streaming Data Transmission over CoAP. Int. J. Commun. Netw. Inf. Secur. (IJCNIS) 2022 , 11 , 304–312. [ Google Scholar ] [ CrossRef ]
- Zhang, L.; Ma, M.; Qiu, Y. An enhanced handover authentication solution for 6LoWPAN networks. Comput. Secur. 2021 , 109 , 102373. [ Google Scholar ] [ CrossRef ]
- Mbarek, B.; Ge, M.; Pitner, T. Proactive trust classification for detection of replication attacks in 6LoWPAN-based IoT. Internet Things 2021 , 16 , 100442. [ Google Scholar ] [ CrossRef ]
- Ingham, M.; Marchang, J.; Bhowmik, D. IoT security vulnerabilities and predictive signal jamming attack analysis in LoRaWAN. IET Inf. Secur. 2020 , 14 , 368–379. [ Google Scholar ] [ CrossRef ]
- Ugwuanyi, S.; Paul, G.; Irvine, J. Survey of IoT for Developing Countries: Performance Analysis of LoRaWAN and Cellular NB-IoT Networks. Electronics 2021 , 10 , 2224. [ Google Scholar ] [ CrossRef ]
- Kuntke, F.; Romanenko, V.; Linsner, S.; Steinbrink, E.; Reuter, C. LoRaWAN security issues and mitigation options by the example of agricultural IoT scenarios. Trans. Emerg. Telecommun. Technol. 2022 , 5 , 33. [ Google Scholar ] [ CrossRef ]
- Seoane, V.; Garcia-Rubio, C.; Almenares, F.; Campo, C. Performance evaluation of CoAP and MQTT with security support for IoT environments. Comput. Netw. 2021 , 197 , 108338. [ Google Scholar ] [ CrossRef ]
- Bilal, D.; Rehman, A.U.; Ali, R. Internet of Things (IoT) Protocols: A Brief Exploration of MQTT and CoAP. Int. J. Comput. Appl. 2018 , 179 , 9–14. [ Google Scholar ] [ CrossRef ]
- Tsai, W.C.; Tsai, T.H.; Wang, T.J.; Chiang, M.L. Automatic Key Update Mechanism for Lightweight M2M Communication and Enhancement of IoT Security: A Case Study of CoAP Using Libcoap Library. Sensors 2022 , 22 , 340. [ Google Scholar ] [ CrossRef ]
- Park, J.H.; Kim, H.S.; Kim, W.T. DM-MQTT: An Efficient MQTT Based on SDN Multicast for Massive IoT Communications. Sensors 2018 , 18 , 3071. [ Google Scholar ] [ CrossRef ]
- Lee, J.G.; Lee, S.J.; Kim, Y.W. Attack Detection and Classification Method Using PCA and LightGBM in MQTT-based IoT Environment. J. Inf. Secur. 2022 , 22 , 17–24. [ Google Scholar ] [ CrossRef ]
- Hussein, N.; Nhlabatsi, A. Living in the Dark: MQTT-Based Exploitation of IoT Security Vulnerabilities in ZigBee Networks for Smart Lighting Control. IoT 2022 , 3 , 450–472. [ Google Scholar ] [ CrossRef ]
- Venkatraman, S.; Overmars, A. New Method of Prime Factorisation-Based Attacks on RSA Authentication in IoT. Cryptography 2019 , 3 , 20. [ Google Scholar ] [ CrossRef ]
- Hung, C.W.; Hsu, W.T. Power Consumption and Calculation Requirement Analysis of AES for WSN IoT. Sensors 2018 , 18 , 1675. [ Google Scholar ] [ CrossRef ]
- Sheikhpour, S.; Ko, S.B.; Mahani, A. A low cost fault-attack resilient AES for IoT applications. Microelectron. Reliab. 2021 , 123 , 114202. [ Google Scholar ] [ CrossRef ]
- Sreekanth, M.; Jeyachitra, R. Implementation of area-efficient AES using FPGA for IOT applications. Int. J. Embed. Syst. 2022 , 15 , 354. [ Google Scholar ] [ CrossRef ]
- OPEN. MQTT—The Standard for IoT Messaging. MQTT—The Standard for IoT Messaging. December 2022. Available online: https://mqtt.org/ (accessed on 2 January 2023).
- Muñoz Castañeda, Á.L.; Mata, J.A.A.; Aláiz-Moretón, H. Characterization of threats in IoT from an MQTT protocol-oriented dataset. Complex Intell. Syst. 2023 , 1–16. [ Google Scholar ] [ CrossRef ]
- Kim, G.; Park, J.; Chung, K. MQTT-based Gateway System for Auto-configuration of IoT Devices and Services. J. KIISE 2019 , 46 , 385–390. [ Google Scholar ] [ CrossRef ]
- Yu, H.; Park, Y. Design and implementation of IIoT edge device for collecting heterogeneous machine data. J. Internet Electron. Commer. Resarch 2021 , 21 , 23–32. [ Google Scholar ] [ CrossRef ]
- Vaclavova, A.; Strelec, P.; Horak, T.; Kebisek, M.; Tanuska, P.; Huraj, L. Proposal for an IIoT Device Solution According to Industry 4.0 Concept. Sensors 2022 , 22 , 325. [ Google Scholar ] [ CrossRef ] [ PubMed ]
- Pappalardo, M.; Virdis, A.; Mingozzi, E. An Edge-Based LWM2M Proxy for Device Management to Efficiently Support QoS-Aware IoT Services. IoT 2022 , 3 , 169–190. [ Google Scholar ] [ CrossRef ]
- Debroy, S.; Samanta, P.; Bashir, A.; Chatterjee, M. SpEED-IoT: Spectrum aware energy efficient routing for device-to-device IoT communication. Future Gener. Comput. Syst. 2019 , 93 , 833–848. [ Google Scholar ] [ CrossRef ]
- Che, B.; Liu, L.; Zhang, H. KNEMAG: Key Node Estimation Mechanism Based on Attack Graph for IoT Security. J. Internet Things 2020 , 2 , 145–162. [ Google Scholar ] [ CrossRef ]
- Agrawal, S.; Das, M.L.; Lopez, J. Detection of Node Capture Attack in Wireless Sensor Networks. IEEE Syst. J. 2019 , 13 , 238–247. [ Google Scholar ] [ CrossRef ]
- Kim, M.; Suh, T. Eavesdropping Vulnerability and Countermeasure in Infrared Communication for IoT Devices. Sensors 2021 , 21 , 8207. [ Google Scholar ] [ CrossRef ] [ PubMed ]
- Alharbi, I.A.; Almalki, A.J.; Alyami, M.; Zou, C.; Solihin, Y. Profiling Attack on WiFi-based IoT Devices using an Eavesdropping of an Encrypted Data Frames. Adv. Sci. Technol. Eng. Syst. J. 2022 , 7 , 49–57. [ Google Scholar ] [ CrossRef ]
- Singh, Y.; Mohindru, V. Node authentication algorithm for securing static wireless sensor networks from node clone attack. Int. J. Inf. Comput. Secur. 2018 , 10 , 129. [ Google Scholar ] [ CrossRef ]
- Jenisha, R. Node to Node Communication Security in IOT Networks. Int. J. Res. Appl. Sci. Eng. Technol. 2022 , 10 , 3212–3226. [ Google Scholar ] [ CrossRef ]
- Staniec, K.; Kowal, M. On Vulnerability of Selected IoT Systems to Radio Jamming—A Proposal of Deployment Practices. Sensors 2020 , 20 , 6152. [ Google Scholar ] [ CrossRef ]
- Khadr, M.H.; Salameh, H.B.; Ayyash, M.; Elgala, H.; Almajali, S. Jamming resilient multi-channel transmission for cognitive radio IoT-based medical networks. J. Commun. Netw. 2022 , 24 , 666–678. [ Google Scholar ] [ CrossRef ]
- Chung, W.J. Modeling and Simulation of Replay Attack Detection using V2X Message in Autonomous Vehicles in WSN based IoT Environment. Int. J. Eng. Adv. Technol. 2020 , 9 , 1279–1286. [ Google Scholar ] [ CrossRef ]
- Yildirim, M.; Demiroğlu, U.; Şenol, B. An in-depth exam of IoT, IoT Core Components, IoT Layers, and Attack Types. Eur. J. Sci. Technol. 2021 , 28 , 665–669. [ Google Scholar ] [ CrossRef ]
- Ramadan, M.; Abdollahi, F. An active approach for isolating replay attack from sensor faults. Eur. J. Control 2023 , 69 , 100725. [ Google Scholar ] [ CrossRef ]
- Abdulla, H.; Al-Raweshidy, H.; SAwad, W. ARP Spoofing Detection for IoT Networks Using Neural Networks. SSRN Electron. J. 2020 , 20 , 1–9. [ Google Scholar ] [ CrossRef ]
- Singh, A.; Sikdar, B. Adversarial Attack and Defence Strategies for Deep-Learning-Based IoT Device Classification Techniques. IEEE Internet Things J. 2022 , 9 , 2602–2613. [ Google Scholar ] [ CrossRef ]
- Mehta, M.; Patel, K. Experimental Study of Location Spoofing and Identity Spoofing Attack in Internet of Things Network. Int. J. Intell. Inf. Technol. 2022 , 18 , 1–13. [ Google Scholar ] [ CrossRef ]
- Madhurikkha, S.; Sabitha, R. Hierarchical Honey Bee Model to Avoid Sleep Deprivation Attack in MANET. Int. J. Eng. Technol. 2018 , 7 , 358. [ Google Scholar ] [ CrossRef ]
- Vivekanadam, B. A Novel Hybrid HNN and Firefly Algorithm to Overcome Denial of Sleep Attack on Wireless Sensor Nodes. J. Ubiquitous Comput. Commun. Technol. 2021 , 2 , 223–227. [ Google Scholar ] [ CrossRef ]
- Bani-Yaseen, T.; Tahat, A.; Kastell, K.; Edwan, T.A. Denial-of-Sleep Attack Detection in NB-IoT Using Deep Learning. J. Telecommun. Digit. Econ. 2022 , 10 , 14–38. [ Google Scholar ] [ CrossRef ]
- Yoon, J. Deep-learning approach to attack handling of IoT devices using IoT-enabled network services. Internet Things 2020 , 11 , 100241. [ Google Scholar ] [ CrossRef ]
- Abbasi, M.; Plaza-Hernandez, M.; Prieto, J.; Corchado, J.M. Security in the Internet of Things Application Layer: Requirements, Threats, and Solutions. IEEE Access 2022 , 10 , 97197–97216. [ Google Scholar ] [ CrossRef ]
- Rodionov, A.; Belyanin, V.; Gorbunov, A. Improving the Methods for Protecting Information from Unauthorized Access. NBI Technol. 2018 , 2 , 39–43. [ Google Scholar ] [ CrossRef ]
- Aldhyani, T.H.H.; Alkahtani, H. Cyber Security for Detecting Distributed Denial of Service Attacks in Agriculture 4.0: Deep Learning Model. Mathematics 2023 , 11 , 233. [ Google Scholar ] [ CrossRef ]
- Jin, R.; Zhang, H.; Liu, D.; Yan, X. IoT-based detecting, locating and alarming of unauthorized intrusion on construction sites. Autom. Constr. 2020 , 118 , 103278. [ Google Scholar ] [ CrossRef ]
- Minu, R.I.; Nagarajan, G.; Munshi, A.; Venkatachalam, K.; Almukadi, W.; Abouhawwash, M. An Edge Based Attack Detection Model (EBAD) for Increasing the Trustworthiness in IoT Enabled Smart City Environment. IEEE Access 2022 , 10 , 89499–89508. [ Google Scholar ] [ CrossRef ]
- Tahir, M.; Sardaraz, M.; Muhammad, S.; Saud Khan, M. A Lightweight Authentication and Authorization Framework for Blockchain-Enabled IoT Network in Health-Informatics. Sustainability 2020 , 12 , 6960. [ Google Scholar ] [ CrossRef ]
- Ayfaa, B.; Apa, C. LMAAS-IoT: Lightweight Multi-factor Authentication and Authorization Scheme for Real-time Data Access in IoT Cloud-based Environment. J. Netw. Comput. Appl. 2021 , 192 , 103177. [ Google Scholar ] [ CrossRef ]
- Mohammad, A.; Al-Refai, H.; Alawneh, A.A. User Authentication and Authorization Framework in IoT Protocols. Computers 2022 , 11 , 147. [ Google Scholar ] [ CrossRef ]
- Mullen, G.; Meany, L. Assessment of buffer overflow based attacks on an IoT operating system. In Proceedings of the 2019 Global IoT Summit (GIoTS), Aarhus, Denmark, 17–21 June 2019; pp. 1–6. [ Google Scholar ] [ CrossRef ]
- Mazumdar, N.; Roy, S.; Nag, A.; Singh, J.P. A buffer-aware dynamic UAV trajectory design for data collection in resource-constrained IoT frameworks. Comput. Electr. Eng. 2022 , 100 , 107934. [ Google Scholar ] [ CrossRef ]
- Akhtar, M.S.; Feng, T. A Systemic Security and Privacy Review: Attacks and Prevention Mechanisms over IOT Layers. ICST Trans. Secur. Saf. 2022 , 8 , e5. [ Google Scholar ] [ CrossRef ]
- Zeng, J.Y.; Chang, L.E.; Cho, H.H.; Chen, C.Y.; Chao, H.C.; Yeh, K.H. Using Poisson Distribution to Enhance CNN-based NB-IoT LDoS Attack Detection. In Proceedings of the 2022 IEEE Conference on Dependable and Secure Computing (DSC), Edinburgh, UK, 22–24 June 2022; pp. 1–7. [ Google Scholar ]
- Rani, S.J.; Ioannou, I.; Nagaradjane, P.; Christophorou, C.; Vassiliou, V.; Charan, S.; Pitsillides, A. Detection of DDoS attacks in D2D communications using machine learning approach. Comput. Commun. 2023 , 198 , 32–51. [ Google Scholar ] [ CrossRef ]
- Kareem, M.K.; Aborisade, O.D.; Onashoga, S.A.; Sutikno, T.; Olayiwola, O.M. Efficient model for detecting application layer distributed denial of service attacks. Bull. Electr. Eng. Inform. 2023 , 12 , 441–450. [ Google Scholar ] [ CrossRef ]
- Alduais, N.; Abdullah, J.; Jamil, A. APRS: Adaptive real-time payload data reduction scheme for IoT/WSN sensor board with multivariate sensors. Int. J. Sens. Netw. 2018 , 28 , 211. [ Google Scholar ] [ CrossRef ]
- Khosravi, M.R.; Samadi, S. Efficient payload communications for IoT-enabled ViSAR vehicles using discrete cosine transform-based quasi-sparse bit injection. EURASIP J. Wirel. Commun. Netw. 2019 , 2019 , 262. [ Google Scholar ] [ CrossRef ]
- Wang, H.; Singhal, A.; Liu, P. Tackling imbalanced data in cybersecurity with transfer learning: A case with ROP payload detection. Cybersecurity 2023 , 6 , 2. [ Google Scholar ] [ CrossRef ]
- Jung, J.H.; Gohar, M.; Koh, S.J. CoAP-Based Streaming Control for IoT Applications. Electronics 2020 , 9 , 1320. [ Google Scholar ] [ CrossRef ]
- Gladson Oliver, S.; Purusothaman, T. Lightweight and Secure Mutual Authentication Scheme for IoT Devices Using CoAP Protocol. Comput. Syst. Sci. Eng. 2022 , 41 , 767–780. [ Google Scholar ] [ CrossRef ]
- Ahmad, M.Z.; Adenan, A.R.; Rohmad, M.S.; Yussoff, Y.M. Performance Analysis of Secure MQTT Communication Protocol. In Proceedings of the 2023 19th IEEE International Colloquium on Signal Processing & Its Applications (CSPA), Kedah, Malaysia, 3–4 March 2023; pp. 225–229. [ Google Scholar ] [ CrossRef ]
- Jang, W.; Jeong, D.; Lee, S. A Method of IoT Object Control based on MQTT for Enhancing Object Mobility. J. Korean Inst. Inf. Technol. 2022 , 20 , 107–119. [ Google Scholar ] [ CrossRef ]
- Husnain, M.; Hayat, K.; Cambiaso, E.; Fayyaz, U.U.; Mongelli, M.; Akram, H.; Ghazanfar Abbas, S.; Shah, G.A. Preventing MQTT Vulnerabilities Using IoT-Enabled Intrusion Detection System. Sensors 2022 , 22 , 567. [ Google Scholar ] [ CrossRef ]
- Celesti, A.; Fazio, M.; Villari, M. Enabling Secure XMPP Communications in Federated IoT Clouds Through XEP 0027 and SAML/SASL SSO. Sensors 2017 , 17 , 301. [ Google Scholar ] [ CrossRef ] [ PubMed ]
- Jun, H.J.; Yang, H.S. Performance of the XMPP and the MQTT Protocols on IEC 61850-Based Micro Grid Communication Architecture. Energies 2021 , 14 , 5024. [ Google Scholar ] [ CrossRef ]
- Yoshino, D.; Watanobe, Y.; Yaguchi, Y.; Nakamura, K.; Ogawa, J.; Naruse, K. AMQP Communication Interface on RT Middleware for highly-reliable IoR System Construction. Proc. JSME Annu. Conf. Robot. Mechatron. (Robomec) 2019 , 2019 , 2A1-M09. [ Google Scholar ] [ CrossRef ]
- Srivastava, A.; Shah, P. Identification of the Issues in IoT Devices with HSTS Not Enforced and Their Exploitation. In Proceedings of the 2021 International Conference on Security and Information Technologies with AI, Internet Computing and Big-Data Applications, Taichung City, Taiwan, 18–20 November 2021; Springer: Cham, Switzerland, 2023; pp. 325–334. [ Google Scholar ] [ CrossRef ]
- Chatzoglou, E.; Kouliaridis, V.; Kambourakis, G.; Karopoulos, G.; Gritzalis, S. A hands-on gaze on HTTP/3 security through the lens of HTTP/2 and a public dataset. Comput. Secur. 2023 , 125 , 103051. [ Google Scholar ] [ CrossRef ]
- Bezawada, B.; Bachani, M.; Peterson, J.; Shirazi, H.; Ray, I.; Ray, I. Behavioral fingerprinting of iot devices. In 2018 Workshop on Attacks and Solutions in Hardware Security ; ACM: New York, NY, USA, 2018; pp. 41–50. [ Google Scholar ] [ CrossRef ]
- Lee, S.; Abdullah, A.; Jhanjhi, N.; Kok, S. Classification of botnet attacks in IoT smart factory using honeypot combined with machine learning. PeerJ Comput. Sci. 2021 , 7 , e350. [ Google Scholar ] [ CrossRef ]
- Menard, P.; Bott, G.J. Analyzing IOT users’ mobile device privacy concerns: Extracting privacy permissions using a disclosure experiment. Comput. Secur. 2020 , 95 , 101856. [ Google Scholar ] [ CrossRef ]
- Bindrwish, F.B.; Ali, A.N.A.; Ghabban, W.H.; Alrowwad, A.; Fallatah, N.A.; Ameerbakhsh, O.; Alfadli, I.M. Internet of Things for Digital Forensics Application in Saudi Arabia. Adv. Internet Things 2023 , 13 , 1–11. [ Google Scholar ] [ CrossRef ]
- Shanmugapriya, R.; Santhosh Kumar, S.V.N. Comprehensive survey on data dissemination protocols for efficient reprogramming in Internet of Things. Concurr. Comput. Pract. Exp. 2022 , 34 , e7280. [ Google Scholar ] [ CrossRef ]
- Salah, S.; Amro, B.M. Big picture: Analysis of DDoS attacks map-systems and network, cloud computing, SCADA systems, and IoT. Int. J. Internet Technol. Secur. Trans. 2022 , 12 , 543–565. [ Google Scholar ] [ CrossRef ]
- Gowtham, M.; Pramod, H.B. Semantic Query-Featured Ensemble Learning Model for SQL-Injection Attack Detection in IoT-Ecosystems. IEEE Trans. Reliab. 2022 , 71 , 1057–1074. [ Google Scholar ] [ CrossRef ]
- Fanani, G.; Riadi, I. Analysis of Digital Evidence on Denial of Service (DoS) Attack Log Based. Bul. Ilm. Sarj. Tek. Elektro 2020 , 2 , 70. [ Google Scholar ] [ CrossRef ]
- Anthi, E.; Williams, L.; Javed, A.; Burnap, P. Hardening machine learning denial of service (DoS) defences against adversarial attacks in IoT smart home networks. Comput. Secur. 2021 , 108 , 102352. [ Google Scholar ] [ CrossRef ]
- Shah, Z.; Ullah, I.; Li, H.; Levula, A.; Khurshid, K. Blockchain Based Solutions to Mitigate Distributed Denial of Service (DDoS) Attacks in the Internet of Things (IoT): A Survey. Sensors 2022 , 22 , 1094. [ Google Scholar ] [ CrossRef ]
- Singhal, P.; Sharma, P.; Arora, D. An approach towards preventing iot based sybil attack based on contiki framework through cooja simulator. Int. J. Eng. Technol. 2018 , 7 , 261. [ Google Scholar ] [ CrossRef ]
- Pu, C.; Choo, K.K.R. Lightweight Sybil Attack Detection in IoT based on Bloom Filter and Physical Unclonable Function. Comput. Secur. 2022 , 113 , 102541. [ Google Scholar ] [ CrossRef ]
- Vaishnavi, S.; Sethukarasi, T. Retraction Note to: SybilWatch: A novel approach to detect Sybil attack in IoT based smart health care. J. Ambient Intell. Humaniz. Comput. 2022 , 14 , 539. [ Google Scholar ] [ CrossRef ]
- Tripathy, A.K.; Sinha, M.; Mishra, A.K. A sinkhole prevention mechanism for RPL in IoT. Int. J. Comput. Sci. Eng. 2020 , 23 , 262. [ Google Scholar ] [ CrossRef ]
- Jebadurai, I.J.; Paulraj, G.J.L.; Jebadurai, J. Mitigating Sinkhole attack in RPL based Internet of Things Environment using Optimized K means Clustering technique. In Proceedings of the 2022 6th International Conference on Electronics, Communication and Aerospace Technology, Coimbatore, India, 1–3 December 2022; pp. 502–507. [ Google Scholar ] [ CrossRef ]
- Bilal, A.; Hasany, S.M.N.; Pitafi, A.H. Effective modelling of sinkhole detection algorithm for edge-based Internet of Things (IoT) sensing devices. IET Commun. 2022 , 16 , 845–855. [ Google Scholar ] [ CrossRef ]
- Shiranzaei, A.; Khan, R.Z. An Approach to Discover the Sinkhole and Selective Forwarding Attack in IoT. J. Inf. Secur. Res. 2018 , 9 , 107. [ Google Scholar ] [ CrossRef ]
- Prathapchandran, K.; Janani, T. A trust aware security mechanism to detect sinkhole attack in RPL-based IoT environment using random forest—RFTRUST. Comput. Netw. 2021 , 198 , 108413. [ Google Scholar ] [ CrossRef ]
- An, G.H.; Cho, T.H. Improving Sinkhole Attack Detection Rate through Knowledge-Based Specification Rule for a Sinkhole Attack Intrusion Detection Technique of IoT. Int. J. Comput. Netw. Appl. 2022 , 9 , 169. [ Google Scholar ] [ CrossRef ]
- Yang, N.; Chen, K.; Wang, M. SmartDetour: Defending Blackhole and Content Poisoning Attacks in IoT NDN Networks. IEEE Internet Things J. 2021 , 8 , 12119–12136. [ Google Scholar ] [ CrossRef ]
- Kaur, R.; Sandhu, J.K.; Pundir, M.; Mehta, A. Blackhole Prevention Techniques Using Machine Learning. SSRN Electron. J. 2021 , 11 , 100241. [ Google Scholar ] [ CrossRef ]
- Kumar, R.; Venkanna, U.; Tiwari, V. A Time Granular Analysis of Software Defined Wireless Mesh Based IoT (SDWM-IoT) Network Traffic Using Supervised Learning. Wirel. Pers. Commun. 2020 , 116 , 2083–2109. [ Google Scholar ] [ CrossRef ]
- Shahraki, A.; Taherkordi, A.; Haugen, Y. TONTA: Trend-based Online Network Traffic Analysis in ad-hoc IoT networks. Comput. Netw. 2021 , 194 , 108125. [ Google Scholar ] [ CrossRef ]
- Mishra, S. Network traffic analysis using machine learning techniques in IoT network. Int. J. Veh. Inf. Commun. Syst. 2022 , 9 , 107–123. [ Google Scholar ] [ CrossRef ]
- Li, Y.; Qin, Y. Real-Time Cost Optimization Approach Based on Deep Reinforcement Learning in Software-Defined Security Middle Platform. Information 2023 , 14 , 209. [ Google Scholar ] [ CrossRef ]
- Kwon, S.; Park, S.; Cho, H.; Park, Y.; Kim, D.; Yim, K. Towards 5G-based IoT security analysis against Vo5G eavesdropping. Computing 2021 , 103 , 425–447. [ Google Scholar ] [ CrossRef ]
- Lauria, F. How to Footprint, Report and Remotely Secure Compromised IoT Devices. Netw. Secur. 2017 , 2017 , 10–16. [ Google Scholar ] [ CrossRef ]
- Tang, F.; Kawamoto, Y.; Kato, N.; Yano, K.; Suzuki, Y. Probe Delay Based Adaptive Port Scanning for IoT Devices with Private IP Address Behind NAT. IEEE Netw. 2020 , 34 , 195–201. [ Google Scholar ] [ CrossRef ]
- Gibson, D. IoT law and order. Netw. Secur. 2021 , 2021 , 20. [ Google Scholar ] [ CrossRef ]
- Nguyen-An, H.; Silverston, T.; Yamazaki, T.; Miyoshi, T. IoT Traffic: Modeling and Measurement Experiments. IoT 2021 , 2 , 140–162. [ Google Scholar ] [ CrossRef ]
- Kore, A.; Patil, S. IC-MADS: IoT Enabled Cross Layer Man-in-Middle Attack Detection System for Smart Healthcare Application. Wirel. Pers. Commun. 2020 , 113 , 727–746. [ Google Scholar ] [ CrossRef ]
- Kilinçer, L.F.; Ertam, F.; Şengür, A. Automated Fake Access Point Attack Detection and Prevention System with IoT Devices. Balk. J. Electr. Comput. Eng. 2020 , 8 , 50–56. [ Google Scholar ] [ CrossRef ]
- Jamil, H.; Ali, A.; Jamil, F. Spoofing Attack Mitigation in Address Resolution Protocol (ARP) and DDoS in Software-Defined Networking. J. Inf. Secur. Cybercrimes Res. 2022 , 5 , 31–42. [ Google Scholar ] [ CrossRef ]
- Banadaki, Y.M.; Robert, S. Detecting Malicious DNS over HTTPS Traffic in Domain Name System using Machine Learning Classifiers. J. Comput. Sci. Appl. 2020 , 8 , 46–55. [ Google Scholar ] [ CrossRef ]
- Humaira, F.; Islam, M.S.; Luva, S.A.; Rahman, M.B. A Secure Framework for IoT Smart Home by Resolving Session Hijacking. Glob. J. Comput. Sci. Technol. 2020 , 20 , 9–20. [ Google Scholar ] [ CrossRef ]
- Satapathy, A.; Livingston, J. A Comprehensive Survey on SSL/ TLS and their Vulnerabilities. Int. J. Comput. Appl. 2016 , 153 , 31–38. [ Google Scholar ] [ CrossRef ]
- Rouhani, S.; Belchior, R.; Cruz, R.S.; Deters, R. Distributed attribute-based access control system using permissioned blockchain. World Wide Web 2021 , 24 , 1617–1644. [ Google Scholar ] [ CrossRef ]
- Li, H.; Yu, K.; Liu, B.; Feng, C.; Qin, Z.; Srivastava, G. An Efficient Ciphertext-Policy Weighted Attribute-Based Encryption for the Internet of Health Things. IEEE J. Biomed. Health Inform. 2022 , 26 , 1949–1960. [ Google Scholar ] [ CrossRef ]
- Song, Q.; Chen, Y.; Zhong, Y.; Lan, K.; Fong, S.; Tang, R. A Supply-chain System Framework Based on Internet of Things Using Blockchain Technology. ACM Trans. Internet Technol. 2021 , 21 , 1–24. [ Google Scholar ] [ CrossRef ]
- Bouras, M.A.; Xia, B.; Abuassba, A.O.; Ning, H.; Lu, Q. IoT-CCAC: A blockchain-based consortium capability access control approach for IoT. PeerJ Comput. Sci. 2021 , 7 , e455. [ Google Scholar ] [ CrossRef ] [ PubMed ]
- Li, C.; Li, F.; Huang, C.; Yin, L.; Luo, T.; Wang, B. A Traceable Capability-based Access Control for IoT. Comput. Mater. Contin. 2022 , 72 , 4967–4982. [ Google Scholar ] [ CrossRef ]
- Fossen, K. Exploring Capability-Based Security in Software Design with Rust. Master’s Thesis, The University of Bergen, Bergen, Norway, 2022. Available online: https://hdl.handle.net/11250/3001153 (accessed on 5 February 2023).
- Saha, R.; Kumar, G.; Conti, M.; Devgun, T.; Kim, T.H.; Alazab, M.; Thomas, R. DHACS: Smart Contract-Based Decentralized Hybrid Access Control for Industrial Internet-of-Things. IEEE Trans. Ind. Inform. 2022 , 18 , 3452–3461. [ Google Scholar ] [ CrossRef ]
- El Bouanani, S.; El Kiram, M.A.; Achbarou, O.; Outchakoucht, A. Pervasive-Based Access Control Model for IoT Environments. IEEE Access 2019 , 7 , 54575–54585. [ Google Scholar ] [ CrossRef ]
- Astillo, P.V.; Kim, J.; Sharma, V.; You, I. SGF-MD: Behavior Rule Specification-Based Distributed Misbehavior Detection of Embedded IoT Devices in a Closed-Loop Smart Greenhouse Farming System. IEEE Access 2020 , 8 , 196235–196252. [ Google Scholar ] [ CrossRef ]
- Wang, Q.; Chen, D.; Zhang, N.; Qin, Z.; Qin, Z. LACS: A Lightweight Label-Based Access Control Scheme in IoT-Based 5G Caching Context. IEEE Access 2017 , 5 , 4018–4027. [ Google Scholar ] [ CrossRef ]
- Lee, W.; Jung, B.C.; Lee, H. DeCoNet: Density Clustering-Based Base Station Control for Energy-Efficient Cellular IoT Networks. IEEE Access 2020 , 8 , 120881–120891. [ Google Scholar ] [ CrossRef ]
- Yu, C.; Zhan, Y.; Sohail, M. SDSM: Secure Data Sharing for Multilevel Partnerships in IoT Based Supply Chain. Symmetry 2022 , 14 , 2656. [ Google Scholar ] [ CrossRef ]
- Sivaselvan, N.; Bhat, K.V.; Rajarajan, M.; Das, A.K.; Rodrigues, J.J.P.C. SUACC-IoT: Secure unified authentication and access control system based on capability for IoT. Clust. Comput. 2022 , 22 , 1–20. [ Google Scholar ] [ CrossRef ]
- Zhang, J.; Cheng, Z.; Cheng, X.; Chen, B. OAC-HAS: Outsourced access control with hidden access structures in fog-enhanced IoT systems. Connect. Sci. 2020 , 33 , 1060–1076. [ Google Scholar ] [ CrossRef ]
- Nakamura, S.; Enokido, T.; Takizawa, M. Information Flow Control Based on the CapBAC (Capability-Based Access Control) Model in the IoT. Int. J. Mob. Comput. Multimed. Commun. 2019 , 10 , 13–25. [ Google Scholar ] [ CrossRef ]
- Nakamura, S.; Enokido, T.; Takizawa, M. Information Flow Control Based on Capability Token Validity for Secure IoT: Implementation and Evaluation. Internet Things 2021 , 15 , 100423. [ Google Scholar ] [ CrossRef ]
- Silva, C.; Barraca, J.P. Dynamic Delegation-based Privacy Preserving in IoT Architectures. In Proceedings of the 2022 9th International Conference on Future Internet of Things and Cloud (FiCloud), Rome, Italy, 22–24 August 2022; pp. 46–54. [ Google Scholar ] [ CrossRef ]
- Pal, S.; Jadidi, Z. Protocol-Based and Hybrid Access Control for the IoT: Approaches and Research Opportunities. Sensors 2021 , 21 , 6832. [ Google Scholar ] [ CrossRef ]
- Namane, S.; Ben Dhaou, I. Blockchain-Based Access Control Techniques for IoT Applications. Electronics 2022 , 11 , 2225. [ Google Scholar ] [ CrossRef ]
- Nadkarni, A.; McCarthy, D.; Filkins, P.; Mehra, R. Internet of Things and Intelligent Edge: Infrastructure. IDC: The Premier Global Market Intelligence Company. Available online: https://www.idc.com/getdoc.jsp?containerId=IDC_P35569 (accessed on 30 December 2022).
- Kandele, S.; Paul, S. Key Assignment Scheme with Authenticated Encryption. IACR Trans. Symmetric Cryptol. 2018 , 2018 , 150–196. [ Google Scholar ] [ CrossRef ]
- Sarkar, A. A symmetric neural cryptographic key generation scheme for Iot security. Appl. Intell. 2022 , 22 , 1–19. [ Google Scholar ] [ CrossRef ]
- López Delgado, J.L.; Álvarez Bermejo, J.A.; López Ramos, J.A. Homomorphic Asymmetric Encryption Applied to the Analysis of IoT Communications. Sensors 2022 , 22 , 8022. [ Google Scholar ] [ CrossRef ]
- Suresh Kumar, M.; Purosothaman, T. Multivariate Broadcast Encryption with Group Key Algorithm for Secured IoT. Comput. Syst. Sci. Eng. 2023 , 45 , 925–938. [ Google Scholar ] [ CrossRef ]
- Liu, Z.; Seo, H. IoT-NUMS: Evaluating NUMS Elliptic Curve Cryptography for IoT Platforms. IEEE Trans. Inf. Secur. 2019 , 14 , 720–729. [ Google Scholar ] [ CrossRef ]
- Chauhan, C.; Ramaiya, M.K.; Rajawat, A.S.; Goyal, S.B.; Verma, C.; Raboaca, M.S. Improving IoT Security Using Elliptic Curve Integrated Encryption Scheme with Primary Structure-Based Block Chain Technology. Procedia Comput. Sci. 2022 , 215 , 488–498. [ Google Scholar ] [ CrossRef ]
- Han, K.; Lee, W.K.; Hwang, S.O. cuGimli: Optimized implementation of the Gimli authenticated encryption and hash function on GPU for IoT applications. Clust. Comput. 2021 , 25 , 433–450. [ Google Scholar ] [ CrossRef ]
- Chien, H.-Y. Two-Level-Composite-Hashing Facilitating Highly Efficient Anonymous IoT and D2D Authentication. Electronics 2021 , 10 , 789. [ Google Scholar ] [ CrossRef ]
- Braghin, C.; Lilli, M.; Riccobene, E. A Model-based approach for Vulnerability Analysis of IoT Security Protocols: The Z-Wave case study. Comput. Secur. 2022 , 127 , 103037. [ Google Scholar ] [ CrossRef ]
- Castellon, C.E.; Roy, S.; Kreidl, O.P.; Dutta, A.; Bölöni, L. Towards an Energy-Efficient Hash-based Message Authentication Code (HMAC). In Proceedings of the 2022 IEEE 13th International Green and Sustainable Computing Conference (IGSC), Pittsburgh, PA, USA, 24–25 October 2022; pp. 1–7. [ Google Scholar ] [ CrossRef ]
- Narlagiri, S.; Malathy, V.; Sudharani, C.; Sridevi, C.; Chakradhar, A. Modified advanced encryption standard using cipher based message authentication code algorithm. In Proceedings of the AIP Conference Proceedings, Sathyamangalam, India, 25–26 March 2022; AIP Publishing LLC: Melville, NY, USA, 2022; Volume 2418, p. 030011. [ Google Scholar ] [ CrossRef ]
- Kureshi, R.R.; Mishra, B.K. A Comparative Study of Data Encryption Techniques for Data Security in the IoT Device. In Internet of Things and Its Applications ; Springer: Singapore, 2022; pp. 451–460. [ Google Scholar ] [ CrossRef ]
- Rivero, J.; Huynh, T.N.B.; Smith-Evans, A.; Thao, O.; Cheng, Y. Analyzing the Efficiency of Lightweight Symmetric Ciphers on IoT Devices. California State University Sacramento . 2021, pp. 1–6. Available online: https://scholarworks.calstate.edu/downloads/m326m683z (accessed on 27 February 2023).
- Altameem, A.; Poonia, R.C.; Saudagar, A.K.J. A Hybrid AES with a Chaotic Map-Based Biometric Authentication Framework for IoT and Industry 4.0. Systems 2023 , 11 , 28. [ Google Scholar ] [ CrossRef ]
- Tsantikidou, K.; Sklavos, N. Hardware Limitations of Lightweight Cryptographic Designs for IoT in Healthcare. Cryptography 2022 , 6 , 45. [ Google Scholar ] [ CrossRef ]
- Hsiao, F.H. Chaotic synchronization cryptosystems using a Twofish encryption algorithms. Asian J. Control 2022 , 24 , 1022–1041. [ Google Scholar ] [ CrossRef ]
- Bhagat, V.; Kumar, S.; Gupta, S.K.; Chaube, M.K. Lightweight cryptographic algorithms based on different model architectures: A systematic review and futuristic applications. Concurr. Comput. Pract. Exp. 2023 , 35 , e7425. [ Google Scholar ] [ CrossRef ]
- Hachim, E.A.W.; Abbas, T.; Gaata, M.T. Modified RC4 Algorithm for Improve Data Protection in Cloud Environment. In Proceedings of the 2022 International Conference on Information Technology Systems and Innovation (ICITSI), Bandung, Indonesia, 8–9 November 2022; pp. 295–299. [ Google Scholar ] [ CrossRef ]
- Najm, H. Data authentication for web of things (WoT) by using modified secure hash algorithm-3 (SHA-3) and Salsa20 algorithm. Turk. J. Comput. Math. Educ. (TURCOMAT) 2021 , 12 , 2541–2551. [ Google Scholar ] [ CrossRef ]
- Paul, K. Vulnerability Analysis of Salsa20: Differential Analysis and Deep Learning Analysis of Salsa20. Master’s Thesis, Universitetet i Sørøst-Norge, Norge, Norway, 2020. [ Google Scholar ]
- Aamir, M.; Sharma, S.; Grover, A. ChaCha20-in-Memory for Side-Channel Resistance in IoT Edge-Node Devices. IEEE Open J. Circuits Syst. 2021 , 2 , 833–842. [ Google Scholar ] [ CrossRef ]
- Serrano, R.; Duran, C.; Sarmiento, M.; Pham, C.K.; Hoang, T.T. ChaCha20–Poly1305 Authenticated Encryption with Additional Data for Transport Layer Security 1.3. Cryptography 2022 , 6 , 30. [ Google Scholar ] [ CrossRef ]
- Liu, W.; Gao, J. Quantum security of Grain-128/Grain-128a stream cipher against HHL algorithm. Quantum Inf. Process. 2021 , 20 , 1–22. [ Google Scholar ] [ CrossRef ]
- Carlson, A.; Dutta, I.; Ghosh, B. Using the Collision Attack for Breaking Cryptographic Modes. In Proceedings of the 2022 13th International Conference on Computing Communication and Networking Technologies (ICCCNT), Kharagpur, India, 3–5 October 2022; pp. 1–7. [ Google Scholar ] [ CrossRef ]
- Madani, M.; Tanougast, C. FPGA implementation of an optimized A5/3 encryption algorithm. Microprocess. Microsyst. 2020 , 78 , 103212. [ Google Scholar ] [ CrossRef ]
- Gundaram, P.K.; Tentu, A.N.; Allu, S.N. State Transition Analysis of GSM Encryption Algorithm A5/1. J. Commun. Softw. Syst. 2022 , 18 , 36–41. [ Google Scholar ] [ CrossRef ]
- Zhang, B. Cryptanalysis of GSM encryption in 2G/3G networks without rainbow tables. In Proceedings of the25th International Conference on the Theory and Application of Cryptology and Information Security, Kobe, Japan, 8–12 December 2019; Springer: Cham, Switzerland, 2019; pp. 428–456. [ Google Scholar ] [ CrossRef ]
- Muthalagu, R.; Jain, S. A novel modified KASUMI block chiper for global system for mobile communications. Int. J. Comput. Appl. 2021 , 43 , 805–811. [ Google Scholar ] [ CrossRef ]
- Manz, O. Symmetric Ciphers. In Encrypt, Sign, Attack. Mathematics Study Resources ; Springer: Berlin/Heidelberg, Germany, 2022; Volume 4. [ Google Scholar ] [ CrossRef ]
- Kumar, A.; Mishra, P.R.; Pal, S.K.; Ojjela, O. Analysis of variability and degree of non-linearity of HC-128. J. Discret. Math. Sci. Cryptogr. 2021 , 24 , 2093–2108. [ Google Scholar ] [ CrossRef ]
- Walden, J. The impact of a major security event on an open source project: The case of OpenSSL. In Proceedings of the 17th International Conference on Mining Software Repositories, Seoul, Republic of Korea, 29–30 June 2020; pp. 409–419. [ Google Scholar ] [ CrossRef ]
- Alrowaithy, M.; Thomas, N. Investigating the performance of C and C++ cryptographic libraries. In Proceedings of the 12th EAI International Conference on Performance Evaluation Methodologies and Tools, Palma, Spain, 12–15 March 2019; pp. 167–170. [ Google Scholar ] [ CrossRef ]
- Boesgaard, M.; Vesterager, M.; Zenner, E. Information on RFC 4503. 21 January 2021. Available online: https://www.rfc-editor.org/info/rfc4503 (accessed on 13 January 2023).
- Surantha, N. Secure Portable Virtual Private Network with Rabbit Stream Cipher Algorithm. Procedia Comput. Sci. 2018 , 135 , 259–266. [ Google Scholar ] [ CrossRef ]
- Marpaung, J.A.; Ndibanje, B.; Lee, H.J. Higher-Order Countermeasures against Side-Channel Cryptanalysis on Rabbit Stream Cipher. J. Inf. Commun. Converg. Eng. 2014 , 12 , 237–245. [ Google Scholar ] [ CrossRef ]
- Sajid, F.; Hassan, M.A.; Khan, A.A.; Rizwan, M.; Kryvinska, N.; Vincent, K.; Khan, I.U. Secure and Efficient Data Storage Operations by Using Intelligent Classification Technique and RSA Algorithm in IoT-Based Cloud Computing. Sci. Program. 2022 , 2022 , 2195646. [ Google Scholar ] [ CrossRef ]
- Bhutta, M.N.M.; Bhattia, S.; Alojail, M.A.; Nisar, K.; Cao, Y.; Chaudhry, S.A.; Sun, Z. Towards Secure IoT-Based Payments by Extension of Payment Card Industry Data Security Standard (PCI DSS). Wirel. Commun. Mob. Comput. 2022 , 2022 , 9942270. [ Google Scholar ] [ CrossRef ]
- Kerry, C.F.; Gallagher, P.D. Digital Signature Standard (DSS) ; FIPS PUB 186–4; Information Technology Laboratory, National Institute of Standards and Technology: Gaithersburg, MD, USA, 2013. [ Google Scholar ]
- Alhayani, B.S.; Hamid, N.; Almukhtar, F.H.; Alkawak, O.A.; Mahajan, H.B.; Kwekha-Rashid, A.S.; Alkhayyat, A. Optimized video internet of things using elliptic curve cryptography based encryption and decryption. Comput. Electr. Eng. 2022 , 101 , 108022. [ Google Scholar ] [ CrossRef ]
- Verma, U.; Bhardwaj, D. A secure lightweight anonymous elliptic curve cryptography-based authentication and key agreement scheme for fog assisted-Internet of Things enabled networks. Concurr. Comput. Pract. Exp. 2022 , 34 , e7172. [ Google Scholar ] [ CrossRef ]
- Matiyko, A.A. The Comparative Analysis of NTRUCipher and NTRUEncrypt Encryption Schemes. Mathematical and Computer Modelling. Ser. Tech. Sci. 2019 , 19 , 81–87. [ Google Scholar ] [ CrossRef ]
- DENIAL. Bouncycastle Fails NTRU Generation. Stack Overflow. 15 April 2014. Available online: https://stackoverflow.com/questions/23095051/bouncycastle-fails-ntru-generation (accessed on 13 January 2023).
- Hauser, F.; Haberle, M.; Schmidt, M.; Menth, M. P4-IPsec: Site-to-Site and Host-to-Site VPN With IPsec in P4-Based SDN. IEEE Access 2020 , 8 , 139567–139586. [ Google Scholar ] [ CrossRef ]
- Hong, S. Issues and Security on IPSec: Survey. J. Digit. Converg. 2014 , 12 , 243–248. [ Google Scholar ] [ CrossRef ]
- Khan, A.F.; Anandharaj, G. A Multi-layer Security approach for DDoS detection in Internet of Things. Int. J. Intell. Unmanned Syst. 2020 , 9 , 178–191. [ Google Scholar ] [ CrossRef ]
- Aravind, K.A.; Naik, B.R.; Chennarao, C.S. Combined Digital Signature with SHA Hashing Technique-based Secure System: An Application of Blockchain using IoT. Turk. J. Comput. Math. Educ. (TURCOMAT) 2022 , 13 , 402–418. [ Google Scholar ]
- Varo, Q.; Lardier, W.; Yan, J. Dynamic Reduced-Round TLS Extension for Secure and Energy-Saving Communication of IoT Devices. IEEE Internet Things J. 2022 , 9 , 23366–23378. [ Google Scholar ] [ CrossRef ]
- Kumari, N.; Mohapatra, A.K. A comprehensive and critical analysis of TLS 1.3. J. Inf. Optim. Sci. 2022 , 43 , 689–703. [ Google Scholar ] [ CrossRef ]
- Alwazzeh, M.; Karaman, S.; Shamma, M.N. Man in The Middle Attacks Against SSL/TLS: Mitigation and Defeat. J. Cyber Secur. Mobil. 2020 , 9 , 449–468. [ Google Scholar ] [ CrossRef ]
- Timko, A.M. Cybersecurity of Internet of Things Devices: A Secure Shell Implementation. 2022. Available online: https://urn.fi/URN:NBN:fi:amk-202205139197 (accessed on 10 March 2023).
- Kaiser. SSH Client/Server for SM-R760. SSH Client/Server for SM-R760|Tizen Developers. 3 February 2001. Available online: https://developer.tizen.org/forums/general-support/ssh-clientserver-sm-r760 (accessed on 13 January 2023).
- Ganeshkumar, P.; Albalawi, T. A Locality-Sensitive Hashing-Based Jamming Detection System for IoT Networks. Comput. Mater. Contin. 2022 , 73 , 5943–5959. [ Google Scholar ] [ CrossRef ]
- Khadidos, A.O.; Shitharth, S.; Khadidos, A.O.; Sangeetha, K.; Alyoubi, K.H. Healthcare Data Security Using IoT Sensors Based on Random Hashing Mechanism. J. Sens. 2022 , 2022 , 1–17. [ Google Scholar ] [ CrossRef ]
- Wang, F.; Zhu, M.; Wang, M.; Khosravi, M.R.; Ni, Q.; Yu, S.; Qi, L. 6G-Enabled Short-Term Forecasting for Large-Scale Traffic Flow in Massive IoT Based on Time-Aware Locality-Sensitive Hashing. IEEE Internet Things J. 2021 , 8 , 5321–5331. [ Google Scholar ] [ CrossRef ]
- Lin, C.H.; Liu, J.C.; Chen, J.I.Z.; Chu, T.P. On the Performance of Cracking Hash Function SHA-1 Using Cloud and GPU Computing. Wirel. Pers. Commun. 2019 , 109 , 491–504. [ Google Scholar ] [ CrossRef ]
- Martino, R.; Cilardo, A. Designing a SHA-256 processor for blockchain-based IoT applications. Internet Things 2020 , 11 , 100254. [ Google Scholar ] [ CrossRef ]
- Zellagui, A.; Hadj-Said, N.; Ali-Pacha, A. Comparative Study Between Merkle-Damgård And Other Alternative Hashes Construction. In Proceedings of the Second Conference on Informatics and Applied Mathematics IAM, Guelma, Algeria, 24–25 April 2019; Volume 180, pp. 30–34. [ Google Scholar ]
- Al-Odat, Z.A.; Khan, S.U.; Al-Qtiemat, E. A modified secure hash design to circumvent collision and length extension attacks. J. Inf. Secur. Appl. 2022 , 71 , 103376. [ Google Scholar ] [ CrossRef ]
- Tang, Y.; Zeng, G.; Han, W. Classification of disturbance vectors for collision attack in SHA-1. Sci. China Inf. Sci. 2015 , 58 , 1–10. [ Google Scholar ] [ CrossRef ]
- Kumar, K.K.; Ramaraj, E.; Srikanth, B.; Rao, A.S.; Prasad, P.B.V.N. Role of MD5 Message-Digest Algorithm for Providing Security to Low-Power Devices. In Proceedings of the 2022 6th International Conference on Intelligent Computing and Control Systems (ICICCS), Madurai, India, 25–27 May 2022; pp. 352–358. [ Google Scholar ] [ CrossRef ]
- Kuznetsov, A. Parallel algorithm for MD5 collision attack. Program Syst. Theory Appl. 2015 , 6 , 61–72. [ Google Scholar ] [ CrossRef ]
- RFC 7693. BLAKE2. BLAKE2—Fast Secure Hashing. 13 June 2018. Available online: https://www.blake2.net/ (accessed on 14 January 2023).
- EL Makhtoum, H.; Bentaleb, Y. Comparative Study of Keccak and Blake2 Hash Functions. In Networking, Intelligent Systems and Security ; Springer: Singapore, 2022; pp. 343–350. [ Google Scholar ] [ CrossRef ]
- Liu, F.; Dobraunig, C.; Mendel, F.; Isobe, T.; Wang, G.; Cao, Z. Efficient collision attack frameworks for RIPEMD-160. In Proceedings of the 39th Annual International Cryptology Conference, Santa Barbara, CA, USA, 18–22 August 2019; Springer: Cham, Switzerland, 2019; pp. 117–149. [ Google Scholar ] [ CrossRef ]
- Asare, B.T.; Quist-Aphetsi, K.; Nana, L. Using RC4 and whirlpool for the encryption and validation of data in IoT. In Proceedings of the 2019 International Conference on Cyber Security and Internet of Things (ICSIoT), Accra, Ghana, 29–31 May 2019; pp. 114–117. [ Google Scholar ] [ CrossRef ]
- Venkatesan, R.; Srinivasan, B.; Rajendiran, P. Tiger hash based AdaBoost machine learning classifier for secured multicasting in mobile healthcare system. Clust. Comput. 2019 , 22 , 7039–7053. [ Google Scholar ] [ CrossRef ]
- Waguie, F.T.; Al-Turjman, F. Artificial Intelligence for Edge Computing Security: A Survey. In Proceedings of the 2022 International Conference on Artificial Intelligence in Everything (AIE), Lefkosa, Cyprus, 2–4 August 2022; pp. 446–450. [ Google Scholar ] [ CrossRef ]
- Arp, D.; Quiring, E.; Pendlebury, F.; Warnecke, A.; Pierazzi, F.; Wressnegger, C.; Rieck, K. Dos and don’ts of machine learning in computer security. arXiv 2020 , arXiv:2010.09470. [ Google Scholar ]
Click here to enlarge figure
| Wireless Communication Technology | ZigBee | BLE | 6LoWPAN | LoRaWAN |
|---|---|---|---|---|
| Mesh topology | Mesh topology | Mesh topology | Star topology | |
| 1–100 m | Approximately 10 m | ~200 m max. | 6.2 miles max. | |
| 12 μA | 9 μA 0.4 μA at low energy | 12 μA | 7.66 μA to 34 μA | |
| 50 mA | 35 mA | >40 mA | >34 mA | |
| 52 mA | 37 mA | >50 mA | >52 mA | |
| ✓ | x | ✓ | ✓ | |
| x | x | ✓ | ✓ | |
| (VBAT) | 3.3 V | 3.3 V | 3.3 V | 4.2 V |
| Home Automation, Embedded Sensing, Industrial Control Systems | Transfer Data Files, Data Logging Equipment, Short-range Data Transmission | Transmission of IPv6 Packets, Wireless Sensor Networks (WSN), Low-power Mesh networks | Smart City, Chirp Spread Spectrum (CSS) technology | |
| 1 or 0 | 1 or 0 | 1 or 0 | 1 or 0 |
| Attack | Portrayal | Purpose |
|---|---|---|
| Intrusion into a node [ , ] | IoT nodes are the components of an IoT ecosystem that facilitate data transfer between devices in the real world and the cloud. These devices are envisioned as aggregators of data from several sensors coming from various sources. The attacker makes changes to the nodes or disrupts their functions and then acquires full control of the node. This exploit damages the hardware, which will reduce the availability of resources. | Attacks that entail tampering with the device can take advantage of newly discovered vulnerabilities and exploit them. In point of fact, they are a type of physical attack in which the attacker attempts to break security after first attempting to corrupt the memory or the computation, and then gaining further knowledge by interacting with the IoT equipment. This occurs after the attacker has attempted to break security by corrupting the memory or the computation. Following this, the attacker will try to circumvent the security. |
| Node Dependency Injection [ , ] | When one or more dependents (or services) are “injected” into a reliant entity, they are given by reference to the instrument. This can be done with several dependents at the same time. The term “dependency injection” refers to this specific approach to creating software applications. Moreover, when an adversary injects fake nodes into a complete network, this is known as fake node injection. This occurs when the adversary inserts counterfeit nodes into the linked authorized nodes of the network. | It grants the attacker the ability to exert control over the data stream. The need to govern the data flow will arise as a direct consequence of this attack. Any kind of data might be susceptible to being processed by an opponent, who could then take control of it. A variety of different physical devices might be compromised by using this attack. When working in an environment such as this one, establishing reliable connections between every sensor/IoT node and the user who will ultimately be using the system is of the highest importance. |
| Node Acquisition Attack [ , ] | A typical example of a physical attack on a network is the capture of a node and subsequent extraction of its ciphering data. Later, it will be used to initiate more exploits within the network. There are several different types of IoT Node Acquisition Attacks, including spoofing, jamming, physical compromise, supply chain attack, firmware attack, and malware. | The adversary’s purpose is to trick the unidentified nodes into thinking they are at a known location by manipulating the signals between known nodes or by posing as a recognized node to falsify, change, or replay signals. With that in mind, precautions must be taken to ensure the estimated locations remain accurate even when under attack. |
| Eavesdropping Attack [ , ] | Eavesdropping attacks, in which hackers listen in on normally private network traffic, can successfully target any device connected to the Internet of Things (IoT). Types of eavesdropping attacks include passive eavesdropping, active eavesdropping, phishing and spear phishing attacks, drive-by attack, password attack, SQL injection attack, cross-site scripting (XSS) attack, eavesdropping attack, device fingerprinting, malware, and AI-powered IoT-based attacks. | Eavesdropping can occur when a connection between two endpoints is neither secure nor sufficiently strong. This leaves the link vulnerable to assault. Lack of encryption, outdated software or hardware, malware infection, or a mix of the three is all potential causes of unprotected switches and routers. Eavesdropping attacks might yield a large reward for the perpetrators. Information such as credit card numbers, names, addresses, phone numbers, email addresses, passwords, and even privileged information might be stolen. |
| Node Cloning [ , ] | Most IoT installations are placed in unrestricted, potentially dangerous areas. Consequently, they are extremely susceptible to intrusions through clone nodes or node replication. Some common types of Node Cloning Attacks in IoT are physical cloning, software cloning, address spoofing, configuration injection, replay attack, and side-channel attacks. | Capturing valid IoT devices allows the attacker to extract them, get access to important data such as node ID and keys, and launch a replication operation. If an attacker uses this vulnerability, he or she can eventually take over the entire network and do any action permitted by the approved nodes. |
| Radio Frequency (RF) Jamming [ , ] | One of the most common and successful forms of exploitation is the jamming of infrastructure communication, which disrupts or halts data transmission through the system. Jamming occurs when an adversary takes over the channel where legitimate nodes are trying to communicate. Many methods exist for an attacker to cause interference and clutter in the wireless frequency. One method is to flood the network with noise in the form of continual, uncontrolled data transmissions. It is also possible that there is a constantly high volume of data transmitting valid frames but just taking up all the available bandwidth. Some of the common types of RF Jamming attacks include pulse jamming, continuous wave jamming, random jamming, selective jamming, and reactive jamming. | The majority of devices include RF capabilities for sharing data wirelessly. A denial-of-service attack can be caused by any circumstance preventing normal data transmission. |
| Replay Attack [ , , ] | When a malicious user falsely delays or retransmits a secure network message to trick the intended recipient into performing the hacker’s desired action, this is known as a replay attack. Several types of replay attacks can be used against IoT devices, including authentication replay attacks, session hijacking replay attacks, and encrypted data replay attacks. In an authentication replay attack, an attacker can intercept an authentication request and then delay or repeat it in order to gain access to a system. In a session hijacking replay attack, an attacker can intercept a valid session and use it to bypass authentication and access the system. In an encrypted data replay attack, an attacker can intercept and replay encrypted data in order to gain access to confidential information. | To steal private information, hack into secure networks, or make identical transactions are common goals of replay attacks. To protect against these types of attacks, devices should be secured with encryption, authentication, and authorization. Additionally, monitoring devices for suspicious activity and regularly patching any vulnerabilities is important. |
| Device Spoofing Attack [ , , ] | Spoofing occurs when a linked IoT network suffers a cybersecurity failure at a lower layer. When, for instance, a computer system containing financial information is connected to the same IoT network as a Zigbee-enabled smart appliance with minimal security measures in place. In this context, “device spoofing” refers to the process of impersonating a different device using specialized software. The tools can fake software and hardware characteristics to deceive surveillance software. Some of the most occurring vulnerabilities are MAC address spoofing, IP address spoofing, DNS spoofing, HTTP spoofing, IoT cloud spoofing, and node spoofing. | It is a practice of impersonating a trusted entity to gain access to protected resources, commit fraud, steal sensitive information, obtain financial gain, or distribute malicious codes. A wide variety of spoofing attacks relate to data, domain, IP, and ARP. A few methods can be used to help prevent an IoT device spoofing attack. The first is to ensure that all devices on the network have strong authentication methods in place, such as passwords and two-factor authentication. Additionally, it is important to keep all devices up to date with the latest security patches and updates. It is also important to use encryption technologies such as a Secure Socket Layer (SSL) or Transport Layer Security (TLS) to protect data transmissions. Finally, it is important to enabling firewalls and network address translation (NAT) to protect the network from outside access. |
| Sleep Deprivation Attack [ , , ] | As part of a sleep deprivation or denial-of-sleep exploit, a malevolent device transmits requests to target endpoints only at the frequency required for keeping them active. Therefore, unlike in a barrage assault, the target devices are kept awake but are not forced to carry out any particularly taxing tasks. There are several types of IoT sleep deprivation attacks. These include flooding the target device with requests, sending malicious code to disrupt its sleep cycle, and exploiting vulnerabilities in the device’s firmware to prevent it from entering a low-power state. Additionally, some attackers may attempt to use social engineering tactics to induce the user to keep the device active and thus prevent it from entering a low-power state. | The interactions are meant to prevent the victim node from entering a power-saving sleep state. As a result, the victim’s lifespan can be drastically shortened by this attack. |
| Temporary Disabling Attack (TDA) [ , ] | The malware injected into an IoT system by an attacker can compromise its integrity and allow for the theft of sensitive information or the implementation of additional attacks. Furthermore, if vendors do not guarantee proper software protection, certain systems might be compromised with viruses’ right out of the box. IoT devices are particularly vulnerable to TDA attacks because of their limited processing capability. Thus, several types of IoT temporary disabling attacks exist, including exploiting hardware or firmware vulnerabilities, distributed denial-of-service (DDoS) attacks, flooding servers with requests, and using malicious scripts to disable devices. Additionally, attackers may use physical access to the device to temporarily disable it, such as unplugging it or removing its battery. | Denial-of-service attacks, such as TDA hinder a system’s ability to handle legitimate requests by flooding it with spam. In most cases, these attacks are used to disrupt services or interfere with the normal functioning of the device, but in some cases, the goal may be access to the device or its data. |
| Unauthorized Access Attack [ , , , ] | The term “unauthorized access” describes when hackers enter a system without authorization. Passwords that are too easy to crack, a failure to safeguard against thought control, hacked credentials, and even insider threats all contribute to the prevalence of these types of attacks. Types of unauthorized access attacks include a brute force attack, man-in-the-middle attack, IoT-focused phishing attacks, and social engineering attacks that attempt to trick device users into revealing sensitive information. Extensive monitoring of shadow devices and regular software updates can furnish safeguard against such attacks. | Access is gained to an IoT system by an unauthorized user/device who intends to commit an attack of some kind, whether it relates to data theft, system destruction, or the activation of a ransomware vulnerability. |
| Authentication and Authorization [ , , ] | Whether an individual is using an IoT device for home automation or a major corporation is using hundreds of IoT devices to track and monitor processes and resources, authentication and authorization are crucial components of security breaches. The first step in developing an IoT authentication and authorization strategy is gaining an in-depth knowledge of the organization’s IoT usage and network communication patterns. Some common types of authentication and authorization attacks in IoT include password attacks (i.e., brute force or dictionary attacks), man-in-the-middle attacks, spoofing attacks, repudiation attacks, and session hijacking attacks. | For devices that can only communicate to one other device, “one-way authentication” is the best option for establishing trust. It is still important to implement security measures, although constant monitoring is not required for such setups. The process of two devices engaging with each other verifying the identities of the other device before transferring data is referred to as “mutual authentication”. Both devices need to be able to compare their IDs and maintain access to the technologies used by the other gadgets. Unless both devices trust each other’s digital certificates, there will be no way for them to talk to each other. Through the TLS protocol, certifications can be transferred and compared. Devices are authorized in three separate ways using the “centralized three-way authentication” approach, which requires a valid digital certificate to be registered with a central authority or server. The trustworthy third-party acts as an intermediary between the communication devices to facilitate the transfer of cryptographic guarantees. Hackers are unable to steal the three-factor authentication security certificates since they are not stored on the devices. |
| Buffer-overflow Attack [ , , ] | Overflow happens when more data is being stored than can fit in a buffer. When the IoT application tries to save the input to the buffer, it writes over the neighboring system memory, which can cause serious issues. A system can be exploited by malicious actors that are aware of its storage architecture if they purposefully feed it data that exceeds the capacity of the buffer or if they get access to the system and modify the source code stored in the system’s memory. Buffer overflow attacks in IoT can take several forms, including stack-based buffer overflows, heap-based buffer overflows, format string attacks, integer overflows, and stack smashing. | By far, the most common kind of buffer overflow exploits the ephemeral data on the stack, which is reserved for use within a function. It is more challenging to carry out a heap-based attack since doing so necessitates using more memory than the system has allotted to the program, which is needed for its continuous dynamic activities. To prevent this type of attack, IoT developers should ensure that their code is secure by using secure coding practices and ensuring all buffers are properly allocated and all input is validated. Additionally, security patches should be consistently applied to ensure that any newly discovered vulnerabilities are addressed. |
| DDoS (Slowloris) Attack [ , , ] | Slowloris is an application layer distributed denial-of-service (DDoS) attack that overloads and eventually shuts down a target Web server by repeatedly delivering unclear Hypertext Transfer Protocol (HTTP) requests from a single IoT device. This specific DDoS attack can be launched with minimal bandwidth while leaving other applications and ports unaffected. A Slowloris attack can take several forms, including HTTP flood, SYN flood, DNS amplification, SQLi, ICMP Echo request attack, and fraggal attack. | The attack of a Slowloris is deliberate and meticulous in nature. A series of incomplete connection requests are sent to the vulnerable central server. Therefore, the intended server responds to requests by opening additional connections. All the server’s available sockets for connections will be used up quickly, preventing any new connections from being established. In the end, even though it may take a while for Slowloris to totally take over high-traffic services, the DDoS attack will cause all legitimate requests to be refused. |
| Large Payload Transfer Attack [ , , ] | The current utilization of the Internet of Things involves various applications that require large payload transfer, such as uploading medical data, transmitting audio data from medical devices, detecting vehicle crashes through digital audio, uploading images related to traffic crimes, and uploading binary files generated by industrial machines. Nevertheless, if such data transfers are initiated by devices controlled by hackers, they must be treated as anomalous and potentially malicious. | Complex and large payload transfer can have devastating impact on data transfer messaging protocols namely Constrained Application Protocol (CoAP) [ , ], MQ Telemetry Transport (MQTT) [ , , ], Extensible Messaging and Presence Protocol (XMPP) [ , ], Advanced Message Queuing Protocol (AMQP) [ ], and HTTP [ , ] Anomaly can trigger latency in constant and real-time data transfers. It is crucial to minimize data packet latency and inefficiency without compromising on reliability. It is worth highlighting that a certain amount of inefficiency is necessary for maintainability, flexibility, and testability in an IoT network; without it, these features would be impossible. |
| Mimicked Device Behavior [ , ] | Behaviors are incorporated into a IoT node Security Profile. For each pattern, the applied protocol will find an associated metric that defines the baseline performance of IoT devices as a whole or as a subset. There are two broad types of actions: behavioral patterns can be detected by either rules or machine learning (ML). ML utilizes past device data to analyze device behavior, whereas rules lets the administrator specify the device behavior. Both machine learning and rule-based thresholds are viable options for a Security Profile to mimic device behavior. Mimicked Device Behavior Attacks in the IoT include malicious software injection attacks, command and control (C&C) attacks, botnet attacks, data manipulation attacks, and rogue access point attacks. | Device behavior analysis triggered by hackers can lead to revealing critical information and may compromise data related to scalability and reliability of IoT network, user’s private data and device design flaws. |
| Permissions Manipulation [ , ] | The term “permission” refers to the action of bestowing rights upon a verified individual or entity. Authenticated identities in an IoT environment have their capabilities constrained by fundamental regulations. Devices, mobile apps, online apps, and desktop apps all rely on an authorized identity. The types of Permissions Manipulation Attacks in IoT include privilege escalation, horizontal attacks (i.e., attackers can gain access to accounts with limited permissions and then attempt to escalate privileges to gain more), data leaks, and DoS attacks. | The IoT’s inclination to cache copies of policy implies that it may take a few minutes for an adversary’s alterations to bring an action. Then it might take a few seconds to obtain a connection to a resource once it has been introduced to the network, and it can continue to be available for some time after access has been revoked. |
| Payload Flooding [ , ] | In communications networks, inundation is a straightforward routing approach in which a source or node broadcasts packets over all available outbound connections. When originating packets (lacking routing data) are sent to entire connected network, a phenomenon known as flooding unfolds. Payload Flooding Attacks in the IoT include malformed flooding, unauthorized message flooding, data flooding, command flooding, and fragmentation attack (i.e., the attacker fragments large messages into smaller pieces and sends them to the IoT device, which can cause the device to become overwhelmed and unresponsive). | A “payload flood” attack aims to overwhelm a system with data, making it impossible to distinguish between legitimate and unauthorized data traffic. |
| SQLi [ ] | One typical method for hackers to break into the data-repository of IoT systems illegally, hack the system, and carry out malicious actions is through SQL injection (SQLi). The attack is carried out by inserting malicious script into an otherwise innocuous database query. SQLi attacks can be categorized into three main types (a) In-Band SQLi attacks, (b) Out-of-Bound SQLi attacks, and (c) Inferential SQLi attacks. The main difference between the three categories of SQLi attacks is the method used to send malicious data. In-Band SQLi attacks send malicious data via an input field or web application, Out-of-Band SQLi attacks send malicious data via a different channel such as an email or file transfer, and Inferential SQLi attacks infer data from the database without directly interacting with it. | In SQLi, the contributor’s input is changed by inserting special characters that change the setting of the SQL query. This situation reinforces the attacker’s goals by tricking the repository into running a malicious script rather than the user’s input. Since SQLi may lead to the exposure of private user information or even provide attackers complete administrator access to a database, it can have far-reaching consequences. |
| DoS Attack [ , , ] | A Denial-of-Service (DoS) attack is one in which the target system or network is intentionally overloaded to the point where it cannot serve its intended purpose. The types of DoS attacks in the IoT include, but are not limited to, amplification attacks, reflection attacks, flooding attacks, protocol attacks, and resource exhaustion attacks. | The goal of a denial-of-service attack is to make the target system unusable by overloading it with traffic or delivering it data that causes it to fail. DoS attacks can either overload the target’s system or bring it down entirely. When a server is hit with an overwhelming number of requests at once, it is said to be experiencing a flood attack. |
| Sybil Attack [ , , ] | During a Sybil attack, the attacker mimics the identities of several different targets. Communicating to a peer-to-peer network presents this as one of the most significant challenges. By constructing several false identities, it is able to influence the network and exert complete control over it. There are several types of Sybil attacks in IoT, including false identity attacks, false data attacks, resource depletion attacks, and denial-of-service attacks. | Sybil attacks, if successful, can prevent Internet of Things devices from communicating with the network and thereby execute a 51% assault. Such attacks can be averted by the use of direct and indirect node validation. |
| Sinkhole [ , , ] | In this type of attack, malevolent nodes spread false information to other adjacent nodes in an effort to gain their trust. By sending their transmissions to the compromised nodes, the legitimate nodes equip them to carry out a variety of cyber-attacks. Some of the types of sinkhole attack include selective forwarding attack, blackhole attack, gratuitous routing attack, and replay attack. | With the intention of diverting traffic away from the main hub, the malicious node poses as the shortest path to the access point. This pulls in nodes from a wider area, not just the immediate vicinity of the sinkhole. The data may then be easily manipulated by the intruder node or sinkhole, which compromises the security of the network. A sinkhole attack might originate either from within the network or from the outside IoT environment. |
| Sinkhole Attack (DNS Configured) [ , , ] | In a sinkhole attack, a hacked node actively seeks out network packets by spreading the message of its deceptive routing transformation. Alternative attacks, such as node capture attacks, acknowledgement replay attack, and dropped or changed routing tables, can be launched from a sinkhole attack. DNS Sinkholing, on the other hand, is a method of user protection that involves redirecting DNS queries that are intended for known harmful or undesired domains to a controlled, fake IP address. | An Internet of Things sinkhole attack is one that intentionally slows down or stops an entire network by delivering false routing data. Disrupting communications, denying users access to services, and even launching more assaults on the network are all possible outcomes. In addition, a sinkhole attack may be used to steal information from a network, including IP addresses, data packets, and user passwords. The two most popular forms of sinkhole attacks are blackhole attacks and grayhole attacks. In a blackhole attack, the adversary does not pass along any information it obtains. In a grayhole attack, the malicious node selectively suppresses packets while allowing others to get through. |
| Blackhole Attack [ , ] | Black hole attacks occur when a router stops forwarding relevant data. A router’s settings can be tweaked such that it establishes a direct connection to any other node on the IoT network at no additional expense. Therefore, all network traffic will be sent to specific routers. The router can also exhibit false failure under certain conditions. Some common types of blackhole attacks in IoT are routing-based blackhole attacks, selective data forwarding attack, false data injection attack, timing attack, reflection attack, and resource consumption attack. | When a malicious node alters the standard operation of the routing protocol, the vulnerable node continues to believe that it has a good route and continues sending data to its intended recipient. An originating node will send out RREQ (route request) to all its communication range as part of the route-finding procedure. When an adversary gets such a request, it will send a RREP (route reply) packet to the originating node, with a high identifier and a low hop count of 1. Data is rendered inaccessible, because the intruder node, upon receiving these packets, discards them without forwarding them to the intended IoT node. |
| Traffic Analysis Attack [ , , ] | When an attacker targets an IoT network, they potentially seek to conduct a traffic analysis attack by intercepting or monitoring data sent and received between connected devices. Common types of traffic analysis attacks include eavesdropping [ , ], footprinting [ ], network scanning [ , ], and traffic redirection [ ]. | These exploits have the potential to learn the type of device that is linked to a network, to analyze user behavior, and to extract private information. To counter these threats, enterprises should use an Intrusion Detection System to keep tabs on network activity and implement encryption and robust authentication to safeguard their IoT networks. Researchers should also implement secure protocols such as HTTPS to encrypt data transferred between IoT gadgets. |
| Man-in-the-Middle Attack (MITM) [ ] | A man-in-the-middle attack is a type of cyberattack that occurs in the context of the IoT, in which an attacker intercepts and alters data that is transmitted between two endpoints. This is possible because many IoT devices and infrastructures lack sufficient security measures, making them susceptible to such attacks. The attacker positions himself as the “man in the middle” and has the ability to modify and monitor the data that is being exchanged between the two systems or devices. There are many types of MITM attacks that attackers can use to exploit insecure applications and user data. Some of the most common types of MITM attacks include rogue access point attacks [ ], address resolution protocol (ARP) spoofing [ ], domain name system (DNS) spoofing [ ], session hijacking [ ], and SSL/TLS interception [ ]. | Passwords and critical information are only two examples of the kinds of private data that might be compromised by this kind of cyberattack. The attacker can take charge of the device or system, changing data or issuing malicious commands. In order to stop man-in-the-middle attacks in the IoT, it is essential that all sensors are protected and that all data sent between them is encrypted. In addition, only approved respondents should be provided access to the system; hence, robust authentication mechanisms such as two-factor authentication are highly recommended. |
| IoT Anomaly Detection | Data Security and Consequence Administration Procedure (DSCAP) | Intrusion Detection, Management and Prevention System (IDMPS) | Firewall | ||
|---|---|---|---|---|---|
| Physical and Service security | Physical and Service security | Physical and Service security | Physical and Service security | ||
| System and interconnected network supervision | System and interconnected network supervision | Access Management | |||
| Guaranteeing IoT/IIoT/IoMT accessibility and throughput | |||||
| Monitoring and evaluation of the active state of “Operational Technology (OT) networks” that are complicated and have predictable communication techniques | Surveillance of intricate IoT network infrastructures. | Governance of permissions | IoT edge security and monitoring | ||
| IoT Control Systems and OT settings are the primary focus, with smart IT infrastructure as a secondary consideration. | |||||
| As a component of a defensive strategy, Tier-based security protects against (persistent, unknown) external attacks. | |||||
| Identification of any deviations from the norm in information exchange (identified and unfamiliar) | An extended inspection of the framework of data transmission | Intercepting internal and external attacks based on their characteristic patterns (identifiers). | Neutralization of identified external anomalies. | ||
| Accessibility and availability in the digital realm | Systems’ security vulnerabilities are being identified | ||||
| A comprehensive evaluation of the communication medium | |||||
| Governance of IoT Assets | |||||
| Assessment of identified abnormalities’ risk levels | Extensive policy framework | The efficacy of the defense largely dependent on the anomaly-signature repository. | Defense effectiveness is tied to the availability of a comprehensive database of threats. | ||
| Wide-ranging scenario filtering options | Recurrent false-positive and false-negative identification | ||||
| A non-proactive source of information | Real-time data input | Obliges specialized technical understanding. | Consistently implement and upgrade the policy | ||
| Need for specific setup and data hosting | Significant constraints for setup and data handling | ||||
| Necessitates specialized, in-depth understanding of environment ruleset and data requirements. | |||||
| Scalability | Process-Centric | Distribution | Data Privacy | Device Imposed Policies | Security | Access Model/Method | |
|---|---|---|---|---|---|---|---|
| Attribute-based [ , , ] | Decentralized access control management application | ||||||
| Capability-based [ , , ] | Blockchain driven privacy assurance. | ||||||
| Rule-based [ , , ] | Prioritize sensing and communicating nodes as per their role | ||||||
| LACS [ ] | Authorizing Fog nodes based on caching services, | ||||||
| DeCoNet [ ] | Cluster reachability-distance based utilization of thinning operation to enforce Access validation. | ||||||
| SDSM [ ] | Enforcement of combination of blockchain and ciphertext-based attribute cryptography | ||||||
| SUACC-IoT [ ] | Capability-driven authorization system for IoT devices with limited resources. | ||||||
| OAC-HAS [ ] | Fog-cloud computing outsourcing verification to avoid access structure data leaks |
| The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
Share and Cite
Tariq, U.; Ahmed, I.; Bashir, A.K.; Shaukat, K. A Critical Cybersecurity Analysis and Future Research Directions for the Internet of Things: A Comprehensive Review. Sensors 2023 , 23 , 4117. https://doi.org/10.3390/s23084117
Tariq U, Ahmed I, Bashir AK, Shaukat K. A Critical Cybersecurity Analysis and Future Research Directions for the Internet of Things: A Comprehensive Review. Sensors . 2023; 23(8):4117. https://doi.org/10.3390/s23084117
Tariq, Usman, Irfan Ahmed, Ali Kashif Bashir, and Kamran Shaukat. 2023. "A Critical Cybersecurity Analysis and Future Research Directions for the Internet of Things: A Comprehensive Review" Sensors 23, no. 8: 4117. https://doi.org/10.3390/s23084117
Article Metrics
Article access statistics, further information, mdpi initiatives, follow mdpi.

Subscribe to receive issue release notifications and newsletters from MDPI journals
- Conferences
- Registration Information
- Registration Discounts
- Grant Opportunities
- Venue, Hotel, and Travel
- Program at a Glance
- Technical Sessions
- Summer Accepted Papers
- Fall Accepted Papers
- Poster Session and Happy Hour
- Call for Papers
- Submission Policies and Instructions
- Call for Artifacts
- Instructions for Presenters
- Exhibitor Services
- Symposium Organizers
- Past Symposia
- Conference Policies
- Code of Conduct
USENIX Security '23 Summer Accepted Papers
Usenix security '23 is sold out., please do not plan to walk into the venue and register on site. the event has reached maximum physical capacity, and we will not be able to accommodate any additional registrations..
All sessions will be held in [INSERT ROOM] unless otherwise noted.
Papers are available for download below to registered attendees now and to everyone beginning [INSERT DATE]. Paper abstracts are available to everyone now. Copyright to the individual works is retained by the author[s].
Improving Logging to Reduce Permission Over-Granting Mistakes
Bingyu Shen, Tianyi Shan, and Yuanyuan Zhou, University of California, San Diego
Access control configurations are gatekeepers to block unwelcome access to sensitive data. Unfortunately, system administrators (sysadmins) sometimes over-grant permissions when resolving unintended access-deny issues reported by legitimate users, which may open up security vulnerabilities for attackers. One of the primary reasons is that modern software does not provide informative logging to guide sysadmins to understand the reported problems.
This paper makes one of the first attempts (to the best of our knowledge) to help developers improve log messages in order to help sysadmins correctly understand and fix access-deny issues without over-granting permissions. First, we conducted an observation study to understand the current practices of access-deny logging in the server software. Our study shows that many access-control program locations do not have any log messages; and a large percentage of existing log messages lack useful information to guide sysadmins to correctly understand and fix the issues. On top of our observations, we built SECLOG, which uses static analysis to automatically help developers find missing access-deny log locations and identify relevant information at the log location.
We evaluated SECLOG with ten widely deployed server applications. Overall, SECLOG identified 380 new log statements for access-deny cases, and also enhanced 550 existing access-deny log messages with diagnostic information. We have reported 114 log statements to the developers of these applications, and so far 70 have been accepted into their main branches. We also conducted a user study with sysadmins (n=32) on six real-world access-deny issues. SECLOG can reduce the number of insecure fixes from 27 to 1, and also improve the diagnosis time by 64.2% on average.
V-Cloak: Intelligibility-, Naturalness- & Timbre-Preserving Real-Time Voice Anonymization
Jiangyi Deng, Fei Teng, and Yanjiao Chen, Zhejiang University; Xiaofu Chen and Zhaohui Wang, Wuhan University; Wenyuan Xu, Zhejiang University
Voice data generated on instant messaging or social media applications contains unique user voiceprints that may be abused by malicious adversaries for identity inference or identity theft. Existing voice anonymization techniques, e.g., signal processing and voice conversion/synthesis, suffer from degradation of perceptual quality. In this paper, we develop a voice anonymization system, named V-Cloak, which attains real-time voice anonymization while preserving the intelligibility, naturalness and timbre of the audio. Our designed anonymizer features a one-shot generative model that modulates the features of the original audio at different frequency levels. We train the anonymizer with a carefully-designed loss function. Apart from the anonymity loss, we further incorporate the intelligibility loss and the psychoacoustics-based naturalness loss. The anonymizer can realize untargeted and targeted anonymization to achieve the anonymity goals of unidentifiability and unlinkability.
We have conducted extensive experiments on four datasets, i.e., LibriSpeech (English), AISHELL (Chinese), CommonVoice (French) and CommonVoice (Italian), five Automatic Speaker Verification (ASV) systems (including two DNN-based, two statistical and one commercial ASV), and eleven Automatic Speech Recognition (ASR) systems (for different languages). Experiment results confirm that V-Cloak outperforms five baselines in terms of anonymity performance. We also demonstrate that V-Cloak trained only on the VoxCeleb1 dataset against ECAPA-TDNN ASV and DeepSpeech2 ASR has transferable anonymity against other ASVs and cross-language intelligibility for other ASRs. Furthermore, we verify the robustness of V-Cloak against various de-noising techniques and adaptive attacks. Hopefully, V-Cloak may provide a cloak for us in a prism world.
PatchVerif: Discovering Faulty Patches in Robotic Vehicles
Hyungsub Kim, Muslum Ozgur Ozmen, Z. Berkay Celik, Antonio Bianchi, and Dongyan Xu, Purdue University
Modern software is continuously patched to fix bugs and security vulnerabilities. Patching is particularly important in robotic vehicles (RVs), in which safety and security bugs can cause severe physical damages. However, existing automated methods struggle to identify faulty patches in RVs, due to their inability to systematically determine patch-introduced behavioral modifications, which affect how the RV interacts with the physical environment.
In this paper, we introduce PATCHVERIF, an automated patch analysis framework. PATCHVERIF’s goal is to evaluate whether a given patch introduces bugs in the patched RV control software. To this aim, PATCHVERIF uses a combination of static and dynamic analysis to measure how the analyzed patch affects the physical state of an RV. Specifically, PATCHVERIF uses a dedicated input mutation algorithm to generate RV inputs that maximize the behavioral differences (in the physical space) between the original code and the patched one. Using the collected information about patch-introduced behavioral modifications, PATCHVERIF employs support vector machines (SVMs) to infer whether a patch is faulty or correct.
We evaluated PATCHVERIF on two popular RV control software (ArduPilot and PX4), and it successfully identified faulty patches with an average precision and recall of 97.9% and 92.1%, respectively. Moreover, PATCHVERIF discovered 115 previously unknown bugs, 103 of which have been acknowledged, and 51 of them have already been fixed.
DISTDET: A Cost-Effective Distributed Cyber Threat Detection System
Feng Dong, School of Cyber Science and Engineering, Huazhong University of Science and Technology / Sangfor Technologies Inc.; Liu Wang and Xu Nie, Beijing University of Posts and Telecommunications; Fei Shao, Case Western Reserve University; Haoyu Wang, School of Cyber Science and Engineering, Huazhong University of Science and Technology; Ding Li, Key Laboratory of High-Confidence Software Technologies (MOE), School of Computer Science, Peking University; Xiapu Luo, The Hong Kong Polytechnic University; Xusheng Xiao, Arizona State University
Building provenance graph that considers causal relationships among software behaviors can better provide contextual information of cyber attacks, especially for advanced attacks such as Advanced Persistent Threat (APT) attacks. Despite its promises in assisting attack investigation, existing approaches that use provenance graphs to perform attack detection suffer from two fundamental limitations. First, existing approaches adopt a centralized detection architecture that sends all system auditing logs to the server for processing, incurring intolerable costs of data transmission, data storage, and computation. Second, they adopt either rule-based techniques that cannot detect unknown threats, or anomaly-detection techniques that produce numerous false alarms, failing to achieve a balance of precision and recall in APT detection. To address these fundamental challenges, we propose DISTDET, a distributed detection system that detects APT attacks by (1) performing light weight detection based on the host model built in the client side, (2) filtering false alarms based on the semantics of the alarm proprieties, and (3) deriving global models to complement the local bias of the host models. Our experiments on a large-scale industrial environment (1,130 hosts, 14 days, ∼1.6 billion events) and the DARPA TC dataset show that DISTDET is as effective as sate-of-the-art techniques in detecting attacks, while dramatically reducing network bandwidth from 11.28Mb/s to 17.08Kb/S (676.5× reduction), memory usages from 364MB to 5.523MB (66× reduction), and storage from 1.47GB to 130.34MB (11.6× reduction). By the time of this writing, DISTDET has been deployed to 50+ industry customers with 22,000+ hosts for more than 6 months, and identified over 900 real-world attacks.
The Impostor Among US(B): Off-Path Injection Attacks on USB Communications
Robert Dumitru, The University of Adelaide and Defence Science and Technology Group; Daniel Genkin, Georgia Tech; Andrew Wabnitz, Defence Science and Technology Group; Yuval Yarom, The University of Adelaide
USB is the most prevalent peripheral interface in modern computer systems and its inherent insecurities make it an appealing attack vector. A well-known limitation of USB is that traffic is not encrypted. This allows on-path adversaries to trivially perform man-in-the-middle attacks. Off-path attacks that compromise the confidentiality of communications have also been shown to be possible. However, so far no off-path attacks that breach USB communications integrity have been demonstrated.
In this work we show that the integrity of USB communications is not guaranteed even against off-path attackers. Specifically, we design and build malicious devices that, even when placed outside of the path between a victim device and the host, can inject data to that path. Using our developed injectors we can falsify the provenance of data input as interpreted by a host computer system. By injecting on behalf of trusted victim devices we can circumvent any software-based authorisation policy defences that computer systems employ against common USB attacks. We demonstrate two concrete attacks. The first injects keystrokes allowing an attacker to execute commands. The second demonstrates file-contents replacement including during system install from a USB disk. We test the attacks on 29 USB 2.0 and USB 3.x hubs and find 14 of them to be vulnerable.
Fuzztruction: Using Fault Injection-based Fuzzing to Leverage Implicit Domain Knowledge
Nils Bars, Moritz Schloegel, Tobias Scharnowski, and Nico Schiller, Ruhr-Universität Bochum; Thorsten Holz, CISPA Helmholtz Center for Information Security
Distinguished Paper Award Winner and Runner-Up Winner of the 2023 Internet Defense Prize
Today's digital communication relies on complex protocols and specifications for exchanging structured messages and data. Communication naturally involves two endpoints: One generating data and one consuming it. Traditional fuzz testing approaches replace one endpoint, the generator , with a fuzzer and rapidly test many mutated inputs on the target program under test. While this fully automated approach works well for loosely structured formats, this does not hold for highly structured formats, especially those that go through complex transformations such as compression or encryption.
In this work, we propose a novel perspective on generating inputs in highly complex formats without relying on heavyweight program analysis techniques, coarse-grained grammar approximation, or a human domain expert. Instead of mutating the inputs for a target program, we inject faults into the data generation program so that this data is almost of the expected format. Such data bypasses the initial parsing stages in the consumer program and exercises deeper program states, where it triggers more interesting program behavior. To realize this concept, we propose a set of compile-time and run-time analyses to mutate the generator in a targeted manner, so that it remains intact and produces semi-valid outputs that satisfy the constraints of the complex format. We have implemented this approach in a prototype called Fuzztruction and show that it outperforms the state-of-the-art fuzzers AFL++, SYMCC, and WEIZZ. Fuzztruction finds significantly more coverage than existing methods, especially on targets that use cryptographic primitives. During our evaluation, Fuzztruction uncovered 151 unique crashes (after automated deduplication). So far, we manually triaged and reported 27 bugs and 4 CVEs were assigned.
NVLeak: Off-Chip Side-Channel Attacks via Non-Volatile Memory Systems
Zixuan Wang, UC San Diego; Mohammadkazem Taram, Purdue University and UC San Diego; Daniel Moghimi, UT Austin and UC San Diego; Steven Swanson, Dean Tullsen, and Jishen Zhao, UC San Diego
We study microarchitectural side-channel attacks and defenses on non-volatile RAM (NVRAM) DIMMs. In this study, we first perform reverse-engineering of NVRAMs as implemented by the Intel Optane DIMM and reveal several of its previously undocumented microarchitectural details: on-DIMM cache structures (NVCache) and wear-leveling policies. Based on these findings, we first develop cross-core and cross-VM covert channels to establish the channel capacity of these shared hardware resources. Then, we devise NVCache-based side channels under the umbrella of NVLeak. We apply NVLeak to a series of attack case studies, including compromising the privacy of databases and key-value storage backed by NVRAM and spying on the execution path of code pages when NVRAM is used as a volatile runtime memory. Our results show that side-channel attacks exploiting NVRAM are practical and defeat previously-proposed defense that only focuses on on-chip hardware resources. To fill this gap in defense, we develop system-level mitigations based on cache partitioning to prevent side-channel leakage from NVCache.
A Research Framework and Initial Study of Browser Security for the Visually Impaired
Elaine Lau and Zachary Peterson, Cal Poly, San Luis Obispo
The growth of web-based malware and phishing attacks has catalyzed significant advances in the research and use of interstitial warning pages and modals by a browser prior to loading the content of a suspect site. These warnings commonly use visual cues to attract users' attention, including specialized iconography, color, and the placement and size of buttons to communicate the importance of the scenario. While the efficacy of visual techniques has improved safety for sighted users, these techniques are unsuitable for blind and visually impaired users. We attribute this not to a lack of interest or technical capability by browser manufactures, where universal design is a core tenet of their engineering practices, but instead a reflection of the very real dearth of research literature to inform their choices, exacerbated by a deficit of clear methodologies for conducting studies with this population. Indeed, the challenges are manifold. In this paper, we analyze and address the methodological challenges of conducting security and privacy research with a visually impaired population, and contribute a new set of methodological best practices when conducting a study of this kind. Using our methodology, we conduct a preliminary study analyzing the experiences of the visually impaired with browser security warnings, perform a thematic analysis identifying common challenges visually impaired users experience, and present some initial solutions that could improve security for this population.
PUMM: Preventing Use-After-Free Using Execution Unit Partitioning
Carter Yagemann, The Ohio State University; Simon P. Chung, Brendan Saltaformaggio, and Wenke Lee, Georgia Institute of Technology
Critical software is written in memory unsafe languages that are vulnerable to use-after-free and double free bugs. This has led to proposals to secure memory allocators by strategically deferring memory reallocations long enough to make such bugs unexploitable. Unfortunately, existing solutions suffer from high runtime and memory overheads. Seeking a better solution, we propose to profile programs to identify units of code that correspond to the handling of individual tasks. With the intuition that little to no data should flow between separate tasks at runtime, reallocation of memory freed by the currently executing unit is deferred until after its completion; just long enough to prevent use-after-free exploitation.
To demonstrate the efficacy of our design, we implement a prototype for Linux, PUMM, which consists of an offline profiler and an online enforcer that transparently wraps standard libraries to protect C/C++ binaries. In our evaluation of 40 real-world and 3,000 synthetic vulnerabilities across 26 programs, including complex multi-threaded cases like the Chakra JavaScript engine, PUMM successfully thwarts all real-world exploits, and only allows 4 synthetic exploits, while reducing memory overhead by 52.0% over prior work and incurring an average runtime overhead of 2.04%.
POLICYCOMP: Counterpart Comparison of Privacy Policies Uncovers Overbroad Personal Data Collection Practices
Lu Zhou, Xidian University and Shanghai Jiao Tong University; Chengyongxiao Wei, Tong Zhu, and Guoxing Chen, Shanghai Jiao Tong University; Xiaokuan Zhang, George Mason University; Suguo Du, Hui Cao, and Haojin Zhu, Shanghai Jiao Tong University
Since mobile apps' privacy policies are usually complex, various tools have been developed to examine whether privacy policies have contradictions and verify whether privacy policies are consistent with the apps' behaviors. However, to the best of our knowledge, no prior work answers whether the personal data collection practices (PDCPs) in an app's privacy policy are necessary for given purposes (i.e., whether to comply with the principle of data minimization). Though defined by most existing privacy regulations/laws such as GDPR, the principle of data minimization has been translated into different privacy practices depending on the different contexts (e.g., various developers and targeted users). In the end, the developers can collect personal data claimed in the privacy policies as long as they receive authorizations from the users.
Currently, it mainly relies on legal experts to manually audit the necessity of personal data collection according to the specific contexts, which is not very scalable for millions of apps. In this study, we aim to take the first step to automatically investigate whether PDCPs in an app's privacy policy are overbroad from the perspective of counterpart comparison. Our basic insight is that, if an app claims to collect much more personal data in its privacy policy than most of its counterparts, it is more likely to be conducting overbroad collection. To achieve this, POLICYCOMP, an automatic framework for detecting overbroad PDCPs is proposed. We use POLICYCOMP to perform a large-scale analysis on 10,042 privacy policies and flag 48.29% of PDCPs to be overbroad. We shared our findings with 2,000 app developers and received 52 responses from them, 39 of which acknowledged our findings and took actions (e.g., removing overbroad PDCPs).
The Maginot Line: Attacking the Boundary of DNS Caching Protection
Xiang Li, Chaoyi Lu, and Baojun Liu, Tsinghua University; Qifan Zhang and Zhou Li, University of California, Irvine; Haixin Duan, Tsinghua University, QI-ANXIN Technology Research Institute, and Zhongguancun Laboratory; Qi Li, Tsinghua University and Zhongguancun Laboratory
In this paper, we report MaginotDNS , a powerful cache poisoning attack against DNS servers that simultaneously act as forwarder and recursive resolver (termed as CDNS ). The attack is made possible through exploiting vulnerabilities in the bailiwick checking algorithms, one of the cornerstones of DNS security since the 1990s, and affects multiple versions of popular DNS software, including BIND and Microsoft DNS. Through field tests, we find that the attack is potent, allowing attackers to take over entire DNS zones, even including Top-Level Domains (e.g., .com and .net ). Through a large-scale measurement study, we also confirm the extensive usage of CDNSes in real-world networks (up to 41.8% of our probed open DNS servers) and find that at least 35.5% of all CDNSes are vulnerable to MaginotDNS . After interviews with ISPs, we show a wide range of CDNS use cases and real-world attacks. We have reported all the discovered vulnerabilities to DNS software vendors and received acknowledgments from all of them. 3 CVE-ids have been assigned, and 2 vendors have fixed their software. Our study brings attention to the implementation inconsistency of security checking logic in different DNS software and server modes (i.e., recursive resolvers and forwarders), and we call for standardization and agreements among software vendors.
One Server for the Price of Two: Simple and Fast Single-Server Private Information Retrieval
Alexandra Henzinger, Matthew M. Hong, and Henry Corrigan-Gibbs, MIT; Sarah Meiklejohn, Google; Vinod Vaikuntanathan, MIT
We present SimplePIR, the fastest single-server private information retrieval scheme known to date. SimplePIR’s security holds under the learning-with-errors assumption. To answer a client’s query, the SimplePIR server performs fewer than one 32-bit multiplication and one 32-bit addition per database byte. SimplePIR achieves 10 GB/s/core server throughput, which approaches the memory bandwidth of the machine and the performance of the fastest two-server private-information-retrieval schemes (which require non-colluding servers). SimplePIR has relatively large communication costs: to make queries to a 1 GB database, the client must download a 121 MB "hint" about the database contents; thereafter, the client may make an unbounded number of queries, each requiring 242 KB of communication. We present a second single-server scheme, DoublePIR, that shrinks the hint to 16 MB at the cost of slightly higher per-query communication (345 KB) and slightly lower throughput (7.4 GB/s/core). Finally, we apply our new private-information-retrieval schemes, together with a novel data structure for approximate set membership, to the task of private auditing in Certificate Transparency. We achieve a strictly stronger notion of privacy than Google Chrome’s current approach with 13x more communication: 16 MB of download per week, along with 1.5 KB per TLS connection.
Exploring User Reactions and Mental Models Towards Perceptual Manipulation Attacks in Mixed Reality
Kaiming Cheng, Jeffery F. Tian, Tadayoshi Kohno, and Franziska Roesner, University of Washington
Perceptual Manipulation Attacks (PMA) involve manipulating users’ multi-sensory (e.g., visual, auditory, haptic) perceptions of the world through Mixed Reality (MR) content, in order to influence users' judgments and following actions. For example, a MR driving application that is expected to show safety-critical output might also (maliciously or unintentionally) overlay the wrong signal on a traffic sign, misleading the user into slamming on the brake. While current MR technology is sufficient to create such attacks, little research has been done to understand how users perceive, react to, and defend against such potential manipulations. To provide a foundation for understanding and addressing PMA in MR, we conducted an in-person study with 21 participants. We developed three PMA in which we focused on attacking three different perceptions: visual, auditory, and situational awareness. Our study first investigates how user reactions are affected by evaluating their performance on “microbenchmark'' tasks under benchmark and different attack conditions. We observe both primary and secondary impacts from attacks, later impacting participants' performance even under non-attack conditions. We follow up with interviews, surfacing a range of user reactions and interpretations of PMA. Through qualitative data analysis of our observations and interviews, we identify various defensive strategies participants developed, and we observe how these strategies sometimes backfire. We derive recommendations for future investigation and defensive directions based on our findings.
Eavesdropping Mobile App Activity via Radio-Frequency Energy Harvesting
Tao Ni, Shenzhen Research Institute, City University of Hong Kong, and Department of Computer Science, City University of Hong Kong; Guohao Lan, Department of Software Technology, Delft University of Technology; Jia Wang, College of Computer Science and Software Engineering, Shenzhen University; Qingchuan Zhao, Department of Computer Science, City University of Hong Kong; Weitao Xu, Shenzhen Research Institute, City University of Hong Kong, and Department of Computer Science, City University of Hong Kong
Radio-frequency (RF) energy harvesting is a promising technology for Internet-of-Things (IoT) devices to power sensors and prolong battery life. In this paper, we present a novel side-channel attack that leverages RF energy harvesting signals to eavesdrop mobile app activities. To demonstrate this novel attack, we propose AppListener, an automated attack framework that recognizes fine-grained mobile app activities from harvested RF energy. The RF energy is harvested from a custom-built RF energy harvester which generates voltage signals from ambient Wi-Fi transmissions, and app activities are recognized from a three-tier classification algorithm. We evaluate AppListener with four mobile devices running 40 common mobile apps (e.g., YouTube, Facebook, and WhatsApp) belonging to five categories (i.e., video, music, social media, communication, and game); each category contains five application-specific activities. Experiment results show that AppListener achieves over 99% accuracy in differentiating four different mobile devices, over 98% accuracy in classifying 40 different apps, and 86.7% accuracy in recognizing five sets of application-specific activities. Moreover, a comprehensive study is conducted to show AppListener is robust to a number of impact factors, such as distance, environment, and non-target connected devices. Practices of integrating AppListener into commercial IoT devices also demonstrate that it is easy to deploy. Finally, countermeasures are presented as the first step to defend against this novel attack.
Side-Channel Attacks on Optane Persistent Memory
Sihang Liu, University of Virginia; Suraaj Kanniwadi, Cornell University; Martin Schwarzl, Andreas Kogler, and Daniel Gruss, Graz University of Technology; Samira Khan, University of Virginia
There is a constant evolution of technology for cloud environments, including the development of new memory storage technology, such as persistent memory. The newly-released Intel Optane persistent memory provides high-performance, persistent, and byte-addressable access for storage-class applications in data centers. While Optane’s direct data management is fast and efficient, it is unclear whether it comes with undesirable security implications. This is problematic, as cloud tenants are physically co-located on the same hardware.
In this paper, we present the first side-channel security analysis of Intel Optane persistent memory. We reverse-engineer the internal cache hierarchy, cache sizes, associativity, replacement policies, and wear-leveling mechanism of the Optane memory. Based on this reverse-engineering, we construct four new attack primitives on Optane’s internal components. We then present four case studies using these attack primitives. First, we present local covert channels based on Optane’s internal caching. Second, we demonstrate a keystroke side-channel attack on a remote user via Intel’s Optane-optimized key-value store, pmemkv. Third, we study a fully remote covert channel through pmemkv. Fourth, we present our Note Board attack, also through pmemkv, enabling two parties to store and exchange messages covertly across long time gaps and even power cycles of the server. Finally, we discuss mitigations against our attacks.
A Study of Multi-Factor and Risk-Based Authentication Availability
Anthony Gavazzi, Ryan Williams, Engin Kirda, and Long Lu, Northeastern University; Andre King, Andy Davis, and Tim Leek, MIT Lincoln Laboratory
Password-based authentication (PBA) remains the most popular form of user authentication on the web despite its long-understood insecurity. Given the deficiencies of PBA, many online services support multi-factor authentication (MFA) and/or risk-based authentication (RBA) to better secure user accounts. The security, usability, and implementations of MFA and RBA have been studied extensively, but attempts to measure their availability among popular web services have lacked breadth. Additionally, no study has analyzed MFA and RBA prevalence together or how the presence of Single-Sign-On (SSO) providers affects the availability of MFA and RBA on the web.
In this paper, we present a study of 208 popular sites in the Tranco top 5K that support account creation to understand the availability of MFA and RBA on the web, the additional authentication factors that can be used for MFA and RBA, and how logging into sites through more secure SSO providers changes the landscape of user authentication security. We find that only 42.31% of sites support any form of MFA, and only 22.12% of sites block an obvious account hijacking attempt. Though most sites do not offer MFA or RBA, SSO completely changes the picture. If one were to create an account for each site through an SSO provider that offers MFA and/or RBA, whenever available, 80.29% of sites would have access to MFA and 72.60% of sites would stop an obvious account hijacking attempt. However, this proliferation through SSO comes with a privacy trade-off, as nearly all SSO providers that support MFA and RBA are major third-party trackers.
Person Re-identification in 3D Space: A WiFi Vision-based Approach
Yili Ren and Yichao Wang, Florida State University; Sheng Tan, Trinity University; Yingying Chen, Rutgers University; Jie Yang, Florida State University
Person re-identification (Re-ID) has become increasingly important as it supports a wide range of security applications. Traditional person Re-ID mainly relies on optical camera-based systems, which incur several limitations due to the changes in the appearance of people, occlusions, and human poses. In this work, we propose a WiFi vision-based system, 3D-ID, for person Re-ID in 3D space. Our system leverages the advances of WiFi and deep learning to help WiFi devices "see'', identify, and recognize people. In particular, we leverage multiple antennas on next-generation WiFi devices and 2D AoA estimation of the signal reflections to enable WiFi to visualize a person in the physical environment. We then leverage deep learning to digitize the visualization of the person into 3D body representation and extract both the static body shape and dynamic walking patterns for person Re-ID. Our evaluation results under various indoor environments show that the 3D-ID system achieves an overall rank-1 accuracy of 85.3%. Results also show that our system is resistant to various attacks. The proposed 3D-ID is thus very promising as it could augment or complement camera-based systems.
Fourteen Years in the Life: A Root Server’s Perspective on DNS Resolver Security
Alden Hilton, Sandia National Laboratories; Casey Deccio, Brigham Young University; Jacob Davis, Sandia National Laboratories
We consider how the DNS security and privacy landscape has evolved over time, using data collected annually at A-root between 2008 and 2021. We consider issues such as deployment of security and privacy mechanisms, including source port randomization, TXID randomization, DNSSEC, and QNAME minimization. We find that achieving general adoption of new security practices is a slow, ongoing process. Of particular note, we find a significant number of resolvers lacking nearly all of the security mechanisms we considered, even as late as 2021. Specifically, in 2021, over 4% of the resolvers analyzed were unprotected by either source port randomization, DNSSEC validation, DNS cookies, or 0x20 encoding. Encouragingly, we find that the volume of traffic from resolvers with secure practices is significantly higher than that of other resolvers.
ClepsydraCache -- Preventing Cache Attacks with Time-Based Evictions
Jan Philipp Thoma, Ruhr University Bochum; Christian Niesler, University of Duisburg-Essen; Dominic Funke, Gregor Leander, Pierre Mayr, and Nils Pohl, Ruhr University Bochum; Lucas Davi, University of Duisburg-Essen; Tim Güneysu, Ruhr University Bochum & DFKI
In the recent past, we have witnessed the shift towards attacks on the microarchitectural CPU level. In particular, cache side-channels play a predominant role as they allow an attacker to exfiltrate secret information by exploiting the CPU microarchitecture. These subtle attacks exploit the architectural visibility of conflicting cache addresses. In this paper, we present ClepsydraCache, which mitigates state-of-the-art cache attacks using a novel combination of cache decay and index randomization. Each cache entry is linked with a Time-To-Live (TTL) value. We propose a new dynamic scheduling mechanism of the TTL which plays a fundamental role in preventing those attacks while maintaining performance. ClepsydraCache efficiently protects against the latest cache attacks such as Prime+(Prune+)Probe. We present a full prototype in gem5 and lay out a proof-of-concept hardware design of the TTL mechanism, which demonstrates the feasibility of deploying ClepsydraCache in real-world systems.
Guarding Serverless Applications with Kalium
Deepak Sirone Jegan, University of Wisconsin-Madison; Liang Wang, Princeton University; Siddhant Bhagat, Microsoft; Michael Swift, University of Wisconsin-Madison
As an emerging application paradigm, serverless computing attracts attention from more and more adversaries. Unfortunately, security tools for conventional web applications cannot be easily ported to serverless computing due to its distributed nature, and existing serverless security solutions focus on enforcing user specified information flow policies which are unable to detect the manipulation of the order of functions in application control flow paths. In this paper, we present Kalium , an extensible security framework that leverages local function state and global application state to enforce control-flow integrity (CFI) in serverless applications. We evaluate the performance overhead and security of Kalium using realistic open-source applications; our results show that Kalium mitigates several classes of attacks with relatively low performance overhead and outperforms the state-of-the-art serverless information flow protection systems.
DynSQL: Stateful Fuzzing for Database Management Systems with Complex and Valid SQL Query Generation
Zu-Ming Jiang, ETH Zurich; Jia-Ju Bai, Tsinghua University; Zhendong Su, ETH Zurich
Database management systems (DBMSs) are essential parts of modern software. To ensure the security of DBMSs, recent approaches apply fuzzing to testing DBMSs by automatically generating SQL queries. However, existing DBMS fuzzers are limited in generating complex and valid queries, as they heavily rely on their predefined grammar models and fixed knowledge about DBMSs, but do not capture DBMS-specific state information. As a result, these approaches miss many deep bugs in DBMSs.
In this paper, we propose a novel stateful fuzzing approach to effectively test DBMSs and find deep bugs. Our basic idea is that after DBMSs process each SQL statement, there is useful state information that can be dynamically collected to facilitate later query generation. Based on this idea, our approach performs dynamic query interaction to incrementally generate complex and valid SQL queries, using the captured state information. To further improve the validity of generated queries, our approach uses the error status of query processing to filter out invalid test cases. We implement our approach as a fully automatic fuzzing framework, DynSQL. DynSQL is evaluated on 6 widely-used DBMSs (including SQLite, MySQL, MariaDB, PostgreSQL, MonetDB, and ClickHouse) and finds 40 unique bugs. Among these bugs, 38 have been confirmed, 21 have been fixed, and 19 have been assigned with CVE IDs. In our evaluation, DynSQL outperforms other state-of-the-art DBMS fuzzers, achieving 41% higher code coverage and finding many bugs missed by other fuzzers.
Automated Security Analysis of Exposure Notification Systems
Kevin Morio and Ilkan Esiyok, CISPA Helmholtz Center for Information Security; Dennis Jackson, Mozilla; Robert Künnemann, CISPA Helmholtz Center for Information Security
We present the first formal analysis and comparison of the security of the two most widely deployed exposure notification systems, ROBERT and the Google and Apple Exposure Notification (GAEN) framework.
ROBERT is the most popular instalment of the centralised approach to exposure notification, in which the risk score is computed by a central server. GAEN, in contrast, follows the decentralised approach, where the user's phone calculates the risk. The relative merits of centralised and decentralised systems have proven to be a controversial question. The majority of the previous analyses have focused on the privacy implications of these systems, ours is the first formal analysis to evaluate the security of the deployed systems—the absence of false risk alerts.
We model the French deployment of ROBERT and the most widely deployed GAEN variant, Germany's Corona-Warn-App. We isolate the precise conditions under which these systems prevent false alerts. We determine exactly how an adversary can subvert the system via network and Bluetooth sniffing, database leakage or the compromise of phones, back-end systems and health authorities. We also investigate the security of the original specification of the DP3T protocol, in order to identify gaps between the proposed scheme and its ultimate deployment.
We find a total of 27 attack patterns, including many that distinguish the centralised from the decentralised approach, as well as attacks on the authorisation procedure that differentiate all three protocols. Our results suggest that ROBERT's centralised design is more vulnerable against both opportunistic and highly resourced attackers trying to perform mass-notification attacks.
xNIDS: Explaining Deep Learning-based Network Intrusion Detection Systems for Active Intrusion Responses
Feng Wei, University at Buffalo; Hongda Li, Palo Alto Networks; Ziming Zhao and Hongxin Hu, University at Buffalo
While Deep Learning-based Network Intrusion Detection Systems (DL-NIDS) have recently been significantly explored and shown superior performance, they are insufficient to actively respond to the detected intrusions due to the semantic gap between their detection results and actionable interpretations. Furthermore, their high error costs make network operators unwilling to respond solely based on their detection results. The root cause of these drawbacks can be traced to the lack of explainability of DL-NIDS. Although some methods have been developed to explain deep learning-based systems, they are incapable of handling the history inputs and complex feature dependencies of structured data and do not perform well in explaining DL-NIDS.
In this paper, we present XNIDS, a novel framework that facilitates active intrusion responses by explaining DL-NIDS. Our explanation method is highlighted by: (1) approximating and sampling around history inputs; and (2) capturing feature dependencies of structured data to achieve a high-fidelity explanation. Based on the explanation results, XNIDS can further generate actionable defense rules. We evaluate XNIDS with four state-of-the-art DL-NIDS. Our evaluation results show that XNIDS outperforms previous explanation methods in terms of fidelity, sparsity, completeness, and stability, all of which are important to active intrusion responses. Moreover, we demonstrate that XNIDS can efficiently generate practical defense rules, help understand DL-NIDS behaviors and troubleshoot detection errors
Pspray: Timing Side-Channel based Linux Kernel Heap Exploitation Technique
Yoochan Lee and Jinhan Kwak, Seoul National University; Junesoo Kang and Yuseok Jeon, UNIST; Byoungyoung Lee, Seoul National University
The stealthiness of an attack is the most vital consideration for an attacker to reach their goals without being detected. Therefore, attackers put in a great deal of effort to increase the success rate of attacks in order not to expose information on the attacker and attack attempts resulting from failures. Exploitation of the kernel, which is a prime target for the attacker, usually takes advantage of heap-based vulnerabilities, and these exploits' success rates fortunately remain low (e.g., 56.1% on average) due to the operating principle of the default Linux kernel heap allocator, SLUB.
This paper presents Pspray, a timing side-channel attack-based exploitation technique that significantly increases the success probability of exploitation. According to our evaluation, with 10 real-world vulnerabilities, Pspray significantly improves the success rate of all those vulnerabilities (e.g., from 56.1% to 97.92% on average). To prevent this exploitation technique from being abused by the attacker, we further introduce a new defense mechanism to mitigate the threat of Pspray. After applying mitigation, the overall success rate of Pspray becomes similar to that from before using Pspray with negligible performance overhead (0.25%) and memory overhead (0.52%).
Strategies and Vulnerabilities of Participants in Venezuelan Influence Operations
Ruben Recabarren, Bogdan Carbunar, Nestor Hernandez, and Ashfaq Ali Shafin, Florida International University
Studies of online influence operations, coordinated efforts to disseminate and amplify disinformation, focus on forensic analysis of social networks or of publicly available datasets of trolls and bot accounts. However, little is known about the experiences and challenges of human participants in influence operations. We conducted semi-structured interviews with 19 influence operations participants that contribute to the online image of Venezuela, to understand their incentives, capabilities, and strategies to promote content while evading detection. To validate a subset of their answers, we performed a quantitative investigation using data collected over almost four months, from Twitter accounts they control.
We found diverse participants that include pro-government and opposition supporters, operatives and grassroots campaigners, and sockpuppet account owners and real users. While pro-government and opposition participants have similar goals and promotion strategies, they differ in their motivation, organization, adversaries and detection avoidance strategies. We report the Patria framework, a government platform for operatives to log activities and receive benefits. We systematize participant strategies to promote political content, and to evade and recover from Twitter penalties. We identify vulnerability points associated with these strategies, and suggest more nuanced defenses against influence operations.
Investigating Verification Behavior and Perceptions of Visual Digital Certificates
Dañiel Gerhardt and Alexander Ponticello, CISPA Helmholtz Center for Information Security and Saarland University; Adrian Dabrowski and Katharina Krombholz, CISPA Helmholtz Center for Information Security
This paper presents a qualitative study to explore how individuals perceive and verify visual digital certificates with QR codes. During the COVID-19 pandemic, such certificates have been used in the EU to provide standardized proof of vaccination.
We conducted semi-structured interviews with N =17 participants responsible for verifying COVID-19 certificates as part of their job. Using a two-fold thematic analysis approach, we, among other things, identified and classified multiple behavioral patterns, including inadequate reliance on visual cues as a proxy for proper digital verification.
We present design and structural recommendations based on our findings, including conceptual changes and improvements to storage and verification apps to limit shortcut opportunities. Our empirical findings are hence essential to improve the usability, robustness, and effectiveness of visual digital certificates and their verification.
Remote Attacks on Speech Recognition Systems Using Sound from Power Supply
Lanqing Yang, Xinqi Chen, Xiangyong Jian, Leping Yang, Yijie Li, Qianfei Ren, Yi-Chao Chen, and Guangtao Xue, Shanghai Jiao Tong University; Xiaoyu Ji, Zhejiang University
Speech recognition (SR) systems are used on smart phones and speakers to make inquiries, compose emails, and initiate phone calls. However, they also impose a serious security risk. Researchers have demonstrated that the introduction of certain sounds can threaten the security of SR systems. Nonetheless, most of those methods require that the attacker approach to within a short distance of the victim, thereby limiting the applicability of such schemes. Other researchers have attacked SR systems remotely using peripheral devices (e.g., lasers); however, those methods require line of sight access and an always-on speaker in the vicinity of the victim. To the best of our knowledge, this paper presents the first-ever scheme, named SingAttack, in which SR systems are manipulated by human-like sounds generated in the switching mode power supply of the victim’s device. The fact that attack signals are transmitted via the power grid enables long-range attacks on existing SR systems. The proposed SingAttack system does not rely on extraneous hardware or unrealistic assumptions pertaining to device access. In experiments on ten SR systems, SingAttack achieved Mel-Cepstral Distortion of 7.8 from an attack initiated at a distance of 23m.
HOMESPY: The Invisible Sniffer of Infrared Remote Control of Smart TVs
Kong Huang, YuTong Zhou, and Ke Zhang, The Chinese University of Hong Kong; Jiacen Xu, University of California, Irvine; Jiongyi Chen, National University of Defense Technology; Di Tang, Indiana University Bloomington; Kehuan Zhang, The Chinese University of Hong Kong
Infrared (IR) remote control is a widely used technology at home due to its simplicity and low cost. Most considered it to be "secure'' because of the line-of-sight usage within the home. In this paper, we revisit the security of IR remote control schemes and examine their security assumptions under the settings of internet-connected smart homes. We focus on two specific questions: (1) whether IR signals could be sniffed by an IoT device; and (2) what information could be leaked out through the sniffed IR control signals.
To answer these questions, we design a sniff module using a commercial-off-the-shelf IR receiver on a Raspberry Pi and show that the Infrared (IR) signal emanating from the remote control of a Smart TV can be captured by one of the nearby IoT devices, for example, a smart air-conditioner, even the signal is not aimed at the air-conditioner. The IR signal range and receiving angle are larger than most have thought. We also developed algorithms to extract semantic information from the sniffed IR control signals, and evaluated with real-world applications. The results showed that lots of sensitive information could be leaked out through the sniffed IR control signals, including account name and password, PIN code, and even payment information.
FuzzJIT: Oracle-Enhanced Fuzzing for JavaScript Engine JIT Compiler
Junjie Wang, College of Intelligence and Computing, Tianjin University; Zhiyi Zhang, CodeSafe Team, Qi An Xin Group Corp.; Shuang Liu, College of Intelligence and Computing, Tianjin University; Xiaoning Du, Monash University; Junjie Chen, College of Intelligence and Computing, Tianjin University
We present a novel fuzzing technique, FuzzJIT, for exposing JIT compiler bugs in JavaScript engines, based on our insight that JIT compilers shall only speed up the execution but never change the execution result of JavaScript code. FuzzJIT can activate the JIT compiler for every test case and acutely capture any execution discrepancy caused by JIT compilers. The key to success is the design of an input wrapping template, which proactively activates the JIT compiler and makes the generated samples oracle-aware themselves and the oracle is tested during execution spontaneously. We also design a set of mutation strategies to emphasize program elements promising in revealing JIT compiler bugs. FuzzJIT drills to JIT compilers and at the same time retains the high efficiency of fuzzing. We have implemented the design and applied the prototype to find new JIT compiler bugs in four mainstream JavaScript engines. In one month, ten, five, two, and 16 new bugs are exposed in JavaScriptCore, V8, SpiderMonkey, and ChakraCore, respectively, with three demonstrated exploitable.
TPatch: A Triggered Physical Adversarial Patch
Wenjun Zhu and Xiaoyu Ji, USSLAB, Zhejiang University; Yushi Cheng, BNRist, Tsinghua University; Shibo Zhang and Wenyuan Xu, USSLAB, Zhejiang University
Autonomous vehicles increasingly utilize the vision-based perception module to acquire information about driving environments and detect obstacles. Correct detection and classification are important to ensure safe driving decisions. Existing works have demonstrated the feasibility of fooling the perception models such as object detectors and image classifiers with printed adversarial patches. However, most of them are indiscriminately offensive to every passing autonomous vehicle. In this paper, we propose TPatch, a physical adversarial patch triggered by acoustic signals. Unlike other adversarial patches, TPatch remains benign under normal circumstances but can be triggered to launch a hiding, creating or altering attack by a designed distortion introduced by signal injection attacks towards cameras. To avoid the suspicion of human drivers and make the attack practical and robust in the real world, we propose a content-based camouflage method and an attack robustness enhancement method to strengthen it. Evaluations with three object detectors, YOLO V3/V5 and Faster R-CNN, and eight image classifiers demonstrate the effectiveness of TPatch in both the simulation and the real world. We also discuss possible defenses at the sensor, algorithm, and system levels.
TAP: Transparent and Privacy-Preserving Data Services
Daniel Reijsbergen and Aung Maw, Singapore University of Technology and Design; Zheng Yang, Southwest University; Tien Tuan Anh Dinh and Jianying Zhou, Singapore University of Technology and Design
Users today expect more security from services that handle their data. In addition to traditional data privacy and integrity requirements, they expect transparency, i.e., that the service’s processing of the data is verifiable by users and trusted auditors. Our goal is to build a multi-user system that provides data privacy, integrity, and transparency for a large number of operations, while achieving practical performance.
To this end, we first identify the limitations of existing approaches that use authenticated data structures. We find that they fall into two categories: 1) those that hide each user’s data from other users, but have a limited range of verifiable operations (e.g., CONIKS, Merkle2, and Proofs of Liabilities), and 2) those that support a wide range of verifiable operations, but make all data publicly visible (e.g., IntegriDB and FalconDB). We then present TAP to address the above limitations. The key component of TAP is a novel tree data structure that supports efficient result verification, and relies on independent audits that use zero-knowledge range proofs to show that the tree is constructed correctly without revealing user data. TAP supports a broad range of verifiable operations, including quantiles and sample standard deviations. We conduct a comprehensive evaluation of TAP, and compare it against two state-of-the-art baselines, namely IntegriDB and Merkle2, showing that the system is practical at scale.
UnGANable: Defending Against GAN-based Face Manipulation
Zheng Li, CISPA Helmholtz Center for Information Security; Ning Yu, Salesforce Research; Ahmed Salem, Microsoft Research; Michael Backes, Mario Fritz, and Yang Zhang, CISPA Helmholtz Center for Information Security
Deepfakes pose severe threats of visual misinformation to our society. One representative deepfake application is face manipulation that modifies a victim's facial attributes in an image, e.g., changing her age or hair color. The state-of-the-art face manipulation techniques rely on Generative Adversarial Networks (GANs). In this paper, we propose the first defense system, namely UnGANable, against GAN-inversion-based face manipulation. In specific, UnGANable focuses on defending GAN inversion, an essential step for face manipulation. Its core technique is to search for alternative images (called cloaked images) around the original images (called target images) in image space. When posted online, these cloaked images can jeopardize the GAN inversion process. We consider two state-of-the-art inversion techniques including optimization-based inversion and hybrid inversion, and design five different defenses under five scenarios depending on the defender's background knowledge. Extensive experiments on four popular GAN models trained on two benchmark face datasets show that UnGANable achieves remarkable effectiveness and utility performance, and outperforms multiple baseline methods. We further investigate four adaptive adversaries to bypass UnGANable and show that some of them are slightly effective.
Back to School: On the (In)Security of Academic VPNs
Ka Lok Wu, The Chinese University of Hong Kong; Man Hong Hue, The Chinese University of Hong Kong and Georgia Institute of Technology; Ngai Man Poon, The Chinese University of Hong Kong; Kin Man Leung, The University of British Columbia; Wai Yin Po, Kin Ting Wong, Sze Ho Hui, and Sze Yiu Chau, The Chinese University of Hong Kong
In this paper, we investigate the security of academic VPNs around the globe, covering various protocols that are used to realize VPN services. Our study considers 3 aspects that can go wrong in a VPN setup, which include (i) the design and implementation of VPN front-ends, (ii) the client-side configurations, and (iii) the back-end configurations. For (i), we tested more than 140 front-ends, and discovered numerous design and implementation issues that enable stealthy but severe attacks, including credential theft and remote code execution. For (ii), we collected and evaluated 2097 VPN setup guides from universities, and discovered many instances of secret key leakage and lack of consideration to potential attacks, leaving many client-side setups vulnerable. Finally, for (iii), we probed more than 2000 VPN back-ends to evaluate their overall health, and uncovered some concerning configuration and maintenance issues on many of them. Our findings suggest that severe cracks exist in the VPN setups of many organizations, making them profitable targets for criminals.
Squint Hard Enough: Attacking Perceptual Hashing with Adversarial Machine Learning
Jonathan Prokos, Johns Hopkins University; Neil Fendley, Johns Hopkins University Applied Physics Laboratory; Matthew Green, Johns Hopkins University; Roei Schuster, Vector Institute; Eran Tromer, Tel Aviv University and Columbia University; Tushar Jois and Yinzhi Cao, Johns Hopkins University
Many online communications systems use perceptual hash matching systems to detect illicit files in user content. These systems employ specialized perceptual hash functions such as Microsoft's PhotoDNA or Facebook's PDQ to produce a compact digest of an image file that can be approximately compared to a database of known illicit-content digests. Recently, several proposals have suggested that hash-based matching systems be incorporated into client-side and end-to-end encrypted (E2EE) systems: in these designs, files that register as illicit content will be reported to the provider, while the remaining content will be sent confidentially. By using perceptual hashing to determine confidentiality guarantees, this new setting significantly changes the function of existing perceptual hashing — thus motivating the need to evaluate these functions from an adversarial perspective, using their perceptual capabilities against them. For example, an attacker may attempt to trigger a match on innocuous, but politically-charged, content in an attempt to stifle speech.
In this work we develop threat models for perceptual hashing algorithms in an adversarial setting, and present attacks against the two most widely deployed algorithms: PhotoDNA and PDQ. Our results show that it is possible to efficiently generate targeted second-preimage attacks in which an attacker creates a variant of some source image that matches some target digest. As a complement to this main result, we also further investigate the production of images that facilitate detection avoidance attacks , continuing a recent investigation of Jain et al. Our work shows that existing perceptual hash functions are likely insufficiently robust to survive attacks on this new setting.
"All of them claim to be the best": Multi-perspective study of VPN users and VPN providers
Reethika Ramesh, University of Michigan; Anjali Vyas, Cornell Tech; Roya Ensafi, University of Michigan
As more users adopt VPNs for a variety of reasons, it is important to develop empirical knowledge of their needs and mental models of what a VPN offers. Moreover, studying VPN users alone is not enough because, by using a VPN, a user essentially transfers trust, say from their network provider, onto the VPN provider. To that end, we are the first to study the VPN ecosystem from both the users' and the providers' perspectives. In this paper, we conduct a quantitative survey of 1,252 VPN users in the U.S. and qualitative interviews of nine providers to answer several research questions regarding the motivations, needs, threat model, and mental model of users, and the key challenges and insights from VPN providers. We create novel insights by augmenting our multi-perspective results, and highlight cases where the user and provider perspectives are misaligned. Alarmingly, we find that users rely on and trust VPN review sites, but VPN providers shed light on how these sites are mostly motivated by money. Worryingly, we find that users have flawed mental models about the protection VPNs provide, and about data collected by VPNs. We present actionable recommendations for technologists and security and privacy advocates by identifying potential areas on which to focus efforts and improve the VPN ecosystem.
GlitchHiker: Uncovering Vulnerabilities of Image Signal Transmission with IEMI
Qinhong Jiang, Xiaoyu Ji, Chen Yan, Zhixin Xie, Haina Lou, and Wenyuan Xu, Zhejiang University
Cameras have evolved into one of the most important gadgets in a variety of applications. In this paper, we identify a new class of vulnerabilities involving the hitherto disregarded image signal transmission phase and explain the underlying principles of camera glitches for the first time. Based on the vulnerabilities, we design the GlitchHiker attack that can actively induce controlled glitch images of a camera at various positions, widths, and numbers using intentional electromagnetic interference (IEMI). We successfully launch the GlitchHiker attack on 8 off-the-shelf camera systems in 5 categories in their original packages at a distance of up to 30 cm. Experiments with 2 case studies involving 4 object detectors and 2 face detectors show that injecting one ribboning suffices to hide, create or alter objects and persons with a maximum success rate of 98.5% and 80.4%, respectively. Then, we discuss real-world attack scenarios and perform preliminary investigations on the feasibility of targeted attacks. Finally, we propose hardware- and software-based countermeasures.
Device Tracking via Linux’s New TCP Source Port Selection Algorithm
Moshe Kol, Amit Klein, and Yossi Gilad, Hebrew University of Jerusalem
We describe a tracking technique for Linux devices, exploiting a new TCP source port generation mechanism recently introduced to the Linux kernel. This mechanism is based on an algorithm, standardized in RFC 6056, for boosting security by better randomizing port selection. Our technique detects collisions in a hash function used in the said algorithm, based on sampling TCP source ports generated in an attacker-prescribed manner. These hash collisions depend solely on a per-device key, and thus the set of collisions forms a device ID that allows tracking devices across browsers, browser privacy modes, containers, and IPv4/IPv6 networks (including some VPNs). It can distinguish among devices with identical hardware and software, and lasts until the device restarts.
We implemented this technique and then tested it using tracking servers in two different locations and with Linux devices on various networks. We also tested it on an Android device that we patched to introduce the new port selection algorithm. The tracking technique works in real-life conditions, and we report detailed findings about it, including its dwell time, scalability, and success rate in different network types. We worked with the Linux kernel team to mitigate the exploit, resulting in a security patch introduced in May 2022 to the Linux kernel, and we provide recommendations for better securing the port selection algorithm in the paper.
The Writing on the Wall and 3D Digital Twins: Personal Information in (not so) Private Real Estate
Rachel McAmis and Tadayoshi Kohno, University of Washington
Online real estate companies are starting to offer 3D virtual tours of homes (3D digital twins). We qualitatively analyzed 44 3D home tours with personal artifacts visible on Zillow and assessed each home for the extent and type of personal information shared. Using a codebook we created, we analyzed three categories of personal information in each home: government-provided guidance of what not to share on the internet, identity information, and behavioral information. Our analysis unearthed a wide variety of sensitive information across all homes, including names, hobbies, employment and education history, product preferences (e.g., pantry items, types of cigarettes), medications, credit card numbers, passwords, and more. Based on our analysis, residents both employed privacy protections and had privacy oversights. We identify potential adversaries that might use 3D tour information, highlight additional sensitive sources of indoor space information, and discuss future tools and policy changes that could address these issues.
PrivTrace: Differentially Private Trajectory Synthesis by Adaptive Markov Models
Haiming Wang, Zhejiang University; Zhikun Zhang, CISPA Helmholtz Center for Information Security; Tianhao Wang, University of Virginia; Shibo He, Zhejiang University; Michael Backes, CISPA Helmholtz Center for Information Security; Jiming Chen, Zhejiang University; Yang Zhang, CISPA Helmholtz Center for Information Security
Publishing trajectory data (individual's movement information) is very useful, but it also raises privacy concerns. To handle the privacy concern, in this paper, we apply differential privacy, the standard technique for data privacy, together with Markov chain model, to generate synthetic trajectories. We notice that existing studies all use Markov chain model and thus propose a framework to analyze the usage of the Markov chain model in this problem. Based on the analysis, we come up with an effective algorithm PrivTrace that uses the first-order and second-order Markov model adaptively. We evaluate PrivTrace and existing methods on synthetic and real-world datasets to demonstrate the superiority of our method.
Egg Hunt in Tesla Infotainment: A First Look at Reverse Engineering of Qt Binaries
Haohuang Wen and Zhiqiang Lin, The Ohio State University
As one of the most popular C++ extensions for developing graphical user interface (GUI) based applications, Qt has been widely used in desktops, mobiles, IoTs, automobiles, etc. Although existing binary analysis platforms (e.g., angr and Ghidra) could help reverse engineer Qt binaries, they still need to address many fundamental challenges such as the recovery of control flow graphs and symbols. In this paper, we take a first look at understanding the unique challenges and opportunities in Qt binary analysis, developing enabling techniques, and demonstrating novel applications. In particular, although callbacks make control flow recovery challenging, we notice that Qt’s signal and slot mechanism can be used to recover function callbacks. More interestingly, Qt’s unique dynamic introspection can also be repurposed to recover semantic symbols. Based on these insights, we develop QtRE for function callback and semantic symbol recovery for Qt binaries. We have tested QtRE with two suites of Qt binaries: Linux KDE and the Tesla Model S firmware, where QtRE additionally recovered 10,867 callback instances and 24,973 semantic symbols from 123 binaries, which cannot be identified by existing tools. We demonstrate a novel application of using QtRE to extract hidden commands from a Tesla Model S firmware. QtRE discovered 12 hidden commands including five unknown to the public, which can potentially be exploited to manipulate vehicle settings.
Learning Normality is Enough: A Software-based Mitigation against Inaudible Voice Attacks
Xinfeng Li, Xiaoyu Ji, and Chen Yan, USSLAB, Zhejiang University; Chaohao Li, USSLAB, Zhejiang University and Hangzhou Hikvision Digital Technology Co., Ltd.; Yichen Li, Hong Kong University of Science and Technology; Zhenning Zhang, University of Illinois at Urbana-Champaign; Wenyuan Xu, USSLAB, Zhejiang University
Inaudible voice attacks silently inject malicious voice commands into voice assistants to manipulate voice-controlled devices such as smart speakers. To alleviate such threats for both existing and future devices, this paper proposes NormDetect, a software-based mitigation that can be instantly applied to a wide range of devices without requiring any hardware modification. To overcome the challenge that the attack patterns vary between devices, we design a universal detection model that does not rely on audio features or samples derived from specific devices. Unlike existing studies’ supervised learning approach, we adopt unsupervised learning inspired by anomaly detection. Though the patterns of inaudible voice attacks are diverse, we find that benign audios share similar patterns in the time-frequency domain. Therefore, we can detect the attacks (the anomaly) by learning the patterns of benign audios (the normality). NormDetect maps spectrum features to a low-dimensional space, performs similarity queries, and replaces them with the standard feature embeddings for spectrum reconstruction. This results in a more significant reconstruction error for attacks than normality. Evaluation based on the 383,320 test samples we collected from 24 smart devices shows an average AUC of 99.48% and EER of 2.23%, suggesting the effectiveness of NormDetect in detecting inaudible voice attacks.
FirmSolo: Enabling dynamic analysis of binary Linux-based IoT kernel modules
Ioannis Angelakopoulos, Gianluca Stringhini, and Manuel Egele, Boston University
The Linux-based firmware running on Internet of Things (IoT) devices is complex and consists of user level programs as well as kernel level code. Both components have been shown to have serious security vulnerabilities, and the risk linked to kernel vulnerabilities is particularly high, as these can lead to full system compromise. However, previous work only focuses on the user space component of embedded firmware. In this paper, we present Firm ware Sol uti o n ( FirmSolo ), a system designed to incorporate the kernel space into firmware analysis. FirmSolo features the Kernel Configuration Reverse Engineering (K.C.R.E.) process that leverages information (i.e., exported and required symbols and version magic) from the kernel modules found in firmware images to build a kernel that can load the modules within an emulated environment. This capability allows downstream analysis to broaden their scope into code executing in privileged mode.
We evaluated FirmSolo on 1,470 images containing 56,688 kernel modules where it loaded 64% of the kernel modules. To demonstrate how FirmSolo aids downstream analysis, we integrate it with two representative analysis systems; the TriforceAFL kernel fuzzer and Firmadyne, a dynamic firmware analysis tool originally devoid of kernel mode analysis capabilities. Our TriforceAFL experiments on a subset of 75 kernel modules discovered 19 previously-unknown bugs in 11 distinct proprietary modules. Through Firmadyne we confirmed the presence of these previously-unknown bugs in 84 firmware images. Furthermore, by using FirmSolo , Firmadyne confirmed a previously-known memory corruption vulnerability in five different versions of the closed-source Kcodes' NetUSB module across 15 firmware images.
CacheQL: Quantifying and Localizing Cache Side-Channel Vulnerabilities in Production Software
Yuanyuan Yuan, Zhibo Liu, and Shuai Wang, The Hong Kong University of Science and Technology
Cache side-channel attacks extract secrets by examining how victim software accesses cache. To date, practical attacks on crypto systems and media libraries are demonstrated under different scenarios, inferring secret keys from crypto algorithms and reconstructing private media data such as images.
This work first presents eight criteria for designing a fullfledged detector for cache side-channel vulnerabilities. Then, we propose CacheQL , a novel detector that meets all of these criteria. CacheQL precisely quantifies information leaks of binary code, by characterizing the distinguishability of logged side channel traces. Moreover, CacheQL models leakage as a cooperative game, allowing information leakage to be precisely distributed to program points vulnerable to cache side channels. CacheQL is meticulously optimized to analyze whole side channel traces logged from production software (where each trace can have millions of records), and it alleviates randomness introduced by crypto blinding, ORAM, or real-world noises.
Our evaluation quantifies side-channel leaks of production crypto and media software. We further localize vulnerabilities reported by previous detectors and also identify a few hundred new vulnerable program points in recent OpenSSL (ver. 3.0.0), MbedTLS (ver. 3.0.0), Libgcrypt (ver. 1.9.4). Many of our localized program points are within the pre-processing modules of crypto libraries, which are not analyzed by existing works due to scalability. We also localize vulnerabilities in Libjpeg (ver. 2.1.2) that leak privacy about input images.
“If sighted people know, I should be able to know:” Privacy Perceptions of Bystanders with Visual Impairments around Camera-based Technology
Yuhang Zhao, University of Wisconsin—Madison; Yaxing Yao, University of Maryland, Baltimore County; Jiaru Fu and Nihan Zhou, University of Wisconsin—Madison
Camera-based technology can be privacy-invasive, especially for bystanders who can be captured by the cameras but do not have direct control or access to the devices. The privacy threats become even more significant to bystanders with visual impairments (BVI) since they cannot visually discover the use of cameras nearby and effectively avoid being captured. While some prior research has studied visually impaired people's privacy concerns as direct users of camera-based assistive technologies, no research has explored their unique privacy perceptions and needs as bystanders. We conducted an in-depth interview study with 16 visually impaired participants to understand BVI's privacy concerns, expectations, and needs in different camera usage scenarios. A preliminary survey with 90 visually impaired respondents and 96 sighted controls was conducted to compare BVI and sighted bystanders' general attitudes towards cameras and elicit camera usage scenarios for the interview study. Our research revealed BVI's unique privacy challenges and perceptions around cameras, highlighting their needs for privacy awareness and protection. We summarized design considerations for future privacy-enhancing technologies to fulfill BVI's privacy needs.
Access Denied: Assessing Physical Risks to Internet Access Networks
Alexander Marder, CAIDA / UC San Diego; Zesen Zhang, UC San Diego; Ricky Mok and Ramakrishna Padmanabhan, CAIDA / UC San Diego; Bradley Huffaker, CAIDA/ UC San Diego; Matthew Luckie, University of Waikato; Alberto Dainotti, Georgia Tech; kc claffy, CAIDA/ UC San Diego; Alex C. Snoeren and Aaron Schulman, UC San Diego
Regional access networks play an essential role in connecting both wireline and mobile users to the Internet. Today’s access networks support 5G cellular phones, cloud services, hospital and financial services, and remote work essential to the modern economy. Yet long-standing economic and architectural constraints produce points of limited redundancy that leave these networks exposed to targeted physical attacks resulting in widespread outages. This risk was dramatically shown in December 2020, when a bomb destroyed part of AT&T’s regional access network in Nashville, Tennessee disabling 911 emergency dispatch, air traffic control, hospital networks, and credit card processing, among other services.
We combine new techniques for analyzing access-network infrastructure deployments with measurements of large-scale outages to demonstrate the feasibility and quantify potential impacts of targeted attacks. Our study yields insights into physical attack surfaces and resiliency limits of regional access networks. We analyze potential approaches to mitigate the risks we identify and discuss drawbacks identified by network operators. We hope that our empirical evaluation will inform risk assessments and operational practices, as well as motivate further analyses of this critical infrastructure.
Security and Privacy Failures in Popular 2FA Apps
Conor Gilsenan, UC Berkeley / ICSI; Fuzail Shakir and Noura Alomar, UC Berkeley; Serge Egelman, UC Berkeley / ICSI
The Time-based One-Time Password (TOTP) algorithm is a 2FA method that is widely deployed because of its relatively low implementation costs and purported security benefits over SMS 2FA. However, users of TOTP 2FA apps face a critical usability challenge: maintain access to the secrets stored within the TOTP app, or risk getting locked out of their accounts. To help users avoid this fate, popular TOTP apps implement a wide range of backup mechanisms, each with varying security and privacy implications. In this paper, we define an assessment methodology for conducting systematic security and privacy analyses of the backup and recovery functionality of TOTP apps. We identified all general purpose Android TOTP apps in the Google Play Store with at least 100k installs that implemented a backup mechanism ( n = 22). Our findings show that most backup strategies end up placing trust in the same technologies that TOTP 2FA is meant to supersede: passwords, SMS, and email. Many backup implementations shared personal user information with third parties, had serious cryptographic flaws, and/or allowed the app developers to access the TOTP secrets in plaintext. We present our findings and recommend ways to improve the security and privacy of TOTP 2FA app backup mechanisms.
A comprehensive, formal and automated analysis of the EDHOC protocol
Charlie Jacomme, Inria Paris; Elise Klein, Steve Kremer, and Maïwenn Racouchot, Inria Nancy and Université de Lorraine
EDHOC is a key exchange proposed by IETF’s Lightweight Authenticated Key Exchange (LAKE) Working Group (WG). Its design focuses on small message sizes to be suitable for constrained IoT communication technologies. In this paper we provide an in-depth formal analysis of EDHOC–draft version 12, taking into account the different proposed authentication methods and various options. For our analysis we use the SAPIC+ protocol platform that allows to compile a single specification to 3 state-of-the-art protocol verification tools (PROVERIF, TAMARIN and DEEPSEC) and take advantage of the strengths of each of the tools. In our analysis we consider a large variety of compromise scenarios, and also exploit recent results that allow to model existing weaknesses in cryptographic primitives, relaxing the perfect cryptography assumption, common in symbolic analysis. While our analysis confirmed security for the most basic threat models, a number of weaknesses were uncovered in the current design when more advanced threat models were taken into account. These weaknesses have been acknowledged by the LAKE WG and the mitigations we propose (and prove secure) have been included in version 14 of the draft.
Hash Gone Bad: Automated discovery of protocol attacks that exploit hash function weaknesses
Vincent Cheval, Inria Paris; Cas Cremers and Alexander Dax, CISPA Helmholtz Center for Information Security; Lucca Hirschi, Inria & LORIA; Charlie Jacomme, Inria Paris; Steve Kremer, Université de Lorraine, LORIA, Inria Nancy Grand-Est
Distinguished Paper Award Winner
Most cryptographic protocols use cryptographic hash functions as a building block. The security analyses of these protocols typically assume that the hash functions are perfect (such as in the random oracle model). However, in practice, most widely deployed hash functions are far from perfect -- and as a result, the analysis may miss attacks that exploit the gap between the model and the actual hash function used.
We develop the first methodology to systematically discover attacks on security protocols that exploit weaknesses in widely deployed hash functions. We achieve this by revisiting the gap between theoretical properties of hash functions and the weaknesses of real-world hash functions, from which we develop a lattice of threat models. For all of these threat models, we develop fine-grained symbolic models.
Our methodology's fine-grained models cannot be directly encoded in existing state-of-the-art analysis tools by just using their equational reasoning. We therefore develop extensions for the two leading tools, Tamarin and Proverif. In extensive case studies using our methodology, the extended tools rediscover all attacks that were previously reported for these protocols and discover several new variants.
(M)WAIT for It: Bridging the Gap between Microarchitectural and Architectural Side Channels
Ruiyi Zhang, CISPA Helmholtz Center for Information Security; Taehyun Kim, Independent; Daniel Weber and Michael Schwarz, CISPA Helmholtz Center for Information Security
In the last years, there has been a rapid increase in microarchitectural attacks, exploiting side effects of various parts of the CPU. Most of them have in common that they rely on timing differences, requiring an architectural high-resolution timer to make microarchitectural states visible to an attacker.
In this paper, we present a new primitive that converts microarchitectural states into architectural states without relying on time measurements. We exploit the unprivileged idle-loop optimization instructions umonitor and umwait introduced with the new Intel microarchitectures (Tremont and Alder Lake). Although not documented, these instructions provide architectural feedback about the transient usage of a specified memory region. In three case studies, we show the versatility of our primitive. First, with Spectral, we present a way of enabling transient-execution attacks to leak bits architecturally with up to 200 kbit/s without requiring any architectural timer. Second, we show traditional side-channel attacks without relying on an architectural timer. Finally, we demonstrate that when augmented with a coarse-grained timer, we can also mount interrupt-timing attacks, allowing us to, e.g., detect which website a user opens. Our case studies highlight that the boundary between architecture and microarchitecture becomes more and more blurry, leading to new attack variants and complicating effective countermeasures.
Content-Type: multipart/oracle - Tapping into Format Oracles in Email End-to-End Encryption
Fabian Ising, Damian Poddebniak, Tobias Kappert, Christoph Saatjohann, and Sebastian Schinzel, Münster University of Applied Sciences
Fabian Ising, Münster University of Applied Sciences and National Research Center for Applied Cybersecurity ATHENE; Damian Poddebniak and Tobias Kappert, Münster University of Applied Sciences; Christoph Saatjohann and Sebastian Schinzel, Münster University of Applied Sciences and National Research Center for Applied Cybersecurity ATHENE
S/MIME and OpenPGP use cryptographic constructions repeatedly shown to be vulnerable to format oracle attacks in protocols like TLS, SSH, or IKE. However, format oracle attacks in the End-to-End Encryption (E2EE) email setting are considered impractical as victims would need to open many attacker-modified emails and communicate the decryption result to the attacker. But is this really the case?
In this paper, we survey how an attacker may remotely learn the decryption state in email E2EE. We analyze the interplay of MIME and IMAP and describe side-channels emerging from network patterns that leak the decryption status in Mail User Agents (MUAs). Concretely, we introduce specific MIME trees that produce decryption-dependent network patterns when opened in a victim’s email client.
We survey 19 OpenPGP- and S/MIME-enabled email clients and four cryptographic libraries and uncover a side-channel leaking the decryption status of S/MIME messages in one client. Further, we discuss why the exploitation in the other clients is impractical and show that it is due to missing feature support and implementation quirks. These unintended defenses create an unfortunate conflict between usability and security. We present more rigid countermeasures for MUA developers and the standards to prevent exploitation.
Glowing in the Dark: Uncovering IPv6 Address Discovery and Scanning Strategies in the Wild
Hammas Bin Tanveer, The University of Iowa; Rachee Singh, Microsoft and Cornell University; Paul Pearce, Georgia Tech; Rishab Nithyanand, University of Iowa
In this work we identify scanning strategies of IPv6 scanners on the Internet. We offer a unique perspective on the behavior of IPv6 scanners by conducting controlled experiments leveraging a large and unused /56 IPv6 subnet. We selectively make parts of the subnet visible to scanners by hosting applications that make direct or indirect contact with IPv6- capable servers on the Internet. By careful experiment design, we mitigate the effects of hidden variables on scans sent to our /56 subnet and establish causal relationships between IPv6 host activity types and the scanner attention they evoke. We show that IPv6 host activities e.g., Web browsing, membership in the NTP pool and Tor network, cause scanners to send a magnitude higher number of unsolicited IP scans and reverse DNS queries to our subnet than before. DNS scanners focus their scans in narrow regions of the address space where our applications are hosted whereas IP scanners broadly scan the entire subnet. Even after the host activity from our subnet subsides, we observe persistent residual scanning to portions of the address space that previously hosted applications.
Every Signature is Broken: On the Insecurity of Microsoft Office’s OOXML Signatures
Simon Rohlmann, Vladislav Mladenov, Christian Mainka, Daniel Hirschberger, and Jörg Schwenk, Ruhr University Bochum
Microsoft Office is one of the most widely used applications for office documents. For documents of prime importance, such as contracts and invoices, the content can be signed to guarantee authenticity and integrity. Since 2019, security researchers have uncovered attacks against the integrity protection in other office standards like PDF and ODF. Since Microsoft Office documents rely on different specifications and processing rules, the existing attacks are not applicable.
We are the first to provide an in-depth analysis of Office Open XML (OOXML) Signatures, the Ecma/ISO standard that all Microsoft Office applications use. Our analysis reveals major discrepancies between the structure of office documents and the way digital signatures are verified. These discrepancies lead to serious security flaws in the specification and in the implementation. As a result, we discovered five new attack classes. Each attack allows attackers to modify the content in signed documents, while the signatures are still displayed as valid.
We tested the attacks against different Microsoft Office versions on Windows and macOS, as well as against OnlyOffice Desktop on Windows, macOS and Linux. All tested Office versions are vulnerable. On macOS, we could reveal a surprising result: although Microsoft Office indicates that the document is protected by a signature, the signature is not validated. The attacks’ impact is alarming: attackers can arbitrarily manipulate the displayed content of a signed document, and victims are unable to detect the tampering. Even worse, we present a universal signature forgery attack that allows the attacker to create an arbitrary document and apply a signature extracted from a different source, such as an ODF document or a SAML token. For the victim, the document is displayed as validly signed by a trusted entity.
We propose countermeasures to prevent such issues in the future. During a coordinated disclosure, Microsoft acknowledged and awarded our research with a bug bounty.
Humans vs. Machines in Malware Classification
Simone Aonzo, EURECOM; Yufei Han, INRIA; Alessandro Mantovani and Davide Balzarotti, EURECOM
Today, the classification of a file as either benign or malicious is performed by a combination of deterministic indicators (such as antivirus rules), Machine Learning classifiers, and, more importantly, the judgment of human experts.
However, to compare the difference between human and machine intelligence in malware analysis, it is first necessary to understand how human subjects approach malware classification. In this direction, our work presents the first experimental study designed to capture which `features' of a suspicious program (e.g., static properties or runtime behaviors) are prioritized for malware classification according to humans and machines intelligence. For this purpose, we created a malware classification game where 110 human players worldwide and with different seniority levels (72 novices and 38 experts) have competed to classify the highest number of unknown samples based on detailed sandbox reports. Surprisingly, we discovered that both experts and novices base their decisions on approximately the same features, even if there are clear differences between the two expertise classes.
Furthermore, we implemented two state-of-the-art Machine Learning models for malware classification and evaluated their performances on the same set of samples. The comparative analysis of the results unveiled a common set of features preferred by both Machine Learning models and helped better understand the difference in the feature extraction.
This work reflects the difference in the decision-making process of humans and computer algorithms and the different ways they extract information from the same data. Its findings serve multiple purposes, from training better malware analysts to improving feature encoding.
How fast do you heal? A taxonomy for post-compromise security in secure-channel establishment
Olivier Blazy, LIX, CNRS, Inria, École Polytechnique, Institut Polytechnique de Paris, France; Ioana Boureanu, University of Surrey, Surrey Centre for Cyber Security, UK; Pascal Lafourcade, LIMOS, University of Clermont Auvergne, France; Cristina Onete, XLIM, University of Limoges, France; Léo Robert, LIMOS, University of Clermont Auvergne, France
Post-Compromise Security (PCS) is a property of secure-channel establishment schemes, which limits the security breach of an adversary that has compromised one of the endpoint to a certain number of messages, after which the channel heals. An attractive property, especially in view of Snowden’s revelation of mass-surveillance, PCS was pioneered by the Signal messaging protocol, and is present in OTR. In this paper, we introduce a framework for quantifying and comparing PCS security, with respect to a broad taxonomy of adversaries. The generality and flexibility of our approach allows us to model the healing speed of a broad class of protocols, including Signal, but also an identity-based messaging protocol named SAID, and even a composition of 5G handover protocols.
Assessing Anonymity Techniques Employed in German Court Decisions: A De-Anonymization Experiment
Dominic Deuber and Michael Keuchen, Friedrich-Alexander-Universität Erlangen-Nürnberg; Nicolas Christin, Carnegie Mellon University
Democracy requires transparency. Consequently, courts of law must publish their decisions. At the same time, the interests of the persons involved in these court decisions must be protected. For this reason, court decisions in Europe are anonymized using a variety of techniques. To understand how well these techniques protect the persons involved, we conducted an empirical experiment with 54 law students, whom we asked to de-anonymize 50 German court decisions. We found that all anonymization techniques used in these court decisions were vulnerable, most notably the use of initials. Since even supposedly secure anonymization techniques proved vulnerable, our work empirically reveals the complexity involved in the anonymization of court decisions, and thus calls for further research to increase anonymity while preserving comprehensibility. Toward that end, we provide recommendations for improving anonymization quality. Finally, we provide an empirical notion of “reasonable effort,” to flesh out the definition of anonymity in the legal context. In doing so, we bridge the gap between the technical and the legal understandings of anonymity.
GLeeFuzz: Fuzzing WebGL Through Error Message Guided Mutation
Hui Peng, Purdue University; Zhihao Yao and Ardalan Amiri Sani, UC Irvine; Dave (Jing) Tian, Purdue University; Mathias Payer, EPFL
WebGL is a set of standardized JavaScript APIs for GPU accelerated graphics. Security of the WebGL interface is paramount because it exposes remote and unsandboxed access to the underlying graphics stack (including the native GL libraries and GPU drivers) in the host OS. Unfortunately, applying state-of-the-art fuzzing techniques to the WebGL interface for vulnerability discovery is challenging because of (1) its huge input state space, and (2) the infeasibility of collecting code coverage across concurrent processes, closed-source libraries, and device drivers in the kernel.
Our fuzzing technique, GLeeFuzz, guides input mutation by error messages instead of code coverage. Our key observation is that browsers emit meaningful error messages to aid developers in debugging their WebGL programs. Error messages indicate which part of the input fails (e.g., incomplete arguments, invalid arguments, or unsatisfied dependencies between API calls). Leveraging error messages as feedback, the fuzzer effectively expands coverage by focusing mutation on erroneous parts of the input. We analyze Chrome’s WebGL implementation to identify the dependencies between error-emitting statements and rejected parts of the input, and use this information to guide input mutation. We evaluate our GLeeFuzz prototype on Chrome, Firefox, and Safari on diverse desktop and mobile OSes. We discovered 7 vulnerabilities, 4 in Chrome, 2 in Safari, and 1 in Firefox. The Chrome vulnerabilities allow a remote attacker to freeze the GPU and possibly execute remote code at the browser privilege.
Are You Spying on Me? Large-Scale Analysis on IoT Data Exposure through Companion Apps
Yuhong Nan, Sun Yat-sen University; Xueqiang Wang, University of Central Florida; Luyi Xing and Xiaojing Liao, Indiana University Bloomington; Ruoyu Wu and Jianliang Wu, Purdue University; Yifan Zhang and XiaoFeng Wang, Indiana University Bloomington
Recent research has highlighted privacy as a primary concern for IoT device users. However, due to the challenges in conducting a large-scale study to analyze thousands of devices, there has been less study on how pervasive unauthorized data exposure has actually become on today's IoT devices and the privacy implications of such exposure. To fill this gap, we leverage the observation that most IoT devices on the market today use their companion mobile apps as an intermediary to process, label and transmit the data they collect. As a result, the semantic information carried by these apps can be recovered and analyzed automatically to track the collection and sharing of IoT data.
In this paper, we report the first of such a study, based upon a new framework IoTProfiler, which statically analyzes a large number of companion apps to infer and track the data collected by their IoT devices. Our approach utilizes machine learning to detect the code snippet in a companion app that handles IoT data and further recovers the semantics of the data from the snippet to evaluate whether their exposure has been properly communicated to the user. By running IoTProfiler on 6,208 companion apps, our research has led to the discovery of 1,973 apps that expose user data without proper disclosure, covering IoT devices from at least 1,559 unique vendors. Our findings include highly sensitive information, such as health status and home address, and the pervasiveness of unauthorized sharing of the data to third parties, including those in different countries. Our findings highlight the urgent need to regulate today's IoT industry to protect user privacy.
The Space of Adversarial Strategies
Ryan Sheatsley, Blaine Hoak, Eric Pauley, and Patrick McDaniel, University of Wisconsin-Madison
Adversarial examples , inputs designed to induce worst-case behavior in machine learning models, have been extensively studied over the past decade. Yet, our understanding of this phenomenon stems from a rather fragmented pool of knowledge; at present, there are a handful of attacks, each with disparate assumptions in threat models and incomparable definitions of optimality. In this paper, we propose a systematic approach to characterize worst-case (i.e., optimal) adversaries. We first introduce an extensible decomposition of attacks in adversarial machine learning by atomizing attack components into surfaces and travelers . With our decomposition, we enumerate over components to create 576 attacks (568 of which were previously unexplored). Next, we propose the Pareto Ensemble Attack (PEA): a theoretical attack that upper-bounds attack performance. With our new attacks, we measure performance relative to the PEA on: both robust and non-robust models, seven datasets, and three extended ℓ p -based threat models incorporating compute costs, formalizing the Space of Adversarial Strategies . From our evaluation we find that attack performance to be highly contextual: the domain, model robustness, and threat model can have a profound influence on attack efficacy. Our investigation suggests that future studies measuring the security of machine learning should: (1) be contextualized to the domain & threat models, and (2) go beyond the handful of known attacks used today.
Credit Karma: Understanding Security Implications of Exposed Cloud Services through Automated Capability Inference
Xueqiang Wang, University of Central Florida; Yuqiong Sun, Meta; Susanta Nanda, ServiceNow; XiaoFeng Wang, Indiana University Bloomington
The increasing popularity of mobile applications (apps) has led to a rapid increase in demand for backend services, such as notifications, data storage, authentication, etc., hosted in cloud platforms. This has induced the attackers to consistently target such cloud services, resulting in a rise in data security incidents. In this paper, we focus on one of the main reasons why cloud services become increasingly vulnerable: (over-)privileges in cloud credentials. We propose a systematic approach to recover cloud credentials from apps, infer their capabilities in cloud, and verify if the capabilities exceed the legitimate needs of the apps. We further look into the security implications of the leaked capabilities, demonstrating how seemingly benevolent, unprivileged capabilities, when combined, can lead to unexpected, severe security problems. A large-scale study of ~1.3 million apps over two types of cloud services, notification and storage, on three popular cloud platforms, AWS, Azure, and Alibaba Cloud, shows that ~27.3% of apps that use cloud services expose over-privileged cloud credentials. Moreover, a majority of over-privileged cloud credentials (~64.8%) potentially lead to data attacks. During the study, we also uncover new types of attacks enabled by regular cloud credentials, such as spear-phishing through push notification and targeted user data pollution. We have made responsible disclosures to both app vendors and cloud providers and start seeing the impact---over 300 app vendors already fixed the problems.
That Person Moves Like A Car: Misclassification Attack Detection for Autonomous Systems Using Spatiotemporal Consistency
Yanmao Man, University of Arizona; Raymond Muller, Purdue University; Ming Li, University of Arizona; Z. Berkay Celik, Purdue University; Ryan Gerdes, Virginia Tech
Autonomous systems commonly rely on object detection and tracking (ODT) to perceive the environment and predict the trajectory of surrounding objects for planning purposes. An ODT’s output contains object classes and tracks that are traditionally predicted independently. Recent studies have shown that ODT’s output can be falsified by various perception attacks with well-crafted noise, but existing defenses are limited to specific noise injection methods and thus fail to generalize. In this work we propose PercepGuard for the detection of misclassification attacks against perception modules regardless of attack methodologies. PercepGuard exploits the spatiotemporal properties of a detected object (inherent in the tracks), and cross-checks the consistency between the track and class predictions. To improve adversarial robustness against defense-aware (adaptive) attacks, we additionally consider context data (such as ego-vehicle velocity) for contextual consistency verification, which dramatically increases the attack difficulty. Evaluations with both real-world and simulated datasets produce a FPR of 5% and a TPR of 99% against adaptive attacks. A baseline comparison confirms the advantage of leveraging temporal features. Real-world experiments with displayed and projected adversarial patches show that PercepGuard detects 96% of the attacks on average.
CipherH: Automated Detection of Ciphertext Side-channel Vulnerabilities in Cryptographic Implementations
Sen Deng, Southern University of Science and Technology; Mengyuan Li, The Ohio State University; Yining Tang, Southern University of Science and Technology; Shuai Wang, Hong Kong University of Science and Technology; Shoumeng Yan, The Ant Group; Yinqian Zhang, Southern University of Science and Technology
The ciphertext side channel is a new type of side channels that exploits deterministic memory encryption of trusted execution environments (TEE). It enables the adversary with read accesses to the ciphertext of the encrypted memory, either logically or physically, to compromise cryptographic implementations protected by TEEs with high fidelity. Prior studies have concluded that the ciphertext side channel is a severe threat to not only AMD SEV-SNP, where the vulnerability was first discovered, but to all TEEs with deterministic memory encryption.
In this paper, we propose CipherH, a practical framework for automating the analysis of cryptographic software and detecting program points vulnerable to ciphertext side channels. CipherH is designed to perform a practical hybrid analysis in production cryptographic software, with a speedy dynamic taint analysis to track the usage of secrets throughout the entire program and a static symbolic execution procedure on each “tainted” function to reason about ciphertext side channel vulnerabilities using symbolic constraint. Empirical evaluation has led to the discovery of over 200 vulnerable program points from the state-of-the-art RSA and ECDSA/ECDH implementations from OpenSSL, MbedTLS, and WolfSSL. Representative cases have been reported to and confirmed or patched by the developers.
"My Privacy for their Security": Employees' Privacy Perspectives and Expectations when using Enterprise Security Software
Jonah Stegman, Patrick J. Trottier, Caroline Hillier, and Hassan Khan, University of Guelph; Mohammad Mannan, Concordia University
Employees are often required to use Enterprise Security Software (“ESS”) on corporate and personal devices. ESS products collect users’ activity data including users’ location, applications used, and websites visited — operating from employees’ device to the cloud. To the best of our knowledge, the privacy implications of this data collection have yet to be explored. We conduct an online survey (n=258) and a semistructured interview (n=22) with ESS users to understand their privacy perceptions, the challenges they face when using ESS, and the ways they try to overcome those challenges. We found that while many participants reported receiving no information about what data their ESS collected, those who received some information often underestimated what was collected. Employees reported lack of communication about various data collection aspects including: the entities with access to the data and the scope of the data collected. We use the interviews to uncover several sources of misconceptions among the participants. Our findings show that while employees understand the need for data collection for security, the lack of communication and ambiguous data collection practices result in the erosion of employees’ trust on the ESS and employers. We obtain suggestions from participants on how to mitigate these misconceptions and collect feedback on our design mockups of a privacy notice and privacy indicators for ESS. Our work will benefit researchers, employers, and ESS developers to protect users’ privacy in the growing ESS market.
Combating Robocalls with Phone Virtual Assistant Mediated Interaction
Sharbani Pandit, Georgia Institute of Technology; Krishanu Sarker, Georgia State University; Roberto Perdisci, University of Georgia and Georgia Institute of Technology; Mustaque Ahamad and Diyi Yang, Georgia Institute of Technology
Mass robocalls affect millions of people on a daily basis. Unfortunately, most current defenses against robocalls rely on phone blocklists and are ineffective against caller ID spoofing. To enable detection and blocking of spoofed robocalls, we propose a NLP based smartphone virtual assistant that automatically vets incoming calls. Similar to a human assistant, the virtual assistant picks up an incoming call and uses machine learning models to interact with the caller to determine if the call source is a human or a robocaller. It interrupts a user by ringing the phone only when the call is determined to be not from a robocaller. Security analysis performed by us shows that such a system can stop current and more sophisticated robocallers that might emerge in the future. We also conduct a user study that shows that the virtual assistant can preserve phone call user experience.
On the Feasibility of Malware Unpacking via Hardware-assisted Loop Profiling
Binlin Cheng, Shandong University & Hubei Normal University; Erika A Leal, Tulane University; Haotian Zhang, The University of Texas at Arlington; Jiang Ming, Tulane University
Hardware Performance Counters (HPCs) are built-in registers of modern processors to count the occurrences of various micro-architectural events. Measuring HPCs values is a cost-effective way to characterize dynamic program behaviors. Because of the ease of use and tamper-resistant advantages, using HPCs coupled with machine learning models to address security problems is on the rise in recent years. However, lately the suitability of HPCs for security has been questioned in light of the non-determinism concerns: measurement errors caused by interrupt skid and time-division multiplexing can undermine the effectiveness of using HPCs in security applications.
With these cautions in mind, we explore ways to tame hardware event’s non-determinism nature for malware unpacking, which is a long-standing challenge in malware analysis. Our research is motivated by two key observations. First, the unpacking process, which involves expensive iterations of decryption or decompression, can incur identifiable deviations in hardware events. Second, loop-centric HPCs profiling can minimize the imprecisions caused by interrupt skid and time-division multiplexing. Therefore, we utilize two mechanisms offered by Intel CPUs (i.e., Precise Event-Based Sampling (PEBS) and Last Branch Record) to develop a generic, hardware-assisted unpacking technique, called LoopHPCs. It offers a new, obfuscation-resilient solution to identify the original code from multiple “written-then-executed” layers. Our controlled experiments demonstrate that LoopHPCs can obtain precise and consistent HPCs values across different Intel CPU architectures and OSs.
Distance-Aware Private Set Intersection
Anrin Chakraborti, Duke University; Giulia Fanti, Carnegie Mellon University; Michael K. Reiter, Duke University
Private set intersection (PSI) allows two mutually untrusting parties to compute an intersection of their sets, without revealing information about items that are not in the intersection. This work introduces a PSI variant called distance-aware PSI (DA-PSI) for sets whose elements lie in a metric space. DAPSI returns pairs of items that are within a specified distance threshold of each other. This paper puts forward DA-PSI constructions for two metric spaces: (i) Minkowski distance of order 1 over the set of integers (i.e., for integers a and b, their distance is |a−b|); and (ii) Hamming distance over the set of binary strings of length ℓ. In the Minkowski DA-PSI protocol, the communication complexity scales logarithmically in the distance threshold and linearly in the set size. In the Hamming DA-PSI protocol, the communication volume scales quadratically in the distance threshold and is independent of the dimensionality of string length ℓ. Experimental results with real applications confirm that DA-PSI provides more effective matching at lower cost than naïve solutions.
NeuroPots: Realtime Proactive Defense against Bit-Flip Attacks in Neural Networks
Qi Liu, Lehigh University; Jieming Yin, Nanjing University of Posts and Telecommunications; Wujie Wen, Lehigh University; Chengmo Yang, University of Delaware; Shi Sha, Wilkes University
Deep neural networks (DNNs) are becoming ubiquitous in various safety- and security-sensitive applications such as self-driving cars and financial systems. Recent studies revealed that bit-flip attacks (BFAs) can destroy DNNs' functionality via DRAM rowhammer—by precisely injecting a few bit-flips into the quantized model parameters, attackers can either degrade the model accuracy to random guessing, or misclassify certain inputs into a target class. BFAs can cause catastrophic consequences if left undetected. However, detecting BFAs is challenging because bit-flips can occur on any weights in a DNN model, leading to a large detection surface. Unlike prior works that attempt to "patch'' vulnerabilities of DNN models, our work is inspired by the idea of "honeypot''. Specifically, we propose a proactive defense concept named NeuroPots, which embeds a few "honey neurons'' as crafted vulnerabilities into the DNN model to lure the attacker into injecting faults in them, thus making detection and model recovery efficient. We utilize NeuroPots to develop a trapdoor-enabled defense framework. We design a honey neuron selection strategy, and propose two methods for embedding trapdoors into the DNN model. Furthermore, since the majority of injected bit flips will concentrate in the trapdoors, we use a checksum-based detection approach to efficiently detect faults in them, and rescue the model accuracy by "refreshing'' those faulty trapdoors. Our experiments show that trapdoor-enabled defense achieves high detection performance and effectively recovers a compromised model at a low cost across a variety of DNN models and datasets.
Towards a General Video-based Keystroke Inference Attack
Zhuolin Yang, Yuxin Chen, and Zain Sarwar, University of Chicago; Hadleigh Schwartz, Columbia University; Ben Y. Zhao and Haitao Zheng, University of Chicago
A large collection of research literature has identified the privacy risks of keystroke inference attacks that use statistical models to extract content typed onto a keyboard. Yet existing attacks cannot operate in realistic settings, and rely on strong assumptions of labeled training data, knowledge of keyboard layout, carefully placed sensors or data from other side-channels. This paper describes experiences developing and evaluating a general, video-based keystroke inference attack that operates in common public settings using a single commodity camera phone, with no pretraining, no keyboard knowledge, no local sensors, and no side-channels. We show that using a self-supervised approach, noisy finger tracking data from a video can be processed, labeled and filtered to train DNN keystroke inference models that operate accurately on the same video. Using IRB approved user studies, we validate attack efficacy across a variety of environments, keyboards, and content, and users with different typing behaviors and abilities. Our project website is located at: https://sandlab.cs.uchicago.edu/keystroke/ .

URET: Universal Robustness Evaluation Toolkit (for Evasion)
Kevin Eykholt, Taesung Lee, Douglas Schales, Jiyong Jang, and Ian Molloy, IBM Research; Masha Zorin, University of Cambridge
Machine learning models are known to be vulnerable to adversarial evasion attacks as illustrated by image classification models. Thoroughly understanding such attacks is critical in order to ensure the safety and robustness of critical AI tasks. However, most evasion attacks are difficult to deploy against a majority of AI systems because they have focused on image domain with only few constraints. An image is composed of homogeneous, numerical, continuous, and independent features, unlike many other input types to AI systems used in practice. Furthermore, some input types include additional semantic and functional constraints that must be observed to generate realistic adversarial inputs. In this work, we propose a new framework to enable the generation of adversarial inputs irrespective of the input type and task domain. Given an input and a set of pre-defined input transformations, our framework discovers a sequence of transformations that result in a semantically correct and functional adversarial input. We demonstrate the generality of our approach on several diverse machine learning tasks with various input representations. We also show the importance of generating adversarial examples as they enable the deployment of mitigation techniques.
You Can't See Me: Physical Removal Attacks on LiDAR-based Autonomous Vehicles Driving Frameworks
Yulong Cao, University of Michigan; S. Hrushikesh Bhupathiraju and Pirouz Naghavi, University of Florida; Takeshi Sugawara, The University of Electro-Communications; Z. Morley Mao, University of Michigan; Sara Rampazzi, University of Florida
Autonomous Vehicles (AVs) increasingly use LiDAR-based object detection systems to perceive other vehicles and pedestrians on the road. While existing attacks on LiDAR-based autonomous driving architectures focus on lowering the confidence score of AV object detection models to induce obstacle misdetection, our research discovers how to leverage laser-based spoofing techniques to selectively remove the LiDAR point cloud data of genuine obstacles at the sensor level before being used as input to the AV perception. The ablation of this critical LiDAR information causes autonomous driving obstacle detectors to fail to identify and locate obstacles and, consequently, induces AVs to make dangerous automatic driving decisions. In this paper, we present a method invisible to the human eye that hides objects and deceives autonomous vehicles’ obstacle detectors by exploiting inherent automatic transformation and filtering processes of LiDAR sensor data integrated with autonomous driving frameworks. We call such attacks Physical Removal Attacks (PRA), and we demonstrate their effectiveness against three popular AV obstacle detectors (Apollo, Autoware, PointPillars), and we achieve 45◦ attack capability. We evaluate the attack impact on three fusion models (Frustum-ConvNet, AVOD, and Integrated-Semantic Level Fusion) and the consequences on the driving decision using LGSVL, an industry-grade simulator. In our moving vehicle scenarios, we achieve a 92.7% success rate removing 90% of a target obstacle’s cloud points. Finally, we demonstrate the attack’s success against two popular defenses against spoofing and object hiding attacks and discuss two enhanced defense strategies to mitigate our attack.
Framing Frames: Bypassing Wi-Fi Encryption by Manipulating Transmit Queues
Domien Schepers and Aanjhan Ranganathan, Northeastern University; Mathy Vanhoef, imec-DistriNet, KU Leuven
This paper is under embargo and will be released on the first day of the symposium.
Wi-Fi devices routinely queue frames at various layers of the network stack before transmitting, for instance, when the receiver is in sleep mode. In this work, we investigate how Wi-Fi access points manage the security context of queued frames. By exploiting power-save features, we show how to trick access points into leaking frames in plaintext, or encrypted using the group or an all-zero key. We demonstrate resulting attacks against several open-source network stacks. We attribute our findings to the lack of explicit guidance in managing security contexts of buffered frames in the 802.11 standards. The unprotected nature of the power-save bit in a frame’s header, which our work reveals to be a fundamental design flaw, also allows an adversary to force queue frames intended for a specific client resulting in its disconnection and trivially executing a denial-of-service attack. Furthermore, we demonstrate how an attacker can override and control the security context of frames that are yet to be queued. This exploits a design flaw in hotspot-like networks and allows the attacker to force an access points to encrypt yet to be queued frames using an adversary-chosen key, thereby bypassing Wi-Fi encryption entirely. Our attacks have a widespread impact as they affect various devices and operating systems (Linux, FreeBSD, iOS, and Android) and because they can be used to hijack TCP connections or intercept client and web traffic. Overall, we highlight the need for transparency in handling security context across the network stack layers and the challenges in doing so.
SMACK: Semantically Meaningful Adversarial Audio Attack
Zhiyuan Yu, Yuanhaur Chang, and Ning Zhang, Washington University in St. Louis; Chaowei Xiao, Arizona State University
Voice controllable systems rely on speech recognition and speaker identification as the key enabling technologies. While they bring revolutionary changes to our daily lives, their security has become a growing concern. Existing work has demonstrated the feasibility of using maliciously crafted perturbations to manipulate speech or speaker recognition. Although these attacks vary in targets and techniques, they all require the addition of noise perturbations. While these perturbations are generally restricted to L p -bounded neighborhood, the added noises inevitably leave unnatural traces recognizable by humans, and can be used for defense. To address this limitation, we introduce a new class of adversarial audio attack, named S emantically M eaningful Adversarial A udio Atta CK (SMACK), where the inherent speech attributes (such as prosody) are modified such that they still semantically represent the same speech and preserves the speech quality. The efficacy of SMACK was evaluated against five transcription systems and two speaker recognition systems in a black-box manner. By manipulating semantic attributes, our adversarial audio examples are capable of evading the state-of-the-art defenses, with better speech naturalness compared to traditional L p -bounded attacks in the human perceptual study.
Gradient Obfuscation Gives a False Sense of Security in Federated Learning
Kai Yue, North Carolina State University; Richeng Jin, Zhejiang University; Chau-Wai Wong, Dror Baron, and Huaiyu Dai, North Carolina State University
Federated learning has been proposed as a privacy-preserving machine learning framework that enables multiple clients to collaborate without sharing raw data. However, client privacy protection is not guaranteed by design in this framework. Prior work has shown that the gradient sharing strategies in federated learning can be vulnerable to data reconstruction attacks. In practice, though, clients may not transmit raw gradients considering the high communication cost or due to privacy enhancement requirements. Empirical studies have demonstrated that gradient obfuscation, including intentional obfuscation via gradient noise injection and unintentional obfuscation via gradient compression, can provide more privacy protection against reconstruction attacks. In this work, we present a new reconstruction attack framework targeting the image classification task in federated learning. We show how commonly adopted gradient postprocessing procedures, such as gradient quantization, gradient sparsification, and gradient perturbation may give a false sense of security in federated learning. Contrary to prior studies, we argue that privacy enhancement should not be treated as a byproduct of gradient compression. Additionally, we design a new method under the proposed framework to reconstruct images at the semantic level. We quantify the semantic privacy leakage and compare it with conventional image similarity scores. Our comparisons challenge the image data leakage evaluation schemes in the literature. The results emphasize the importance of revisiting and redesigning the privacy protection mechanisms for client data in existing federated learning algorithms.
Automata-Guided Control-Flow-Sensitive Fuzz Driver Generation
Cen Zhang and Yuekang Li, Nanyang Technological University, Continental-NTU Corporate Lab; Hao Zhou, The Hong Kong Polytechnic University; Xiaohan Zhang, Xidian University; Yaowen Zheng, Nanyang Technological University, Continental-NTU Corporate Lab; Xian Zhan, Southern University of Science and Technology; The Hong Kong Polytechnic University; Xiaofei Xie, Singapore Management University; Xiapu Luo, The Hong Kong Polytechnic University; Xinghua Li, Xidian University; Yang Liu, Nanyang Technological University, Continental-NTU Corporate Lab; Sheikh Mahbub Habib, Continental AG, Germany
Fuzz drivers are essential for fuzzing library APIs. However, manually composing fuzz drivers is difficult and time-consuming. Therefore, several works have been proposed to generate fuzz drivers automatically. Although these works can learn correct API usage from the consumer programs of the target library, three challenges still hinder the quality of the generated fuzz drivers: 1) How to learn and utilize the control dependencies in API usage; 2) How to handle the noises of the learned API usage, especially for complex real-world consumer programs; 3) How to organize independent sets of API usage inside the fuzz driver to better coordinate with fuzzers.
To solve these challenges, we propose RUBICK, an automata-guided control-flow-sensitive fuzz driver generation technique. RUBICK has three key features: 1) it models the API usage (including API data and control dependencies) as a deterministic finite automaton; 2) it leverages active automata learning algorithm to distill the learned API usage; 3) it synthesizes a single automata-guided fuzz driver, which provides scheduling interface for the fuzzer to test independent sets of API usage during fuzzing. During the experiments, the fuzz drivers generated by RUBICK showed a significant performance advantage over the baselines by covering an average of 50.42% more edges than fuzz drivers generated by FUZZGEN and 44.58% more edges than manually written fuzz drivers from OSS-Fuzz or human experts. By learning from large-scale open source projects, RUBICK has generated fuzz drivers for 11 popular Java projects and two of them have been merged into OSS-Fuzz. So far, 199 bugs, including four CVEs, are found using these fuzz drivers, which can affect popular PC and Android software with dozens of millions of downloads.
Are Consumers Willing to Pay for Security and Privacy of IoT Devices?
Pardis Emami-Naeini, Duke University; Janarth Dheenadhayalan, Yuvraj Agarwal, and Lorrie Faith Cranor, Carnegie Mellon University
Internet of Things (IoT) device manufacturers provide little information to consumers about their security and data handling practices. Therefore, IoT consumers cannot make informed purchase choices around security and privacy. While prior research has found that consumers would likely consider security and privacy when purchasing IoT devices, past work lacks empirical evidence as to whether they would actually pay more to purchase devices with enhanced security and privacy. To fill this gap, we conducted a two-phase incentive-compatible online study with 180 Prolific participants. We measured the impact of five security and privacy factors (e.g., access control) on participants' purchase behaviors when presented individually or together on an IoT label. Participants were willing to pay a significant premium for devices with better security and privacy practices. The biggest price differential we found was for de-identified rather than identifiable cloud storage. Mainly due to its usability challenges, the least valuable improvement for participants was to have multi-factor authentication as opposed to passwords. Based on our findings, we provide recommendations on creating more effective IoT security and privacy labeling programs.
PhyAuth: Physical-Layer Message Authentication for ZigBee Networks
Ang Li and Jiawei Li, Arizona State University; Dianqi Han, University of Texas at Arlington; Yan Zhang, The University of Akron; Tao Li, Indiana University–Purdue University Indianapolis; Ting Zhu, The Ohio State University; Yanchao Zhang, Arizona State University
ZigBee is a popular wireless communication standard for Internet of Things (IoT) networks. Since each ZigBee network uses hop-by-hop network-layer message authentication based on a common network key, it is highly vulnerable to packet-injection attacks, in which the adversary exploits the compromised network key to inject arbitrary fake packets from any spoofed address to disrupt network operations and consume the network/device resources. In this paper, we present PhyAuth, a PHY hop-by-hop message authentication framework to defend against packet-injection attacks in ZigBee networks. The key idea of PhyAuth is to let each ZigBee transmitter embed into its PHY signals a PHY one-time password (called POTP) derived from a device-specific secret key and an efficient cryptographic hash function. An authentic POTP serves as the transmitter's PHY transmission permission for the corresponding packet. PhyAuth provides three schemes to embed, detect, and verify POTPs based on different features of ZigBee PHY signals. In addition, PhyAuth involves lightweight PHY signal processing and no change to the ZigBee protocol stack. Comprehensive USRP experiments confirm that PhyAuth can efficiently detect fake packets with very low false-positive and false-negative rates while having a negligible negative impact on normal data transmissions.
Fairness Properties of Face Recognition and Obfuscation Systems
Harrison Rosenberg, University of Wisconsin–Madison; Brian Tang, University of Michigan; Kassem Fawaz and Somesh Jha, University of Wisconsin–Madison
The proliferation of automated face recognition in the commercial and government sectors has caused significant privacy concerns for individuals. One approach to address these privacy concerns is to employ evasion attacks against the metric embedding networks powering face recognition systems: Face obfuscation systems generate imperceptibly perturbed images that cause face recognition systems to misidentify the user. Perturbed faces are generated on metric embedding networks, which are known to be unfair in the context of face recognition. A question of demographic fairness naturally follows: are there demographic disparities in face obfuscation system performance? We answer this question with an analytical and empirical exploration of recent face obfuscation systems. Metric embedding networks are found to be demographically aware: face embeddings are clustered by demographic. We show how this clustering behavior leads to reduced face obfuscation utility for faces in minority groups. An intuitive analytical model yields insight into these phenomena.
Beyond The Gates: An Empirical Analysis of HTTP-Managed Password Stealers and Operators
Athanasios Avgetidis, Omar Alrawi, Kevin Valakuzhy, and Charles Lever, Georgia Institute of Technology; Paul Burbage, MalBeacon; Angelos D. Keromytis, Fabian Monrose, and Manos Antonakakis, Georgia Institute of Technology
Password Stealers (Stealers) are commodity malware that specialize in credential theft. This work presents a large-scale longitudinal study of Stealers and their operators. Using a commercial dataset, we characterize the activity of over 4, 586 distinct Stealer operators through their devices spanning 10 different Stealer families. Operators make heavy use of proxies, including traditional VPNs, residential proxies, mobile proxies, and the Tor network when managing their botnet. Our affiliation analysis unveils a stratified enterprise of cybercriminals for each service offering and we identify privileged operators using graph analysis. We find several Stealer-as-a-Service providers that lower the economical and technical barrier for many cybercriminals. We estimate that service providers benefit from high-profit margins (up to 98%) and a lower-bound profit estimate of $11, 000 per month. We find high-profile targeting like the Social Security Administration, the U.S. House of Representatives, and the U.S. Senate. We share our findings with law enforcement and publish six months of the dataset, analysis artifact, and code.
Decompiling x86 Deep Neural Network Executables
Zhibo Liu, Yuanyuan Yuan, and Shuai Wang, The Hong Kong University of Science and Technology; Xiaofei Xie, Singapore Management University; Lei Ma, University of Alberta
Due to their widespread use on heterogeneous hardware devices, deep learning (DL) models are compiled into executables by DL compilers to fully leverage low-level hardware primitives. This approach allows DL computations to be undertaken at low cost across a variety of computing platforms, including CPUs, GPUs, and various hardware accelerators.
We present BTD (Bin to DNN), a decompiler for deep neural network (DNN) executables. BTD takes DNN executables and outputs full model specifications, including types of DNN operators, network topology, dimensions, and parameters that are (nearly) identical to those of the input models. BTD delivers a practical framework to process DNN executables compiled by different DL compilers and with full optimizations enabled on x86 platforms. It employs learning-based techniques to infer DNN operators, dynamic analysis to reveal network architectures, and symbolic execution to facilitate inferring dimensions and parameters of DNN operators.
Our evaluation reveals that BTD enables accurate recovery of full specifications of complex DNNs with millions of parameters (e.g., ResNet). The recovered DNN specifications can be re-compiled into a new DNN executable exhibiting identical behavior to the input executable. We show that BTD can boost two representative attacks, adversarial example generation and knowledge stealing, against DNN executables. We also demonstrate cross-architecture legacy code reuse using BTD, and envision BTD being used for other critical downstream tasks like DNN security hardening and patching.
PolyFuzz: Holistic Greybox Fuzzing of Multi-Language Systems
Wen Li, Jinyang Ruan, and Guangbei Yi, Washington State University; Long Cheng, Clemson University; Xiapu Luo, The Hong Kong Polytechnic University; Haipeng Cai, Washington State University
While offering many advantages during software process, the practice of using multiple programming languages in constructing one software system also introduces additional security vulnerabilities in the resulting code. As this practice becomes increasingly prevalent, securing multi-language systems is of pressing criticality. Fuzzing has been a powerful security testing technique, yet existing fuzzers are commonly limited to single-language software. In this paper, we present PolyFuzz, a greybox fuzzer that holistically fuzzes a given multi-language system through cross-language coverage feedback and explicit modeling of the semantic relationships between (various segments of) program inputs and branch predicates across languages. PolyFuzz is extensible for supporting multilingual code written in different language combinations and has been implemented for C, Python, Java, and their combinations. We evaluated PolyFuzz versus state-of-the-art single-language fuzzers for these languages as baselines against 15 real-world multi-language systems and 15 single-language benchmarks. PolyFuzz achieved 25.3–52.3% higher code coverage and found 1–10 more bugs than the baselines against the multilingual programs, and even 10-20% higher coverage against the single-language benchmarks. In total, PolyFuzz has enabled the discovery of 12 previously unknown multilingual vulnerabilities and 2 single-language ones, with 5 CVEs assigned. Our results show great promises of PolyFuzz for cross-language fuzzing, while justifying the strong need for holistic fuzzing against trivially applying single-language fuzzers to multi-language software.
Linear Private Set Union from Multi-Query Reverse Private Membership Test
Cong Zhang, State Key Laboratory of Information Security, Institute of Information Engineering, Chinese Academy of Sciences; School of Cyber Security, University of Chinese Academy of Sciences; Yu Chen, School of Cyber Science and Technology, Shandong University; State Key Laboratory of Cryptology; Key Laboratory of Cryptologic Technology and Information Security, Ministry of Education, Shandong University; Weiran Liu, Alibaba Group; Min Zhang, School of Cyber Science and Technology, Shandong University; State Key Laboratory of Cryptology; Key Laboratory of Cryptologic Technology and Information Security, Ministry of Education, Shandong University; Dongdai Lin, State Key Laboratory of Information Security, Institute of Information Engineering, Chinese Academy of Sciences; School of Cyber Security, University of Chinese Academy of Sciences
Private set union (PSU) protocol enables two parties, each holding a set, to compute the union of their sets without revealing anything else to either party. So far, there are two known approaches for constructing PSU protocols. The first mainly depends on additively homomorphic encryption (AHE), which is generally inefficient since it needs to perform a non-constant number of homomorphic computations on each item. The second is mainly based on oblivious transfer and symmetric-key operations, which is recently proposed by Kolesnikov et al. (ASIACRYPT 2019). It features good practical performance, which is several orders of magnitude faster than the first one. However, neither of these two approaches is optimal in the sense that their computation and communication complexity are not both O ( n ), where n is the size of the set. Therefore, the problem of constructing the optimal PSU protocol remains open.
In this work, we resolve this open problem by proposing a generic framework of PSU from oblivious transfer and a newly introduced protocol called multi-query reverse private membership test (mq-RPMT). We present two generic constructions of mq-RPMT. The first is based on symmetric-key encryption and general 2PC techniques. The second is based on re-randomizable public-key encryption. Both constructions lead to PSU with linear computation and communication complexity.
We implement our two PSU protocols and compare them with the state-of-the-art PSU. Experiments show that our PKE-based protocol has the lowest communication of all schemes, which is 3.7-14.8× lower depending on set size. The running time of our PSU scheme is 1.2-12× faster than that of state-of-the-art depending on network environments.
An Efficient Design of Intelligent Network Data Plane
Guangmeng Zhou, Tsinghua University; Zhuotao Liu, Tsinghua University and Zhongguancun Laboratory; Chuanpu Fu, Tsinghua University; Qi Li and Ke Xu, Tsinghua University and Zhongguancun Laboratory
Deploying machine learning models directly on the network data plane enables intelligent traffic analysis at line-speed using data-driven models rather than predefined protocols. Such a capability, referred to as Intelligent Data Plane (IDP), may potentially transform a wide range of networking designs. The emerging programmable switches provide crucial hardware support to realize IDP. Prior art in this regard is divided into two major categories: (i) focusing on extract useful flow information from the data plane, while placing the learning-based traffic analysis on the control plane; and (ii) taking a step further to embed learning models into the data plane, while failing to use flow-level features that are critical to achieve high learning accuracies. In this paper, we propose NetBeacon to advance the state-of-the-art in both model accuracy and model deployment efficiency. In particular, NetBeacon proposes a multi-phase sequential model architecture to perform dynamic packet analysis at different phases of a flow as it proceeds, by incorporating flow-level features that are computable at line-speed to boost learning accuracies. Further, NetBeacon designs efficient model representation mechanisms to address the table entry explosion problem when deploying tree-based models on the network data plane. Finally, NetBeacon hardens its scalability for handling concurrent flows via multiple tightly-coupled designs for managing stateful storage used to store per-flow state. We implement a prototype of NetBeacon and extensively evaluate its performance over multiple traffic analysis tasks.
AIFORE: Smart Fuzzing Based on Automatic Input Format Reverse Engineering
Ji Shi, {CAS-KLONAT, BKLONSPT}, Institute of Information Engineering, Chinese Academy of Sciences; Institute for Network Science and Cyberspace & BNRist, Tsinghua University; Zhongguancun Lab; Singular Security Lab, Huawei Technologies; School of Cyber Security, University of Chinese Academy of Sciences; Zhun Wang, Institute for Network Science and Cyberspace & BNRist, Tsinghua University; Zhongguancun Lab; Zhiyao Feng, Institute for Network Science and Cyberspace & BNRist, Tsinghua University; Zhongguancun Lab; EPFL; Yang Lan and Shisong Qin, Institute for Network Science and Cyberspace & BNRist, Tsinghua University; Zhongguancun Lab; Wei You, Renmin University of China; Wei Zou, {CAS-KLONAT, BKLONSPT}, Institute of Information Engineering, Chinese Academy of Sciences; School of Cyber Security, University of Chinese Academy of Sciences; Mathias Payer, EPFL; Chao Zhang, Institute for Network Science and Cyberspace & BNRist, Tsinghua University; Zhongguancun Lab
Knowledge of a program’s input format is essential for effective input generation in fuzzing. Automated input format reverse engineering represents an attractive but challenging approach to learning the format. In this paper, we address several challenges of automated input format reverse engineering, and present a smart fuzzing solution AIFORE which makes full use of the reversed format and benefits from it. The structures and semantics of input fields are determined by the basic blocks (BBs) that process them rather than the input specification. Therefore, we first utilize byte-level taint analysis to recognize the input bytes processed by each BB, then identify indivisible input fields that are always processed together with a minimum cluster algorithm, and learn their types with a neural network model that characterizes the behavior of BBs. Lastly, we design a new power scheduling algorithm based on the inferred format knowledge to guide smart fuzzing. We implement a prototype of AIFORE and evaluate both the accuracy of format inference and the performance of fuzzing against state-of-the-art (SOTA) format reversing solutions and fuzzers. AIFORE significantly outperforms SOTA baselines on the accuracy of field boundary and type recognition. With AIFORE, we uncovered 20 bugs in 15 programs that were missed by other fuzzers.
Inducing Authentication Failures to Bypass Credit Card PINs
David Basin, Patrick Schaller, and Jorge Toro-Pozo, ETH Zurich
For credit card transactions using the EMV standard, the integrity of transaction information is protected cryptographically by the credit card. Integrity checks by the payment terminal use RSA signatures and are part of EMV’s offline data authentication mechanism. Online integrity checks by the card issuer use a keyed MAC. One would expect that failures in either mechanism would always result in transaction failure, but this is not the case as offline authentication failures do not always result in declined transactions. Consequently, the integrity of transaction data that is not protected by the keyed MAC (online) cannot be guaranteed.
We show how this missing integrity protection can be exploited to bypass PIN verification for high-value Mastercard transactions. As a proof-of-concept, we have built an Android app that modifies unprotected card-sourced data, including the data relevant for cardholder verification. Using our app, we have tricked real-world terminals into downgrading from PIN verification to either no cardholder verification or (paper) signature verification, for transactions of up to 500 Swiss Francs. Our findings have been disclosed to the vendor with the recommendation to decline any transaction where offline data authentication fails.
Silent Spring: Prototype Pollution Leads to Remote Code Execution in Node.js
Mikhail Shcherbakov and Musard Balliu, KTH Royal Institute of Technology; Cristian-Alexandru Staicu, CISPA Helmholtz Center for Information Security
Prototype pollution is a dangerous vulnerability affecting prototype-based languages like JavaScript and the Node.js platform. It refers to the ability of an attacker to inject properties into an object's root prototype at runtime and subsequently trigger the execution of legitimate code gadgets that access these properties on the object's prototype, leading to attacks such as Denial of Service (DoS), privilege escalation, and Remote Code Execution (RCE). While there is anecdotal evidence that prototype pollution leads to RCE, current research does not tackle the challenge of gadget detection, thus only showing feasibility of DoS attacks, mainly against Node.js libraries.
In this paper, we set out to study the problem in a holistic way, from the detection of prototype pollution to detection of gadgets, with the ambitious goal of finding end-to-end exploits beyond DoS, in full-fledged Node.js applications. We build the first multi-staged framework that uses multi-label static taint analysis to identify prototype pollution in Node.js libraries and applications, as well as a hybrid approach to detect universal gadgets , notably, by analyzing the Node.js source code. We implement our framework on top of GitHub's static analysis framework CodeQL to find 11 universal gadgets in core Node.js APIs, leading to code execution. Furthermore, we use our methodology in a study of 15 popular Node.js applications to identify prototype pollutions and gadgets. We manually exploit eight RCE vulnerabilities in three high-profile applications such as NPM CLI, Parse Server, and Rocket.Chat. Our results provide alarming evidence that prototype pollution in combination with powerful universal gadgets lead to RCE in Node.js.
Reassembly is Hard: A Reflection on Challenges and Strategies
Hyungseok Kim, KAIST and The Affiliated Institute of ETRI; Soomin Kim and Junoh Lee, KAIST; Kangkook Jee, University of Texas at Dallas; Sang Kil Cha, KAIST
Reassembly, a branch of static binary rewriting, has become a focus of research today. However, despite its widespread use and research interest, there have been no systematic investigations on the techniques and challenges of reassemblers. In this paper, we formally define different types of errors that occur in current existing reassemblers, and present an automated tool named REASSESSOR to find such errors. We attempt to show through our tool and the large-scale benchmark we created the current challenges in the field and how they can be approached.
PCAT: Functionality and Data Stealing from Split Learning by Pseudo-Client Attack
Xinben Gao and Lan Zhang, University of Science and Technology of China
Split learning (SL) is a popular framework to protect a client's training data by splitting up a model among the client and the server. Previous efforts have shown that a semi-honest server can conduct a model inversion attack to recover the client's inputs and model parameters to some extent, as well as to infer the labels. However, those attacks require the knowledge of the client network structure and the performance deteriorates dramatically as the client network gets deeper (≥ 2 layers). In this work, we explore the attack on SL in a more general and challenging situation where the client model is a unknown to the server and gets more complex and deeper. Different from the conventional model inversion, we investigate the inherent privacy leakage through the server model in SL and reveal that clients' functionality and private data can be easily stolen by the server model, and a series of intermediate server models during SL can even cause more leakage. Based on the insights, we propose a new attack on SL: P seudo- C lient AT tack (PCAT). To the best of our knowledge, this is the first attack for a semi-honest server to steal clients' functionality, reconstruct private inputs and infer private labels without any knowledge about the clients' model. The only requirement for the server is a tiny dataset (about 0.1% - 5% of the private training set) for the same learning task. What's more, the attack is transparent to clients, so a server can obtain clients' privacy without taking any risk of being detected by the client. We implement PCAT on various benchmark datasets and models. Extensive experiments testify that our attack significantly outperforms the state-of-the-art attack in various conditions, including more complex models and learning tasks, even in non-i.i.d. conditions. Moreover, our functionality stealing attack is resilient to the existing defensive mechanism.
VulChecker: Graph-based Vulnerability Localization in Source Code
Yisroel Mirsky, Ben-Gurion University of the Negev; George Macon, Georgia Tech Research Institute; Michael Brown, Georgia Institute of Technology; Carter Yagemann, Ohio State University; Matthew Pruett, Evan Downing, Sukarno Mertoguno, and Wenke Lee, Georgia Institute of Technology
In software development, it is critical to detect vulnerabilities in a project as early as possible. Although, deep learning has shown promise in this task, current state-of-the-art methods cannot classify and identify the line on which the vulnerability occurs. Instead, the developer is tasked with searching for an arbitrary bug in an entire function or even larger region of code.
In this paper, we propose VulChecker: a tool that can precisely locate vulnerabilities in source code (down to the exact instruction) as well as classify their type (CWE). To accomplish this, we propose a new program representation, program slicing strategy, and the use of a message-passing graph neural network to utilize all of code's semantics and improve the reach between a vulnerability's root cause and manifestation points.
We also propose a novel data augmentation strategy for cheaply creating strong datasets for vulnerability detection in the wild, using free synthetic samples available online. With this training strategy, VulChecker was able to identify 24 CVEs (10 from 2019 & 2020) in 19 projects taken from the wild, with nearly zero false positives compared to a commercial tool that could only detect 4. VulChecker also discovered an exploitable zero-day vulnerability, which has been reported to developers for responsible disclosure.
Examining Consumer Reviews to Understand Security and Privacy Issues in the Market of Smart Home Devices
Swaathi Vetrivel, Veerle van Harten, Carlos H. Gañán, Michel van Eeten, and Simon Parkin, Delft University of Technology
Despite growing evidence that consumers care about secure Internet-of-Things (IoT) devices, relevant security and privacy-related information is unavailable at the point of purchase. While initiatives such as security labels create new avenues to signal a device's security and privacy posture, we analyse an existing avenue for such market signals - customer reviews. We investigate whether and to what extent customer reviews of IoT devices with well-known security and privacy issues reflect these concerns. We examine 83,686 reviews of four IoT device types commonly infected with Mirai across all Amazon websites in English. We perform topic modelling to group the reviews and conduct manual coding to understand (i) the prevalence of security and privacy issues and (ii) the themes that these issues articulate. Overall, around one in ten reviews (9.8%) mentions security and privacy issues; the geographical distribution varies across the six countries. We distil references to security and privacy into seven themes and identify two orthogonal themes: reviews written in technical language and those that mention friction with security steps. Our results thus highlight the value of the already existing avenue of customer reviews. We draw on these results to make recommendations and identify future research directions.
Timeless Timing Attacks and Preload Defenses in Tor's DNS Cache
Rasmus Dahlberg and Tobias Pulls, Karlstad University
This paper and abstract are under embargo and will be released on the first day of the symposium.
We show that Tor's DNS cache is vulnerable to a timeless timing attack, allowing anyone to determine if a domain is cached or not without any false positives. The attack requires sending a single TLS record. It can be repeated to determine when a domain is no longer cached to leak the insertion time. Our evaluation in the Tor network shows no instances of cached domains being reported as uncached and vice versa after 12M repetitions while only targeting our own domains. This shifts DNS in Tor from an unreliable side-channel—using traditional timing attacks with network jitter—to being perfectly reliable. We responsibly disclosed the attack and suggested two short-term mitigations.
As a long-term defense for the DNS cache in Tor against all types of (timeless) timing attacks, we propose a redesign where only an allowlist of domains is preloaded to always be cached across circuits. We compare the performance of a preloaded DNS cache to Tor's current solution towards DNS by measuring aggregated statistics for four months from two exits (after engaging with the Tor Research Safety Board and our university ethical review process). The evaluated preload lists are variants of the following top-lists: Alexa, Cisco Umbrella, and Tranco. Our results show that four-months-old preload lists can be tuned to offer comparable performance under similar resource usage or to significantly improve shared cache-hit ratios (2–3x) with a modest increase in memory usage and resolver load compared to a 100 Mbit/s exit. We conclude that Tor's current DNS cache is mostly a privacy harm because the majority of cached domains are unlikely to lead to cache hits but remain there to be probed by attackers.
Isolated and Exhausted: Attacking Operating Systems via Site Isolation in the Browser
Matthias Gierlings, Marcus Brinkmann, and Jörg Schwenk, Ruhr University Bochum
Site Isolation is a security architecture for browsers to protect against side-channel and renderer exploits by separating content from different sites at the operating system (OS) process level. By aligning web and OS security boundaries, Site Isolation promises to defend against these attack classes systematically in a streamlined architecture. However, Site Isolation is a large-scale architectural change that also makes OS resources more accessible to web attackers, and thus exposes web users to new risks at the OS level. In this paper, we present the first systematic study of OS resource exhaustion attacks based on Site Isolation, in the web attacker model, in three steps: (1) first-level resources directly accessible with Site Isolation; (2) second-level resources whose direct use is protected by the browser sandbox; (3) an advanced, real-world attack. For (1) we show how to create a fork bomb, highlighting conceptual gaps in the Site Isolation architecture. For (2) we show how to block all UDP sockets in an OS, using a variety of advanced browser features. For (3), we implement a fully working DNS Cache Poisoning attack based on Site Isolation, building on (2) and bypassing a major security feature of DNS. Our results show that the interplay between modern browser features and older OS features is increasingly problematic and needs further research.
Internet Service Providers' and Individuals' Attitudes, Barriers, and Incentives to Secure IoT
Nissy Sombatruang, National Institute of Information and Communications Technology; Tristan Caulfield and Ingolf Becker, University College London; Akira Fujita, Takahiro Kasama, Koji Nakao, and Daisuke Inoue, National Institute of Information and Communications Technology
Internet Service Providers (ISPs) and individual users of Internet of Things (IoT) play a vital role in securing IoT. However, encouraging them to do so is hard. Our study investigates ISPs' and individuals' attitudes towards the security of IoT, the obstacles they face, and their incentives to keep IoT secure, drawing evidence from Japan.
Due to the complex interactions of the stakeholders, we follow an iterative methodology where we present issues and potential solutions to our stakeholders in turn. For ISPs, we survey 27 ISPs in Japan, followed by a workshop with representatives from government and 5 ISPs. Based on the findings from this, we conduct semi-structured interviews with 20 participants followed by a more quantitative survey with 328 participants. We review these results in a second workshop with representatives from government and 7 ISPs. The appreciation of challenges by each party has lead to findings that are supported by all stakeholders.
Securing IoT devices is neither users' nor ISPs' priority. Individuals are keen on more interventions both from the government as part of regulation and from ISPs in terms of filtering malicious traffic. Participants are willing to pay for enhanced monitoring and filtering. While ISPs do want to help users, there appears to be a lack of effective technology to aid them. ISPs would like to see more public recognition for their efforts, but internally they struggle with executive buy-in and effective means to communicate with their customers. The majority of barriers and incentives are external to ISPs and individuals, demonstrating the complexity of keeping IoT secure and emphasizing the need for relevant stakeholders in the IoT ecosystem to work in tandem.

- Search by keyword
- Search by citation
Page 1 of 5
Phishing behavior detection on different blockchains via adversarial domain adaptation
Despite the growing attention on blockchain, phishing activities have surged, particularly on newly established chains. Acknowledging the challenge of limited intelligence in the early stages of new chains, we...
- View Full Text
Ensemble learning based anomaly detection for IoT cybersecurity via Bayesian hyperparameters sensitivity analysis
The Internet of Things (IoT) integrates more than billions of intelligent devices over the globe with the capability of communicating with other connected devices with little to no human intervention. IoT enab...
CommanderUAP: a practical and transferable universal adversarial attacks on speech recognition models
Most of the adversarial attacks against speech recognition systems focus on specific adversarial perturbations, which are generated by adversaries for each normal example to achieve the attack. Universal adver...
Enhancing fairness of trading environment: discovering overlapping spammer groups with dynamic co-review graph optimization
Within the thriving e-commerce landscape, some unscrupulous merchants hire spammer groups to post misleading reviews or ratings, aiming to manipulate public perception and disrupt fair market competition. This...
In-depth Correlation Power Analysis Attacks on a Hardware Implementation of CRYSTALS-Dilithium
During the standardisation process of post-quantum cryptography, NIST encourages research on side-channel analysis for candidate schemes. As the recommended lattice signature scheme, CRYSTALS-Dilithium, when i...
Atomic cross-chain swap based on private key exchange
Atomic Cross-Chain Swap (ACCS) is one important topic in cryptocurrency, where users can securely and trustlessly exchange assets between two different blockchains. However, most known ACCS schemes assume spec...
HSS: enhancing IoT malicious traffic classification leveraging hybrid sampling strategy
Using deep learning models to deal with the classification tasks in network traffic offers a new approach to address the imbalanced Internet of Things malicious traffic classification problems. However, the em...
Key derivable signature and its application in blockchain stealth address
Stealth address protocol (SAP) is widely used in blockchain to achieve anonymity. In this paper, we formalize a key derivable signature scheme (KDS) to capture the functionality and security requirements of SA...
Polar code-based secure transmission with higher message rate combining channel entropy and computational entropy
The existing physical layer security schemes, which are based on the key generation model and the wire-tap channel model, achieve security by utilizing channel reciprocity entropy and noise entropy, respective...
Dissecting zero trust: research landscape and its implementation in IoT
As a progressive security strategy, the zero trust model has attracted notable attention and importance within the realm of network security, especially in the context of the Internet of Things (IoT). This pap...
Study of smart grid cyber-security, examining architectures, communication networks, cyber-attacks, countermeasure techniques, and challenges
Smart Grid (SG) technology utilizes advanced network communication and monitoring technologies to manage and regulate electricity generation and transport. However, this increased reliance on technology and co...
A multi-agent adaptive deep learning framework for online intrusion detection
The network security analyzers use intrusion detection systems (IDSes) to distinguish malicious traffic from benign ones. The deep learning-based (DL-based) IDSes are proposed to auto-extract high-level featur...
Iterative and mixed-spaces image gradient inversion attack in federated learning
As a distributed learning paradigm, federated learning is supposed to protect data privacy without exchanging users’ local data. Even so, the gradient inversion attack , in which the adversary can reconstruct the ...
Winternitz stack protocols for embedded systems and IoT
This paper proposes and evaluates a new bipartite post-quantum digital signature protocol based on Winternitz chains and an oracle. Mutually mistrustful Alice and Bob are able to agree and sign a series of do...
Joint contrastive learning and belief rule base for named entity recognition in cybersecurity
Named Entity Recognition (NER) in cybersecurity is crucial for mining information during cybersecurity incidents. Current methods rely on pre-trained models for rich semantic text embeddings, but the challenge...
DTA: distribution transform-based attack for query-limited scenario
In generating adversarial examples, the conventional black-box attack methods rely on sufficient feedback from the to-be-attacked models by repeatedly querying until the attack is successful, which usually res...
A survey on lattice-based digital signature
Lattice-based digital signature has become one of the widely recognized post-quantum algorithms because of its simple algebraic operation, rich mathematical foundation and worst-case security, and also an impo...
Shorter ZK-SNARKs from square span programs over ideal lattices
Zero-knowledge succinct non-interactive arguments of knowledge (zk-SNARKs) are cryptographic protocols that offer efficient and privacy-preserving means of verifying NP language relations and have drawn consid...
Revocable and verifiable weighted attribute-based encryption with collaborative access for electronic health record in cloud
The encryption of user data is crucial when employing electronic health record services to guarantee the security of the data stored on cloud servers. Attribute-based encryption (ABE) scheme is considered a po...
Maxwell’s Demon in MLP-Mixer: towards transferable adversarial attacks
Models based on MLP-Mixer architecture are becoming popular, but they still suffer from adversarial examples. Although it has been shown that MLP-Mixer is more robust to adversarial attacks compared to convolu...
Practical solutions in fully homomorphic encryption: a survey analyzing existing acceleration methods
Fully homomorphic encryption (FHE) has experienced significant development and continuous breakthroughs in theory, enabling its widespread application in various fields, like outsourcing computation and secure...
A circuit area optimization of MK-3 S-box
In MILCOM 2015, Kelly et al. proposed the authentication encryption algorithm MK-3, which applied the 16-bit S-box. This paper aims to implement the 16-bit S-box with less circuit area. First, we classified th...
Intrusion detection system for controller area network
The rapid expansion of intra-vehicle networks has increased the number of threats to such networks. Most modern vehicles implement various physical and data-link layer technologies. Vehicles are becoming incre...
CT-GCN+: a high-performance cryptocurrency transaction graph convolutional model for phishing node classification
Due to the anonymous and contract transfer nature of blockchain cryptocurrencies, they are susceptible to fraudulent incidents such as phishing. This poses a threat to the property security of users and hinder...
Enhanced detection of obfuscated malware in memory dumps: a machine learning approach for advanced cybersecurity
In the realm of cybersecurity, the detection and analysis of obfuscated malware remain a critical challenge, especially in the context of memory dumps. This research paper presents a novel machine learning-bas...
BRITD: behavior rhythm insider threat detection with time awareness and user adaptation
Researchers usually detect insider threats by analyzing user behavior. The time information of user behavior is an important concern in internal threat detection.

F3l: an automated and secure function-level low-overhead labeled encrypted traffic dataset construction method for IM in Android
Fine-grained function-level encrypted traffic classification is an essential approach to maintaining network security. Machine learning and deep learning have become mainstream methods to analyze traffic, and ...
WAS: improved white-box cryptographic algorithm over AS iteration
The attacker in white-box model has full access to software implementation of a cryptographic algorithm and full control over its execution environment. In order to solve the issues of high storage cost and in...
Full-round impossible differential attack on shadow block cipher
Lightweight block ciphers are the essential encryption algorithm for devices with limited resources. Its goal is to ensure the security of data transmission through resource-constrained devices. Impossible dif...
Minimizing CNOT-count in quantum circuit of the extended Shor’s algorithm for ECDLP
The elliptic curve discrete logarithm problem (ECDLP) is a popular choice for cryptosystems due to its high level of security. However, with the advent of the extended Shor’s algorithm, there is concern that E...
Towards the transferable audio adversarial attack via ensemble methods
In recent years, deep learning (DL) models have achieved significant progress in many domains, such as autonomous driving, facial recognition, and speech recognition. However, the vulnerability of deep learnin...
LayerCFL: an efficient federated learning with layer-wised clustering
Federated Learning (FL) suffers from the Non-IID problem in practice, which poses a challenge for efficient and accurate model training. To address this challenge, prior research has introduced clustered FL (C...
A novel botnet attack detection for IoT networks based on communication graphs
Intrusion detection systems have been proposed for the detection of botnet attacks. Various types of centralized or distributed cloud-based machine learning and deep learning models have been suggested. Howeve...

Machine learning based fileless malware traffic classification using image visualization
In today’s interconnected world, network traffic is replete with adversarial attacks. As technology evolves, these attacks are also becoming increasingly sophisticated, making them even harder to detect. Fortu...
Research on privacy information retrieval model based on hybrid homomorphic encryption
The computational complexity of privacy information retrieval protocols is often linearly related to database size. When the database size is large, the efficiency of privacy information retrieval protocols is...
Performance evaluation of Cuckoo filters as an enhancement tool for password cracking
Cyberthreats continue their expansion, becoming more and more complex and varied. However, credentials and passwords are still a critical point in security. Password cracking can be a powerful tool to fight ag...
Tor network anonymity evaluation based on node anonymity
In order to address the shortcomings of traditional anonymity network anonymity evaluation methods, which only analyze from the perspective of the overall network and ignore the attributes of individual nodes,...
Verifiable delay functions and delay encryptions from hyperelliptic curves
Verifiable delay functions (VDFs) and delay encryptions (DEs) are two important primitives in decentralized systems, while existing constructions are mainly based on time-lock puzzles. A disparate framework ha...
MSLFuzzer: black-box fuzzing of SOHO router devices via message segment list inference
The popularity of small office and home office routers has brought convenience, but it also caused many security issues due to vulnerabilities. Black-box fuzzing through network protocols to discover vulnerabi...
A deep learning aided differential distinguisher improvement framework with more lightweight and universality
In CRYPTO 2019, Gohr opens up a new direction for cryptanalysis. He successfully applied deep learning to differential cryptanalysis against the NSA block cipher SPECK32/64, achieving higher accuracy than trad...
Attack based on data: a novel perspective to attack sensitive points directly
Adversarial attack for time-series classification model is widely explored and many attack methods are proposed. But there is not a method of attack based on the data itself. In this paper, we innovatively pro...
Improved lower bound for the complexity of unique shortest vector problem
Unique shortest vector problem (uSVP) plays an important role in lattice based cryptography. Many cryptographic schemes based their security on it. For the cofidence of those applications, it is essential to c...

Evolution of blockchain consensus algorithms: a review on the latest milestones of blockchain consensus algorithms
Blockchain technology has gained widespread adoption in recent years due to its ability to enable secure and transparent record-keeping and data transfer. A critical aspect of blockchain technology is the use ...
Graph neural network based approach to automatically assigning common weakness enumeration identifiers for vulnerabilities
Vulnerability reports are essential for improving software security since they record key information on vulnerabilities. In a report, CWE denotes the weakness of the vulnerability and thus helps quickly under...
EPASAD: ellipsoid decision boundary based Process-Aware Stealthy Attack Detector
Due to the importance of Critical Infrastructure (CI) in a nation’s economy, they have been lucrative targets for cyber attackers. These critical infrastructures are usually Cyber-Physical Systems such as powe...
Generic attacks on small-state stream cipher constructions in the multi-user setting
Small-state stream ciphers (SSCs), which violate the principle that the state size should exceed the key size by a factor of two, still demonstrate robust security properties while maintaining a lightweight de...
Evicting and filling attack for linking multiple network addresses of Bitcoin nodes
Bitcoin is a decentralized P2P cryptocurrency. It supports users to use pseudonyms instead of network addresses to send and receive transactions at the data layer, hiding users’ real network identities. Tradit...
Aparecium: understanding and detecting scam behaviors on Ethereum via biased random walk
Ethereum’s high attention, rich business, certain anonymity, and untraceability have attracted a group of attackers. Cybercrime on it has become increasingly rampant, among which scam behavior is convenient, c...
An efficient permutation approach for SbPN-based symmetric block ciphers
It is challenging to devise lightweight cryptographic primitives efficient in both hardware and software that can provide an optimum level of security to diverse Internet of Things applications running on low-...
IHVFL: a privacy-enhanced intention-hiding vertical federated learning framework for medical data
Vertical Federated Learning (VFL) has many applications in the field of smart healthcare with excellent performance. However, current VFL systems usually primarily focus on the privacy protection during model ...
- Editorial Board
- Sign up for article alerts and news from this journal
Affiliated with

The Institute of Information Engineering (IIE) is a national research institute in Beijing that specializes in comprehensive research on theories and applications related to information technology.
IIE strives to be a leading global academic institution by creating first-class research platforms and attracting top researchers. It also seeks to become an important national strategic power in the field of information technology.
IIE’s mission is to promote China’s innovation and industrial competitiveness by advancing information science, standards, and technology in ways that enhance economic security and public safety as well as improve our quality of life.
Read more..
The journal is indexed by
- EI Compendex
- Emerging Sources Citation Index
- EBSCO Discovery Service
- Institute of Scientific and Technical Information of China
- Google Scholar
- Norwegian Register for Scientific Journals and Series
- OCLC WorldCat Discovery Service
- ProQuest-ExLibris Primo
- ProQuest-ExLibris Summon
- TD Net Discovery Service
- UGC-CARE List (India)
Annual Journal Metrics
2022 Citation Impact 3.1 - 2-year Impact Factor 4.8 - 5-year Impact Factor 2.071 - SNIP (Source Normalized Impact per Paper) 1.266 - SJR (SCImago Journal Rank)
2023 Speed 8 days submission to first editorial decision for all manuscripts (Median) 95 days submission to accept (Median)
2023 Usage 408,523 downloads 15 Altmetric mentions
- ISSN: 2523-3246 (electronic)
IEEE Account
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.

Proceedings of International Conference on Network Security and Blockchain Technology
ICNSBT 2023
- Conference proceedings
- © 2024
- Jyotsna Kumar Mandal 0 ,
- Biswapati Jana 1 ,
- Tzu-Chuen Lu 2 ,
- Debashis De 3
Department of Computer Science and Engineering, Kalyani University, Kalyani, India
You can also search for this editor in PubMed Google Scholar
Department of Computer Science, Vidyasagar University, Midnapore, India
Department of information management, chaoyang university of technology, taichung, taiwan, department of computer science and engineering, maulana abul kalam azad university of technology, kolkata, india.
- Presents research works in the field of network security and blockchain technology
- Serves as a reference for researchers and practitioners in academia and industry
- Provides original works presented at ICNSBT 2023 held in Midnapore, India
Part of the book series: Lecture Notes in Networks and Systems (LNNS, volume 738)
Included in the following conference series:
- ICNSBT: International Conference on Network Security and Blockchain Technology
Conference proceedings info: ICNSBT 2023.
4684 Accesses
1 Citations
1 Altmetric
This is a preview of subscription content, log in via an institution to check access.
Access this book
- Available as EPUB and PDF
- Read on any device
- Instant download
- Own it forever
- Compact, lightweight edition
- Dispatched in 3 to 5 business days
- Free shipping worldwide - see info
Tax calculation will be finalised at checkout
Other ways to access
Licence this eBook for your library
Institutional subscriptions
Table of contents (44 papers)
Front matter, security and privacy, machine learning-based identification of ddos flood attack in ehealth cloud environment.
- Anindya Bose, Sandip Roy, Rajesh Bose
Machine Learning-Based Phishing E-mail Detection Using Persuasion Principle and NLP Techniques
- Chanchal Patra, Debasis Giri
Cryptanalysis and Improvement of a Mutual Authentication Scheme for Smart Grid Communications
- Piyush Sharma, Garima Thakur, Pankaj Kumar
Collision Avoidance and Drowsiness Detection System for Drivers
- Fatima Mohammad Amin
A New Algorithm for Encryption and Decryption Using AUM Block Sum Labeling
- A. Uma Maheswari, C. Ambika
Secured Reversible Data Hiding Scheme with NMI Interpolation and Arnold Transformation
- Manasi Jana, Biswapati Jana, Shubhankar Joardar, Sharmistha Jana, Tzu Chuen Lu
Face Mask Detection Exploiting CNN and MobileNetV2
- Nandana Ghosh, Biswapati Jana, Sharmistha Jana, Nguyen Kim Sao
Malicious Transaction URL Detection Using Logistic Regression
- Aratrik Bose, Anandaprova Majumder, Sumana Kundu
Secured Information Communication Exploiting Fuzzy Weight Strategy
- Alok Haldar, Biswapati Jana, Sharmistha Jana, Nguyen Kim Sao, Thanh Nhan Vo
Secure Data Communication Through Improved Multi-level Pixel Value Ordering Using Center-Folding Strategy
- Sudipta Meikap, Biswapati Jana, Prabhash Kumar Singh, Debkumar Bera, Tzu Chuen Lu
Perseverance of the Audio Data using RNN Implied Matrix Segmentation based Lossless Encoder
- Asish Debnath, Uttam Kr. Mondal
SVD-Based Watermarking Scheme for Medical Image Authentication
- Ashis Dey, Partha Chowdhuri, Pabitra Pal, Lu Tzu-Chuen
Watermark-Based Image Authentication with Coefficient Value Differencing and Histogram Shifting
- Bibek Ranjan Ghosh, Siddhartha Banerjee, Jyotsna Kumar Mandal, Arpan Baiagi, Rahul Deb Bhandari
IEMS3: An Image Encryption Scheme Using Modified SNOW 3G Algorithm
- Subrata Nandi, Satyabrata Roy, Srinivasan Krishnaswamy, Pinaki Mitra
Detection of Deepfakes in Financial Transactions Using Algorand Blockchain Consensus Mechanism
- S. Anitha, N. Anitha, N. Ashok, T. Daranya, B. Nandhini, V. Chandrasekaran
Effective Ransomware Detection Method Using PE Header and YARA Rules
- S. Hashwanth, S. Kirthica
Applied S P Integration Procedure for Enhanced Haphazardly Misplaced Values in Data Mining for Database Protection
- Darshanaben Dipakkumar Pandya, Abhijeetsinh Jadeja
DDoS Attack, a Threat to IoT Devices in the High-Speed Networks—An Overview
- Pravir Chitre, Srinivasan Sriramulu
Other volumes
- Virtual Private Networks
- Network Security
- Cyber Security
- Digital Watermarking
- ICNSBT 2023 Proceedings
- Social Networking
- Supply Chain Management
About this book
Editors and affiliations.
Jyotsna Kumar Mandal
Biswapati Jana
Tzu-Chuen Lu
Debashis De
About the editors
Bibliographic information.
Book Title : Proceedings of International Conference on Network Security and Blockchain Technology
Book Subtitle : ICNSBT 2023
Editors : Jyotsna Kumar Mandal, Biswapati Jana, Tzu-Chuen Lu, Debashis De
Series Title : Lecture Notes in Networks and Systems
DOI : https://doi.org/10.1007/978-981-99-4433-0
Publisher : Springer Singapore
eBook Packages : Engineering , Engineering (R0)
Copyright Information : The Editor(s) (if applicable) and The Author(s), under exclusive license to Springer Nature Singapore Pte Ltd. 2024
Softcover ISBN : 978-981-99-4432-3 Published: 29 November 2023
eBook ISBN : 978-981-99-4433-0 Published: 28 November 2023
Series ISSN : 2367-3370
Series E-ISSN : 2367-3389
Edition Number : 1
Number of Pages : XXVI, 537
Number of Illustrations : 63 b/w illustrations, 211 illustrations in colour
Topics : Communications Engineering, Networks , Mobile and Network Security , Cryptology , Professional Computing , Artificial Intelligence
- Publish with us
Policies and ethics
- Find a journal
- Track your research

105 Latest Cyber Security Research Topics in 2024
Home Blog Security 105 Latest Cyber Security Research Topics in 2024
The concept of cybersecurity refers to cracking the security mechanisms that break in dynamic environments. Implementing Cyber Security Project topics and cybersecurity thesis topics helps overcome attacks and take mitigation approaches to security risks and threats in real-time. Undoubtedly, it focuses on events injected into the system, data, and the whole network to attack/disturb it.
The network can be attacked in various ways, including Distributed DoS, Knowledge Disruptions, Computer Viruses / Worms, and many more. Cyber-attacks are still rising, and more are waiting to harm their targeted systems and networks. Detecting Intrusions in cybersecurity has become challenging due to their Intelligence Performance. Therefore, it may negatively affect data integrity, privacy, availability, and security.
This article aims to demonstrate the most current Cyber Security Research Topics for Projects and areas of research currently lacking. We will talk about cyber security research questions, cyber security topics for the project, latest research titles about cyber security.
List of Trending Cyber Security Research Topics in 2024
Digital technology has revolutionized how all businesses, large or small, work, and even governments manage their day-to-day activities, requiring organizations, corporations, and government agencies to utilize computerized systems. To protect data against online attacks or unauthorized access, cybersecurity is a priority. There are many Cyber Security Courses online where you can learn about these topics. With the rapid development of technology comes an equally rapid shift in Cyber Security Research Topics and cybersecurity trends, as data breaches, ransomware, and hacks become almost routine news items. In 2024, these will be the top cybersecurity trends .
A. Exciting Mobile Cyber Security Research Paper Topics
- The significance of continuous user authentication on mobile gadgets.
- The efficacy of different mobile security approaches.
- Detecting mobile phone hacking.
- Assessing the threat of using portable devices to access banking services.
- Cybersecurity and mobile applications.
- The vulnerabilities in wireless mobile data exchange.
- The rise of mobile malware.
- The evolution of Android malware.
- How to know you’ve been hacked on mobile.
- The impact of mobile gadgets on cybersecurity.
B. Top Computer and Software Security Topics to Research
- Learn algorithms for data encryption
- Concept of risk management security
- How to develop the best Internet security software
- What are Encrypting Viruses- How does it work?
- How does a Ransomware attack work?
- Scanning of malware on your PC
- Infiltrating a Mac OS X operating system
- What are the effects of RSA on network security ?
- How do encrypting viruses work?
- DDoS attacks on IoT devices
C. Trending Information Security Research Topics
- Why should people avoid sharing their details on Facebook?
- What is the importance of unified user profiles?
- Discuss Cookies and Privacy
- White hat and black hat hackers
- What are the most secure methods for ensuring data integrity?
- Talk about the implications of Wi-Fi hacking apps on mobile phones
- Analyze the data breaches in 2024
- Discuss digital piracy in 2024
- critical cyber-attack concepts
- Social engineering and its importance
D. Current Network Security Research Topics
- Data storage centralization
- Identify Malicious activity on a computer system.
- Firewall
- Importance of keeping updated Software
- wireless sensor network
- What are the effects of ad-hoc networks
- How can a company network be safe?
- What are Network segmentation and its applications?
- Discuss Data Loss Prevention systems
- Discuss various methods for establishing secure algorithms in a network.
- Talk about two-factor authentication
E. Best Data Security Research Topics
- Importance of backup and recovery
- Benefits of logging for applications
- Understand physical data security
- Importance of Cloud Security
- In computing, the relationship between privacy and data security
- Talk about data leaks in mobile apps
- Discuss the effects of a black hole on a network system.
F. Important Application Security Research Topics
- Detect Malicious Activity on Google Play Apps
- Dangers of XSS attacks on apps
- Discuss SQL injection attacks.
- Insecure Deserialization Effect
- Check Security protocols
G. Cybersecurity Law & Ethics Research Topics
- Strict cybersecurity laws in China
- Importance of the Cybersecurity Information Sharing Act.
- USA, UK, and other countries' cybersecurity laws
- Discuss The Pipeline Security Act in the United States
H. Recent Cyberbullying Topics
- Protecting your Online Identity and Reputation
- Online Safety
- Sexual Harassment and Sexual Bullying
- Dealing with Bullying
- Stress Center for Teens
I. Operational Security Topics
- Identify sensitive data
- Identify possible threats
- Analyze security threats and vulnerabilities
- Appraise the threat level and vulnerability risk
- Devise a plan to mitigate the threats
J. Cybercrime Topics for a Research Paper
- Crime Prevention.
- Criminal Specialization.
- Drug Courts.
- Criminal Courts.
- Criminal Justice Ethics.
- Capital Punishment.
- Community Corrections.
- Criminal Law.
Cyber Security Future Research Topics
- Developing more effective methods for detecting and responding to cyber attacks
- Investigating the role of social media in cyber security
- Examining the impact of cloud computing on cyber security
- Investigating the security implications of the Internet of Things
- Studying the effectiveness of current cyber security measures
- Identifying new cyber security threats and vulnerabilities
- Developing more effective cyber security policies
- Examining the ethical implications of cyber security
Cyber Security Topics For Research Paper
- Cyber security threats and vulnerabilities
- Cyber security incident response and management
- Cyber security risk management
- Cyber security awareness and training
- Cyber security controls and countermeasures
- Cyber security governance
- Cyber security standards
- Cyber security insurance
Top 5 Current Research Topics in Cybersecurity
Below are the latest 5 cybersecurity research topics. They are:
- Artificial Intelligence
- Digital Supply Chains
- Internet of Things
- State-Sponsored Attacks
- Working From Home
Research Area in Cyber Security
The field of cyber security is extensive and constantly evolving. Its research covers a wide range of subjects, including:
- Quantum & Space
- Data Privacy
- Criminology & Law
- AI & IoT Security
- RFID Security
- Authorization Infrastructure
- Digital Forensics
- Autonomous Security
- Social Influence on Social Networks
How to Choose the Best Research Topics in Cyber Security?
A good cybersecurity assignment heading is a skill that not everyone has, and unfortunately, not everyone has one. You might have your teacher provide you with the topics, or you might be asked to come up with your own. If you want more cyber security research topics, you can take references from Certified Ethical Hacker Certification, where you will get more hints on new topics. If you don't know where to start, here are some tips. Follow them to create compelling cybersecurity assignment topics.
1. Brainstorm
In order to select the most appropriate heading for your cybersecurity assignment, you first need to brainstorm ideas. What specific matter do you wish to explore? In this case, come up with relevant topics about the subject and select those relevant to your issue when you use our list of topics. You can also go to cyber security-oriented websites to get some ideas. Using any blog post on the internet can prove helpful if you intend to write a research paper on security threats in 2024. Creating a brainstorming list with all the keywords and cybersecurity concepts you wish to discuss is another great way to start. Once that's done, pick the topics you feel most comfortable handling. Keep in mind to stay away from common topics as much as possible.
2. Understanding the Background
In order to write a cybersecurity assignment, you need to identify two or three research paper topics. Obtain the necessary resources and review them to gain background information on your heading. This will also allow you to learn new terminologies that can be used in your title to enhance it.
3. Write a Single Topic
Make sure the subject of your cybersecurity research paper doesn't fall into either extreme. Make sure the title is neither too narrow nor too broad. Topics on either extreme will be challenging to research and write about.
4. Be Flexible
There is no rule to say that the title you choose is permanent. It is perfectly okay to change your research paper topic along the way. For example, if you find another topic on this list to better suit your research paper, consider swapping it out.
The Layout of Cybersecurity Research Guidance
It is undeniable that usability is one of cybersecurity's most important social issues today. Increasingly, security features have become standard components of our digital environment, which pervade our lives and require both novices and experts to use them. Supported by confidentiality, integrity, and availability concerns, security features have become essential components of our digital environment.
In order to make security features easily accessible to a wider population, these functions need to be highly usable. This is especially true in this context because poor usability typically translates into the inadequate application of cybersecurity tools and functionality, resulting in their limited effectiveness.
Cyber Security Research Topic Writing Tips from Expert
Additionally, a well-planned action plan and a set of useful tools are essential for delving into Cyber Security research topics. Not only do these topics present a vast realm of knowledge and potential innovation, but they also have paramount importance in today's digital age. Addressing the challenges and nuances of these research areas will contribute significantly to the global cybersecurity landscape, ensuring safer digital environments for all. It's crucial to approach these topics with diligence and an open mind to uncover groundbreaking insights.
- Before you begin writing your research paper, make sure you understand the assignment.
- Your Research Paper Should Have an Engaging Topic
- Find reputable sources by doing a little research
- Precisely state your thesis on cybersecurity
- A rough outline should be developed
- Finish your paper by writing a draft
- Make sure that your bibliography is formatted correctly and cites your sources.
Discover the Power of ITIL 4 Foundation - Unleash the Potential of Your Business with this Cost-Effective Solution. Boost Efficiency, Streamline Processes, and Stay Ahead of the Competition. Learn More!
Studies in the literature have identified and recommended guidelines and recommendations for addressing security usability problems to provide highly usable security. The purpose of such papers is to consolidate existing design guidelines and define an initial core list that can be used for future reference in the field of Cyber Security Research Topics.
The researcher takes advantage of the opportunity to provide an up-to-date analysis of cybersecurity usability issues and evaluation techniques applied so far. As a result of this research paper, researchers and practitioners interested in cybersecurity systems who value human and social design elements are likely to find it useful. You can find KnowledgeHut’s Cyber Security courses online and take maximum advantage of them.
Frequently Asked Questions (FAQs)
Businesses and individuals are changing how they handle cybersecurity as technology changes rapidly - from cloud-based services to new IoT devices.
Ideally, you should have read many papers and know their structure, what information they contain, and so on if you want to write something of interest to others.
Inmates having the right to work, transportation of concealed weapons, rape and violence in prison, verdicts on plea agreements, rehab versus reform, and how reliable are eyewitnesses?
The field of cyber security is extensive and constantly evolving. Its research covers various subjects, including Quantum & Space, Data Privacy, Criminology & Law, and AI & IoT Security.

Mrinal Prakash
I am a B.Tech Student who blogs about various topics on cyber security and is specialized in web application security
Avail your free 1:1 mentorship session.
Something went wrong
Upcoming Cyber Security Batches & Dates
| Name | Date | Fee | Know more |
|---|

An official website of the United States government
Here’s how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock A locked padlock ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
Free Cyber Services #protect2024 Secure Our World Shields Up Report A Cyber Issue
Modern Approaches to Network Access Security
CISA, in collaboration with the following organizations, co-authored this joint guidance:
- Federal Bureau of Investigation (FBI)
- New Zealand’s Government Communications Security Bureau (GCSB);
- New Zealand’s Computer Emergency Response Team (CERT-NZ); and
- The Canadian Centre for Cyber Security (CCCS).
The guidance urges business owners of all sizes to move toward more robust security solutions—such as Zero Trust, Secure Service Edge (SSE), and Secure Access Service Edge (SASE)—that provide greater visibility of network activity. Additionally, this guidance helps organizations to better understand the vulnerabilities, threats, and practices associated with traditional remote access and VPN deployment, as well as the inherent business risk posed to an organization’s network by remote access misconfiguration.
Resource Materials
Related resources, barriers to single sign-on (sso) adoption for small and medium-sized businesses: identifying challenges and opportunities, encrypted dns implementation guidance, secure by design alert: eliminating directory traversal vulnerabilities in software, secure by design alert: eliminating sql injection vulnerabilities in software.

IMAGES
VIDEO
COMMENTS
Volume 97, September 2023, 101804. ... The article is a full research paper (i.e., not a presentation or supplement to a poster). ... Customized optimal allocation and network security configuration: Planning: Bringhenti et al. [22] Automated configuration assessment: Reasoning:
This paper discusses network security for secure data communication. Discover the world's research. ... March 2023 · Journal for Research in Applied Sciences and Biotechnology. Maroof Khan;
The framework of forecasting cyber threats. The architecture of our framework for forecasting cyber threats is illustrated in Fig. 1. As seen in the Data Sources component (l.h.s), to harness all ...
Network security situational awareness is based on the extraction and analysis of big data, and by understanding these data to evaluate the current network security status and predict future development trends, provide feedback to decision-makers to make corresponding countermeasures, and achieve security protection for the network environment. This article focuses on artificial intelligence ...
This paper provides a comprehensive survey of the state-of-the-art use of Artificial Intelligence (AI) and Machine Learning (ML) in the field of cybersecurity. The paper illuminates key applications of AI and ML in cybersecurity, while also addressing existing challenges and posing unresolved questions for future research.
Network Security Monitoring (NSM) is a popular term to refer to the detection of security incidents by monitoring the network events. An NSM system is central for the security of current networks, given the escalation in sophistication of cyberwarfare. In this paper, we review the state-of-the-art in NSM, and derive a new taxonomy of the functionalities and modules in an NSM system. This ...
This survey paper provides a comprehensive overview of recent research and development in network security that uses graphs and graph-based data representation and analytics. The paper focuses on the graph-based representation of network traffic records and the application of graph-based analytics in intrusion detection and botnet detection. The paper aims to answer several questions related ...
- 56% of security leaders now meet monthly or more often with their board. This is rapidly narrowing the cybersecurity perception gap. However, more needs to be done to promote understanding between business and security teams to support effective action by organizational leaders. - Building a security-focused culture requires
Feature papers represent the most advanced research with significant potential for high impact in the field. A Feature Paper should be a substantial original Article that involves several techniques or approaches, provides an outlook for future research directions and describes possible research applications. ... Network 2023, 3(3), 298-325 ...
Profile Information. Communications Preferences. Profession and Education. Technical Interests. Need Help? US & Canada:+1 800 678 4333. Worldwide: +1 732 981 0060. Contact & Support. About IEEE Xplore.
NDSS 2023 has a full agenda featuring 2 keynotes, 94 accepted papers, 40 posters, and a 30th anniversary retrospective from Tuesday, 28 February to Thursday, 2 March 2023. In addition, there will be eight co-located events on the Monday before, and the Friday after, the main symposium focusing on specific areas of network security research.
With the ever-growing concern for internet security, the field of quantum cryptography emerges as a promising solution for enhancing the security of networking systems. In this paper, 20 notable papers from leading conferences and journals are reviewed and categorized based on their focus on various aspects of quantum cryptography, including key distribution, quantum bit commitment, post ...
Submission deadline: 12 June 2023 18 June 2023 (AoE) Submit a paper. The IEEE Conference on Communications and Network Security (CNS) is a premier forum for cybersecurity researchers, engineers, practitioners, and policy makers to exchange ideas, techniques and tools related to all practical and theoretical aspects of communications and network ...
The review also examines network threats and data web security procedures. The report proposes new research directions to advance research. This paper discusses network security for secure data communication. Keywords— Remote access, security measures, network hazards, Research Directions. 1. INTRODUCTION. The rapid incorporation of computer ...
The 32nd USENIX Security Symposium will be held August 9-11, 2023, in Anaheim, CA. Important: In 2023, we are introducing substantial changes to the review process, aimed to provide a more consistent path towards acceptance and reduce the number of times papers reenter the reviewing process. Detailed information is available at USENIX ...
The emergence of the Internet of Things (IoT) technology has brought about tremendous possibilities, but at the same time, it has opened up new vulnerabilities and attack vectors that could compromise the confidentiality, integrity, and availability of connected systems. Developing a secure IoT ecosystem is a daunting challenge that requires a systematic and holistic approach to identify and ...
Hide details . USENIX Security '23 has three submission deadlines. Prepublication versions of the accepted papers from the summer submission deadline are available below. Improving Logging to Reduce Permission Over-Granting Mistakes. Bingyu Shen, Tianyi Shan, and Yuanyuan Zhou, University of California, San Diego.
Network Security: Network security protects the computer network from disruptors, which can be malware or hacking. Network security is a set of solutions that enable organizations to keep computer networks out of the reach of hackers, organized attackers, and malware (Zhang, 2021). Download : Download high-res image (282KB)
The network security analyzers use intrusion detection systems (IDSes) to distinguish malicious traffic from benign ones. ... This research paper presents a novel machine learning-bas... Authors: Md. Alamgir Hossain and Md. Saiful Islam. Citation: Cybersecurity ... 2023 Usage 408,523 downloads 15 Altmetric mentions . ISSN: 2523-3246 (electronic)
With the development of information and network technology, all kinds of network attacks have also brought more and more serious threats to network security, and network security problems have become increasingly serious and concerned by everyone. However, the traditional security protection technology cannot fully adapt to the current network security situation, network security situation ...
The book is a collection of best selected research papers presented at International Conference on Network Security and Blockchain Technology (ICNSBT 2023), held at Vidyasagar University, Midnapore, India, during March 24-26, 2023. The book discusses recent developments and contemporary research in cryptography, network security ...
The Future of Network Security Technology: A SANS Survey. This survey looks at how organizations are updating and adapting their network security strategies and design models to fit into cloud infrastructure. By. Matt Bromiley. February 22, 2024. Login to download. All papers are copyrighted.
These trends support the need for balance between people, process and technology, in order to successfully reduce cybersecurity risk.. Human-centric security design prioritizes the role of employee experience — rather than technical considerations alone — across the controls management life cycle. Drawing upon the behavioral sciences, user-experience (UX) and related disciplines, it helps ...
In 2024, these will be the top cybersecurity trends. A. Exciting Mobile Cyber Security Research Paper Topics. The significance of continuous user authentication on mobile gadgets. The efficacy of different mobile security approaches. Detecting mobile phone hacking.
The Canadian Centre for Cyber Security (CCCS). The guidance urges business owners of all sizes to move toward more robust security solutions—such as Zero Trust, Secure Service Edge (SSE), and Secure Access Service Edge (SASE)—that provide greater visibility of network activity.
above, the defaults for Network Security Configuration block all cleartext (unencrypted HTTP) traffic. Developers must explicitly opt-in to specific domains to use cleartext traffic in their applications. Android Studio also warns developers when their app includes a potentially insecure Network Security Configuration.