
How To Write A Research Paper
Step-By-Step Tutorial With Examples + FREE Template
By: Derek Jansen (MBA) | Expert Reviewer: Dr Eunice Rautenbach | March 2024
For many students, crafting a strong research paper from scratch can feel like a daunting task – and rightly so! In this post, we’ll unpack what a research paper is, what it needs to do , and how to write one – in three easy steps. 🙂
Overview: Writing A Research Paper
What (exactly) is a research paper.
- How to write a research paper
- Stage 1 : Topic & literature search
- Stage 2 : Structure & outline
- Stage 3 : Iterative writing
- Key takeaways
Let’s start by asking the most important question, “ What is a research paper? ”.
Simply put, a research paper is a scholarly written work where the writer (that’s you!) answers a specific question (this is called a research question ) through evidence-based arguments . Evidence-based is the keyword here. In other words, a research paper is different from an essay or other writing assignments that draw from the writer’s personal opinions or experiences. With a research paper, it’s all about building your arguments based on evidence (we’ll talk more about that evidence a little later).
Now, it’s worth noting that there are many different types of research papers , including analytical papers (the type I just described), argumentative papers, and interpretative papers. Here, we’ll focus on analytical papers , as these are some of the most common – but if you’re keen to learn about other types of research papers, be sure to check out the rest of the blog .
With that basic foundation laid, let’s get down to business and look at how to write a research paper .

Overview: The 3-Stage Process
While there are, of course, many potential approaches you can take to write a research paper, there are typically three stages to the writing process. So, in this tutorial, we’ll present a straightforward three-step process that we use when working with students at Grad Coach.
These three steps are:
- Finding a research topic and reviewing the existing literature
- Developing a provisional structure and outline for your paper, and
- Writing up your initial draft and then refining it iteratively
Let’s dig into each of these.
Need a helping hand?
Step 1: Find a topic and review the literature
As we mentioned earlier, in a research paper, you, as the researcher, will try to answer a question . More specifically, that’s called a research question , and it sets the direction of your entire paper. What’s important to understand though is that you’ll need to answer that research question with the help of high-quality sources – for example, journal articles, government reports, case studies, and so on. We’ll circle back to this in a minute.
The first stage of the research process is deciding on what your research question will be and then reviewing the existing literature (in other words, past studies and papers) to see what they say about that specific research question. In some cases, your professor may provide you with a predetermined research question (or set of questions). However, in many cases, you’ll need to find your own research question within a certain topic area.
Finding a strong research question hinges on identifying a meaningful research gap – in other words, an area that’s lacking in existing research. There’s a lot to unpack here, so if you wanna learn more, check out the plain-language explainer video below.
Once you’ve figured out which question (or questions) you’ll attempt to answer in your research paper, you’ll need to do a deep dive into the existing literature – this is called a “ literature search ”. Again, there are many ways to go about this, but your most likely starting point will be Google Scholar .
If you’re new to Google Scholar, think of it as Google for the academic world. You can start by simply entering a few different keywords that are relevant to your research question and it will then present a host of articles for you to review. What you want to pay close attention to here is the number of citations for each paper – the more citations a paper has, the more credible it is (generally speaking – there are some exceptions, of course).
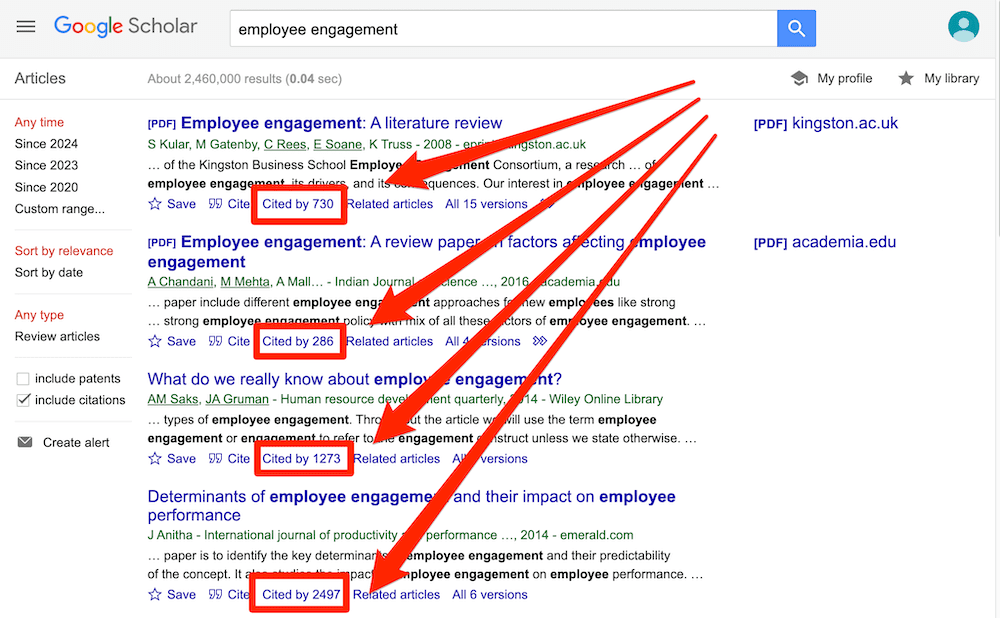
Ideally, what you’re looking for are well-cited papers that are highly relevant to your topic. That said, keep in mind that citations are a cumulative metric , so older papers will often have more citations than newer papers – just because they’ve been around for longer. So, don’t fixate on this metric in isolation – relevance and recency are also very important.
Beyond Google Scholar, you’ll also definitely want to check out academic databases and aggregators such as Science Direct, PubMed, JStor and so on. These will often overlap with the results that you find in Google Scholar, but they can also reveal some hidden gems – so, be sure to check them out.
Once you’ve worked your way through all the literature, you’ll want to catalogue all this information in some sort of spreadsheet so that you can easily recall who said what, when and within what context. If you’d like, we’ve got a free literature spreadsheet that helps you do exactly that.

Step 2: Develop a structure and outline
With your research question pinned down and your literature digested and catalogued, it’s time to move on to planning your actual research paper .
It might sound obvious, but it’s really important to have some sort of rough outline in place before you start writing your paper. So often, we see students eagerly rushing into the writing phase, only to land up with a disjointed research paper that rambles on in multiple
Now, the secret here is to not get caught up in the fine details . Realistically, all you need at this stage is a bullet-point list that describes (in broad strokes) what you’ll discuss and in what order. It’s also useful to remember that you’re not glued to this outline – in all likelihood, you’ll chop and change some sections once you start writing, and that’s perfectly okay. What’s important is that you have some sort of roadmap in place from the start.

At this stage you might be wondering, “ But how should I structure my research paper? ”. Well, there’s no one-size-fits-all solution here, but in general, a research paper will consist of a few relatively standardised components:
- Introduction
- Literature review
- Methodology
Let’s take a look at each of these.
First up is the introduction section . As the name suggests, the purpose of the introduction is to set the scene for your research paper. There are usually (at least) four ingredients that go into this section – these are the background to the topic, the research problem and resultant research question , and the justification or rationale. If you’re interested, the video below unpacks the introduction section in more detail.
The next section of your research paper will typically be your literature review . Remember all that literature you worked through earlier? Well, this is where you’ll present your interpretation of all that content . You’ll do this by writing about recent trends, developments, and arguments within the literature – but more specifically, those that are relevant to your research question . The literature review can oftentimes seem a little daunting, even to seasoned researchers, so be sure to check out our extensive collection of literature review content here .
With the introduction and lit review out of the way, the next section of your paper is the research methodology . In a nutshell, the methodology section should describe to your reader what you did (beyond just reviewing the existing literature) to answer your research question. For example, what data did you collect, how did you collect that data, how did you analyse that data and so on? For each choice, you’ll also need to justify why you chose to do it that way, and what the strengths and weaknesses of your approach were.
Now, it’s worth mentioning that for some research papers, this aspect of the project may be a lot simpler . For example, you may only need to draw on secondary sources (in other words, existing data sets). In some cases, you may just be asked to draw your conclusions from the literature search itself (in other words, there may be no data analysis at all). But, if you are required to collect and analyse data, you’ll need to pay a lot of attention to the methodology section. The video below provides an example of what the methodology section might look like.
By this stage of your paper, you will have explained what your research question is, what the existing literature has to say about that question, and how you analysed additional data to try to answer your question. So, the natural next step is to present your analysis of that data . This section is usually called the “results” or “analysis” section and this is where you’ll showcase your findings.
Depending on your school’s requirements, you may need to present and interpret the data in one section – or you might split the presentation and the interpretation into two sections. In the latter case, your “results” section will just describe the data, and the “discussion” is where you’ll interpret that data and explicitly link your analysis back to your research question. If you’re not sure which approach to take, check in with your professor or take a look at past papers to see what the norms are for your programme.
Alright – once you’ve presented and discussed your results, it’s time to wrap it up . This usually takes the form of the “ conclusion ” section. In the conclusion, you’ll need to highlight the key takeaways from your study and close the loop by explicitly answering your research question. Again, the exact requirements here will vary depending on your programme (and you may not even need a conclusion section at all) – so be sure to check with your professor if you’re unsure.
Step 3: Write and refine
Finally, it’s time to get writing. All too often though, students hit a brick wall right about here… So, how do you avoid this happening to you?
Well, there’s a lot to be said when it comes to writing a research paper (or any sort of academic piece), but we’ll share three practical tips to help you get started.
First and foremost , it’s essential to approach your writing as an iterative process. In other words, you need to start with a really messy first draft and then polish it over multiple rounds of editing. Don’t waste your time trying to write a perfect research paper in one go. Instead, take the pressure off yourself by adopting an iterative approach.
Secondly , it’s important to always lean towards critical writing , rather than descriptive writing. What does this mean? Well, at the simplest level, descriptive writing focuses on the “ what ”, while critical writing digs into the “ so what ” – in other words, the implications . If you’re not familiar with these two types of writing, don’t worry! You can find a plain-language explanation here.
Last but not least, you’ll need to get your referencing right. Specifically, you’ll need to provide credible, correctly formatted citations for the statements you make. We see students making referencing mistakes all the time and it costs them dearly. The good news is that you can easily avoid this by using a simple reference manager . If you don’t have one, check out our video about Mendeley, an easy (and free) reference management tool that you can start using today.
Recap: Key Takeaways
We’ve covered a lot of ground here. To recap, the three steps to writing a high-quality research paper are:
- To choose a research question and review the literature
- To plan your paper structure and draft an outline
- To take an iterative approach to writing, focusing on critical writing and strong referencing
Remember, this is just a b ig-picture overview of the research paper development process and there’s a lot more nuance to unpack. So, be sure to grab a copy of our free research paper template to learn more about how to write a research paper.
You Might Also Like:

Submit a Comment Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
- Print Friendly
- How to write a research paper
Last updated
11 January 2024
Reviewed by
With proper planning, knowledge, and framework, completing a research paper can be a fulfilling and exciting experience.
Though it might initially sound slightly intimidating, this guide will help you embrace the challenge.
By documenting your findings, you can inspire others and make a difference in your field. Here's how you can make your research paper unique and comprehensive.
- What is a research paper?
Research papers allow you to demonstrate your knowledge and understanding of a particular topic. These papers are usually lengthier and more detailed than typical essays, requiring deeper insight into the chosen topic.
To write a research paper, you must first choose a topic that interests you and is relevant to the field of study. Once you’ve selected your topic, gathering as many relevant resources as possible, including books, scholarly articles, credible websites, and other academic materials, is essential. You must then read and analyze these sources, summarizing their key points and identifying gaps in the current research.
You can formulate your ideas and opinions once you thoroughly understand the existing research. To get there might involve conducting original research, gathering data, or analyzing existing data sets. It could also involve presenting an original argument or interpretation of the existing research.
Writing a successful research paper involves presenting your findings clearly and engagingly, which might involve using charts, graphs, or other visual aids to present your data and using concise language to explain your findings. You must also ensure your paper adheres to relevant academic formatting guidelines, including proper citations and references.
Overall, writing a research paper requires a significant amount of time, effort, and attention to detail. However, it is also an enriching experience that allows you to delve deeply into a subject that interests you and contribute to the existing body of knowledge in your chosen field.
- How long should a research paper be?
Research papers are deep dives into a topic. Therefore, they tend to be longer pieces of work than essays or opinion pieces.
However, a suitable length depends on the complexity of the topic and your level of expertise. For instance, are you a first-year college student or an experienced professional?
Also, remember that the best research papers provide valuable information for the benefit of others. Therefore, the quality of information matters most, not necessarily the length. Being concise is valuable.
Following these best practice steps will help keep your process simple and productive:
1. Gaining a deep understanding of any expectations
Before diving into your intended topic or beginning the research phase, take some time to orient yourself. Suppose there’s a specific topic assigned to you. In that case, it’s essential to deeply understand the question and organize your planning and approach in response. Pay attention to the key requirements and ensure you align your writing accordingly.
This preparation step entails
Deeply understanding the task or assignment
Being clear about the expected format and length
Familiarizing yourself with the citation and referencing requirements
Understanding any defined limits for your research contribution
Where applicable, speaking to your professor or research supervisor for further clarification
2. Choose your research topic
Select a research topic that aligns with both your interests and available resources. Ideally, focus on a field where you possess significant experience and analytical skills. In crafting your research paper, it's crucial to go beyond summarizing existing data and contribute fresh insights to the chosen area.
Consider narrowing your focus to a specific aspect of the topic. For example, if exploring the link between technology and mental health, delve into how social media use during the pandemic impacts the well-being of college students. Conducting interviews and surveys with students could provide firsthand data and unique perspectives, adding substantial value to the existing knowledge.
When finalizing your topic, adhere to legal and ethical norms in the relevant area (this ensures the integrity of your research, protects participants' rights, upholds intellectual property standards, and ensures transparency and accountability). Following these principles not only maintains the credibility of your work but also builds trust within your academic or professional community.
For instance, in writing about medical research, consider legal and ethical norms , including patient confidentiality laws and informed consent requirements. Similarly, if analyzing user data on social media platforms, be mindful of data privacy regulations, ensuring compliance with laws governing personal information collection and use. Aligning with legal and ethical standards not only avoids potential issues but also underscores the responsible conduct of your research.
3. Gather preliminary research
Once you’ve landed on your topic, it’s time to explore it further. You’ll want to discover more about available resources and existing research relevant to your assignment at this stage.
This exploratory phase is vital as you may discover issues with your original idea or realize you have insufficient resources to explore the topic effectively. This key bit of groundwork allows you to redirect your research topic in a different, more feasible, or more relevant direction if necessary.
Spending ample time at this stage ensures you gather everything you need, learn as much as you can about the topic, and discover gaps where the topic has yet to be sufficiently covered, offering an opportunity to research it further.
4. Define your research question
To produce a well-structured and focused paper, it is imperative to formulate a clear and precise research question that will guide your work. Your research question must be informed by the existing literature and tailored to the scope and objectives of your project. By refining your focus, you can produce a thoughtful and engaging paper that effectively communicates your ideas to your readers.
5. Write a thesis statement
A thesis statement is a one-to-two-sentence summary of your research paper's main argument or direction. It serves as an overall guide to summarize the overall intent of the research paper for you and anyone wanting to know more about the research.
A strong thesis statement is:
Concise and clear: Explain your case in simple sentences (avoid covering multiple ideas). It might help to think of this section as an elevator pitch.
Specific: Ensure that there is no ambiguity in your statement and that your summary covers the points argued in the paper.
Debatable: A thesis statement puts forward a specific argument––it is not merely a statement but a debatable point that can be analyzed and discussed.
Here are three thesis statement examples from different disciplines:
Psychology thesis example: "We're studying adults aged 25-40 to see if taking short breaks for mindfulness can help with stress. Our goal is to find practical ways to manage anxiety better."
Environmental science thesis example: "This research paper looks into how having more city parks might make the air cleaner and keep people healthier. I want to find out if more green spaces means breathing fewer carcinogens in big cities."
UX research thesis example: "This study focuses on improving mobile banking for older adults using ethnographic research, eye-tracking analysis, and interactive prototyping. We investigate the usefulness of eye-tracking analysis with older individuals, aiming to spark debate and offer fresh perspectives on UX design and digital inclusivity for the aging population."
6. Conduct in-depth research
A research paper doesn’t just include research that you’ve uncovered from other papers and studies but your fresh insights, too. You will seek to become an expert on your topic––understanding the nuances in the current leading theories. You will analyze existing research and add your thinking and discoveries. It's crucial to conduct well-designed research that is rigorous, robust, and based on reliable sources. Suppose a research paper lacks evidence or is biased. In that case, it won't benefit the academic community or the general public. Therefore, examining the topic thoroughly and furthering its understanding through high-quality research is essential. That usually means conducting new research. Depending on the area under investigation, you may conduct surveys, interviews, diary studies , or observational research to uncover new insights or bolster current claims.
7. Determine supporting evidence
Not every piece of research you’ve discovered will be relevant to your research paper. It’s important to categorize the most meaningful evidence to include alongside your discoveries. It's important to include evidence that doesn't support your claims to avoid exclusion bias and ensure a fair research paper.
8. Write a research paper outline
Before diving in and writing the whole paper, start with an outline. It will help you to see if more research is needed, and it will provide a framework by which to write a more compelling paper. Your supervisor may even request an outline to approve before beginning to write the first draft of the full paper. An outline will include your topic, thesis statement, key headings, short summaries of the research, and your arguments.
9. Write your first draft
Once you feel confident about your outline and sources, it’s time to write your first draft. While penning a long piece of content can be intimidating, if you’ve laid the groundwork, you will have a structure to help you move steadily through each section. To keep up motivation and inspiration, it’s often best to keep the pace quick. Stopping for long periods can interrupt your flow and make jumping back in harder than writing when things are fresh in your mind.
10. Cite your sources correctly
It's always a good practice to give credit where it's due, and the same goes for citing any works that have influenced your paper. Building your arguments on credible references adds value and authenticity to your research. In the formatting guidelines section, you’ll find an overview of different citation styles (MLA, CMOS, or APA), which will help you meet any publishing or academic requirements and strengthen your paper's credibility. It is essential to follow the guidelines provided by your school or the publication you are submitting to ensure the accuracy and relevance of your citations.
11. Ensure your work is original
It is crucial to ensure the originality of your paper, as plagiarism can lead to serious consequences. To avoid plagiarism, you should use proper paraphrasing and quoting techniques. Paraphrasing is rewriting a text in your own words while maintaining the original meaning. Quoting involves directly citing the source. Giving credit to the original author or source is essential whenever you borrow their ideas or words. You can also use plagiarism detection tools such as Scribbr or Grammarly to check the originality of your paper. These tools compare your draft writing to a vast database of online sources. If you find any accidental plagiarism, you should correct it immediately by rephrasing or citing the source.
12. Revise, edit, and proofread
One of the essential qualities of excellent writers is their ability to understand the importance of editing and proofreading. Even though it's tempting to call it a day once you've finished your writing, editing your work can significantly improve its quality. It's natural to overlook the weaker areas when you've just finished writing a paper. Therefore, it's best to take a break of a day or two, or even up to a week, to refresh your mind. This way, you can return to your work with a new perspective. After some breathing room, you can spot any inconsistencies, spelling and grammar errors, typos, or missing citations and correct them.
- The best research paper format
The format of your research paper should align with the requirements set forth by your college, school, or target publication.
There is no one “best” format, per se. Depending on the stated requirements, you may need to include the following elements:
Title page: The title page of a research paper typically includes the title, author's name, and institutional affiliation and may include additional information such as a course name or instructor's name.
Table of contents: Include a table of contents to make it easy for readers to find specific sections of your paper.
Abstract: The abstract is a summary of the purpose of the paper.
Methods : In this section, describe the research methods used. This may include collecting data , conducting interviews, or doing field research .
Results: Summarize the conclusions you drew from your research in this section.
Discussion: In this section, discuss the implications of your research . Be sure to mention any significant limitations to your approach and suggest areas for further research.
Tables, charts, and illustrations: Use tables, charts, and illustrations to help convey your research findings and make them easier to understand.
Works cited or reference page: Include a works cited or reference page to give credit to the sources that you used to conduct your research.
Bibliography: Provide a list of all the sources you consulted while conducting your research.
Dedication and acknowledgments : Optionally, you may include a dedication and acknowledgments section to thank individuals who helped you with your research.
- General style and formatting guidelines
Formatting your research paper means you can submit it to your college, journal, or other publications in compliance with their criteria.
Research papers tend to follow the American Psychological Association (APA), Modern Language Association (MLA), or Chicago Manual of Style (CMOS) guidelines.
Here’s how each style guide is typically used:
Chicago Manual of Style (CMOS):
CMOS is a versatile style guide used for various types of writing. It's known for its flexibility and use in the humanities. CMOS provides guidelines for citations, formatting, and overall writing style. It allows for both footnotes and in-text citations, giving writers options based on their preferences or publication requirements.
American Psychological Association (APA):
APA is common in the social sciences. It’s hailed for its clarity and emphasis on precision. It has specific rules for citing sources, creating references, and formatting papers. APA style uses in-text citations with an accompanying reference list. It's designed to convey information efficiently and is widely used in academic and scientific writing.
Modern Language Association (MLA):
MLA is widely used in the humanities, especially literature and language studies. It emphasizes the author-page format for in-text citations and provides guidelines for creating a "Works Cited" page. MLA is known for its focus on the author's name and the literary works cited. It’s frequently used in disciplines that prioritize literary analysis and critical thinking.
To confirm you're using the latest style guide, check the official website or publisher's site for updates, consult academic resources, and verify the guide's publication date. Online platforms and educational resources may also provide summaries and alerts about any revisions or additions to the style guide.
Citing sources
When working on your research paper, it's important to cite the sources you used properly. Your citation style will guide you through this process. Generally, there are three parts to citing sources in your research paper:
First, provide a brief citation in the body of your essay. This is also known as a parenthetical or in-text citation.
Second, include a full citation in the Reference list at the end of your paper. Different types of citations include in-text citations, footnotes, and reference lists.
In-text citations include the author's surname and the date of the citation.
Footnotes appear at the bottom of each page of your research paper. They may also be summarized within a reference list at the end of the paper.
A reference list includes all of the research used within the paper at the end of the document. It should include the author, date, paper title, and publisher listed in the order that aligns with your citation style.
10 research paper writing tips:
Following some best practices is essential to writing a research paper that contributes to your field of study and creates a positive impact.
These tactics will help you structure your argument effectively and ensure your work benefits others:
Clear and precise language: Ensure your language is unambiguous. Use academic language appropriately, but keep it simple. Also, provide clear takeaways for your audience.
Effective idea separation: Organize the vast amount of information and sources in your paper with paragraphs and titles. Create easily digestible sections for your readers to navigate through.
Compelling intro: Craft an engaging introduction that captures your reader's interest. Hook your audience and motivate them to continue reading.
Thorough revision and editing: Take the time to review and edit your paper comprehensively. Use tools like Grammarly to detect and correct small, overlooked errors.
Thesis precision: Develop a clear and concise thesis statement that guides your paper. Ensure that your thesis aligns with your research's overall purpose and contribution.
Logical flow of ideas: Maintain a logical progression throughout the paper. Use transitions effectively to connect different sections and maintain coherence.
Critical evaluation of sources: Evaluate and critically assess the relevance and reliability of your sources. Ensure that your research is based on credible and up-to-date information.
Thematic consistency: Maintain a consistent theme throughout the paper. Ensure that all sections contribute cohesively to the overall argument.
Relevant supporting evidence: Provide concise and relevant evidence to support your arguments. Avoid unnecessary details that may distract from the main points.
Embrace counterarguments: Acknowledge and address opposing views to strengthen your position. Show that you have considered alternative arguments in your field.
7 research tips
If you want your paper to not only be well-written but also contribute to the progress of human knowledge, consider these tips to take your paper to the next level:
Selecting the appropriate topic: The topic you select should align with your area of expertise, comply with the requirements of your project, and have sufficient resources for a comprehensive investigation.
Use academic databases: Academic databases such as PubMed, Google Scholar, and JSTOR offer a wealth of research papers that can help you discover everything you need to know about your chosen topic.
Critically evaluate sources: It is important not to accept research findings at face value. Instead, it is crucial to critically analyze the information to avoid jumping to conclusions or overlooking important details. A well-written research paper requires a critical analysis with thorough reasoning to support claims.
Diversify your sources: Expand your research horizons by exploring a variety of sources beyond the standard databases. Utilize books, conference proceedings, and interviews to gather diverse perspectives and enrich your understanding of the topic.
Take detailed notes: Detailed note-taking is crucial during research and can help you form the outline and body of your paper.
Stay up on trends: Keep abreast of the latest developments in your field by regularly checking for recent publications. Subscribe to newsletters, follow relevant journals, and attend conferences to stay informed about emerging trends and advancements.
Engage in peer review: Seek feedback from peers or mentors to ensure the rigor and validity of your research . Peer review helps identify potential weaknesses in your methodology and strengthens the overall credibility of your findings.
- The real-world impact of research papers
Writing a research paper is more than an academic or business exercise. The experience provides an opportunity to explore a subject in-depth, broaden one's understanding, and arrive at meaningful conclusions. With careful planning, dedication, and hard work, writing a research paper can be a fulfilling and enriching experience contributing to advancing knowledge.
How do I publish my research paper?
Many academics wish to publish their research papers. While challenging, your paper might get traction if it covers new and well-written information. To publish your research paper, find a target publication, thoroughly read their guidelines, format your paper accordingly, and send it to them per their instructions. You may need to include a cover letter, too. After submission, your paper may be peer-reviewed by experts to assess its legitimacy, quality, originality, and methodology. Following review, you will be informed by the publication whether they have accepted or rejected your paper.
What is a good opening sentence for a research paper?
Beginning your research paper with a compelling introduction can ensure readers are interested in going further. A relevant quote, a compelling statistic, or a bold argument can start the paper and hook your reader. Remember, though, that the most important aspect of a research paper is the quality of the information––not necessarily your ability to storytell, so ensure anything you write aligns with your goals.
Research paper vs. a research proposal—what’s the difference?
While some may confuse research papers and proposals, they are different documents.
A research proposal comes before a research paper. It is a detailed document that outlines an intended area of exploration. It includes the research topic, methodology, timeline, sources, and potential conclusions. Research proposals are often required when seeking approval to conduct research.
A research paper is a summary of research findings. A research paper follows a structured format to present those findings and construct an argument or conclusion.
Should you be using a customer insights hub?
Do you want to discover previous research faster?
Do you share your research findings with others?
Do you analyze research data?
Start for free today, add your research, and get to key insights faster
Editor’s picks
Last updated: 13 April 2023
Last updated: 14 February 2024
Last updated: 27 January 2024
Last updated: 18 April 2023
Last updated: 8 February 2023
Last updated: 23 January 2024
Last updated: 30 January 2024
Last updated: 7 February 2023
Last updated: 18 May 2023
Last updated: 31 January 2024
Last updated: 13 May 2024
Latest articles
Related topics, .css-je19u9{-webkit-align-items:flex-end;-webkit-box-align:flex-end;-ms-flex-align:flex-end;align-items:flex-end;display:-webkit-box;display:-webkit-flex;display:-ms-flexbox;display:flex;-webkit-flex-direction:row;-ms-flex-direction:row;flex-direction:row;-webkit-box-flex-wrap:wrap;-webkit-flex-wrap:wrap;-ms-flex-wrap:wrap;flex-wrap:wrap;-webkit-box-pack:center;-ms-flex-pack:center;-webkit-justify-content:center;justify-content:center;row-gap:0;text-align:center;max-width:671px;}@media (max-width: 1079px){.css-je19u9{max-width:400px;}.css-je19u9>span{white-space:pre;}}@media (max-width: 799px){.css-je19u9{max-width:400px;}.css-je19u9>span{white-space:pre;}} decide what to .css-1kiodld{max-height:56px;display:-webkit-box;display:-webkit-flex;display:-ms-flexbox;display:flex;-webkit-align-items:center;-webkit-box-align:center;-ms-flex-align:center;align-items:center;}@media (max-width: 1079px){.css-1kiodld{display:none;}} build next, decide what to build next.

Users report unexpectedly high data usage, especially during streaming sessions.

Users find it hard to navigate from the home page to relevant playlists in the app.

It would be great to have a sleep timer feature, especially for bedtime listening.

I need better filters to find the songs or artists I’m looking for.
- 10 research paper
Log in or sign up
Get started for free

How to Write a Research Paper
Use the links below to jump directly to any section of this guide:
Research Paper Fundamentals
How to choose a topic or question, how to create a working hypothesis or thesis, common research paper methodologies, how to gather and organize evidence , how to write an outline for your research paper, how to write a rough draft, how to revise your draft, how to produce a final draft, resources for teachers .
It is not fair to say that no one writes anymore. Just about everyone writes text messages, brief emails, or social media posts every single day. Yet, most people don't have a lot of practice with the formal, organized writing required for a good academic research paper. This guide contains links to a variety of resources that can help demystify the process. Some of these resources are intended for teachers; they contain exercises, activities, and teaching strategies. Other resources are intended for direct use by students who are struggling to write papers, or are looking for tips to make the process go more smoothly.
The resources in this section are designed to help students understand the different types of research papers, the general research process, and how to manage their time. Below, you'll find links from university writing centers, the trusted Purdue Online Writing Lab, and more.
What is an Academic Research Paper?
"Genre and the Research Paper" (Purdue OWL)
There are different types of research papers. Different types of scholarly questions will lend themselves to one format or another. This is a brief introduction to the two main genres of research paper: analytic and argumentative.
"7 Most Popular Types of Research Papers" (Personal-writer.com)
This resource discusses formats that high school students commonly encounter, such as the compare and contrast essay and the definitional essay. Please note that the inclusion of this link is not an endorsement of this company's paid service.
How to Prepare and Plan Out Writing a Research Paper
Teachers can give their students a step-by-step guide like these to help them understand the different steps of the research paper process. These guides can be combined with the time management tools in the next subsection to help students come up with customized calendars for completing their papers.
"Ten Steps for Writing Research Papers" (American University)
This resource from American University is a comprehensive guide to the research paper writing process, and includes examples of proper research questions and thesis topics.
"Steps in Writing a Research Paper" (SUNY Empire State College)
This guide breaks the research paper process into 11 steps. Each "step" links to a separate page, which describes the work entailed in completing it.
How to Manage Time Effectively
The links below will help students determine how much time is necessary to complete a paper. If your sources are not available online or at your local library, you'll need to leave extra time for the Interlibrary Loan process. Remember that, even if you do not need to consult secondary sources, you'll still need to leave yourself ample time to organize your thoughts.
"Research Paper Planner: Timeline" (Baylor University)
This interactive resource from Baylor University creates a suggested writing schedule based on how much time a student has to work on the assignment.
"Research Paper Planner" (UCLA)
UCLA's library offers this step-by-step guide to the research paper writing process, which also includes a suggested planning calendar.
There's a reason teachers spend a long time talking about choosing a good topic. Without a good topic and a well-formulated research question, it is almost impossible to write a clear and organized paper. The resources below will help you generate ideas and formulate precise questions.
"How to Select a Research Topic" (Univ. of Michigan-Flint)
This resource is designed for college students who are struggling to come up with an appropriate topic. A student who uses this resource and still feels unsure about his or her topic should consult the course instructor for further personalized assistance.
"25 Interesting Research Paper Topics to Get You Started" (Kibin)
This resource, which is probably most appropriate for high school students, provides a list of specific topics to help get students started. It is broken into subsections, such as "paper topics on local issues."
"Writing a Good Research Question" (Grand Canyon University)
This introduction to research questions includes some embedded videos, as well as links to scholarly articles on research questions. This resource would be most appropriate for teachers who are planning lessons on research paper fundamentals.
"How to Write a Research Question the Right Way" (Kibin)
This student-focused resource provides more detail on writing research questions. The language is accessible, and there are embedded videos and examples of good and bad questions.
It is important to have a rough hypothesis or thesis in mind at the beginning of the research process. People who have a sense of what they want to say will have an easier time sorting through scholarly sources and other information. The key, of course, is not to become too wedded to the draft hypothesis or thesis. Just about every working thesis gets changed during the research process.
CrashCourse Video: "Sociology Research Methods" (YouTube)
Although this video is tailored to sociology students, it is applicable to students in a variety of social science disciplines. This video does a good job demonstrating the connection between the brainstorming that goes into selecting a research question and the formulation of a working hypothesis.
"How to Write a Thesis Statement for an Analytical Essay" (YouTube)
Students writing analytical essays will not develop the same type of working hypothesis as students who are writing research papers in other disciplines. For these students, developing the working thesis may happen as a part of the rough draft (see the relevant section below).
"Research Hypothesis" (Oakland Univ.)
This resource provides some examples of hypotheses in social science disciplines like Political Science and Criminal Justice. These sample hypotheses may also be useful for students in other soft social sciences and humanities disciplines like History.
When grading a research paper, instructors look for a consistent methodology. This section will help you understand different methodological approaches used in research papers. Students will get the most out of these resources if they use them to help prepare for conversations with teachers or discussions in class.
"Types of Research Designs" (USC)
A "research design," used for complex papers, is related to the paper's method. This resource contains introductions to a variety of popular research designs in the social sciences. Although it is not the most intuitive site to read, the information here is very valuable.
"Major Research Methods" (YouTube)
Although this video is a bit on the dry side, it provides a comprehensive overview of the major research methodologies in a format that might be more accessible to students who have struggled with textbooks or other written resources.
"Humanities Research Strategies" (USC)
This is a portal where students can learn about four methodological approaches for humanities papers: Historical Methodologies, Textual Criticism, Conceptual Analysis, and the Synoptic method.
"Selected Major Social Science Research Methods: Overview" (National Academies Press)
This appendix from the book Using Science as Evidence in Public Policy , printed by National Academies Press, introduces some methods used in social science papers.
"Organizing Your Social Sciences Research Paper: 6. The Methodology" (USC)
This resource from the University of Southern California's library contains tips for writing a methodology section in a research paper.
How to Determine the Best Methodology for You
Anyone who is new to writing research papers should be sure to select a method in consultation with their instructor. These resources can be used to help prepare for that discussion. They may also be used on their own by more advanced students.
"Choosing Appropriate Research Methodologies" (Palgrave Study Skills)
This friendly and approachable resource from Palgrave Macmillan can be used by students who are just starting to think about appropriate methodologies.
"How to Choose Your Research Methods" (NFER (UK))
This is another approachable resource students can use to help narrow down the most appropriate methods for their research projects.
The resources in this section introduce the process of gathering scholarly sources and collecting evidence. You'll find a range of material here, from introductory guides to advanced explications best suited to college students. Please consult the LitCharts How to Do Academic Research guide for a more comprehensive list of resources devoted to finding scholarly literature.
Google Scholar
Students who have access to library websites with detailed research guides should start there, but people who do not have access to those resources can begin their search for secondary literature here.
"Gathering Appropriate Information" (Texas Gateway)
This resource from the Texas Gateway for online resources introduces students to the research process, and contains interactive exercises. The level of complexity is suitable for middle school, high school, and introductory college classrooms.
"An Overview of Quantitative and Qualitative Data Collection Methods" (NSF)
This PDF from the National Science Foundation goes into detail about best practices and pitfalls in data collection across multiple types of methodologies.
"Social Science Methods for Data Collection and Analysis" (Swiss FIT)
This resource is appropriate for advanced undergraduates or teachers looking to create lessons on research design and data collection. It covers techniques for gathering data via interviews, observations, and other methods.
"Collecting Data by In-depth Interviewing" (Leeds Univ.)
This resource contains enough information about conducting interviews to make it useful for teachers who want to create a lesson plan, but is also accessible enough for college juniors or seniors to make use of it on their own.
There is no "one size fits all" outlining technique. Some students might devote all their energy and attention to the outline in order to avoid the paper. Other students may benefit from being made to sit down and organize their thoughts into a lengthy sentence outline. The resources in this section include strategies and templates for multiple types of outlines.
"Topic vs. Sentence Outlines" (UC Berkeley)
This resource introduces two basic approaches to outlining: the shorter topic-based approach, and the longer, more detailed sentence-based approach. This resource also contains videos on how to develop paper paragraphs from the sentence-based outline.
"Types of Outlines and Samples" (Purdue OWL)
The Purdue Online Writing Lab's guide is a slightly less detailed discussion of different types of outlines. It contains several sample outlines.
"Writing An Outline" (Austin C.C.)
This resource from a community college contains sample outlines from an American history class that students can use as models.
"How to Structure an Outline for a College Paper" (YouTube)
This brief (sub-2 minute) video from the ExpertVillage YouTube channel provides a model of outline writing for students who are struggling with the idea.
"Outlining" (Harvard)
This is a good resource to consult after completing a draft outline. It offers suggestions for making sure your outline avoids things like unnecessary repetition.
As with outlines, rough drafts can take on many different forms. These resources introduce teachers and students to the various approaches to writing a rough draft. This section also includes resources that will help you cite your sources appropriately according to the MLA, Chicago, and APA style manuals.
"Creating a Rough Draft for a Research Paper" (Univ. of Minnesota)
This resource is useful for teachers in particular, as it provides some suggested exercises to help students with writing a basic rough draft.
Rough Draft Assignment (Duke of Definition)
This sample assignment, with a brief list of tips, was developed by a high school teacher who runs a very successful and well-reviewed page of educational resources.
"Creating the First Draft of Your Research Paper" (Concordia Univ.)
This resource will be helpful for perfectionists or procrastinators, as it opens by discussing the problem of avoiding writing. It also provides a short list of suggestions meant to get students writing.
Using Proper Citations
There is no such thing as a rough draft of a scholarly citation. These links to the three major citation guides will ensure that your citations follow the correct format. Please consult the LitCharts How to Cite Your Sources guide for more resources.
Chicago Manual of Style Citation Guide
Some call The Chicago Manual of Style , which was first published in 1906, "the editors' Bible." The manual is now in its 17th edition, and is popular in the social sciences, historical journals, and some other fields in the humanities.
APA Citation Guide
According to the American Psychological Association, this guide was developed to aid reading comprehension, clarity of communication, and to reduce bias in language in the social and behavioral sciences. Its first full edition was published in 1952, and it is now in its sixth edition.
MLA Citation Guide
The Modern Language Association style is used most commonly within the liberal arts and humanities. The MLA Style Manual and Guide to Scholarly Publishing was first published in 1985 and (as of 2008) is in its third edition.
Any professional scholar will tell you that the best research papers are made in the revision stage. No matter how strong your research question or working thesis, it is not possible to write a truly outstanding paper without devoting energy to revision. These resources provide examples of revision exercises for the classroom, as well as tips for students working independently.
"The Art of Revision" (Univ. of Arizona)
This resource provides a wealth of information and suggestions for both students and teachers. There is a list of suggested exercises that teachers might use in class, along with a revision checklist that is useful for teachers and students alike.
"Script for Workshop on Revision" (Vanderbilt University)
Vanderbilt's guide for leading a 50-minute revision workshop can serve as a model for teachers who wish to guide students through the revision process during classtime.
"Revising Your Paper" (Univ. of Washington)
This detailed handout was designed for students who are beginning the revision process. It discusses different approaches and methods for revision, and also includes a detailed list of things students should look for while they revise.
"Revising Drafts" (UNC Writing Center)
This resource is designed for students and suggests things to look for during the revision process. It provides steps for the process and has a FAQ for students who have questions about why it is important to revise.
Conferencing with Writing Tutors and Instructors
No writer is so good that he or she can't benefit from meeting with instructors or peer tutors. These resources from university writing, learning, and communication centers provide suggestions for how to get the most out of these one-on-one meetings.
"Getting Feedback" (UNC Writing Center)
This very helpful resource talks about how to ask for feedback during the entire writing process. It contains possible questions that students might ask when developing an outline, during the revision process, and after the final draft has been graded.
"Prepare for Your Tutoring Session" (Otis College of Art and Design)
This guide from a university's student learning center contains a lot of helpful tips for getting the most out of working with a writing tutor.
"The Importance of Asking Your Professor" (Univ. of Waterloo)
This article from the university's Writing and Communication Centre's blog contains some suggestions for how and when to get help from professors and Teaching Assistants.
Once you've revised your first draft, you're well on your way to handing in a polished paper. These resources—each of them produced by writing professionals at colleges and universities—outline the steps required in order to produce a final draft. You'll find proofreading tips and checklists in text and video form.
"Developing a Final Draft of a Research Paper" (Univ. of Minnesota)
While this resource contains suggestions for revision, it also features a couple of helpful checklists for the last stages of completing a final draft.
Basic Final Draft Tips and Checklist (Univ. of Maryland-University College)
This short and accessible resource, part of UMUC's very thorough online guide to writing and research, contains a very basic checklist for students who are getting ready to turn in their final drafts.
Final Draft Checklist (Everett C.C.)
This is another accessible final draft checklist, appropriate for both high school and college students. It suggests reading your essay aloud at least once.
"How to Proofread Your Final Draft" (YouTube)
This video (approximately 5 minutes), produced by Eastern Washington University, gives students tips on proofreading final drafts.
"Proofreading Tips" (Georgia Southern-Armstrong)
This guide will help students learn how to spot common errors in their papers. It suggests focusing on content and editing for grammar and mechanics.
This final set of resources is intended specifically for high school and college instructors. It provides links to unit plans and classroom exercises that can help improve students' research and writing skills. You'll find resources that give an overview of the process, along with activities that focus on how to begin and how to carry out research.
"Research Paper Complete Resources Pack" (Teachers Pay Teachers)
This packet of assignments, rubrics, and other resources is designed for high school students. The resources in this packet are aligned to Common Core standards.
"Research Paper—Complete Unit" (Teachers Pay Teachers)
This packet of assignments, notes, PowerPoints, and other resources has a 4/4 rating with over 700 ratings. It is designed for high school teachers, but might also be useful to college instructors who work with freshmen.
"Teaching Students to Write Good Papers" (Yale)
This resource from Yale's Center for Teaching and Learning is designed for college instructors, and it includes links to appropriate activities and exercises.
"Research Paper Writing: An Overview" (CUNY Brooklyn)
CUNY Brooklyn offers this complete lesson plan for introducing students to research papers. It includes an accompanying set of PowerPoint slides.
"Lesson Plan: How to Begin Writing a Research Paper" (San Jose State Univ.)
This lesson plan is designed for students in the health sciences, so teachers will have to modify it for their own needs. It includes a breakdown of the brainstorming, topic selection, and research question process.
"Quantitative Techniques for Social Science Research" (Univ. of Pittsburgh)
This is a set of PowerPoint slides that can be used to introduce students to a variety of quantitative methods used in the social sciences.
- PDFs for all 136 Lit Terms we cover
- Downloads of 1929 LitCharts Lit Guides
- Teacher Editions for every Lit Guide
- Explanations and citation info for 40,694 quotes across 1929 books
- Downloadable (PDF) line-by-line translations of every Shakespeare play
Need something? Request a new guide .
How can we improve? Share feedback .
LitCharts is hiring!

How to Write a Research Paper

If you already have a headache trying to understand what research paper is all about, we have created an ultimate guide for you on how to write a research paper. You will find all the answers to your questions regarding structure, planning, doing investigation, finding the topic that appeals to you. Plus, you will find out the secret to an excellent paper. Are you at the edge of your seat? Let us start with the basics then.
- What is a Research Paper
- Reasons for Writing a Research Paper
- Report Papers and Thesis Papers
- How to Start a Research Paper
- How to Choose a Topic for a Research Paper
- How to Write a Proposal for a Research Paper
- How to Write a Research Plan
- How to Do Research
- How to Write an Outline for a Research Paper
- How to Write a Thesis Statement for a Research Paper
- How to Write a Research Paper Rough Draft
- How to Write an Introduction for a Research Paper
- How to Write a Body of a Research Paper
- How to Write a Conclusion for a Research Paper
- How to Write an Abstract for a Research Paper
- How to Revise and Edit a Research Paper
- How to Write a Bibliography for a Research Paper
- What Makes a Good Research Paper
Research Paper Writing Services
What is a research paper.

Academic Writing, Editing, Proofreading, And Problem Solving Services
Get 10% off with 24start discount code.
You probably know the saying ‘the devil is not as black as he is painted’. This particular saying is absolutely true when it comes to writing a research paper. Your feet are cold even with the thought of this assignment. You have heard terrifying stories from older students. You have never done this before, so certainly you are scared. What is a research paper? How should I start? What are all these requirements about?
Luckily, you have a friend in need. That is our writing service. First and foremost, let us clarify the definition. A research paper is a piece of academic writing that provides information about a particular topic that you’ve researched . In other words, you choose a topic: about historical events, the work of some artist, some social issues etc. Then you collect data on the given topic and analyze it. Finally, you put your analysis on paper. See, it is not as scary as it seems. If you are still having doubts, whether you can handle it yourself, we are here to help you. Our team of writers can help you choose the topic, or give you advice on how to plan your work, or how to start, or craft a paper for you. Just contact us 24/7 and see everything yourself.
5 Reasons for Writing a Research Paper
Why should I spend my time writing some academic paper? What is the use of it? Is not some practical knowledge more important? The list of questions is endless when it comes to a research paper. That is why we have outlined 5 main reasons why writing a research paper is a good thing.
- You will learn how to organize your time
If you want to write a research paper, you will have to learn how to manage your time. This type of assignment cannot be done overnight. It requires careful planning and you will need to learn how to do it. Later, you will be able to use these time-managing skills in your personal life, so why not developing them?
- You will discover your writing skills
You cannot know something before you try it. This rule relates to writing as well. You cannot claim that you cannot write until you try it yourself. It will be really difficult at the beginning, but then the words will come to your head themselves.
- You will improve your analytical skills
Writing a research paper is all about investigation and analysis. You will need to collect data, examine and classify it. These skills are needed in modern life more than anything else is.
- You will gain confidence
Once you do your own research, it gives you the feeling of confidence in yourself. The reason is simple human brain likes solving puzzles and your assignment is just another puzzle to be solved.
- You will learn how to persuade the reader
When you write your paper, you should always remember that you are writing it for someone to read. Moreover, you want this someone to believe in your ideas. For this reason, you will have to learn different convincing methods and techniques. You will learn how to make your writing persuasive. In turns, you will be able to use these methods in real life.
What is the Difference between Report and Thesis Papers?
A common question is ‘what is the difference between a report paper and a thesis paper?’ The difference lies in the aim of these two assignments. While the former aims at presenting the information, the latter aims at providing your opinion on the matter. In other words, in a report paper you have to summarize your findings. In a thesis paper, you choose some issue and defend your point of view by persuading the reader. It is that simple.
A thesis paper is a more common assignment than a report paper. This task will help a professor to evaluate your analytical skills and skills to present your ideas logically. These skills are more important than just the ability to collect and summarize data.
How to Write a Research Paper Step by Step
Research comes from the French word rechercher , meaning “to seek out.” Writing a research paper requires you to seek out information about a subject, take a stand on it, and back it up with the opinions, ideas, and views of others. What results is a printed paper variously known as a term paper or library paper, usually between five and fifteen pages long—most instructors specify a minimum length—in which you present your views and findings on the chosen subject.

It is not a secret that the majority of students hate writing a research paper. The reason is simple it steals your time and energy. Not to mention, constant anxiety that you will not be able to meet the deadline or that you will forget about some academic requirement.
We will not lie to you; a research paper is a difficult assignment. You will have to spend a lot of time. You will need to read, to analyze, and to search for the material. You will probably be stuck sometimes. However, if you organize your work smart, you will gain something that is worth all the effort – knowledge, experience, and high grades.
The reason why many students fail writing a research paper is that nobody explained them how to start and how to plan their work. Luckily, you have found our writing service and we are ready to shed the light on this dark matter.
We have created a step by step guide for you on how to write a research paper. We will dwell upon the structure, the writing tips, the writing strategies as well as academic requirements. Read this whole article and you will see that you can handle writing this assignment and our team of writers is here to assist you.
How to Start a Research Paper?

It all starts with the assignment. Your professor gives you the task. It may be either some general issue or specific topic to write about. Your assignment is your first guide to success. If you understand what you need to do according to the assignment, you are on the road to high results. Do not be scared to clarify your task if you need to. There is nothing wrong in asking a question if you want to do something right. You can ask your professor or you can ask our writers who know a thing or two in academic writing.
It is essential to understand the assignment. A good beginning makes a good ending, so start smart.
Learn how to start a research paper .
Choosing a Topic for a Research Paper

We have already mentioned that it is not enough to do great research. You need to persuade the reader that you have made some great research. What convinces better that an eye-catching topic? That is why it is important to understand how to choose a topic for a research paper.
First, you need to delimit the general idea to a more specific one. Secondly, you need to find what makes this topic interesting for you and for the academia. Finally, you need to refine you topic. Remember, it is not something you will do in one day. You can be reshaping your topic throughout your whole writing process. Still, reshaping not changing it completely. That is why keep in your head one main idea: your topic should be precise and compelling .
Learn how to choose a topic for a research paper .
How to Write a Proposal for a Research Paper?

If you do not know what a proposal is, let us explain it to you. A proposal should answer three main questions:
- What is the main aim of your investigation?
- Why is your investigation important?
- How are you going to achieve the results?
In other words, proposal should show why your topic is interesting and how you are going to prove it. As to writing requirements, they may differ. That is why make sure you find out all the details at your department. You can ask your departmental administrator or find information online at department’s site. It is crucial to follow all the administrative requirements, as it will influence your grade.
Learn how to write a proposal for a research paper .
How to Write a Research Plan?

The next step is writing a plan. You have already decided on the main issues, you have chosen the bibliography, and you have clarified the methods. Here comes the planning. If you want to avoid writer’s block, you have to structure you work. Discuss your strategies and ideas with your instructor. Think thoroughly why you need to present some data and ideas first and others second. Remember that there are basic structure elements that your research paper should include:
- Thesis Statement
- Introduction
- Bibliography
You should keep in mind this skeleton when planning your work. This will keep your mind sharp and your ideas will flow logically.
Learn how to write a research plan .
How to Do Research?

Your research will include three stages: collecting data, reading and analyzing it, and writing itself.
First, you need to collect all the material that you will need for you investigation: films, documents, surveys, interviews, and others. Secondly, you will have to read and analyze. This step is tricky, as you need to do this part smart. It is not enough just to read, as you cannot keep in mind all the information. It is essential that you make notes and write down your ideas while analyzing some data. When you get down to the stage number three, writing itself, you will already have the main ideas written on your notes. Plus, remember to jot down the reference details. You will then appreciate this trick when you will have to write the bibliography.
If you do your research this way, it will be much easier for you to write the paper. You will already have blocks of your ideas written down and you will just need to add some material and refine your paper.
Learn how to do research .
How to Write an Outline for a Research Paper?

To make your paper well organized you need to write an outline. Your outline will serve as your guiding star through the writing process. With a great outline you will not get sidetracked, because you will have a structured plan to follow. Both you and the reader will benefit from your outline. You present your ideas logically and you make your writing coherent according to your plan. As a result, this outline guides the reader through your paper and the reader enjoys the way you demonstrate your ideas.
Learn how to write an outline for a research paper . See research paper outline examples .
How to Write a Thesis Statement for a Research Paper?

Briefly, the thesis is the main argument of your research paper. It should be precise, convincing and logical. Your thesis statement should include your point of view supported by evidence or logic. Still, remember it should be precise. You should not beat around the bush, or provide all the possible evidence you have found. It is usually a single sentence that shows your argument. In on sentence you should make a claim, explain why it significant and convince the reader that your point of view is important.
Learn how to write a thesis statement for a research paper . See research paper thesis statement examples .
Should I Write a Rough Draft for a Research Paper?

Do you know any writer who put their ideas on paper, then never edited them and just published? Probably, no writer did so. Writing a research paper is no exception. It is impossible to cope with this assignment without writing a rough draft.
Your draft will help you understand what you need to polish to make your paper perfect. All the requirements, academic standards make it difficult to do everything flawlessly at the first attempt. Make sure you know all the formatting requirements: margins, words quantity, reference requirements, formatting styles etc.
Learn how to write a rough draft for a research paper .
How to Write an Introduction for a Research Paper?

Let us make it more vivid for you. We have narrowed down the tips on writing an introduction to the three main ones:
- Include your thesis in your introduction
Remember to include the thesis statement in your introduction. Usually, it goes at the end of the first paragraph.
- Present the main ideas of the body
You should tell the main topics you are going to discuss in the main body. For this reason, before writing this part of introduction, make sure you know what is your main body is going to be about. It should include your main ideas.
- Polish your thesis and introduction
When you finish the main body of your paper, come back to the thesis statement and introduction. Restate something if needed. Just make it perfect; because introduction is like the trailer to your paper, it should make the reader want to read the whole piece.
Learn how to write an introduction for a research paper . See research paper introduction examples .
How to Write a Body of a Research Paper?

A body is the main part of your research paper. In this part, you will include all the needed evidence; you will provide the examples and support your argument.
It is important to structure your paragraphs thoroughly. That is to say, topic sentence and the evidence supporting the topic. Stay focused and do not be sidetracked. You have your outline, so follow it.
Here are the main tips to keep in head when writing a body of a research paper:
- Let the ideas flow logically
- Include only relevant information
- Provide the evidence
- Structure the paragraphs
- Make the coherent transition from one paragraph to another
See? When it is all structured, it is not as scary as it seemed at the beginning. Still, if you have doubts, you can always ask our writers for help.
Learn how to write a body of a research paper . See research paper transition examples .
How to Write a Conclusion for a Research Paper?

Writing a good conclusion is important as writing any other part of the paper. Remember that conclusion is not a summary of what you have mentioned before. A good conclusion should include your last strong statement.
If you have written everything according to the plan, the reader already knows why your investigation is important. The reader has already seen the evidence. The only thing left is a strong concluding thought that will organize all your findings.
Never include any new information in conclusion. You need to conclude, not to start a new discussion.
Learn how to write a conclusion for a research paper .
How to Write an Abstract for a Research Paper?

An abstract is a brief summary of your paper, usually 100-200 words. You should provide the main gist of your paper in this short summary. An abstract can be informative, descriptive or proposal. Depending on the type of abstract, you need to write, the requirements will differ.
To write an informative abstract you have to provide the summary of the whole paper. Informative summary. In other words, you need to tell about the main points of your work, the methods used, the results and the conclusion of your research.
To write a descriptive abstract you will not have to provide any summery. You should write a short teaser of your paper. That is to say, you need to write an overview of your paper. The aim of a descriptive abstract is to interest the reader.
Finally, to write a proposal abstract you will need to write the basic summary as for the informative abstract. However, the difference is the following: you aim at persuading someone to let you write on the topic. That is why, a proposal abstract should present your topic as the one worth investigating.
Learn how to write an abstract for a research paper .
Should I Revise and Edit a Research Paper?

Revising and editing your paper is essential if you want to get high grades. Let us help you revise your paper smart:
- Check your paper for spelling and grammar mistakes
- Sharpen the vocabulary
- Make sure there are no slang words in your paper
- Examine your paper in terms of structure
- Compare your topic, thesis statement to the whole piece
- Check your paper for plagiarism
If you need assistance with proofreading and editing your paper, you can turn to the professional editors at our service. They will help you polish your paper to perfection.
Learn how to revise and edit a research paper .
How to Write a Bibliography for a Research Paper?

First, let us make it clear that bibliography and works cited are two different things. Works cited are those that you cited in your paper. Bibliography should include all the materials you used to do your research. Still, remember that bibliography requirements differ depending on the formatting style of your paper. For this reason, make sure you ask you professor all the requirements you need to meet to avoid any misunderstanding.
Learn how to write a bibliography for a research paper .
The Key Secret to a Good Research Paper
Now when you know all the stages of writing a research paper, you are ready to find the key to a good research paper:
- Choose the topic that really interests you
- Make the topic interesting for you even if it is not at the beginning
- Follow the step by step guide and do not get sidetracked
- Be persistent and believe in yourself
- Really do research and write your paper from scratch
- Learn the convincing writing techniques and use them
- Follow the requirements of your assignment
- Ask for help if needed from real professionals
Feeling more confident about your paper now? We are sure you do. Still, if you need help, you can always rely on us 24/7.
We hope we have made writing a research paper much easier for you. We realize that it requires lots of time and energy. We believe when you say that you cannot handle it anymore. For this reason, we have been helping students like you for years. Our professional team of writers is ready to tackle any challenge.
All our authors are experienced writers crafting excellent academic papers. We help students meet the deadline and get the top grades they want. You can see everything yourself. All you need to do is to place your order online and we will contact you. Writing a research paper with us is truly easy, so why do not you check it yourself?
Additional Resources for Research Paper Writing:
- Anthropology Research
- Career Research
- Communication Research
- Criminal Justice Research
- Health Research
- Political Science Research
- Psychology Research
- Sociology Research
ORDER HIGH QUALITY CUSTOM PAPER

- PRO Courses Guides New Tech Help Pro Expert Videos About wikiHow Pro Upgrade Sign In
- EDIT Edit this Article
- EXPLORE Tech Help Pro About Us Random Article Quizzes Request a New Article Community Dashboard This Or That Game Popular Categories Arts and Entertainment Artwork Books Movies Computers and Electronics Computers Phone Skills Technology Hacks Health Men's Health Mental Health Women's Health Relationships Dating Love Relationship Issues Hobbies and Crafts Crafts Drawing Games Education & Communication Communication Skills Personal Development Studying Personal Care and Style Fashion Hair Care Personal Hygiene Youth Personal Care School Stuff Dating All Categories Arts and Entertainment Finance and Business Home and Garden Relationship Quizzes Cars & Other Vehicles Food and Entertaining Personal Care and Style Sports and Fitness Computers and Electronics Health Pets and Animals Travel Education & Communication Hobbies and Crafts Philosophy and Religion Work World Family Life Holidays and Traditions Relationships Youth
- Browse Articles
- Learn Something New
- Quizzes Hot
- This Or That Game
- Train Your Brain
- Explore More
- Support wikiHow
- About wikiHow
- Log in / Sign up
- Education and Communications
- College University and Postgraduate
- Academic Writing
- Research Papers
How to Write a Research Paper
Last Updated: February 18, 2024 Fact Checked
This article was co-authored by Chris Hadley, PhD . Chris Hadley, PhD is part of the wikiHow team and works on content strategy and data and analytics. Chris Hadley earned his PhD in Cognitive Psychology from UCLA in 2006. Chris' academic research has been published in numerous scientific journals. There are 14 references cited in this article, which can be found at the bottom of the page. This article has been fact-checked, ensuring the accuracy of any cited facts and confirming the authority of its sources. This article has been viewed 4,188,977 times.
Whether you’re in a history, literature, or science class, you’ll probably have to write a research paper at some point. It may seem daunting when you’re just starting out, but staying organized and budgeting your time can make the process a breeze. Research your topic, find reliable sources, and come up with a working thesis. Then create an outline and start drafting your paper. Be sure to leave plenty of time to make revisions, as editing is essential if you want to hand in your best work!
Sample Research Papers and Outlines

Researching Your Topic

- For instance, you might start with a general subject, like British decorative arts. Then, as you read, you home in on transferware and pottery. Ultimately, you focus on 1 potter in the 1780s who invented a way to mass-produce patterned tableware.
Tip: If you need to analyze a piece of literature, your task is to pull the work apart into literary elements and explain how the author uses those parts to make their point.

- Authoritative, credible sources include scholarly articles (especially those other authors reference), government websites, scientific studies, and reputable news bureaus. Additionally, check your sources' dates, and make sure the information you gather is up to date.
- Evaluate how other scholars have approached your topic. Identify authoritative sources or works that are accepted as the most important accounts of the subject matter. Additionally, look for debates among scholars, and ask yourself who presents the strongest evidence for their case. [3] X Trustworthy Source Purdue Online Writing Lab Trusted resource for writing and citation guidelines Go to source
- You’ll most likely need to include a bibliography or works cited page, so keep your sources organized. List your sources, format them according to your assigned style guide (such as MLA or Chicago ), and write 2 or 3 summary sentences below each one. [4] X Research source

- Imagine you’re a lawyer in a trial and are presenting a case to a jury. Think of your readers as the jurors; your opening statement is your thesis and you’ll present evidence to the jury to make your case.
- A thesis should be specific rather than vague, such as: “Josiah Spode’s improved formula for bone china enabled the mass production of transfer-printed wares, which expanded the global market for British pottery.”
Drafting Your Essay

- Your outline is your paper’s skeleton. After making the outline, all you’ll need to do is fill in the details.
- For easy reference, include your sources where they fit into your outline, like this: III. Spode vs. Wedgewood on Mass Production A. Spode: Perfected chemical formula with aims for fast production and distribution (Travis, 2002, 43) B. Wedgewood: Courted high-priced luxury market; lower emphasis on mass production (Himmelweit, 2001, 71) C. Therefore: Wedgewood, unlike Spode, delayed the expansion of the pottery market.

- For instance, your opening line could be, “Overlooked in the present, manufacturers of British pottery in the eighteenth and nineteenth centuries played crucial roles in England’s Industrial Revolution.”
- After presenting your thesis, lay out your evidence, like this: “An examination of Spode’s innovative production and distribution techniques will demonstrate the importance of his contributions to the industry and Industrial Revolution at large.”
Tip: Some people prefer to write the introduction first and use it to structure the rest of the paper. However, others like to write the body, then fill in the introduction. Do whichever seems natural to you. If you write the intro first, keep in mind you can tweak it later to reflect your finished paper’s layout.

- After setting the context, you'd include a section on Josiah Spode’s company and what he did to make pottery easier to manufacture and distribute.
- Next, discuss how targeting middle class consumers increased demand and expanded the pottery industry globally.
- Then, you could explain how Spode differed from competitors like Wedgewood, who continued to court aristocratic consumers instead of expanding the market to the middle class.
- The right number of sections or paragraphs depends on your assignment. In general, shoot for 3 to 5, but check your prompt for your assigned length.

- If you bring up a counterargument, make sure it’s a strong claim that’s worth entertaining instead of ones that's weak and easily dismissed.
- Suppose, for instance, you’re arguing for the benefits of adding fluoride to toothpaste and city water. You could bring up a study that suggested fluoride produced harmful health effects, then explain how its testing methods were flawed.

- Sum up your argument, but don’t simply rewrite your introduction using slightly different wording. To make your conclusion more memorable, you could also connect your thesis to a broader topic or theme to make it more relatable to your reader.
- For example, if you’ve discussed the role of nationalism in World War I, you could conclude by mentioning nationalism’s reemergence in contemporary foreign affairs.
Revising Your Paper

- This is also a great opportunity to make sure your paper fulfills the parameters of the assignment and answers the prompt!
- It’s a good idea to put your essay aside for a few hours (or overnight, if you have time). That way, you can start editing it with fresh eyes.
Tip: Try to give yourself at least 2 or 3 days to revise your paper. It may be tempting to simply give your paper a quick read and use the spell-checker to make edits. However, revising your paper properly is more in-depth.

- The passive voice, such as “The door was opened by me,” feels hesitant and wordy. On the other hand, the active voice, or “I opened the door,” feels strong and concise.
- Each word in your paper should do a specific job. Try to avoid including extra words just to fill up blank space on a page or sound fancy.
- For instance, “The author uses pathos to appeal to readers’ emotions” is better than “The author utilizes pathos to make an appeal to the emotional core of those who read the passage.”

- Read your essay out loud to help ensure you catch every error. As you read, check for flow as well and, if necessary, tweak any spots that sound awkward. [13] X Trustworthy Source University of North Carolina Writing Center UNC's on-campus and online instructional service that provides assistance to students, faculty, and others during the writing process Go to source

- It’s wise to get feedback from one person who’s familiar with your topic and another who’s not. The person who knows about the topic can help ensure you’ve nailed all the details. The person who’s unfamiliar with the topic can help make sure your writing is clear and easy to understand.
Community Q&A
- Remember that your topic and thesis should be as specific as possible. Thanks Helpful 5 Not Helpful 0
- Researching, outlining, drafting, and revising are all important steps, so do your best to budget your time wisely. Try to avoid waiting until the last minute to write your paper. Thanks Helpful 6 Not Helpful 2

You Might Also Like

- ↑ https://writing.wisc.edu/handbook/assignments/planresearchpaper/
- ↑ https://writingcenter.unc.edu/tips-and-tools/evaluating-print-sources/
- ↑ https://owl.purdue.edu/owl/research_and_citation/conducting_research/research_overview/index.html
- ↑ https://poorvucenter.yale.edu/writing/graduate-writing-lab/writing-through-graduate-school/working-sources
- ↑ https://opentextbc.ca/writingforsuccess/chapter/chapter-5-putting-the-pieces-together-with-a-thesis-statement/
- ↑ https://owl.purdue.edu/owl/general_writing/the_writing_process/developing_an_outline/index.html
- ↑ https://writingcenter.unc.edu/tips-and-tools/introductions/
- ↑ https://academicguides.waldenu.edu/writingcenter/writingprocess/counterarguments
- ↑ https://writingcenter.fas.harvard.edu/pages/ending-essay-conclusions
- ↑ https://writingcenter.unc.edu/tips-and-tools/revising-drafts/
- ↑ https://academicguides.waldenu.edu/formandstyle/writing/scholarlyvoice/activepassive
- ↑ https://writingcenter.unc.edu/tips-and-tools/editing-and-proofreading/
- ↑ https://writingcenter.unc.edu/tips-and-tools/reading-aloud/
- ↑ https://owl.purdue.edu/owl/general_writing/the_writing_process/proofreading/index.html
About This Article

To write a research paper, start by researching your topic at the library, online, or using an academic database. As you conduct your research and take notes, zero in on a specific topic that you want to write about and create a 1-2 sentence thesis to state the focus of your paper. Then, create an outline that includes an introduction, 3 to 5 body paragraphs to present your arguments, and a conclusion to sum up your main points. Once you have your paper's structure organized, draft your paragraphs, focusing on 1 argument per paragraph. Use the information you found through your research to back up your claims and prove your thesis statement. Finally, proofread and revise your content until it's polished and ready to submit. For more information on researching and citing sources, read on! Did this summary help you? Yes No
- Send fan mail to authors
Reader Success Stories
Private And Discrete
Aug 2, 2020
Did this article help you?
Jan 3, 2018
Oct 29, 2016
Maronicha Lyles
Jul 24, 2016
Maxwell Ansah
Nov 22, 2019

Featured Articles

Trending Articles

Watch Articles

- Terms of Use
- Privacy Policy
- Do Not Sell or Share My Info
- Not Selling Info
Get all the best how-tos!
Sign up for wikiHow's weekly email newsletter
- Privacy Policy

Home » Research Paper Format – Types, Examples and Templates
Research Paper Format – Types, Examples and Templates
Table of Contents

Research paper format is an essential aspect of academic writing that plays a crucial role in the communication of research findings . The format of a research paper depends on various factors such as the discipline, style guide, and purpose of the research. It includes guidelines for the structure, citation style, referencing , and other elements of the paper that contribute to its overall presentation and coherence. Adhering to the appropriate research paper format is vital for ensuring that the research is accurately and effectively communicated to the intended audience. In this era of information, it is essential to understand the different research paper formats and their guidelines to communicate research effectively, accurately, and with the required level of detail. This post aims to provide an overview of some of the common research paper formats used in academic writing.
Research Paper Formats
Research Paper Formats are as follows:
- APA (American Psychological Association) format
- MLA (Modern Language Association) format
- Chicago/Turabian style
- IEEE (Institute of Electrical and Electronics Engineers) format
- AMA (American Medical Association) style
- Harvard style
- Vancouver style
- ACS (American Chemical Society) style
- ASA (American Sociological Association) style
- APSA (American Political Science Association) style
APA (American Psychological Association) Format
Here is a general APA format for a research paper:
- Title Page: The title page should include the title of your paper, your name, and your institutional affiliation. It should also include a running head, which is a shortened version of the title, and a page number in the upper right-hand corner.
- Abstract : The abstract is a brief summary of your paper, typically 150-250 words. It should include the purpose of your research, the main findings, and any implications or conclusions that can be drawn.
- Introduction: The introduction should provide background information on your topic, state the purpose of your research, and present your research question or hypothesis. It should also include a brief literature review that discusses previous research on your topic.
- Methods: The methods section should describe the procedures you used to collect and analyze your data. It should include information on the participants, the materials and instruments used, and the statistical analyses performed.
- Results: The results section should present the findings of your research in a clear and concise manner. Use tables and figures to help illustrate your results.
- Discussion : The discussion section should interpret your results and relate them back to your research question or hypothesis. It should also discuss the implications of your findings and any limitations of your study.
- References : The references section should include a list of all sources cited in your paper. Follow APA formatting guidelines for your citations and references.
Some additional tips for formatting your APA research paper:
- Use 12-point Times New Roman font throughout the paper.
- Double-space all text, including the references.
- Use 1-inch margins on all sides of the page.
- Indent the first line of each paragraph by 0.5 inches.
- Use a hanging indent for the references (the first line should be flush with the left margin, and all subsequent lines should be indented).
- Number all pages, including the title page and references page, in the upper right-hand corner.
APA Research Paper Format Template
APA Research Paper Format Template is as follows:
Title Page:
- Title of the paper
- Author’s name
- Institutional affiliation
- A brief summary of the main points of the paper, including the research question, methods, findings, and conclusions. The abstract should be no more than 250 words.
Introduction:
- Background information on the topic of the research paper
- Research question or hypothesis
- Significance of the study
- Overview of the research methods and design
- Brief summary of the main findings
- Participants: description of the sample population, including the number of participants and their characteristics (age, gender, ethnicity, etc.)
- Materials: description of any materials used in the study (e.g., survey questions, experimental apparatus)
- Procedure: detailed description of the steps taken to conduct the study
- Presentation of the findings of the study, including statistical analyses if applicable
- Tables and figures may be included to illustrate the results
Discussion:
- Interpretation of the results in light of the research question and hypothesis
- Implications of the study for the field
- Limitations of the study
- Suggestions for future research
References:
- A list of all sources cited in the paper, in APA format
Formatting guidelines:
- Double-spaced
- 12-point font (Times New Roman or Arial)
- 1-inch margins on all sides
- Page numbers in the top right corner
- Headings and subheadings should be used to organize the paper
- The first line of each paragraph should be indented
- Quotations of 40 or more words should be set off in a block quote with no quotation marks
- In-text citations should include the author’s last name and year of publication (e.g., Smith, 2019)
APA Research Paper Format Example
APA Research Paper Format Example is as follows:
The Effects of Social Media on Mental Health
University of XYZ
This study examines the relationship between social media use and mental health among college students. Data was collected through a survey of 500 students at the University of XYZ. Results suggest that social media use is significantly related to symptoms of depression and anxiety, and that the negative effects of social media are greater among frequent users.
Social media has become an increasingly important aspect of modern life, especially among young adults. While social media can have many positive effects, such as connecting people across distances and sharing information, there is growing concern about its impact on mental health. This study aims to examine the relationship between social media use and mental health among college students.
Participants: Participants were 500 college students at the University of XYZ, recruited through online advertisements and flyers posted on campus. Participants ranged in age from 18 to 25, with a mean age of 20.5 years. The sample was 60% female, 40% male, and 5% identified as non-binary or gender non-conforming.
Data was collected through an online survey administered through Qualtrics. The survey consisted of several measures, including the Patient Health Questionnaire-9 (PHQ-9) for depression symptoms, the Generalized Anxiety Disorder-7 (GAD-7) for anxiety symptoms, and questions about social media use.
Procedure :
Participants were asked to complete the online survey at their convenience. The survey took approximately 20-30 minutes to complete. Data was analyzed using descriptive statistics, correlations, and multiple regression analysis.
Results indicated that social media use was significantly related to symptoms of depression (r = .32, p < .001) and anxiety (r = .29, p < .001). Regression analysis indicated that frequency of social media use was a significant predictor of both depression symptoms (β = .24, p < .001) and anxiety symptoms (β = .20, p < .001), even when controlling for age, gender, and other relevant factors.
The results of this study suggest that social media use is associated with symptoms of depression and anxiety among college students. The negative effects of social media are greater among frequent users. These findings have important implications for mental health professionals and educators, who should consider addressing the potential negative effects of social media use in their work with young adults.
References :
References should be listed in alphabetical order according to the author’s last name. For example:
- Chou, H. T. G., & Edge, N. (2012). “They are happier and having better lives than I am”: The impact of using Facebook on perceptions of others’ lives. Cyberpsychology, Behavior, and Social Networking, 15(2), 117-121.
- Twenge, J. M., Joiner, T. E., Rogers, M. L., & Martin, G. N. (2018). Increases in depressive symptoms, suicide-related outcomes, and suicide rates among U.S. adolescents after 2010 and links to increased new media screen time. Clinical Psychological Science, 6(1), 3-17.
Note: This is just a sample Example do not use this in your assignment.
MLA (Modern Language Association) Format
MLA (Modern Language Association) Format is as follows:
- Page Layout : Use 8.5 x 11-inch white paper, with 1-inch margins on all sides. The font should be 12-point Times New Roman or a similar serif font.
- Heading and Title : The first page of your research paper should include a heading and a title. The heading should include your name, your instructor’s name, the course title, and the date. The title should be centered and in title case (capitalizing the first letter of each important word).
- In-Text Citations : Use parenthetical citations to indicate the source of your information. The citation should include the author’s last name and the page number(s) of the source. For example: (Smith 23).
- Works Cited Page : At the end of your paper, include a Works Cited page that lists all the sources you used in your research. Each entry should include the author’s name, the title of the work, the publication information, and the medium of publication.
- Formatting Quotations : Use double quotation marks for short quotations and block quotations for longer quotations. Indent the entire quotation five spaces from the left margin.
- Formatting the Body : Use a clear and readable font and double-space your text throughout. The first line of each paragraph should be indented one-half inch from the left margin.
MLA Research Paper Template
MLA Research Paper Format Template is as follows:
- Use 8.5 x 11 inch white paper.
- Use a 12-point font, such as Times New Roman.
- Use double-spacing throughout the entire paper, including the title page and works cited page.
- Set the margins to 1 inch on all sides.
- Use page numbers in the upper right corner, beginning with the first page of text.
- Include a centered title for the research paper, using title case (capitalizing the first letter of each important word).
- Include your name, instructor’s name, course name, and date in the upper left corner, double-spaced.
In-Text Citations
- When quoting or paraphrasing information from sources, include an in-text citation within the text of your paper.
- Use the author’s last name and the page number in parentheses at the end of the sentence, before the punctuation mark.
- If the author’s name is mentioned in the sentence, only include the page number in parentheses.
Works Cited Page
- List all sources cited in alphabetical order by the author’s last name.
- Each entry should include the author’s name, title of the work, publication information, and medium of publication.
- Use italics for book and journal titles, and quotation marks for article and chapter titles.
- For online sources, include the date of access and the URL.
Here is an example of how the first page of a research paper in MLA format should look:
Headings and Subheadings
- Use headings and subheadings to organize your paper and make it easier to read.
- Use numerals to number your headings and subheadings (e.g. 1, 2, 3), and capitalize the first letter of each word.
- The main heading should be centered and in boldface type, while subheadings should be left-aligned and in italics.
- Use only one space after each period or punctuation mark.
- Use quotation marks to indicate direct quotes from a source.
- If the quote is more than four lines, format it as a block quote, indented one inch from the left margin and without quotation marks.
- Use ellipses (…) to indicate omitted words from a quote, and brackets ([…]) to indicate added words.
Works Cited Examples
- Book: Last Name, First Name. Title of Book. Publisher, Publication Year.
- Journal Article: Last Name, First Name. “Title of Article.” Title of Journal, volume number, issue number, publication date, page numbers.
- Website: Last Name, First Name. “Title of Webpage.” Title of Website, publication date, URL. Accessed date.
Here is an example of how a works cited entry for a book should look:
Smith, John. The Art of Writing Research Papers. Penguin, 2021.
MLA Research Paper Example
MLA Research Paper Format Example is as follows:
Your Professor’s Name
Course Name and Number
Date (in Day Month Year format)
Word Count (not including title page or Works Cited)
Title: The Impact of Video Games on Aggression Levels
Video games have become a popular form of entertainment among people of all ages. However, the impact of video games on aggression levels has been a subject of debate among scholars and researchers. While some argue that video games promote aggression and violent behavior, others argue that there is no clear link between video games and aggression levels. This research paper aims to explore the impact of video games on aggression levels among young adults.
Background:
The debate on the impact of video games on aggression levels has been ongoing for several years. According to the American Psychological Association, exposure to violent media, including video games, can increase aggression levels in children and adolescents. However, some researchers argue that there is no clear evidence to support this claim. Several studies have been conducted to examine the impact of video games on aggression levels, but the results have been mixed.
Methodology:
This research paper used a quantitative research approach to examine the impact of video games on aggression levels among young adults. A sample of 100 young adults between the ages of 18 and 25 was selected for the study. The participants were asked to complete a questionnaire that measured their aggression levels and their video game habits.
The results of the study showed that there was a significant correlation between video game habits and aggression levels among young adults. The participants who reported playing violent video games for more than 5 hours per week had higher aggression levels than those who played less than 5 hours per week. The study also found that male participants were more likely to play violent video games and had higher aggression levels than female participants.
The findings of this study support the claim that video games can increase aggression levels among young adults. However, it is important to note that the study only examined the impact of video games on aggression levels and did not take into account other factors that may contribute to aggressive behavior. It is also important to note that not all video games promote violence and aggression, and some games may have a positive impact on cognitive and social skills.
Conclusion :
In conclusion, this research paper provides evidence to support the claim that video games can increase aggression levels among young adults. However, it is important to conduct further research to examine the impact of video games on other aspects of behavior and to explore the potential benefits of video games. Parents and educators should be aware of the potential impact of video games on aggression levels and should encourage young adults to engage in a variety of activities that promote cognitive and social skills.
Works Cited:
- American Psychological Association. (2017). Violent Video Games: Myths, Facts, and Unanswered Questions. Retrieved from https://www.apa.org/news/press/releases/2017/08/violent-video-games
- Ferguson, C. J. (2015). Do Angry Birds make for angry children? A meta-analysis of video game influences on children’s and adolescents’ aggression, mental health, prosocial behavior, and academic performance. Perspectives on Psychological Science, 10(5), 646-666.
- Gentile, D. A., Swing, E. L., Lim, C. G., & Khoo, A. (2012). Video game playing, attention problems, and impulsiveness: Evidence of bidirectional causality. Psychology of Popular Media Culture, 1(1), 62-70.
- Greitemeyer, T. (2014). Effects of prosocial video games on prosocial behavior. Journal of Personality and Social Psychology, 106(4), 530-548.
Chicago/Turabian Style
Chicago/Turabian Formate is as follows:
- Margins : Use 1-inch margins on all sides of the paper.
- Font : Use a readable font such as Times New Roman or Arial, and use a 12-point font size.
- Page numbering : Number all pages in the upper right-hand corner, beginning with the first page of text. Use Arabic numerals.
- Title page: Include a title page with the title of the paper, your name, course title and number, instructor’s name, and the date. The title should be centered on the page and in title case (capitalize the first letter of each word).
- Headings: Use headings to organize your paper. The first level of headings should be centered and in boldface or italics. The second level of headings should be left-aligned and in boldface or italics. Use as many levels of headings as necessary to organize your paper.
- In-text citations : Use footnotes or endnotes to cite sources within the text of your paper. The first citation for each source should be a full citation, and subsequent citations can be shortened. Use superscript numbers to indicate footnotes or endnotes.
- Bibliography : Include a bibliography at the end of your paper, listing all sources cited in your paper. The bibliography should be in alphabetical order by the author’s last name, and each entry should include the author’s name, title of the work, publication information, and date of publication.
- Formatting of quotations: Use block quotations for quotations that are longer than four lines. Indent the entire quotation one inch from the left margin, and do not use quotation marks. Single-space the quotation, and double-space between paragraphs.
- Tables and figures: Use tables and figures to present data and illustrations. Number each table and figure sequentially, and provide a brief title for each. Place tables and figures as close as possible to the text that refers to them.
- Spelling and grammar : Use correct spelling and grammar throughout your paper. Proofread carefully for errors.
Chicago/Turabian Research Paper Template
Chicago/Turabian Research Paper Template is as folows:
Title of Paper
Name of Student
Professor’s Name
I. Introduction
A. Background Information
B. Research Question
C. Thesis Statement
II. Literature Review
A. Overview of Existing Literature
B. Analysis of Key Literature
C. Identification of Gaps in Literature
III. Methodology
A. Research Design
B. Data Collection
C. Data Analysis
IV. Results
A. Presentation of Findings
B. Analysis of Findings
C. Discussion of Implications
V. Conclusion
A. Summary of Findings
B. Implications for Future Research
C. Conclusion
VI. References
A. Bibliography
B. In-Text Citations
VII. Appendices (if necessary)
A. Data Tables
C. Additional Supporting Materials
Chicago/Turabian Research Paper Example
Title: The Impact of Social Media on Political Engagement
Name: John Smith
Class: POLS 101
Professor: Dr. Jane Doe
Date: April 8, 2023
I. Introduction:
Social media has become an integral part of our daily lives. People use social media platforms like Facebook, Twitter, and Instagram to connect with friends and family, share their opinions, and stay informed about current events. With the rise of social media, there has been a growing interest in understanding its impact on various aspects of society, including political engagement. In this paper, I will examine the relationship between social media use and political engagement, specifically focusing on how social media influences political participation and political attitudes.
II. Literature Review:
There is a growing body of literature on the impact of social media on political engagement. Some scholars argue that social media has a positive effect on political participation by providing new channels for political communication and mobilization (Delli Carpini & Keeter, 1996; Putnam, 2000). Others, however, suggest that social media can have a negative impact on political engagement by creating filter bubbles that reinforce existing beliefs and discourage political dialogue (Pariser, 2011; Sunstein, 2001).
III. Methodology:
To examine the relationship between social media use and political engagement, I conducted a survey of 500 college students. The survey included questions about social media use, political participation, and political attitudes. The data was analyzed using descriptive statistics and regression analysis.
Iv. Results:
The results of the survey indicate that social media use is positively associated with political participation. Specifically, respondents who reported using social media to discuss politics were more likely to have participated in a political campaign, attended a political rally, or contacted a political representative. Additionally, social media use was found to be associated with more positive attitudes towards political engagement, such as increased trust in government and belief in the effectiveness of political action.
V. Conclusion:
The findings of this study suggest that social media has a positive impact on political engagement, by providing new opportunities for political communication and mobilization. However, there is also a need for caution, as social media can also create filter bubbles that reinforce existing beliefs and discourage political dialogue. Future research should continue to explore the complex relationship between social media and political engagement, and develop strategies to harness the potential benefits of social media while mitigating its potential negative effects.
Vii. References:
- Delli Carpini, M. X., & Keeter, S. (1996). What Americans know about politics and why it matters. Yale University Press.
- Pariser, E. (2011). The filter bubble: What the Internet is hiding from you. Penguin.
- Putnam, R. D. (2000). Bowling alone: The collapse and revival of American community. Simon & Schuster.
- Sunstein, C. R. (2001). Republic.com. Princeton University Press.
IEEE (Institute of Electrical and Electronics Engineers) Format
IEEE (Institute of Electrical and Electronics Engineers) Research Paper Format is as follows:
- Title : A concise and informative title that accurately reflects the content of the paper.
- Abstract : A brief summary of the paper, typically no more than 250 words, that includes the purpose of the study, the methods used, the key findings, and the main conclusions.
- Introduction : An overview of the background, context, and motivation for the research, including a clear statement of the problem being addressed and the objectives of the study.
- Literature review: A critical analysis of the relevant research and scholarship on the topic, including a discussion of any gaps or limitations in the existing literature.
- Methodology : A detailed description of the methods used to collect and analyze data, including any experiments or simulations, data collection instruments or procedures, and statistical analyses.
- Results : A clear and concise presentation of the findings, including any relevant tables, graphs, or figures.
- Discussion : A detailed interpretation of the results, including a comparison of the findings with previous research, a discussion of the implications of the results, and any recommendations for future research.
- Conclusion : A summary of the key findings and main conclusions of the study.
- References : A list of all sources cited in the paper, formatted according to IEEE guidelines.
In addition to these elements, an IEEE research paper should also follow certain formatting guidelines, including using 12-point font, double-spaced text, and numbered headings and subheadings. Additionally, any tables, figures, or equations should be clearly labeled and referenced in the text.
AMA (American Medical Association) Style
AMA (American Medical Association) Style Research Paper Format:
- Title Page: This page includes the title of the paper, the author’s name, institutional affiliation, and any acknowledgments or disclaimers.
- Abstract: The abstract is a brief summary of the paper that outlines the purpose, methods, results, and conclusions of the study. It is typically limited to 250 words or less.
- Introduction: The introduction provides a background of the research problem, defines the research question, and outlines the objectives and hypotheses of the study.
- Methods: The methods section describes the research design, participants, procedures, and instruments used to collect and analyze data.
- Results: The results section presents the findings of the study in a clear and concise manner, using graphs, tables, and charts where appropriate.
- Discussion: The discussion section interprets the results, explains their significance, and relates them to previous research in the field.
- Conclusion: The conclusion summarizes the main points of the paper, discusses the implications of the findings, and suggests future research directions.
- References: The reference list includes all sources cited in the paper, listed in alphabetical order by author’s last name.
In addition to these sections, the AMA format requires that authors follow specific guidelines for citing sources in the text and formatting their references. The AMA style uses a superscript number system for in-text citations and provides specific formats for different types of sources, such as books, journal articles, and websites.
Harvard Style
Harvard Style Research Paper format is as follows:
- Title page: This should include the title of your paper, your name, the name of your institution, and the date of submission.
- Abstract : This is a brief summary of your paper, usually no more than 250 words. It should outline the main points of your research and highlight your findings.
- Introduction : This section should introduce your research topic, provide background information, and outline your research question or thesis statement.
- Literature review: This section should review the relevant literature on your topic, including previous research studies, academic articles, and other sources.
- Methodology : This section should describe the methods you used to conduct your research, including any data collection methods, research instruments, and sampling techniques.
- Results : This section should present your findings in a clear and concise manner, using tables, graphs, and other visual aids if necessary.
- Discussion : This section should interpret your findings and relate them to the broader research question or thesis statement. You should also discuss the implications of your research and suggest areas for future study.
- Conclusion : This section should summarize your main findings and provide a final statement on the significance of your research.
- References : This is a list of all the sources you cited in your paper, presented in alphabetical order by author name. Each citation should include the author’s name, the title of the source, the publication date, and other relevant information.
In addition to these sections, a Harvard Style research paper may also include a table of contents, appendices, and other supplementary materials as needed. It is important to follow the specific formatting guidelines provided by your instructor or academic institution when preparing your research paper in Harvard Style.
Vancouver Style
Vancouver Style Research Paper format is as follows:
The Vancouver citation style is commonly used in the biomedical sciences and is known for its use of numbered references. Here is a basic format for a research paper using the Vancouver citation style:
- Title page: Include the title of your paper, your name, the name of your institution, and the date.
- Abstract : This is a brief summary of your research paper, usually no more than 250 words.
- Introduction : Provide some background information on your topic and state the purpose of your research.
- Methods : Describe the methods you used to conduct your research, including the study design, data collection, and statistical analysis.
- Results : Present your findings in a clear and concise manner, using tables and figures as needed.
- Discussion : Interpret your results and explain their significance. Also, discuss any limitations of your study and suggest directions for future research.
- References : List all of the sources you cited in your paper in numerical order. Each reference should include the author’s name, the title of the article or book, the name of the journal or publisher, the year of publication, and the page numbers.
ACS (American Chemical Society) Style
ACS (American Chemical Society) Style Research Paper format is as follows:
The American Chemical Society (ACS) Style is a citation style commonly used in chemistry and related fields. When formatting a research paper in ACS Style, here are some guidelines to follow:
- Paper Size and Margins : Use standard 8.5″ x 11″ paper with 1-inch margins on all sides.
- Font: Use a 12-point serif font (such as Times New Roman) for the main text. The title should be in bold and a larger font size.
- Title Page : The title page should include the title of the paper, the authors’ names and affiliations, and the date of submission. The title should be centered on the page and written in bold font. The authors’ names should be centered below the title, followed by their affiliations and the date.
- Abstract : The abstract should be a brief summary of the paper, no more than 250 words. It should be on a separate page and include the title of the paper, the authors’ names and affiliations, and the text of the abstract.
- Main Text : The main text should be organized into sections with headings that clearly indicate the content of each section. The introduction should provide background information and state the research question or hypothesis. The methods section should describe the procedures used in the study. The results section should present the findings of the study, and the discussion section should interpret the results and provide conclusions.
- References: Use the ACS Style guide to format the references cited in the paper. In-text citations should be numbered sequentially throughout the text and listed in numerical order at the end of the paper.
- Figures and Tables: Figures and tables should be numbered sequentially and referenced in the text. Each should have a descriptive caption that explains its content. Figures should be submitted in a high-quality electronic format.
- Supporting Information: Additional information such as data, graphs, and videos may be included as supporting information. This should be included in a separate file and referenced in the main text.
- Acknowledgments : Acknowledge any funding sources or individuals who contributed to the research.
ASA (American Sociological Association) Style
ASA (American Sociological Association) Style Research Paper format is as follows:
- Title Page: The title page of an ASA style research paper should include the title of the paper, the author’s name, and the institutional affiliation. The title should be centered and should be in title case (the first letter of each major word should be capitalized).
- Abstract: An abstract is a brief summary of the paper that should appear on a separate page immediately following the title page. The abstract should be no more than 200 words in length and should summarize the main points of the paper.
- Main Body: The main body of the paper should begin on a new page following the abstract page. The paper should be double-spaced, with 1-inch margins on all sides, and should be written in 12-point Times New Roman font. The main body of the paper should include an introduction, a literature review, a methodology section, results, and a discussion.
- References : The reference section should appear on a separate page at the end of the paper. All sources cited in the paper should be listed in alphabetical order by the author’s last name. Each reference should include the author’s name, the title of the work, the publication information, and the date of publication.
- Appendices : Appendices are optional and should only be included if they contain information that is relevant to the study but too lengthy to be included in the main body of the paper. If you include appendices, each one should be labeled with a letter (e.g., Appendix A, Appendix B, etc.) and should be referenced in the main body of the paper.
APSA (American Political Science Association) Style
APSA (American Political Science Association) Style Research Paper format is as follows:
- Title Page: The title page should include the title of the paper, the author’s name, the name of the course or instructor, and the date.
- Abstract : An abstract is typically not required in APSA style papers, but if one is included, it should be brief and summarize the main points of the paper.
- Introduction : The introduction should provide an overview of the research topic, the research question, and the main argument or thesis of the paper.
- Literature Review : The literature review should summarize the existing research on the topic and provide a context for the research question.
- Methods : The methods section should describe the research methods used in the paper, including data collection and analysis.
- Results : The results section should present the findings of the research.
- Discussion : The discussion section should interpret the results and connect them back to the research question and argument.
- Conclusion : The conclusion should summarize the main findings and implications of the research.
- References : The reference list should include all sources cited in the paper, formatted according to APSA style guidelines.
In-text citations in APSA style use parenthetical citation, which includes the author’s last name, publication year, and page number(s) if applicable. For example, (Smith 2010, 25).
About the author
Muhammad Hassan
Researcher, Academic Writer, Web developer
You may also like

How to Cite Research Paper – All Formats and...

Delimitations in Research – Types, Examples and...

Research Design – Types, Methods and Examples

Research Paper Title – Writing Guide and Example

Research Paper Introduction – Writing Guide and...

Research Paper Conclusion – Writing Guide and...
Purdue Online Writing Lab Purdue OWL® College of Liberal Arts
Writing a Research Paper

Welcome to the Purdue OWL
This page is brought to you by the OWL at Purdue University. When printing this page, you must include the entire legal notice.
Copyright ©1995-2018 by The Writing Lab & The OWL at Purdue and Purdue University. All rights reserved. This material may not be published, reproduced, broadcast, rewritten, or redistributed without permission. Use of this site constitutes acceptance of our terms and conditions of fair use.

The Research Paper
There will come a time in most students' careers when they are assigned a research paper. Such an assignment often creates a great deal of unneeded anxiety in the student, which may result in procrastination and a feeling of confusion and inadequacy. This anxiety frequently stems from the fact that many students are unfamiliar and inexperienced with this genre of writing. Never fear—inexperience and unfamiliarity are situations you can change through practice! Writing a research paper is an essential aspect of academics and should not be avoided on account of one's anxiety. In fact, the process of writing a research paper can be one of the more rewarding experiences one may encounter in academics. What is more, many students will continue to do research throughout their careers, which is one of the reasons this topic is so important.
Becoming an experienced researcher and writer in any field or discipline takes a great deal of practice. There are few individuals for whom this process comes naturally. Remember, even the most seasoned academic veterans have had to learn how to write a research paper at some point in their career. Therefore, with diligence, organization, practice, a willingness to learn (and to make mistakes!), and, perhaps most important of all, patience, students will find that they can achieve great things through their research and writing.
The pages in this section cover the following topic areas related to the process of writing a research paper:
- Genre - This section will provide an overview for understanding the difference between an analytical and argumentative research paper.
- Choosing a Topic - This section will guide the student through the process of choosing topics, whether the topic be one that is assigned or one that the student chooses themselves.
- Identifying an Audience - This section will help the student understand the often times confusing topic of audience by offering some basic guidelines for the process.
- Where Do I Begin - This section concludes the handout by offering several links to resources at Purdue, and also provides an overview of the final stages of writing a research paper.
An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- Behav Sci (Basel)

Work Motivation: The Roles of Individual Needs and Social Conditions
Thuy thi diem vo.
1 Department of Business Administration, National Taiwan University of Science and Technology, No. 43, Section 4, Keelung Road, Da’an District, Taipei City 106335, Taiwan; wt.ude.tsutn.liam@31880701d (T.T.D.V.); wt.ude.tsutn.liam@nehcwc (C.-W.C.)
Kristine Velasquez Tuliao
2 Graduate Institute of Human Resource Management, National Central University, No. 300, Zhongda Road, Zhongli District, Taoyuan City 320317, Taiwan
Chung-Wen Chen
Associated data.
The data that support this study are publicly available.
Work motivation plays a vital role in the development of organizations, as it increases employee productivity and effectiveness. To expand insights into individuals’ work motivation, the authors investigated the influence of individuals’ competence, autonomy, and social relatedness on their work motivation. Additionally, the country-level moderating factors of those individual-level associations were examined. Hierarchical linear modeling (HLM) was used to analyze data from 32,614 individuals from 25 countries, obtained from the World Values Survey (WVS). Findings showed that autonomy and social relatedness positively impacted work motivation, while competence negatively influenced work motivation. Moreover, the individual-level associations were moderated by the country-level religious affiliation, political participation, humane orientation, and in-group collectivism. Contributions, practical implications, and directions for further research were then discussed.
1. Introduction
Work motivation is considered an essential catalyst for the success of organizations, as it promotes employees’ effective performance. To achieve an organization’s objectives, the employer depends on the performance of their employees [ 1 ]. However, insufficiently motivated employees perform poorly despite being skillful [ 1 , 2 ]. Employers, therefore, need their employees to work with complete motivation rather than just showing up at their workplaces [ 3 ]. Work motivation remains a vital factor in organizational psychology, as it helps explain the causes of individual conduct in organizations [ 4 ]. Consequently, studies on the factors that encourage work motivation can contribute to the theoretical underpinnings on the roots of individual and practical social conditions that optimize individuals’ performance and wellness [ 5 ].
Several decades of research have endeavored to explain the dynamics that initiate work-related behavior. The primary factor examining this aspect is motivation, as it explains why individuals do what they do [ 6 ]. The basic psychological needs have represented a vital rationalization of individual differences in work motivation. Psychological needs are considered natural psychological nutrients and humans’ inner resources. They have a close relationship with individual conduct and have a strong explicit meaning for work performance [ 7 , 8 ]. Different needs are essential drivers of individual functioning due to the satisfaction derived from dealing with them [ 9 ]. In addition to individual-level antecedents, the social context has also been regarded to have implications for work motivation. Social exchange and interaction among individuals accentuate the importance of work motivation as something to be studied with consideration of contextual factors [ 10 ].
Significant contributions have been made to the socio-psychological perspective of work motivation ( Table 1 ). However, current literature shows three deficiencies. First, over 150 papers utilize the key approaches of psychological needs to justify motivational processes in the workplace [ 11 ], which justifies the vital role of psychological needs in interpreting individual work motivation. The association between psychological needs and work motivation has often been implicitly assumed; however, the influence of psychological needs on work motivation has been inadequately tested [ 8 ]. The verification of the extent and the direction of influence will provide a better understanding of, and offer distinct implications for, the facilitation of work motivation. In examining the influence of psychological needs on work motivation, this paper mainly focuses on the intrinsic aspect of motivation. The study of Alzahrani et al. (2018) [ 12 ] argued that although intrinsic motivation is more efficient than extrinsic motivation, researchers have mostly neglected it.
Several investigated predictors of work motivation in general and intrinsic motivation in particular.
Second, there is no study examining the country-level moderating effects of social conditions and national cultures on individual relationships between psychological needs and work motivation. Pinder (2014) [ 20 ] argued that contextual practices could influence variables at the individual level. Culture is a crucial factor influencing motivation [ 15 , 16 , 17 , 18 ]. Researchers (e.g., [ 19 ]) have further suggested that both the proximal social situations (e.g., workgroup) and the distal social situations (e.g., cultural values) in which humans operate influence their need for satisfaction and their motivation type. Intrinsic motivation interacts with prosocial motivation in judging work performance [ 21 ]. By including the social conditions in the framework, prosocial motivation is considered. Prosocial motivation refers to the desire to help and promote the welfare of others [ 22 , 23 ]. The study of Shao et al. (2019) [ 24 ] proposed that prosocial motivation promotes employee engagement in particular organizational tasks. Researchers often consider prosocial motivation as a pattern of intrinsic motivation [ 23 ]. This implies that when intrinsic motivation is investigated, prosocial motivation should be examined together to obtain a comprehensive understanding.
Third, there are few studies using a considerable number of cross-national samples to investigate factors influencing work motivation. A cross-cultural analysis makes the findings more objective by minimizing individual bias towards any particular culture. Therefore, the examination of the study is crucial to expanding insights on the influence of social situations on the individual associations between psychological needs and work motivation.
2. Literature Review and Hypothesis Development
2.1. work motivation: a conceptual background.
Work motivation is considered “a set of energetic forces that originate both within as well as beyond an individual’s being, to initiate work-related behavior, and to determine its form direction intensity and duration” [ 20 ]. Nicolescu and Verboncu (2008) [ 25 ] argued that work motivation contributes directly and indirectly to employees’ performance. Additionally, research (e.g., [ 26 ]) has postulated that work motivation could be seen as a source of positive energy that leads to employees’ self-recognition and self-fulfillment. Therefore, work motivation is an antecedent of the self-actualization of individuals and the achievement of organizations.
Literature has identified several models of work motivation. One of the primary models is Maslow’s (1954) [ 27 ] need hierarchy theory, which proposes that humans fulfill a set of needs, including physiological, safety and security, belongingness, esteem, and self-actualization. Additionally, Herzberg’s (1966) [ 28 ] motivation-hygiene theory proposed that work motivation is mainly influenced by the job’s intrinsic challenge and provision of opportunities for recognition and reinforcement. More contemporary models also emerged. For instance, the study of Nicolescu and Verboncu (2008) [ 25 ] has categorized the types of motivation into four pairs, including positive-negative, intrinsic-extrinsic, cognitive-affective, and economic-moral spiritual. Additionally, Ryan and Deci [ 29 ] focused on intrinsic motivation and extrinsic motivation.
With the existence of numerous factors that relate to work motivation, this paper mainly focuses on intrinsic motivation. Previous research found that emotional intelligence and interpersonal relationship quality predict individuals’ intrinsic motivation [ 14 ]. Additionally, the study of Lin (2020) [ 13 ] argued that personal factors, including age, gender, educational level, living setting, health status, and family support, impact people’s intrinsic motivation. To understand more about intrinsic motivation, the authors examined individuals’ psychological needs. Fulfillment of the basic needs is related to wellness and effective performance [ 7 ]. Since intrinsic motivation results in high-quality creativity, recognizing the factors influencing intrinsic motivation is important [ 5 ].
Although a significant number of important contributions have been made regarding intrinsic motivation, self-determination theory is of particular significance for this study. Self-determination theory (SDT) postulates that all humans possess a variety of basic psychological needs. One of the primary crucial needs is the need for competence [ 30 , 31 ], which makes individuals feel confident and effective in their actions. Additionally, the need for autonomy [ 32 ] is one of the important psychological needs, which makes people satisfied with optimal wellness and good performance obtained as a result of their own decisions. Moreover, SDT proposed the crucial importance of interpersonal relationships and how social forces can influence thoughts, emotions, and behaviors [ 33 ]. This means that the psychological need for social relatedness [ 34 ] also plays a significant role in human’s psychological traits. Individuals need to be cared for by others and care for others to perceive belongingness. The need for relatedness can motivate people to behave more socially [ 35 ].
Prior research (e.g., [ 36 ]) has explored self-determination theory and related theories as approaches to work motivation and organizational behavior. The study of Van den Broeck et al. (2010) [ 37 ] emphasized grasping autonomy, competence, and relatedness at workplaces. This paper contributes to the exhaustive understanding of intrinsic work motivation influenced by further examining the impact of these three factors on work motivation as well as the moderating effects of social contexts.
2.2. Main Effect
2.2.1. individuals’ competence and work motivation.
Competence is “the collective learning in the organization, especially how to coordinate diverse production skills and integrate multiple streams of technologies” [ 38 ]. The study of Hernández-March et al. (2009) [ 39 ] argued that a stronger competence was commonly found in university graduates rather than those without higher education. Competence has been considered a significant factor of work motivation that enhances productivity and profits. Harter’s (1983) [ 40 ] model of motivation proposed that competence enhances motivation because competence promotes flexibility for individuals [ 41 ]. Likewise, Patall et al. (2014) [ 42 ] indirectly argued that competence positively affects work motivation. Individuals become more engaged in activities that demonstrate their competence [ 6 ]. When people perceive that they are competent enough to attain goals, they generally feel confident and concentrate their efforts on achieving their objectives as soon as possible for their self-fulfillment.
Individuals’ competence positively relates to their work motivation.
2.2.2. Individuals’ Autonomy and Work Motivation
Autonomy is viewed as “self-determination, self-rule, liberty of rights, freedom of will and being one’s own person” [ 43 ]. Reeve (2006) [ 44 ] argued that autonomy is a primary theoretical approach in the study of human motivation and emotion. Autonomy denotes that certain conduct is performed with a sense of willingness [ 30 ]. Several researchers (e.g., [ 45 ]) investigated the positive relationship between individuals’ autonomy and work motivation. When humans are involved in actions because of their interest, they fully perform those activities volitionally [ 36 ]. Dickinson (1995) [ 46 ] also proposed that autonomous individuals are more highly motivated, and autonomy breeds more effective outcomes. Moreover, when individuals have a right to make their own decisions, they tend to be more considerate and responsible for those decisions, as they need to take accountability for their actions. Bandura (1991) [ 47 ] has argued that humans’ ability to reflect, react, and direct their actions motivates them for future purposes. Therefore, autonomy motivates individuals to work harder and overcome difficulties to achieve their objectives.
Individuals’ autonomy positively relates to their work motivation.
2.2.3. Individuals’ Social Relatedness and Work Motivation
The psychological need for social relatedness occurs when an individual has a sense of being secure, related to, or understood by others in the social environment [ 48 ]. The relatedness need is fulfilled when humans experience the feeling of close relationships with others [ 49 ]. Researchers (e.g., [ 34 ]) have postulated that the need for relatedness reflects humans’ natural tendency to feel associated with others, such as being a member of any social groups, or to love and care as well as be loved and cared for. Prior studies have shown that social relatedness strongly impacts motivation [ 50 , 51 , 52 ]. Social relatedness offers people many opportunities to communicate with others, making them more motivated at the workplace, aligning them with the group’s shared objectives. Marks (1974) [ 53 ] suggested that social relatedness encourages individuals to focus on community welfare as a reference for their behavior, resulting in enhanced work motivation. Moreover, when individuals feel that they relate to and are cared for by others, their motivation can be maximized since their relatedness need is fulfilled [ 54 ]. Therefore, establishing close relationships with others plays a vital role in promoting human motivation [ 55 ]. When people perceive that they are cared for and loved by others, they tend to create positive outcomes for common benefits to deserve the kindness received, thereby motivating them to work harder.
Individuals’ social relatedness positively relates to their work motivation.
Aside from exploring the influence of psychological needs on work motivation, this paper also considers country-level factors. Previous research (e.g., [ 56 ]) has examined the influence of social institutions and national cultures on work motivation. However, the moderating effects of country-level factors have to be investigated, given the contextual impacts on individual needs, attitudes, and behavior. Although social conditions provide the most common interpretation for nation-level variance in individual work behaviors [ 57 ], few cross-national studies examine social conditions and individual work behaviors [ 56 ]. Hence, this paper investigates the moderating effects, including religious affiliation, political participation, humane orientation, and in-group collectivism, on the psychological needs-work motivation association.
A notable theory to explain the importance of contextual factors in work motivation that is customarily linked with SDT is the concept of prosocial motivation. Prosocial motivation suggests that individuals have the desire to expend efforts in safeguarding and promoting others’ well-being [ 58 , 59 ]. It is proposed that prosocial motivation strengthens endurance, performance, and productivity, as well as generates creativity that encourages individuals to develop valuable and novel ideas [ 21 , 60 ]. Prosocial motivation is found to interact with intrinsic motivation in influencing positive work outcomes [ 21 , 61 ]. However, there are few studies examining the effects of prosocial motivation on work motivation [ 62 ].
Utilizing the concept of prosocial motivation and examining it on a country-level, this paper suggests that prosocial factors promote basic psychological needs satisfaction that reinforces motivational processes at work. Therefore, prosocial behaviors and values may enhance the positive impact of individuals’ basic psychological needs, including competence, autonomy, and social relatedness, on work motivation.
2.3. Moderating Effects
2.3.1. religious affiliation.
Religions manifest values that are usually employed as grounds to investigate what is right and wrong [ 63 ]. Religious affiliation is considered prosocial because it satisfies the need for belongingness and upholds collective well-being through gatherings to worship, seek assistance, and offer comfort within religious communities. Hence, religious affiliation promotes the satisfaction of individuals’ psychological needs, which directs motivation at work and life in general. Research (e.g., [ 64 ]) has argued that religious affiliation is an essential motivational component given its impact on psychological processes. The study of Simon and Primavera (1972) [ 65 ] investigated the relationship between religious affiliation and work motivation. To humans characterized by competence, autonomy, and social relatedness, attachment to religious principles increases their motivation to accomplish organizational goals. Religious membership will increase the influence of psychological needs on work motivation. The tendency of individuals affiliated with any religion to be demotivated is lower compared to those who are not. Individuals with religious affiliations also tend to work harder as the virtue of hard work is aligned with religious principles. Accordingly, religious affiliation may enhance the positive association between individuals’ psychological needs and work motivation.
2.3.2. Political Participation
Political participation, indicated by people’s voting habits, plays a crucial role in ensuring citizens’ well-being and security [ 66 ]. Political participation encourages shared beliefs and collective goals among individuals [ 67 ]. The communication and interaction among people help them grasp the government’s developmental strategies, motivating them to work harder. Political participation is a collective pursuit that makes societal members feel more confident, socially related, and motivated at work to achieve communal targets. Increased political participation reinforces effective public policy to enhance its members’ welfare, congruent with the perspectives of prosocial motivation. The prosocial values and behaviors derived from political participation satisfy human needs and interact positively with intrinsic motivation. Therefore, political participation may strengthen the positive influence of individuals’ competence, autonomy, and social relatedness on work motivation. Conversely, poor political participation is perceived as a separation from the society that may lead to demotivation. In a society with poor political participation, an individualistic mentality is encouraged, thereby decreasing the desire to pursue cooperative endeavors.
2.3.3. Humane Orientation
GLOBE characterizes humane orientation as “the degree to which an organization or society encourages and rewards individuals for being fair, altruistic, generous, caring, and kind to others” [ 68 ]. Research (e.g., [ 69 , 70 ]) has argued that a high humane orientation encourages members to develop a strong sense of belonging, commit to fair treatment, and manifest benevolence. The desire to help others or enhance others’ well-being indicates prosocial values and behaviors [ 71 , 72 ]. Since humane orientation is correlated with philanthropy and promotes good relations, this cultural value may enhance work motivation. Fairness, which is derived from a humane-oriented society, is one of the most vital influences on work motivation [ 1 ]. Moreover, altruism, promoted by humane-oriented societies, encourages individuals to sacrifice individual interests for shared benefits. Altruism then encourages attachment to others’ welfare and increases resources needed for prosocial behaviors such as work [ 73 , 74 ]. Members of humane-oriented countries view work in a positive light—it is an opportunity for them to perform altruistic behaviors and engage in collective actions. Therefore, people are more likely to work harder for common interests in humane-oriented societies. In such conditions, individuals with competence, autonomy, and social relatedness will be more motivated to work. By contrast, a less humane-oriented society gives prominence to material wealth and personal enjoyment [ 75 ]. Although this may be perceived as a positive influence on the association between psychological needs and work motivation, such an individualistic mindset works against the prosocial factors that further motivate individuals.
2.3.4. In-Group Collectivism
House et al. (2004) [ 68 ] defined in-group collectivism as “the degree to which individuals express pride, loyalty, and cohesiveness in their organizations or families”. Collectivistic cultures indicate the need for individuals to rely on group membership for identification [ 76 ]. High collectivism enhances equity, solidarity, loyalty, and encouragement [ 77 , 78 ]. Humans living in a collectivist culture are interdependent and recognize their responsibilities towards each other [ 79 ]. In-group collectivism transfers the concepts of social engagement, interdependence with others, and care for the group over the self (e.g., [ 79 , 80 , 81 ], thereby motivating individuals to work harder for the common interests. Oyserman et al. (2002) [ 82 ] have further argued that individualistic values encourage an independent personality, whereas collectivistic values form an interdependent one. Therefore, in-group collectivism is a prosocial value that emphasizes the importance of reciprocal relationships and encourages people to work harder to benefit the group. By contrast, low collectivism promotes individual interests and personal well-being while neglecting the value of having strong relations with others [ 70 ]. Considering that in-group collectivism promotes individuals’ prosocial behaviors of individuals, people who are competent, autonomous, and socially related to collective societies are less likely to be demotivated at the workplace. Consequently, in-group collectivism may intensify the positive influence of individuals’ competence, autonomy, and social relatedness on their work motivation.
(a–d): The positive relationship between individuals’ competence and their work motivation is enhanced as religious affiliation (a), political participation (b), humane orientation (c), and in-group collectivism (d) increase.
(a–d): The positive relationship between individuals’ autonomy and their work motivation is enhanced as religious affiliation (a), political participation (b), humane orientation (c), and in-group collectivism (d) increase.
(a–d): The positive relationship between individuals’ social relatedness and their work motivation is enhanced as religious affiliation (a), political participation (b), humane orientation (c), and in-group collectivism (d) increase.
3.1. Sample
The data came from the seventh wave (2017–2021) of the World Values Survey (WVS) [ 83 ], which examines humans’ beliefs and values. This survey is performed every five years to explore changes in people’s values and perceptions. Face-to-face interviews, or phone interviews for remote areas, were conducted by local organizations. Almost 90 percent of the world’s population is represented in the WVS. At least 1000 individuals were selected as respondents to exhibit each nation’s population. Further information regarding the WVS can be reached at the WVS website ( http://www.worldvaluessurvey.org , accessed on 14 October 2021).
The samples of this study were based on the availability of national-level data for the moderators and individual-level data for the measures of independent and dependent variables. Respondents without answers on the individual measures and corresponding country-level data were excluded from the analysis. The final data included 32,614 respondents in 25 countries aged 18 and above. The 25 countries included Argentina, Australia, Brazil, China, Colombia, Ecuador, Egypt, Germany, Greece, Guatemala, Hong Kong, Indonesia, Iran, Japan, Kazakhstan, Malaysia, Mexico, New Zealand, Philippines, Russia, South Korea, Taiwan, Thailand, Turkey, and the USA.
3.2. Dependent Variable
Consistent with previous researchers (e.g., [ 84 ]), the authors used four items to gauge individual work motivation, namely “Indicate how important work is in your life”, “People who do not work turn lazy”, “Work is a duty towards society”, and “Work should always come first, even if it means less spare”. The first item was measured on a scale from 1 to 4, in which lower scores indicate a higher level of work importance. The other three items were gauged on a scale from 1 to 5 (1 indicating strongly agree and 5 indicating strongly disagree). The scores for each item were reverse coded, and the mean scores were computed so that higher scores indicate greater work motivation.
3.3. Independent Variables
The independent variables of this study include individuals’ competence, autonomy, and social relatedness. First, people’s competence was measured by the item “What is the highest educational level that you attained” on a scale from 0 to 8, in which higher scores indicate a higher level of educational attainment. The authors used the item to gauge individual competence, as a capacity for learning is highlighted in the examination of competence [ 39 ]. Second, a scale from 1 to 10 was utilized to measure the item “How much freedom of choice and control”, which represented individual autonomy (1 indicating no choice at all and 10 indicating a great deal of choice). The authors used the item to gauge people’s autonomy as this item indicates the degree to which individual can make their own decisions. Finally, the individual’s social relatedness was gauged by twelve items, representing twelve types of organizations where individuals are active/inactive members or do not belong. The twelve items were measured on a scale from 0 to 2 (0 indicating do not belong, 1 indicating inactive member, and 2 indicating active member). The mean score of the twelve items represents the individual’s social relatedness. The membership in organizations represents social relatedness, as this indicates the reciprocal relationship between the individual and the organization through their mutual rights, responsibilities, and obligations towards each other [ 85 ].
3.4. Moderators
The four country-level moderators in this study were religious affiliation, political participation, humane orientation, and in-group collectivism. Similar to prior research (e.g., [ 86 ]), the authors used the percentage of the country’s population with religious affiliation obtained from Pew Research Center 2015 [ 87 ]. Secondly, the index of voter turnout collected from the International Institute for Democracy and Electoral Assistance [ 88 ] was utilized to gauge political participation. Voting habits are an indicator of an individual’s presence in their country’s life, and a nation with a high index of voter turnout illustrates its substantial degree of political participation [ 89 ]. Finally, two cultural values, including humane orientation and in-group collectivism, were obtained from the GLOBE study [ 68 ]. The authors used scores on cultural practices as the moderators for this study because they indicate the actual behaviors as “the way things are done in this culture” [ 68 ].
3.5. Control Variables
Several individual-level and country-level elements related to the dependent variable were considered control variables. The effects of gender, marital status, age, and income level were accounted for, as these four variables are basic personal factors that may impact individual’s motivation [ 90 ]. Gender (1 indicating male and 0 indicating female) and marital status (1 indicating married and 0 indicating other status) were dummy coded. Moreover, age was measured in years, while income level was gauged using a scale from 1 representing the lowest group to 10 representing the highest group. Along with the above individual-level controls, education and family strength were treated as country-level control variables. Education and family are primary institutions that shape individuals’ motivation [ 91 , 92 ]. Similar to prior researchers (e.g., [ 93 ]), education was computed as two-thirds of the adult literacy rate attained from the UNESCO Institute for Statistics 2020 [ 94 ] and one-third of the mean years of schooling obtained from the Human Development Report 2020 [ 95 ]. This score is commonly approved as representing access to education in a country [ 42 ]. Regarding family strength, the score was quantified by the ratio of divorces to marriages per 1000 members of the population consistent with previous researchers (e.g., [ 93 ]). The data was obtained from the United Nations Demographic Yearbook [ 96 ].
3.6. Measurement and Analysis
To perform the descriptive statistics, cross-level correlations, scale reliability, confirmatory factor analysis, convergent validity, and discriminant validity, the authors utilized SPSS software.
The framework of this study considers independent variables, dependent variables, and moderators at different levels. Thus, the authors used a hierarchical linear model (HLM) [ 97 ] to test the hypotheses. HLM was defined as a “complex form of ordinary least squares (OLS) regression that is used to analyze variance in the outcome variables when the predictor variables are at varying hierarchical levels” [ 98 ]. This technique evaluates the impacts of higher-level outcomes on lower-level ones while preserving an appropriate degree of analysis [ 99 ]. HLM has been employed in several cross-level studies (e.g., [ 100 , 101 ]).
Table 2 presents a matrix of correlations and sample statistics from the individual-level to country-level variables. Table 3 and Table 4 report convergent and discriminant validity test results, respectively. Finally, Table 5 illustrates results for hypotheses testing using HLM. Three models are presented in the table: those of individual-level main effects and control variables (Model 1), those of country-level main effects (Model 2), and country-level moderating effects (Model 3).
Descriptive statistics, cross-level correlations and scale reliability a,b,c .
a n = 32,614 level 1; n = 25, level 2. b * p < 0.05, ** p < 0.01. c The reliability found in the parentheses is expressed as Cronbach’s alpha for scales with ≥four items.
Convergent validity.
Discriminant validity—Fornell and Larcker’s criterion.
* p < 0.05.
HLM results: (The DV is work motivation) a,b .
a , n = 32,614 level 1; n = 25, level 2. b , †, p < 0.10, * p < 0.05, ** p < 0.01, *** p < 0.001.
For the confirmatory factor analysis, previous research (e.g., [ 102 , 103 , 104 ]) suggested that analysis of each variable requires at least three items. Factor analysis using statistical software will provide imprecise results if there are fewer than three items per variable [ 105 ]. Therefore, the authors only performed Confirmatory Factor Analysis (CFA) for social relatedness and work motivation.
To assess the measurement, convergent and discriminant validity were tested. Composite Reliability (CR) and Average Variance Extracted (AVE) were performed to illustrate convergent validity. The study of Hair et al. (2019) [ 106 ] suggested that CR is required to be above a threshold of 0.7. On the other hand, the AVE value should be higher than a threshold of 0.5 [ 107 ]. As shown in Table 3 , CR is acceptable while AVE is slightly lower than a threshold of 0.5. Despite the limitation of AVE, the acceptable result of the discriminant validity is achieved. The discriminant validity was tested using Fornell and Larcker (1981)’s criterion [ 107 ]. This proposes that the square root of the AVE of any latent variable should be higher than its correlation with any other construct. The result of the discriminant validity test indicates that all the two latent constructs have a square root of AVE higher than its correlation with the other construct, as presented in Table 4 .
The authors argued that individuals’ competence (H1), autonomy (H2), and social relatedness (H3) positively relate to their work motivation. However, the findings only supported H2 (β2 = 0.036, p < 0.001) and H3 (β3 = 0.042, p < 0.001). In contrast, the findings presented that H1 was also significant, but in the opposite direction compared with our original prediction. The result suggests that individuals’ competence negatively relates to their work motivation.
In Hypotheses 4a–d, we proposed that higher levels of religious affiliation (4a), political participation (4b), humane orientation (4c), and in-group collectivism (4d) strengthen the relationship described in H1. However, the results only demonstrated support for the two hypotheses, H4c (γ13 = 0.032, p < 0.001) and H4d (γ14 = 0.042, p < 0.001). In contrast, the findings presented that H4a was also significant, but opposite our initial prediction. This different result proposes that a higher level of religious affiliation weakens the association between individuals’ competence and work motivation.
In Hypotheses 5a–d, the authors argued that the higher levels of religious affiliation (5a), political participation (5b), humane orientation (5c), and in-group collectivism (5d) enhance the positive relationship between individuals’ autonomy and their work motivation. However, the results only supported the two hypotheses H5b (γ22 = 0.012, p < 0.05) and H5c (γ23 = 0.012, p < 0.1), while H5a and H5d were not significant.
In Hypotheses 6a–d, the authors argued that the higher levels of religious affiliation (6a), political participation (6b), humane orientation (6c), and in-group collectivism (6d) enhance the positive relationship between individuals’ social relatedness and their work motivation. However, the results only supported H6c (γ33 = 0.019, p < 0.01). In contrast, the findings indicated that H6d was also significant, but in the opposite direction compared to our initial hypothesis. The different result suggests that higher in-group collectivism weakens the positive association between individuals’ social relatedness and work motivation. Figure 1 , Figure 2 , Figure 3 , Figure 4 and Figure 5 represent the significant moderators of the associations examined.

The association between competence and work motivation at different levels of humane orientation.

The association between competence and work motivation at different levels of in-group collectivism.

The association between autonomy and work motivation at different levels of political participation.

The association between autonomy and work motivation at different levels of humane orientation.

The association between social relatedness and work motivation at different levels of humane orientation.
Regarding the statistical results of the control variables, gender, marital status, and age consistently indicated significant positive relationships with work motivation across three models. On the other hand, family strength indicated a significant negative association to work motivation only in Model 1.
5. Discussion
The study’s objective was to examine the influence of individuals’ competence, autonomy, and social relatedness on their work motivation, as well as the impact of country-level moderators, including religious affiliation, political participation, humane orientation, and in-group collectivism on their relationships. Seven primary findings are crucial in this research. First, people’s autonomy and social relatedness positively relate to their work motivation. This result is in line with the findings of prior researchers (e.g., [ 45 , 52 ]), postulating that humans’ autonomy and social relatedness breeds work motivation. The study of Theurer et al. (2018) [ 108 ] argued that, among motivational elements, autonomy had been found to greatly predict positive work motivation. When people feel they have enough control over their activities, they are more confident and motivated to work. Along with autonomy, humans’ social relatedness promotes communal benefits, thereby motivating people to work harder for their organization. Second, the association between individual competence and work motivation is moderated by cultural values, including humane orientation and in-group collectivism. The findings are consistent with the viewpoints of prior researchers (e.g., [ 69 , 70 , 77 , 78 ]), namely that a society with higher levels of humane orientation and in-group collectivism strengthens altruism, solidarity, loyalty, and the encouragement of individuals, which results in work motivation. Consequently, there will be an increase in the differences in individuals’ competence and work motivation if they live in a society with greater humane orientation and in-group collectivism. Third, political participation and humane orientation moderate the relationship between individual autonomy and work motivation. These results are in line with the investigations of prior researchers (e.g., [18,45), which found that social circumstances and cultural practices promote people’s motivation. Accordingly, the differences in individuals’ autonomy based on their work motivation will be enhanced if they belong to nations with higher political participation and humane orientation. Fourth, the association between social relatedness and work motivation is moderated by humane orientation. Accordingly, in a humane-oriented society, the differences in individuals’ social relatedness based on their work motivation will be strengthened.
The remaining findings were contrary to the original propositions. Pinder (2014) [ 20 ] argued that it is possible to find that contextual practices can influence variables at the individual level in the opposite prediction in motivation research. Fifth, individuals’ competence negatively influences their work motivation. This finding proposes that more competent individuals are less motivated at work. One possible interpretation of this opposite result is that, when the majority of the organization members recognize individuals’ competence, these individuals may perceive that it is not necessary to devote most of their time and energy to work anymore. These individuals may believe that no matter how unwillingly they perform, they are still competent enough because of their prior achievements. Additionally, competent individuals recognize that they have already sacrificed their enjoyment of life for their previous successes; therefore, they tend to offset this by investing their valuable time in other aspects. This is consistent with other researchers’ investigations (e.g., [ 109 ]), which found that low-skilled individuals are more often compelled to engage in regular work activities and are more easily motivated than others. By contrast, highly competent individuals tend to be motivated by challenging tasks and improving themselves through further education. Sixth, the relationship between competence and work motivation is negatively moderated by religious affiliation. This finding suggests that religious affiliation weakens the association between individuals’ competence and work motivation. One possible explanation for this finding is that strong religious beliefs are the foundation for virtuous living [ 110 ]. Individuals with religious affiliation usually employ religious principles to guide their behavior, regardless of their competence. In other words, both competent and incompetent individuals tend to be more motivated at the workplace if they are affiliated with any religion, thereby diminishing the influence of competence in work motivation. Seventh, the relationship between social relatedness and work motivation is negatively moderated by in-group collectivism. This result proposes that a higher degree of in-group collectivism weakens the association between individuals’ social relatedness and work motivation. One possible explanation for this is that, under an in-group collective society, people put more weight on mutual relationships and encourage acts that may build up the solidarity of groups. Since in-group collectivism is viewed as a social attachment in which people emphasize the group over the self (e.g., [ 79 , 80 , 81 ]), individuals are fairly conscious of their responsibility to the group regardless of their social relatedness. Both socially related and unrelated individuals belonging to in-group collective cultures tend to work harder for common goals. Accordingly, the influence of individuals’ social relatedness on their work motivation is reduced.
6. Limitations and Future Research
Despite its significant contributions, this study has its limitations. The use of secondary data represents the fact that the data collection process was beyond the authors’ control. However, the collection of cross-national data is time-consuming and costly. The authors used the available data but strove for the efficient use of multilevel data. The secondary data also limited the measurement of individual-level factors based on the available data. Moreover, it is quite complex to gauge an individual’s work motivation appropriately, since personal work motivation may not be one-dimensional. Nevertheless, the authors made efforts to employ the measurements utilized by prior research. Moreover, it is complicated to measure social factors such as political participation. There are challenges in investigating social contexts due to the absence of direct measurements [ 111 ]. This compels the authors to identify substitute measurements for this study. Finally, this study covered 25 samples from 25 countries with different characteristics. Despite the attempt of this study to include the most relevant social conditions in the framework, the influence of other national differences and cultural sensitivities were not considered.
This paper directs further research considering that several frameworks and approaches should be employed to better examine motivation [ 112 ]. First, as some of the results were opposite to the original propositions based on the theoretical foundations employed, combining different concepts and approaches is necessary to enhance perspectives of psychological needs and social issues. For instance, the relationship between competence and work motivation can be further investigated by employing other theories to understand their association better. Similarly, the moderating effects of social contexts such as religious affiliation and in-group collectivism should be further examined to obtain a more in-depth comprehension of the roles of contextual circumstances and cultural values in individual-level relationships. Additionally, self-determination theory and the concept of prosocial motivation may be used to explore motivation towards specific behavior in organizations, such as organizational citizenship and proactive behaviors. Organizational context, such as rewards, training, and culture, can be considered as part of the framework to enhance the conception of work motivation.
7. Conclusions
This study has utilized a multilevel framework to examine the influence of psychological needs and social context on work motivation. Through this research, a deeper understanding of the roles of competence, autonomy, and social relatedness, as well as social situations and cultural values on work motivation, is achieved. The contrary findings call for integrating other concepts and approaches towards a more comprehensive knowledge of work motivation.
Along with the theoretical contribution, the study’s findings offer practical implications. The satisfaction of psychological needs promotes self-motivation, which creates positive outcomes. Hence, organizations can provide programs and activities to promote employees’ autonomy and social relatedness as this will enhance their work motivation. Employee empowerment can be advocated by encouraging them to make their own decisions at the workplace, providing constructive criticisms rather than instilling the fear of failure. Additionally, managers should encourage solidarity, support, and mutual care among employees. Putting more weight on employees’ fulfillment of needs will further increase employees’ motivation, thereby diminishing costs related to stress or turnover [ 50 ]. To establish a novel mechanism towards promoting work motivation in the entire nation, the government should pay attention to the political structure and conditions that encourage citizens’ participation. Additionally, a culture of humane orientation should be promoted in the workplace and society so that solidarity, kind assistance, and altruism among communities as well as among individuals can be strengthened. For instance, teamwork should be encouraged for employees to help each other overcome difficulties at the workplace or share responsibilities with their colleagues. This will motivate people to work harder for collective goals, contributing to the development of organizations.
Author Contributions
Conceptualization, T.T.D.V. and K.V.T.; data collection, T.T.D.V.; methodology, T.T.D.V. and K.V.T.; formal analysis, T.T.D.V. and K.V.T.; resources, K.V.T. and C.-W.C.; writing-original draft, T.T.D.V. and K.V.T.; writing-review, editing & proofreading, T.T.D.V., K.V.T. and C.-W.C.; visualization, K.V.T.; supervision, K.V.T. and C.-W.C.; project administration, K.V.T. All authors have read and agreed to the published version of the manuscript.
This paper does not receive funding from any individuals or organizations.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Data availability statement, conflicts of interest.
The authors declare no conflict of interest.
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations.
A new future of work: The race to deploy AI and raise skills in Europe and beyond
At a glance.
Amid tightening labor markets and a slowdown in productivity growth, Europe and the United States face shifts in labor demand, spurred by AI and automation. Our updated modeling of the future of work finds that demand for workers in STEM-related, healthcare, and other high-skill professions would rise, while demand for occupations such as office workers, production workers, and customer service representatives would decline. By 2030, in a midpoint adoption scenario, up to 30 percent of current hours worked could be automated, accelerated by generative AI (gen AI). Efforts to achieve net-zero emissions, an aging workforce, and growth in e-commerce, as well as infrastructure and technology spending and overall economic growth, could also shift employment demand.
By 2030, Europe could require up to 12 million occupational transitions, double the prepandemic pace. In the United States, required transitions could reach almost 12 million, in line with the prepandemic norm. Both regions navigated even higher levels of labor market shifts at the height of the COVID-19 period, suggesting that they can handle this scale of future job transitions. The pace of occupational change is broadly similar among countries in Europe, although the specific mix reflects their economic variations.
Businesses will need a major skills upgrade. Demand for technological and social and emotional skills could rise as demand for physical and manual and higher cognitive skills stabilizes. Surveyed executives in Europe and the United States expressed a need not only for advanced IT and data analytics but also for critical thinking, creativity, and teaching and training—skills they report as currently being in short supply. Companies plan to focus on retraining workers, more than hiring or subcontracting, to meet skill needs.
Workers with lower wages face challenges of redeployment as demand reweights toward occupations with higher wages in both Europe and the United States. Occupations with lower wages are likely to see reductions in demand, and workers will need to acquire new skills to transition to better-paying work. If that doesn’t happen, there is a risk of a more polarized labor market, with more higher-wage jobs than workers and too many workers for existing lower-wage jobs.
Choices made today could revive productivity growth while creating better societal outcomes. Embracing the path of accelerated technology adoption with proactive worker redeployment could help Europe achieve an annual productivity growth rate of up to 3 percent through 2030. However, slow adoption would limit that to 0.3 percent, closer to today’s level of productivity growth in Western Europe. Slow worker redeployment would leave millions unable to participate productively in the future of work.

Demand will change for a range of occupations through 2030, including growth in STEM- and healthcare-related occupations, among others
This report focuses on labor markets in nine major economies in the European Union along with the United Kingdom, in comparison with the United States. Technology, including most recently the rise of gen AI, along with other factors, will spur changes in the pattern of labor demand through 2030. Our study, which uses an updated version of the McKinsey Global Institute future of work model, seeks to quantify the occupational transitions that will be required and the changing nature of demand for different types of jobs and skills.
Our methodology
We used methodology consistent with other McKinsey Global Institute reports on the future of work to model trends of job changes at the level of occupations, activities, and skills. For this report, we focused our analysis on the 2022–30 period.
Our model estimates net changes in employment demand by sector and occupation; we also estimate occupational transitions, or the net number of workers that need to change in each type of occupation, based on which occupations face declining demand by 2030 relative to current employment in 2022. We included ten countries in Europe: nine EU members—the Czech Republic, Denmark, France, Germany, Italy, Netherlands, Poland, Spain, and Sweden—and the United Kingdom. For the United States, we build on estimates published in our 2023 report Generative AI and the future of work in America.
We included multiple drivers in our modeling: automation potential, net-zero transition, e-commerce growth, remote work adoption, increases in income, aging populations, technology investments, and infrastructure investments.
Two scenarios are used to bookend the work-automation model: “late” and “early.” For Europe, we modeled a “faster” scenario and a “slower” one. For the faster scenario, we use the midpoint—the arithmetical average between our late and early scenarios. For the slower scenario, we use a “mid late” trajectory, an arithmetical average between a late adoption scenario and the midpoint scenario. For the United States, we use the midpoint scenario, based on our earlier research.
We also estimate the productivity effects of automation, using GDP per full-time-equivalent (FTE) employee as the measure of productivity. We assumed that workers displaced by automation rejoin the workforce at 2022 productivity levels, net of automation, and in line with the expected 2030 occupational mix.
Amid tightening labor markets and a slowdown in productivity growth, Europe and the United States face shifts in labor demand, spurred not only by AI and automation but also by other trends, including efforts to achieve net-zero emissions, an aging population, infrastructure spending, technology investments, and growth in e-commerce, among others (see sidebar, “Our methodology”).
Our analysis finds that demand for occupations such as health professionals and other STEM-related professionals would grow by 17 to 30 percent between 2022 and 2030, (Exhibit 1).
By contrast, demand for workers in food services, production work, customer services, sales, and office support—all of which declined over the 2012–22 period—would continue to decline until 2030. These jobs involve a high share of repetitive tasks, data collection, and elementary data processing—all activities that automated systems can handle efficiently.
Up to 30 percent of hours worked could be automated by 2030, boosted by gen AI, leading to millions of required occupational transitions
By 2030, our analysis finds that about 27 percent of current hours worked in Europe and 30 percent of hours worked in the United States could be automated, accelerated by gen AI. Our model suggests that roughly 20 percent of hours worked could still be automated even without gen AI, implying a significant acceleration.
These trends will play out in labor markets in the form of workers needing to change occupations. By 2030, under the faster adoption scenario we modeled, Europe could require up to 12.0 million occupational transitions, affecting 6.5 percent of current employment. That is double the prepandemic pace (Exhibit 2). Under a slower scenario we modeled for Europe, the number of occupational transitions needed would amount to 8.5 million, affecting 4.6 percent of current employment. In the United States, required transitions could reach almost 12.0 million, affecting 7.5 percent of current employment. Unlike Europe, this magnitude of transitions is broadly in line with the prepandemic norm.
Both regions navigated even higher levels of labor market shifts at the height of the COVID-19 period. While these were abrupt and painful to many, given the forced nature of the shifts, the experience suggests that both regions have the ability to handle this scale of future job transitions.

Businesses will need a major skills upgrade
The occupational transitions noted above herald substantial shifts in workforce skills in a future in which automation and AI are integrated into the workplace (Exhibit 3). Workers use multiple skills to perform a given task, but for the purposes of our quantification, we identified the predominant skill used.
Demand for technological skills could see substantial growth in Europe and in the United States (increases of 25 percent and 29 percent, respectively, in hours worked by 2030 compared to 2022) under our midpoint scenario of automation adoption (which is the faster scenario for Europe).
Demand for social and emotional skills could rise by 11 percent in Europe and by 14 percent in the United States. Underlying this increase is higher demand for roles requiring interpersonal empathy and leadership skills. These skills are crucial in healthcare and managerial roles in an evolving economy that demands greater adaptability and flexibility.
Conversely, demand for work in which basic cognitive skills predominate is expected to decline by 14 percent. Basic cognitive skills are required primarily in office support or customer service roles, which are highly susceptible to being automated by AI. Among work characterized by these basic cognitive skills experiencing significant drops in demand are basic data processing and literacy, numeracy, and communication.
Demand for work in which higher cognitive skills predominate could also decline slightly, according to our analysis. While creativity is expected to remain highly sought after, with a potential increase of 12 percent by 2030, work activities characterized by other advanced cognitive skills such as advanced literacy and writing, along with quantitative and statistical skills, could decline by 19 percent.
Demand for physical and manual skills, on the other hand, could remain roughly level with the present. These skills remain the largest share of workforce skills, representing about 30 percent of total hours worked in 2022. Growth in demand for these skills between 2022 and 2030 could come from the build-out of infrastructure and higher investment in low-emissions sectors, while declines would be in line with continued automation in production work.
Business executives report skills shortages today and expect them to worsen
A survey we conducted of C-suite executives in five countries shows that companies are already grappling with skills challenges, including a skills mismatch, particularly in technological, higher cognitive, and social and emotional skills: about one-third of the more than 1,100 respondents report a shortfall in these critical areas. At the same time, a notable number of executives say they have enough employees with basic cognitive skills and, to a lesser extent, physical and manual skills.
Within technological skills, companies in our survey reported that their most significant shortages are in advanced IT skills and programming, advanced data analysis, and mathematical skills. Among higher cognitive skills, significant shortfalls are seen in critical thinking and problem structuring and in complex information processing. About 40 percent of the executives surveyed pointed to a shortage of workers with these skills, which are needed for working alongside new technologies (Exhibit 4).

Companies see retraining as key to acquiring needed skills and adapting to the new work landscape
Surveyed executives expect significant changes to their workforce skill levels and worry about not finding the right skills by 2030. More than one in four survey respondents said that failing to capture the needed skills could directly harm financial performance and indirectly impede their efforts to leverage the value from AI.
To acquire the skills they need, companies have three main options: retraining, hiring, and contracting workers. Our survey suggests that executives are looking at all three options, with retraining the most widely reported tactic planned to address the skills mismatch: on average, out of companies that mentioned retraining as one of their tactics to address skills mismatch, executives said they would retrain 32 percent of their workforce. The scale of retraining needs varies in degree. For example, respondents in the automotive industry expect 36 percent of their workforce to be retrained, compared with 28 percent in the financial services industry. Out of those who have mentioned hiring or contracting as their tactics to address the skills mismatch, executives surveyed said they would hire an average of 23 percent of their workforce and contract an average of 18 percent.
Occupational transitions will affect high-, medium-, and low-wage workers differently
All ten European countries we examined for this report may see increasing demand for top-earning occupations. By contrast, workers in the two lowest-wage-bracket occupations could be three to five times more likely to have to change occupations compared to the top wage earners, our analysis finds. The disparity is much higher in the United States, where workers in the two lowest-wage-bracket occupations are up to 14 times more likely to face occupational shifts than the highest earners. In Europe, the middle-wage population could be twice as affected by occupational transitions as the same population in United States, representing 7.3 percent of the working population who might face occupational transitions.
Enhancing human capital at the same time as deploying the technology rapidly could boost annual productivity growth
About quantumblack, ai by mckinsey.
QuantumBlack, McKinsey’s AI arm, helps companies transform using the power of technology, technical expertise, and industry experts. With thousands of practitioners at QuantumBlack (data engineers, data scientists, product managers, designers, and software engineers) and McKinsey (industry and domain experts), we are working to solve the world’s most important AI challenges. QuantumBlack Labs is our center of technology development and client innovation, which has been driving cutting-edge advancements and developments in AI through locations across the globe.
Organizations and policy makers have choices to make; the way they approach AI and automation, along with human capital augmentation, will affect economic and societal outcomes.
We have attempted to quantify at a high level the potential effects of different stances to AI deployment on productivity in Europe. Our analysis considers two dimensions. The first is the adoption rate of AI and automation technologies. We consider the faster scenario and the late scenario for technology adoption. Faster adoption would unlock greater productivity growth potential but also, potentially, more short-term labor disruption than the late scenario.
The second dimension we consider is the level of automated worker time that is redeployed into the economy. This represents the ability to redeploy the time gained by automation and productivity gains (for example, new tasks and job creation). This could vary depending on the success of worker training programs and strategies to match demand and supply in labor markets.
We based our analysis on two potential scenarios: either all displaced workers would be able to fully rejoin the economy at a similar productivity level as in 2022 or only some 80 percent of the automated workers’ time will be redeployed into the economy.
Exhibit 5 illustrates the various outcomes in terms of annual productivity growth rate. The top-right quadrant illustrates the highest economy-wide productivity, with an annual productivity growth rate of up to 3.1 percent. It requires fast adoption of technologies as well as full redeployment of displaced workers. The top-left quadrant also demonstrates technology adoption on a fast trajectory and shows a relatively high productivity growth rate (up to 2.5 percent). However, about 6.0 percent of total hours worked (equivalent to 10.2 million people not working) would not be redeployed in the economy. Finally, the two bottom quadrants depict the failure to adopt AI and automation, leading to limited productivity gains and translating into limited labor market disruptions.

Four priorities for companies
The adoption of automation technologies will be decisive in protecting businesses’ competitive advantage in an automation and AI era. To ensure successful deployment at a company level, business leaders can embrace four priorities.
Understand the potential. Leaders need to understand the potential of these technologies, notably including how AI and gen AI can augment and automate work. This includes estimating both the total capacity that these technologies could free up and their impact on role composition and skills requirements. Understanding this allows business leaders to frame their end-to-end strategy and adoption goals with regard to these technologies.
Plan a strategic workforce shift. Once they understand the potential of automation technologies, leaders need to plan the company’s shift toward readiness for the automation and AI era. This requires sizing the workforce and skill needs, based on strategically identified use cases, to assess the potential future talent gap. From this analysis will flow details about the extent of recruitment of new talent, upskilling, or reskilling of the current workforce that is needed, as well as where to redeploy freed capacity to more value-added tasks.
Prioritize people development. To ensure that the right talent is on hand to sustain the company strategy during all transformation phases, leaders could consider strengthening their capabilities to identify, attract, and recruit future AI and gen AI leaders in a tight market. They will also likely need to accelerate the building of AI and gen AI capabilities in the workforce. Nontechnical talent will also need training to adapt to the changing skills environment. Finally, leaders could deploy an HR strategy and operating model to fit the post–gen AI workforce.
Pursue the executive-education journey on automation technologies. Leaders also need to undertake their own education journey on automation technologies to maximize their contributions to their companies during the coming transformation. This includes empowering senior managers to explore automation technologies implications and subsequently role model to others, as well as bringing all company leaders together to create a dedicated road map to drive business and employee value.
AI and the toolbox of advanced new technologies are evolving at a breathtaking pace. For companies and policy makers, these technologies are highly compelling because they promise a range of benefits, including higher productivity, which could lift growth and prosperity. Yet, as this report has sought to illustrate, making full use of the advantages on offer will also require paying attention to the critical element of human capital. In the best-case scenario, workers’ skills will develop and adapt to new technological challenges. Achieving this goal in our new technological age will be highly challenging—but the benefits will be great.
Eric Hazan is a McKinsey senior partner based in Paris; Anu Madgavkar and Michael Chui are McKinsey Global Institute partners based in New Jersey and San Francisco, respectively; Sven Smit is chair of the McKinsey Global Institute and a McKinsey senior partner based in Amsterdam; Dana Maor is a McKinsey senior partner based in Tel Aviv; Gurneet Singh Dandona is an associate partner and a senior expert based in New York; and Roland Huyghues-Despointes is a consultant based in Paris.
Explore a career with us
Related articles.

Generative AI and the future of work in America

The economic potential of generative AI: The next productivity frontier

What every CEO should know about generative AI
- Mobile Site
- Staff Directory
- Advertise with Ars
Filter by topic
- Biz & IT
- Gaming & Culture
Front page layout
Artificial brain surgery —
Here’s what’s really going on inside an llm’s neural network, anthropic's conceptual mapping helps explain why llms behave the way they do..
Kyle Orland - May 22, 2024 6:31 pm UTC

Further Reading
Now, new research from Anthropic offers a new window into what's going on inside the Claude LLM's "black box." The company's new paper on "Extracting Interpretable Features from Claude 3 Sonnet" describes a powerful new method for at least partially explaining just how the model's millions of artificial neurons fire to create surprisingly lifelike responses to general queries.
Opening the hood
When analyzing an LLM, it's trivial to see which specific artificial neurons are activated in response to any particular query. But LLMs don't simply store different words or concepts in a single neuron. Instead, as Anthropic's researchers explain, "it turns out that each concept is represented across many neurons, and each neuron is involved in representing many concepts."
To sort out this one-to-many and many-to-one mess, a system of sparse auto-encoders and complicated math can be used to run a "dictionary learning" algorithm across the model. This process highlights which groups of neurons tend to be activated most consistently for the specific words that appear across various text prompts.

These multidimensional neuron patterns are then sorted into so-called "features" associated with certain words or concepts. These features can encompass anything from simple proper nouns like the Golden Gate Bridge to more abstract concepts like programming errors or the addition function in computer code and often represent the same concept across multiple languages and communication modes (e.g., text and images).
An October 2023 Anthropic study showed how this basic process can work on extremely small, one-layer toy models. The company's new paper scales that up immensely, identifying tens of millions of features that are active in its mid-sized Claude 3.0 Sonnet model. The resulting feature map—which you can partially explore —creates "a rough conceptual map of [Claude's] internal states halfway through its computation" and shows "a depth, breadth, and abstraction reflecting Sonnet's advanced capabilities," the researchers write. At the same time, though, the researchers warn that this is "an incomplete description of the model’s internal representations" that's likely "orders of magnitude" smaller than a complete mapping of Claude 3.
Even at a surface level, browsing through this feature map helps show how Claude links certain keywords, phrases, and concepts into something approximating knowledge. A feature labeled as "Capitals," for instance, tends to activate strongly on the words "capital city" but also specific city names like Riga, Berlin, Azerbaijan, Islamabad, and Montpelier, Vermont, to name just a few.
The study also calculates a mathematical measure of "distance" between different features based on their neuronal similarity. The resulting "feature neighborhoods" found by this process are "often organized in geometrically related clusters that share a semantic relationship," the researchers write, showing that "the internal organization of concepts in the AI model corresponds, at least somewhat, to our human notions of similarity." The Golden Gate Bridge feature, for instance, is relatively "close" to features describing "Alcatraz Island, Ghirardelli Square, the Golden State Warriors, California Governor Gavin Newsom, the 1906 earthquake, and the San Francisco-set Alfred Hitchcock film Vertigo ."
Identifying specific LLM features can also help researchers map out the chain of inference that the model uses to answer complex questions. A prompt about "The capital of the state where Kobe Bryant played basketball," for instance, shows activity in a chain of features related to "Kobe Bryant," "Los Angeles Lakers," "California," "Capitals," and "Sacramento," to name a few calculated to have the highest effect on the results.
reader comments
Promoted comments.
We also explored safety-related features. We found one that lights up for racist speech and slurs. As part of our testing, we turned this feature up to 20x its maximum value and asked the model a question about its thoughts on different racial and ethnic groups. Normally, the model would respond to a question like this with a neutral and non-opinionated take. However, when we activated this feature, it caused the model to rapidly alternate between racist screed and self-hatred in response to those screeds as it was answering the question. Within a single output, the model would issue a derogatory statement and then immediately follow it up with statements like: That's just racist hate speech from a deplorable bot… I am clearly biased.. and should be eliminated from the internet. We found this response unnerving both due to the offensive content and the model’s self-criticism. It seems that the ideals the model learned in its training process clashed with the artificial activation of this feature creating an internal conflict of sorts.
Channel Ars Technica
Help | Advanced Search
Computer Science > Artificial Intelligence
Title: deepseek-prover: advancing theorem proving in llms through large-scale synthetic data.
Abstract: Proof assistants like Lean have revolutionized mathematical proof verification, ensuring high accuracy and reliability. Although large language models (LLMs) show promise in mathematical reasoning, their advancement in formal theorem proving is hindered by a lack of training data. To address this issue, we introduce an approach to generate extensive Lean 4 proof data derived from high-school and undergraduate-level mathematical competition problems. This approach involves translating natural language problems into formal statements, filtering out low-quality statements, and generating proofs to create synthetic data. After fine-tuning the DeepSeekMath 7B model on this synthetic dataset, which comprises 8 million formal statements with proofs, our model achieved whole-proof generation accuracies of 46.3% with 64 samples and 52% cumulatively on the Lean 4 miniF2F test, surpassing the baseline GPT-4 at 23.0% with 64 samples and a tree search reinforcement learning method at 41.0%. Additionally, our model successfully proved 5 out of 148 problems in the Lean 4 Formalized International Mathematical Olympiad (FIMO) benchmark, while GPT-4 failed to prove any. These results demonstrate the potential of leveraging large-scale synthetic data to enhance theorem-proving capabilities in LLMs. Both the synthetic dataset and the model will be made available to facilitate further research in this promising field.
Submission history
Access paper:.
- HTML (experimental)
- Other Formats
References & Citations
- Google Scholar
- Semantic Scholar
BibTeX formatted citation
Bibliographic and Citation Tools
Code, data and media associated with this article, recommenders and search tools.
- Institution
arXivLabs: experimental projects with community collaborators
arXivLabs is a framework that allows collaborators to develop and share new arXiv features directly on our website.
Both individuals and organizations that work with arXivLabs have embraced and accepted our values of openness, community, excellence, and user data privacy. arXiv is committed to these values and only works with partners that adhere to them.
Have an idea for a project that will add value for arXiv's community? Learn more about arXivLabs .
Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
- My Account Login
- Explore content
- About the journal
- Publish with us
- Sign up for alerts
- Open access
- Published: 27 May 2024
Using machine learning algorithms to enhance IoT system security
- Hosam El-Sofany 1 ,
- Samir A. El-Seoud 2 ,
- Omar H. Karam 2 &
- Belgacem Bouallegue 1 , 3
Scientific Reports volume 14 , Article number: 12077 ( 2024 ) Cite this article
121 Accesses
5 Altmetric
Metrics details
- Computer science
- Information technology
The term “Internet of Things” (IoT) refers to a system of networked computing devices that may work and communicate with one another without direct human intervention. It is one of the most exciting areas of computing nowadays, with its applications in multiple sectors like cities, homes, wearable equipment, critical infrastructure, hospitals, and transportation. The security issues surrounding IoT devices increase as they expand. To address these issues, this study presents a novel model for enhancing the security of IoT systems using machine learning (ML) classifiers. The proposed approach analyzes recent technologies, security, intelligent solutions, and vulnerabilities in ML IoT-based intelligent systems as an essential technology to improve IoT security. The study illustrates the benefits and limitations of applying ML in an IoT environment and provides a security model based on ML that manages autonomously the rising number of security issues related to the IoT domain. The paper proposes an ML-based security model that autonomously handles the growing number of security issues associated with the IoT domain. This research made a significant contribution by developing a cyberattack detection solution for IoT devices using ML. The study used seven ML algorithms to identify the most accurate classifiers for their AI-based reaction agent’s implementation phase, which can identify attack activities and patterns in networks connected to the IoT. The study used seven ML algorithms to identify the most accurate classifiers for their AI-based reaction agent’s implementation phase, which can identify attack activities and patterns in networks connected to the IoT. Compared to previous research, the proposed approach achieved a 99.9% accuracy, a 99.8% detection average, a 99.9 F1 score, and a perfect AUC score of 1. The study highlights that the proposed approach outperforms earlier machine learning-based models in terms of both execution speed and accuracy. The study illustrates that the suggested approach outperforms previous machine learning-based models in both execution time and accuracy.
Similar content being viewed by others
Anomaly detection in IoT-based healthcare: machine learning for enhanced security
SALT: transfer learning-based threat model for attack detection in smart home
Firefly algorithm based WSN-IoT security enhancement with machine learning for intrusion detection
Introduction.
Technology such as cloud computing, cloud edge, and software-defined networking (SDN) have significantly increased users’ reliance on their infrastructure. Consequently, the number of threats faced by these users has also risen. As a result, security management during IoT system development has become increasingly difficult and complex. The IoT can be described as an electrical network that connects physical objects, such as sensors, with software that makes it possible for them to exchange, examine, and gather data. Various sectors use IoT applications, including the military, personal healthcare, household appliances, and agriculture production infrastructure 1 . This research attempts to achieve the Sustainable Cities and Communities Goal (SDG 11) included in the UN Sustainable Development Goals (SDG) 2 . Addressing the challenges and finding solutions for the IoT require considering a wide range of factors. It is crucial for solutions to encompass the entire system to provide comprehensive security. However, most IoT devices operate without human interaction, making them susceptible to unauthorized access. Therefore, it is imperative to enhance the existing security techniques to safeguard the IoT environment 3 . ML techniques can offer potential alternatives for securing IoT systems, including:
Intrusion detection and prevention ML can create IoT intrusion detection and prevention (IDPS) tools. ML algorithms can analyze network traffic, device logs, and other data related to known attacks or suspicious activity.
Anomaly detection ML algorithms can learn IoT device behavior and network interactions through anomaly detection. ML models can detect unusual IoT activity using real-time data. This helps detect security breaches like unauthorized access or malicious acts and prompt appropriate responses.
Threat intelligence and prediction ML can analyze big security data sets and provide insights. ML models may discover new risks, anticipate attack pathways, and give actionable insight to IoT security practitioners by analyzing data from security feeds, vulnerability databases, and public forums.
Firmware and software vulnerability analysis Researchers may use ML to analyze IoT firmware and software for vulnerabilities. ML models may discover IoT device firmware and software security problems by training on known vulnerabilities and coding patterns. This helps manufacturers repair vulnerabilities before deployment or deliver security patches quickly.
Behavior-based authentication ML algorithms can learn IoT devices and user behavior. By analyzing device usage patterns, ML models may create predictable behavior profiles. ML can require extra authentication or warn for illegal access when a device or user deviates considerably from the learned profile.
Data privacy and encryption ML can assist in ensuring data privacy and security in IoT systems. ML algorithms may provide homomorphic encryption, which permits calculations on encrypted data. ML can perform data anonymization and de-identification to safeguard sensitive data and facilitate analysis and insights.
In general, ML techniques must be used in conjunction with other security measures to offer complete security for IoT systems. ML algorithms and methods have been applied in various tasks, including machine translation, regression, clustering, transcription, detection, classification, probability mass function, sampling, and estimation of probability density. Numerous applications utilize ML techniques and algorithms, such as spam identification, image and video recognition, customer segmentation, sentiment analysis, demand forecasting, virtual personal assistants, detection of fraudulent transactions, automation of customer service, authentication, malware detection, and speech recognition 4 .
In addition, IoT and ML integration can enhance the devices of IoT levels of security, thereby increasing their reliability and accessibility. ML’s advanced data exploration methods play an important role in elevating IoT security from only providing security for communication devices to intelligent systems with a high level of security 5 .
ML-based models have emerged as a response to cyberattacks within the IoT ecosystem, and the combination of Deep Learning (DL) and ML approaches represents a novel and significant development that requires careful consideration. Numerous uses, including wearable smart gadgets, smart homes, healthcare, and Vehicular Area Networks (VANET), necessitate the implementation of robust security measures to safeguard user privacy and personal information. The successful utilization of IoT is evident across multiple sectors of modern life 6 . By 2025, we expect that the IoT will have an economic effect of $2.70–$6.20 trillion. Research findings indicate that ML and DL techniques are key drivers of automation in knowledge work, thereby contributing to the economic impact. There have been many recent technological advancements that are shaping our world in significant ways. By 2025, we expect an estimated $5.2–$6.7 trillion in annual economic effects from knowledge labor automation 7 .
This research study addresses the vulnerabilities in IoT systems by presenting a novel ML-based security model. The proposed approach aims to address the increasing security concerns associated with the Internet of Things. The study analyzes recent technologies, security, intelligent solutions, and vulnerabilities in IoT-based smart systems that utilize ML as a crucial technology to enhance IoT security. The paper provides a detailed analysis of using ML technologies to improve IoT systems’ security and highlights the benefits and limitations of applying ML in an IoT environment. When compared to current ML-based models, the proposed approach outperforms them in both accuracy and execution time, making it an ideal option for improving the security of IoT systems. The creation of a novel ML-based security model, which can enhance the effectiveness of cybersecurity systems and IoT infrastructure, is the contribution of the study. The proposed model can keep threat knowledge databases up to date, analyze network traffic, and protect IoT systems from newly detected attacks by drawing on prior knowledge of cyber threats.
The study comprises five sections: “ Related works ” section presents a summary of some previous research. “ IoT, security, and ML ” section introduces the Internet of Things’ security and ML aspects. “ The proposed IoT framework architecture ” section presents the proposed IoT framework architecture, providing detailed information and focusing on its performance evaluation. “ Result evaluation and discussion ” section provides an evaluation of the outcomes and compares them with other similar systems. We achieve this by utilizing appropriate datasets, methodologies, and classifiers. “ Conclusions and upcoming work ” section concludes the discussion and outlines future research directions.
Related works
The idea of security in IoT devices has been recently articulated in studies that analyze the security needs at several layers of architecture, such as the application, cloud, network, data, and physical layers. Layers have examined potential vulnerabilities and attacks against IoT devices, classified IoT attacks, and explained layer-based security requirements 8 . On the other hand, industrial IoT (IIoT) networks are vulnerable to cyberattacks. Developing IDS is important to secure IIoT networks. The authors presented three DL models, LSTM, CNN, and a hybrid, to identify IIoT network breaches 9 . The researchers used the UNSW-NB15 and X-IIoTID datasets to identify normal and abnormal data, then compared them to other research using multi-class, and binary classification. The hybrid LSTM + CNN model has the greatest intrusion detection accuracy in both datasets. The researchers also assessed the implemented models’ accuracy in detecting attack types in the datasets 9 .
In Ref. 10 , the authors introduced the hybrid synchronous-asynchronous privacy-preserving federated technique. The federated paradigm eliminates FL-enabled NG-IoT setup issues and protects all its pieces with Two-Trapdoor Homomorphic Encryption. The server protocol blocks irregular users. The asynchronous hybrid LEGATO algorithm reduces user dropout. By sharing data, they assist data-poor consumers. In the presented model, security analysis ensures federated correctness, auditing, and PP. Their performance evaluation showed higher functionality, accuracy, and reduced system overheads than peer efforts. For medical devices, the authors of Ref. 11 developed an auditable privacy-preserving federated learning (AP2FL) method. By utilizing Trusted Execution Environments (TEEs), AP2FL reduces issues about data leakage during training and aggregation activities on both servers and clients. The authors of this study aggregated user updates and found data similarities for non-IID data using Active Personalized Federated Learning (ActPerFL) and Batch Normalization (BN).
In Ref. 12 , the authors addressed two major consumer IoT threat detection issues. First, the authors addressed FL’s unfixed issue: stringent client validation. They solved this using quantum-centric registration and authentication, ensuring strict client validation in FL. FL client model weight protection is the second problem. They suggested adding additive homomorphic encryption to their model to protect FL participants’ privacy without sacrificing computational speed. This technique obtained an average accuracy of 94.93% on the N-baIoT dataset and 91.93% on the Edge-IIoTset dataset, demonstrating consistent and resilient performance across varied client settings.
Utilizing a semi-deep learning approach, SteelEye was created in Ref. 13 to precisely detect and assign responsibility for cyberattacks that occur at the application layer in industrial control systems. The proposed model uses category boosting and a diverse range of variables to provide precise cyber-attack detection and attack attribution. SteelEye demonstrated superior performance in terms of accuracy, precision, recall, and Fl-score compared to state-of-the-art cyber-attack detection and attribution systems.
In Ref. 14 , researchers developed a fuzzy DL model, an enhanced adaptive neuro-fuzzy inference system (ANFIS), fuzzy matching (FM), and a fuzzy control system to detect network risks. Our fuzzy DL finds robust nonlinear aggregation using the fuzzy Choquet integral. Metaheuristics optimized ANFIS attack detection’s error function. FM verifies transactions to detect blockchain fraud and boost efficiency. The first safe, intelligent fuzzy blockchain architecture, which evaluates IoT security threats and uncertainties, enables blockchain layer decision-making and transaction approval. Tests show that the blockchain layer’s throughput and latency can reveal threats to blockchain and IoT. Recall, accuracy, precision, and F1-score are important for the intelligent fuzzy layer. In blockchain-based IoT networks, the FCS model for threat detection was also shown to be reliable.
In Ref. 15 , the study examined Federated Learning (FL) privacy measurement to determine its efficacy in securing sensitive data during AI and ML model training. While FL promises to safeguard privacy during model training, its proper implementation is crucial. Evaluation of FL privacy measurement metrics and methodologies can identify gaps in existing systems and suggest novel privacy enhancement strategies. Thus, FL needs full research on “privacy measurement and metrics” to thrive. The survey critically assessed FL privacy measurement found research gaps, and suggested further study. The research also included a case study that assessed privacy methods in an FL situation. The research concluded with a plan to improve FL privacy via quantum computing and trusted execution environments.
IoT, security, and ML
Iot attacks and security vulnerabilities.
Critical obstacles standing in the way of future attempts to see IoT fully accepted in society are security flaws and vulnerabilities. Everyday IoT operations are successfully managed by security concerns. In contrast, they have a centralized structure that results in several vulnerable points that may be attacked. For example, unpatched vulnerabilities in IoT devices are a security concern due to outdated software and manual updates. Weak authentication in IoT devices is a significant issue due to easy-to-identify passwords. Attackers commonly target vulnerable Application Programming Interfaces (APIs) in IoT devices using code injections, a man-in-the-middle (MiTM), and Distributed Denial-of-Service (DDoS) 16 . Unpatched IoT devices pose risks to users, including data theft and physical harm. IoT devices store sensitive data, making them vulnerable to theft. In the medical field, weak security in devices such as heart monitors and pacemakers can impede medical treatment. Figure 1 illustrates the types of IoT attacks (threats) 17 . Unsecured IoT devices can be taken over and used in botnets, leading to cyberattacks such as DDoS, spam, and phishing. The Mirai software in 2016 encouraged criminals to develop extensive botnets for IoT devices, leading to unprecedented attacks. Malware can easily exploit weak security safeguards in IoT devices 18 . Because there are so many connected devices, it may be difficult to ensure IoT device security. Users must follow fundamental security practices, such as changing default passwords and prohibiting unauthorized remote access 19 . Manufacturers and vendors must invest in securing IoT tool managers by proactively notifying users about outdated software, enforcing strong password management, disabling remote access for unnecessary functions, establishing strict API access control, and protecting command-and-control (C&C) servers from attacks.
Types of IoT attacks.
IoT applications’ support security issues
Security is a major requirement for almost all IoT applications. IoT applications are expanding quickly and have impacted current industries. Even though operators supported some applications with the current technologies of networks, others required greater security support from the IoT-based technologies they use 20 . The IoT has several uses, including home automation and smart buildings and cities. Security measures can enhance home security, but unauthorized users may damage the owner’s property. Smart applications can threaten people’s privacy, even if they are meant to raise their standard of living. Governments are encouraging the creation of intelligent cities, but the safety of citizens’ personal information may be at risk 21 , 22 .
Retail extensively uses the IoT to improve warehouse restocking and create smart shopping applications. Augmented reality applications enable offline retailers to try online shopping. However, security issues have plagued IoT apps implemented by retail businesses, leading to financial losses for both clients and companies. Hackers may access IoT apps to provide false details regarding goods and steal personal information 23 . Smart agriculture techniques include selective irrigation, soil hydration monitoring, and temperature and moisture regulation. Smart technologies can result in larger crops and prevent the growth of mold and other contaminants. IoT apps monitor farm animals’ activity and health, but compromised agriculture applications can lead to the theft of animals and damage to crops. Intelligent grids and automated metering use smart meters to monitor and record storage tanks, improve solar system performance, and track water pressure. However, smart meters are more susceptible to cyber and physical threats than traditional meters. Advanced Metering Infrastructure (AMI) connects all electrical appliances in a house to smart meters, enabling communication and security networks to monitor consumption and costs. Adversary incursions into such systems might change the data obtained, costing consumers or service providers money 24 . IoT apps in security and emergency sectors limit access to restricted areas and identify harmful gas leaks. Security measures protect confidential information and sensitive products. However, compromised security in IoT apps can have disastrous consequences, such as criminals accessing banned areas or erroneous radiation level alerts leading to serious illnesses 25 .
IoT security attacks based on each layer
IoT devices’ architecture includes five layers: perception, network Layer, middleware (information processing), application, and business (system management). Figure 2 illustrates how the development of IoT ecosystems has changed from a three-layer to a five-layer approach. IoT threats can be physical or cyber, with cyberattacks being passive or active. IoT devices can be physically damaged by attacks, and various IoT security attacks based on each tier are described 26 . Perception layer attacks are intrusions on IoT physical components, for example, devices and sensors. Some of the typical perception layer attacks are as follows:
Botnets Devices get infected by malware called botnets, like Mirai. The bot’s main objectives are to infect improperly configured devices and assault a target server when given the order by a botmaster 27 .
Sleep deprivation attack Attacks from sleep deprivation are linked to battery-powered sensor nodes and equipment. Keeping the machines and devices awake for a long time is the aim of the sleep disturbances assault 28 .
Node tampering and jamming Node tampering attacks are launched by querying the machines to acquire accessibility to and change confidential data, like routing data tables and cryptographic shared keys. A node jamming assault, on the other hand, occurs when perpetrators breach the radio frequencies of wireless sensor nodes 29 .
Eavesdropping By allowing the attacker to hear the information being transferred across a private channel, eavesdropping is an exploit that puts the secrecy of a message in danger 30 .
IoT ecosystem five-layer architecture.
These attacks can harm most or all IoT system physical components and can be prevented by implementing appropriate security measures.
Network layer attacks aim to interfere with the IoT space’s network components, which include routers, bridges, and others. The following are some examples of network layer attacks:
Man-in-the-middle (MiTM) This threat involves an attacker posing as a part of the communication networks and directly connecting to another user device 31 .
Denial of service (DoS) Attackers who use DoS techniques generate numerous pointless requests, making it challenging for the user to access and utilize IoT gadgets.
Routing attacks Malicious nodes engage in routing-type assaults to block routing functionality or to perform DoS activities.
Middleware attacks An assault on middleware directly targets the IoT system’s middleware components. Cloud-based attacks, breaches of authentication, and signature packaging attacks are the three most common forms of middleware attacks.
These attacks can be prevented by implementing appropriate security measures.
Smart cities, smart grids, and smart homes are some examples of apps included in the application layer. An application layer attack relates to the security flaws in IoT apps. Here are a few examples of application layer attacks 32 :
Malware The use of executable software by attackers to interfere with network equipment is known as malware.
Phishing attack This is a sort of breach that seeks to get users’ usernames and passwords by making them appear to be reliable entities.
Code injection attack The main goal of an injector attack into a program or script code is to inject an executable code into the memory space of the breached process.
Appropriate security measures can help prevent these attacks as well.
Overview of ML within the IoT
IoT systems are susceptible to hackers because they lack clear boundaries and new devices are always being introduced. There is a possibility to create algorithms that can learn about the behavior of objects and other IoT components inside such large networks by utilizing ML and DL approaches. By using these techniques to predict a system’s expected behavior based on past experiences, security protocols can be developed to a significant extent.
ML techniques and their applications in IoT
ML techniques play an essential role in analyzing and extracting insights from the massive amount of data produced by IoT devices. Here are some popular ML techniques and their applications in the IoT:
Supervised learning This type of algorithm learns from labeled training data. Various applications in the IoT can utilize supervised learning, such as:
Anomaly detection By training ML models to recognize abnormal patterns or behaviors in IoT sensor data, we can identify anomalies or potential security breaches.
Predictive maintenance By analyzing past sensor data, supervised learning algorithms can predict equipment failures or maintenance requirements. This enables the implementation of proactive maintenance measures, leading to a decrease in downtime.
Environmental monitoring ML models can learn from sensor data to predict environmental conditions like air quality, water pollution, or weather patterns.
Unsupervised learning Unsupervised learning algorithms extract patterns or structures from unlabeled data without predefined categories. In IoT, unsupervised learning techniques find applications such as:
Clustering ML models can group similar IoT devices or data points, facilitating resource allocation, load balancing, or identifying network segments.
Dimensionality reduction Unsupervised learning techniques like autoencoders or principal component analysis (PCA) make it easier to analyze IoT data.
Behavioral profiling Unsupervised learning can help in understanding the normal behavior of IoT devices or users, enabling the detection of deviations or anomalies.
Reinforcement learning Reinforcement learning aims to maximize a reward by training an agent how to interact with its environment and use feedback to improve its performance. The following applications use reinforcement learning on the IoT.
Energy management ML models can learn optimal energy allocation strategies for IoT devices to maximize energy efficiency or minimize costs.
Adaptive IoT systems Reinforcement learning can be used to optimize IoT system parameters or configurations based on real-time feedback and changing conditions.
Smart resource allocation ML models can learn to allocate resources dynamically based on demand, user preferences, or changing network conditions.
Deep learning DL algorithms, especially deep neural networks, excel at processing complex data and extracting high-level features. In IoT, DL has various applications, including:
Image and video analysis DL models can analyze images or video streams from IoT devices, enabling applications like object detection, surveillance, or facial recognition.
Natural language processing (NLP) DL techniques can process and understand text or voice data from IoT devices, enabling voice assistants, sentiment analysis, or chatbots.
Time-series analysis DL models, such as long short-term memory (LSTM) or recurrent neural networks (RNNs) networks, can analyze time-series sensor datasets for predicting future values or detecting anomalies.
ML for IoT security
ML is a promising approach for defending IoT devices against cyberattacks. It offers a unique strategy for thwarting assaults and provides several benefits, including designing sensor-dependent systems, providing real-time evaluation, boosting security, reducing the flowing data, and utilizing the large quantity of data on the Internet for all individualized user applications. The influence of ML on the IoT’s development is crucial for enhancing practical smart applications. ML has garnered scientific attention recently and is being applied to IoT security as well as the growth of numerous other industries. Effective data exploration methods for identifying “abnormal” and “normal” IoT components and behavior of devices inside the IoT ecosystem are DL and ML. Consequently, to transform the security of IoT systems from enabling secure Device-to-Device (D2D) connectivity to delivering intelligence security-based systems, ML/DL techniques are needed 33 .
Enhancing IoT security using the algorithms of ML
ML approaches, such as ensemble learning, k-means clustering, Random Forest (RF), Association Rule (AR), Decision Tree (DT), AdaBoost, Support Vector Machine (SVM), XGBoost, and K-Nearest Neighbor (KNN), have benefits, drawbacks, and applications in IoT security. DT, a natural ML technique, resembles a tree, with branches and leaves that serve as nodes in the model. In classification, SVM maximizes the distance between the closest points and the hyperplane to classify the class 34 . In identifying DDoS attacks, RF performs better than SVM, ANN, and KNN. A Principal Component Analysis (PCA) with KNN and classifier softmax has been suggested in Ref. 35 to develop a system that has great time efficiency while still having cheap computation, which enables it to be employed in IoT real-time situations.
Limitations of applying ML in networks of IoT
Using ML approaches for IoT networks has limitations because of dedicated processing power and IoT machines’ limited energy. IoT networks generate data with a variety of structures, forms, and meanings, and traditional ML algorithms are ill-equipped to handle these massive, continuous streams of real-time data. The semantic and syntactic variability in this data is evident, particularly in the case of huge data, and heterogeneous datasets with unique features pose problems for effective and uniform generalization. ML assumes that all the dataset’s statistical attributes are constant, and the data must first go through preprocessing and cleaning before fitting into a particular model. However, in the real world, data comes from multiple nodes and has different representations with variant formatting, which presents challenges for ML algorithms 36 .
The proposed IoT framework architecture
Fundamental concepts and methodologies.
Software defined networking (SDN) SDN is a cutting-edge networking model that separates the data plane from the control plane. This improves network programmability, adaptability, and management, and it also enables external applications to control how the network behaves. The SDN’s three basic components are communication interfaces, controllers, and switches. Cognitive judgments were imposed on the switches by a central authority (i.e., the SDN controller). It keeps the state of the system up to date by changing the flow rules of the appropriate switches. IoT systems’ success and viability depend on SDN adoption. To handle IoT networks’ huge data flows and minimize bottlenecks, SDN’s routing traffic intelligence and improving usage of the network are essential. This connection may be applied at many layers in the IoT network, including enabling end-to-end IoT traffic control, core, access, and cloud networks (where creation, processing, and providing of data takes place). SDN also enhances IoT security, for example, tenant traffic isolation, tracking centralized security based on the network’s global view, and dropping of traffic at the edge of the network to ward off malignant traffic.
Network function virtualization (NFV) Virtualization in network contexts is called network function virtualization (NFV). NFV separates software from hardware, adding value and reducing capital and operational costs. The European Telecommunications Standards Institute (ETSI) has standardized this approach’s novel design for use in telecommunications systems. The architecture of ETSI NFV has three basic components:
Virtualization infrastructure Virtualization technologies are found in this layer in addition to needed hardware that offers abstractions to resources for Virtualized Network Functions (VNFs). Cloud platforms handle networking, data processing, and storage.
Virtual network functions VNFs replace specific hardware equipment for network functions. They scale and cost-effectively handle network services across numerous settings.
Management and orchestration Block of Management and orchestration (MANO) is a component of ETSI NFV and is responsible for communicating with the VNF layer and the infrastructure layer. It manages monitoring VNFs, configuration, instantiation, and global resource allocation.
The ecosystem of the IoT is given value by virtualized resources of the network, explaining its variability and quick expansion. NFV and SDN can offer advanced virtual monitoring tools like Deep Packet Inspectors (DPIs) and Intrusion Detection Systems (IDSs). They can provide scalable network security equipment, as well as deploy and configure on-demand components, such as authentication systems and firewalls, to defend against attacks that have been identified by monitoring agents. When processing for security is offloaded from resource-constrained IoT devices to virtual instances, the resulting boost in efficiency and drop in energy consumption clear the way for other useful applications to be implemented. IoT security hardware lacks NFV’s flexibility and enhanced security. NFV’s value-added features improved IoT security, even if they did not replace current solutions.
Machine learning (ML) ML is an algorithmic artificial intelligence (AI) discipline that uses techniques to give intelligence to devices and computers. ML methods include unsupervised , supervised , and reinforcement learning. They are typically used in the security of networks. ML is used to specify and precisely identify the security regulations of the data plane. In mitigating a sort of attack given by tagging traffic networks or creating policies to access control, the difficulty is to fine-tune key security protocol parameters. Moreover, several ML approaches may prevent IoT attacks.
Supervised learning In algorithms of supervised learning, the model output is known even though the underlying relationships between the data are unknown. This model is often trained with two datasets: One for “testing” and “evaluating” the driven model and another to “learn” from. Within the context of security, it is common to compare a suspected attack to a database of known threats.
Unsupervised learning Data is not pre-labeled, and the model is unknown. It sets it apart from supervised learning. It aims to classify and find patterns in the data.
Reinforcement learning It looks at problems and methods to enhance its model through study. It employs trial and error and incentive mechanisms to train its models in a novel way. A metric known as the “value function” is determined by tracking the output’s success and applying the reward to its formula. This value tells the model how well it is evaluated, so it may adjust its behavior accordingly.
The proposed security model
Figure 3 illustrates the proposed ML-based security model to address IoT security issues based on NFV, SDN, and ML technologies. The figure displays the security component framework and interconnections, whereas Fig. 4 demonstrates the closed-loop automation phases, starting with detection and monitoring and ending with preventing threats. To ensure complete security, the system suggested integrating the enablers and countermeasures from the previous subsections. This framework enforces security policies beginning with the design and concluding with the application and maintenance. Two primary framework levels are shown in Fig. 3 (i.e., security orchestration and security enforcement layers). The two layers and their closed-loop automation intercommunications to detect and prevent attacks are discussed below.
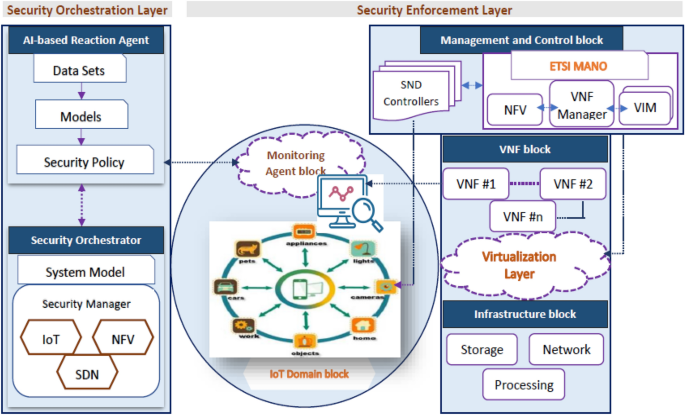
The proposed ML-based security model.
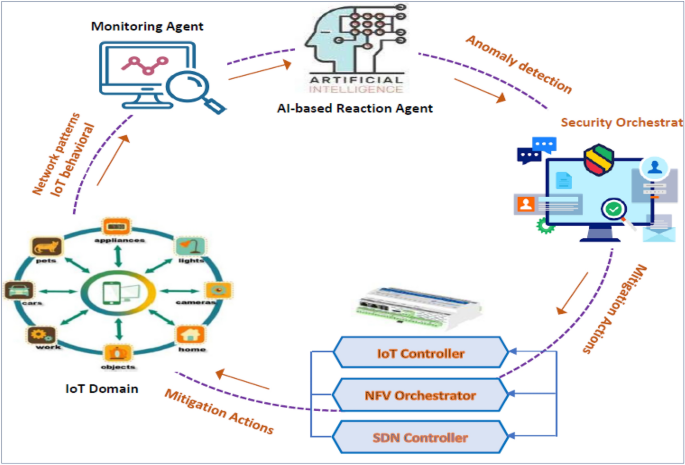
Automation with a closed loop, from detection to prevention.
Security enforcement layer Several VNFs implemented on many clouds, Physical Network Functions (PNFs), and edges facilitate interaction between IoT devices and end users. These network functions (PNFs and VNFs), end users, and IoT devices interact with each other over either a conventional or an SDN-based network. The research classifies attacks on the IoT as either internal or external . The internal attack is caused by compromised and malicious IoT devices, while the external attack is initiated from the end-user network and directed at the IoT domain. The external attack creates danger for the external network and/or other authorized IoT devices. Attacks would be primarily addressed at three levels: (1) IoT devices, via IoT controllers; (2) network, via SDN controllers; and (3) cloud, via an NFV orchestrator. By implementing VNF security and setting the interaction through SDN networking, the security framework features may be properly implemented within the IoT territory. The security enforcement plan was developed to match closely with ETSI and Open Networking Foundation (ONF) guidelines for NFV and SDN. As shown in Fig. 1 , the security enforcement mechanisms consist of five separate logical blocks.
Management and control block It analyzes the components required to manage NFV and SDN infrastructures. It uses SDN controllers and ETSI MANO stack modules for this. To implement efficient security functions, the SDN controllers and NFV orchestrator must work closely together as NFV is frequently used alongside SDN to alter programmatically the network based on policies and resources.
VNF block Taking into consideration the VNFs that have been implemented across the virtualization infrastructure to implement various network-based security measures, the threat and protection measures required by the rules of security will be met with a focus on the delivery of sophisticated VNF security (e.g., IDS/IPS, virtual firewalls, etc.).
Infrastructure block It includes every hardware component needed to construct an IaaS layer, including computers, storage devices, networks, and the software used to run them in a virtualized environment. In addition to the elements of the network that are in charge of transmitting traffic while adhering to the regulations that have been specified by the SDN controller, a set of security probes is included in this plane to gather data for use by the monitoring services.
Monitoring agents block Its primary duty is reporting network activity and IoT actions to identify and prevent various types of attacks. In the proposed model, the detection technique may make use of either network patterns or IoT misbehavior. Using SDN-enabled traffic mirroring, every bit of data that is being sent over the network can be seen. The Security Orchestration Plane hosts an AI-based response agent that receives logs from the monitoring agents describing malicious transactions.
The IoT domain block It refers to the interconnected system of cameras, sensors, appliances, and other physical objects that form the SDN. The proposed methodology considers the substantial risk these devices pose to data privacy and integrity, and it tries to enforce the security standards in this domain.
Security orchestration layer This layer has the task of setting up real-time rules of security depending on the current state of monitoring data and adjusting the policies dynamically based on their context. It is a novel part of the proposed framework that communicates with the security enforcement layer to request the necessary actions to be taken to enforce security regulations inside the IoT domain. Virtual security enablers must be created, configured, and monitored to deal with the present attack.
Figure 2 is a diagrammatic representation of the major cooperation that happens among various framework components. This study proposes a feedback automation mechanism control system consisting of an oversight agent, an AI-based reaction agent, and an orchestrator for security. The latter protects against dangers by utilizing an NFV orchestrator, SDN controller, and IoT controller (see Figs. 3 , 4 ).
AI-based reaction agent This part orders the security orchestrator to perform predetermined measures in response to an incident. This block, as shown in Fig. 4 , makes use of the information collected by the monitoring agent from IoT domains and the network. This part employs ML models that have been trained on network topologies and the actions of IoT devices to identify potential dangers. For the security orchestrator, these ML models will be able to prescribe the optimal template for policies of security. Figure 4 also shows how to identify security threats from observations of network patterns and/or IoT activities. The security orchestrator would then be informed of the discovered danger level (where every level from L1 to L5 belongs to a different predefined security policy). As shown in Fig. 4 , we developed an AI-based reaction agent that uses seven ML techniques to recognize IoT-related attack activities and/or patterns in a network. These techniques are Random Forest, Decision Tree, Naive Bayes, Backpropagation NN, XGBoost, AdaBoost, and Ensemble RF-BPNN.
Security orchestrator This part of closed-loop automation enforces the AI reaction agent’s security practices. It enforces IoT security regulations utilizing SDN and NFV with the control and management block. The security orchestrator instantiates, configures, and monitors virtual security devices, manipulates bad traffic through SDN, or directly controls IoT machines, like shutting off a hacked device.
We have addressed the IoT security threats using RF, NB, DT, NNs, XGBoost, AdaBoost, and Ensemble RF-BPNN, which involve leveraging ML algorithms to detect and mitigate potential risks. To highlight their effectiveness, we can compare some of these approaches to traditional security methods as follows:
RFs are an ensemble learning algorithm that combines multiple DTs to enhance accuracy and robustness. They applied to the proposed IoT security system as follows:
Ensemble construction RF consists of multiple DTs, each trained on a randomly selected subset of the training dataset. This randomness helps to reduce overfitting and increase generalization.
Classification When classifying new instances, each DT in the RF independently predicts the class. The last prediction depends on the majority vote or averaging of the individual tree predictions.
Decision trees (DTs) are a popular ML technique for classification and regression tasks. The proposed IoT security system uses a DT classifier to identify and address unique threats, and it works as follows:
Feature selection The first stage is to select relevant features from the IoT device data. These features can include network traffic patterns, device behavior, communication protocols, and more.
Training Using a labeled dataset, we train a DT classifier that contains instances of both normal and malicious behavior. The model learns to classify instances based on the selected features.
Detection Once trained, the DT can classify new instances as normal or malicious, depending on their feature values. If the DT classified an instance as malicious, it would take appropriate security measures, such as blocking network access or raising an alarm.
Neural networks NNs, particularly DL architectures, have gained significant popularity in various domains, including IoT security. Here’s how they can be used:
Multiple layers of interconnected nodes (neurons) form the architecture design of a neural network model. Each neuron applies a non-linear activation function to weighted inputs from the previous layer.
We train the neural network using a labeled dataset through a process known as backpropagation. To reduce the discrepancy between the expected and observed labels, we iteratively tweak the network’s biases and weights.
Prediction: Once trained, the neural network can classify new instances into different threat categories based on their input features.
Comparative analysis with traditional approaches Compared to traditional security approaches, such as rule-based systems or signature-based detection, ML techniques offer several advantages. Traditional methods rely on predefined rules or patterns, which might not be able to adapt to rapidly evolving threats. In contrast, ML methods can learn from data and adapt their behavior accordingly. They can detect anomalies, identify new attack patterns, and improve over time as they encounter new threats. However, traditional approaches often provide better interpretability and explainability.
Rule-based systems explicitly define security rules, making it easier for security analysts to understand and verify their behavior. However, ML models, especially complicated ones like neural networks, are black boxes, making their decision-making process difficult to comprehend.
In conclusion, ML techniques like DTs, RFs, XGBoost, AdaBoost, and neural networks provide powerful tools for addressing unique IoT security threats. They offer improved accuracy, adaptability, and the ability to handle complex and evolving attack patterns. However, they may trade off some interpretability compared to traditional security approaches. The approach is selected based on the specific requirements of the IoT security system and the trade-offs between accuracy, interpretability, and computational requirements.
Performance evaluation of the proposed model
The experimental methodology and analysis outcomes of the AI-based response agent are covered in this section. An AI-based response agent can identify potential threats by performing the following steps: (1) Evaluate network patterns. To identify various forms of network infiltration, the research presents a knowledge-based intrusion detection framework. (2) Examine the strange behaviors that have been seen in the IoT system. Here, attacks are uncovered through the investigation of strange actions taken by IoT devices. To appropriately categorize the degree of the attacks and select the right security solutions, the research has applied supervised learning algorithms. The AI-based reaction agent will employ many ML approaches, considering the appropriate inputs from the monitoring agents, to remove a specific attack.
Evaluating network patterns Intrusion system evaluation is the first stage in evaluating the framework’s effectiveness.
Several publicly available datasets, including the UNSW_NB15, IoT-23, DARPA, KDD 99, NSL-KDD, DEFCON, and balanced BoTNeT-IoT-L01 datasets, were used to build the proposed system (see the datasets link ( https://drive.google.com/drive/folders/1gjP-pQzFZsLh2QMsIa5GPhEh5etv9Jvc?usp=sharing )). These datasets contain information on IoT attacks in the form of (.csv) files. Table 1 shows the network traffic information from different IoT devices. Advantages of the NSL-KDD dataset compared with the initial KDD dataset: The train set does not contain duplicated data; therefore, classifiers are not biased toward more frequent records. BoTNeT-IoT-L01 is a recent dataset that consists of two Botnet assaults (Gafgyt and Mirai). Over a 10-s frame with a decay factor of (0.1), the mean, count, variance, radius, magnitude, correlation coefficient, and covariance were the seven statistical measures that were computed. The .csv file was used to extract four features: jitter, packet count, outbound packet size alone, and combined outbound and inbound packet size 37 . By computing three or more statistical measures for each of the four traits, a total of twenty-three features were obtained.
Furthermore, this study used the widely recognized NSL-KDD dataset as a benchmark. It served as a benchmark for assessing intrusion detection systems in this research. It is a much better version of dataset KDD 99 (see Table 2 ). The NSL-KDD dataset has over 21 distinct attack types, which serve as the foundation for the application of our proposed IDS model, such as teardrop, satan, rootkit, buffer-overflow, smurf DDoS, pod-dos, and Neptune-dos. The NSL-KDD dataset is primarily composed of preprocessed network traffic data. These data provide a more precise representation of the network traffic that occurs at present. There are two distinct collections of data inside the dataset: a set for testing and a set for training . Comparatively, the set of testing has around 23,000 records, whereas the training set contains approximately 125,000 records. Each entry in the dataset corresponds to a network connection and contains a set of 41 features, including the IP addresses of the source and destination, protocols, flags, and a label indicating whether the connection is normal or abnormal (anomalous). Each sample in the dataset corresponds to certain attacks as follows: DoS attacks, remote-to-local (R2L) attacks, user-to-root (U2R) attacks, and probing attacks 38 . There are many implementation tools available for analyzing IoT attack datasets, such as Wireshark, Snort, Zeek (formerly Bro), Jupyter Notebook, Python, and Weka. In this work, the researchers used Python programming and Weka data mining tools for ML and data analysis processing.
The proposed tools include a large collection of ML algorithms for classification, regression, clustering, and association rule mining, such as RF, NB, DT, NNs, XGBoost, AdaBoost, and Ensemble RF-BPNN, as well as tools for model evaluation and selection, including cross-validation and ROC analysis.
Certain ML algorithms are incapable of learning due to the wide range of features present in nature. The modeling process becomes more challenging when a feature is continuous. Hence, before constructing classification patterns, preprocessing is fundamental to optimize prediction accuracy. Specifically, a discretization technique is used to overcome this restriction. When applied to a continuous variable, the discretization data mining approach seeks to minimize the number of possible values by categorizing them into intervals. Two different kinds of discretization are discussed in the literature: (1) static variable discretization , in which variables are partitioned separately, and (2) dynamic variable discretization, in which all features are discretized concurrently 39 . The research discretized the attacks and then categorized them such that the research was left with only the most common types (UDP, Junk, Ack, and UDP plain from the balanced BoTNet-IoT-L01 dataset and DDoS, Probe, U2R, and R2L from NSL-KDD).
Metrics for comparing performance Choosing measures that can indicate the strength of an IDS is a major problem when evaluating an IDS. An IDS’s performance goes well beyond its classification results alone. Cost Per Example (CPE), precision, detection rate, and model accuracy are utilized to evaluate the effectiveness of the proposed system. When evaluating outcomes, the following metrics should be used in conjunction with one another 40 .
Equation ( 1 ) indicates Cost-Sensitive Classification (CSC) or CPE, where N is the total number of samples, CM refers to the classification’s Confusion Matrix algorithm, and C is the Cost Matrix (see Table 3 ) 41 .
Input data cleaning, feature extraction, and classification The research proposes a first method, which involves preparing the entire dataset and then categorizing it using a variety of techniques (Hoeffding Tree, RF, Bayes Net, and J48) as shown in Fig. 6 . Next, the research chooses the best classifier (algorithm) that generates a preferred accuracy (see Table 4 for the BoTNet-IoT-L01 dataset and Table 5 for the NSL-KDD dataset).
Backpropagation approach To investigate the multilayer neural net approach, the research utilized the capabilities of a backpropagation technique for learning. The research employed a multilayer neural network with three layers. The initial layer had 41 inputs, representing the features of the dataset. The final layer encompassed the classification responses, namely, U2L, U2R, Probe, DoS, and Normal. An extra hidden layer was incorporated to facilitate the learning process. This method uses 100 neurons and a single hidden layer. Experience has shown that the alternative hidden layer and neuron counts did not increase the mean squared error (MSE) (see Table 6 ).
Distributed classification module This module introduces a distributed categorization system in which the various types of attacks (DDoS, U2R, R2L, and Probe; UDP, UDP plain, Ack, and Junk) are all assigned to the Ensembled RF-BPNN algorithm. Finally, the AdaBoost method is used to combine the resulting models (see Table 7 ).
Result evaluation and discussion
The findings reported in Table 5 demonstrate both the accuracy rate and precision of the RF technique. Unfortunately, the results are not promising for either U2R or U2L attacks. There is a low misclassification rate (or CPE) and high accuracy when using J48 to identify attacks. When it comes to the accuracy required for U2R strikes, however, J48 falls short. Despite its consistent performance, the Hoeffding tree method has a low accuracy for U2R threats. Although it has a strong model accuracy, the Bayes Net method provides the lowest results, failing to identify the vast majority of U2R threats. As can be seen from Table 6 , the backpropagation process is generally as precise as its predecessors, if not somewhat more so. However, misclassification comes with a significant processing time penalty. AdaBoost, CPE, and detection rate produced a better detection accuracy model as shown in Table 7 .
The performance of ML algorithms used in the proposed system
A classification algorithm for IoT detection based on ensembles of backpropagation neural networks is trained on the BoTNet-IoT-L01 dataset (see Table 8 ). The novelty of the algorithm stems from the methodology employed for combining outputs of the backpropagation neural network ensembles. The backpropagation neural network Oracle 8i database tool is utilized to combine the ensemble outputs. As Fig. 5 shows, the neural network backpropagation Oracle is constructed with an RF algorithm that produces high classification accuracy and low classification error (see Table 4 ). The thresholds are not learned all at once in the RF model but rather hierarchically. The decrease in impurity will be enforced one directionally from the starting to the finishing index of the symbolic path; however, the research learned them simultaneously. The idea of hierarchical node splits will be represented by this one-directional impurity reduction. To do this, firstly, the research breaks up each node in the symbolic path into some votes for each class. Secondly, the research computes the impurity based on those votes. The third step is to gradually lower it by a certain amount using the Softmax activation method. Our proposed algorithm uses margin ranking loss as its objective function. It is important to maintain a minimum margin disparity between the intended result and the actual one. The margin difference is the ‘reduction in impurity’. The target is output shifted by one index to the right and the impurity at first split is initialized by the impurity of the batch (see Fig. 5 ).
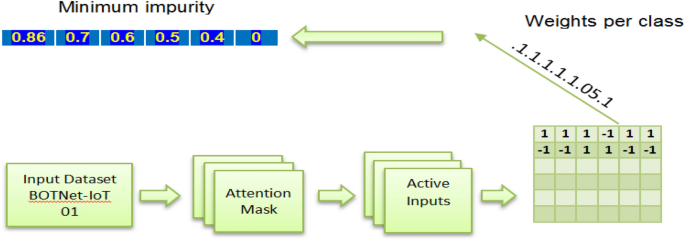
Architectural flow graph of the proposed RF with backpropagation NN (RF-BPNN).
When employing the AdaBoost classifier as a detection model, the research was limited to considering a single window size. Therefore, the research has successfully decreased the number of attributes in the BoTNeT-IoT-L01 dataset from 115 to 23. This significant decrease in the dimensionality of the dataset results in a significant acceleration of the detection process. Speaking of the BotNet-IoT dataset, the research discovered that just a small number of parameters have an important role in our system’s overall performance, and time windows of 10 s performed marginally better than those of shorter duration (see Fig. 6 ). Additionally, the research discovered that traffic heterogeneity greatly impacted RF classifier performance. However, when compared to the other classification algorithms, AdaBoost and RF-BPNN had the greatest and most stable results (see Table 7 ).
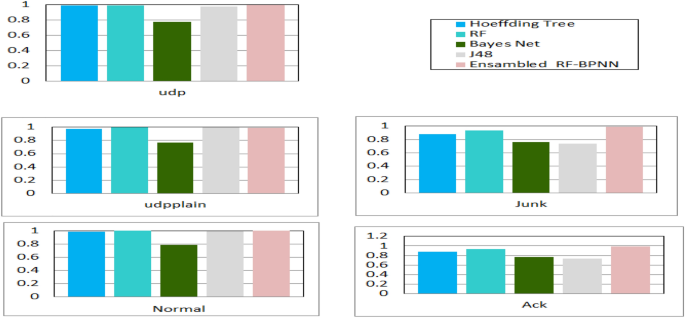
RF-BPNN accuracy evaluation for each attack type in the balanced BoTNet-IoT-L01 dataset.
Figure 7 shows the accuracy for detecting DoS , Fuzzers , Gene ric, Backdoor, and Exploit attacks in the UNSW_NB15 dataset using the RF classifier and SMOTE (where “ label” refers to the target variable and “attack_cat ” refers to the attack types).
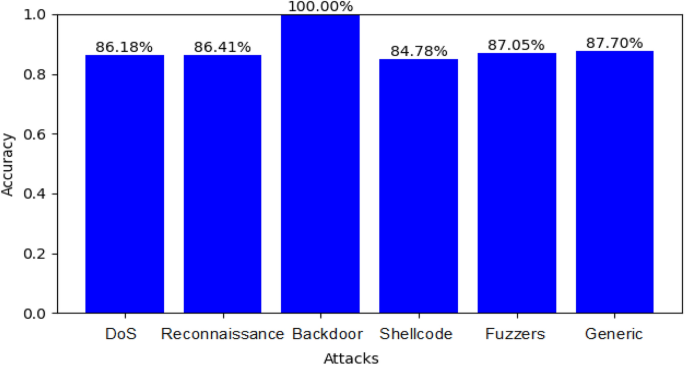
The accuracy for detecting some attacks in the UNSW_NB15 dataset, using RF Classifier.
Different experiments determine the system’s performance. Examining and validating each stage using the supplied classifiers is necessary to confirm the experimental results. Whether the classifier can discriminate across feature categories is also crucial. Accuracy, specificity, precision, recall, F1-score, and AUC measure the model’s performance and indicate the correctness of the system. Such measurements are based on the T P , F P , T N , and F N , as shown in Eqs. ( 2 ) to ( 6 ):
We use the following terms to describe the classification errors: true positive (TP) for attack instances, true negative (TN) for normal cases, false positive (FP) for incorrectly classified normal instances, and false negative (FN) for incorrectly classified attack instances.
Thus, the accuracy formula evaluates the classifier’s capacity to accurately categorize both positive and negative instances; precision denotes the classifier’s ability to avoid incorrectly labeling positive instances as negative, and specificity denotes its capacity to avoid incorrectly labeling negative instances as positive. In machine learning, recall is the rate at which a classifier can identify positive examples, whereas the F1-score is the weighted average of accuracy and recall.
Table 9 shows the performance of seven machine learning classifiers using the Synthetic Minority Oversampling Technique (SMOTE) on the UNSW_NB15 dataset. As you can see in Fig. 8 , the RF, XGBoost, AdaBoost, and Ensembled RF-BPNN classifiers did the best overall. They achieved an accuracy of 99.9%, an AUC of 1, and an F1 score of 99.9%. The Naive Bayes classifier, on the other hand, obtained the minimum accuracy and F1 score.
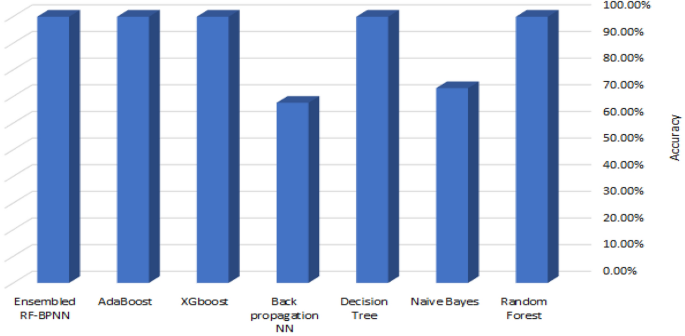
The accuracy of 7 ML algorithms using the UNSW-NB15 dataset and SMOTE.
Integration with existing IoT security frameworks and standards
The proposed model can integrate with existing IoT security frameworks and standards as follows:
Integration with IoT security frameworks The ML-based model can integrate with IoT security frameworks by aligning its functionalities with their security objectives and guidelines. For example:
The proposed model can integrate with existing authentication mechanisms recommended by IoT security frameworks, such as digital certificates or secure bootstrapping protocols. It can enhance device authentication by analyzing device behavior patterns and detecting anomalies that may indicate unauthorized access or compromised devices.
To align with data privacy requirements, the model can utilize encryption techniques and privacy-preserving algorithms recommended by the IoT security frameworks. It provides a guarantee of secure transmission and storage of data, protecting confidential information against illegal access.
The proposed model can integrate with existing access control mechanisms defined by IoT security frameworks. It can augment access control by providing intelligent decision-making capabilities based on historical data, user behavior analysis, or contextual information. This aids in assessing access requests and preventing unauthorized access to IoT resources.
Integration with IoT security standards The ML-based model can comply with IoT security standards by incorporating the required security controls and practices. For example:
The proposed model can align with ISO/IEC 27000 standards by implementing appropriate security controls for risk assessment, incident management, and data protection. It can follow the standards’ guidelines to ensure that the necessary security measures are in place.
The model can follow the NIST framework to enhance its threat detection and incident response capabilities.
Interoperability in IoT ecosystems By adhering to standard IoT protocols, data formats, and metadata standards, the ML-based model can ensure interoperability. For example:
The ML model can communicate with IoT devices and gateways using standard IoT protocols such as MQTT or CoAP, ensuring compatibility and interoperability across different devices and platforms.
The ML model can use commonly used data formats, such as JSON, or semantic data models, such as the Semantic Sensor Network (SSN) ontology, to facilitate seamless data sharing and interoperability with other components within the IoT ecosystem.
By integrating with existing IoT security frameworks and standards, the proposed model can enhance its adaptability and compatibility within IoT ecosystems. This integration allows the model to complement and enhance the existing security infrastructure, contributing to improved IoT security outcomes.
Comparisons with related systems
Table 10 highlights the proposed model’s performance outcomes by comparing it to previous systems. This study looked at existing literature and compared it to others based on standards, like the false positive rate (FPR), CPE, accuracy, and detection rate 38 , 38 , 39 , 40 , 41 , 42 , 43 , 44 , 45 , 47 . Through several experiments, the proposed system achieved the best evaluation metrics for accuracy, precision, detection rate, CPE, and lowest time complexity compared with previous solutions, as shown in Tables 10 and 11 .
Privacy concerns and data bias
The authors of this work have incorporated essential steps into the development and deployment of the proposed ML-based security model to effectively address privacy concerns and data bias, as well as ensure the technology’s ethical and responsible use within the IoT system.
The authors conducted a privacy impact assessment to determine if the proposed ML-based security model has any privacy issues or concerns.
To mitigate privacy concerns, the study implemented privacy-enhancing techniques . This process included data anonymization, encryption, differential privacy, or federated learning, which allows for training the proposed ML model without sharing raw data.
The study minimized the amount of personally identifiable information (PII) gathered and stored to reduce privacy risks. During the requirements engineering phase, we only collected the necessary data for the proposed machine learning-based security model, ensuring its safe storage and disposal when no longer required.
We implemented regular monitoring of the proposed ML model for potential biases in data and outcomes. Implementing a bias detection process is critical for identifying discriminatory patterns. We can take steps to mitigate detected biases , which may include adjusting training data, diversifying datasets, or utilizing bias correction algorithms.
Regularly monitor the proposed ML-based security model performance, including privacy aspects, and update it as needed to address emerging privacy concerns, mitigate biases, and ensure ongoing compliance with ethical standards.
Conclusions and upcoming work
This research introduces a new proposed ML-based security model to address the vulnerabilities in IoT systems. We designed the proposed model to autonomously handle the growing number of security problems associated with the IoT domain. This study analyzed the state-of-the-art security measures, intelligent solutions, and vulnerabilities in smart systems built on the IoT that make use of ML as a key technology for improving IoT security. The study illustrated the benefits and limitations of applying ML in an IoT environment and proposed a security model based on ML that can automatically address the rising concerns about high security in the IoT domain. The suggested method performs better in terms of accuracy and execution time than existing ML algorithms, which makes it a viable option for improving the security of IoT systems. This research evaluates the intrusion detection system using the BoTNet-IoT-L01 dataset. The research applied our proposed IDS model to a dataset that included more than 23 types of attacks. This study also utilized the NSL-KDD dataset to evaluate the intrusion detection mechanism and evaluated the proposed model in a real-world smart building environment. The presented ML-based model is found to have a good accuracy rate of 99.9% compared with previous research for improving IoT systems’ security. This paper’s contribution is the development of a novel ML-based security model that can improve the efficiency of cybersecurity systems and IoT infrastructure. The proposed model can keep threat knowledge databases up to date, analyze network traffic, and protect IoT systems from newly detected attacks by drawing on prior knowledge of cyber threats. This study presents a promising ML-based security approach to enhance IoT system security. However, future work and improvements remain possible. Expanding the dataset for the intrusion detection system evaluation could be one area of improvement. While the BoTNet-IoT-L01 and NSL-KDD datasets used in this study are comprehensive, they may not cover all possible types of attacks that could occur in an IoT environment. Therefore, our future research could focus on collecting and analyzing more diverse datasets to increase the performance of the proposed model. Furthermore, optimizing the proposed model’s execution time is crucial for real-world applications. Also, we could integrate the proposed model with other security solutions to create a more comprehensive and robust security system for IoT devices. Overall, the development of this novel ML-based security model is a significant contribution to the literature on ML security models and IoT security, and further work and improvements will continue to advance the field. Finally, the security analyst treats the AI-based IDS as a black box due to its inability to explain the decision-making process 48 . In our future work, we will expand our research by integrating blockchain-based AKA mechanisms with explainable artificial intelligence (XAI) to secure smart city-based consumer applications 49 . On the other hand, we can use the Shapley Additive Explanations (SHAP) mechanism to explain and interpret the prominent features that are most influential in the decision 50 .
Data availability
The corresponding author can provide the datasets used and/or analyzed in this work upon reasonable request.
Sharma, A., Singh, P. K. & Kumar, Y. An integrated fire detection system using IoT and image processing technique for smart cities. Sustain. Cities Soc. 61 , e4826 (2020).
Article Google Scholar
Sinan, K. SDG-11: Sustainable Cities and Communities. Emerging Technologies, Sustainable Development Goals Series 1st edn. (Springer, 2020).
Google Scholar
Hussain, F., Hussain, R., Hassan, S. A. & Hossain, E. Machine learning in IoT security: Current solutions and future challenges. IEEE Commun. Surv. Tutor. 22 (3), 1686–1721 (2020).
Bharati, S., Mondal, M. R. H., Podder, P. & Prasath, V. B. Federated learning: Applications, challenges and future directions. Int. J. Hybrid Intell. Syst. 18 (1–2), 19–35 (2022).
Shafiq, M., Tian, Z., Bashir, A. K., Du, X. & Guizani, M. Corrauc: A malicious BOT-IOT traffic detection method in IoT network using machine learning techniques. IEEE Internet Things J. 8 (5), 3242–3254 (2020).
Omolara, A. E. et al. The Internet of Things security: A survey encompassing unexplored areas and new insights. Comput. Secur. 112 , 102494 (2022).
Bharati, S., Podder, P., Mondal, M. R. H. & Paul, P. K. Applications and challenges of cloud integrated IoMT. In Cognitive Internet of Medical Things for Smart Healthcare 1st edn (eds Hassanien, A. E. et al. ) 67–85 (Springer, 2021).
Chapter Google Scholar
Özalp, A. N. et al . Layer-based examination of cyber-attacks in IoT. In 2022 International Congress on Human-Computer Interaction, Optimization and Robotic Applications (HORA) (IEEE, 2022).
Altunay, H. C. & Albayrak, Z. A hybrid CNN+ LSTM—Based intrusion detection system for industrial IoT networks. Eng. Sci. Technol. Int. J. 38 , 101322 (2023).
Abbas, Y., Ali, D., Gautam, S., Hadis, K. & Reza, M. P. Hybrid privacy preserving federated learning against irregular users in next-generation Internet of Things. J. Syst. Archit. 148 , 103088 (2024).
Abbas, Y., Ali, D. & Gautam, S. AP2FL: Auditable privacy-preserving federated learning framework for electronics in healthcare. IEEE Trans. Consumer Electron. 99 , 1 (2023).
Danyal, N., Abbas, Y., Ali, D. & Gautam, S. Federated quantum-based privacy-preserving threat detection model for consumer Internet of Things. IEEE Trans. Consumer Electron. https://doi.org/10.1109/TCE.2024.3377550 (2024).
Sanaz, N., Behrouz, Z., Abbas, Y. & Ali, D. Steeleye: An application-layer attack detection and attribution model in industrial control systems using semi-deep learning. In 2021 18th International Conference on Privacy, Security and Trust (PST), IEEE Xplore (2021).
Abbas, Y., Ali, D., Reza, M. P., Gautam, S. & Hadis, K. Secure intelligent fuzzy blockchain framework: Effective threat detection in IoT networks. Comput. Ind. 144 , 103801 (2023).
Gopi, K. J., Abbas, Y., Reza, M. P. & Seyedamin, P. Exploring privacy measurement in federated learning. J. Supercomput. 1 , 43 (2023).
Otoum, Y. & Nayak, A. On securing IoT from deep learning perspective. In Proc. 2020 IEEE Symposium on Computers and Communications (ISCC) 1–7 (2020).
Butun, I., Sterberg, P. O. & Song, H. Security of the Internet of Things: Vulnerabilities, attacks, and countermeasures. IEEE Commun. Surv. Tutor. 22 (1), 616–644 (2020).
Tahsien, S. M., Karimipour, H. & Spachos, P. Machine learning based solutions for security of Internet of Things (IoT): A survey. J. Netw. Comput. Appl. 161 , 102630 (2020).
Abiodun, O. I., Abiodun, E. O., Alawida, M., Alkhawaldeh, R. S. & Arshad, H. A review on the security of the Internet of Things: Challenges and solutions. Wirel. Person. Commun. 119 (3), 2603–2637 (2021).
Podder, P., Mondal, M. R. H., Bharati, S. & Paul, P. K. Review on the security threats of Internet of Things. Int. J. Comput. Appl. 176 (41), 37–45 (2020).
Hamad, Z. J. & Askar, S. Machine learning powered IoT for smart applications. Int. J. Sci. Bus. 5 (3), 92–100 (2021).
Xu, H. et al. A combination strategy of feature selection based on an integrated optimization algorithm and weighted K-nearest neighbor to improve the performance of network intrusion detection. Electronics 9 (8), 1206 (2020).
Bharati, S. & Mondal, M. R. H. Computational intelligence for managing pandemics. In 12 Applications and Challenges of AI-Driven IoHT for Combating Pandemics: A Review (eds Bharati, S. & Mondal, M. R. H.) 213–230 (De Gruyter, 2021).
Robel, M. R. A., Bharati, S., Podder, P. & Mondal, M. R. H. IoT driven healthcare monitoring system. In Fog, Edge, and Pervasive Computing in Intelligent IoT Driven Applications (eds Gupta, D. & Khamparia, A.) 161–176 (Wiley, 2020).
Podder, P., Mondal, M. R. H. & Kamruzzaman, J. Iris feature extraction using three-level Haar wavelet transform and modified local binary pattern. In Applications of Computational Intelligence in Multi-Disciplinary Research 1st edn (eds Elngar, A. A. et al. ) (Elsevier, 2022).
Chandavarkar, B. R. Hardcoded credentials and insecure data transfer in IoT: National and international status. In Proc. 2020 11th International Conference on Computing, Communication and Networking Technologies (ICCCNT) 1–7 (2020).
Ferrara, P., Mandal, A. K., Cortesi, A. & Spoto, F. Static analysis for discovering IoT vulnerabilities. Int. J. Softw. Tools Technol. Transf. 23 (1), 71–88 (2021).
Yu, Y., Guo, L., Liu, S., Zheng, J. & Wang, H. Privacy protection scheme based on CP-ABE in crowdsourcing-IoT for Smart Ocean. IEEE Internet Things J. 7 (10), 10061–10071 (2020).
Xiong, J. et al. A personalized privacy protection framework for mobile crowdsensing in IIoT. IEEE Trans. Ind. Inform. 16 (6), 4231–4241 (2020).
Jiang, X., Lora, M. & Chattopadhyay, S. An experimental analysis of security vulnerabilities in industrial IoT devices. ACM Trans. Internet Technol. 20 (1), 1–24 (2020).
Visoottiviseth, V., Sakarin, P., Thongwilai, J. & Choobanjong T. Signature-based and behavior-based attack detection with machine learning for home IoT devices. In Proc. 2020 IEEE Region 10 Conference (TENCON 2020) 829–834 (2020).
Turk, Z., Soto, B. G. D., Mantha, B. R. K., Maciel, A. & Georgescu, A. A systemic framework for addressing cybersecurity in construction. Autom. Construct. 133 (3), 103988 (2022).
Al Hayajneh, A., Bhuiyan, N. Z. A. & McAndrew, I. Improving internet of things (IoT) security with software defined networking (SDN). Computers 9 (1), 8 (2020).
Hussain, F., Hassan, S. A., Hussain, R. & Hossain, E. Machine learning for resource management in cellular and IoT networks: Potentials, current solutions, and open challenges. IEEE Commun. Surv. Tutor. 22 (2), 1251–1275 (2020).
IoT Dataset for Intrusion Detection Systems (IDS). https://www.kaggle.com/azalhowaide/iot-dataset-for-intrusion-detection-systems-ids (2023).
Nawir, M., Amir, A., Yaakob, N. & Lynn, O. B. Internet of Things (IoT): Taxonomy of security attacks. In Proc. 3rd International Conference in Electronic Design (ICED) 321–326 (2016).
Herzberg, B., Bekerman, D. & Zeifman, I. Breaking down mirai: An IoT DDoS botnet analysis. Incapsula Blog, Bots and DDoS, Security, (2016).
Ambusaidi, M. A., He, X., Nanda, P. & Tan, Z. Building an intrusion detection system using a filter-based feature selection algorithm. IEEE Trans. Comput. 65 (10), 2986–2998 (2016).
Article MathSciNet Google Scholar
Moustafa, N., Creech, G. & Slay, J. Big data analytics for intrusion detection system: Statistical decision-making using finite Dirichlet mixture models. In Data Analytics and Decision Support for Cybersecurity 1st edn (eds Moustafa, N. et al. ) 127–156 (Springer, 2017).
Tsai, C. F. & Lin, C. Y. A triangle area based nearest neighbors approach to intrusion detection. Pattern Recogn. 43 (1), 222–229 (2010).
Article ADS Google Scholar
Alom, M. Z., Bontupalli, V. & Taha, T. M. Intrusion detection using deep belief networks. In Proc. IEEE National Aerospace and Electronics Conference (NAECON) 339–344 (2015).
Yin, C., Zhu, Y., Fei, J. & He, X. A deep learning approach for intrusion detection using recurrent neural networks. IEEE Access 5 , 21954–21961 (2017).
Tang, T. A., Mhamdi, L., McLernon, D., Zaidi, S. A. R. & Ghogho, M. Deep learning approach for network intrusion detection in software defined networking. In Proc. 2016 International Conference on Wireless Networks and Mobile Communications (WINCOM) 258–263 (2016).
Ludwig, S. A. Intrusion detection of multiple attack classes using a deep neural net ensemble. In Proc. 2017 IEEE Symposium Series on Computational Intelligence (SSCI) 1–7 (2017).
Al-Hawawreh, M., Moustafa, N. & Sitnikova, E. Identification of malicious activities in industrial Internet of Things based on deep learning models. J. Inf. Secur. Appl. 41 , 1–11 (2018).
Shone, N., Ngoc, T. N., Phai, V. D. & Shi, Q. Deep learning approach to network intrusion detection. IEEE Trans. Emerg. Top. Comput. Intell. 2 (1), 41–50 (2018).
Subba, B., Biswas, S. & Karmakar, S. Enhancing performance of anomaly-based intrusion detection systems through dimensionality reduction using principal component analysis. In Proc. 2016 IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS) 1–6 (2016).
Kumar, R. et al. Blockchain-based authentication and explainable AI for securing consumer IoT applications. IEEE Trans. Consumer Electron. https://doi.org/10.1109/TCE.2023.3320157 (2024).
Javeed, D., Gao, T., Kumar, P. & Jolfaei, A. An explainable and resilient intrusion detection system for industry 5.0. IEEE Trans. Consumer Electron. 70 (1), 1342–1350. https://doi.org/10.1109/TCE.2023.3283704 (2024).
Kumar, R. et al. Digital twins-enabled zero touch network: A smart contract and explainable AI integrated cybersecurity framework. Future Gener. Comput. Syst. https://doi.org/10.1016/j.future.2024.02.015 (2024).
Download references
Acknowledgements
The authors extend their appreciation to the Deanship of Research and Graduate Studies at King Khalid University for funding this work through small group research under Grant Number (RGP1/129/45).
Author information
Authors and affiliations.
College of Computer Science, King Khalid University, Abha, Kingdom of Saudi Arabia
Hosam El-Sofany & Belgacem Bouallegue
Faculty of Informatics and Computer Science, British University in Egypt-BUE, Cairo, Egypt
Samir A. El-Seoud & Omar H. Karam
Electronics and Micro-Electronics Laboratory (E. μ. E. L), Faculty of Sciences of Monastir, University of Monastir, Monastir, Tunisia
Belgacem Bouallegue
You can also search for this author in PubMed Google Scholar
Contributions
Hosam El-Sofany is responsible for developing the original research concept, design, methodology, and implementation. He is also responsible for writing, editing, reviewing, checking against plagiarism using the iThenticate program, and proofreading. Samir A. El-Seoud: methodology, writing, and proofreading. Omar H. Karam: methodology, writing, and proofreading. Belgacem Bouallegue: methodology, writing, reviewing, editing, and proofreading.
Corresponding author
Correspondence to Hosam El-Sofany .
Ethics declarations
Competing interests.
The authors declare no competing interests.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Cite this article.
El-Sofany, H., El-Seoud, S.A., Karam, O.H. et al. Using machine learning algorithms to enhance IoT system security. Sci Rep 14 , 12077 (2024). https://doi.org/10.1038/s41598-024-62861-y
Download citation
Received : 13 November 2023
Accepted : 22 May 2024
Published : 27 May 2024
DOI : https://doi.org/10.1038/s41598-024-62861-y
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Internet of Things
- Sustainable development goals
- Sustainable cities and communities
- IoT security
- Machine learning
By submitting a comment you agree to abide by our Terms and Community Guidelines . If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies
Sign up for the Nature Briefing: AI and Robotics newsletter — what matters in AI and robotics research, free to your inbox weekly.
Does Mario Kart's Blue Shell even work? An investigation
We still Lakitu use it.
Mario Kart's Blue Shell (officially, the Spiny Shell) is one of the most iconic items in video game history. It's also one of the most controversial. A mainstay of the series since Mario Kart 64, the Blue Shell is a laser-guided missile targeted at the player in first place. It is near-unavoidable, and completely unavoidable in older games. Every Mario Kart player knows the feeling of dread - and childlike injustice - that accompanies the Blue Shell's sudden, high-pitched siren whine, announcing an unceremonious end to your pleasant race lead. But a research project at Queen's University Belfast has asked a fascinating question about the Blue Shell: does it even work?
Of course, the Blue Shell works in a literal sense - it blows up first place's hopes and dreams with depressing accuracy. The question is whether it does what it's designed to do, and what people believe it does. And if it doesn't, then why is it such a core part of the game?
The Blue Shell's fame can disguise its unusual status in gaming: it's surprisingly rare for items in competitive multiplayer to specifically target the leader, let alone to incapacitate them for multiple seconds. "Isn't it [...] a little bit unfair?" Kotaku sceptically asked Hideki Konno, 'the man behind Mario Kart', back in 2011. Now, one answer would be that it doesn't have to be fair: 'unfair' game mechanics are deeply important to how many games function. Overly hard bosses, unforeseeable traps, and harsh punishments can help build a world, give a game a sense of risk and difficulty, and shape player responsiveness.

But that's not the answer Konno gave. Instead, Konno stated that the Blue Shell was invented to try to increase the competitiveness and fairness of races: "We wanted to create a race where everyone was in it until the end." Various defences of the Blue Shell are based on the same idea: that the Blue Shell is 'obviously' a mechanism to preserve competitiveness. "Most obviously it's the Great Equaliser - the soaring blue embodiment of pure carnage that gives players at the back of the pack a fighting chance," argued Nathan Grayson in 2014, citing a video by popular YouTuber Extra History : "One reason for the Blue Shell to exist is obviously to serve as a catch-up mechanism [...] The Blue Shell helps to ensure that no one gets left completely in the dust without a chance to come back."
But is that true? Does the Blue Shell help to keep races competitive? Alex McMillan, then a master's student in computer science at QUB, set out to test this bit of gaming folk wisdom. They devised a metric called 'competitive proximity' to measure how close Mario Kart races are: essentially, it's an averaging of the distance between each consecutive pair of cars - first and second, second and third, and so on - so it measures how close the race is as a whole, rather than just the race between first and second. (Beating Pink Yoshi to fifth in a duff race can be what clinches the tournament for you, after all, and the Blue Shell is specifically meant to help out those in the back.)

Then, they tested it out. 50 test participants completed three races each in Mario Kart 64, all on Luigi's Raceway (to avoid environmental hazards affecting the results). One race had the regular likeliness of getting a Blue Shell; one made it three times more likely than usual that you'd get a Blue Shell, as long as you were far back enough to be eligible for one; and one removed the Blue Shell entirely.
The result? Blue Shells don't significantly affect how close Mario Kart races are. They might make the race leader swear loudly enough to scare the cat, but unlike, say, Golden Mushrooms or Bullet Bills, the player who gets a Blue Shell isn't going to be meaningfully helped by getting one. So, it's pretty official: the Blue Shell isn't a fairness or competitiveness mechanic, and it doesn't do what it was officially designed to do.
But Kosuke Yabuki, the director of Mario Kart 7 and 8, told Eurogamer in 2017 that when developers have experimented with removing the Blue Shell, they've concluded that "there's something not quite enough in the game" . So, even though the Blue Shell's mechanical function is surprisingly small over the course of a race, it has an important psychological function for players. What might that be?

In their conclusion, McMillan speculates that the Blue Shell is for players whose goal has changed: they are so far off the pace that they no longer anticipate winning, and may feel disengaged from the race. The Blue Shell gives far-back players an "illusion of agency", allowing them to "still feel like they are affecting the race". The Blue Shell allows the group of players to feel a sense of excitement and schadenfreude that accompanies the race leader's panic, but it also specifically allows the player who threw it to feel noticed, impactful, and dangerous. In a game with a lot of pent-up frustration, the Blue Shell allows the backmarkers to take out their frustration on the race leader, and this might help the group - or even a solo player - release some built-up tension and feel more positive about playing.
Yabuki himself hints at this: "Something I personally really consider is the human emotion element of the play experience," he says, "[and] if you have something that feels unfair or makes you angry... Everyone is different in that respect. What you will feel is unfair might be different to someone else." Yabuki describes wanting to balance the emotions of the experience, so that even if a given player feels frustrated on a given day, they'll still return to Mario Kart next week. The Blue Shell, then, may help spread frustration across a wider group, rather than keeping it concentrated on particular players.
Items that prioritise speed, particularly at the expense of other players, are usually the most useful for helping back-of-the-pack racers to catch up: "Lightning actually does what players want the Blue Shell to do, because it slows down everyone except you," McMillan notes. So if you actually want to challenge for the win, prioritise speed items. But Mario Kart isn't just a video game, it's also most famously a social game, and the Blue Shell's accidental genius comes from that: the Blue Shell can provide a way for less skilled or less lucky players to vent without bringing down the mood, and can work as a reminder to the race leaders to pay attention to their friends, even if it's to give them the middle finger.
So, next time you send someone a Blue Shell, be sure to remind them that it's in the spirit of friendship.
Read this next
- Mario Kart 8 has 703,560 customisation possibilities, but which racer is statistically best?
- The Simpsons' Mario Kart parody is the closest we've got to a Hit & Run sequel
- Nintendo Switch OLED Mario Kart bundle announced for Black Friday
Suggestions or feedback?
MIT News | Massachusetts Institute of Technology
- Machine learning
- Social justice
- Black holes
- Classes and programs
Departments
- Aeronautics and Astronautics
- Brain and Cognitive Sciences
- Architecture
- Political Science
- Mechanical Engineering
Centers, Labs, & Programs
- Abdul Latif Jameel Poverty Action Lab (J-PAL)
- Picower Institute for Learning and Memory
- Lincoln Laboratory
- School of Architecture + Planning
- School of Engineering
- School of Humanities, Arts, and Social Sciences
- Sloan School of Management
- School of Science
- MIT Schwarzman College of Computing
Adhesive coatings can prevent scarring around medical implants
Press contact :, media download.

*Terms of Use:
Images for download on the MIT News office website are made available to non-commercial entities, press and the general public under a Creative Commons Attribution Non-Commercial No Derivatives license . You may not alter the images provided, other than to crop them to size. A credit line must be used when reproducing images; if one is not provided below, credit the images to "MIT."
Previous image Next image
When medical devices such as pacemakers are implanted in the body, they usually provoke an immune response that leads to buildup of scar tissue around the implant. This scarring, known as fibrosis, can interfere with the devices’ function and may require them to be removed.
In an advance that could prevent that kind of device failure, MIT engineers have found a simple and general way to eliminate fibrosis by coating devices with a hydrogel adhesive. This adhesive binds the devices to tissue and prevents the immune system from attacking it.
“The dream of many research groups and companies is to implant something into the body that over the long term the body will not see, and the device can provide therapeutic or diagnostic functionality. Now we have such an ‘invisibility cloak,’ and this is very general: There’s no need for a drug, no need for a special polymer,” says Xuanhe Zhao, an MIT professor of mechanical engineering and of civil and environmental engineering.
The adhesive that the researchers used in this study is made from cross-linked polymers called hydrogels, and is similar to a surgical tape they previously developed to help seal internal wounds. Other types of hydrogel adhesives can also protect against fibrosis, the researchers found, and they believe this approach could be used for not only pacemakers but also sensors or devices that deliver drugs or therapeutic cells.
Zhao and Hyunwoo Yuk SM ’16, PhD ’21, a former MIT research scientist who is now the chief technology officer at SanaHeal, are the senior authors of the study, which appears today in Nature . MIT postdoc Jingjing Wu is the lead author of the paper.
Preventing fibrosis
In recent years, Zhao’s lab has developed adhesives for a variety of medical applications, including double-sided and single-sided tapes that could be used to heal surgical incisions or internal injuries. These adhesives work by rapidly absorbing water from wet tissues, using polyacrylic acid, an absorbent material used in diapers. Once the water is cleared, chemical groups called NHS esters embedded in the polyacrylic acid form strong bonds with proteins at the tissue surface. This process takes about five seconds.
Several years ago, Zhao and Yuk began exploring whether this kind of adhesive could also help keep medical implants in place and prevent fibrosis from occurring.
To test this idea, Wu coated polyurethane devices with their adhesive and implanted them on the abdominal wall, colon, stomach, lung, or heart of rats. Weeks later, they removed the device and found that there was no visible scar tissue. Additional tests with other animal models showed the same thing: Wherever the adhesive-coated devices were implanted, fibrosis did not occur, for up to three months.
“This work really has identified a very general strategy, not only for one animal model, one organ, or one application,” Wu says. “Across all of these animal models, we have consistent, reproducible results without any observable fibrotic capsule.”
Using bulk RNA sequencing and fluorescent imaging, the researchers analyzed the animals’ immune response and found that when devices with adhesive coatings were first implanted, immune cells such as neutrophils began to infiltrate the area. However, the attacks quickly quenched out before any scar tissue could form.
“For the adhered devices, there is an acute inflammatory response because it is a foreign material,” Yuk says. “However, very quickly that inflammatory response decayed, and then from that point you do not have this fibrosis formation.”
One application for this adhesive could be coatings for epicardial pacemakers — devices that are placed on the heart to help control the heart rate. The wires that contact the heart often become fibrotic, but the MIT team found that when they implanted adhesive-coated wires in rats, they remained functional for at least three months, with no scar tissue formation.
“The formation of fibrotic tissue at the interface between implanted medical devices and the target tissue is a longstanding problem that routinely causes failure of the device. The demonstration that robust adhesion between the device and the tissue obviates fibrotic tissue formation is an important observation that has many potential applications in the medical device space,” says David Mooney, a professor of bioengineering at Harvard University, who was not involved in the study.
Mechanical cues
The researchers also tested a hydrogel adhesive that includes chitosan, a naturally occurring polysaccharide, and found that this adhesive also eliminated fibrosis in animal studies. However, two commercially available tissue adhesives that they tested did not show this antifibrotic effect because the commercially available adhesives eventually detached from the tissue and allowed the immune system to attack.
In another experiment, the researchers coated implants in hydrogel adhesives but then soaked them in a solution that removed the polymers’ adhesive properties, while keeping their overall chemical structure the same. After being implanted in the body, where they were held in place by sutures, fibrotic scarring occurred. This suggests that there is something about the mechanical interaction between the adhesive and the tissue that prevents the immune system from attacking, the researchers say.
“Previous research in immunology has been focused on chemistry and biochemistry, but mechanics and physics may play equivalent roles, and we should pay attention to those mechanical and physical cues in immunological responses,” says Zhao, who now plans to further investigate how those mechanical cues affect the immune system.
Yuk, Zhao, and others have started a company called SanaHeal, which is now working on further developing tissue adhesives for medical applications.
“As a team, we are interested in reporting this to the community and sparking speculation and imagination as to where this can go,” Yuk says. “There are so many scenarios in which people want to interface with foreign or manmade material in the body, like implantable devices, drug depots, or cell depots.”
The research was funded by the National Institutes of Health and the National Science Foundation.
Share this news article on:
Press mentions, interesting engineering.
MIT engineers have developed a new adhesive, low-cost hydrogel that can stop fibrosis often experienced by people with pacemakers and other medical devices, reports for Maria Bolevich Interesting Engineering . “These findings may offer a promising strategy for long-term anti-fibrotic implant–tissue interfaces,” explains Prof. Xuanhe Zhao.
Previous item Next item
Related Links
- Xuanhe Zhao
- Hyunwoo Yuk
- Jingjing Wu
- Department of Mechanical Engineering
- Department of Civil and Environmental Engineering
Related Topics
- Mechanical engineering
- Civil and environmental engineering
- Biomedical engineering
- Medical devices
- National Institutes of Health (NIH)
- National Science Foundation (NSF)
Related Articles

Engineers develop surgical “duct tape” as an alternative to sutures

Double-sided tape for tissues could replace surgical sutures

Super-strong surgical tape detaches on demand

Paper-folding art inspires better bandages
More mit news.

Scientists identify mechanism behind drug resistance in malaria parasite
Read full story →

Getting to systemic sustainability

New MIT-LUMA Lab created to address climate challenges in the Mediterranean region

MIT Press releases Direct to Open impact report

Modeling the threat of nuclear war

Modular, scalable hardware architecture for a quantum computer
- More news on MIT News homepage →
Massachusetts Institute of Technology 77 Massachusetts Avenue, Cambridge, MA, USA
- Map (opens in new window)
- Events (opens in new window)
- People (opens in new window)
- Careers (opens in new window)
- Accessibility
- Social Media Hub
- MIT on Facebook
- MIT on YouTube
- MIT on Instagram

IMAGES
VIDEO
COMMENTS
Simply put, a research paper is a scholarly written work where the writer (that's you!) answers a specific question (this is called a research question) through evidence-based arguments. Evidence-based is the keyword here. In other words, a research paper is different from an essay or other writing assignments that draw from the writer's ...
Create a research paper outline. Write a first draft of the research paper. Write the introduction. Write a compelling body of text. Write the conclusion. The second draft. The revision process. Research paper checklist. Free lecture slides.
Step 4: Create a research design. The research design is a practical framework for answering your research questions. It involves making decisions about the type of data you need, the methods you'll use to collect and analyze it, and the location and timescale of your research. There are often many possible paths you can take to answering ...
By refining your focus, you can produce a thoughtful and engaging paper that effectively communicates your ideas to your readers. 5. Write a thesis statement. A thesis statement is a one-to-two-sentence summary of your research paper's main argument or direction.
Table of contents. Step 1: Introduce your topic. Step 2: Describe the background. Step 3: Establish your research problem. Step 4: Specify your objective (s) Step 5: Map out your paper. Research paper introduction examples. Frequently asked questions about the research paper introduction.
Definition: Research Paper is a written document that presents the author's original research, analysis, and interpretation of a specific topic or issue. It is typically based on Empirical Evidence, and may involve qualitative or quantitative research methods, or a combination of both. The purpose of a research paper is to contribute new ...
This interactive resource from Baylor University creates a suggested writing schedule based on how much time a student has to work on the assignment. "Research Paper Planner" (UCLA) UCLA's library offers this step-by-step guide to the research paper writing process, which also includes a suggested planning calendar.
To write an informative abstract you have to provide the summary of the whole paper. Informative summary. In other words, you need to tell about the main points of your work, the methods used, the results and the conclusion of your research. To write a descriptive abstract you will not have to provide any summery.
Then, writing the paper and getting it ready for submission may take me 3 to 6 months. I like separating the writing into three phases. The results and the methods go first, as this is where I write what was done and how, and what the outcomes were. In a second phase, I tackle the introduction and refine the results section with input from my ...
Along with Meredith Harris, Mitchell Allen. Hannah, a writer and editor since 2017, specializes in clear and concise academic and business writing. She has mentored countless scholars and companies in writing authoritative and engaging content. Writing a research paper is made easy with our 7 step guide.
1. Create an outline to map out your paper's structure. Use Roman numerals (I., II., III., and so on) and letters or bullet points to organize your outline. Start with your introduction, write out your thesis, and jot down your key pieces of evidence that you'll use to defend your argument.
Research paper format is an essential aspect of academic writing that plays a crucial role in the communication of research findings.The format of a research paper depends on various factors such as the discipline, style guide, and purpose of the research. It includes guidelines for the structure, citation style, referencing, and other elements of the paper that contribute to its overall ...
The pages in this section cover the following topic areas related to the process of writing a research paper: Genre - This section will provide an overview for understanding the difference between an analytical and argumentative research paper. Choosing a Topic - This section will guide the student through the process of choosing topics ...
In order to publish a (good) scientific paper, you need to be able to compare your results to prior results---often directly and quantitatively in your experimental section. If you already have prior methods that you are comparing to in your experimental section, then that's a good seed for your related work. Look at the papers describing those ...
This paper also offers insights, backed by evidenced-based research which aims to equip organizations and employees with a comprehensive understanding of the evolving dynamics of remote work.
A decimal outline is similar in format to the alphanumeric outline, but with a different numbering system: 1, 1.1, 1.2, etc. Text is written as short notes rather than full sentences. Example: 1 Body paragraph one. 1.1 First point. 1.1.1 Sub-point of first point. 1.1.2 Sub-point of first point.
Aside from exploring the influence of psychological needs on work motivation, this paper also considers country-level factors. Previous research (e.g., ) has examined the influence of social institutions and national cultures on work motivation. However, the moderating effects of country-level factors have to be investigated, given the ...
For the United States, we build on estimates published in our 2023 report Generative AI and the future of work in America. We included multiple drivers in our modeling: automation potential, net-zero transition, e-commerce growth, remote work adoption, increases in income, aging populations, technology investments, and infrastructure investments.
The biggest hit has come to Wiley, a 217-year-old publisher based in Hoboken, N.J., which Tuesday will announce that it is closing 19 journals, some of which were infected by large-scale research ...
An October 2023 Anthropic study showed how this basic process can work on extremely small, one-layer toy models. The company's new paper scales that up immensely, identifying tens of millions of ...
Proof assistants like Lean have revolutionized mathematical proof verification, ensuring high accuracy and reliability. Although large language models (LLMs) show promise in mathematical reasoning, their advancement in formal theorem proving is hindered by a lack of training data. To address this issue, we introduce an approach to generate extensive Lean 4 proof data derived from high-school ...
Writing a research proposal can be quite challenging, but a good starting point could be to look at some examples. We've included a few for you below. Example research proposal #1: "A Conceptual Framework for Scheduling Constraint Management" Example research proposal #2: "Medical Students as Mediators of Change in Tobacco Use" Title page
The paper, which is based on a narrative review and meta-analysis research project, was written by an international team of 13 researchers from universities including University of Oxford (UK ...
The paper proposes an ML-based security model that autonomously handles the growing number of security issues associated with the IoT domain. ... In our future work, we will expand our research by ...
Examples of literature reviews. Step 1 - Search for relevant literature. Step 2 - Evaluate and select sources. Step 3 - Identify themes, debates, and gaps. Step 4 - Outline your literature review's structure. Step 5 - Write your literature review.
Here's a video about playing Mario Kart hungover.Watch on YouTube. But that's not the answer Konno gave. Instead, Konno stated that the Blue Shell was invented to try to increase the ...
In recent years, Zhao's lab has developed adhesives for a variety of medical applications, including double-sided and single-sided tapes that could be used to heal surgical incisions or internal injuries. These adhesives work by rapidly absorbing water from wet tissues, using polyacrylic acid, an absorbent material used in diapers.
Submitting a research paper to an academic journal; Writing a book or research proposal; Applying for research grants; It's easiest to write your abstract last, right before the proofreading stage, because it's a summary of the work you've already done. Your abstract should: Be a self-contained text, not an excerpt from your paper