Navigation Menu
Search code, repositories, users, issues, pull requests..., provide feedback.
We read every piece of feedback, and take your input very seriously.

Saved searches
Use saved searches to filter your results more quickly.
To see all available qualifiers, see our documentation .
- Notifications
Model of virtual power plant as a part of Msc thesis
wiola94/VirtualPowerPlant
Folders and files, repository files navigation, virtualpowerplant.
Model of a virtual power plant as a part of MSc thesis
The repository is a part of the thesis about the system for Negawatt Virtual Power Plant, which heads up groups of heat pumps. Virtual Power Plant is a concept of connected power plants and regular users of electric power. The main aim of such a system is to take control over dependent installations in order to maintain good collaborations with power system and to make a profit. The program compares two types of heat pump operation. The first one (later called ‘Simple Mode’) did not take into consideration managing with the Virtual Power Plant concept and was a base version to economically compare it to the enhanced one. The second type of simulation ( later called ‘VPPMode’), was to manage dependent cells by a Virtual Power Plant way of thinking.
Title of the thesis: "Project of negawatt virtual power plant based on the work of heat pumps"
Link to the thesis: https://repo.pw.edu.pl/info/master/WUT56b33692a18a4f65aa5cae9fec04b136/
Warsaw University of Technology, Poland, 2018
- Python 100.0%
- Bibliography
- More Referencing guides Blog Automated transliteration Relevant bibliographies by topics
- Automated transliteration
- Relevant bibliographies by topics
- Referencing guides
Virtual Power Plants and Integrated Energy System: Current Status and Future Prospects
- Living reference work entry
- First Online: 26 February 2022
- Cite this living reference work entry

- Sambeet Mishra 4 , 5 ,
- Chiara Bordin 6 ,
- Madis Leinakse 7 ,
- Fushuan Wen 7 ,
- Robert J Howlett 8 &
- Ivo Palu 7
229 Accesses
The power system is undergoing a digitalization, decarbonization, and decentralization. Economic incentives along with resiliency and reliability concerns are partly driving the transition. In the process of decentralization, local energy markets are forming at various places. A virtual power plant (VPP) is a by-product of this digitalization capitalizing on the opportunity to further promote renewable resources, demand-side flexibility, and sector coupling. A VPP enables resilient operation of power system while assembling small- to large-scale generation units and demand-side flexibility. Specifically, during the pandemic uncertainty, virtual work meets virtual power plants. A VPP has two both cyber and physical components. On one side, the physical component presents the operational challenges in terms of security, stability, reliability, and efficiency. On the other side, the cyber component introduces the challenges on communication, computation, security, and privacy. A VPP synthesizes synergies between the cyber and physical components, thereby harnessing the potential in terms of enhancing energy efficiency and reducing the cost. The objective of this chapter is to introduce the virtual power plant and integrated energy system with associated concepts, terminology, and relation thereof. The secondary objective is to categorize the key concepts while highlighting subsequent issues in planning, operations, and control of a VPP with an integrated energy system. Moreover, this chapter knits together the concepts and challenges in realizing virtual power plants with integrated energy systems.
This is a preview of subscription content, log in via an institution to check access.
Access this chapter
Institutional subscriptions
A4 large scale storage options under special consideration of 6 × 15 mw battery example, http://www.eqmagpro.com/wp-content/uploads/2017/06/VGB-Congress_Benesch.pdf . Accessed on 21 Oct 2020
K. Aduda, T. Labeodan, W. Zeiler, G. Boxem, Demand side flexibility coordination in office buildings: a framework and case study application. Sustain. Cities Soc. 29 , 139–158 (2017)
Google Scholar
A. Ajanovic, A. Hiesl, R. Haas, On the role of storage for electricity in smart energy systems. Energy 200 117473 (2020)
A. Alahyari, M. Ehsan, M. Moghimi, Managing distributed energy resources (DERs) through virtual power plant technology (VPP): a stochastic information-gap decision theory (IGDT) approach. Iranian J. Sci. Technol. Trans. Electric. Eng. 44 (1), 279–291 (2020). https://doi.org/10.1007/s40998-019-00248-w
A. Aldegheishem, R. Bukhsh, N. Alrajeh, N. Javaid, FaaVPP: fog as a virtual power plant service for community energy management. Futur. Gener. Comput. Syst. 105 , 675–683 (2020)
A.A. Alkahtani, S.T. Alfalahi, A.A. Athamneh, A.Q. Al-Shetwi, M.B. Mansor, M. Hannan, V.G. Agelidis, Power quality in microgrids including supraharmonics: issues, standards, and mitigations. IEEE Access 8 , 127104–127122 (2020)
A.Q. Al-Shetwi, M.Z. Sujod, Modeling and control of grid-connected photovoltaic power plant with fault ride-through capability. J. Solar Energy Eng. 140 (2), 1–8 (2018)
A.Q. Al-Shetwi, M. Hannan, K.P. Jern, A.A. Alkahtani, A. PG Abas, Power quality assessment of grid-connected pv system in compliance with the recent integration requirements. Electronics 9 (2), 366 (2020)
M.A. Ancona, M. Bianchi, L. Branchini, A. De Pascale, F. Melino, A. Peretto, Low temperature district heating networks for complete energy needs fulfillment. Int. J. Sustain. Energy Plan. Manag. 24 , 33–42 (2019)
K.E. Antoniadou-Plytaria, I.N. Kouveliotis-Lysikatos, P.S. Georgilakis, n.d. Hatziargyriou, Distributed and decentralized voltage control of smart distribution networks: models, methods, and future research. IEEE Trans. Smart Grid 8 (6), 2999–3008 (2017)
S.G. Argade, V. Aravinthan, I.E. Büyüktahtakın, S. Joseph, Performance and consumer satisfaction-based bi-level tariff scheme for EV charging as a VPP. IET Gener. Transm. Distrib. 13 (11), 2112–2122 (2018)
P. Asmus, Microgrids, virtual power plants and our distributed energy future. Electric. J. 23 (10), 72–82 (2010)
S. Babaei, C. Zhao, L. Fan, A data-driven model of virtual power plants in day-ahead unit commitment. IEEE Trans. Power Syst. 34 (6), 5125–5135 (2019)
L. Bai, F. Li, H. Cui, T. Jiang, H. Sun, J. Zhu, Interval optimization based operating strategy for gas-electricity integrated energy systems considering demand response and wind uncertainty. Appl. Energy 167 , 270–279 (2016). https://doi.org/10.1016/j.apenergy.2015.10.119
R. Boampong, D.P. Brown, On the benefits of behind-the-meter rooftop solar and energy storage: the importance of retail rate design. Energy Econ. 86 , 104682 (2020)
C. Bordin, A. Gordini, D. Vigo, An optimization approach for district heating strategic network design. Eur. J. Oper. Res. 252 (1), 296–307 (2016)
C. Bordin, A. Håkansson, S. Mishra, Smart energy and power systems modelling: an IOT and cyber-physical systems perspective, in the context of energy informatics. Proc. Comput. Sci. 176 , 2254–2263 (2020)
T. Brown, D. Schlachtberger, A. Kies, S. Schramm, M. Greiner, Synergies of sector coupling and transmission reinforcement in a cost-optimised, highly renewable European energy system. Energy 160 , 720–739 (2018). arXiv:1801.05290, https://doi.org/10.1016/j.energy.2018.06.222
Building a battery power plant wemag – aggreko, https://www.aggreko.com/en-pg/case-studies/utilities/building-a-battery-power-plant-wemag#challenge . Accessed on 21 Oct 2020
Centrica’s restore business launches 32 mw ‘virtual power plant’ in Belgium – centrica plc, https://www.centrica.com/news/centricas-restore-business-launches-32-mw-virtual-power-plant-belgium . Accessed on 21 Oct 2020
P. Chaudhari, P. Rane, A. Bawankar, P. Shete, K. Kalange, A. Moghe, J. Panda, A. Kadrolkar, K. Gaikwad, N. Bhor et al., Design and implementation of statcom for reactive power compensation and voltage fluctuation mitigation in microgrid, in 2015 IEEE International Conference on Signal Processing, Informatics, Communication and Energy Systems (SPICES) (IEEE, 2015), pp. 1–5
S.T. Chavhan, C. Bhattar, P.V. Koli, V.S. Rathod, Application of statcom for power quality improvement of grid integrated wind mill, in 2015 IEEE 9th International Conference on Intelligent Systems and Control (ISCO) (IEEE, 2015), pp. 1–7
C.-I. Chen, Y.-C. Chen, C.-N. Chen, A high-resolution technique for flicker measurement in power quality monitoring, in 2013 IEEE 8th Conference on Industrial Electronics and Applications (ICIEA) (IEEE, 2013), pp. 528–533
K.J. Chua, S.K. Chou, W. Yang, Advances in heat pump systems: a review. Appl. Energy 87 (12), 3611–3624 (2010)
e2m announces strategic partnership with swytch to collaborate on proof of concept pilot – with e2m, https://www.e2m.energy/en/news-entry/Strategic-Partnership-with-Swytch.html . Accessed on 21 Oct 2020
Edf offers 866 mw at VPP auction, no additional power tenders on horizon – icis, https://www.icis.com/explore/resources/news/2007/11/29/9300807/edf-offers-866-mw-at-vpp-auction-no-additional-power-tenders-on-horizon/ . Accessed on 21 Oct 2020
N. Edomah, Effects of voltage sags, swell and other disturbances on electrical equipment and their economic implications, in IEEE Proceedings of 20th International Conference on Electricity Distribution (IET, 2009), pp. 1–4
K. El Bakari, W.L. Kling, Virtual power plants: an answer to increasing distributed generation, in IEEE PES Innovative Smart Grid Technologies Conference Europe, ISGT Europe (2010). https://doi.org/10.1109/ISGTEUROPE.2010.5638984
M. Emarati, F. Keynia, M. Rashidinejad, A two-stage stochastic programming framework for risk-based day-ahead operation of a virtual power plant. Int. Trans. Electric. Energy Syst. 30 (3) (2020). https://doi.org/10.1002/2050-7038.12255
Enel increases ‘virtual power plant’ to 157 mw – Vermont business magazine, https://vermontbiz.com/news/2018/march/01/enel-increases-virtual-power-plant-157mw . Accessed on 21 Oct 2020
Engie, kiwi power partner on virtual power plants in US – s&p global market intelligence, https://www.spglobal.com/marketintelligence/en/news-insights/latest-news-headlines/engie-kiwi-power-partner-on-virtual-power-plants-in-us-59480758 . Accessed on 21 Oct 2020
E.on and thyssenkrupp bring hydrogen to the electric market – energy live news, https://www.en ergylivenews.com/2020/06/30/e-on-and-thyssenkrupp-bring-hydrogen-to-the-electric-market/ . Accessed on 21 Oct 2020
Evegen virtual power plant, https://www.evergen.com.au/ . Accessed on 21 Oct 2020
First 5 mw virtual power plant from major utility origin gets funding in victoria, Australia, https://www.energy-storage.news . Accessed on 21 Oct 2020
J. Freeman, I. Guarracino, S.A. Kalogirou, C.N. Markides, A small-scale solar organic Rankine cycle combined heat and power system with integrated thermal energy storage. Appl. Thermal Eng. 127 , 1543–1554 (2017)
G. Fridgen, R. Keller, M.-F. Körner, M. Schöpf, A holistic view on sector coupling. Energy Policy 147 , 111913 (2020)
I. Gerami Moghaddam, Scheduling a smart energy hub-based virtual power plant using benders decomposition to considering power system constraints. Int. Trans. Electric. Energy Syst. 28 (10), e2608 (2018)
A. Ghosh, G. Ledwich, A unified power quality conditioner (UPQC) for simultaneous voltage and current compensation. Electric Power Syst. Res. 59 (1), 55–63 (2001)
C. Goebel, H.-A. Jacobsen, V. del Razo, C. Doblander, J. Rivera, J. Ilg, C. Flath, H. Schmeck, C. Weinhardt, D. Pathmaperuma et al., Energy Inf. Bus. Inf. Syst. Eng. 6 (1), 25–31 (2014)
D. Graovac, V. Katic, A. Rufer, Power quality problems compensation with universal power quality conditioning system. IEEE Trans. Power Delivery 22 (2), 968–976 (2007)
A. Hariri, M.O. Faruque, Impacts of distributed generation on power quality, in 2014 North American Power Symposium (NAPS) (IEEE, 2014), pp. 1–6
A. Hariri, M.O. Faruque, R. Soman, R. Meeker, Impacts and interactions of voltage regulators on distribution networks with high pv penetration, in 2015 North American Power Symposium (NAPS) (IEEE, 2015), pp. 1–6
A. Hauer, Storage technology issues and opportunities, international low-carbon energy technology platform, in, Proceedings of the Strategic and Cross-Cutting Workshop “Energy Storage—Issues and Opportunities” , Paris, vol. 15 (2011)
R. Hemmati, H. Saboori, S. Saboori, Stochastic risk-averse coordinated scheduling of grid integrated energy storage units in transmission constrained wind-thermal systems within a conditional value-at-risk framework. Energy 113 , 762–775 (2016). https://doi.org/10.1016/ j.energy.2016.07.089
A. Honrubia-Escribano, T. García-Sánchez, E. Gómez-Lázaro, E. Muljadi, A. Molina-Garcia, Power quality surveys of photovoltaic power plants: characterisation and analysis of grid-code requirements. IET Renew. Power Gener. 9 (5), 466–473 (2015)
E. Hossain, M.R. Tür, S. Padmanaban, S. Ay, I. Khan, Analysis and mitigation of power quality issues in distributed generation systems using custom power devices. IEEE Access 6 , 16816–16833 (2018)
K. Ilango, A. Bhargav, A. Trivikram, P. Kavya, G. Mounika, M.G. Nair, Power quality improvement using statcom with renewable energy sources, in 2012 IEEE 5th India International Conference on Power Electronics (IICPE) (IEEE, 2012), pp. 1–6
S.-I. Inage, Prospects for large-scale energy storage in decarbonised power grids. Int. Energy Agency 3 (4), 125 (2009)
M. Jadidbonab, B. Mohammadi-Ivatloo, M. Marzband, P. Siano, Short-term self-scheduling of virtual energy hub plant within thermal energy market. IEEE Trans. Ind. Electron. 1 (2020). https://doi.org/10.1109/tie.2020.2978707
J.-P. Jimenez-Navarro, K. Kavvadias, F. Filippidou, M. Pavičević, S. Quoilin, Coupling the heating and power sectors: the role of centralised combined heat and power plants and district heat in a European decarbonised power system. Appl. Energy 270 , 115134 (2020)
J.T. Johnson, Design and evaluation of a secure virtual power plant. Technical report, Sandia National Lab.(SNL-NM), Albuquerque, NM (United States) (2017)
M. Kesler, E. Ozdemir, Synchronous-reference-frame-based control method for upqc under unbalanced and distorted load conditions. IEEE Trans. Ind. Electron. 58 (9), 3967–3975 (2010)
V. Khadkikar, Enhancing electric power quality using UPQC: a comprehensive overview. IEEE Trans. Power Electron. 27 (5), 2284–2297 (2011)
V. Khadkikar, A. Chandra, A. Barry, T. Nguyen, Analysis of power flow in UPQC during voltage sag and swell conditions for selection of device ratings, in 2006 Canadian Conference on Electrical and Computer Engineering (IEEE, 2006), pp. 867–872
J. Kiviluoma, S. Heinen, H. Qazi, H. Madsen, G. Strbac, C. Kang, N. Zhang, D. Patteeuw, T. Naegler, Harnessing flexibility from hot and cold: heat storage and hybrid systems can play a major role. IEEE Power Energy Mag. 15 (1), 25–33 (2017)
A. Kulmala, S. Repo, P. Järventausta, Coordinated voltage control in distribution networks including several distributed energy resources. IEEE Trans. Smart Grid 5 (4), 2010–2020 (2014)
T.-L. Lee, S.-H. Hu, Y.-H. Chan, D-statcom with positive-sequence admittance and negative-sequence conductance to mitigate voltage fluctuations in high-level penetration of distributed-generation systems. IEEE Trans. Ind. Electron. 60 (4), 1417–1428 (2011)
S. Lehnhoff, A. Nieße, Recent trends in energy informatics research. IT-Inf. Technol. 59 (1), 1–3 (2017)
P. Li, Y. Liu, H. Xin, X. Jiang, A robust distributed economic dispatch strategy of virtual power plant under cyber-attacks. IEEE Trans. Ind. Inform. 14 (10), 4343–4352 (2018)
Limejump gets all clear to chase big six in UK grid balancing market – rethink, https://rethi- nkresearch.biz/articles/limejump-gets-all-clear-to-chase-big-six-in-uk-grid-balancing-market/ . Accessed on 21 Oct 2020
L. Lin, X. Guan, Y. Peng, N. Wang, S. Maharjan, T. Ohtsuki, Deep reinforcement learning for economic dispatch of virtual power plant in internet of energy. IEEE Internet Things J. 7 , 6288–6301 (2020)
X. Liu, A. Aichhorn, L. Liu, H. Li, Coordinated control of distributed energy storage system with tap changer transformers for voltage rise mitigation under high photovoltaic penetration. IEEE Trans. Smart Grid 3 (2), 897–906 (2012)
J. Lizana, C. Bordin, T. Rajabloo, Integration of solar latent heat storage towards optimal small-scale combined heat and power generation by organic Rankine cycle. J. Energy Storage 29 , 101367 (2020)
J. Lu, X. Zheng, A. Gharaei, K. Kalaboukas, D. Kiritsis, Cognitive twins for supporting decision-makings of internet of things systems, in Proceedings of 5th International Conference on the Industry 4.0 Model for Advanced Manufacturing (Springer, 2020), pp. 105–115
C. Mateu-Royo, S. Sawalha, A. Mota-Babiloni, J. Navarro-Esbrí, High temperature heat pump integration into district heating network. Energy Convers. Manag. 210 , 112719 (2020)
S. Mishra, C. Bordin, A. Tomasgard, I. Palu, A multi-agent system approach for optimal microgrid expansion planning under uncertainty. Int. J. Electric. Power Energy Syst. 109 , 696–709 (2019)
‘modelling electricity demand the key’ as UK comes out of lockdown: Kiwi power – s&p global platts, https://www.spglobal.com . Accessed on 21 Oct 2020
Moixa to build virtual power plant as first phase of UK smart energy project – pv magazine international, https://www.moixa.com/ . Accessed on 21 Oct 2020
M. Molinas, J.A. Suul, T. Undeland, Low voltage ride through of wind farms with cage generators: statcom versus SVC. IEEE Trans. Power Electron. 23 (3), 1104–1117 (2008)
J.M. Morales, A.J. Conejo, H. Madsen, P. Pinson, M. Zugno, Integrating Renewables in Electricity Markets: Operational Problems , vol. 205 (Springer Science & Business Media, New York, 2013)
Navigant research names autogrid as #1 virtual power plant platform provider in 2020 – autogrid, https://www.auto-grid.com/products/virtual-power-plant/ . Accessed on 21 Oct 2020
Next kraftwerke connects 2 mw battery to its VPP in Belgium – pv magazine international, https://www.pv-magazine.com/2018/07/13/next-kraftwerke-connects-2-mw-battery-to-its-vpp-in-belgium/ . Accessed on 21 Oct 2020
Next kraftwerke records strong portfolio growth in 2017, https://www.next-kraftwerke.com/news/next-kraftwerke-records-strong-portfolio-growth-in-2017 . Accessed on 21 Oct 2020
H.T. Nguyen, L.B. Le, Z. Wang, A bidding strategy for virtual power plants with the intraday demand response exchange market using the stochastic programming. IEEE Trans. Ind. Appl. 54 (4), 3044–3055 (2018)
Open energi – dynamic demand 2.0 distributed energy platform, https://www.openenergi.com/ . Accessed on 21 Oct 2020
G. Papaefthymiou, K. Dragoon, Towards 100% renewable energy systems: uncapping power system flexibility. Energy Policy 92 , 69–82 (2016). https://doi.org/10.1016/j.enpol.2016. 01.025
T. Pavleska, H. Aranha, M. Masi, G.P. Sellitto, Drafting a cybersecurity framework profile for smart grids in EU: A goal-based methodology, in European Dependable Computing Conference (Springer, 2020), pp. 143–155
J.S. Pereira, J.B. Ribeiro, R. Mendes, G.C. Vaz, J.C. André, Orc based micro-cogeneration systems for residential application–a state of the art review and current challenges. Renew. Sustain. Energy Rev. 92 , 728–743 (2018)
Pge program will transform hundreds of homes into a virtual power plant – news releases – pge, https://www.portlandgeneral.com . Accessed on 21 Oct 2020
G. Plancke, K. De Vos, R. Belmans, A. Delnooz, Virtual power plants: definition, applications and barriers to the implementation in the distribution system, in International Conference on the European Energy Market, EEM , Aug 2015 (IEEE Computer Society, 2015). https://doi.org/ 10.1109/EEM.2015.7216693
Book Google Scholar
D. Pudjianto, C. Ramsay, G. Strbac, Virtual power plant and system integration of distributed energy resources. IET Renew. Power Gener. 1 (1), 10–16 (2007). https://doi.org/10.1049/iet-rpg:20060023
Quinbrook invests in flexible generation, grid support and demand response, https://www.quinbrook.com . Accessed on 21 Oct 2020
D. Ranamuka, A. Agalgaonkar, K. Muttaqi, Online voltage control in distribution systems with multiple voltage regulating devices. IEEE Trans. Sustain. Energy 5 (2), 617–628 (2013)
D. Ranamuka, A.P. Agalgaonkar, K.M. Muttaqi, Examining the interactions between dg units and voltage regulating devices for effective voltage control in distribution systems. IEEE Trans. Ind. Appl. 53 (2), 1485–1496 (2016)
D. Ranamuka, A.P. Agalgaonkar, K.M. Muttaqi, Examining the interactions between dg units and voltage regulating devices for effective voltage control in distribution systems. IEEE Trans. Ind. Appl. 53 (2), 1485–1496 (2017)
T.B. Rasmussen, G. Yang, A.H. Nielsen, Z. Dong, A review of cyber-physical energy system security assessment, in 2017 IEEE Manchester PowerTech (IEEE, 2017), pp. 1–6
P.K. Ray, S.R. Mohanty, N. Kishor, Classification of power quality disturbances due to environmental characteristics in distributed generation system. IEEE Trans. Sustain. Energy 4 (2), 302–313 (2012)
P.K. Ray, S.R. Mohanty, N. Kishor, J.P. Catalão, Optimal feature and decision tree-based classification of power quality disturbances in distributed generation systems. IEEE Trans. Sustain. Energy 5 (1), 200–208 (2013)
repowering-clean-sunrun.pdf, https://www.sunrun.com/sites/default/files/repowering-clean-sunrun.pdf . Accessed on 21 Oct 2020
M. Robinius, A. Otto, P. Heuser, L. Welder, K. Syranidis, D.S. Ryberg, T. Grube, P. Markewitz, R. Peters, D. Stolten, Linking the power and transport sectors – part 1: The principle of sector coupling. Energies 10 (7), 956 (2017)
J.M. Rozanec, L. Jinzhi, Towards actionable cognitive digital twins for manufacturing, in International Workshop On Semantic Digital Twins (SeDiT 2020) , Greece (2020)
Sa virtual power plant – tesla Australia, https://www.tesla.com/en_au/sa-virtual-power-plant . Accessed on 21 Oct 2020
O. Sadeghian, A. Oshnoei, R. Khezri, S. Muyeen, Risk-constrained stochastic optimal allocation of energy storage system in virtual power plants. J. Energy Storage 31 , 101732 (2020)
R. Saint, N. Friedman, The application guide for distributed generation interconnection-the nreca guide to IEEE 1547, in 2002 Rural Electric Power Conference. Papers Presented at the 46th Annual Conference (Cat. No. 02CH37360) (IEEE, 2002), pp. D2–1
I. Sarbu, C. Sebarchievici, A comprehensive review of thermal energy storage. Sustainability 10 (1), 191 (2018)
Simply energy virtual power plant – Australian renewable energy agency, https://arena.gov.au/projects/simply-energy-virtual-power-plant-vpp/ . Accessed on 21 Oct 2020
Software for virtual power plants powered by residential solar-plus-storage, https://www.pv-magazine.com/ . Accessed on 21 Oct 2020
M. Sony, Lean six sigma in the power sector: frog into prince. Benchmarking: Int. J. 26 , 356– 370 (2019)
Springer, Aims and scope of energy informatics journal, https://energyinformatics.springeropen.com , online; Accessed 2020
Statkraft unveils 1gw virtual power plant in UK, intends to double capacity by summer – current news, https://www.statkraft.com/newsroom/news-and-stories/archive/2020/vpp-balancing-services/ . Accessed on 21 Oct 2020
Storage and the rise of the virtual power plant – energy storage news, https://www.energy-storage.news/blogs/storage-and-the-rise-of-the-virtual-power-plant . Accessed on 21 Oct 2020
R. Thallam, G. Heydt, Power acceptability and voltage sag indices in the three phase sense, in 2000 Power Engineering Society Summer Meeting (Cat. No. 00CH37134), vol. 2 (IEEE, 2000), pp. 905–910
A. Van der Veen, M. Van der Laan, H. De Heer, E. Klaassen, W. Van den Reek, Flexibility value chain (2018)
S.K. Venkatachary, J. Prasad, R. Samikannu, A. Alagappan, L.J.B. Andrews, Cybersecurity infrastructure challenges in IoT based virtual power plants. J. Stat. Manag. Syst. 23 (2), 263–276 (2020)
F.A. Viawan, D. Karlsson, Combined local and remote voltage and reactive power control in the presence of induction machine distributed generation. IEEE Trans. Power Syst. 22 (4), 2003–2012 (2007)
VPP, Why Ecotricity has entered the flexibility market – theenergyst.com, https://theenergyst.com/ecotricity-enters-flexibility-market/ . Accessed on 21 Oct 2020
VPP.pdf, https://www.enbala.com/wp-content/uploads/2018/01/VPP.pdf . Accessed on 21 Oct 2020
S. Vukmirović, A. Erdeljan, F. Kulić, S. Luković, Software architecture for smart metering systems with virtual power plant, in MELECON 2010-2010 15th IEEE Mediterranean Electrotechnical Conference (IEEE, 2010), pp. 448–451
W.a. community virtual power plant confirms $50m Swiss investment – one step off the grid, https://onestepoffthegrid.com.au/w-a-community-virtual-power-plant-confirms-50m-swiss-investment/ . Accessed on 21 Oct 2020
R. Walling, R. Saint, R.C. Dugan, J. Burke, L.A. Kojovic, Summary of distributed resources impact on power delivery systems. IEEE Trans. Power Delivery 23 (3), 1636–1644 (2008)
What is a virtual power plant? https://www.solarpowerworldonline.com/2017/09/virtual-power-plant/ . Accessed on 21 Oct 2020
M. Wickert, S. Liebehentze, A. Zündorf, Experience report: first steps towards a microservice architecture for virtual power plants in the energy sector, in Joint Post-proceedings of the First and Second International Conference on Microservices (Microservices 2017/2019) , Schloss Dagstuhl-Leibniz-Zentrum für Informatik (2020)
S. Wong, J.-P. Pinard, Opportunities for smart electric thermal storage on electric grids with renewable energy. IEEE Trans. Smart Grid 8 (2), 1014–1022 (2016)
Y. Wong, L. Lai, S. Gao, K. Chau, Stationary and mobile battery energy storage systems for smart grids, in 2011 4th International Conference on Electric Utility Deregulation and Restructuring and Power Technologies (DRPT) (IEEE, 2011), pp. 1–6
Q.-H. Wu, J. Zheng, Z. Jing, X. Zhou, Large-Scale Integrated Energy Systems . Energy Systems in Electrical Engineering (Springer, Singapore, 2019). https://doi.org/10.1007/978-981-13-6943-8
Y. Yohanis, O. Popel, S. Frid, B. Norton, Geographic variation of solar water heater performance in Europe. Proc. Inst. Mech. Eng. Part A: J. Power Energy 220 (4), 395–407 (2006)
V. Yuvaraj, S. Deepa, A.R. Rozario, M. Kumar, Improving grid power quality with facts device on integration of wind energy system, in 2011 Fifth Asia Modelling Symposium (IEEE, 2011), pp. 157–162
Z. Zhai, J.F. Martínez, N.L. Martínez, V.H. Díaz, Applying case-based reasoning and a learning-based adaptation strategy to irrigation scheduling in grape farming. Comput. Electron. Agric. 178 , 105741 (2020)
X. Zhang, M. Shahidehpour, A. Alabdulwahab, A. Abusorrah, Optimal expansion planning of energy hub with multiple energy infrastructures. IEEE Trans. Smart Grid 6 (5), 2302–2311 (2015). https://doi.org/10.1109/TSG.2015.2390640
G. Zhang, C. Jiang, X. Wang, Comprehensive review on structure and operation of virtual power plant in electrical system (2019). https://doi.org/10.1049/iet-gtd.2018.5880
Y. Zhao, Electrical power systems quality. Univ. Buffalo (2016)
B. Zwaenepoel, J. Vansteenbrugge, T. Vandoorn, G. Van Eetvelde, L. Vandevelde, Renewable energy balancing with thermal grid support, in 16th International conference on Process Integration, Modelling and Optimisation for Energy Saving and Pollution Reduction (PRES 2013) , vol. 35 (AIDIC Servizi, 2013), pp. 535–540
Download references
Acknowledgements
This work is supported by the Estonian Research Council grant PUTJD915.
Author information
Authors and affiliations.
Tallinn University of Technology, Tallinn, Estonia
Sambeet Mishra
Danish Technical University, Kongens Lyngby, Denmark
The Arctic University of Norway, Tromsø, Norway
Chiara Bordin
Madis Leinakse, Fushuan Wen & Ivo Palu
KES International, Shoreham-by-sea, UK
Robert J Howlett
You can also search for this author in PubMed Google Scholar
Corresponding authors
Correspondence to Sambeet Mishra or Chiara Bordin .
Editor information
Editors and affiliations.
Information Technology and Decision Sciences, University of North Texas, Denton, TX, USA
Mahdi Fathi
Department of Energy, Politecnico di Milano, MILANO, Milano, Italy
Industrial & Systems Engineering, University of Florida, GAINESVILLE, FL, USA
Panos M. Pardalos
Rights and permissions
Reprints and permissions
Copyright information
© 2021 Springer Nature Switzerland AG
About this entry
Cite this entry.
Mishra, S., Bordin, C., Leinakse, M., Wen, F., Howlett, R.J., Palu, I. (2021). Virtual Power Plants and Integrated Energy System: Current Status and Future Prospects. In: Fathi, M., Zio, E., Pardalos, P.M. (eds) Handbook of Smart Energy Systems. Springer, Cham. https://doi.org/10.1007/978-3-030-72322-4_73-1
Download citation
DOI : https://doi.org/10.1007/978-3-030-72322-4_73-1
Published : 26 February 2022
Publisher Name : Springer, Cham
Print ISBN : 978-3-030-72322-4
Online ISBN : 978-3-030-72322-4
eBook Packages : Springer Reference Economics and Finance Reference Module Humanities and Social Sciences Reference Module Business, Economics and Social Sciences
- Publish with us
Policies and ethics
- Find a journal
- Track your research
Characterisation of Virtual Power Plants
- Department of Electrical & Electronic Engineering
Student thesis : Phd
- Virtual Power Plants
- Distributed Generation
- Characterisation
File : application/pdf, -1 bytes
Type : Thesis
- Open access
- Published: 31 March 2021
Cybersecurity challenges in energy sector (virtual power plants) - can edge computing principles be applied to enhance security?
- Sampath Kumar Venkatachary ORCID: orcid.org/0000-0002-5583-7313 1 ,
- Annamalai Alagappan 2 &
- Leo John Baptist Andrews 3
Energy Informatics volume 4 , Article number: 5 ( 2021 ) Cite this article
8221 Accesses
7 Citations
3 Altmetric
Metrics details
Distributed generators (D.G.’s) enable us to generate, supply and be self-reliant on power while also allows us to supply power to meet the demand through virtual power plants. The virtual power plants also help us analyse, control, optimise, and help bridge the gap of demand and supply in these vast energy requirements. With this also comes challenges associated with securing physical systems, data protection and information privacy. Recent technological advancements have aided cybercriminals to disrupt operations by carrying out deliberate attacks on the energy sector. Though security researchers have tried to mitigate the risks, vulnerabilities, and it remains a challenge. This paper aims to present a comprehensive Edge-based security architecture to help reduce the risks and help secure the physical systems and ensure privacy and data protection.
Introduction
Virtual Power Plants (VPP), Smart Grids (S.G.). Virtual Power Plant, “As its name infers, a virtual power plant does not exist in the solid and-turbine sense. It utilises the smart grid infrastructure to integrate little, divergent energy assets as though they were a single generator. Pretty much any energy source can be connected up. (Kumagai, 2012 ). Moreover, the energy can likewise add to a virtual power, not plant’s capacity” The point of VPP’s is to distributed appropriated energy assets over the virtual energy pool. (Fig . 1 ) shows a brief overview of a Virtual Power Plant. Unlike traditional energy systems, the energy generation is not centralised in a remote location and then transmitted in a complex network but instead generated in small individual distributed areas. In this, a consumer can become a prosumer and supply the excess energy generated back to the grid. The traditional model, though, is cost-effective the outreach of the model in third world countries pose a problem where the majority of the population have no access to energy. This problem technically can be addressed by using distributed energy networks and effectively exercise control through a VPP operator. It is expected that by 2035–2040 the electricity system will mostly constitute decentralised IoT devices effectively communicating through virtual power plants and distributed energy systems. In short, electricity will be digital.
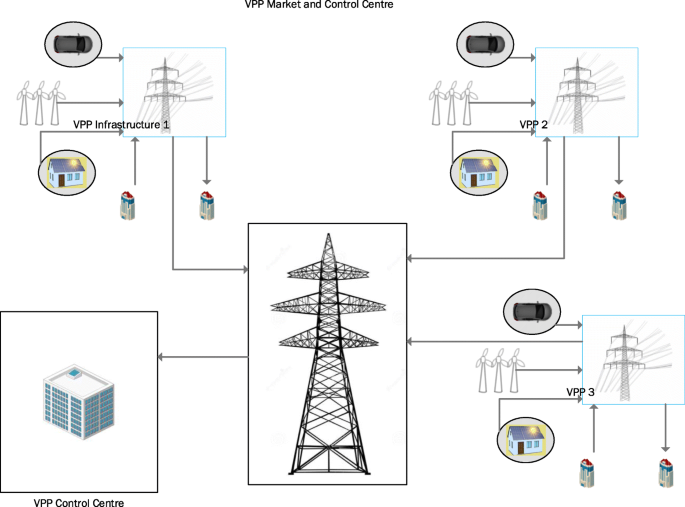
VPP Energy System
This growing deployment of small prosumers also poses a problem in the grid systems which also needs to adopt a decentralised approach to reduce the complexity and overcome the increasingly new challenges in management (Pop et al., 2019 ). These deployments pose a different set of problems in the form of efficiency in integration, energy supply security, continuity. Assuming the energy generated is not consumed by the consumer in the resource, it could also technically lead to over-voltage problems, losses, transformer ageing and efficiency.
The future energy networks will relate to advance distribution and management systems, including using data relating to grid monitoring, control, sensors, load balancing requirements, environmental parameters etc. (Rennie, 2019 ). The range of data shared between transmission and distribution, system, grid operators, consumers, prosumers, aggregators are enormous. Most of these systems will also be using intelligent control systems, distributed intelligence employing A.I. This will also help enhance consumers with improving capabilities, reporting and managing infrastructure.
Edge virtual power plants
The term edge computing is relatively a new concept, though very similar to other computing terminologies in use. Edge computing refers to simple process operations carried out close to the origins of data. In simple terms, the processes can be done on the devices rather than on the servers, increasing the processing speed. Therefore, it is possible to offload a few resource-hungry tasks to the new edge layer, thereby reducing the impact on resource-constrained resources. The application of edge technology in virtual power plant technically involves optimising resources through machine learning algorithms. As more and more DER systems integrate, the data must be processed balloons, requiring more processing power. Since each of these devices communicates with the IoT devices in the household, the information processed can be done locally (Rennie, 2019 ).
Traditional VPP’s mostly are controlled centrally, and the information is collated and transmitted to these central units through a communication environment including 5G technologies (Jaber et al., 2016 ; Khodashenas et al., 2016 ) (Zaho & Gerla, 2019 ). 5G communication technologies are said to noted to have privacy issues in a centralised environment (Cai et al., 2019 ; Cai & Zheng, 2019 ; Tian et al., 2019 ), leading researchers to suggest distributed control methods (Chen et al., 2018a , b , c ; Cai & He, 2019 ; Huang et al., 2019 ). The advancement of technology has also led to research on edge computing for processing information and control. (Chen et al., 2018a , b , c ; Chen et al., 2018a , b , c ). The rise of A.I. and cognitive computing (Chen et al., 2019 ) has paved the way for applying mathematical tools to improve processes and efficiency, which are popularly termed as Edge Intelligence (Zhou et al., 2019 ; Rausch & Dustdar, 2019 ). Due to this huge demand for processing on the edge nodes, edge computing applies the A.I. to enhance the processing speeds. The application of edge intelligence computing requires a huge communication network and bandwidth. As VPP is also a combination of distributed networks, some of these problems apply. Some of these problems have been effectively addressed to minimise the costs and reduce the communication environment by Li et al. (Li et al., 2018 ).
These dependencies on the ICT infrastructure also has potential cybersecurity threats. Since the operations are widespread and network-based with individual endpoints, the attack surface in a virtual power plant is vast since the core of the processes is from the control centre. The threat actors multiply manifold due to the different RTUs and SCADA gadgets. Any vulnerability in a single system is a gateway for hackers to get into the network. It can be noticed from the data analysed that the critical infrastructure services are frequently being targeted with malware or ransomware with a motive for financial gain or disruption. (Venkatachary et al., 2017 ; Venkatachary et al., 2018a ; Venkatachary et al., 2018 b). They are thus providing a way for enhancing security mechanisms across the network. Therefore, this new edge concept also offers the opportunity to deploy new based security solutions on the end devices, thus optimising performance. (Montero et al., 2016 ; Mach et al., 2017 ; Errabelly et al., 2017 ; Tao et al., 2017 ; Hsu et al., 2018 ).
Against this backdrop, this paper aims to provide an insight into various cybersecurity threats that emanate from these advance technological applications. Section 2 provides a detailed insight into cybersecurity trends and facilities attacked, and the need for better security. Section 3 discusses at length the proposed Edge-based solutions towards enhancing security in virtual power plants. Section 4 and 5 provides a detailed discussion and conclusions.
Cybersecurity trends and the edge centric architecture for VPP
Among the sectors, the energy sector is one of the most targeted sectors in recent times. The motivation of the attackers has changed over time. Though the primary motivation still remains money, other motivations like cyber warfare and causing disruptions have also witnessed an increase Figs. 2 & 3 , and Table 1 outlines the basis and the sectors targeted. As can be seen, the trends during 2020 have changed an increase in health care facilities being targeted more than other industries. Given the vulnerabilities in the firmware of different types of equipment and addressing the vulnerabilities through patch mechanisms a nightmare for security firms, the energy sector is a primary motivator for cyber-attacks. According to data by Kaspersky labs, the attack vectors included DDos, Java Script, BAT, V.B. Script, Python, Word on the platforms (Kaspersky Labs, 2020 ).
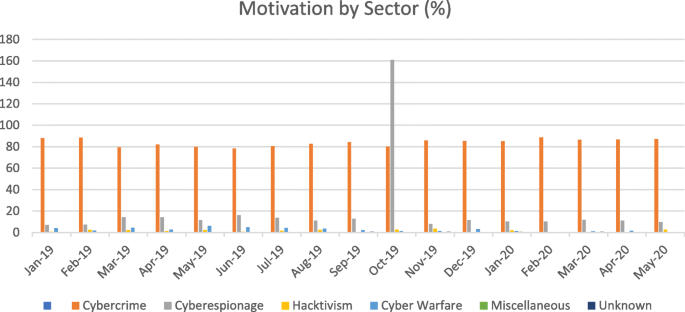
Motivation trends for Attacks from 2019 to 2020
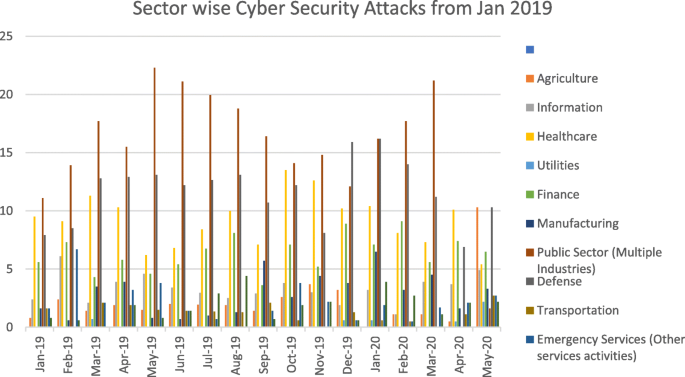
Sectors targeted from 2019 to 20
The traditional approaches to handling cybersecurity using firewalls and cryptography incidents are outmoded due to the variety and complexity of attacks in recent times. The complexity of cybersecurity attacks in the form of disabling, tampering, reprogramming the control systems can lead to malfunctions, unavailability of system services during critical operations, which could lead to other consequences in the form of human life. (Venkatachary et al., 2018a ; Venkatachary, 2018b ; Venkatachary et al., 2020 ) In short, the cybersecurity attacks in the recent past has undergone a sea change. Some notable examples are black energy, Stuxnet and so on (Symantec, 2009 ; Symantec, 2011 ; Liu et al., 2012 ).
Overview of cyber attacks and the need for better security to secure energy systems
With the rise in energy demand, the distributed generators play a vital role in bridging the gap between demand and supply, securing the devices gain prominence. Security in device controllers is often overlooked as it is mostly isolated and tied to the infrastructure. This poses a problem of often not getting the control devices patched, thereby exposing them to vulnerabilities and attacks. An underlying problem in securing devices is the responsibility attached to the person. Often, it is found that most operators operating these machines simply do not have the experience or expertise and the knowledge of how these I.T. systems function and vice versa applies to the I.T. personnel developing necessary patches etc. (Brook, 2018 ).
The complexity of the distributed generators also poses a considerable risk, unlike computers and other devices, which can be managed through upgrades and patches (Bekara, 2014 ). The different layers that encompass the virtual power plant are complex, and the interlinks in each layer interwinds with the other layers. The nature of architecture in VPP has many ICS devices interconnected, and the attacks can take place on any of the devices like AMI, SCADA, control and monitoring devices. Taking this into account, the entire network can be made unavailable with a single point of failure.
The number of critical infrastructures targeted across the countries is tabled in Table 2 . Some notable special attacks between Jan-20 to June 2020 on the critical infrastructures is tabled in Table 3 . As can be seen from the table, there is a rising volume and sophistication of the attacks on the infrastructure services and the need to safeguard the equipment, data becomes critical (Lathrop et al., 2016 ; Kimani et al., 2019 ).
Security breaches are a significant concern in virtual power plant systems and could lead to colossal property losses (Sha et al., 2016 ) in millions. Although the overall security apparatus in the virtual power plant is challenged due to many factors involved in the design; among them, the serious is the availability. Many security features are employed to protect and ensure availability, including some of the advanced access control mechanism (Alramadhan et al., 2017 ), signature-based authentication (Chen et al., 2018a , b , c ), homomorphic encryption (Wang et al., 2013 ).
Edge centric VPP architecture
Security research on IoT-based platforms that intends to provide security solutions have been carried out by many researchers, and these efforts include Edge-based security solutions. (Mach et al., 2017 ; Errabelly et al., 2017 ; Montero et al., 2016 ; Hsu et al., 2018 ), firewall protection (Hu et al., 2014 ), IDS (Roman et al., 2018 ; Haddadi et al., 2018 ), IPS, privacy preservation (Lu et al., 2017 ; Du, 2018 ; Singh et al., 2017 ), authentication protocols (Ali et al., 2018 ) etc. Edge-based protection in IoT centric devices mainly is concentrated on the user (Montero & Serral-Gracia, 2016 ; Montero, 2015 ), device (Errabelly et al., 2017 ; Hsu et al., 2018 ) and endpoint security (Mukherjee et al., 2017 ).
The edge centric VPP architecture contains four major components, the cloud architecture, the edge layer, VPP operators, VPP end consumers/prosumers. Though resource-intensive, the cloud architecture is located far away from the virtual power plants consumers/ prosumers. Therefore the architecture cannot function efficiently, just as in IoT (Chen et al., 2016 ) due to its real-time application of distributing power on the grids. With the edge layer coming into effect, the components and the dynamics of the fundamental architecture changes with the Edge being the core as it can coordinate with different VPP’s while at the same time complement and ensure optimised performance of the plant. The edge layer handles the VPP consumers queries or demand response in the edge environment, thus acting as a bridge between the users and the cloud (Sha et al., 2020 ). Researchers have made efforts to study and design appropriate security solutions for Edge. However, as the Edge is still in its infancy stage, security is still a long way to go (Sha et al., 2016 ). There needs to be continuous research for enhancing general cybersecurity (Venkatachary et al., 2018a ).
Edge provides a new opportunity to explore new security mechanism for a virtual power plant. Most edge designs target offloading endpoint protection on the devices to edge. This could, in turn, pose new challenges in the form of resource constraints at the Virtual Power Plant layer.
User-centric edge-based VPP security
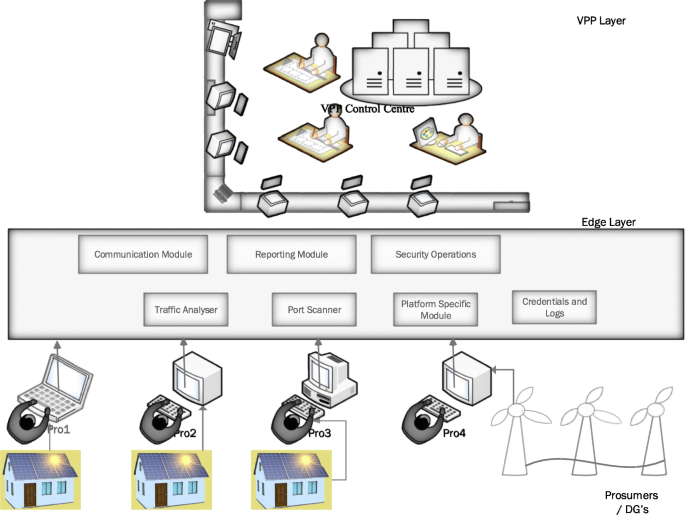
The key to cybersecurity is the weakest link, and the security is as good as the weakest link in the virtual power plant. With numerous VPP devices connected in a network, the prosumers/consumers access to generation, transmission & distribution of energy and data using terminal devices is imminent. When considering the security aspects, significant concerns arise. For example, the consumer may either login in from a terminal device, which is trusted and secure or from an untrusted device. In the event of the prosumer logging from an untrusted device, the security could be compensated with additional security control measures as in the case of untrusted networks. The second aspect is that the consumer may not be aware of the security or have enough knowledge to manage the infrastructure, thereby resulting in potential risk effectively. Incorporating the Edge layer in managing such as scenario is an option; however, the drawbacks could be network challenges. The additional aspect could be on the personal security of the data on the network edge (Montero et al., 2016 ) and the virtual guard in Edge (Montero, 2015 ).
Figure 4 provides a brief overview of user-centric VPP security architecture. The design incorporates a trusted domain on the edge layer. The consumers/prosumers who generate, distribute and access data incorporate additional endpoint security. This translates to user security policy such as antivirus, firewalls (Basile et al., 2010 ), SCADA device isolations and other inspection tools. The edge layer, which is the trusted domain, will manage the secure access to the virtual power plant operator or the virtual power transmission system operator. The trusted domain, in this case, acts as an encapsulation layer to user-specific policy. The user is verified using RVA techniques to ensure trust between the prosumer. This design is based on the Network Functions Virtualisation technology to construct the edge layer. In this way, security can effectively be managed by deploying Edge.
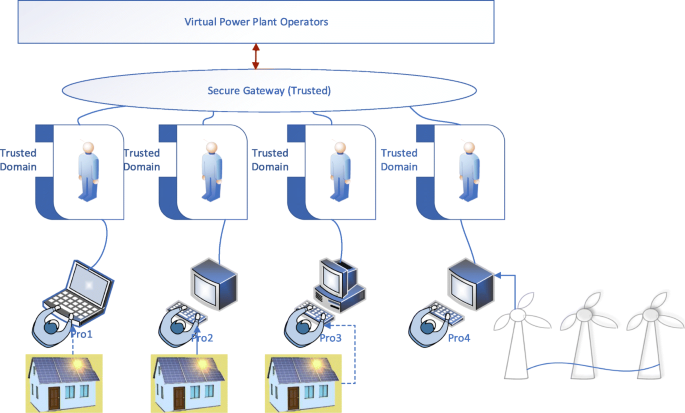
User-centric Edge-based VPP Security
Device-centric edge security for VPP
Unlike the user-centric security layer, the Device-Centric security layer is tailored to suit the prosumer or the consumer’s requirement based on the resource availability, the data sensitivity and its impact on tasks and in consideration with the security needs of the endpoint VPP devices. Erabally et al. (Errabelly et al., 2017 ), in their paper, discuss the device-centric edge layer security comprising of six modules that function in a synchronised manner to handle specific security challenges in the IoT systems. The individual modules in each case include a systematic analysis of security profile, protocols, simulation, communication and request handling.
Figure 5 shows Device-Centric Edge security for Virtual Power Plant based on EdgeSec Model. In this model, each prosumer registers the devices with a specific security profile managing the module. The prosumer specific security details are then collected, and device-specific requirements are then identified. A detailed security check is implemented carrying out particular functions, one to verify the security dependency on the specific device registered and second to deploy the security function accordingly. The Edge then identifies a suitable protocol for each of the prosumer based on the resource availability and prosumer security profile. The security simulation model in the Edge simulates the instructions before deployment. This is done to protect the safety of the virtual plant prosumer’s physical system. Other functions such as encrypting communication, coordination etc., work together.
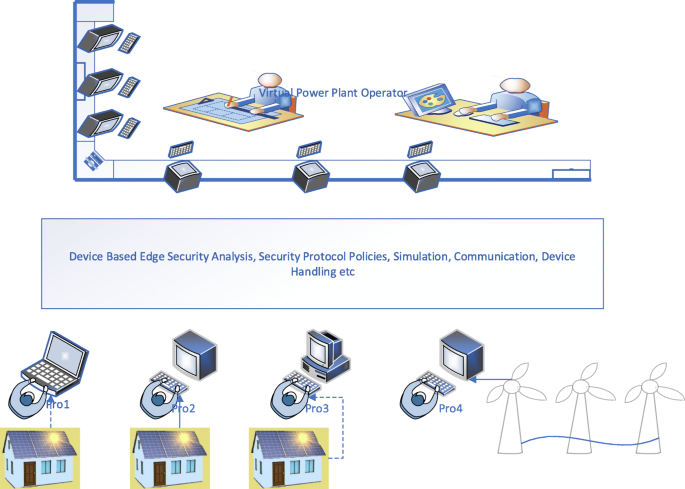
Device-Centric Edge Security for VPP

Firewall edge security for VPP
Edge-based firewall systems is an innovative approach to protecting resources. Hu et al. base their research using software-defined networking and suggest a comprehensive framework to detect anomalies and offer effective firewall policy resolutions accurately. This SDN based firewall has three functional components, violation detection, flow tracking and authorisation. Violation detection is handled using traditional firewall packet filtering techniques. Flow tracking is based on headers using a Header Space Analysis (HAS) tool, one of the several invariant verification tools. (Kazemian et l., 2012 ; Kazemian et al., 2013 ; Khurshid et al., 2013 ). The authors further define Firewall Authorisation Space to allow or deny packets based on the firewall rules, thereby enabling conversion into smaller denied and allowed spaces. On the other hand, the distributed firewall architecture is placed at the network edge and adopts a master-slave architecture, thereby providing centralised management (Markham et al., 2001 ).
Most prosumers in a virtual power plant are small-time operators and cannot support huge firewalls or necessary infrastructure to support them. Assuming that a single virtual power plant operator has a considerable number of generators connected, it will be too costly to manage the installation of firewalls.
Figure 6 describes an edge-based firewall design. The firewall policies are converted into flow policies. The conflictions in these policies are resolved and later applied as a firewall rule. These firewall rules are applied in the edge layer. The incoming and the outgoing traffic out of the individual prosumers/consumers are examined and later allowed or disallowed. The edge-based firewalls are feasible and easier to deploy. The managing of the firewall is also easy as there is only one centralised firewall. Further, the system can be modified to suit the need-base security model.
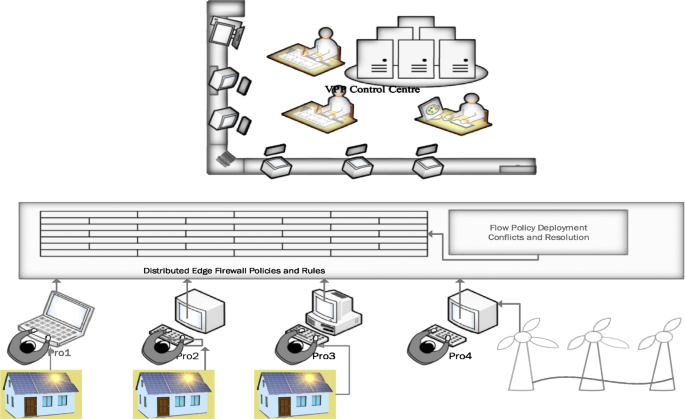
Distributed Edge Based Firewall
Edge-based intrusion detection systems (EIDS)
According to security researchers, the energy sector is the most frequently targeted sector by cybercriminals. As of 2019, 16% of the attacks were concentrated on energy with advance attacks and remained at the top 10 targeted industries (Kreyenber, 2019 ). The recent DDoS attacks in 2016 caused significant losses (Brewster, 2016 ). The availability of a distributed intrusion detection could significantly have enabled the security researchers to detect these type of security attacks at an early stage and prevent it (Sha et al., 2020 ). The availability of the information in this makes a vital difference. Researchers. The use of A.I. and machine learning algorithms in the security layer could significantly change the dynamics of security due to learning from multiple sources. The ease of adaptability to the changing scenarios could make a huge difference. Some notable research in apply edge-based IDS is discussed in papers by several researchers Yaseen et al. (Yaseen et al., 2016 ). (Roman et al., 2018 ). (Haddadi et al., 2018 ). (Roman et al., 2018 ) suggest a VIS (Virtual Immune System) to analyse network traffic with two functions: the kernel and the immune cells. The orchestrator inside the kernel is used for the configuration and deployment of the immune cells. The immune cells scan, analyse, manages the traffics and is also responsible for storing logs. Haddadi et al., in their research paper on SIOTOME, illustrate Edge-based architecture for IoT security. Here, the edge data collector is used for monitoring the network traffic information in the IoT devices. The edge layer analyses the traffic collected information on network threats, attacks, and feedback on the controller’s collected information. The SIOTOME also enables the defence mechanism like network isolation (Nunes et al. 2014 ), limiting the attack surface area. They also aid in stopping vulnerability scans and DDoS attacks.
Figure 7 and Fig. 8 shows a simple Edge-based IDS system design and Virtual Immune System. The DTM (Distributed Traffic Monitoring System) collects the information from the individual prosumers in real-time. The system then runs the intrusion detection algorithms. There is a collaborative compilation of the traffic, and the results are then enforced on to the network controller.
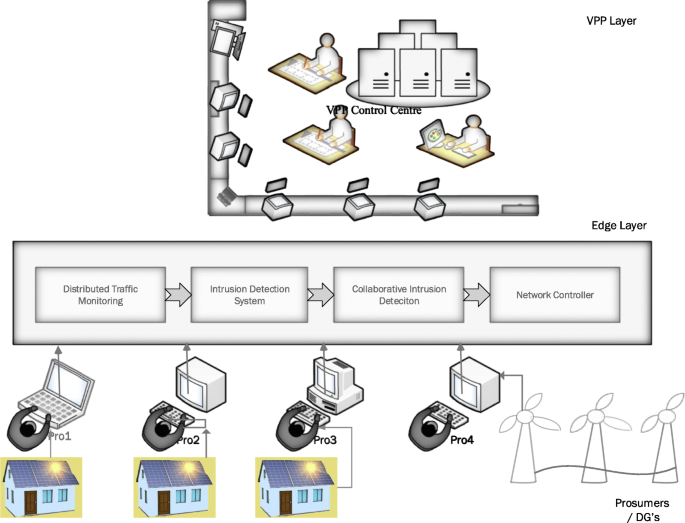
Edge Based Intrusion Detection System (EIDS)
Edge-based Virtual Immune System
Edge-based authentication and authorisation in virtual power plants
Industrial Control system attacks in the energy sector have witnessed a surge in recent times (Wilhoit et al., 2013 ; Dasgupta et al., 2017 ). This brings into focus two main features, authentication and authorisation, which can unauthorised attacks and DDoS attacks (Kolias et al., 2017 ). The drawback in the devices using end to end communication is difficult to create due to heteromerous peers. Secondly, signature-based algorithms can only be employed in the traditional authentication mechanism, making it difficult to apply in virtual power plant areas. The insertion of an Edge layer improves the prospects of utilising multi-authentical protocols and multiple phase authorisation. Sha et al., in their paper, discuss the Edge-based device as a mutual authenticator with a two-phase authentication protocol. In the first stage, the edge authenticator authenticates using a digital signature and gathers users credentials. The credentials obtained are then reauthenticated using a mutual authenticator using a symmetric key-based algorithm (Sha et al., 2014 ; Sha et al., 2017 ). Researchers have also attempted to enhance the authentication protocols using RFID based algorithms. (Fan et al., 2012 ; Gope et al., 2018 ).
The process of authenticating prosumers in a virtual power plant is segmented, including the prosumers end devices and the edge layer. Depending on the characteristics of the communication, the protocols can be customised. Thus, the Edge layer works as the man in the middle, which helps set up mutual authentication and authorisation. As the Edge provides multiple authentication interfaces; thus, it provides a secure interface (Dasgupta et al., 2017 ).
Edge-based privacy-preserving designs
Virtual power plants are a host of data hubs as prosumers and consumers contribute to power generation and attract vast cybercriminals. Data privacy takes precedence and requires stringent policies, monitoring and protection. As more and more devices get connected to virtual power plant operators, the data available to the plant operators is vast and needs to be protected from both the prosumer and operator levels. It is possible to achieve greater privacy by adapting different privacy protection algorithms like differential privacy (Dwork, 2014 ), k-anonymity (Sweeney, 2002 ; Sha et al., 2006 ; Xi et al., 2007 ), privacy preservation aggregation (Lu et al., 2017 ) etc.
Lu et al., in their paper on privacy protection, suggest a method to keep the privacy intact by using a lightweight privacy-preserving data aggregation scheme for IoT devices. They use a message authentication code to process the information reported by the devices. Once the Edge receives the authenticate of the devices by comparing the MAC and then generate a value for the IoT applications. Gentry, in his thesis, for solving a cryptographic problem, present fully homomorphic encryption. They use a simple algorithm based on a bootstrap mechanism for encryption through a recursive self-embedding algorithm “Paillier” (Gentry, C, 2009 ). One way hashing technique and the Chinese remainder theorem have also been used to address the privacy problem (Pei et al., 1996 ; McSherry & Talwar, 2007 ).
Figure 9 shows a brief overview of applying Edge design for preserving privacy. The Edge architecture uses privacy-preserving aggregation, k-anonymity and differential privacy together to decipher the queried data and responses between the prosumers and virtual plant operators to ensure data protection at either end. Data transmitted is verified, authenticated and established, thus ensuring privacy protection.
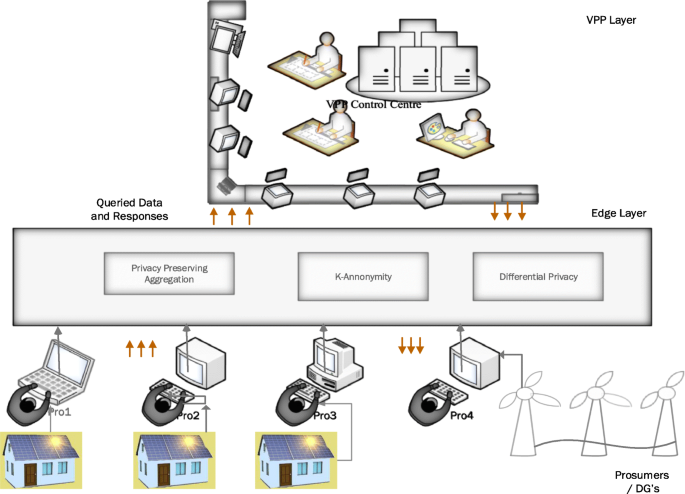
Edge-Based Privacy-Preserving Model
The previous section portrays different research techniques that have been applied in different platforms and suggest applications in virtual power plant areas. The Edge computing methods are still in their infancy, and there are still numerous challenging issues that need to be addressed. Though the Edge layer provides a new model for providing security solution, the Edge has a vast surface area and could, in turn, be subjected to attack. Addressing the security concerns in the Edge layer is not a huge task as opposed to other data centre securities. Thus, warranting more research in the area.
Though there are several Edge-based privacy protection techniques, the Edge protocols applied may, in turn, start to track the data and may have vested interests. (Razeghi & Voloshynovski, 2018 ) (Sharma & Chen, 2017 ). This in-turn, will warrant other innovative security solutions for protecting privacy. Studies have been carried out using Isolation techniques, but it remains to be seen how to implement the techniques in the edge layer effectively. It also remains to be seen how to effectively adopt new algorithms to establish trusted security between the Edge devices and the prosumer devices. Researchers have also proposed adopting machine learning algorithms to advance researches in intrusion detection techniques. Buczak et al. present a survey on using data mining and machine learning techniques as methods for intrusion detection. (Buczak & Guven, 2016 ). The popularity of deep learning has also contributed to understanding intrusion detection (Yin et al., 2017 ). However, the machine learning algorithmic methods require huge data sets and are most central to the environment and hence is a drawback for deployment in small Edge environments. Secondly, machine learning algorithms are more suited and beneficial in the cloud. This provides us with an opportunity to research and deploy cross-domain algorithms for intrusion detection.
Machine learning algorithms are learners, and they learn from the different attack detection techniques employed for intrusion detection. Therefore, the returned data has to be accurate and correct, on which decisions are based (Sha & Zeadally, 2015 ). However, there is a lack of data protocols to analyse and ensure the correctness of a high-quality dataset. In this environment, cross-domain verifications would be of great interests. (Sha et al., 2010 ). There has been a little contribution towards researching the cost impacts in the Edge environment. Research in the cost-benefit analysis of deploying Edge should be encouraged with active participation and collaboration. Though the safety of the prosumer equipment is extremely important, the research in this field is limited to a few. As virtual power plants are real-time, the requirements are real-time, thus complicating the simulations and modelling a suitable design (Weber & Studer, 2016 ). This also poses a challenge for response time to potential safety risks to minimise damages caused towards the equipment etc.
Virtual machines have found widespread use in many areas, and it is being researched in the application of the Edge layer. The ease of deploying V.M.s in the environment also pose a security threat as more than one V.M. could be deployed in the layer (Tsai, 2012 ; Eldefrawy et al., 2017 ). Considering the virtual power plant environment, these machines need to be simple, light and should meet the requirements of the prosumers. Thus, there is a huge scope for researching in this area.
Remarks and conclusions
The challenge of securing virtual power plants systems has generated great interests among researchers. The nature and operations of the virtual plants and prosumer/consumer generators pose significant challenge and risks. The advancement of new technologies in computing like edge computing has resulted in researching edge-based security systems for virtual power plants and distributed generators. This paper aims to present an assessment and a way of adopting Edge-based security systems in virtual power plants. In this context, it has defined to provide Edge-centric architecture. These solutions aim to address key protection of VPP devices, including a comprehensive cybersecurity architecture, application of Edge-based firewalls, intrusion detection systems, Edge-based authentication and authorisations.
Abbreviations
Internet of Energy
Distributed Denial of Service
Remote Terminal unit
Master Terminal Unit
Supervisory Control and Data Acquisition
Transmission System Operator
Distribution System Operator
Advanced Metering Infrastructure
Artificial Intelligence
Alexander, G. (2012). The Flame: Questions and Answers. Kaspersky Labs, Kaspersky Labs. Retrieved 07 06, 2017, from https://securelist.com/34344/the-flame-questions-and-answers-51/
Ali Z, Hossain MS, Muhammad G, Ullah I, Abachi H, Alamri A (2018) Edge-centric multimodal authentication system using encrypted biometric templates. Futur Gener Comput Syst 85:76–87. https://doi.org/10.1016/j.future.2018.02.040
Article Google Scholar
Alramadhan, M., K. Sha, (2017). An overview of access control mechanisms for the internet of things. 26th International Conference on Computer Communications and Networks (ICCCN) (pp. 1-7). Vancouver, Canada: IEEE doi: https://doi.org/10.1109/ICCCN.2017.8038503
Basile C, Lioy A, Scozzi S, Vallini M (2010) Ontology-based security policy translation. J Information Assurance Security 5(1):437–445
MATH Google Scholar
BBC. (2014). Energy firms hacked by 'cyber-espionage group Dragonfly. BBC News (Online), BBC. BBC. Retrieved 06 09, 2017, from http://www.bbc.com/news/technology-28106478
Bekara, C. (2014). Security issues and challenges for IoT based smart grid. International Workshop on communicating objects and machine to machine for mission-critical applications (COMMCA). Doi: https://doi.org/10.1016/j.procs.2014.07.064
Boldizsar B, Gabor, P´., Levente, B., Mark, F. (2012) The cousins of Stuxnet: Duqu, flame, and gauss. Future internet , MDPI 4(4):971–1003. https://doi.org/10.3390/fi4040971
Boldizsár, B., Gábor, P., Levente, B., Félegyházi, M. (2011). Duqu: A Stuxnet-like malware found in the wild. Budapest University of Technology and Economics, Department of Telecommunications. Budapest, Hungary: Laboratory of Cryptography and System Security (CrySyS). Retrieved 06 11, 2017, from https://www.crysys.hu/publications/files/bencsathPBF11duqu.pdf
Brewster, T. (2016). How hacked cameras are helping launch the biggest attacks on the Internet has ever seen . Retrieved from www.forebes.com/sites : https://www.forbes.com/sites/thomasbrewster/2016/09/25/briankrebs-overwatch-ovh-smashed-bylargest-ddos-attacks-ever/$705007235899
Brook, C. (2018, 12, 05). Data Protection 101: What is ICS Security . Retrieved from www.digitalguardian.com : https://digitalguardian.com/blog/what-ics-security
Buczak AL, Guven E (2016) A survey of data mining and machine learning methods for cybersecurity intrusion detection. IEEE Communications Surveys & Tutorials 18(2):1153–1176. https://doi.org/10.1109/COMST.2015.2494502
Cai Z, He Z (2019) Trading private range counting over big IoT data. In: IEEE 39th International Conference on Distributed Computing Systems. IEEE, Texas, pp 144–153
Google Scholar
Cai Z, Zheng X (2019) A private and efficient mechanism for data uploading in smart cyber-physical systems. IEEE Transactions on Network Science and Engineering 7(2):766–775. https://doi.org/10.1109/TNSE.2018.2830307
Article MathSciNet Google Scholar
Cai Z, Zheng X, Yu J (2019) A differential-private framework for urban traffic flows estimation via taxi companies. IEEE Transactions on Industrial Informatics 15(12):6492–6499. https://doi.org/10.1109/TII.2019.2911697
Chen M, Hao Y, Gharavi H, Leung V (2019) Cognitive information measurements: a new perspective. Inf Sci 505:487–497. https://doi.org/10.1016/j.ins.2019.07.046
Article MathSciNet MATH Google Scholar
Chen M, Hao Y, Lai C, Wu D, Li Y, Hwang K (2018a) Opportunistic task scheduling over co-located clouds in the mobile environment. IEEE Transaction on Services Computing 11(3):549–561. https://doi.org/10.1109/TSC.2016.2589247
Chen M, Zhou J, Tao G, Yang J, Hu L (2018b) Wearable effective robot. IEEE Access 6:64766–64776. https://doi.org/10.1109/ACCESS.2018.2877919
Chen S, Zeng P, Choo KR, Dong X (2018c) Efficient ring signature and group signature schemes based on Q-ary identification protocols. Comput J 61(4):545–560. https://doi.org/10.1093/comjnl/bxx112
Chen X, Jiao L, Li W, Fu X (2016) Efficient multi-user computation offloading for mobile-edge cloud computing. IEEE/ACM Trans Networking 5(1):2795–2808
Dasgupta D, Roy A, Nag A (2017) Multi-factor authentication. Advances in User Authentication, pp 185–233. https://doi.org/10.1007/978-3-319-58808-7_5
Book Google Scholar
David. (2014). Havex Hunts For ICS/SCADA Systems. (F-Secure Labs) Retrieved 06 15, 2017, from https://www.f-secure.com/weblog/archives/00002718.html
Desarnaud G (2017) Cyber attacks and energy infrastructures - anticipating risks. IFRI Centre for Energy, Paris
Doffman, Z. (2020). Warning : You must not download this dangerous Coronavirus map. Retrieved from www.forbes.com : https://www.forbes.com/sites/zakdoffman/2020/03/11/warning-you-must-not-download-this-dangerous-coronavirus-map/#4049aef83253
Du M (2018) Big data privacy-preserving in multi-access edge computing for heterogeneous internet of things. IEEE Communication Magazine 56(8):62–67. https://doi.org/10.1109/MCOM.2018.1701148
Dwork C, Roth A (2014) The algorithmic foundations of differential privacy. Foundations and Trends in Theoretical Computer Science, pp 211–407
Eldefrawy, K., Rattanavipanon, N., Tsudik, G. (2017). Fusing hybrid remote attestation with a formally verified microkernel: lessons learned. 2017 47th Annual IEEE/IFIP International Conference on Dependable Systems and Networks Workshop (DSN-W) (pp. 141-144). Denver, USA: IEEE. doi: https://doi.org/10.1109/DSN-W.2017.31
ENISA. (2019, 01 07). Shamoon Campaigns with Disttrack. (European Union) retrieved 08 04, 2019, from European Union Agency for cyber security: https://www.enisa.europa.eu/publications/info-notes/shamoon-campaigns-with-disttrack
Errabelly, R., Sha, K., Wei, W., Yang, T.A., Wang, Z. (2017). Edges: design of an edge layer security service to enhance internet of things security. First IEEE International Conference on Fog and Edge Computing (ICFEC 2017) . IEEE
Falliere, N., Liam O.M., Chien, E. (2011). Symantec Response - W32.Stuxnet Dossier. Symantec Labs, Symantec. Symantec. Retrieved from https://www.symantec.com/content/en/us/enterprise/media/security_response/whitepapers/w32_stuxnet_dossier.pdf
Fan, K., Li, J., Li, H., Liang, X., Shen, X., Yang, Y. (2012). ESLRAS: a lightweight RFID authentication scheme with high efficiency and strong security for IoT. 2012 4th International Conference on Intelligent Networking and Collaborative Systems (INCoS) (pp. 323-328). Bucharest: IEEE. doi: https://doi.org/10.1109/iNCoS.2012.48
Gentry, C. (2009). A fully Homomorphic encryption scheme. (Thesis) , 1-209. Stanford University
Glyer, C., Perez, D., Jones, S., Miller, S. (2020). This Is Not a Test: APT41 Initiates Global Intrusion Campaign Using Multiple Exploits Retrieved from www.fireeye.com : https:// www.fireeye.com /blog/threat-research/2020/03/apt41-initiates-global-intrusion-campaign-using-multiple-exploits.html
Glymin, E. (2017). Detailed Threat Analysis of Shamoon 2.0 Malware. Retrieved 08 04, 2019, from global secure solutions: https://globalsecuresolutions.com/detailed-threat-analysis-of-shamoon-2-0-malware/
Goodin, D. (2012). Discovery of new "zero-day" exploit links developers of Stuxnet, Flame. (arstechnica) retrieved 06 12, 2017, from https://arstechnica.com/security/2012/06/zero-day-exploit-links-stuxnet-flame/
Gope P, Amin R, Islam H, Kumar N, Bhalla VK (2018) Lightweight and privacy-preserving RFID authentication scheme for distributed IoT infrastructure with secure localisation services for the smart city environment. Futur Gener Comput Syst 83:629–637. https://doi.org/10.1016/j.future.2017.06.023
Gorman, S. (2009). FAA's Air-Traffic Networks Breached by Hackers. (the wall street journal) retrieved 06 12, 2017, from http://online.wsj.com/articles/SB124165272826193727
Guilherme, V., Peter, S. (2011). The Day of the Golden Jackal – The Next Tale in the Stuxnet Files: Duqu. McAfee. McAfee. Retrieved 06 09, 2017
Haddadi, H., Christophides, V., Teixeira, R., Cho, K., Suzuki, S., Perrig, A. (2018). Siotome: an edge-isp collaborative architecture for IoT security. 1st International Workshop on Security and Privacy for the Internet-of-Things (IoTSec) , (pp. 42–45). Florida, USA
Hsu R, Lee J, Quek T, Chen J (2018) Reconfigurable security: edge computing based framework for IoT. IEEE Netw 30(5):92–99
Hu, H., Han, W., Ahn, G., Zhao, Z. (2014). Flow guard: building robust firewalls for software-defined networks. 3rd Workshop on hot topics in software-defined networking. ACM
Huang, C., Wu, Z., Lin, S. (2019). The mobile edge computing (MEC)-based VANET data offloading using the staying-time-oriented k-hop away offloading agent. 2019 International Conference on Information Networking (pp. 357-362). Kuala Lumpur, Malaysia: IEEE
Jaber M, Imran MA, Tafazolli R, Tukmanov A (2016) 5G backhaul challenges and emerging research directions: a survey. IEEE Access 4:1743–1766. https://doi.org/10.1109/ACCESS.2016.2556011
Kaspersky Corp. (2011). Duqu: Steal Everything. (Kaspersky Labs) retrieved 05 09, 2017, from http://www.kaspersky.com/about/press/major_malware_outbreaks/duqu
Kaspersky Corp. (2015). The DuQu 2.0 Technical Details- The Mystery of DuQu 2.0 - Sophisticated Cyber Espionage Actor. Kaspersky Labs, research Labs. Kaspersky Labs
Kaspersky Labs. (2020, 07). Kaspersky ICS-CERT. (Kaspersky) retrieved 08 10, 2020, from https://ics-cert.kaspersky.com/
Kazemian, P., Chang, M., Zeng, H., Varghese, G., McKeown, N., Whyte, S. (2013). Real-time network policy checking using header space analysis. 10th USENIX Symposium on Networked Systems Design and Implementation (NSDI'13) (pp. 99-111). USENIX association. Retrieved from https://www.usenix.org/system/files/conference/nsdi13/nsdi13-final8.pdf
Kazemian, P., Varghese, G., McKeown, N. (2012). Header space analysis: static checking for networks. 9th USENIX Symposium on Networked Systems Design and Implementation (NSDI'12) (pp. 1-14). USENIX association
Khodashenas, Aznar, J., Legarrea, A., Ruiz, M., Siddiqui, S., Escalona, E., Figuerola, S. (2016). 5G network challenges and realisation insights. IEEE Xplore, 1–4. doi: https://doi.org/10.1109/ICTON.2016.7550539
Khurshid, A., Zou, X., Zhou, W., Caesar, M., Godfrey, P.B. (2013). Veriflow: verifying network-wide invariants in real-time. 10th USENIX Symposium on Networked Systems Design and Implementation (NSDI'13) (pp. 15-27). USENIX association
Kimani K, Oduol V, Langat K (2019) Cyber security challenges for IoT based smart grid networks. Int J Crit Infrastruct Prot 25:36–49. https://doi.org/10.1016/j.ijcip.2019.01.001
Kochman, B. (2020). How criminals are exploiting the coronavirus outbreak. Retrieved from www.law360.com : https://www.law360.com/cybersecurity-privacy/articles/1255130/how-cybercriminals-are-exploiting-the-coronavirus-outbreak
Kolias C, Kambourakis G, Stavrou A, Voas J (2017) DDoS in the IoT: Mirai and other botnets. Computer 50(7):80–84. https://doi.org/10.1109/MC.2017.201
Kreyenberg, H. (2019). The energy sector as target of cyber attacks . HornetSecurty: Security Information. Retrieved from https://www.hornetsecurity.com/data/downloads/reports/document-cybersecurity-special-energy-en.pdf
Kumagai J (2012) Virtual power plants, real power, 5 kw here and 100 kw there it all adds up
Kushner D (2013) The real story of Stuxnet. IEEE Spectrum Posted
Langill, J.T. (2014). Defending Against the Dragonfly Cyber Security Attacks . BELDEN. BELDEN. Retrieved 06 09, 2017
Langner, R., (2013). To Kill a Centrifuge - Technical Analysis of What Stuxnet's Creators tried to Achieve. The Langer group. Munich: the Langer group. Retrieved 06 11, 2017, from https://www.langner.com/wp-content/uploads/2017/03/to-kill-a-centrifuge.pdf
Lathrop AJ, Stanisz HM (2016) Hackers are after more than just data: will your company property policies respond when cyberattacks cause physical damage and shut down operations? Environmental Claims J 28(4):286–303. https://doi.org/10.1080/10406026.2016.1197653
Lee, R.M., Michael, J. A., Conway, T. (2016). Analysis of the Cyber Attack on the Ukrainian Power Grid Defense Use Case. SANS. Washington, DC: SANS. Retrieved 05 08, 2017, from https://ics.sans.org/media/E-ISAC_SANS_Ukraine_DUC_5.pdf
Leyden, J. (2012). Hack on Saudi Aramco hit 30,000 workstations, oil firm admits - First hacktivist-style assault to use malware? (TheRegister) retrieved 06 12, 2017, from http://www.theregister.co.uk/2012/08/29/saudi_aramco_malware_attack_analysis
Li, P., Liu, Y., Xin, H., Jiang, X. (2018). A robust distributed economic dispatch strategy of the virtual power plant under cyber-attacks. IEEE Transactions on Industrial Informatics, 4343-4352
Liu, J., Xiao, Y., Li, S., Liang, W., Chen, C.L.P. (2012). Cyber security and privacy issues in smart grids. IEEE COMMUNICATIONS SURVEYS & TUTORIALS, 14(4, fourth quarter)
Lu R, Heung K, Lashkari A, Ghorbani AA (2017) A lightweight privacy-preserving data aggregation scheme for fog computing-enhanced IoT. IEEE Access 5:3302–3312. https://doi.org/10.1109/ACCESS.2017.2677520
Mach P, Becavar Z (2017) Mobile edge computing a survey on architecture and computation offloading. IEEE Communications Surveys & Tutorials 19(3):1628–1656. https://doi.org/10.1109/COMST.2017.2682318
Markham T, Payne C (2001) Security at the network edge: a distributed firewall architecture. DARPA Information Surviv ability Conference and Exposition II, DISCEX'01 (pp. 279–286). IEEE, Anaheim
McElroy, D., Williams, C. (2012). Flame: world's most complex computer virus exposed. (the telegraph) retrieved 06 12, 2017, from http://www.telegraph.co.uk/news/worldnews/middleeast/iran/9295938/Flame-worlds-most-complex-computer-virus-exposed.html
Mcguinn MG (2004) Prioritising cyber vulnerabilities . Homeland Security, National Infrastructure Advisory Council. Homeland Security
McSherry, F., Talwar, K. (2007). Mechanism design via differential privacy. 48th Annual IEEE Symposium on Foundations of Computer Science (FOCS'07) (pp. 94-103). IEEE. doi: https://doi.org/10.1109/FOCS.2007.66
Miller, B., Rowe, D.C. (2012). A Survey of SCADA and Critical Infrastructure Incidents. Annual Conference on Research in Information Technology (pp. 51–56). New York, ISA: ACM
Mills, E. (2009). Report: Hackers have broken into the air traffic control mission-support systems of the U.S. Federal Aviation Administration several times in recent years. (ZDNet) retrieved 06 12, 2017, from http://www.zdnet.com/news/report-us-airtraffic-control-systems-hacked/300164
Montero D (2015) Virtualised security at the network edge: a user-centric approach. IEEE Commun Mag 53(4):176–186. https://doi.org/10.1109/MCOM.2015.7081092
Montero, D., Serral-Gracia, R. (2016). Offloading personal security applications to the network edge: A mobile user case scenario. 2016 International conference on wireless communication and Mobile computing . IEEE
Moore, D., Paxson, V., Savage, S., Shannon, C., Staniford, S., Weaver, N. (2003). Inside the slammer worm. (IEEE, Ed.) IEEE Computer and Security, 99(4), 33-39. Retrieved 06 15, 2017, from http://cseweb.ucsd.edu/~savage/papers/IEEESP03.pdf
Mukherjee, B., Neupane, R., Calyam, P. (2017). End to end IoT security middleware for cloud-fog communication. IEEE 4th International Conference on Cyber Security and Cloud Computing (pp. 151-156). New York, USA: IEEE. doi: https://doi.org/10.1109/CSCloud.2017.62
Nakashima, E., Miller, G., Tate, J. (2017, 06, 12). U.S., Israel developed Flame computer virus to slow Iranian nuclear efforts, officials say. (Washington post) retrieved 06 12, 2017, from https://www.washingtonpost.com/world/national-security/us-israel-developed-computer-virus-to-slow-iranian-nuclear-efforts-officials-say/2012/06/19/gJQA6xBPoV_story.html
Nakashima, E., Warrick, J. (2012). Stuxnet was work of U.S. and Israeli experts, officials say. (Washington post) retrieved 06 12, 2017, from https://www.washingtonpost.com/world/national-security/stuxnet-was-work-of-us-and-israeli-experts-officials-say/2012/06/01/gJQAlnEy6U_story.html
Naraine, R. (2010). Stuxnet attackers used 4 Windows zero-day exploits. (ZDNet) retrieved 06 12, 2017, from http://www.zdnet.com/blog/security/stuxnet-attackers-used-4-windows-zero-day-exploits/7347
Nelson, N. (2016). The Impact of Dragonfly Malware on Industrial Control Systems. SANS institute, SANS institute InfoSec Reading room. SANS. Retrieved 06 15, 2017, from https://www.sans.org/reading-room/whitepapers/ICS/impact-dragonfly-malware-industrial-control-systems-36672
NewYork Times. (2012). Aramco Says Cyberattack Was Aimed at Production. (the Newyork Times) retrieved 06 12, 2017, from http://www.nytimes.com/2012/12/10/business/global/saudi-aramco-says-hackers-took-aim-at-its-production.html
Nunes R, Pontes R, Guedes D (2014) Virtualised network isolation using software defined networks (SDN). 38th Annual IEEE Conference on Local Computer Networks (pp. 683–686). IEEE, Sydney
Panda. (2015). Critical Infrastructure. Panda security. Retrieved from www.pandasecurity.com/mediacenter/src/uploads/2018/10/1611-WP-CriticalInfrastructure-EN.pdf
Pei D, Salomaa A, Ding C (1996) Chinese remainder theorem: applications. Computing, Coding , Cryptography - World Scientific Forum
Perlroth, N. (201210, 2,3). In Cyberattack on Saudi Firm, U.S. Sees Iran Firing Back. (the Newyork Times) retrieved 06 12, 2017, from http://www.nytimes.com/2012/10/24/business/global/cyberattack-on-saudi-oil-firm-disquiets-us.html
Pop C, Antal M, Cioara T, Anghel I, Salomie I, Bertoncini C (2019) A fog computing enabled virtual power plant model for delivery of frequency restoration reserve services. Sensors, pp 1–20. https://doi.org/10.3390/s19214688
Poulsen, K. (2003). Slammer worm crashed Ohio nuke plant network. (SecurityFocus) retrieved 06 12, 2017, from http://www.securityfocus.com/news/6767
Poulsen, K. (2004). South Pole' cyberterrorist' hack wasn't the first. (TheRegister) retrieved 06 12, 2017, from http://www.theregister.co.uk/2004/08/19/south_pole_hack
Rausch, T., Dustdar, S. (2019). Edge intelligence: the convergence of humans, things, and a.I. 2019 IEEE International Conference on Cloud Engineering, IC2E (pp. 86-96). Prague, Chech Republic: IEEE
Razeghi, B., Voloshynovski, S. (2018). Privacy-preserving out-sourced media search using secure sparse ternary codes. 2018 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP) (pp. 1992-1996). Calgary: IEEE. doi: https://doi.org/10.1109/ICASSP.2018.8461862
Rene, M. (2015, 06, 22). Hackers successfully ground 1,400 passengers. (CNN) retrieved 06 12, 2017, from http://edition.cnn.com/2015/06/22/politics/lot-polish-airlines-hackers-ground-planes/index.html
Rennie, M. (2019). Virtual Power Plants: On the Edge or the in the cloud. Retrieved from linkedin.com
Roman R, Rios R, Onieva J, Lopez J (2018) The immune system for the internet of things using edge technologies. IEEE Internet of Things Journal, pp 1–8
Sanger, D.E. (2012). Obama Order Sped Up Wave of Cyberattacks Against Iran. (the Newyork Times) retrieved 06 12, 2017, from http://www.nytimes.com/2012/06/01/world/middleeast/obama-ordered-wave-of-cyberattacks-against-iran.html
Sha K, Alatrash N, Wang A (2017) A secure and efficient framework to read isolated smart grid devices. IEEE Transactions on Smart Grid 8(6):2519–2531. https://doi.org/10.1109/TSG.2016.2526045
Sha K, Wang S, Shi W (2010) Rd4: role differentiated cooperative deceptive data detection and filtering in vanets. IEEE Trans Veh Technol 59(3):1183–1190
Sha K, Wei W, Yang A, Shi W (2016) Security in the internet of things: opportunities and challenges. International conference on identification, information and knowledge in the Internet of things (pp. 512-518). IEEE, Beijing. https://doi.org/10.1109/IIKI.2016.35
Sha, K., Xi, Y., Shi, W, Schwiebert, L., Zhang, T. (2006). Adaptive privacy-preserving authentication in vehicular networks. 2006 First International Conference on Communications and Networking in China (pp. 1-8). Beijing, China: IEEE. doi: https://doi.org/10.1109/CHINACOM.2006.344746
Sha, K., Xu, C., Wang, Z. (2014). One-time symmetric key-based cloud supported secure smart meter reading. 2014 23rd International Conference on Computer Communication and Networks (ICCCN) (pp. 1-6). Shanghai: IEEE. doi: https://doi.org/10.1109/ICCCN.2014.6911854
Sha K, Yang AT, Wei W, Davari S (2020) A survey of edge computing-based designs for IoT security. Digital communication networks 6(2):195–202. https://doi.org/10.1016/j.dcan.2019.08.006
Sha, K., Zeadally, S. (2015). Data quality challenges in cyber-physical systems. Journal of Data and Information Quality (JDIQ), 6(2-3). Doi: https://doi.org/10.1145/2740965
Sharma, S., Chen, K. (2017). Privategraph: a cloud-centric system for spectral analysis of large encrypted graphs. 2017 IEEE 37th International Conference on Distributed Computing Systems (ICDCS) (pp. 2507-2510). Atlanta, GA: IEEE. doi: https://doi.org/10.1109/ICDCS.2017.189
Singh, A., Auluck, N., Rana, O.F., Jones, A.C., Nepal, S. (2017). Rt-sane: real-time security-aware scheduling on the network edge. Proceedings of the 10th International Conference on Utility and Cloud Computing. doi: https://doi.org/10.1145/3147213.3147216
sKyWiper Analysis Team. (2012). sKyWIper (a.k.a. Flame a.k.a. Flamer - A complex malware for targeted attacks. Budapest University of Technology and Economics, Department of Telecommunications. Budapest: Laboratory of Cryptography and System Security (CrySyS Lab). Retrieved 06 11, 2017, from http://www.bme.hu/
Sweeney L (2002) K-anonymity: a model for protecting privacy. Int J Uncertainty, Fuzziness and Knowledge-based Systems 10(5):557–570. https://doi.org/10.1142/S0218488502001648
Symantec Corp. (2009). Symantec global internet security threat report trends . Symantec
Symantec Corp. (2011). Internet security threat report . Symantec
Symantec Corp. (2014). Security Response - Dragonfly: Cyberespionage Attacks Against Energy Suppliers. Symantec Labs, Symantec Labs. Symantec. Retrieved 06 11, 2017
Symantec Corp. (2018). Shamoon: Destructive Threat Re-Emerges with New Sting in its Tail. (Symantec response team) retrieved 08 04, 2019, from Symantec: https://www.symantec.com/blogs/threat-intelligence/shamoon-destructive-threat-re-emerges-new-sting-its-tail
Symantec Crop. (2017). Shamoon: Multi-staged destructive attacks limited to specific targets . (Symantec Labs) retrieved 06 08, 2017, from https://www.symantec.com/connect/blogs/shamoon-multi-staged-destructive-attacks-limited-specific-targets
Tao X, Ota K, Dong M, Qi H, Li K (2017) Performance guaranteed computation offloading for mobile edge cloud computing. IEEE Wireless Communication Letters 6(6):774–777. https://doi.org/10.1109/LWC.2017.2740927
Thomson, L. (2013). Snowden: U.S. and Israel did create Stuxnet attack code . (TheRegister) retrieved 06 12, 2017, from http://www.theregister.co.uk/2013/07/08/snowden_us_israel_stuxnet
Tian L, Li J, Li W, Ramesh B, Cai Z (2019) Optimal contract-based mechanisms for online data trading markets. IEEE Internet Things J 6(5):7800–7810. https://doi.org/10.1109/JIOT.2019.2902528
Trend Micro. (2018). New Version of Disk-Wiping Shamoon/Disttrack Spotted What you need to know . (T. Micro, producer) retrieved 08 04, 2019, from trend Micro: https://www.trendmicro.com/vinfo/hk-en/security/news/cybercrime-and-digital-threats/new-version-of-disk-wiping-shamoon-disttrack-spotted-what-you-need-to-know
Tsai H (2012) Treat as a service: Virtualisations impact on cloud security. I.T . Professional 14(1):32–37. https://doi.org/10.1109/MITP.2011.117
Venkatachary SK, Prasad J, Samikannu R (2017) Economic impacts of cyber security in energy sector: a review. (IJEEP, Ed.). Int J Energy Econ Policy 7(5):250–262 Retrieved from www.econjournals.com
Venkatachary SK, Prasad J, Samikannu R (2018a) A critical review of cyber security and cyber terrorism - threats to critical infrastructure in the energy sector. International Journal of Critical Infrastructures 14(2):101–119
Venkatachary, S.K., Prasad, J., Samikannu, R. (2018b). Cyber security and cyber terrorism in energy sector - a review. Journal of Cyber Security Technology , 2(3–4), 111–130. doi: https://doi.org/10.1080/23742917.2018.1518057
Venkatachary SK, Prasad J, Samikannu R, Alagappan A, Andrews LJB (2020) Cybersecurity infrastructure challenges in IoT based virtual power plants. Journal of Statistics and Management Systems 23(2):263–276. https://doi.org/10.1080/09720510.2020.1724625
Wang Z, Sha K, Lv W (2013) Slight homomorphic signature for access controlling in cloud computing. Wirel Pers Commun 73(1):51–61. https://doi.org/10.1007/s11277-012-0977-8
Weber RH, Studer E (2016) Cybersecurity in the internet of things: legal aspects. Comput Law Secur Rev 32(5):715–728. https://doi.org/10.1016/j.clsr.2016.07.002
Wilhoit, K. (2013). Who's really attacking your ICS equipment? Retrieved 11 28, 2020, from www.trendmicro.com : https://www.trendmicro.com.tr/media/wp/whos-really-attacking-your-ics-equipment-whitepaper-en.pdf
Xi, Y., Sha, K., Shi, W., Schwiebert, L., Zhang, T. (2007). Enforcing privacy using symmetric key-set in vehicular networks. Eighth International Symposium on Autonomous Decentralized Systems (ISADS'07) (pp. 344-351). Sedona: IEEE
Yaseen, Q., Al-Balas, F., Jararweh, Y., Al-Ayyoub. (2016). A FOG computing-based system for selective forwarding detection in mobile wireless sensor networks. 2016 IEEEE 1st International Workshop on Foundations and Applications of Self* Systems (pp. 256-262). Augsburg: IEEE doi: https://doi.org/10.1109/FAS-W.2016.60
Yin C, Zhu Y, Fei J, He X (2017) A deep learning approach for intrusion detection using recurrent neural networks. IEEE Access 5:21954–21961. https://doi.org/10.1109/ACCESS.2017.2762418
Zaho, Q., Gerla, M. (2019). Energy efficiency enhancement in 5G mobile networks. IEEE 20th International Symposium on a world of wireless mobile and multimedia networks (pp. 1-3). Washington, USA: IEEE explore
Zakhmatov, V.D., Glushkova, V.V., Kryazhich, O.A. (2011). Explosion , Which was not. Retrieved from ogas.kiev.ua: http://ogas.kiev.ua/perspective/vzryv-kotorogo-ne-bylo-581
Zhou, Z., Chen, X., Li, E., Zeng, L., Luo, K., Zhang, J. (2019). Edge intelligence: paving the last mile of artificial intelligence with edge computing. Proc. IEEE, 1738-1762
Download references
Author information
Authors and affiliations.
Grant Thornton, Plot 50370, Acumen Park, Fairgrounds, Gaborone, Botswana
Sampath Kumar Venkatachary
Department of Network and Infrastructure Management, Faculty of Engineering and Technology, Botho University, Gaborone, Botswana
Annamalai Alagappan
Department of Information Technology, Faculty of Engineering and Technology, Botho University, Gaborone, Botswana
Leo John Baptist Andrews
You can also search for this author in PubMed Google Scholar
Contributions
The author(s) read and approved the final manuscript.
Corresponding author
Correspondence to Sampath Kumar Venkatachary .
Ethics declarations
Competing interests.
The authors declare that they have no competing interests.
Additional information
Publisher’s note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Cite this article.
Venkatachary, S.K., Alagappan, A. & Andrews, L.J.B. Cybersecurity challenges in energy sector (virtual power plants) - can edge computing principles be applied to enhance security?. Energy Inform 4 , 5 (2021). https://doi.org/10.1186/s42162-021-00139-7
Download citation
Received : 01 December 2020
Accepted : 11 March 2021
Published : 31 March 2021
DOI : https://doi.org/10.1186/s42162-021-00139-7
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Edge computing
- Virtual power plants (VPP)
- Distributed energy resource (DER)
- Security architecture
- Authentication and authorisation
Interactive Power Prediction Model for Virtual Power Plant Based on Wave-Attention Network
Ieee account.
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
News & Updates
What are states doing to make virtual power plants a reality.
By: Brian Lips, Senior Policy Project Manager
Virtual Power Plants (VPPs) are attracting a lot of attention at the moment. Our upcoming 50 States of Grid Modernization Q1 2024 report documents numerous policy and program actions taken by several states, and our very own Autumn Proudlove moderated a session on VPPs at the 2024 North Carolina State Energy Conference . Additionally, the U.S. Department of Energy published an extensive report on VPPs last year, and even mainstream media is publishing articles on their potential. But what exactly are VPPs, and what are states doing to enable their development?
VPPs can incorporate a variety of technologies with different characteristics, leading to the challenge of adequately defining them. However, all VPPs share the common elements of quantity and controllability. At their heart, VPPs involve the aggregation of a large number of distributed energy resources (DERs), which can be collectively controlled to benefit the grid and potentially obviate a utility’s need to activate a traditional peaking power plant.
The Smart Electric Power Alliance (SEPA) groups VPPs into three general categories: Supply VPPs, Demand VPPs, and Mixed Asset VPPs. Supply VPPs involve electricity-generating DERs, such as solar-plus-storage systems, which can be aggregated and controlled as a single resource when needed. Demand VPPs build off traditional demand response programs by aggregating curtailable load at a scale that can have a meaningful impact on the grid. Mixed Asset VPPs include a mix of both supply and demand resources.
While the benefits of VPPs are clear, the pathway to greater deployment is not. However, state policymakers are currently testing a variety of methods to encourage their development. Common approaches include a mix of mandates for utilities to procure energy from VPPs, incentives for utility customers to deploy DERs and participate in utility programs, and market access reforms to allow third-party aggregators to participate. Different varieties of these approaches have been considered by several states and utilities over the past year.
Recent Notable Virtual Power Plant Actions
The California Energy Commission (CEC) approved a new incentive program for VPPs in July 2023. The Demand Side Grid Support (DSGS) program compensates eligible customers for upfront capacity commitments and per-unit reductions in net energy load during extreme events achieved through reduced usage, backup generation, or both. Third-party battery providers, publicly-owned utilities, and Community Choice Aggregators (CCAs) are eligible to serve as VPP aggregators. At a minimum, each individual customer site participating in the program must have an operational stationary battery system capable of discharging at least 1 kW for at least 2 hours. Incentive payments will be made to VPP aggregators based on the demonstrated battery capacity of an aggregated VPP. VPP aggregators will then allocate incentive payments between the VPP aggregator and its participants based on their own contractual agreement.
California lawmakers are also currently considering legislation to stimulate the market for VPPs. S.B. 1305 requires the California Public Utilities Commission to estimate the resource potential of VPPs in the state, and to develop procurement targets for each utility to be achieved by December 31, 2028 and December 31, 2033.
The Colorado Public Utilities Commission opened a new proceeding in September 2023 to explore third-party implementation of virtual power plant pilots in Xcel Energy’s service area. The Commission issued a decision in April 2024 requiring Xcel to issue an RFP for a distributed energy management system (DERMS), which would then be used to manage a VPP. The Commission stopped short of directing Xcel to file a VPP tariff, but speaks of their merit and suggests that Xcel should propose separate “prosumer tariffs” for residential and non-residential customers, including different aggregation capacities.
A stipulation agreed to by the Public Interest Advocacy Staff and Georgia Power in its 2023 Integrated Resource Plan Update proceeding commits the utility to developing a residential and small commercial solar and battery storage pilot program that will provide grid reliability and capacity benefits. Georgia Power will work with interested stakeholders to develop the program and will file it for approval with its 2025 Integrated Resource Plan.
In December 2023, the Hawaii Public Utilities Commission approved a new VPP program for the Hawaiian Electric Companies (HECO). The Bring-Your-Own-Device (BYOD) will replace HECO’s Battery Bonus Program and will provide varying levels of incentives based on the value of the grid services provided. The program will only allow energy storage systems at first, but may be expanded in the future to include other DERs.
The Maryland General Assembly enacted a bill in April 2024, which opens the door to VPPs in the state. H.B. 1256 requires investor-owned utilities in the state to develop pilot programs to compensate owners and aggregators of DERs for distribution system support services. The programs must be filed for approval with the Public Service Commission by July 1, 2025.
Michigan lawmakers introduced legislation in 2024 related to VPPs. S.B. 773 requires the Public Service Commission to develop requirements for programs that would allow behind-the-meter generation and energy storage owners to be compensated for services they provide to the distribution system, including through aggregators of DERs. Utilities would then need to file applications for these programs during their rate cases.
Massachusetts
In January 2024, the state’s three investor-owned utilities filed their Electric Sector Modernization Plans (ESMPs) with the Commission for approval. The three ESMPs include plans to invest in DERMS and customer programs to advance VPPs.
In December 2023, Public Service Electric & Gas (PSEG) New Jersey filed a petition for a VPP demonstration as part of its energy efficiency and peak demand reduction programs. The VPP demonstration will network behind-the-meter energy storage to provide grid services. The petition contains an energy storage incentive of $8,000 to $16,000 for 8 kW energy storage systems. Battery costs over the incentive amount would be eligible for on-bill repayments to PSEG.
In April 2024, the Governor announced a new proceeding within the Public Service Commission to “develop a comprehensive New York Grid of the Future plan that establishes targets for the deployment of flexible resources such as virtual power plants and identifies the utility investments needed to enable the grid of the future.”
North Carolina
In January 2024, the North Carolina Utilities Commission approved Duke Energy’s application for PowerPair, a solar-plus-storage incentive program. Through the program, Duke Energy Carolinas and Duke Energy Progress will each provide incentives of $0.36/Watt for 30 MW of solar systems, plus $500/kWh for paired energy storage devices. Participants will be divided into two cohorts. One cohort will be on the utilities’ new Solar Choice Tariffs, which is coupled with time-of-use rates. These customers will retain complete control of their energy storage devices, but the time-of-use rates will incentivize them to configure them to provide energy during peak times. The other cohort will be on the utilities’ Bridge Tariff, which does not use time-of-use rates. These customers will grant full control of their systems to the utility to use as part of a VPP in exchange for an additional monthly incentive.
Lawmakers in Virginia passed a pair of bills related to VPPs in 2024. H.B. 1062 and S.B. 271 clarify that customer-generators may participate in demand response, energy efficiency, or peak reduction programs from dispatch of on-site battery service, provided that the compensation received is in exchange for a distinct service that is not already compensated by net metering.
In November 2023, Avista Utilities filed a proposed tariff for the Spokane Connected Communities Pilot Program. The program will provide a variety of incentives to different customer classes for a mix of customer products including smart thermostats, residential energy storage batteries, building control systems, and heat pumps.
Looking Ahead
As trendy as VPPs are today, we are still in the early stages of their development. Wider electrification and the growing body of connected devices, in addition to the further proliferation of solar-plus-storage, will unlock more potential flavors of VPPs. Overtime, technological advances will also open the door to new policy solutions to better harness their benefits. With policymakers, utilities, and private enterprise working collaboratively to find solutions that work for a given state’s unique circumstances, we will surely see continued growth of VPPs.
Upcoming Events
The open sustainability policy summit.
NCCETC’s Executive Director, Steve Kalland, will be speaking at the all new Open Sustainability Policy Summit May 2-3 in Washington, DC. Hear from him during the “Node Collective’s Open Data […]
Sustainable Fleet Technology Webinar Series: Hydrogen: Considerations in Fleet Use
This webinar will focus on hydrogen as a transportation fleet. Come listen to subject matter experts discuss the logistics you should consider when using hydrogen as a fuel for your […]
Get Involved
Newsletter signup, take action.

IMAGES
VIDEO
COMMENTS
This thesis was prepared at the Center for Electric Technology (CET), Department of Electrical Engineering of Technical University of Denmark (DTU) in partial fulfillment of the requirements for the Ph. D degree in Denmark. It was financed by the Danish ... C Virtual Power Plant Related Researches ...
The repository is a part of the thesis about the system for Negawatt Virtual Power Plant, which heads up groups of heat pumps. Virtual Power Plant is a concept of connected power plants and regular users of electric power. The main aim of such a system is to take control over dependent installations in order to maintain good collaborations with ...
power plants, power system operators are facing difficulties in frequency control and other services which are essential to system reliability [2]. For example, it is possible to integrate 20% renewable energy into California electric system. However, the frequency regulation capacity needs to increase by 170 MW to 250 MW for ―Up Regulation ...
CHARACTERISATION OF VIRTUAL POWER PLANTS A thesis submitted to the University of Manchester for the degree of PhD in the Faculty of Engineering and Physical Sciences 2010 Guy Newman School of Electrical and Electronic Engineering View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by OpenGrey Repository
Chapter 4 of this thesis is published as [X. Lu, J. Qiu, C. Zhang, G. Lei and J. Zhu. Assembly and Competition for Virtual Power Plants with Multiple ESPs Through a "Recruitment-Participation" Approach. IEEE Transactions on Power Systems, 39(2), 4382-4396]. I designed the study, analyzed the data, and wrote the drafts.
To address the model inaccuracy and uncertainty of virtual power plants (VPPs), a model-free economic dispatch approach for multiple VPPs is studied in this article, which does not rely on an accurate environmental model. An adversarial safe reinforcement learning approach is proposed, which promotes the safety of the actions and makes the model robust to deviations between the training and ...
Recently, the integration of distributed generation and energy systems has been associated with new approaches to plant operations. As a result, it is becoming increasingly important to improve management skills related to distributed generation and demand aggregation through different types of virtual power plants (VPPs). It is also important to leverage their ability to participate in ...
The need for future sustainable energy and better transmission efficiency has advocated the large-scale integration of distributed energy resources (DER) in the utility network. The high penetration of DERs such as solar PV can potentially result in serious issues such as reverse power flow, voltage fluctuations, and utility revenue loss. The concept of a virtual power plant (VPP) can be a ...
In this thesis, we build a virtual power plant model and use the concept of demand response and time of use pricing to control the distributed energy resources, such as battery energy storage system, to maximize the profits. A demand response contract is designed and different factors are taken into account in operation scheduling.
Mechanism Design for Virtual Power Plant with Independent Distributed Generators Thesis by Al ya Kulmukhanova In Partial Ful llment of the Requirements For the Degree of Masters of Science King Abdullah University of Science and Technology Thuwal, Kingdom of Saudi Arabia May, 2018. 2
In the process of decentralization, local energy markets are forming at various places. A virtual power plant (VPP) is a by-product of this digitalization capitalizing on the opportunity to further promote renewable resources, demand-side flexibility, and sector coupling. A VPP enables resilient operation of power system while assembling small ...
and Virtual Power Plants: Barriers and Solutions Master Thesis Sustainable Development - Energy and Resources Tomas Olejnczak 0357022 Date : 26-03-2011 ... In 1.6, an outline of the thesis is presented. 1.1 Background The transition from conventional to renewable energy sources is on-going. In 2008, the EU
Virtual Power Plants (VPPs) aggregate a group of small/medium distributed supply-side energy resources (DERs), such as PV, wind, electric generators, and even demand side response, and control this potential net supply, such that they act as a single power plant for grid operations and energy trading.
A Virtual Power Plant (VPP) is a practical concept that aggregates various Renewable Energy Sources (RESs) to improve energy management efficiency and facilitate energy trading. Operation scheduling for all energy components in VPPs plays a vital role from an energy management perspective. Technical and economic constraints and uncertainties ...
This thesis presents definitions and types of Virtual Power Plants (VPP), then developing control through numerical simulation. The thesis proposes three DG controls namely Basic Autocontrol System (BAS), Smart Autocontrol System (SAS) and Tracking Efficiency Autocontrol System (TEAS). The BAS controls the DG output power with the objective to ...
Virtual power plants represent the most immediate future of electricity generation, as they allow for intelligent consumption of energy in a distributed environment through the optimal management of demand and power generation. This means that users produce and consume their own energy, which leads to more active consumer participation in ...
Student thesis: Phd. ... One of the techniques for considering the impacts of thesedevices is the Virtual Power Plant (VPP).The VPP is the aggregation of all the Distributed Generation (DG) connected into thenetwork up to and including the connection voltage of the VPP, such that thecumulative power up the voltage levels can be seen in the ...
Huang, H. Economic Dispatch of Virtual Power Plant Considering Demand Response Uncertainty and Conditional Risk. Ph.D. Thesis, Wuhan University, Wuhan, China, 2018. [Google Scholar] Liu, X. Research on the Economy Dispatch and Optimal Allocation of a Virtual Power Plant. Master's Thesis, Hefei Polytechnic University, Hefei, China, 2020.
Distributed generators (D.G.'s) enable us to generate, supply and be self-reliant on power while also allows us to supply power to meet the demand through virtual power plants. The virtual power plants also help us analyse, control, optimise, and help bridge the gap of demand and supply in these vast energy requirements. With this also comes challenges associated with securing physical ...
Virtual power plant technology has emerged as a crucial technical solution for addressing the challenges related to scheduling of new energy and distributed power grids. However, the interactive power characteristic of virtual power plant is affected by the power generator, renewable energy and load, which results in the characteristics of non-linearity, time series coupling and time variation ...
Virtual power plants (VPPs) can enhance reliability and efficiency of power systems with a high share of renewables. However, their adoption largely ... This thesis is the original work by Saidur Rahman. The results that are presented in Chapter 4 of this thesis are based on a conference publication
Virtual Power Plants (VPPs) are attracting a lot of attention at the moment. Our upcoming 50 States of Grid Modernization Q1 2024 report documents numerous policy and program actions taken by several states, and our very own Autumn Proudlove moderated a session on VPPs at the 2024 North Carolina State Energy Conference.
Y ou, S. Developing Virtual Power Plant for Optimized Distributed Energy Resources Operation and Integration. Ph.D. Thesis, Ph.D. Thesis, T echnical University of Denmark, Kgs.
Therefore, it is believed VPP deployment will have far-reaching positive consequences for grid operations and may provide a robust pathway to high penetrations of renewables on US power systems. In this report, we design VPPs to provide a range of grid-support services and demonstrate one VPP which simultaneously provides bulk-system energy and ...