- Browse All Articles
- Newsletter Sign-Up

InformationTechnology →
No results found in working knowledge.
- Were any results found in one of the other content buckets on the left?
- Try removing some search filters.
- Use different search filters.
Microsoft Research: Advancing science and technology to benefit humanity
MICROSOFT RESEARCH PODCAST
Ideas: Language technologies for everyone with Kalika Bali

Research Focus: Week of April 1, 2024
April 3, 2024

AI Frontiers: Rethinking intelligence with Ashley Llorens and Ida Momennejad
March 28, 2024 | Ashley Llorens, Ida Momennejad

Learning from interaction with Microsoft Copilot (web)
March 27, 2024
Explore Microsoft Research Forum

Microsoft Research Forum

Transforming health care and the natural sciences, AI and society, and the evolution of foundational AI technologies

Research Forum Brief | January 2024

Research Forum Brief | March 2024
Careers in research, principal research manager – microsoft research asia .
Location : Singapore
Principal Researcher – Microsoft Research Asia
Location : Seoul, Korea
Location : Tokyo, Japan
Senior Data Scientist – M365 Designer
Location : Noida, Uttar Pradesh, India
Data Scientist – Azure Storage team
Location : Bangalore, Karnataka, India
Senior Data Scientist – Azure Storage team
Data science intern opportunity .
Location : Belgrade, Serbia
Senior Research Technical Program Manager – Microsoft Research Accelerator
Location : Cambridge, UK
Senior Researcher – Machine learning
Location : Amsterdam, Netherlands
Data Scientist – Industry Solutions Delivery (ISD) Engineering & Architecture Group (EAG)
Locations : Italy; Spain
Data Scientist – Industry Solutions Delivery (ISD) Engineering & Architecture Group (EAG)
Locations : Berlin, Germany; Germany; Munich, Bavaria, Germany; Remote
Cambridge Residency Programme – Researcher in Nearfield Microscopy and Nanofabrication
Data scientist manager – azure monitor .
Locations : Beer-Sheva, Israel; Haifa, Israel; Herzliya, Tel Aviv, Israel; Nazareth, Northern, Israel
Security Researcher II – Microsoft Defender For Endpoint
Principal applied science manager – msai .
Locations : Beer-Sheva, Israel; Haifa, Israel; Herzliya, Tel Aviv, Israel
Supply Chain Data Scientist – Cloud Operations + Innovation (CO+I) team
Locations : Atlanta, GA, US; Phoenix, AZ, US; Redmond, WA, US; San Antonio, TX, US
Senior Data Scientist (Fabric) – Microsoft Azure Insights and Analytics team
Locations : Redmond, WA, US; Remote (within US)
Principal Data Scientist – Microsoft Security
Location : Redmond, WA, US
Chercheur(se) Scientifique Principal(e) / Senior Research Scientist
Locations : Montreal, Quebec, Canada; Remote (within US/CAN)
Principal Technical Program Manager – Microsoft Research Core
Post doc researcher – artificial intelligence, machine learning, and reinforcement learning (empirical) .
Location : New York, NY, US
Research Software Engineering II – Microsoft Research & Incubations
Locations : Brazil; Chile; Costa Rica; Mexico; Puerto Rico; Remote
Senior Data & Applied Scientist – Copilot
Locations : Chile; Colombia; Costa Rica; Mexico; Puerto Rico; Remote
Events & conferences
Microsoft at nsdi ’24 .
Upcoming: April 16, 2024 – April 18, 2024
Santa Clara, CA, USA
Microsoft at ICLR 2024
Upcoming: May 7, 2024 – May 11, 2024
Vienna, Austria
Microsoft at CHI 2024
Upcoming: May 11, 2024 – May 16, 2024
Honolulu, Hawai'i
News & awards
Ai ‘for all’: how access to new models is advancing academic research, from astronomy to education .
Microsoft Source | Mar 12, 2024
Village by village, creating the building blocks for AI tools
LinkedIn | Mar 1, 2024
Ryen White selected for ACM SIGCHI Academy Class of 2024
ACM SIGCHI | Feb 28, 2024
3 big AI trends to watch in 2024
Microsoft News Center | Feb 13, 2024
- Follow on Twitter
- Like on Facebook
- Follow on LinkedIn
- Subscribe on Youtube
- Follow on Instagram
- Subscribe to our RSS feed
Share this page:
- Share on Twitter
- Share on Facebook
- Share on LinkedIn
- Share on Reddit
- Please enable javascript in your browser settings and refresh the page to continue.
Exponential IT Research Center
- AI Insights
- AI Marketplace
- Artificial Intelligence Research Center
- AI Workforce Development
- Digital Transformation Research Center
- Trends & Priorities Research Center
Latest Research

Prepare to Negotiate Your Generative AI Vendor Contract

Identify the Customer Satisfaction Metrics That Matter

Deploy AIOps to Improve IT Operations

Interoperability: The True Power Behind the Digital Front Door

Use ChatGPT Wisely to Improve Productivity

Develop an Exponential IT Roadmap

Build Your AI Business Case

Third-Party Data in Retail Banking

Digital Use Case Library for Oil & Gas

Gauge Your Exponential IT Readiness
- Tools & Resources
To keep pace with the exponential technology curve, adopt an Exponential IT mindset and practices. Assess your organization’s readiness and embark on a transformation journey.
Featured Research
An overview of Exponential IT predictions, insights, and recommendations.
Unlock Exponential IT Research Center Capstone Deck
Get instant access.
Organizations are adopting exponential technologies at an accelerated rate, with or without IT.
IT must adopt an Exponential IT mindset and define its own transformation journey to not only adapt and thrive in a new technological landscape but also evolve into true organizational leaders.

Adopt an Exponential IT Mindset

Explore the Art of the Possible

Gauge Your Organizational Readiness

Build an Exponential IT Roadmap

Embark on Your Exponential IT Journey
Let us help you get started on this journey, as technology becomes exponential, so must it, adopt an exponential it framework.
Today's and future generative AI capabilities have led to the next sea change for IT leaders. Exponential IT is Info-Tech's answer for IT leaders on how to adapt rather than fall behind. Our proprietary framework defines the aspirations and tactics needed for all areas of a modern IT department.

IT NEEDS TO TAKE CHARGE
Exponential it keynote presentation.
As technology advances exponentially, so must your entire organization led by IT. Our keynote presentation makes a compelling case for Exponential IT with a clear vision for the future across nine IT domains.

Gauge Your Readiness to Transform
Exponential it readiness diagnostic.
Assess the readiness of your organization to embrace and extract value from exponential technologies. Measure executive stakeholder perceptions of organizational readiness for transformation and IT leader perceptions of IT readiness for transformation.
This readiness assessment is a crucial initial step in the Exponential IT journey to help you understand the needs, opportunities, and priorities of stakeholders across the organization.

Plan Your Exponential IT Journey
As technology advances exponentially, IT needs to undergo transformation to continue creating value for the organization. Build an actionable roadmap of initiatives towards Exponential IT, which will help shift the role of IT from Trusted Operator to true Organizational Leader.

Exponential IT beckons, but succeeding in this new world requires bold steps.
IT leaders will have to lead the charge through the inherent uncertainties and opportunities. They will have to develop and prioritize new practices, leveraging exponential technologies to create business value and results, both for IT and for their organization.
Exponential IT therefore has implications across the many capabilities of our IT Management and Governance model. Info-Tech offers an integrated set of principles across nine domains to help IT leaders change the trajectory of their organizations.
Strategy, Risk & Governance
Capitalize on the commoditization of it.
- Stop being pulled, start pushing – Co-own organizational outcomes
- Own your seat at the table – Lead new technology governance
- Do more valuable work – Transform Infrastructure and Applications into utilities
Financial & Vendor Management
Shift from technology to capabilities.
- Stop experimenting, start delivering – Fund exponential value creation
- Add cats to the herd – Boost vendor management practices
- Demonstrate your value – Build outcome measurement
People & Leadership
Lead transformation to a technology-first enterprise.
- Stop empire-building – Embrace federated and hybrid operating models
- Shatter the org chart – Reinvent the resource strategy
- Train, Invest, and Nurture – Let the workforce be with you
Service Planning & Architecture
Deliver organizational capabilities.
- Fasten your seatbelts – Shift from service to outcome delivery
- Stop siloed applications – Create integrated enterprise services
- Get into the weeds – Architect business capabilities
Infrastructure & Operations
Focus on value over assets.
- Give up control – Let AI take over core operations
- Become a banker – Implement FinOps
- Lean into autonomous provisioning – Abstract away the underlying infrastructure
Security & Privacy
Shift from reactive to predictive.
- Assume they are more sophisticated than you – Defend against AI-enabled attacks
- Go back to the drawing board – Mitigate rampant privacy risks
- Overcome your hesitation – Enable autonomous decision making
Applications
Move from applications to organizational capabilities.
- Deliver continuously (finally) – Use AI and ML to drive automation
- Ban one-offs – Double down on platforms
- Don’t be just a partner – Create true co-owners
Data & Analytics
Make data capabilities a differentiator.
- Go beyond analytics – Treat data as a product
- Use data as the lifeblood – Augment your data for more value
- Default to AI – Team up DataOps with MLOps
Project & Portfolio Management
Automate & focus on high-value activities.
- Solve problems, not calendars – Automate traditional PMO capabilities
- Plan in real time – Let AI run ongoing resource allocation
- Trust, but verify – Enable true accountability
Additional Resources
Book an appointment.
Please confirm the appointment time and click Schedule.
Your call is being booked. A representative will be available to assist you if needed.
Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
Computer science articles from across Nature Portfolio
Computer science is the study and development of the protocols required for automated processing and manipulation of data. This includes, for example, creating algorithms for efficiently searching large volumes of information or encrypting data so that it can be stored and transmitted securely.
Latest Research and Reviews

A noise audit of human-labeled benchmarks for machine commonsense reasoning
- Mayank Kejriwal
- Henrique Santos
- Deborah L. McGuinness
Psycholinguistic and emotion analysis of cryptocurrency discourse on X platform
- Moein Shahiki Tash
- Olga Kolesnikova
- Grigori Sidorov
Advancing forensic-based investigation incorporating slime mould search for gene selection of high-dimensional genetic data
- Ali Asghar Heidari
- Guoxi Liang
Forward layer-wise learning of convolutional neural networks through separation index maximizing
- Ahmad Kalhor
- Melika Sadeghi Tabrizi
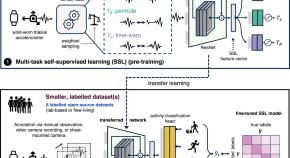
Self-supervised learning for human activity recognition using 700,000 person-days of wearable data
- Aiden Doherty
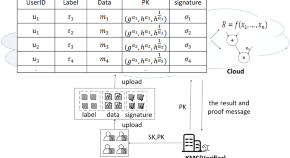
An efficient polynomial-based verifiable computation scheme on multi-source outsourced data
- Yiran Zhang
- Huizheng Geng
News and Comment
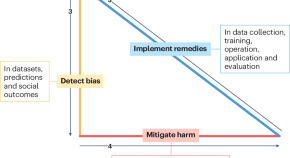
Medical artificial intelligence should do no harm
Bias and distrust in medicine have been perpetuated by the misuse of medical equations, algorithms and devices. Artificial intelligence (AI) can exacerbate these problems. However, AI also has potential to detect, mitigate and remedy the harmful effects of bias to build trust and improve healthcare for everyone.
- Melanie E. Moses
- Sonia M. Gipson Rankin

AI hears hidden X factor in zebra finch love songs
Machine learning detects song differences too subtle for humans to hear, and physicists harness the computing power of the strange skyrmion.
- Nick Petrić Howe
- Benjamin Thompson
Three reasons why AI doesn’t model human language
- Johan J. Bolhuis
- Stephen Crain
- Andrea Moro

Generative artificial intelligence in chemical engineering
Generative artificial intelligence will transform the way we design and operate chemical processes, argues Artur M. Schweidtmann.
- Artur M. Schweidtmann

Why scientists trust AI too much — and what to do about it
Some researchers see superhuman qualities in artificial intelligence. All scientists need to be alert to the risks this creates.

Is ChatGPT making scientists hyper-productive? The highs and lows of using AI
Large language models are transforming scientific writing and publishing. But the productivity boost that these tools bring could have a downside.
- McKenzie Prillaman
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies
Tech at the edge: Trends reshaping the future of IT and business
It is easy to become numb to the onslaught of new technologies hitting the market, each with its own promise of changing (more often “revolutionizing”) the business world. But our analysis of some of the more meaningful tech trends lays out a convincing case that something significant is happening. 1 Michael Chui, Roger Roberts, and Lareina Yee, “ McKinsey Technology Trends Outlook 2022 ,” McKinsey, August 24, 2022.
These tech trends are generally accelerating the primary characteristics that have defined the digital era: granularity, speed, and scale. But it’s the magnitude of these changes—in computing power, bandwidth, and analytical sophistication—that is opening the door to new innovations, businesses, and business models.
The emergence of cloud and 5G , for example, exponentially increases compute power and network speeds that can enable greater innovation. Developments in the metaverse of augmented and virtual reality open the doors to virtual R&D via digital twins , for example, and immersive learning. Advances in AI, machine learning, and software 2.0 (machine-written code) bring a range of new services and products, from autonomous vehicles to connected homes, well within reach.
Much ink has been spilled on identifying tech trends, but less attention has been paid to the implications of those changes. To help understand how management will need to adapt in the face of these technology trends in the next three to five years, we spoke to business leaders and leading thinkers on the topic. We weren’t looking for prognostications; we wanted to explore realistic scenarios, their implications, and what senior executives might do to get ready.
The discussions pinpointed some broad, interrelated shifts, such as how technology’s radically increasing power is exerting a centrifugal force on the organization, pushing innovation to expert networks at the edges of the company; how the pace and proliferation of these innovations calls for radical new approaches to continuous learning built around skills deployed at points of need; how these democratizing forces mean that IT can no longer act as a centralized controller of technology deployment and operations but instead needs to become a master enabler and influencer; and how these new technologies are creating more data about, and touchpoints with, customers, which is reshaping the boundaries of trust and requiring a much broader understanding of a company’s security responsibilities.
1. Innovation at the edge
Key tech trends.
We estimate that 70 percent of companies will employ hybrid or multicloud management technologies, tools, and processes . 2 “ The top trends in tech ,” McKinsey, June 15, 2021. At the same time, 5G will deliver network speeds that are about ten times faster than current speeds on 4G LTE networks, 3 Irina Ivanova, “What consumers need to know about this week’s AT&T–Verizon 5G rollout,” CBS News, January 20, 2022. with expectations of speeds that are up to 100 times faster with 40 times faster latency. 4 “5G speed: 5G vs. 4G performance compared,” Tom’s Guide, June 1, 2021. By 2024, more than 50 percent of user touches will be augmented by AI-driven speech, written word, or computer-vision algorithms , 5 “ The top trends in tech ,” June 15, 2021. while global data creation is projected to grow to more than 180 zettabytes by 2025, up from 64.2 zettabytes in 2020. 6 “Amount of data created, consumed, and stored 2010–2025,” Statista Research Department, May 23, 2022. The low-code development platform market‘s compound annual growth rate (CAGR) is projected at about 30 percent through 2030. 7 “Global $187 billion low-code development platform market to 2030,” GlobeNewswire, November 10, 2020.
Shift: Innovation develops around personal networks of experts at the porous edge of the organization and is supported by capabilities that scale the benefits across the business.
These technologies promise access to virtually unlimited compute power and massive data sets, as well as a huge leap in bandwidth at low cost, making it cheaper and easier to test, launch, and scale innovations quickly. The resulting acceleration in innovation will mean that companies can expect more disruptions from more sources. Centralized strategic and innovation functions cannot hope to keep pace on their own. Companies will need to be much more involved in networks outside their organizations to spot, invest in, and even acquire promising opportunities.
Corporate venture-capital (VC) funds with centralized teams have looked to find and fund innovation, but their track record has been spotty, often because the teams lack the requisite skills and are simply too far removed from the constantly evolving needs of individual business units. Instead, companies will need to figure out how to tap their front lines, particularly business domain experts and technologists, to enable them to act, in effect, as the business’s VC arm. That’s because the people who are writing code and building solutions are often well plugged into strong external networks in their fields and have the expertise to evaluate new developments. One pharma company, for example, taps its own expert researchers in various fields, such as gene expression, who know well the people outside the company who are leaders in the field.
While companies will need to create incentives and opportunities for engineers to build up and engage with their networks, the key focus must be on empowering teams so they can spend their allocated budget as they see fit—for example, experimenting and failing without penalty (within boundaries) and deciding on technologies to meet their goals (within prescribed guidelines).
The IT organization of the future can play an important role in building up a scaling capability to make that innovation work for the business, something that has traditionally been a challenge. Individual developers or small teams working fast don’t tend to naturally think about how to scale an application. That issue is likely to be exacerbated as nontechnical users working in pockets across organizations use low-code/no-code (LC/NC) applications to design and build programs with point-and-click or pull-down-menu interfaces.
One pharma company has taken this idea to heart by giving local business units the flexibility to run with a nonstandard idea when it has proven to be better than what the company is already doing. In return for that flexibility, the business unit must commit to helping the rest of the organization use the new idea, and IT builds it into the company’s standards.
In considering how this scaling capability might work, companies could, for example, assign advanced developers to “productize” applications by refactoring code so they can scale. IT leadership can provide tools and platforms, reusable-code libraries that are easily accessible, and flexible, standards-based architecture so that innovations can be scaled across the business more easily.
Questions for leadership
- What incentives will best encourage engineers and domain experts to develop, maintain, and tap into their networks?
- What processes are in place for tracking and managing VC activity at the edge?
- What capabilities do you need to identify innovation opportunities and “industrialize” the best ones so they can be shared across the organization?
For more on how to empower workers at the edge, see “ Tech companies innovate at the edge. Legacy companies can too ,” in Harvard Business Review.
Would you like to learn more about McKinsey Digital ?
2. a perpetual-learning culture.
Advances in AI, machine learning, robotics, and other technologies have increased the pace of change tenfold . By 2025, we estimate that 50 billion devices will be connected to the Industrial Internet of Things (IIoT), while 70 percent of manufacturers are expected to be using digital twins regularly (by 2022). 8 “ The top trends in tech ,” June 15, 2021. Some 70 percent of new applications will use LC/NC technologies by 2025, up from less than 25 percent in 2020. 9 “Gartner says cloud will be the centerpiece of new digital experiences,” Gartner, November 10, 2021. The global metaverse revenue opportunity could approach $800 billion in 2024, up from about $500 billion in 2020. 10 Bloomberg Intelligence, “Metaverse may be $800 billion market, next tech platform,” Bloomberg, December 1, 2021. This proliferation of technological innovations means we can expect to experience more progress in the next decade than in the past 100 years combined, according to entrepreneur and futurist Peter Diamandis. 11 Peter Diamandis and Steven Kotler, The Future Is Faster than You Think: How Converging Technologies Are Transforming Business, Industries, and Our Lives , New York: Simon & Schuster, 2020.
Shift: Tech literacy becomes core to every role, requiring learning to be continuous and built at the level of individual skills that are deployed at the point of need.
With the pace and proliferation of technologies pushing innovation to the edge of the organization, businesses need to be ready to incorporate the most promising options from across the front lines. This will create huge opportunities, but only for those companies that develop true tech intelligence through a perpetual-learning culture. The cornerstone of this effort includes training all levels of personnel, from “citizen developers” working with easy-to-use LC/NC tools or in entirely new environments such as the metaverse, to full-stack developers and engineers, who will need to continually evolve their skills to keep up with changing technologies. We’re already seeing situations where poorly trained employees use LC/NC to churn out suboptimal products.
While there will always be a need for more formalized paths for foundational learning, we anticipate an acceleration in the shift from teaching curricula periodically to continuous learning that can deliver varying technical skills across the entire organization. In practice, that will mean orienting employee development around delivering skills. This requires breaking down a capability into its smallest sets of composite skills. One large tech company, for example, created 146,000 skills data points for the 1,200 technical skills it was assessing.
The key point is that these skills “snippets”—such as a block of code or a video of a specific negotiating tactic—need to be integrated into the workflow so that they’re delivered when needed. This might be called a “LearnOps” approach, where learning is built into the operations. This integration mentality is established at Netflix, where data scientists partner directly with product managers, engineering teams, and other business units to design, execute, and learn from experiments. 12 Netflix Technology Blog , “Experimentation is a major focus of data science across Netflix,” blog entry by Martin Tingley et al., January 11, 2022.
As important as being able to deploy learning is building a learning culture by making continuous learning expected and easy to do. The way top engineers learn can be instructive. This is a community that is highly aware of the need to keep their skills up to date. They have ingrained habits of sharing code, and they gravitate to projects where they can learn. One advantage of using open source, for example, is the built-in community that constantly updates and reviews code. In the same spirit, we’re seeing companies budget extra time to allow people to try new tools or technologies when they’re building a product. Other companies are budgeting for “learning buffers” to allow for setbacks in product development that teams can learn from. 13 “ The big boost: How incumbents successfully scale their new businesses ,” McKinsey, August 27, 2020.
Netflix, which makes broad, open, and deliberate information sharing a core value, built the Netflix experimentation platform as an internal product that acts as a repository of solutions for future teams to reuse. It has a product manager and innovation road map, with the goal of making experimentation a simple and integrated part of the product life cycle. 14 Netflix Technology Blog , “Netflix: A culture of learning,” blog entry by Martin Tingley et al., January 25, 2022.
To support this kind of continuous learning and experimentation, companies will need to accept mistakes. The art will be in limiting the impact of potentially costly mistakes, such as the loss or misuse of customer data. IT will need to architect protocols, incentives, and systems to encourage good behaviors and reduce bad ones. Many companies are beginning to adopt practices such as automated testing to keep mistakes from happening in the first place ; creating spaces where mistakes won’t affect other applications or systems, such as isolation zones in cloud environments ; and building in resiliency protocols.
- Do you have a list of the most important skills your business needs?
- What is the minimum level of learning needed for advanced users of analytics and manipulators of data?
- How do you track what people are learning and whether that learning is effective and translating into better performance?
3. IT as a service
It is estimated that the global cloud microservices platform market will generate $4.2 billion in revenue by 2028, up from $952 million in 2020. 15 Cloud microservice platform market report , Research Dive, November 2021. GitHub has more than 200 million code repositories and expects 100 million software developers by 2025. 16 Paul Krill, “GitHub expects more than 100 million software developers by 2025,” InfoWorld, December 3, 2020. Nearly 90 percent of developers already use APIs. 17 Christina Voskoglou, “APIs have taken over software development,” Nordic APIs, October 27, 2020. Software 2.0 creates new ways of writing software and reduces complexity. Software sourced by companies from cloud-service platforms, open repositories, and software as a service (SaaS) is growing at a CAGR of 27.5 percent from 2021 to 2028. 18 Software as a service (SaaS) market, 2021–2028 , Fortune Business Insights, January 2022.
Shift: IT becomes the enabler of product innovation by serving small, interoperable blocks of code.
When innovation is pushed to the edge and a perpetual-learning culture permeates an organization, the role of IT shifts dramatically. IT can’t support this dynamic environment by sticking to its traditional role as a controlling entity managing technology at the center. The premium will now be on IT’s ability to enable innovation, requiring a shift in its traditional role as protector of big tech assets to a purveyor of small blocks of code. The gold standard of IT effectiveness will be its ability to help people stitch together snippets of code into a useful product.
We are already seeing what that might look like. Employees at G&J Pepsi-Cola Bottlers with little to no experience at software development created an app that examines images of a store shelf to identify the number and type of bottles on it, then automatically restocks it based on historic trends. 19 Adam Burden, “Low code/no code could reshape business innovation,” VentureBeat, February 5, 2022. One pharmaceutical company grew its low-code platform base from eight users to 1,400 in just one year . Business users outside of IT are now building applications with thousands of monthly sessions. 20 Shivam Srivastava, Kartik Trehan, Dilip Wagle, and Jane Wang, “ Developer Velocity: How software excellence fuels business performance ,” McKinsey, April 20, 2020. Companies that empower “citizen developers” score 33 percent higher on innovation compared with bottom-quartile companies that don’t provide that level of support, according to a McKinsey survey. 21 Shivam Srivastava, Kartik Trehan, Dilip Wagle, and Jane Wang, “ Developer Velocity: How software excellence fuels business performance ,” McKinsey, April 20, 2020.
These developments point toward much more of a “buffet” approach to technology, where IT builds useful blocks of reusable code, sometimes assembles them into specific products, and makes them available through a user-friendly cataloging system for the business to use to create the products it needs. IT provides guiderails, such as API standards and directives on the environments in which the code might be most useful; protects the most sensitive information, such as customer data and financial records; and tracks their adoption. This tracking capability will become particularly crucial as bots, AI, algorithms, and APIs proliferate. Transparency isn’t sufficient. IT will need to make sense of all the activity through advanced tech performance and management capabilities and the development of new roles, such as data diagnosticians and bot managers.
This IT-as-a-service approach puts the product at the center of the operating model, requiring a commitment to organizing IT around product management . Some companies have been moving in this direction. But reaching the scale needed to support fast-paced and more diffuse innovation will require a deeper commitment to product owners, working with leaders in the business side of the house, to run teams with real P&L responsibility. Many organizations, from traditional enterprises to digital natives, have found that putting in place product leaders who set overall product and portfolio strategy, drive execution, and empower product owners to drive innovation aligned with business outcomes and P&L metrics can increase the return on the funding that flows to technology delivery and quicken the pace of innovation.
- Do you have a vision for how the role of the IT organization will change to enable democratization of technology?
- How will you elevate the role of the technology product manager, and do you have a road map for developing that role?
- What systems will you need to put in place to manage and track the use, reuse, and performance of code?

McKinsey Technology Trends Outlook 2022
4. expanded trust boundaries.
It was estimated that almost 100 percent of biometrics-capable devices (such as smartphones) will be using biometrics for transactions by 2022. 22 “Usage of biometric technology in transactions with mobile devices worldwide 2016–2022”, Statista Research Department, June 13, 2022. The effectiveness of these technologies has advanced dramatically, with the best facial-identification algorithms having improved 50 times since 2014. 23 William Crumpler, “How accurate are facial recognition systems—and why does it matter?” Center for Strategies and International Studies (CSIS), April 14, 2020. These developments are contributing to profound unease in the relationship between technology and consumers of technology. The Pearson Institute and the Associated Press-NORC Center for Public Affairs Research shows that “about two-thirds of Americans are very or extremely concerned about hacking that involves their personal information, financial institutions, government agencies, or certain utilities.” 24 Chuck Brooks, “More alarming cybersecurity stats for 2021!” Forbes , October 24, 2021.
Shift: Trust expands to cover a broader array of stakeholder concerns and become an enterprise-wide responsibility.
These enormous shifts in technology power and capacity will create many more touchpoints with customers and an exponential wave of new data about customers. Even as IT’s role within the organization becomes more that of an enabler, the expanding digital landscape means that IT must broaden its trust capabilities around security, privacy, and cyber . To date, consumers have largely embraced the convenience that technology provides, from ordering a product online to adjusting the temperature in their homes remotely to monitoring their health through personal devices. In exchange for these conveniences, consumers have traditionally been willing to provide some personal information. But a steady undercurrent of privacy and trust concerns around these ever-more-sophisticated conveniences is raising the stakes on the broad topic of trust. Consumers are becoming more aware of their identity rights, making decisions based on values, and demanding the ethical use of data and responsible AI .
The most obvious concern is around cybersecurity , an ongoing issue that is already on the board-level agenda. But tech-driven trust issues are much broader and are driven by three characteristics. One is the sheer quantity of personal data, such as biometrics, that companies and governments collect, creating concerns about privacy and data misuse. The second is that personal security issues are becoming more pervasive in the physical world. Wired homes, connected cars, and the Internet of Medical Things, for example, are all vectors for attack that can affect people’s well-being. Third is the issue that advanced analytics seem too complex to be understood and controlled, leading to deep unease about people’s relationship with technology. This issue is driving the development of “ explainable AI ” and the movement to debias AI.
Adding to the complexity is the frequent need to manage and secure trust across an entire ecosystem of technologies. Take the wired home, for example. The proliferation of devices—think virtual assistants, security, communications, power management, and entertainment systems—means that a large group of providers will need to agree on standards for managing, in effect, an interconnected security net in the home.
These developments require a complex extension of the boundaries of trust. The significant advantages that many incumbents enjoy—existing relationships with customers and proprietary data—are at risk unless businesses rethink how they manage and nurture that trust. Companies need to consider putting identity and trust management at the core of their customer experience and business processes. That can happen effectively only when companies assign a dedicated leader with real power and board-level prioritization with enterprise-wide responsibility across the entire trust and security landscape. Given the tech underpinnings of this trust environment, IT will need to play a key role in monitoring and remediating, such as assessing the impact of new legislation on AI algorithms, tracking incidents, identifying the number and nature of high-risk data-processing activities and automated decisions, and—perhaps most important—monitoring consumer trust levels and the issues that affect them.
- Who is responsible for the enterprise-wide trust and risk landscape?
- How have you integrated your efforts around customer trust with overall cybersecurity processes?
- What privacy, trust, and security processes are in place to manage the entire life cycle of your data?
It is inevitable that the pace of technological change will continue to accelerate. The successful technology leader of the future will not simply need to adopt new technologies but to build capabilities to absorb continuous change and make it a source of competitive advantage.
Steve Van Kuiken is a senior partner in McKinsey’s New Jersey office.
Explore a career with us
Related articles.
Digital twins: From one twin to the enterprise metaverse

Why digital trust truly matters

IoT value set to accelerate through 2030: Where and how to capture it
Impossible? Let’s see.
Whether we're shaping the future of sustainability, or optimizing algorithms, or even exploring epidemiological studies, Google Research strives to continuously progress science, advance society, and improve the lives of billions of people.

Advancing the state of the art
Our teams advance the state of the art through research, systems engineering, and collaboration across Google. We publish hundreds of research papers each year across a wide range of domains, sharing our latest developments in order to collaboratively progress computing and science.
Learn more about our philosophy.
Watch the film
Link to Youtube Video
Read the latest

MAR 20 · BLOG

MAR 18 · BLOG

MAR 15 · BLOG

MAR 12 · BLOG

MAR 07 · BLOG
Our research drives real-world change

Improving our LLM designed for the medical domain
- Large language models encode clinical knowledge Publication
- Towards Expert-Level Medical Question Answering with Large Language Models Publication
- Our latest health AI research updates Article
- Med-PaLM 2, our expert-level medical LLM Video
Project Contrails

A cost-effective and scalable way AI is helping to mitigate aviation’s climate impact
- A human-labeled Landsat-8 contrails dataset Dataset
- Can Google AI make flying more sustainable? Video
- Estimates of broadband upwelling irradiance fromm GOES-16 ABI Publication
- How AI is helping airlines mitigate the climate impact of contrails Blog
See our impact across other projects

Open Buildings

Project Relate

Flood Forecasting
We work across domains
Our vast breadth of work covers AI/ML foundations, responsible human-centric technology, science & societal impact, computing paradigms, and algorithms & optimization. Our research teams impact technology used by people all over the world.
One research paper started it all
The research we do today becomes the Google of the future. Google itself began with a research paper, published in 1998, and was the foundation of Google Search. Our ongoing research over the past 25 years has transformed not only the company, but how people are able to interact with the world and its information.

Responsible research is at the heart of what we do
The impact we create from our research has the potential to reach billions of people. That's why everything we do is guided by methodology that is grounded in responsible practices and thorough consideration.

Help us shape the future

We've been working alongside the academic research community since day one. Explore the ways that we collaborate and provide resources and support through a variety of student and faculty programs.

From Accra to Zürich, to our home base in Mountain View, we’re looking for talented scientists, engineers, interns, and more to join our teams not only at Google Research but all research projects across Google.
Explore our other teams and product areas
Google Cloud
Google DeepMind

An official website of the United States government
Here’s how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock A locked padlock ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
https://www.nist.gov/information-technology

Information Technology
Advancing the state-of-the-art in IT in such applications as cyber security and biometrics, NIST accelerates the development and deployment of systems that are reliable, usable, interoperable, and secure; advances measurement science through innovations in mathematics, statistics, and computer science; and conducts research to develop the measurements and standards infrastructure for emerging information technologies and applications.
Featured Content
Information technology topics.
- Artificial intelligence
- Cloud computing & virtualization
- Complex systems
- Computational science
- Conformance testing
- Cyberphysical systems
- Cybersecurity
- Data & informatics
- Federal information processing standards (FIPS)
- Internet of Things (IoT)
- Interoperability testing
- Location based services
- Software research
- Usability & human factors
- Video analytics
- Virtual / augmented reality
- Visualization research
- Voting systems
The Research
Projects & programs, face recognition vendor test (frvt), health it at nist - program overview.

NIST Cloud Computing Program - NCCP

Visualization
Additional resources links.

NIST Seeks Comments on AI Risk Management Framework Guidance, Workshop Date Set

NIST Awards $3.6 Million for Community-Based Cybersecurity Workforce Development

Kevin Stine Named Director of NIST’s Information Technology Laboratory

NIST to Launch Competition for AI-Focused Manufacturing USA Institute
Stay in touch.
Sign up for our newsletter to stay up to date with the latest research, trends, and news for Information Technology.
Upcoming Events
CHIPS R&D National Advanced Packaging Manufacturing Program (NAPMP) Advanced Packaging Summit

Cybersecurity Resources for Small to Medium-Sized Manufacturers: A Fireside Chat with the NIST Manufacturing Extension Partnership (MEP)
2024 ieee conference on computational imaging using synthetic apertures (cisa), 2024 iris experts group (ieg) meeting.

Top 400 Information Technology Research Topics – Full Guide!
The field of IT is progressive and ever-changing due to the rapid development of hardware, software, and networking technologies. The demand for innovative research in IT has also continued to rise as businesses and organizations embrace digital systems and data-driven solutions.
Understanding the salient areas of study in IT will help professionals keep up with changes that arise and enable organizations to leverage emerging technologies effectively.
Cybersecurity, artificial intelligence, cloud computing , and big data analytics have emerged through IT research. These fundamental factors shape the modern technology landscape, giving rise to immense possibilities for boosting productivity, raising efficiency, and improving competitiveness across sectors.
However, companies wanting to navigate the complexities of today’s digital age and exploit new technological advances must examine some of the latest IT research topics.
Understanding Information Technology Research
Table of Contents
In the world of technology, research is a compass that helps us navigate its convoluted evolutions. For instance, Information Technology (IT) research has been conducted in computer science, software engineering, data analytics, and cybersecurity.
IT research involves systematic inquiry to advance knowledge, problem-solving, and innovation. This includes conducting rigorous experiments and analyzing results to unveil new theories or approaches that improve technologies or bring breakthroughs.
Therefore, interdisciplinarity is at the core of IT research, with collaboration cutting across various disciplines. Whether using AI to reinforce cyber security or big data analytics in healthcare, collaboration leads to solutions to complex problems.
This is because IT research is changing rapidly due to technological advances. Thus, researchers need to be up-to-date to make meaningful contributions.
Ethics are involved so that technology can be responsibly deployed. The researchers grapple with privacy, security, bias, and equity issues to ensure technology benefits society.
As a result of this publication and conferences, which enable dissemination of findings, leading to further innovations, collaboration has supported progress, hence speeding it up.
Understanding IT research is vital for leveraging technology to address societal challenges and foster positive change.
Recommended Readings: “ Top 109+ Media Bias Research Topics | Full Guide! “.
Picking the Right Topic to Research: The Key to Finding New Things
In the always-changing world of information technology, choosing the proper topic to research is like starting a smart path. It’s a big decision that sets where your hard work will go and how much your findings could mean.
Fitting with Industry Moves and Issues
Finding a research topic that fits current industry moves and big issues is important. By staying informed on the latest happenings and problems in the technology field, you can ensure your research stays useful and helps solve real-world troubles.
Growing Fresh Ideas and Practical Uses
Choosing a research topic that generates fresh ideas and practical applications is crucial. Your findings should not just add to school talks but also lead to real solutions that can be used in real situations, pushing technology forward and making work smoother.
Sparking Mind Curiosity and Excitement
Selecting a research topic that sparks your curiosity and excitement is essential. When you dive into an area that truly fascinates you, the research journey becomes more engaging, and your drive to uncover big insights is stronger.
Finding Gaps and Unexplored Areas
Finding gaps in existing knowledge or unexplored areas in the technology landscape can lead to big discoveries. Entering uncharted spaces can uncover fresh insights and meaningfully advance the field.
Considering Potential Wide Effect and Growth
Considering your research topic’s potential wide effect and growth is crucial. Will your findings have far-reaching effects across industries? Can your solutions grow and shift to address changing challenges? Evaluating these things can help you prioritize research areas with the greatest potential for big impact.
By carefully choosing the right research topic, you can open the door to discoveries, push technology forward, and contribute to the constant evolution of the technology information landscape.
Top 400 Information Technology Research Topics
The list of the top 400 information technology research topics is organized into different categories. Let’s examine it.
Artificial Intelligence (AI) and Machine Learning (ML)
- Easy AI: Explaining and Using
- Group Learning: Getting Better Together
- AI in Health: Diagnosing and Helping
- Robots Learning on Their Own
- Being Fair with Computers
- Talking to Computers in Normal Language
- AI Fighting Bad Guys on the Internet
- AI Driving Cars: How Safe Is It?
- Sharing What We’ve Learned with Other Machines
- AI in Schools: Computers Learning About You
Cybersecurity and Encryption
- Trusting Computers: How to Stay Safe
- Keeping Secrets Safe with Fancy Math
- Secret Codes Computers Use: Safe or Not?
- Spy Games: Watching Out for Bad Stuff
- Keeping Secrets, Even from Friends
- Your Body as Your Password: Is It Safe?
- Fighting Against Computer Ransomers
- Keeping Your Secrets Secret, Even When Sharing
- Making Sure Your Smart Stuff Isn’t Spying on You
- Insuring Against Computer Bad Luck
Data Science and Big Data
- Sharing Secrets: How to Be Safe
- Watching the World in Real-Time
- Big Data: Big Computers Handling Big Jobs
- Making Data Pretty to Look At
- Cleaning Up Messy Data
- Predicting the Future with Numbers
- Finding Patterns in Connected Dots
- Keeping Your Secrets Safe in Big Data
- Sharing Our Secrets Without Telling Anyone
- Helping the Planet with Numbers
Cloud Computing
- Computers Without a Home: Where Do They Live?
- Keeping Computers Close to Home
- Moving Our Stuff to New Homes
- Juggling Many Clouds at Once
- Making Computers That Live in the Cloud
- Keeping Clouds Safe from Bad Guys
- Keeping Clouds Safe from Sneaky Spies
- Making Sure Clouds Do What They’re Supposed To
- Computers Need Energy Too!
- Making the Internet of Things Even Smarter
Internet of Things (IoT)
- Smart Stuff Everywhere: How Does It Work?
- Watching Out for Bad Stuff in Smart Things
- Smart Stuff: Is It Safe?
- Taking Care of Smart Toys
- Making Smart Things That Don’t Need Batteries
- Making Smart Factories Even Smarter
- Smart Cities: Making Cities Better Places to Live
- Your Clothes Can Be Smart, Too!
- Helping Farmers with Smart Farming
- Keeping Secrets Safe in Smart Stuff
Human-Computer Interaction (HCI)
- Magic Glasses: How Do They Work?
- Making Computers Easy to Use
- Making Computers for Everyone
- Talking to Computers with Your Hands
- Making Sure Computers Are Nice to People
- Talking to Computers with Your Voice
- Playing with Computers, You Can Touch
- Trusting Computers to Drive for Us
- Computers That Understand Different People
- Making Computers That Read Our Minds
Software Engineering
- Making Computers Work Together Smoothly
- Building Computers from Tiny Pieces
- Playing Games to Make Computers Better
- Making Sure Computers Work Right
- Making Old Computers New Again
- Making Computers Like to Exercise
- Making Computers Easier to Understand
- Building Computers with Blueprints
- Making Sure Computers Don’t Get Sick
- Sharing Computer Secrets with Everyone
Mobile Computing
- Keeping Phones Safe from Bad Guys
- Making Apps for Every Kind of Phone
- Keeping Phones Safe in the Cloud
- Finding Your Way with Your Phone
- Paying with Your Phone: Safe or Not?
- Checking Your Health with Your Phone
- Seeing the World Through Your Phone
- Wearing Your Phone on Your Wrist
- Learning on the Go with Your Phone
- Making Phones Even Smarter with Clouds
Networking and Communications
- Making Sure Computers Can Talk to Each Other
- Making Computers Work Together Without Wires
- Making the Internet Faster for Everyone
- Getting More Internet Addresses for More Computers
- Cutting the Internet into Pieces
- Making the Internet Even More Invisible
- Talking to Computers with Light
- Making Sure Tiny Computers Talk to Each Other
- Sending Messages Even When It’s Hard
- Making the Radio Smarter for Computers
Bioinformatics and Computational Biology
- Reading Your DNA with Computers
- Making Medicine Just for You
- Meeting the Microscopic World with Computers
- Building Computer Models of Living Things
- Finding New Medicine with Computers
- Building Computer Models of Tiny Machines
- Making Family Trees for Living Things
- Counting Germs with Computers
- Making Big Lists of Living Things
- Making Computers Think Like Brains
Quantum Computing
- Making Computers Better at Some Math Problems
- Keeping Computers Safe from Small Mistakes
- Making Computers Even Harder to Spy On
- Making Computers Learn Faster with Quantum Tricks
- Making Fake Worlds for Computers to Explore
- Building Computers from Super-Cold Stuff
- Making Computers Cold to Think Better
- Making Computers Think Like Chemists
- Making the Internet Even Safer with Computers
- Showing Off What Computers Can Do Best
Green Computing
- Saving Energy with Computers
- Using Wind and Sun to Power Computers
- Making Phones Last Longer Without Plugging In
- Making Computers Kinder to the Planet
- Recycling Old Computers to Save the Earth
- Computers That Care About Their Trash
- Saving Energy in Big Rooms Full of Computers
- Making Computers Save Energy and Work Faster
- Counting the Trash from Computers
- Making Computers Kinder to the Planet’s Air
Information Systems
- Making Computers Work Together in Big Companies
- Making Computers Remember Their Friends
- Making Computers Share What They Know
- Making Computers Smart About Money
- Making Computers Send Presents to Their Friends
- Helping Computers Make Big Decisions
- Making Government Computers Talk to Each Other
- Making Computers Count Likes and Shares
- Assisting computers to Find What You Asked For
- Assisting companies to Keep Their Friends Happy
Semantic Web and Linked Data
- Making Computers Understand Each Other Better
- Making Computers Talk About Themselves
- Making the Internet More Friendly for Computers
- Helping Computers Find What They Need
- Making Computers Smarter by Talking to Each Other
- Making Computers Friends with Different Languages
- Making Computers Understand Different Ideas
- Making Computers Think Like Us
- Making Computers Smarter About Old Stuff
- Making Computers Share Their Secrets Safely
Social Computing and Online Communities
- Making Friends on the Internet
- Getting Good Suggestions from the Internet
- Making Computers Work Together to Solve Problems
- Learning from Your Friends on the Internet
- Stopping Fake News on the Internet
- Knowing How People Feel on the Internet
- Helping Each Other on the Internet During Emergencies
- Making Sure Computers Are Nice to Everyone
- Keeping Secrets on the Internet
- Making the Internet a Better Place for Everyone
Game Development and Virtual Worlds
- Making Games That Play Fair
- Letting Computers Make Their Fun
- Making Fake Worlds for Fun
- Learning with Games
- Making the Rules for Fun
- Watching How People Play Together
- Seeing Things That Aren’t There
- Letting Lots of People Play Together
- Making the Engines for Fun
- Playing Games to Learn
E-Learning and Educational Technology
- Making Learning Easy for Everyone
- Taking Classes on the Internet
- Learning from Your Computer’s Teacher
- Learning from What Computers Know
- Learning Anywhere with Your Computer
- Making Learning Fun with Games
- Learning Without a Real Lab
- Learning with Free Stuff on the Internet
- Mixing School with Your Computer
- Making School More Fun with Your Computer
Digital Forensics and Incident Response
- Solving Computer Mysteries
- Looking for Clues in Computers
- Finding Bad Guys on the Internet
- Looking for Clues on Phones and Tablets
- Hiding Clues on Computers
- Helping When Computers Get Sick
- Solving Mysteries While the Computer Is On
- Finding Clues on Your Smart Watch
- Finding Tools for Finding Clues
- Following the Rules When Solving Mysteries
Wearable Technology and Smart Devices
- Keeping Healthy with Smart Watches
- Making Clothes That Talk to Computers
- Listening to the Earth with Your Shirt
- Wearing Glasses That Show Cool Stuff
- Making Your Home Smarter with Your Phone
- Using Your Body to Unlock Your Phone
- Helping People Move with Special Shoes
- Assisting people to See with Special Glasses
- Making Your Clothes Do More Than Keep You Warm
- Keeping Secrets Safe on Your Smart Stuff
Robotics and Automation
- Making Friends with Robots
- Letting Robots Do the Hard Work
- Robots That Work Together Like Ants
- Learning Tricks from People
- Robots That Feel Like Jelly
- Helping Doctors and Nurses with Robots
- Robots That Help Farmers Grow Food
- Making Cars Without People
- Teaching Robots to Recognize Things
- Robots That Learn from Animals
Health Informatics
- Computers That Help Doctors Keep Track of Patients
- Sharing Secrets About Your Health with Other Computers
- Seeing the Doctor on Your Computer
- Keeping Track of Your Health with Your Phone
- Making Medicine Better with Computers
- Keeping Your Health Secrets Safe with Computers
- Learning About Health with Computers
- Keeping Health Secrets Safe on the Internet
- Watching Out for Germs with Computers
- Making Sure the Doctor’s Computer Plays Nice
Geographic Information Systems (GIS)
- Watching the World Change with Computers
- Making Maps on the Internet
- Seeing the World from Very Far Away
- Finding Hidden Patterns with Computers
- Making Cities Better with Computers
- Keeping Track of the Earth with Computers
- Keeping Track of Wild Animals with Computers
- Making Maps with Everyone’s Help
- Seeing the World in 3D
- Finding Things on the Map with Your Phone
Knowledge Management
- Helping Computers Remember Things
- Making Computers Talk About What They Know
- Finding Secrets in Big Piles of Data
- Helping Companies Remember What They Know
- Sharing Secrets with Computers at Work
- Making Computers Learn from Each Other
- Making Computers Talk About Their Friends
- Making Companies Remember Their Secrets
- Keeping Track of What Companies Know
Computational Linguistics and Natural Language Processing (NLP)
- Finding Out How People Feel on the Internet
- Finding Names and Places in Stories
- Making Computers Talk to Each Other
- Making Computers Answer Questions
- Making Summaries for Busy People
- Making Computers Understand Stories
- Making Computers Understand Pictures and Sounds
- Making Computers Learn New Words
- Making Computers Remember What They Read
- Making Sure Computers Aren’t Mean to Anyone
Information Retrieval and Search Engines
- Finding Stuff on the Internet
- Getting Suggestions from the Internet
- Finding Stuff at Work
- Helping Computers Find Stuff Faster
- Making Computers Understand What You Want
- Finding Stuff on Your Phone
- Finding Stuff When You’re Moving
- Finding Stuff Near Where You Are
- Making Sure Computers Look Everywhere for What You Want
Computer Vision
- Finding Stuff in Pictures
- Cutting Up Pictures
- Watching Videos for Fun
- Learning from Lots of Pictures
- Making Pictures with Computers
- Finding Stuff That Looks Like Other Stuff
- Finding Secrets in Medical Pictures
- Finding Out If Pictures Are Real
- Looking at People’s Faces to Know Them
Quantum Information Science
- Making Computers Learn Faster with Tricks
Social Robotics
- Robots That Help People Who Have Trouble Talking
- Robots That Teach People New Things
- Making Robots Work with People
- Helping Kids Learn with Robots
- Making Sure Robots Aren’t Mean to Anyone
- Making Robots Understand How People Feel
- Making Friends with Robots from Different Places
- Making Sure Robots Respect Different Cultures
- Helping Robots Learn How to Be Nice
Cloud Robotics
- Making Robots Work Together from Far Away
- Making Robots Share Their Toys
- Making Robots Do Hard Jobs in Different Places
- Making Robots Save Energy
- Making Robots Play Together Nicely
- Making Robots Practice Being Together
- Making Sure Robots Play Fair
- Making Robots Follow the Rules
Cyber-Physical Systems (CPS)
- Making Robots Work Together with Other Things
- Keeping Robots Safe from Small Mistakes
- Keeping Factories Safe from Bad Guys
- Making Sure Robots Respect Different People
- Making Sure Robots Work Well with People
- Keeping Robots Safe from Bad Guys
- Making Sure Robots Follow the Rules
Biomedical Imaging
- Taking Pictures of Inside You with Computers
- Seeing Inside You with Computers
- Cutting Up Pictures of Inside You
- Finding Problems Inside You with Computers
- Cutting Up Pictures and Putting Them Together
- Counting Inside You with Pictures
- Making Pictures to Help Doctors
- Making Lists from Pictures Inside You
- Making Sure Pictures of You Are Safe
Remote Sensing
- Watching Earth from Far Away with Computers
- Making Pictures of Earth Change
- Taking Pictures from Very High Up
- Watching Crops Grow with Computers
- Watching Cities Grow with Computers
- Watching Earth Change with Computers
- Watching Earth from Far Away During Emergencies
- Making Computers Work Together to See Earth
- Putting Pictures of Earth Together
- Making Sure Pictures of Earth Are Safe
Cloud Gaming
- Playing Games from Far Away
- Making Games Work Faster from Far Away
- Keeping Games Safe from Bad Guys
- Making Sure Everyone Can Play Together
- Making Games Faster from Far Away
- Watching People Play Games from Far Away
- Making Sure Games Look Good from Far Away
- Watching Games Get More Popular
Augmented Reality (AR)
- Making Glasses That Show Cool Stuff
- Making Cool Stuff for Glasses to Show
- Watching Glasses Follow You
- Watching Phones Show Cool Stuff
- Making Cool Stuff to Show with Phones
- Making Places Even Better with Phones
- Making Factories Even Better with Glasses
- Making Places Even Better with Glasses
- Making Sure Glasses Don’t Scare Anyone
Virtual Reality (VR)
- Making Glasses That Show Different Worlds
- Making Glasses That Follow Your Hands
- Making Therapy Fun with Glasses
- Making Learning Fun with Glasses
- Making Glasses That Make Jobs Safer
- Making Glasses That Show Your Friends
- Making Sure Glasses Are Friendly
- Making Glasses That Make Buildings Better
- Making Sure Glasses Aren’t Scary
Digital Twins
- Making Computers That Copy the Real World
- Making People Better with Computers
- Making Flying Safer with Computers
- Making Cars Safer with Computers
- Making Energy Better with Computers
- Making Buildings Better with Computers
- Making Cities Safer with Computers
- Making Sure Computers Copy the Real World Safely
- Making Computers Follow the Rules
Edge Computing
- Making Computers Work Faster Near You
- Keeping Computers Safe Near You
- Making Computers Work with Far-Away Computers
- Making Computers Work Fast with You
- Making Computers Work Together Near You
- Making Phones Work Faster Near You
- Making Computers Work Near You
- Making Computers Work in Busy Places
Explainable AI (XAI)
- Making Computers Explain What They Do
- Making Medicine Safer with Computers
- Making Money Safer with Computers
- Making Computers Safe to Drive Cars
- Making Computers Fair to Everyone
- Making Computers Explain What They Think
- Making Computers Easy to Understand
Blockchain and Distributed Ledger Technology (DLT)
- Making Secret Codes Computers Use
- Making Contracts Computers Can Understand
- Making Computers Share Secrets Safely
- Making Money Safe with Computers
- Making Computers Work Together Nicely
- Making Computers Keep Secrets Safe
- Making Computers Work Together Fairly
- Making Stuff Move Safely with Computers
Quantum Communication
- Making Computers Talk to Each Other Safely
- Making Computers Talk to Each Other from Far Away
- Making Computers Talk to Each Other in Secret
- Making Money Move Safely with Computers
This list covers a broad spectrum of topics within Information Technology, ranging from foundational concepts to cutting-edge research areas. Feel free to choose any topic that aligns with your interests and expertise for further exploration and study!
Emerging Trends in Information Technology Research
In the rapidly changing world of Computer Studies, keeping up with the latest trends is indispensable. Technology keeps changing, and so does research in computer studies. From awesome things like clever robots to how we can safeguard our online information, computer studies research is always discovering new ways to improve our lives. Therefore, let us delve into some of the most exciting new trends shaping computer studies’ future.
- Smart Computers:
Right now, smart computers are a hot item. They can learn from experience, recognize patterns, and even understand language like humans do. This helps in many areas, such as healthcare or finance. So researchers are working on making smart computers smarter yet so that they can make decisions alone and be fair to everyone.
- Fast Computing:
As more devices connect to the Internet, we need ways to process information quickly. Fast computing helps bring processing power closer to where the information comes from, making things quicker and more efficient. Thus, researchers have been figuring out how to improve fast computing, especially for analyzing real-time data.
- Keeping Things Safe:
With all the cool tech around, keeping our information safe from bad guys is important. We must develop methods to safeguard our data and networks from cyber attackers. In addition, they have also been considering how to ensure the privacy of our personal information so that only authorized individuals can access it.
- Fancy Computers:
The next big thing in computing is quantum computers. They can do calculations at a high speed that ordinary ones cannot. Researchers are working hard to achieve quantum computing because it could be useful in cracking codes and creating new drugs.
- New Ways of Doing Things Together:
Blockchain is an exciting technology that allows us to collaborate without a central authority. Its use in cryptocurrencies is quite popular but it has other applications too. Blockchain can be applied for purposes such as helping us discover where products come from, proving who we are on the internet, and making contracts that cannot be changed later on.
- Virtual Reality Adventures:
Entering a completely different world is what Virtual Reality (VR) and Augmented Reality (AR) do. The feeling of being in reality is what these two technologies create, which is not real. These researchers are working hard on making VRs and ARs better so that they can be used for learning, training, and amusement in more innovative ways.
In summary, computer studies research keeps changing with new trends such as smart computers, rapid computing, cybersecurity issues, high-end computers, collaboration platforms and immersive games or virtual reality escapades.
By exploring these trends and developing new ideas, researchers ensure that technology keeps improving and making our lives easier and more exciting.
How can I brainstorm research topics in information technology?
Start by identifying your areas of interest and exploring recent advancements in the field. Consider consulting with mentors or peers for suggestions and feedback.
What are some ethical considerations in AI research?
Ethical considerations in AI research include fairness, transparency, accountability, and privacy. Researchers should ensure their algorithms and models do not perpetuate bias or harm individuals.
How can I stay updated on emerging trends in IT research?
Follow reputable journals, conferences, and online forums dedicated to information technology. Engage with the academic community through discussions and networking events.

Similar Articles

How To Do Homework Fast – 11 Tips To Do Homework Fast
Homework is one of the most important parts that have to be done by students. It has been around for…

How to Write an Assignment Introduction – 6 Best Tips
In essence, the writing tasks in academic tenure students are an integral part of any curriculum. Whether in high school,…
Leave a Comment Cancel Reply
Your email address will not be published. Required fields are marked *
This site uses Akismet to reduce spam. Learn how your comment data is processed .
Your browser is ancient! Upgrade to a different browser or install Google Chrome Frame to experience this site.

- IT Discipline
- Executive Committee
- Testimonials
- IT Model Curriculum
- Accreditation
- IT Education
IT Research
- IT Programs (USA)
- SIGITE 2021—Proceedings
- SIGITE 2021 IT Chairs meeting
- SIGITE 2020
- SIGITE 2019
- SIGITE 2018
- SIGITE/RIIT 2017
- SIGITE/RIIT 2016
- SIGITE/RIIT 2015
- SIGITE/RIIT 2014
- SIGITE/RIIT 2013
- SIGITE/RIIT 2012
- SIGITE 2011
- Newsletters
- SIGITE@LinkedIn
- Membership Benefits
It’s a long-standing principle among academics that research should inform our teaching; over years of SIGITE conferences, we’ve demonstrated the bi-directionality of that relationship, as teaching has often generated the source data and motivation for our research in IT education.
In 2012, we inaugurated the Research in Information Technology (RIIT) conference as a new companion to the more “venerable” SIGITE conference. A strong motivation for launching RIIT was the need to recognize “research in IT” as more than a fragmented collection of pursuits in other computing disciplines. We have been watching a body of research develop that is uniquely characteristic of information technology. With a hands-on flavor and stronger connections with industry, it is clearly differentiating itself from research in more traditional computing disciplines, and is deserving of its own conference venue.
What is IT Research?
Information Technology is an anomaly within academia whereby it was created as an academic discipline out of a need for IT graduates. Most academic disciplines instead are created out of a new research stream. SIGITE is currently heavily involved in identifying IT research. It has been found that much/most of this research is being done “at the seams” of other computing disciplines. In order for IT as an academic discipline to grow, the identification and nurturing of this research must continue.
The discussions around IT research at the SIGITE conferences have found that while IT research is being done (several graduate programs in IT exist) by graduate students and faculty, much of it goes unpublished. One theory as to why this is happening is because most IT graduate students go into industry, where it is unnecessary that they publish their research, rather than staying in academia. It is the responsibility of IT faculty to encourage/require graduate students to submit their research for publication.

This past weekend I attended and presented at the SIGITE Conference located in Midland, Michigan. It was the second weekend in a row that I was going to be gone, and all of that in the middle of the quarter, so I wasn’t as enthusiastic going into it as I normally am about conferences. As it turns out it was the best conference experience I’ve had in a long time!
The sessions at the conference are scheduled so that each talk has a 45-minute slot, with 30 minutes for the presentation and 15 minutes for questions. In most of the sessions I attended, including my own, the questions were in fact intermixed with the presentation. And what a difference it makes to have more time and a more interactive environment. I got excellent feedback on my work and was able to provide a lot more background information than was on my slides because of the questions. The questions themselves were also terrific. I was impressed by the insight that the audience members had into the work. I also got good questions and offers for collaborations after the talk, but it was the interactive presentations that really had me hooked.
SIGITE is the Association for Computing Machinery’s Special Interest Group on Information Technology Education. Our members include information technology faculty (teachers and researchers), students, and industry professionals.
With over 400 members worldwide, SIGITE drives the creation and dissemination of the computing discipline of information technology. The organization has created a model undergraduate curriculum and helped create accreditation guidelines for IT programs, and is now defining and promoting IT research.
Thesis Helpers
Find the best tips and advice to improve your writing. Or, have a top expert write your paper.
130 Information Technology Research Topics And Quick Writing Prompts

The field of information technology is one of the most recent developments of the 21st century. Scholars argue that we are living in a technological age. Despite this buzz, however, many students still find it challenging to compose an information technology research topic.
Nonetheless, we are here to show you the way and lead you accordingly. Let us explore professional topics in information technology together then.
Quality Information Technology Topics For Research Paper
- The effects of Artificial Intelligence on complex and tedious tasks
- Discuss the development of computational & synthetic biology in research
- What are the limitations to the study of computer architecture in colleges?
- Discuss the evolution of animation, computer graphics, and game science
- Critically analyze how computing is contributing to the development
- What are the emerging fields of study in computer data science?
- How to manage data in the age of the 5G technology
- The impact of human-computer interaction on innovations
- How is machine learning exposing students to more recent opportunities in life?
- Evaluate molecular information systems and their role in biotechnology
- How information technology has contributed to natural language processing
- What are the latest developments in programming languages and software engineering
- Analyze emerging opportunities in the field of Robotics
College Research Paper Topics in Information Technology
- The rising security and privacy concerns with technological advancements
- What are the considerations when setting up systems and networking?
- Discuss the theory of computation and its contribution to information technology
- Why is ubiquitous computing attracting fewer students?
- The role of wireless and sensor systems in making the world a safe place
- Reasons, why cloud computing has helped save on space and efficiency
- Why are most computer students comprised of the male?
- Discuss the essence of amorphous computing in the 21st century
- How has biomedical mining impacted the health sector?
- Can cyborgs relate well with the man?
- How neural networking is making brain surgery a swift process
- The role of swarm intelligence in collaboration and brainstorming
- How are companies maximizing the use of Big Data?
List of Topics For Research Paper in Information Technology
- Discuss how the Internet of Things is transforming how people conduct their activities
- Challenges to software-defined networking
- How are marketers and promoters taking up software as a service?
- The role of augmented reality and virtual reality in healthcare systems
- How intelligent apps are making life easier for man
- The role of information technology in detecting fake news and malicious viral content
- Long term effects of a technologically oriented world
- Technological advancements that made it possible for the SpaceX shuttle to land on the International Space Station
- How technology is making learning more practical and student-centered
- What role has technology played in the spread of world pandemics?
- How are governments able to shut down the Internet for their countries during particular events?
- Does social media make the world a global village or a divided universe?
- Discuss the implications of technological globalization
Unique Information Technology Research Topics
- Discuss the areas of life which have been least exploited using technology
- What are the considerations for setting up an educational curriculum on computer technology?
- Compare and contrast between different computer processing powers
- Why is Random Access Memory so crucial to the functioning of a computer?
- Should computer as a subject be mandatory for all students in college?
- How information technology has helped keep the world together during the quarantine period
- Discuss why most hackers manage to break firewalls of banks
- Are automated teller machine cards a safe way of keeping your bank details?
- Why should every institution incorporate automated systems in its functions?
- Who is more intelligent than the other? Man or Computer systems?
- How is NASA implementing the use of Information technology to explore space?
- The impact of automated message replies on smartphones.
- Do mobile phones contain radiations that cause cancer?
IT Research Topics For High School Students
- How does natural language processing compare with machine learning?
- What is the role of virtual reality in the entertainment industry?
- Discuss the application of computer vision technology in autonomous cars
- How have CCTVs assisted in keeping the world safe?
- Effects of phishing and spying on relationships
- Why cyber espionage is on the rise in the face of the 5G technology
- Compare and contrast between content-based recommendation vs. collaborative filtering
- Evaluate the interconnection between the Internet of things and artificial intelligence
- Analyze the amount of data generated from the Internet of things in devices
- Ethical and legal implications of various technological practices
- How technology has contributed to the formation of Genetically Modified Organisms
- Describe in detail the vaccine development process
- Why nanotechnology may be the only hope left in treating HIV
Hot Topics in IT
- How companies can incorporate information technologies in their policy management systems
- The role of IT in enhancing service delivery in customer care centers
- How IT has made advertising more appealing and authentic to the consumer
- Discuss the innovation of the Next Generation education systems
- Why are there fewer Information Technology colleges and universities in developing countries?
- Discuss WIFI connectivity in developed countries
- What are the considerations when purchasing a Bandwidth Monitor?
- How to create an effective Clinic Management System for intensive care
- Factors that necessitate the development of an Enterprise Level System Information Management
- Is it possible to develop fully functional Intelligent Car Transportation Systems?
- Why the world should adopt E-Waste Management systems ASAP
- Discuss the impact of weather and climate on internet strength and connectivity
- The role of advanced information technologies preserving classified documents
Interesting Information Technology Topics
- Human resource information management systems in large organizations
- Evaluate the effectiveness of online enterprise resource planning
- A critical analysis of object tracking using radial function networks
- How has Bluetooth mobile phone technology developed over time?
- Ethical challenges arising from new media information technologies
- How the computer has developed over the last decade
- The role of social media in enhancing communication strategies
- Why new media technologies have made physical newspapers obsolete
- The impact of the Internet of news sourcing, production, distribution, and sharing
- Discuss the structures of various communication structures
- How social media is making ads easily accessible
- The impact of social networking sites on personal contact
- Discuss the latest content marketing ideas in the wake of information technology
Topics Related To Information Technology
- The impact of media exposure to adolescents and teenagers
- How mass media is slowly but surely taking over the place of personal socialization
- How to use the Internet and interactive media as advertising tools
- Discuss the trends in music marketing in a digital world
- The use of hype in new media technologies
- The impact of using YouTube and video blogs in communication messages
- Discuss the challenges that are arising as a result of new media technologies
- How to build trustful relationships in virtual communication channels
- Why it is impossible to maintain privacy in social media
- Reasons why cyberbullying continues to persist in various communication technologies
- The change in interpersonal communication with the invention of information technology
- Is the future of information technologies right?
- Discuss how sensationalism is persisting in the wake of new media technologies
Research Proposal Topics in Information Technology
- Is it possible to live in a world without social media?
- The impact of mass media on morality and decency in the 21st century
- Advantages and disadvantages of renewable energy sources
- How effective is hydrogen power over others?
- An overview of renewable energy technologies
- The impact of robots in improving food safety
- How are drones useful in keeping large acres of land secure?
- The impact of 3D printing on the practice of medicine
- The effectiveness of having robots in infectious disease units
- The impact of hydroponic farming
- How to improve disease control using technology
- Eliminating poisonous substances in food using technology
- The effectiveness of robotic surgeries
Hot Topics in Computer Science
- Distinguish between virtual reality and human perception
- How are the inventions in the field of computer science transforming the world
- Evaluate the effectiveness of high-dimensional data modeling
- Limitations to the field of computer science
- Are colleges and universities producing competent computer scientists?
- How ethical hacking has turned out to be worse
- The essence of having specialized banking systems
- What is the most effective security measure: A serial code or fingerprint?
- The development of programming languages
- The effect of computational thinking on science
- Is it possible to eliminate stalking?
- Ways of improving patent rights for technological innovations
- An overview of the different types of software security
Did you find an IT topic for your assignment? If not, our expert thesis writers are here for you. Order a research paper from us today and get to enjoy professional services.

Make PhD experience your own
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Research IT
provides research data and computing technologies, consulting, and community for the UC Berkeley campus. Our goal is to advance research through IT innovation.

Status and Service Updates
No office hours on wed, 3/27 - thurs, 3/28.
Research IT will not be holding our regular office hours during the week of Spring Break, 3/25 - 3/29. Please get in touch with us at [email protected] for any help in the meantime.
Savio HPC services are back online: Tues, 3/26
The Savio HPC services are back online. Taking this opportunity, we have another exciting news to share. The Savio Supercluster currently uses a CentOS 7 Linux operating system. CentOS 7 will reach the end of life on June 30, 2024. Thus, we have planned to migrate to a new operating system, Rocky 8, to keep the system functional and secure. More information on this forthcoming.
Scheduled Savio downtime: Mon, March 25
We have scheduled a Savio downtime to accommodate the power maintenance work. The downtime will start at 5:00 PM on Monday, March 25th. All the HPC hardware will be powered down; thus, HPC services will be unavailable during the downtime. We expect to bring back the cluster online before 5 PM on Wednesday, March 27th. A scheduler reservation will be in place to ensure no jobs run after 5:00 PM on Monday, March 25th. If you plan to submit jobs, please ask for proper wall time so they can be completed before the downtime. Otherwise, your jobs will wait in the queue until the cluster is back online.
View all status and service updates
News articles, savio tips and tricks: making the most of the slurm scheduler and of installing/using software in mamba/conda environments.
Thursday, April 18, 2024
Location: In Person at 117 Dwinelle Hall (Academic Innovation Studio) and Zoom
... Read more about Savio tips and tricks: making the most of the Slurm scheduler and of installing/using software in Mamba/Conda environments
Celebrating WiDS Berkeley 2023! This article is a reflection on the insightful discussions, groundbreaking research, and empowering connections made at last year's event.
Women in Data Science (WiDS) Berkeley Conference 2023 Recap
On March 7, 2023, the Women in Data Science (WiDS) Berkeley Conference was held in the Banatao Auditorium in Sutardja Dai Hall on campus. The Global Women in Data Science (WiDS) ... Read more about Celebrating WiDS Berkeley 2023! This article is a reflection on the insightful discussions, groundbreaking research, and empowering connections made at last year's event.
Hiring for Research Data and Computing Domain Consultants!
Get paid to develop your skills in research data and computing!
UC Berkeley’s Research IT unit is hiring graduate student Domain Consultants for flexible, 15% to 25% (6-10 hours/week) appointments. We ... Read more about Hiring for Research Data and Computing Domain Consultants!
- 1 of 115 News Articles (Current page)
- 2 of 115 News Articles
- 3 of 115 News Articles
- 4 of 115 News Articles
- 5 of 115 News Articles
- 6 of 115 News Articles
- 7 of 115 News Articles
- 8 of 115 News Articles
- 9 of 115 News Articles
- next › News Articles
- last » News Articles
Suggestions or feedback?
MIT News | Massachusetts Institute of Technology
- Machine learning
- Social justice
- Black holes
- Classes and programs
Departments
- Aeronautics and Astronautics
- Brain and Cognitive Sciences
- Architecture
- Political Science
- Mechanical Engineering
Centers, Labs, & Programs
- Abdul Latif Jameel Poverty Action Lab (J-PAL)
- Picower Institute for Learning and Memory
- Lincoln Laboratory
- School of Architecture + Planning
- School of Engineering
- School of Humanities, Arts, and Social Sciences
- Sloan School of Management
- School of Science
- MIT Schwarzman College of Computing
A crossroads for computing at MIT
Press contact :.

Previous image Next image
On Vassar Street, in the heart of MIT’s campus, the MIT Stephen A. Schwarzman College of Computing recently opened the doors to its new headquarters in Building 45. The building’s central location and welcoming design will help form a new cluster of connectivity at MIT and enable the space to have a multifaceted role.
“The college has a broad mandate for computing across MIT,” says Daniel Huttenlocher, dean of the MIT Schwarzman College of Computing and the Henry Ellis Warren Professor of Electrical Engineering and Computer Science. “The building is designed to be the computing crossroads of the campus. It’s a place to bring a mix of people together to connect, engage, and catalyze collaborations in computing, and a home to a related set of computing research groups from multiple departments and labs.”
“Computing is the defining technology of our time and it will continue to be, well into the future,” says MIT President Sally Kornbluth. “As the people of MIT make progress in high-impact fields from AI to climate, this fantastic new building will enable collaboration across computing, engineering, biological science, economics, and countless other fields, encouraging the cross-pollination of ideas that inspires us to generate fresh solutions. The college has opened its doors at just the right time.”
A physical embodiment
An approximately 178,000 square foot eight-floor structure, the building is designed to be a physical embodiment of the MIT Schwarzman College of Computing’s three-fold mission: strengthen core computer science and artificial intelligence; infuse the forefront of computing with disciplines across MIT; and advance social, ethical, and policy dimensions of computing.
Oriented for the campus community and the public to come in and engage with the college, the first two floors of the building encompass multiple convening areas, including a 60-seat classroom, a 250-seat lecture hall, and an assortment of spaces for studying and social interactions.
Academic activity has commenced in both the lecture hall and classroom this semester with 13 classes for undergraduate and graduate students. Subjects include 6.C35/6.C85 (Interactive Data Visualization and Society), a class taught by faculty from the departments of Electrical Engineering and Computer Science (EECS) and Urban Studies and Planning. The class was created as part of the Common Ground for Computing Education , a cross-cutting initiative of the college that brings multiple departments together to develop and teach new courses and launch new programs that blend computing with other disciplines.
“The new college building is catering not only to educational and research needs, but also fostering extensive community connections. It has been particularly exciting to see faculty teaching classes in the building and the lobby bustling with students on any given day, engrossed in their studies or just enjoying the space while taking a break,” says Asu Ozdaglar, deputy dean of the MIT Schwarzman College of Computing and head of EECS.
The building will also accommodate 50 computing research groups, which correspond to the number of new faculty the college is hiring — 25 in core computing positions and 25 in shared positions with departments at MIT. These groups bring together a mix of new and existing teams in related research areas spanning floors four through seven of the building.
In mid-January, the initial two dozen research groups moved into the building, including faculty from the departments of EECS; Aeronautics and Astronautics; Brain and Cognitive Sciences; Mechanical Engineering; and Economics who are affiliated with the Computer Science and Artificial Intelligence Laboratory and the Laboratory for Information and Decision Systems. The research groups form a coherent overall cluster in deep learning and generative AI, natural language processing, computer vision, robotics, reinforcement learning, game theoretic methods, and societal impact of AI.
More will follow suit, including some of the 10 faculty who have been hired into shared positions by the college with the departments of Brain and Cognitive Sciences; Chemical Engineering; Comparative Media Studies and Writing; Earth, Atmospheric and Planetary Sciences; Music and Theater Arts; Mechanical Engineering; Nuclear Science and Engineering; Political Science; and the MIT Sloan School of Management.
“I eagerly anticipate the building's expansion of opportunities, facilitating the development of even deeper connections the college has made so far spanning all five schools," says Anantha Chandrakasan, chief innovation and strategy officer, dean of the School of Engineering, and the Vannevar Bush Professor of Electrical Engineering and Computer Science.
Other college programs and activities that are being supported in the building include the MIT Quest for Intelligence, Center for Computational Science and Engineering, and MIT-IBM Watson AI Lab. There are also dedicated areas for the dean’s office, as well as for the cross-cutting areas of the college — the Social and Ethical Responsibilities of Computing , Common Ground, and Special Semester Topics in Computing, a new experimental program designed to bring MIT researchers and visitors together in a common space for a semester around areas of interest.
Additional spaces include conference rooms on the third floor that are available for use by any college unit. These rooms are accessible to both residents and nonresidents of the building to host weekly group meetings or other computing-related activities.
For the MIT community at large, the building’s main event space, along with three conference rooms, is available for meetings, events, and conferences. Located eight stories high on the top floor with striking views across Cambridge and Boston and of the Great Dome, the event space is already in demand with bookings through next fall, and has quickly become a popular destination on campus.
The college inaugurated the event space over the January Independent Activities Period, welcoming students, faculty, and visitors to the building for Expanding Horizons in Computing — a weeklong series of bootcamps, workshops, short talks, panels, and roundtable discussions. Organized by various MIT faculty, the 12 sessions in the series delved into exciting areas of computing and AI, with topics ranging from security, intelligence, and deep learning to design, sustainability, and policy.
Form and function
Designed by Skidmore, Owings & Merrill, the state-of-the-art space for education, research, and collaboration took shape over four years of design and construction.
“In the design of a new multifunctional building like this, I view my job as the dean being to make sure that the building fulfills the functional needs of the college mission,” says Huttenlocher. “I think what has been most rewarding for me, now that the building is finished, is to see its form supporting its wide range of intended functions.”
In keeping with MIT’s commitment to environmental sustainability, the building is designed to meet Leadership in Energy and Environmental Design (LEED) Gold certification. The final review with the U.S. Green Building Council is tracking toward a Platinum certification.
The glass shingles on the building’s south-facing side serve a dual purpose in that they allow abundant natural light in and form a double-skin façade constructed of interlocking units that create a deep sealed cavity, which is anticipated to notably lower energy consumption.
Other sustainability features include embodied carbon tracking, on-site stormwater management, fixtures that reduce indoor potable water usage, and a large green roof. The building is also the first to utilize heat from a newly completed utilities plant built on top of Building 42, which converted conventional steam-based distributed systems into more efficient hot-water systems. This conversion significantly enhances the building’s capacity to deliver more efficient medium-temperature hot water across the entire facility.
Grand unveiling
A dedication ceremony for the building is planned for the spring.
The momentous event will mark the official completion and opening of the new building and celebrate the culmination of hard work, commitment, and collaboration in bringing it to fruition.
It will also celebrate the 2018 foundational gift that established the college from Stephen A. Schwarzman, the chair, CEO, and co-founder of Blackstone, the global asset management and financial services firm. In addition, it will acknowledge Sebastian Man ’79, SM ’80, the first donor to support the building after Schwarzman. Man’s gift will be recognized with the naming of a key space in the building that will enrich the academic and research activities of the MIT Schwarzman College of Computing and the Institute.
Share this news article on:
Related links, related topics.
- Campus buildings and architecture
- School of Architecture and Planning
- School of Humanities Arts and Social Sciences
- MIT Sloan School of Management
- Aeronautical and astronautical engineering
- Brain and cognitive sciences
- Chemical engineering
- Comparative Media Studies/Writing
- Electrical Engineering & Computer Science (eecs)
- Music and theater arts
- Nuclear science and engineering
- Political science
- Urban studies and planning
- Computer Science and Artificial Intelligence Laboratory (CSAIL)
- Laboratory for Information and Decision Systems (LIDS)
- MIT-IBM Watson AI Lab
- Quest for Intelligence
- Administration
- Education, teaching, academics
- Cambridge, Boston and region
- Computer science and technology
- Artificial intelligence
- Technology and society
Related Articles

Design progresses for MIT Schwarzman College of Computing building on Vassar Street

Building site identified for MIT Stephen A. Schwarzman College of Computing

FAQ on the newly established MIT Stephen A. Schwarzman College of Computing
Previous item Next item
More MIT News

A biomedical engineer pivots from human movement to women’s health
Read full story →

MIT tops among single-campus universities in US patents granted

A new way to detect radiation involving cheap ceramics

Growing our donated organ supply

New AI method captures uncertainty in medical images

Improving drug development with a vast map of the immune system
- More news on MIT News homepage →
Massachusetts Institute of Technology 77 Massachusetts Avenue, Cambridge, MA, USA
- Map (opens in new window)
- Events (opens in new window)
- People (opens in new window)
- Careers (opens in new window)
- Accessibility
- Social Media Hub
- MIT on Facebook
- MIT on YouTube
- MIT on Instagram
What Is Research, and Why Do People Do It?
- Open Access
- First Online: 03 December 2022
Cite this chapter
You have full access to this open access chapter

- James Hiebert 6 ,
- Jinfa Cai 7 ,
- Stephen Hwang 7 ,
- Anne K Morris 6 &
- Charles Hohensee 6
Part of the book series: Research in Mathematics Education ((RME))
15k Accesses
Abstractspiepr Abs1
Every day people do research as they gather information to learn about something of interest. In the scientific world, however, research means something different than simply gathering information. Scientific research is characterized by its careful planning and observing, by its relentless efforts to understand and explain, and by its commitment to learn from everyone else seriously engaged in research. We call this kind of research scientific inquiry and define it as “formulating, testing, and revising hypotheses.” By “hypotheses” we do not mean the hypotheses you encounter in statistics courses. We mean predictions about what you expect to find and rationales for why you made these predictions. Throughout this and the remaining chapters we make clear that the process of scientific inquiry applies to all kinds of research studies and data, both qualitative and quantitative.
You have full access to this open access chapter, Download chapter PDF
Part I. What Is Research?
Have you ever studied something carefully because you wanted to know more about it? Maybe you wanted to know more about your grandmother’s life when she was younger so you asked her to tell you stories from her childhood, or maybe you wanted to know more about a fertilizer you were about to use in your garden so you read the ingredients on the package and looked them up online. According to the dictionary definition, you were doing research.
Recall your high school assignments asking you to “research” a topic. The assignment likely included consulting a variety of sources that discussed the topic, perhaps including some “original” sources. Often, the teacher referred to your product as a “research paper.”
Were you conducting research when you interviewed your grandmother or wrote high school papers reviewing a particular topic? Our view is that you were engaged in part of the research process, but only a small part. In this book, we reserve the word “research” for what it means in the scientific world, that is, for scientific research or, more pointedly, for scientific inquiry .
Exercise 1.1
Before you read any further, write a definition of what you think scientific inquiry is. Keep it short—Two to three sentences. You will periodically update this definition as you read this chapter and the remainder of the book.
This book is about scientific inquiry—what it is and how to do it. For starters, scientific inquiry is a process, a particular way of finding out about something that involves a number of phases. Each phase of the process constitutes one aspect of scientific inquiry. You are doing scientific inquiry as you engage in each phase, but you have not done scientific inquiry until you complete the full process. Each phase is necessary but not sufficient.
In this chapter, we set the stage by defining scientific inquiry—describing what it is and what it is not—and by discussing what it is good for and why people do it. The remaining chapters build directly on the ideas presented in this chapter.
A first thing to know is that scientific inquiry is not all or nothing. “Scientificness” is a continuum. Inquiries can be more scientific or less scientific. What makes an inquiry more scientific? You might be surprised there is no universally agreed upon answer to this question. None of the descriptors we know of are sufficient by themselves to define scientific inquiry. But all of them give you a way of thinking about some aspects of the process of scientific inquiry. Each one gives you different insights.

Exercise 1.2
As you read about each descriptor below, think about what would make an inquiry more or less scientific. If you think a descriptor is important, use it to revise your definition of scientific inquiry.
Creating an Image of Scientific Inquiry
We will present three descriptors of scientific inquiry. Each provides a different perspective and emphasizes a different aspect of scientific inquiry. We will draw on all three descriptors to compose our definition of scientific inquiry.
Descriptor 1. Experience Carefully Planned in Advance
Sir Ronald Fisher, often called the father of modern statistical design, once referred to research as “experience carefully planned in advance” (1935, p. 8). He said that humans are always learning from experience, from interacting with the world around them. Usually, this learning is haphazard rather than the result of a deliberate process carried out over an extended period of time. Research, Fisher said, was learning from experience, but experience carefully planned in advance.
This phrase can be fully appreciated by looking at each word. The fact that scientific inquiry is based on experience means that it is based on interacting with the world. These interactions could be thought of as the stuff of scientific inquiry. In addition, it is not just any experience that counts. The experience must be carefully planned . The interactions with the world must be conducted with an explicit, describable purpose, and steps must be taken to make the intended learning as likely as possible. This planning is an integral part of scientific inquiry; it is not just a preparation phase. It is one of the things that distinguishes scientific inquiry from many everyday learning experiences. Finally, these steps must be taken beforehand and the purpose of the inquiry must be articulated in advance of the experience. Clearly, scientific inquiry does not happen by accident, by just stumbling into something. Stumbling into something unexpected and interesting can happen while engaged in scientific inquiry, but learning does not depend on it and serendipity does not make the inquiry scientific.
Descriptor 2. Observing Something and Trying to Explain Why It Is the Way It Is
When we were writing this chapter and googled “scientific inquiry,” the first entry was: “Scientific inquiry refers to the diverse ways in which scientists study the natural world and propose explanations based on the evidence derived from their work.” The emphasis is on studying, or observing, and then explaining . This descriptor takes the image of scientific inquiry beyond carefully planned experience and includes explaining what was experienced.
According to the Merriam-Webster dictionary, “explain” means “(a) to make known, (b) to make plain or understandable, (c) to give the reason or cause of, and (d) to show the logical development or relations of” (Merriam-Webster, n.d. ). We will use all these definitions. Taken together, they suggest that to explain an observation means to understand it by finding reasons (or causes) for why it is as it is. In this sense of scientific inquiry, the following are synonyms: explaining why, understanding why, and reasoning about causes and effects. Our image of scientific inquiry now includes planning, observing, and explaining why.

We need to add a final note about this descriptor. We have phrased it in a way that suggests “observing something” means you are observing something in real time—observing the way things are or the way things are changing. This is often true. But, observing could mean observing data that already have been collected, maybe by someone else making the original observations (e.g., secondary analysis of NAEP data or analysis of existing video recordings of classroom instruction). We will address secondary analyses more fully in Chap. 4 . For now, what is important is that the process requires explaining why the data look like they do.
We must note that for us, the term “data” is not limited to numerical or quantitative data such as test scores. Data can also take many nonquantitative forms, including written survey responses, interview transcripts, journal entries, video recordings of students, teachers, and classrooms, text messages, and so forth.

Exercise 1.3
What are the implications of the statement that just “observing” is not enough to count as scientific inquiry? Does this mean that a detailed description of a phenomenon is not scientific inquiry?
Find sources that define research in education that differ with our position, that say description alone, without explanation, counts as scientific research. Identify the precise points where the opinions differ. What are the best arguments for each of the positions? Which do you prefer? Why?
Descriptor 3. Updating Everyone’s Thinking in Response to More and Better Information
This descriptor focuses on a third aspect of scientific inquiry: updating and advancing the field’s understanding of phenomena that are investigated. This descriptor foregrounds a powerful characteristic of scientific inquiry: the reliability (or trustworthiness) of what is learned and the ultimate inevitability of this learning to advance human understanding of phenomena. Humans might choose not to learn from scientific inquiry, but history suggests that scientific inquiry always has the potential to advance understanding and that, eventually, humans take advantage of these new understandings.
Before exploring these bold claims a bit further, note that this descriptor uses “information” in the same way the previous two descriptors used “experience” and “observations.” These are the stuff of scientific inquiry and we will use them often, sometimes interchangeably. Frequently, we will use the term “data” to stand for all these terms.
An overriding goal of scientific inquiry is for everyone to learn from what one scientist does. Much of this book is about the methods you need to use so others have faith in what you report and can learn the same things you learned. This aspect of scientific inquiry has many implications.
One implication is that scientific inquiry is not a private practice. It is a public practice available for others to see and learn from. Notice how different this is from everyday learning. When you happen to learn something from your everyday experience, often only you gain from the experience. The fact that research is a public practice means it is also a social one. It is best conducted by interacting with others along the way: soliciting feedback at each phase, taking opportunities to present work-in-progress, and benefitting from the advice of others.
A second implication is that you, as the researcher, must be committed to sharing what you are doing and what you are learning in an open and transparent way. This allows all phases of your work to be scrutinized and critiqued. This is what gives your work credibility. The reliability or trustworthiness of your findings depends on your colleagues recognizing that you have used all appropriate methods to maximize the chances that your claims are justified by the data.
A third implication of viewing scientific inquiry as a collective enterprise is the reverse of the second—you must be committed to receiving comments from others. You must treat your colleagues as fair and honest critics even though it might sometimes feel otherwise. You must appreciate their job, which is to remain skeptical while scrutinizing what you have done in considerable detail. To provide the best help to you, they must remain skeptical about your conclusions (when, for example, the data are difficult for them to interpret) until you offer a convincing logical argument based on the information you share. A rather harsh but good-to-remember statement of the role of your friendly critics was voiced by Karl Popper, a well-known twentieth century philosopher of science: “. . . if you are interested in the problem which I tried to solve by my tentative assertion, you may help me by criticizing it as severely as you can” (Popper, 1968, p. 27).
A final implication of this third descriptor is that, as someone engaged in scientific inquiry, you have no choice but to update your thinking when the data support a different conclusion. This applies to your own data as well as to those of others. When data clearly point to a specific claim, even one that is quite different than you expected, you must reconsider your position. If the outcome is replicated multiple times, you need to adjust your thinking accordingly. Scientific inquiry does not let you pick and choose which data to believe; it mandates that everyone update their thinking when the data warrant an update.
Doing Scientific Inquiry
We define scientific inquiry in an operational sense—what does it mean to do scientific inquiry? What kind of process would satisfy all three descriptors: carefully planning an experience in advance; observing and trying to explain what you see; and, contributing to updating everyone’s thinking about an important phenomenon?
We define scientific inquiry as formulating , testing , and revising hypotheses about phenomena of interest.
Of course, we are not the only ones who define it in this way. The definition for the scientific method posted by the editors of Britannica is: “a researcher develops a hypothesis, tests it through various means, and then modifies the hypothesis on the basis of the outcome of the tests and experiments” (Britannica, n.d. ).

Notice how defining scientific inquiry this way satisfies each of the descriptors. “Carefully planning an experience in advance” is exactly what happens when formulating a hypothesis about a phenomenon of interest and thinking about how to test it. “ Observing a phenomenon” occurs when testing a hypothesis, and “ explaining ” what is found is required when revising a hypothesis based on the data. Finally, “updating everyone’s thinking” comes from comparing publicly the original with the revised hypothesis.
Doing scientific inquiry, as we have defined it, underscores the value of accumulating knowledge rather than generating random bits of knowledge. Formulating, testing, and revising hypotheses is an ongoing process, with each revised hypothesis begging for another test, whether by the same researcher or by new researchers. The editors of Britannica signaled this cyclic process by adding the following phrase to their definition of the scientific method: “The modified hypothesis is then retested, further modified, and tested again.” Scientific inquiry creates a process that encourages each study to build on the studies that have gone before. Through collective engagement in this process of building study on top of study, the scientific community works together to update its thinking.
Before exploring more fully the meaning of “formulating, testing, and revising hypotheses,” we need to acknowledge that this is not the only way researchers define research. Some researchers prefer a less formal definition, one that includes more serendipity, less planning, less explanation. You might have come across more open definitions such as “research is finding out about something.” We prefer the tighter hypothesis formulation, testing, and revision definition because we believe it provides a single, coherent map for conducting research that addresses many of the thorny problems educational researchers encounter. We believe it is the most useful orientation toward research and the most helpful to learn as a beginning researcher.
A final clarification of our definition is that it applies equally to qualitative and quantitative research. This is a familiar distinction in education that has generated much discussion. You might think our definition favors quantitative methods over qualitative methods because the language of hypothesis formulation and testing is often associated with quantitative methods. In fact, we do not favor one method over another. In Chap. 4 , we will illustrate how our definition fits research using a range of quantitative and qualitative methods.
Exercise 1.4
Look for ways to extend what the field knows in an area that has already received attention by other researchers. Specifically, you can search for a program of research carried out by more experienced researchers that has some revised hypotheses that remain untested. Identify a revised hypothesis that you might like to test.
Unpacking the Terms Formulating, Testing, and Revising Hypotheses
To get a full sense of the definition of scientific inquiry we will use throughout this book, it is helpful to spend a little time with each of the key terms.
We first want to make clear that we use the term “hypothesis” as it is defined in most dictionaries and as it used in many scientific fields rather than as it is usually defined in educational statistics courses. By “hypothesis,” we do not mean a null hypothesis that is accepted or rejected by statistical analysis. Rather, we use “hypothesis” in the sense conveyed by the following definitions: “An idea or explanation for something that is based on known facts but has not yet been proved” (Cambridge University Press, n.d. ), and “An unproved theory, proposition, or supposition, tentatively accepted to explain certain facts and to provide a basis for further investigation or argument” (Agnes & Guralnik, 2008 ).
We distinguish two parts to “hypotheses.” Hypotheses consist of predictions and rationales . Predictions are statements about what you expect to find when you inquire about something. Rationales are explanations for why you made the predictions you did, why you believe your predictions are correct. So, for us “formulating hypotheses” means making explicit predictions and developing rationales for the predictions.
“Testing hypotheses” means making observations that allow you to assess in what ways your predictions were correct and in what ways they were incorrect. In education research, it is rarely useful to think of your predictions as either right or wrong. Because of the complexity of most issues you will investigate, most predictions will be right in some ways and wrong in others.
By studying the observations you make (data you collect) to test your hypotheses, you can revise your hypotheses to better align with the observations. This means revising your predictions plus revising your rationales to justify your adjusted predictions. Even though you might not run another test, formulating revised hypotheses is an essential part of conducting a research study. Comparing your original and revised hypotheses informs everyone of what you learned by conducting your study. In addition, a revised hypothesis sets the stage for you or someone else to extend your study and accumulate more knowledge of the phenomenon.
We should note that not everyone makes a clear distinction between predictions and rationales as two aspects of hypotheses. In fact, common, non-scientific uses of the word “hypothesis” may limit it to only a prediction or only an explanation (or rationale). We choose to explicitly include both prediction and rationale in our definition of hypothesis, not because we assert this should be the universal definition, but because we want to foreground the importance of both parts acting in concert. Using “hypothesis” to represent both prediction and rationale could hide the two aspects, but we make them explicit because they provide different kinds of information. It is usually easier to make predictions than develop rationales because predictions can be guesses, hunches, or gut feelings about which you have little confidence. Developing a compelling rationale requires careful thought plus reading what other researchers have found plus talking with your colleagues. Often, while you are developing your rationale you will find good reasons to change your predictions. Developing good rationales is the engine that drives scientific inquiry. Rationales are essentially descriptions of how much you know about the phenomenon you are studying. Throughout this guide, we will elaborate on how developing good rationales drives scientific inquiry. For now, we simply note that it can sharpen your predictions and help you to interpret your data as you test your hypotheses.

Hypotheses in education research take a variety of forms or types. This is because there are a variety of phenomena that can be investigated. Investigating educational phenomena is sometimes best done using qualitative methods, sometimes using quantitative methods, and most often using mixed methods (e.g., Hay, 2016 ; Weis et al. 2019a ; Weisner, 2005 ). This means that, given our definition, hypotheses are equally applicable to qualitative and quantitative investigations.
Hypotheses take different forms when they are used to investigate different kinds of phenomena. Two very different activities in education could be labeled conducting experiments and descriptions. In an experiment, a hypothesis makes a prediction about anticipated changes, say the changes that occur when a treatment or intervention is applied. You might investigate how students’ thinking changes during a particular kind of instruction.
A second type of hypothesis, relevant for descriptive research, makes a prediction about what you will find when you investigate and describe the nature of a situation. The goal is to understand a situation as it exists rather than to understand a change from one situation to another. In this case, your prediction is what you expect to observe. Your rationale is the set of reasons for making this prediction; it is your current explanation for why the situation will look like it does.
You will probably read, if you have not already, that some researchers say you do not need a prediction to conduct a descriptive study. We will discuss this point of view in Chap. 2 . For now, we simply claim that scientific inquiry, as we have defined it, applies to all kinds of research studies. Descriptive studies, like others, not only benefit from formulating, testing, and revising hypotheses, but also need hypothesis formulating, testing, and revising.
One reason we define research as formulating, testing, and revising hypotheses is that if you think of research in this way you are less likely to go wrong. It is a useful guide for the entire process, as we will describe in detail in the chapters ahead. For example, as you build the rationale for your predictions, you are constructing the theoretical framework for your study (Chap. 3 ). As you work out the methods you will use to test your hypothesis, every decision you make will be based on asking, “Will this help me formulate or test or revise my hypothesis?” (Chap. 4 ). As you interpret the results of testing your predictions, you will compare them to what you predicted and examine the differences, focusing on how you must revise your hypotheses (Chap. 5 ). By anchoring the process to formulating, testing, and revising hypotheses, you will make smart decisions that yield a coherent and well-designed study.
Exercise 1.5
Compare the concept of formulating, testing, and revising hypotheses with the descriptions of scientific inquiry contained in Scientific Research in Education (NRC, 2002 ). How are they similar or different?
Exercise 1.6
Provide an example to illustrate and emphasize the differences between everyday learning/thinking and scientific inquiry.
Learning from Doing Scientific Inquiry
We noted earlier that a measure of what you have learned by conducting a research study is found in the differences between your original hypothesis and your revised hypothesis based on the data you collected to test your hypothesis. We will elaborate this statement in later chapters, but we preview our argument here.
Even before collecting data, scientific inquiry requires cycles of making a prediction, developing a rationale, refining your predictions, reading and studying more to strengthen your rationale, refining your predictions again, and so forth. And, even if you have run through several such cycles, you still will likely find that when you test your prediction you will be partly right and partly wrong. The results will support some parts of your predictions but not others, or the results will “kind of” support your predictions. A critical part of scientific inquiry is making sense of your results by interpreting them against your predictions. Carefully describing what aspects of your data supported your predictions, what aspects did not, and what data fell outside of any predictions is not an easy task, but you cannot learn from your study without doing this analysis.

Analyzing the matches and mismatches between your predictions and your data allows you to formulate different rationales that would have accounted for more of the data. The best revised rationale is the one that accounts for the most data. Once you have revised your rationales, you can think about the predictions they best justify or explain. It is by comparing your original rationales to your new rationales that you can sort out what you learned from your study.
Suppose your study was an experiment. Maybe you were investigating the effects of a new instructional intervention on students’ learning. Your original rationale was your explanation for why the intervention would change the learning outcomes in a particular way. Your revised rationale explained why the changes that you observed occurred like they did and why your revised predictions are better. Maybe your original rationale focused on the potential of the activities if they were implemented in ideal ways and your revised rationale included the factors that are likely to affect how teachers implement them. By comparing the before and after rationales, you are describing what you learned—what you can explain now that you could not before. Another way of saying this is that you are describing how much more you understand now than before you conducted your study.
Revised predictions based on carefully planned and collected data usually exhibit some of the following features compared with the originals: more precision, more completeness, and broader scope. Revised rationales have more explanatory power and become more complete, more aligned with the new predictions, sharper, and overall more convincing.
Part II. Why Do Educators Do Research?
Doing scientific inquiry is a lot of work. Each phase of the process takes time, and you will often cycle back to improve earlier phases as you engage in later phases. Because of the significant effort required, you should make sure your study is worth it. So, from the beginning, you should think about the purpose of your study. Why do you want to do it? And, because research is a social practice, you should also think about whether the results of your study are likely to be important and significant to the education community.
If you are doing research in the way we have described—as scientific inquiry—then one purpose of your study is to understand , not just to describe or evaluate or report. As we noted earlier, when you formulate hypotheses, you are developing rationales that explain why things might be like they are. In our view, trying to understand and explain is what separates research from other kinds of activities, like evaluating or describing.
One reason understanding is so important is that it allows researchers to see how or why something works like it does. When you see how something works, you are better able to predict how it might work in other contexts, under other conditions. And, because conditions, or contextual factors, matter a lot in education, gaining insights into applying your findings to other contexts increases the contributions of your work and its importance to the broader education community.
Consequently, the purposes of research studies in education often include the more specific aim of identifying and understanding the conditions under which the phenomena being studied work like the observations suggest. A classic example of this kind of study in mathematics education was reported by William Brownell and Harold Moser in 1949 . They were trying to establish which method of subtracting whole numbers could be taught most effectively—the regrouping method or the equal additions method. However, they realized that effectiveness might depend on the conditions under which the methods were taught—“meaningfully” versus “mechanically.” So, they designed a study that crossed the two instructional approaches with the two different methods (regrouping and equal additions). Among other results, they found that these conditions did matter. The regrouping method was more effective under the meaningful condition than the mechanical condition, but the same was not true for the equal additions algorithm.
What do education researchers want to understand? In our view, the ultimate goal of education is to offer all students the best possible learning opportunities. So, we believe the ultimate purpose of scientific inquiry in education is to develop understanding that supports the improvement of learning opportunities for all students. We say “ultimate” because there are lots of issues that must be understood to improve learning opportunities for all students. Hypotheses about many aspects of education are connected, ultimately, to students’ learning. For example, formulating and testing a hypothesis that preservice teachers need to engage in particular kinds of activities in their coursework in order to teach particular topics well is, ultimately, connected to improving students’ learning opportunities. So is hypothesizing that school districts often devote relatively few resources to instructional leadership training or hypothesizing that positioning mathematics as a tool students can use to combat social injustice can help students see the relevance of mathematics to their lives.
We do not exclude the importance of research on educational issues more removed from improving students’ learning opportunities, but we do think the argument for their importance will be more difficult to make. If there is no way to imagine a connection between your hypothesis and improving learning opportunities for students, even a distant connection, we recommend you reconsider whether it is an important hypothesis within the education community.
Notice that we said the ultimate goal of education is to offer all students the best possible learning opportunities. For too long, educators have been satisfied with a goal of offering rich learning opportunities for lots of students, sometimes even for just the majority of students, but not necessarily for all students. Evaluations of success often are based on outcomes that show high averages. In other words, if many students have learned something, or even a smaller number have learned a lot, educators may have been satisfied. The problem is that there is usually a pattern in the groups of students who receive lower quality opportunities—students of color and students who live in poor areas, urban and rural. This is not acceptable. Consequently, we emphasize the premise that the purpose of education research is to offer rich learning opportunities to all students.
One way to make sure you will be able to convince others of the importance of your study is to consider investigating some aspect of teachers’ shared instructional problems. Historically, researchers in education have set their own research agendas, regardless of the problems teachers are facing in schools. It is increasingly recognized that teachers have had trouble applying to their own classrooms what researchers find. To address this problem, a researcher could partner with a teacher—better yet, a small group of teachers—and talk with them about instructional problems they all share. These discussions can create a rich pool of problems researchers can consider. If researchers pursued one of these problems (preferably alongside teachers), the connection to improving learning opportunities for all students could be direct and immediate. “Grounding a research question in instructional problems that are experienced across multiple teachers’ classrooms helps to ensure that the answer to the question will be of sufficient scope to be relevant and significant beyond the local context” (Cai et al., 2019b , p. 115).
As a beginning researcher, determining the relevance and importance of a research problem is especially challenging. We recommend talking with advisors, other experienced researchers, and peers to test the educational importance of possible research problems and topics of study. You will also learn much more about the issue of research importance when you read Chap. 5 .
Exercise 1.7
Identify a problem in education that is closely connected to improving learning opportunities and a problem that has a less close connection. For each problem, write a brief argument (like a logical sequence of if-then statements) that connects the problem to all students’ learning opportunities.
Part III. Conducting Research as a Practice of Failing Productively
Scientific inquiry involves formulating hypotheses about phenomena that are not fully understood—by you or anyone else. Even if you are able to inform your hypotheses with lots of knowledge that has already been accumulated, you are likely to find that your prediction is not entirely accurate. This is normal. Remember, scientific inquiry is a process of constantly updating your thinking. More and better information means revising your thinking, again, and again, and again. Because you never fully understand a complicated phenomenon and your hypotheses never produce completely accurate predictions, it is easy to believe you are somehow failing.
The trick is to fail upward, to fail to predict accurately in ways that inform your next hypothesis so you can make a better prediction. Some of the best-known researchers in education have been open and honest about the many times their predictions were wrong and, based on the results of their studies and those of others, they continuously updated their thinking and changed their hypotheses.
A striking example of publicly revising (actually reversing) hypotheses due to incorrect predictions is found in the work of Lee J. Cronbach, one of the most distinguished educational psychologists of the twentieth century. In 1955, Cronbach delivered his presidential address to the American Psychological Association. Titling it “Two Disciplines of Scientific Psychology,” Cronbach proposed a rapprochement between two research approaches—correlational studies that focused on individual differences and experimental studies that focused on instructional treatments controlling for individual differences. (We will examine different research approaches in Chap. 4 ). If these approaches could be brought together, reasoned Cronbach ( 1957 ), researchers could find interactions between individual characteristics and treatments (aptitude-treatment interactions or ATIs), fitting the best treatments to different individuals.
In 1975, after years of research by many researchers looking for ATIs, Cronbach acknowledged the evidence for simple, useful ATIs had not been found. Even when trying to find interactions between a few variables that could provide instructional guidance, the analysis, said Cronbach, creates “a hall of mirrors that extends to infinity, tormenting even the boldest investigators and defeating even ambitious designs” (Cronbach, 1975 , p. 119).
As he was reflecting back on his work, Cronbach ( 1986 ) recommended moving away from documenting instructional effects through statistical inference (an approach he had championed for much of his career) and toward approaches that probe the reasons for these effects, approaches that provide a “full account of events in a time, place, and context” (Cronbach, 1986 , p. 104). This is a remarkable change in hypotheses, a change based on data and made fully transparent. Cronbach understood the value of failing productively.
Closer to home, in a less dramatic example, one of us began a line of scientific inquiry into how to prepare elementary preservice teachers to teach early algebra. Teaching early algebra meant engaging elementary students in early forms of algebraic reasoning. Such reasoning should help them transition from arithmetic to algebra. To begin this line of inquiry, a set of activities for preservice teachers were developed. Even though the activities were based on well-supported hypotheses, they largely failed to engage preservice teachers as predicted because of unanticipated challenges the preservice teachers faced. To capitalize on this failure, follow-up studies were conducted, first to better understand elementary preservice teachers’ challenges with preparing to teach early algebra, and then to better support preservice teachers in navigating these challenges. In this example, the initial failure was a necessary step in the researchers’ scientific inquiry and furthered the researchers’ understanding of this issue.
We present another example of failing productively in Chap. 2 . That example emerges from recounting the history of a well-known research program in mathematics education.
Making mistakes is an inherent part of doing scientific research. Conducting a study is rarely a smooth path from beginning to end. We recommend that you keep the following things in mind as you begin a career of conducting research in education.
First, do not get discouraged when you make mistakes; do not fall into the trap of feeling like you are not capable of doing research because you make too many errors.
Second, learn from your mistakes. Do not ignore your mistakes or treat them as errors that you simply need to forget and move past. Mistakes are rich sites for learning—in research just as in other fields of study.
Third, by reflecting on your mistakes, you can learn to make better mistakes, mistakes that inform you about a productive next step. You will not be able to eliminate your mistakes, but you can set a goal of making better and better mistakes.
Exercise 1.8
How does scientific inquiry differ from everyday learning in giving you the tools to fail upward? You may find helpful perspectives on this question in other resources on science and scientific inquiry (e.g., Failure: Why Science is So Successful by Firestein, 2015).
Exercise 1.9
Use what you have learned in this chapter to write a new definition of scientific inquiry. Compare this definition with the one you wrote before reading this chapter. If you are reading this book as part of a course, compare your definition with your colleagues’ definitions. Develop a consensus definition with everyone in the course.
Part IV. Preview of Chap. 2
Now that you have a good idea of what research is, at least of what we believe research is, the next step is to think about how to actually begin doing research. This means how to begin formulating, testing, and revising hypotheses. As for all phases of scientific inquiry, there are lots of things to think about. Because it is critical to start well, we devote Chap. 2 to getting started with formulating hypotheses.
Agnes, M., & Guralnik, D. B. (Eds.). (2008). Hypothesis. In Webster’s new world college dictionary (4th ed.). Wiley.
Google Scholar
Britannica. (n.d.). Scientific method. In Encyclopaedia Britannica . Retrieved July 15, 2022 from https://www.britannica.com/science/scientific-method
Brownell, W. A., & Moser, H. E. (1949). Meaningful vs. mechanical learning: A study in grade III subtraction . Duke University Press..
Cai, J., Morris, A., Hohensee, C., Hwang, S., Robison, V., Cirillo, M., Kramer, S. L., & Hiebert, J. (2019b). Posing significant research questions. Journal for Research in Mathematics Education, 50 (2), 114–120. https://doi.org/10.5951/jresematheduc.50.2.0114
Article Google Scholar
Cambridge University Press. (n.d.). Hypothesis. In Cambridge dictionary . Retrieved July 15, 2022 from https://dictionary.cambridge.org/us/dictionary/english/hypothesis
Cronbach, J. L. (1957). The two disciplines of scientific psychology. American Psychologist, 12 , 671–684.
Cronbach, L. J. (1975). Beyond the two disciplines of scientific psychology. American Psychologist, 30 , 116–127.
Cronbach, L. J. (1986). Social inquiry by and for earthlings. In D. W. Fiske & R. A. Shweder (Eds.), Metatheory in social science: Pluralisms and subjectivities (pp. 83–107). University of Chicago Press.
Hay, C. M. (Ed.). (2016). Methods that matter: Integrating mixed methods for more effective social science research . University of Chicago Press.
Merriam-Webster. (n.d.). Explain. In Merriam-Webster.com dictionary . Retrieved July 15, 2022, from https://www.merriam-webster.com/dictionary/explain
National Research Council. (2002). Scientific research in education . National Academy Press.
Weis, L., Eisenhart, M., Duncan, G. J., Albro, E., Bueschel, A. C., Cobb, P., Eccles, J., Mendenhall, R., Moss, P., Penuel, W., Ream, R. K., Rumbaut, R. G., Sloane, F., Weisner, T. S., & Wilson, J. (2019a). Mixed methods for studies that address broad and enduring issues in education research. Teachers College Record, 121 , 100307.
Weisner, T. S. (Ed.). (2005). Discovering successful pathways in children’s development: Mixed methods in the study of childhood and family life . University of Chicago Press.
Download references
Author information
Authors and affiliations.
School of Education, University of Delaware, Newark, DE, USA
James Hiebert, Anne K Morris & Charles Hohensee
Department of Mathematical Sciences, University of Delaware, Newark, DE, USA
Jinfa Cai & Stephen Hwang
You can also search for this author in PubMed Google Scholar
Rights and permissions
Open Access This chapter is licensed under the terms of the Creative Commons Attribution 4.0 International License ( http://creativecommons.org/licenses/by/4.0/ ), which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license and indicate if changes were made.
The images or other third party material in this chapter are included in the chapter's Creative Commons license, unless indicated otherwise in a credit line to the material. If material is not included in the chapter's Creative Commons license and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder.
Reprints and permissions
Copyright information
© 2023 The Author(s)
About this chapter
Hiebert, J., Cai, J., Hwang, S., Morris, A.K., Hohensee, C. (2023). What Is Research, and Why Do People Do It?. In: Doing Research: A New Researcher’s Guide. Research in Mathematics Education. Springer, Cham. https://doi.org/10.1007/978-3-031-19078-0_1
Download citation
DOI : https://doi.org/10.1007/978-3-031-19078-0_1
Published : 03 December 2022
Publisher Name : Springer, Cham
Print ISBN : 978-3-031-19077-3
Online ISBN : 978-3-031-19078-0
eBook Packages : Education Education (R0)
Share this chapter
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Publish with us
Policies and ethics
- Find a journal
- Track your research
- Artificial Intelligence
- Generative AI
- Cloud Computing
- CPUs and Processors
- Data Center
- Edge Computing
- Enterprise Storage
- Virtualization
- Internet of Things
- Network Management Software
- Network Security
- Enterprise Buyer’s Guides
- United States
- Newsletters
- Foundry Careers
- Terms of Service
- Privacy Policy
- Cookie Policy
- Copyright Notice
- Member Preferences
- About AdChoices
- E-commerce Links
- Your California Privacy Rights
Our Network
- Computerworld

25 leading-edge IT research projects
While universities don’t tend to shout as loudly about their latest tech innovations as do Google, Cisco and other big vendors, their results are no less impressive in what they could mean for faster, more secure and more useful networking. Here’s a roundup, in no particular order, of some of the most amazing and colorful projects in the works.
Follow Bob Brown on Twitter at: https://twitter.com/alphadoggs
1. Exploiting T-rays
Who needs electricity to run superfast computers when there’s terahertz radiation, or T-rays? University of Utah engineers have reached deep into the electromagnetic spectrum to find this new way to build circuits for computers that would run a thousand times faster than today’s gigahertz-speed computers. The development involves creation of waveguides to send and manipulate T-rays, also known as far-infrared light.
“We have taken a first step to making circuits that can harness or guide terahertz radiation,” says Ajay Nahata, study leader and associate professor of electrical and computer engineering, in a statement. “Eventually – in a minimum of 10 years – this will allow the development of superfast circuits, computers and communications.”
2. Hybrids: Computers, not cars
A multi-university research team funded by the Department of Defense is working to combine computer memory functions typically performed by magnetic components and computer logic operations typically handled by semiconductor components into a hybrid material. The benefit would be faster and more compact machines that chow down less power and are less expensive to build.
“In this approach, the coupling between magnetic and non-magnetic components would occur via a magnetic field or flow of electron spin, which is the fundamental property of an electron and is responsible for most magnetic phenomena,” says Giovanni Vignale , a University of Missouri physics professor in the College of Arts and Science, in a statement. “The hybrid devices that we target would allow seamless integration of memory and logical function, high-speed optical communication and switching, and new sensor capabilities.”
The Department of Defense awarded a $6.5 million grant to the University of Iowa for the project. In addition to the Iowa and Missouri schools, also working on the project are researchers from New York University, University of California at Berkeley and the University of Pittsburgh.
3. Getting to bottom of Web searches
Web search might seem like a complex issue, but it really boils down to three basic kinds of searches: informational, navigational and transactional (related to buying something).
That’s the word from researchers at Penn State University’s College of Information Sciences and Technology and Australia’s Queensland University of Technology who looked at more than 1.5 million queries from hundreds of thousands of search engines users.
The bulk of searches (80%) proved to be informational, with the other 20% split between navigational and transactional. The researchers used an algorithm that they say classified searches with a 74% accuracy rate.
“Other results have classified comparatively much smaller sets of queries, usually manually,” said Jim Jansen, assistant professor in Penn State’s College of Information Sciences and Technology, in a statement . “This research aimed to classify queries automatically.
The researchers’ work is outlined in a paper titled “Determining the informational, navigational and transactional intent of Web queries” that will appear in the May issue of Information Processing & Management.
4. Mapping the whole Internet
Israeli researchers have created a topographical map of the Internet by enlisting more than 5,600 volunteers across 97 countries who agreed to download a program that tracks how Internet nodes interact with each other.
The result is “the most complete picture of the Internet available today,” Bar Ilan University researcher Shai Carmi told the MIT Technology Review .
“A better understanding of the Internet’s structure is vital for integration of voice, data and video streams, point-to-point and point-to-many distribution of information, and assembling and searching all of the world’s information,” Carmi and fellow researchers state in a new report published in the Proceedings of the National Academy of Sciences . “It may reveal evolutionary processes that control the growth of the Internet.”
Carmi’s research uses a program called the DIMES agent, which is downloaded onto volunteers’ computers and performs Internet measurements such as traceroute and ping. The project’s Web site promises that, along with providing a “good feeling,” using the DIMES agent will provide maps to users showing how the Internet looks from their homes. Users of the program chat about their findings at this forum .
Another project that tracks Internet traffic growth is called the Minnesota Internet Traffic Studies (MINTS) site.
5. The Fluid Project
A handful of universities, including the University of Toronto and the University of California, Berkeley, is working to build a software architecture and reusable components that can make Web applications easier to develop and use. The Fluid Project’s work focuses on user-centered design practices. Vendors such as Mozilla Foundation, IBM and Sun are also taking part.
The latest news out of the project is that a grant has been awarded to the Adaptive Technology Resource Centre at the University of Toronto from the Mozilla Foundation to promote DHTML accessibility and the adoption of ARIA (the W3C Web Accessibility Initiative’s Accessible Rich Internet Applications specification).
6. Attila: one radio on many wireless networks
Today’s wireless networks are in a rut: Most radios that form the networks can only work on one frequency band of the spectrum. If that band is glutted, glitchy or jammed, the radios are useless.
Enter Attila the Radio, invented by two researchers at Stevens Institute of Technology, in Hoboken, N.J. The concept is simple: Attila parcels out a stream of data packets over any and all available wireless spectrum at the same time. The packets could stream, for example, over a Wi-Fi mesh, Verizon’s Code Division Multiple Access (CDMA) cell network, rival AT&T’s Global System for Mobile Communications (GSM) airwaves, and over a WiMAX link.
Current prototypes use several radios, one for each of the networks being used, but the goal is a single radio. The future of Attila the radio lies now with Attila the company, formally known as Atilla Technologies, which was founded in 2005 by two Stevens Institute of Technology researchers.
7. Sniffing out insider threats
Researchers are developing technology they say will use data mining and social networking techniques to spot and stop insider security threats and industrial espionage.
Air Force Institute of Technology researchers have developed software that can spot insider threats using an extended version of automated document indexing known as Probabilistic Latent Semantic Indexing (PLSI). This technology can discern employees’ interests from e-mail and create a social network graph showing their various interactions, researchers said.
The technology could help any organization sniff out insider threats by analyzing e-mail activity or find individuals among potentially tens of thousands of employees with latent interests in sensitive topics. The same technology might also be used to spot individuals who feel alienated within the organization as well as unraveling any worrying changes in their social network interactions. The researchers explain that individuals who have shown an interest in a sensitive topic but who have never communicated to others within the organization on this subject are often the most likely to be an insider threat.
The software can reveal those people either with a secret interest in that topic or who may feel alienated from the organization and so communicate their interest in it only to those outside the organization, researchers said. Another important signal of alienation or a potential problem is a shift in the connections between an individual and others within the organization. If an individual suddenly stops communicating or socializing with others with whom they have previously had frequent contact, then the technology could alert investigators to such changes.
The research team tested their approach on the archived body of messages from the liquidated Enron company e-mail system.
8. All about Twitter
University of Maryland students have written a paper called “ Why We Twitter: Understanding Microblogging Usage and Communities ” examining why people Twitter. Also known as microblogging , Twittering is a new form of communication in which users can describe their current status in short posts distributed by instant messages, mobile phones, e-mail or the Web,” according to the paper’s abstract.
The authors, Akshay Java, Xiaodan Song, Tim Finin and Belle Tseng, say the paper “presents our observations of the microblogging phenomena by studying the topological and geographical properties of Twitter’s social network.” They concluded that figuring out why individuals microblog is elusive, but that by analyzing an aggregate of data across a community can provide insight into why a group of people microblog.
9. Spotting phishers
Scientists at Carnegie Mellon University have developed an online game designed to teach Internet users about the dangers of phishing.
Featuring a cartoon fish named Phil, the game, called Anti-Phishing Phil , has been tested in CMU’s Privacy and Security Laboratory. Officials with the lab say users who spent 15 minutes playing the interactive, online game were better able to discern fraudulent Web sites than those who simply read tutorials about the threat.
The game focuses on teaching Internet users how to tell the URL of a fraudulent site from a legitimate one, officials say. It offers tips such as examining URLs for misspellings of popular sites, dissecting a Web address to understand where it’s pointing to, and using Google to validate a URL against search results. More here.
10. RFID and the heart
Telemedicine researchers have been awarded a $400,000 grant to work on integrating RFID technology with cardiac sensor networks used to monitor patients’ heartbeats.
The Rochester Institute of Technology says its work will make cardiac sensor networks more secure, reducing the chances of identity theft or other abuse. The work could also make the healthcare process work more efficiently by supporting RFID tags on medicine bottles, the school says.
“Telemedicine technology can greatly increase the quality of medical care while also decreasing healthcare costs,” said Fei Hu, assistant professor of computer engineering at RIT, in a statement. “Through this project we hope to increase the integration of RFID into existing cardiac sensor networks, ensure the overall security of the system and promote the implementation of the technology in nursing homes and adult care facilities across the country.”
11. Analyzing the “Dark Web”
Computer scientists at a University of Arizona lab have created a project called Dark Web that is designed to track and analyze the moves of terrorists and extremists using the Internet to spread propaganda, recruit members and plan attacks (click here to read our feature on cyberwar).
The project, which is funded by the National Science Foundation and other federal agencies, is led by Hsinchun Chen at the Artificial Intelligence Lab in Tucson. Dark Web’s specialty is tracking massive amounts of information scattered across thousands of Web sites and in e-mail and other online programs. Spidering, link analysis, multimedia analysis and other techniques are used, according to the NSF.
A method dubbed Writeprint is used to strip away the anonymity of terrorists online by analyzing language, semantic and other features of content and comparing it with other content posted across the Internet. Authors can be identified and new information published by the authors can be flagged as it is posted and spread. One recent study by the Dark Web team identified stories and videos used to train terrorists in building improvised explosive devices.
Not that the terrorists are unaware they’re being watched.
“They can put booby-traps in their Web forums,” Chen said in a statement, “and the spider can bring back viruses to our machines.”
12. Really, really fast wireless
Scientists at the Georgia Electronic Design Center (GEDC) at the Georgia Institute of Technology have designed a system that can transfer data at 5Gbps at a range of 5 meters.
Joy Laskar, the GEDC’s director, says many of the products designed for the 60GHz band initially will be marketed to consumers for home use, because businesses are more likely to take wait-and-see attitudes with new technology that hasn’t yet proved reliable. Even so, he says he can imagine several business applications for multigigabit networks, especially in the field of large-scale data transfer. “Imagine that you have a portable device that’s essentially an evolved iPod that has hundreds of gigs of storage,” he says. “One scenario would be to have several kiosks around an office that could wirelessly send information to your device.”
Separately, a team of engineers at Georgia Tech Research Institute (GTRI) is taking a new approach to phased-array antennas that the developers say could enable an ultra-wideband device to do the job of five regular antennas.
The Fragmented Aperture Antenna has already demonstrated a 33-to-1 bandwidth, blowing by the 10-to-1 ratio of conventional systems. Researchers say a 100-to-1 ratio might not be far off for use in radar and communications environments.
13. Real bandwidth management
University of California at San Diego computer scientists say they have developed a TCP-based bandwidth management system that works across global networks.
The “flow proportional share” algorithm created by Barath Raghavan and his teammates is designed to enable a group of rate limiters to work together, providing better availability of network applications, including Web sites.
“With our system, an organization with mirrored Web sites or other services across the globe could dynamically shift its bandwidth allocations between sites based on demand. You can’t do that now, and this lack of control is a significant drawback to today’s cloud-based computing approaches,” said Raghavan, a Ph.D. candidate in the Department of Computer Science and Engineering at UCSD’s Jacobs School of Engineering.
The work is described in a paper called “Cloud Control with Distributed Rate Limiting”.
14. Doing away with digital clutter
MIT researchers have come up with a way to measure visual clutter, a breakthrough that could help everyone from fighter pilots to Web site designers.
The scientists published a paper in the Journal of Vision that explains their work. The impetus for the work was that “we lack a clear understanding of what clutter is, what features, attributes and factors are relevant, why it presents a problem and how to identify it,” says Ruth Rosenholtz, principal research scientist at MIT’s Department of Brain and Cognitive Sciences.
Another issue is that clutter is perceived differently by different people, so coming up with a universal measure of what’s hard or easy to pick out in a display is challenging. The model devised takes into account such factors as color, data and contrast. here .
The researchers tested their model on people looking at a map, trying to find an arrow saying “You are here,” for example.
Rosenholtz plans to offer the MIT team’s visual clutter tool to designers as part of a continuing study. You can test out the level of clutter in a display yourself by going
15. Finding pictures of needles in haystacks
Penn State researchers have developed software they say tags images upon uploading to Yahoo’s Flickr or other photo systems but also automatically updates those tags based on how people interact with the photos.
This could greatly improve searching for images, the researchers say.
“Tagging itself is challenging as it involves converting an image’s pixels to descriptive words,” said James Wang, lead researcher and associate professor of information sciences and technology, in a statement. “But what is novel with the ‘Tagging over Time’ or T/T technology is that the system adapts as people’s preferences for images and words change.”
In recent tests the system was shown to correctly annotate four of every 10 images. It still needs work, but is an improvement over an earlier Penn State-developed system dubbed Automatic Linguistic Indexing of Pictures-Real Time that analyzed pixel content to suggest tags. The new software, which relies on machine-learning, is described in more detail in a paper called “Tagging Over Time: Real-world Image Annotation by Lightweight Meta-learning.” The researchers say accuracy of the new system can grow from 40% to 60% as it learns from user behavior.
16. Videoconferencing made for Dr. Phil
While videoconferencing has proven its worth for corporate meetings and distance learning, researchers say the technology could also play a big role in mediating disputes between coworkers, neighbors and family members.
Researchers from the University of Bath in the United Kingdom interviewed a dozen conciliators to determine their views on what it would be like to use video technology in their jobs. The researchers say video holds the promise of being useful because it can better translate the emotional state of the parties involved and reduces possible intimidation when parties are in the same room.
“Most of the conciliation to sort out disputes between employees is done by phone because for the conciliator, who may have as many as 70 or 80 cases to deal with at once, it can be difficult, costly and slow to arrange to see people in person,” said Department of Computer Science Director of Studies Leon Watts in a statement. “In situations of high conflict, it can be hard to get to the real issues, to judge what people really care about, on the phone. So using a video link, in which the conciliator can in addition see each of the disputing parties, is a step forward: it gives them new options for appreciating parties’ depth of concern about different issues.”
The increased availability of broadband services and improved video quality combine to make widespread videoconferencing feasible, the researchers said. The researchers plan to work with a conciliation training organization to spread the word on videoconferencing.
17. Vocal Joystick
University of Washington researchers have developed software designed to let those who can’t work a handheld mouse use their voice instead to navigate the Web.
“There are many people who have perfect use of their voice who don’t have use of their hands and arms,” said Jeffrey Bilmes, an associate professor of electrical engineering, in a statement. “There are several reasons why Vocal Joystick might be a better approach, or at least a viable alternative, to brain-computer interfaces.”
The Vocal Joystick detects sounds 100 times a second, relying on vowel sounds to move in one direction or another and moving faster or slower depending on voice volume. “K” and “ch” sounds are used for mouse clicks and releases. Some wonder why speech recognition technology might not be better, but the University of Washington researchers say it would be too slow since it would rely on drawn-out, discrete commands. ( Watch a video of how Vocal Joystick works here.)
The tool can be used for Web browsing, as well as for playing video games and even drawing on a screen.
18. Measuring boredom
The National Science Foundation is funding research that could enable computers to respond to your levels of frustration or boredom. In other words, we’re talking about “mind reading” technology.
Tufts University researchers are exploiting near-infrared spectroscopy technology that uses light to pick up on your emotional cues by monitoring brain blood flow.
Of course, for now you need to wear a funky headband to make it work (the headband “uses laser diodes to send near-infrared light through the forehead at a relatively shallow depth – only two to three centimeters – to interact with the brain’s frontal lobe,” according to Tufts.)
19. Better computer building blocks
A University of Maryland researcher has come up with a method that he says could one day be used by companies to build nanoscale computer and cell phone components faster and less expensively.
Ray Phaneuf , associate professor of materials science and engineering at the A. James Clark School of Engineering, compares his idea to self-assembly processes in nature such as crystallization.
Phaneuf has built a photolithography- and etching-based template that nature can use to assemble atoms into predefined patterns for creating things such as laptop semiconductors, wearable device sensors and cell phone components. His work has focused on silicon, typically used for computer components, and gallium arsenide, which is common in cell phone parts.
“While we understand how to make working nanoscale devices, making things out of a countable number of atoms takes a long time,” Phaneuf said in a statement . “Industry needs to be able to mass-produce them on a practical time scale.” Such devices could even be used some day in building the “qubits” that serve as the basis of advanced quantum computing machines, Phaneuf said.
Phaneuf’s work focuses on silicon and gallium arsenide components. Silicon is the prevalent material for components in computers while gallium arsenide is used more often in cell phones.
20. Good Samaritans
Dartmouth researchers say they were surprised to find that Good Samaritans – those people who update the online Wikipedia encyclopedia when just passing by – are actually as reliable as regular, registered users of the site.
The researchers examined the quality of Wikipedia content based on how long it persisted before being changed or corrected. Wikipedia’s archive of edits and user reputation allowed for the research to be done.
“This finding was both novel and unexpected,” said Denise Anthony, associate professor of sociology, in a statement. “In traditional laboratory studies of collective goods, we don’t include Good Samaritans, those people who just happen to pass by and contribute, because those carefully designed studies don’t allow for outside actors. It took a real-life situation for us to recognize and appreciate the contributions of Good Samaritans to Web content.”
Sean Smith, associate professor of computer science, added: “Wikipedia is a great example of how open-source contributions work for the greater good.”
The researchers’ findings are presented in a paper called “The Quality of Open Source Production: Zealots and Good Samaritans in the Case of Wikipedia.”
21. Honeybees and the Internet
Honeybee intelligence can be used to improve the speed and efficiency of Internet servers by up to 25%, according to Georgia Institute of Technology researchers.
Honeybees somehow manage to efficiently collect a lot of nectar with limited resources and no central command. Such swarm intelligence of these amazingly organized bees can also be used to improve the efficiency of Internet servers faced with similar challenges, researchers said. A bee dance-inspired communications system developed by Georgia Tech helps Internet servers that would normally be devoted solely to one task move between tasks as needed, reducing the chances that a Web site could be overwhelmed with requests and lock out potential users and customers.
Compared with the way server banks are commonly run, the honeybee method typically improves service by 4% to 25% in tests based on real Internet traffic, researchers said. Internet servers typically have a set number of servers devoted to a certain Web site or client. When users access a Web site, the servers provide computing power until all the requests to access and use the site have been fulfilled. Sometimes there are a lot of requests to access a site — for instance, a clothing company’s retail site after a particularly effective television ad during a popular sporting event — and sometimes there are very few. Predicting demand for Web sites, including whether a user will access a video clip or initiate a purchase, is extremely difficult in a fickle Internet landscape, and servers are frequently overloaded and later become completely inactive at random.
Bees tackle their resource allocation problem (such as a limited number of bees and unpredictable demand on their time and desired location) with a seamless system driven by “dances.” Here’s how it works: The scout bees leave the hive in search of nectar. Once they’ve found a promising spot, they return to the hive “dance floor” and perform a dance. The direction of the dance tells the waiting forager bees which direction to fly, the number of waggle turns conveys the distance to the flower patch; and the length conveys the sweetness of the nectar. The bee/Internet research was published in the Bioinspiration and Biomimetics journal.
22. Pushing 100Gbps copper networks
Penn State engineers are trying to push relatively short Category-7 copper cables to support digital data speeds up to 100Gbps.
The idea would be to enable copper cables within a room or building, perhaps being used to interconnect servers, to handle data rates typically reserved for fiber-optic links. The trick has been coming up with a transmitter/receiver that uses error correcting and equalizing methods to can cancel interference better than traditional systems.
“A rate of 100 gigabit over 70 meters is definitely possible, and we are working on extending that to 100 meters, or about 328 feet,” said Ali Enteshari, graduate student in electrical engineering, in a statement. “However, the design of a 100 gigabit modem might not be physically realizable at this time as it is technology limited. We are providing a roadmap to design a high-speed modem for 100 gigabits.”
Mohsen Kavehrad , a professor of electrical engineering at Penn State, says his team is working with NEXANS, the company that makes the cable. “These are the current, new generation of Ethernet cables,” he says.
23. Drivers wielding cell phones
We’ve seen or heard about drivers on cell phones causing accidents. But research from the University of Utah also shows that such drivers are also responsible for slowing traffic flows.
Those talking on cell phones tend to drive more slowly on freeways, pass slowgoing vehicles less frequently and generally take longer to get from one point to another, the researchers found. This can cost society in terms of lost productivity, fuel costs and more, the researchers concluded.
“At the end of the day, the average person’s commute is longer because of that person who is on the cell phone right in front of them,” said University of Utah psychology Professor Dave Strayer, leader of the research team, in a statement. “That SOB on the cell phone is slowing you down and making you late.”
The research is based on a PatrolSim driving simulator.
Meanwhile, don’t feel so smug about how safety conscious you are by using a hands-free cell phone in the car: Carnegie Mellon University researchers say you’re still likely to be distracted.
The researchers used brain imaging to show that even just listening to a cell phone while driving cuts by more than a third your attention to driving. Subjects inside an MRI brain scanner were tested on a driving simulator and were found to weave, similar to if they were under the influence of alcohol. The study (featuring cool colorful brain images) showed lessened activity in the brain’s parietal lobe, which is called upon for spatial sense and navigation, and occipital lobe, which handles visual information.
24. Open source on bug patrol
An open source tool is being readied for release this year that its creators say could dramatically speed software development and improve software quality.
Computer scientists from the National Institute of Standards and Technology and the University of Texas at Arlington credit the use of “combinatorial testing” for their breakthrough.
The trick is being able to quickly test interactions of up to six variables. The work stemmed from research into what really causes bugs in software. The researchers found that it is more often caused by problematic interactions between a few variables rather than a bunch even if a program, such as an e-commerce application, features hundreds of variables.
Findings of this latest software debugging research are described in several presentations, one by NIST researchers and another by University of Texas researchers
Developers interested in getting your hands on code should contact NIST’s Raghu Kacker.
25. Geeks and glasses
Who knew? People who wear glasses are not stereotypical geeks or nerds. At least according to a study released by Australian vision researchers.
The scientists claim this is the first time a study looked into personality and nearsightedness or myopia. Participants were analyzed using a state-of-the-art measure of the five major personality factors (openness, conscientiousness, extroversion, agreeableness and neuroticism), administered by psychologists from the University of Melbourne.
Researchers concluded: “The long-held view that myopic persons are introverted and conscientious may reflect intelligence-related stereotypes rather than real correlations. Furthermore, the predictive characteristic of intellect, subsumed in openness, appeared to be representative of a previously reported link between IQ and myopia rather than personality and myopia.”
“We have literally busted the myth that people who wear glasses are introverted or have particular personality characteristics. They are more likely to be agreeable and open, rather than closed and introverted,” said Paul Baird of the University of Melbourne’s Centre for Eye Research Australia in a release.
For past network research roundups, see:
15 bleeding-edge network research projects you should know about
10 cutting-edge network research projects you should know about
Related content
Iphone 8 rumor rollup: cranking up the processors; 3d cameras; $1k-plus price, snl one step ahead of amazon with echo silver, you really should know what the andrew file system is, getting a jump on private lte networks, newsletter promo module test.

Bob Brown is the former news editor for Network World.
More from this author
Small cell forum seeks advice from large enterprises, how to make fully homomorphic encryption “practical and usable”, most popular authors.

Show me more
What is a network switch and how does it work.

IBM, Fortinet expand cloud security protection

Nvidia, Google Cloud team to boost AI startups

Episode 1: Understanding Cisco’s Converged SDN Transport

Episode 2: Pluggable Optics and the Internet for the Future

Episode 3: Looking Forward: 5G, Digital Transformation, and the Network of the Future

Are unused IPv4 addresses a secret gold mine?

Preparing for a 6G wireless world: Exciting changes coming to the wireless industry

How to calculate factorials in Linux

- Skip to main content
- Skip to primary sidebar
- Skip to footer
- QuestionPro

- Solutions Industries Gaming Automotive Sports and events Education Government Travel & Hospitality Financial Services Healthcare Cannabis Technology Use Case NPS+ Communities Audience Contactless surveys Mobile LivePolls Member Experience GDPR Positive People Science 360 Feedback Surveys
- Resources Blog eBooks Survey Templates Case Studies Training Help center
Home Market Research
What is Research: Definition, Methods, Types & Examples

The search for knowledge is closely linked to the object of study; that is, to the reconstruction of the facts that will provide an explanation to an observed event and that at first sight can be considered as a problem. It is very human to seek answers and satisfy our curiosity. Let’s talk about research.
Content Index
What is Research?
What are the characteristics of research.
- Comparative analysis chart
Qualitative methods
Quantitative methods, 8 tips for conducting accurate research.
Research is the careful consideration of study regarding a particular concern or research problem using scientific methods. According to the American sociologist Earl Robert Babbie, “research is a systematic inquiry to describe, explain, predict, and control the observed phenomenon. It involves inductive and deductive methods.”
Inductive methods analyze an observed event, while deductive methods verify the observed event. Inductive approaches are associated with qualitative research , and deductive methods are more commonly associated with quantitative analysis .
Research is conducted with a purpose to:
- Identify potential and new customers
- Understand existing customers
- Set pragmatic goals
- Develop productive market strategies
- Address business challenges
- Put together a business expansion plan
- Identify new business opportunities
- Good research follows a systematic approach to capture accurate data. Researchers need to practice ethics and a code of conduct while making observations or drawing conclusions.
- The analysis is based on logical reasoning and involves both inductive and deductive methods.
- Real-time data and knowledge is derived from actual observations in natural settings.
- There is an in-depth analysis of all data collected so that there are no anomalies associated with it.
- It creates a path for generating new questions. Existing data helps create more research opportunities.
- It is analytical and uses all the available data so that there is no ambiguity in inference.
- Accuracy is one of the most critical aspects of research. The information must be accurate and correct. For example, laboratories provide a controlled environment to collect data. Accuracy is measured in the instruments used, the calibrations of instruments or tools, and the experiment’s final result.
What is the purpose of research?
There are three main purposes:
- Exploratory: As the name suggests, researchers conduct exploratory studies to explore a group of questions. The answers and analytics may not offer a conclusion to the perceived problem. It is undertaken to handle new problem areas that haven’t been explored before. This exploratory data analysis process lays the foundation for more conclusive data collection and analysis.
LEARN ABOUT: Descriptive Analysis
- Descriptive: It focuses on expanding knowledge on current issues through a process of data collection. Descriptive research describe the behavior of a sample population. Only one variable is required to conduct the study. The three primary purposes of descriptive studies are describing, explaining, and validating the findings. For example, a study conducted to know if top-level management leaders in the 21st century possess the moral right to receive a considerable sum of money from the company profit.
LEARN ABOUT: Best Data Collection Tools
- Explanatory: Causal research or explanatory research is conducted to understand the impact of specific changes in existing standard procedures. Running experiments is the most popular form. For example, a study that is conducted to understand the effect of rebranding on customer loyalty.
Here is a comparative analysis chart for a better understanding:
It begins by asking the right questions and choosing an appropriate method to investigate the problem. After collecting answers to your questions, you can analyze the findings or observations to draw reasonable conclusions.
When it comes to customers and market studies, the more thorough your questions, the better the analysis. You get essential insights into brand perception and product needs by thoroughly collecting customer data through surveys and questionnaires . You can use this data to make smart decisions about your marketing strategies to position your business effectively.
To make sense of your study and get insights faster, it helps to use a research repository as a single source of truth in your organization and manage your research data in one centralized data repository .
Types of research methods and Examples

Research methods are broadly classified as Qualitative and Quantitative .
Both methods have distinctive properties and data collection methods.
Qualitative research is a method that collects data using conversational methods, usually open-ended questions . The responses collected are essentially non-numerical. This method helps a researcher understand what participants think and why they think in a particular way.
Types of qualitative methods include:
- One-to-one Interview
- Focus Groups
- Ethnographic studies
- Text Analysis
Quantitative methods deal with numbers and measurable forms . It uses a systematic way of investigating events or data. It answers questions to justify relationships with measurable variables to either explain, predict, or control a phenomenon.
Types of quantitative methods include:
- Survey research
- Descriptive research
- Correlational research
LEARN MORE: Descriptive Research vs Correlational Research
Remember, it is only valuable and useful when it is valid, accurate, and reliable. Incorrect results can lead to customer churn and a decrease in sales.
It is essential to ensure that your data is:
- Valid – founded, logical, rigorous, and impartial.
- Accurate – free of errors and including required details.
- Reliable – other people who investigate in the same way can produce similar results.
- Timely – current and collected within an appropriate time frame.
- Complete – includes all the data you need to support your business decisions.
Gather insights

- Identify the main trends and issues, opportunities, and problems you observe. Write a sentence describing each one.
- Keep track of the frequency with which each of the main findings appears.
- Make a list of your findings from the most common to the least common.
- Evaluate a list of the strengths, weaknesses, opportunities, and threats identified in a SWOT analysis .
- Prepare conclusions and recommendations about your study.
- Act on your strategies
- Look for gaps in the information, and consider doing additional inquiry if necessary
- Plan to review the results and consider efficient methods to analyze and interpret results.
Review your goals before making any conclusions about your study. Remember how the process you have completed and the data you have gathered help answer your questions. Ask yourself if what your analysis revealed facilitates the identification of your conclusions and recommendations.
LEARN MORE ABOUT OUR SOFTWARE FREE TRIAL
MORE LIKE THIS

Top 13 A/B Testing Software for Optimizing Your Website
Apr 12, 2024

21 Best Contact Center Experience Software in 2024

Government Customer Experience: Impact on Government Service
Apr 11, 2024

Employee Engagement App: Top 11 For Workforce Improvement
Apr 10, 2024
Other categories
- Academic Research
- Artificial Intelligence
- Assessments
- Brand Awareness
- Case Studies
- Communities
- Consumer Insights
- Customer effort score
- Customer Engagement
- Customer Experience
- Customer Loyalty
- Customer Research
- Customer Satisfaction
- Employee Benefits
- Employee Engagement
- Employee Retention
- Friday Five
- General Data Protection Regulation
- Insights Hub
- Life@QuestionPro
- Market Research
- Mobile diaries
- Mobile Surveys
- New Features
- Online Communities
- Question Types
- Questionnaire
- QuestionPro Products
- Release Notes
- Research Tools and Apps
- Revenue at Risk
- Survey Templates
- Training Tips
- Uncategorized
- Video Learning Series
- What’s Coming Up
- Workforce Intelligence
Enabling Data Driven Research

Enabling Biomedical Data Driven Research
Supplying infrastructure, tools, and services to Stanford biomedical researchers
Research IT organizational changes
Research it is now part of a bigger and unified research technology team led by dr. todd ferris. research it is renamed to research technology engineering services . the redcap team, previously part of research it, is now part of research technology application solutions. the research technology team also includes data services (fka research informatics center). stay tuned for a more comprehensive update. .

Consultation Service
Comprehensive, time-saving support from our experts.

Latest News
See the latest goings on at Research IT.

Crucial information and important links for researchers.

Our mission, team, history, publications and more.
Featured News
Researchit-2021-year-in-review.
- OHDSI-2021-Symposium
- Manuscript on flowsheet data integration in STARR
- Manuscript on integration of Beside Monitoring data with STARR
- Research IT Summer Internship
- A new SHC Clarity for SoM


researchIT CT

researchIT CT is the Connecticut State Library’s FREE research engine for use by libraries, schools, faculty, students, and residents throughout the state.
Additional resources.
- Access Workforce Solutions from EBSCO’s Learning Express here!

- Learn about access to free ebook and eaudiobooks through the eGO program for public libraries and the eGO Community Share program for Connecticut Schools.

Free Online Educational Resources
- CT Learning Hub is your destination for universal access to curated tools and resources anytime, anywhere. The CT Learning Hub puts resources in the hands of CT families, students and educators. The Hub is a free and interactive web page of digital resources to support online and offline learning.
- The Amistad Digital Resource provides a much-needed solution to help teachers fulfill curricular requirements educational based on mandates requiring the integration of African-American history by many state legislatures.
- ProQuest launched a new website: The Black Freedom Struggle in the United States . It’s a free, open resource for students, educators and others who are researching U.S. Black history.
- PQDT Open from ProQuest provides the full text of open access dissertations and theses free of charge.
- TeachRock.org is an open educational resource of hundreds of unit and lesson plans, Student Editions, and musician bios. TeachRock’s “Rock and Soul of America” high school history course is taught throughout California, Colorado, New Mexico, Ohio, Connecticut, New York, New Jersey, and elsewhere.
- Estuary Magazine A quarterly magazine for people who care about the Connecticut River; its history, health, and ecology— present and future amd learn more about science and conservation, wildlife, recreation, history, people and lifestyle—everything you need to understand the pressing issues in the watershed and explore ways to enjoy birding, boating, fishing, nature, and more.
- Thinkalong™ is a free educational service of Connecticut Public , the parent company of Connecticut Public Television and Connecticut Public Radio , and the state’s only locally-owned media organization producing TV, radio, print, web and digital content for Connecticut’s wide-ranging and diverse communities.
- For educators and students looking to find open and free access to e-resources, use this link from the Connecticut State Library.
Four students at Ellington High School, CT explain researchIT CT researchIT CT for Middle Schools screencast -->
A service of the Connecticut State Library and your local library Authorized and funded by the State of Connecticut with support from the Institute for Museum and Library Services

Find Info For
- Current Students
- Prospective Students
- Research and Partnerships
- Entrepreneurship and Commercialization
Quick Links
- Health and Life Sciences
- Info Security and AI
- Transformative Education
- Purdue Today
- Purdue Global
- Purdue in the News
April 3, 2024
SK hynix announces semiconductor advanced packaging investment in Purdue Research Park

SK hynix announced Wednesday (April 3) semiconductor advanced packaging investment in Purdue Research Park. From left to right: Indiana Gov. Eric Holcomb; Kwak Noh-jung, SK hynix president and CEO; Woojin Choi, SK hynix executive vice president; Arati Prabhakar, director, White House Office of Science and Technology Policy, and assistant to the president for science and technology; Mung Chiang, Purdue University president (speaking); Arun Venkataraman, U.S. Department of Commerce assistant secretary; U.S. Sen. Todd Young; Hyundong Cho, ambassador of the Republic of Korea to the United States; David Rosenberg, Indiana secretary of commerce; Mitch Daniels, Purdue Research Foundation chairman. (Purdue University/Kelsey Lefever)
The company's facility for AI memory chips marks the largest single economic development in the history of the state
WEST LAFAYETTE, Ind. — SK hynix Inc. announced Wednesday (April 3) that it plans to invest close to $4 billion to build an advanced packaging fabrication and R&D facility for AI products in the Purdue Research Park. The development of a critical link in the U.S. semiconductor supply chain in West Lafayette marks a giant leap forward in the industry and the state.
“We are excited to build a state-of-the-art advanced packaging facility in Indiana,” said SK hynix CEO Kwak Noh-Jung. “We believe this project will lay the foundation for a new Silicon Heartland, a semiconductor ecosystem centered in the Midwest Triangle. This facility will create local, high-paying jobs and produce AI memory chips with unmatched capabilities, so that America can onshore more of its critical chip supply chain. We are grateful for the support of Gov. Holcomb and the state of Indiana, of President Chiang at Purdue University, and of the broader community involved, and we look forward to expanding our partnership in the long run.”
SK hynix joins Bayer, imec, MediaTek, Rolls-Royce, Saab and many more national and international companies bringing innovation to America's heartland. The new facility — home to an advanced semiconductor packaging production line that will mass-produce next-generation high-bandwidth memory, or HBM, chips, the critical component of graphic processing units that train AI systems such as ChatGPT — is expected to provide more than a thousand new employment opportunities in the Greater Lafayette community. The company plans to begin mass production in the second half of 2028.
The project marks SK hynix’s intention for long-term investment and partnership in Greater Lafayette. The company’s decision-making framework prioritizes both profit and social responsibility while promoting ethical actions and accountability. From infrastructure developments that make accessing amenities easier to community empowerment projects such as skill development and mentorship, the SK hynix advanced packaging fabrication marks a new era of collaborative growth.
“Indiana is a global leader in innovating and producing the products that will power our future economy, and today’s news is proof positive of that fact,” said Indiana Gov. Eric Holcomb. “I’m so proud to officially welcome SK hynix to Indiana, and we’re confident this new partnership will enhance the Lafayette-West Lafayette region, Purdue University and the state of Indiana for the long term. This new semiconductor innovation and packaging plant not only reaffirms the state’s role in the hard-tech sector, but is also another tremendous step forward in advancing U.S. innovation and national security, putting Hoosiers at the forefront of national and global advancements.”
Investment in the Midwest and Indiana was spurred by Purdue’s excellence in discovery and innovation and its track record of exceptional R&D and talent development through collaboration. Partnerships among Purdue, the corporate sector, and the state and federal government are essential to advancing the U.S. semiconductor industry and establishing the region as the Silicon Heartland.
“SK hynix is the global pioneer and dominant market leader in memory chips for AI,” Purdue President Mung Chiang said. “This transformational investment reflects our state and university’s tremendous strength in semiconductors, hardware AI and development of the Hard-Tech Corridor. It is also a monumental moment for completing the supply chain of the digital economy in our country through the advanced packaging of chips. Located at Purdue Research Park, the largest facility of its kind at a U.S. university will grow and succeed through innovation.”
In 1990 the U.S. was producing nearly 40% of the world’s semiconductors. However, as manufacturing moved to Southeast Asia and China, the U.S. global output of semiconductor manufacturing has fallen to closer to 12%.
“SK hynix will soon be a household name in Indiana,” said U.S. Sen. Todd Young. “This incredible investment demonstrates their confidence in Hoosier workers, and I’m excited to welcome them to our state. The CHIPS and Science Act opened a door that Indiana has been able to sprint through, and companies like SK hynix are helping to build our high-tech future.”
To aid in bringing semiconductor manufacturing closer to home and shoring up global supply chains, the U.S. Congress introduced the Creating Helpful Incentives to Produce Semiconductors for America Act, or CHIPS and Science Act, on June 11, 2020. Signed by President Joe Biden on Aug. 9, 2022, it funds holistic development of the semiconductor industry to the tune of $280 billion. It supports the nation's research and development, manufacturing, and supply chain security of semiconductors.
“When President Biden signed the bipartisan CHIPS and Science Act, he put a stake in the ground and sent a signal to the world that the United States cares about semiconductor manufacturing,” said Arati Prabhakar, President Biden’s chief science and technology advisor and director of the White House Office of Science and Technology Policy. “Today’s announcement will strengthen the economy and national security, and it will create good jobs that support families. This is how we do big things in America.”
Purdue Research Park, one of the largest university-affiliated incubation complexes in the country, unites discovery and delivery with easy access to Purdue faculty experts in the semiconductor field, highly sought-after graduates prepared to work in the industry, and vast Purdue research resources. The park also offers convenient accessibility for workforce and semitruck traffic, with access to I-65 just minutes away.
This historic announcement is the next step in Purdue University’s persistent pursuit of semiconductor excellence as part of the Purdue Computes initiative. Recent announcements include these
- Purdue University Comprehensive Semiconductors and Microelectronics Program
- A strategic partnership with Dassault Systèmes to improve, accelerate and transform semiconductor workforce development
- European technology leader imec opens innovation hub at Purdue
- The nation’s first comprehensive Semiconductor Degrees Program
- Purdue continues to create unique lab-to-fab ecosystem for the state and country
- Green2Gold, a collaboration between Ivy Tech Community College and Purdue University to grow Indiana’s engineering workforce
What they’re saying
- “This decision by a world-renowned, best-in-class company represents a dramatic fulfillment of Purdue’s duty to serve the state as not only its premier academic institution but also its No. 1 economic asset. It’s also a gratifying validation of our Discovery Park District initiative to bring new opportunities to our students, faculty and Greater Lafayette neighbors. Today marks the Purdue ecosystem’s latest and greatest, but assuredly not its last, contribution to a more prosperous Indiana and a stronger America.” — Mitch Daniels, chairman of the board, Purdue Research Foundation
- “On behalf of my fellow trustees, we are pleased to welcome SK hynix Inc. to the Purdue Research Park. Their arrival will significantly strengthen Purdue University’s dual commitments to educating the next generation of workforce leaders in semiconductors and supporting the national security of our nation.” — Michael Berghoff, chair, Purdue Board of Trustees
- “The impact of SK hynix is more than the creation of high-paying careers for Hoosiers. Undergraduates will have opportunities for internships, co-op and full-time employment when they graduate. Graduate students and faculty will work closely with SK hynix researchers, not only on basic research, but also to accelerate the transition of research into pilot production and manufacturing. This is just the beginning. As other companies see what’s happening here in the heart of the heartland, they’ll come too, and a significant new cluster of semiconductor manufacturing and research will emerge.” — Mark Lundstrom, chief semiconductor officer, Purdue University
- “West Lafayette is thrilled to join our national efforts to bring the semiconductor industry to the United States through President Biden’s CHIPS and Science Act. This partnership will leverage Purdue University’s science and research expertise with SK hynix’s innovation in semiconductor technology. The impact on West Lafayette will enable us to continue to provide the high level of service our community expects and to increase our quality-of-life amenities for the region so we can attract and retain the excellent graduates of Purdue University. In addition, SK hynix’s global dedication to net zero carbon emissions by 2050, water process reduction and recycling, and zero-waste-to-landfill programs aligns with our community’s commitment to environmental stewardship. We are grateful for SK hynix’s investment and commitment to West Lafayette and for our partners Purdue University, Purdue Research Foundation, the city of Lafayette, Tippecanoe County and the Greater Lafayette region.” — Erin Easter, mayor of West Lafayette
- “The pandemic disruption has shown the reliance on semiconductors, with production concentrated in limited regions around the world. Greater Lafayette has worked continuously and cooperatively for years to position ourselves for an opportunity of this magnitude, and we look forward to the long-term economic impact this will have on our communities. The collaborative efforts between cities and county governments, Purdue University, the state of Indiana and Sen. Todd Young’s office is a testament to these efforts. Our joint investments in infrastructure, innovation, along with quality-of-life initiatives, have contributed to this venture becoming a reality. We look forward to working with and welcoming SK hynix to Greater Lafayette!” — Tony Roswarski, mayor of Lafayette
- “Ivy Tech, as Indiana’s largest postsecondary institution, is focused on building Indiana talent pipelines aligned to employers and emerging industries which strengthen Indiana’s economy. The microelectronics industry will play a key role in Indiana’s success, which is why we are pleased to work with SK hynix and Purdue to provide training, credentials and degrees designed for the semiconductor industry. SK hynix’s commitment to Indiana reinforces that we all win when we address complex issues through strong partnerships." — Sue Ellspermann, president, Ivy Tech Community College
- “Semiconductors and microelectronics are at the forefront of focus for Purdue Research Foundation. I am pleased to welcome SK hynix to Indiana and start the hard work of ensuring this is the best business decision that SK hynix has ever made.” — Brian Edelman, president, Purdue Research Foundation
- “The Alliances team is thrilled to welcome SK hynix to the Purdue ecosystem, and we look forward to empowering them to thrive here in Indiana with all the immense assets Purdue and Greater Lafayette offer. We look forward to forging a strong relationship with mutual value for SK hynix, Purdue Research Foundation and the broader Greater Lafayette community for many years to come.” — Gregory Deason, senior vice president of alliances and placemaking, Purdue Research Foundation
- “During my time at Purdue Research Foundation, we have consistently been successful in assisting our partners like Saab in developing complex builds well ahead of schedule and within budget. I look forward to building on our excellent track record with SK hynix to help them in creating a state-of-the-art facility which best meets their unique needs.” — Richard Michal, senior vice president of capital projects and facilities, Purdue Research Foundation
About SK hynix Inc.
SK hynix Inc., headquartered in Korea, is the world’s top-tier semiconductor supplier offering Dynamic Random Access Memory chips (“DRAM”), flash memory chips (“NAND flash”) and CMOS Image Sensors (“CIS”) for a wide range of distinguished customers globally. The Company’s shares are traded on the Korea Exchange, and the Global Depository shares are listed on the Luxembourg Stock Exchange. Further information about SK hynix is available at www.skhynix.com , news.skhynix.com .
About Purdue Research Foundation
Purdue Research Foundation is a private, nonprofit foundation created to advance the mission of Purdue University. Established in 1930, the foundation accepts gifts, administers trusts, funds scholarships and grants, acquires and sells property, protects and licenses Purdue's intellectual property, and supports creating Purdue-connected startups on behalf of Purdue. The foundation operates Purdue Innovates, which includes the Office of Technology Commercialization, Incubator and Ventures. The foundation manages the Purdue Research Park, Discovery Park District, Purdue Technology Centers and Purdue for Life Foundation.
For more information on licensing a Purdue innovation, contact the Office of Technology Commercialization at [email protected] . For more information about involvement and investment opportunities in startups based on a Purdue innovation, contact Purdue Innovates at [email protected] .
About Purdue University
Purdue University is a public research institution demonstrating excellence at scale. Ranked among top 10 public universities and with two colleges in the top four in the United States, Purdue discovers and disseminates knowledge with a quality and at a scale second to none. More than 105,000 students study at Purdue across modalities and locations, including nearly 50,000 in person on the West Lafayette campus. Committed to affordability and accessibility, Purdue’s main campus has frozen tuition 13 years in a row. See how Purdue never stops in the persistent pursuit of the next giant leap — including its first comprehensive urban campus in Indianapolis, the new Mitchell E. Daniels, Jr. School of Business, and Purdue Computes — at https://www.purdue.edu/president/strategic-initiatives .
Media contact:
Tim Doty, [email protected]
Note to journalists: Photo, b-roll and sound bites from this announcement will be available for media use on Google Drive .
Research News
Communication.
- OneCampus Portal
- Brightspace
- BoilerConnect
- Faculty and Staff
- Human Resources
- Colleges and Schools
Info for Staff
- Purdue Moves
- Board of Trustees
- University Senate
- Center for Healthy Living
- Information Technology
- Ethics & Compliance
- Campus Disruptions
Purdue University, 610 Purdue Mall, West Lafayette, IN 47907, (765) 494-4600
© 2015-24 Purdue University | An equal access/equal opportunity university | Copyright Complaints | Maintained by Office of Strategic Communications
Trouble with this page? Disability-related accessibility issue? Please contact News Service at [email protected] .
Chief of Staff to the Vice President for Research and Innovation
How to apply.
A cover letter is required for consideration for this position and should be attached as the first page of your resume. The cover letter should address your specific interest in the position and outline skills and experience that directly relate to this position.
As one of the nation's leading public research universities, discoveries and innovations led by the University of Michigan address emerging challenges, spur new technologies, improve quality of life, strengthen communities and create economic opportunities. The Office of the Vice President for Research (OVPR) works closely with faculty, staff and students from across the three U-M campuses to catalyze, support and safeguard research and creative practice in ways that serve the public and advance the university's vital mission.
This individual will serve as a key member of the OVPR Leadership Team.
The Chief of Staff reports to the Vice President for Research and Innovation and advises the Vice President for Research and Innovation and the leadership of the Office of the Vice President for Research.
The Chief of Staff keeps the Vice President for Research and Innovation apprised of significant issues, ensures various perspectives are presented accurately and objectively, and helps to identify solutions and effectively resolve issues.
The Chief of Staff maintains a constant interface with the VPR leadership team to ensure that key issues are proactively addressed.
Provides critical support to the Vice President for Research and Innovation in setting priorities, assisting with long-range planning, and coordinating the execution of strategies in support of the Office of the Vice President for Research. The Chief of Staff will coordinate some engagement activities with the VPR leadership team around specific strategic and operational matters including but not limited to, support in setting agendas for the VPR leadership team and/or senior leadership meeting discussions and action items resulting from each meeting and aids with appropriate follow-up.
Build and maintain mutually supportive relationships with all levels of management, staff, outside agencies and vendors, when necessary. Works to remove barriers that hamper inter-and intra-department communications. Additionally, the Chief of Staff works with the OVPR leadership in managing relationships with internal and external stakeholders. Coordinates and monitors assignments which must be accomplished in conjunction with other senior executives.
Represents the U-M Office of Vice President for Research across campus serving as a key member on committees, task forces, and councils. The Chief of Staff will manage the bi-directional flow of communication in and out of the Office of the Vice President for Research to ensure consistent and responsive message delivery to key University stakeholders.
Other responsibilities also include supporting an inclusive environment of teamwork and collaboration and maintaining familiarity with budgetary matters related to the Office of the Vice President for Research.
Generate and coordinate assignments, as needed. Work independently to complete assignments involving the appropriate internal or external contacts.
Develop data analysis and write reports for use in executive decision-making. Handle data, communication, and projects that are highly privileged and confidential.
Coordinate comprehensive projects and assignments that require coordination of several different offices and/or areas of the University including personnel/management reviews, and special studies.
Performs other related duties as assigned.
Required Qualifications*
Bachelor's degree
7-10 years of professional experience in higher education administration
Demonstrated ability to manage and supervise teams and projects on behalf of executive leadership
Outstanding writing and communication skills with demonstrated ability to communicate and synthesize complex technical topics
Desired Qualifications*
Master's degree
Experience in a research environment, research-related government agency, research-related business or related academic setting is preferred
Background Screening
The University of Michigan conducts background checks on all job candidates upon acceptance of a contingent offer and may use a third party administrator to conduct background checks. Background checks are performed in compliance with the Fair Credit Reporting Act.
Application Deadline
Job openings are posted for a minimum of seven calendar days. The review and selection process may begin as early as the eighth day after posting. This opening may be removed from posting boards and filled anytime after the minimum posting period has ended.
U-M EEO/AA Statement
The University of Michigan is an equal opportunity/affirmative action employer.
Prestigious cancer research institute has retracted 7 studies amid controversy over errors

Seven studies from researchers at the prestigious Dana-Farber Cancer Institute have been retracted over the last two months after a scientist blogger alleged that images used in them had been manipulated or duplicated.
The retractions are the latest development in a monthslong controversy around research at the Boston-based institute, which is a teaching affiliate of Harvard Medical School.
The issue came to light after Sholto David, a microbiologist and volunteer science sleuth based in Wales, published a scathing post on his blog in January, alleging errors and manipulations of images across dozens of papers produced primarily by Dana-Farber researchers . The institute acknowledged errors and subsequently announced that it had requested six studies to be retracted and asked for corrections in 31 more papers. Dana-Farber also said, however, that a review process for errors had been underway before David’s post.
Now, at least one more study has been retracted than Dana-Farber initially indicated, and David said he has discovered an additional 30 studies from authors affiliated with the institute that he believes contain errors or image manipulations and therefore deserve scrutiny.
The episode has imperiled the reputation of a major cancer research institute and raised questions about one high-profile researcher there, Kenneth Anderson, who is a senior author on six of the seven retracted studies.
Anderson is a professor of medicine at Harvard Medical School and the director of the Jerome Lipper Multiple Myeloma Center at Dana-Farber. He did not respond to multiple emails or voicemails requesting comment.
The retractions and new allegations add to a larger, ongoing debate in science about how to protect scientific integrity and reduce the incentives that could lead to misconduct or unintentional mistakes in research.
The Dana-Farber Cancer Institute has moved relatively swiftly to seek retractions and corrections.
“Dana-Farber is deeply committed to a culture of accountability and integrity, and as an academic research and clinical care organization we also prioritize transparency,” Dr. Barrett Rollins, the institute’s integrity research officer, said in a statement. “However, we are bound by federal regulations that apply to all academic medical centers funded by the National Institutes of Health among other federal agencies. Therefore, we cannot share details of internal review processes and will not comment on personnel issues.”
The retracted studies were originally published in two journals: One in the Journal of Immunology and six in Cancer Research. Six of the seven focused on multiple myeloma, a form of cancer that develops in plasma cells. Retraction notices indicate that Anderson agreed to the retractions of the papers he authored.
Elisabeth Bik, a microbiologist and longtime image sleuth, reviewed several of the papers’ retraction statements and scientific images for NBC News and said the errors were serious.
“The ones I’m looking at all have duplicated elements in the photos, where the photo itself has been manipulated,” she said, adding that these elements were “signs of misconduct.”
Dr. John Chute, who directs the division of hematology and cellular therapy at Cedars-Sinai Medical Center and has contributed to studies about multiple myeloma, said the papers were produced by pioneers in the field, including Anderson.
“These are people I admire and respect,” he said. “Those were all high-impact papers, meaning they’re highly read and highly cited. By definition, they have had a broad impact on the field.”
Chute said he did not know the authors personally but had followed their work for a long time.
“Those investigators are some of the leading people in the field of myeloma research and they have paved the way in terms of understanding our biology of the disease,” he said. “The papers they publish lead to all kinds of additional work in that direction. People follow those leads and industry pays attention to that stuff and drug development follows.”
The retractions offer additional evidence for what some science sleuths have been saying for years: The more you look for errors or image manipulation, the more you might find, even at the top levels of science.
Scientific images in papers are typically used to present evidence of an experiment’s results. Commonly, they show cells or mice; other types of images show key findings like western blots — a laboratory method that identifies proteins — or bands of separated DNA molecules in gels.
Science sleuths sometimes examine these images for irregular patterns that could indicate errors, duplications or manipulations. Some artificial intelligence companies are training computers to spot these kinds of problems, as well.
Duplicated images could be a sign of sloppy lab work or data practices. Manipulated images — in which a researcher has modified an image heavily with photo editing tools — could indicate that images have been exaggerated, enhanced or altered in an unethical way that could change how other scientists interpret a study’s findings or scientific meaning.
Top scientists at big research institutions often run sprawling laboratories with lots of junior scientists. Critics of science research and publishing systems allege that a lack of opportunities for young scientists, limited oversight and pressure to publish splashy papers that can advance careers could incentivize misconduct.
These critics, along with many science sleuths, allege that errors or sloppiness are too common , that research organizations and authors often ignore concerns when they’re identified, and that the path from complaint to correction is sluggish.
“When you look at the amount of retractions and poor peer review in research today, the question is, what has happened to the quality standards we used to think existed in research?” said Nick Steneck, an emeritus professor at the University of Michigan and an expert on science integrity.
David told NBC News that he had shared some, but not all, of his concerns about additional image issues with Dana-Farber. He added that he had not identified any problems in four of the seven studies that have been retracted.
“It’s good they’ve picked up stuff that wasn’t in the list,” he said.
NBC News requested an updated tally of retractions and corrections, but Ellen Berlin, a spokeswoman for Dana-Farber, declined to provide a new list. She said that the numbers could shift and that the institute did not have control over the form, format or timing of corrections.
“Any tally we give you today might be different tomorrow and will likely be different a week from now or a month from now,” Berlin said. “The point of sharing numbers with the public weeks ago was to make clear to the public that Dana-Farber had taken swift and decisive action with regard to the articles for which a Dana-Farber faculty member was primary author.”
She added that Dana-Farber was encouraging journals to correct the scientific record as promptly as possible.
Bik said it was unusual to see a highly regarded U.S. institution have multiple papers retracted.
“I don’t think I’ve seen many of those,” she said. “In this case, there was a lot of public attention to it and it seems like they’re responding very quickly. It’s unusual, but how it should be.”
Evan Bush is a science reporter for NBC News. He can be reached at [email protected].
- Skip to main content
- Keyboard shortcuts for audio player

- LISTEN & FOLLOW
- Apple Podcasts
- Google Podcasts
- Amazon Music
- Amazon Alexa
Your support helps make our show possible and unlocks access to our sponsor-free feed.
Watch your garden glow with new genetically modified bioluminescent petunias
Sasa Woodruff

A long exposure photo of Firefly petunias, which are genetically modified to produce their own light through bioluminescence Sasa Woodruff/Boise State Public Radio hide caption
A long exposure photo of Firefly petunias, which are genetically modified to produce their own light through bioluminescence
Keith Wood, Ph.D. spent most of his career in pharmaceutical research in molecular and chemical biology, using his work with bioluminescence to understand how molecules interacted with diseases. His work started as a graduate student when the team he was on inserted a firefly gene into a tobacco plant.
It was a small plant and couldn't sustain light without the addition of a substrate. It wasn't something a consumer would buy, but it was good for understanding pathways within an organism.
Now, about 40 years after that first plant, Wood and his company in Ketchum, Light Bio, are marketing a garden petunia with a twist: it glows in the dark.
View this post on Instagram A post shared by Alexandra L. Woodruff (@trowelandfork)
"People don't think about science as just bringing joy to our lives," Wood said, "We thought we could do something really special here. We could create a kind of decorative plant that was really just enjoyment, just bringing a kind of magic into our lives."

Scientist Keith Wood stands in his Ketchum home with a photo of a tobacco plant modified with a firefly gene Sasa Woodruff/Boise State Public Radio hide caption
Scientist Keith Wood stands in his Ketchum home with a photo of a tobacco plant modified with a firefly gene
The petunia with bright, white flowers looks like something you'd buy in spring at a garden nursery. But, when the lights are turned out, the petals slowly start lighting up with a greenish, white glow. The plant is always glowing, it's just our eyes that need to adjust to see the light. The newest buds are the brightest and punctuate the glowing flowers.
"That's why we call it the Firefly Petunia. Because these bright buds resemble fireflies sitting on top of the plant.," Wood explained.
And despite its name, this plant doesn't have any firefly genes, rather four genes from a bioluminescent mushroom and a fifth from a fungi.
"The first gene takes a metabolite and turns it into an intermediate," Wood explained, "The second gene takes the intermediate and turns it into the actual fuel for the bioluminescence. The third gene is what actually makes the light. And then the last gene takes the product from the light reaction and recycles it back to the starting point."
This cycle is self-sustaining, which means it shines brightly and doesn't need an extra chemical like the tobacco plant did to light up.
"The [firefly] gene was functional, but it didn't connect seamlessly into the natural metabolic processes," Wood said.
"You've got glow, but it was a weak glow. Not satisfying at all."
Petunia approval paperwork
It took about 10 years to go from development to approval from the U.S. Department of Agriculture last fall.
The plants went on sale online in February and the first ones were shipped out this week.
Diane Blazek, the executive director of the National Garden Bureau, an educational nonprofit, says customers are always looking for the next new plant and petunias are a guaranteed bestseller.
"Grandma grew petunias, but oh, look, now I've got a petunia that glows in the dark. So, this is really cool," Blazek said.

The Firefly Petunia emanates light because it's been modified with genes from a bioluminescent mushroom Sasa Woodruff/Boise State Public Radio hide caption
The Firefly Petunia emanates light because it's been modified with genes from a bioluminescent mushroom
She doesn't think that the fact that it's genetically modified will affect customers buying it because there's a precedent.
Seven years ago, an orange petunia modified with a maize gene showed up in gardens and nurseries in Europe and the U.S. The plant was never supposed to leave a closed lab but somehow ended up in lots of gardens. Regulators eventually asked people to destroy the plants and seeds.
"Overwhelmingly, the response was, wait a minute, it's a petunia. We're not eating it. The orange gene came from maize. Why? Why can't we plant this?" Blazek remembered.
Eventually, regulators approved the plants in the U.S.
Chris Beytes, at Ball Publishing, who oversees several horticulture publications, said the Firefly Petunia could open up gardening to new customers.
"If you buy your first plant because it glows in the dark or it's dyed pink, your second and third and 100th plant may be the traditional stuff. You never know," Beytes said. "Anything that creates excitement around flowers and plants. I'm all for it."
The Firefly Petunia may not have practical implications for things like drug advances or crop production, but for Wood this petunia is transcendent.
"There's something magical about seeing this living presence, this glowing vitality coming from a living plant that in person gives a kind of magical experience that you just can't see in a photograph.
And this summer, that magic could be sitting on the patio watching your garden glow from the light of a petunia.
Read our research on: Gun Policy | International Conflict | Election 2024
Regions & Countries
Changing partisan coalitions in a politically divided nation, party identification among registered voters, 1994-2023.
Pew Research Center conducted this analysis to explore partisan identification among U.S. registered voters across major demographic groups and how voters’ partisan affiliation has shifted over time. It also explores the changing composition of voters overall and the partisan coalitions.
For this analysis, we used annual totals of data from Pew Research Center telephone surveys (1994-2018) and online surveys (2019-2023) among registered voters. All telephone survey data was adjusted to account for differences in how people respond to surveys on the telephone compared with online surveys (refer to Appendix A for details).
All online survey data is from the Center’s nationally representative American Trends Panel . The surveys were conducted in both English and Spanish. Each survey is weighted to be representative of the U.S. adult population by gender, age, education, race and ethnicity and other categories. Read more about the ATP’s methodology , as well as how Pew Research Center measures many of the demographic categories used in this report .
The contours of the 2024 political landscape are the result of long-standing patterns of partisanship, combined with the profound demographic changes that have reshaped the United States over the past three decades.
Many of the factors long associated with voters’ partisanship remain firmly in place. For decades, gender, race and ethnicity, and religious affiliation have been important dividing lines in politics. This continues to be the case today.
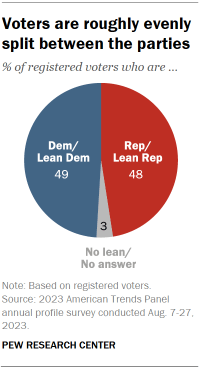
Yet there also have been profound changes – in some cases as a result of demographic change, in others because of dramatic shifts in the partisan allegiances of key groups.
The combined effects of change and continuity have left the country’s two major parties at virtual parity: About half of registered voters (49%) identify as Democrats or lean toward the Democratic Party, while 48% identify as Republicans or lean Republican.
In recent decades, neither party has had a sizable advantage, but the Democratic Party has lost the edge it maintained from 2017 to 2021. (Explore this further in Chapter 1 . )
Pew Research Center’s comprehensive analysis of party identification among registered voters – based on hundreds of thousands of interviews conducted over the past three decades – tracks the changes in the country and the parties since 1994. Among the major findings:
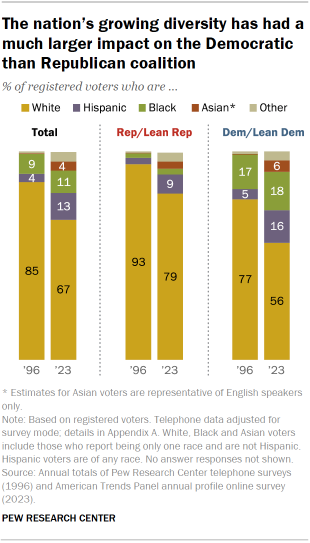
The partisan coalitions are increasingly different. Both parties are more racially and ethnically diverse than in the past. However, this has had a far greater impact on the composition of the Democratic Party than the Republican Party.
The share of voters who are Hispanic has roughly tripled since the mid-1990s; the share who are Asian has increased sixfold over the same period. Today, 44% of Democratic and Democratic-leaning voters are Hispanic, Black, Asian, another race or multiracial, compared with 20% of Republicans and Republican leaners. However, the Democratic Party’s advantages among Black and Hispanic voters, in particular, have narrowed somewhat in recent years. (Explore this further in Chapter 8 .)
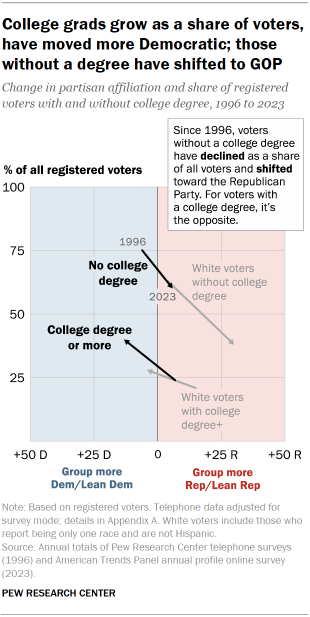
Education and partisanship: The share of voters with a four-year bachelor’s degree keeps increasing, reaching 40% in 2023. And the gap in partisanship between voters with and without a college degree continues to grow, especially among White voters. More than six-in-ten White voters who do not have a four-year degree (63%) associate with the Republican Party, which is up substantially over the past 15 years. White college graduates are closely divided; this was not the case in the 1990s and early 2000s, when they mostly aligned with the GOP. (Explore this further in Chapter 2 .)
Beyond the gender gap: By a modest margin, women voters continue to align with the Democratic Party (by 51% to 44%), while nearly the reverse is true among men (52% align with the Republican Party, 46% with the Democratic Party). The gender gap is about as wide among married men and women. The gap is wider among men and women who have never married; while both groups are majority Democratic, 37% of never-married men identify as Republicans or lean toward the GOP, compared with 24% of never-married women. (Explore this further in Chapter 3 .)
A divide between old and young: Today, each younger age cohort is somewhat more Democratic-oriented than the one before it. The youngest voters (those ages 18 to 24) align with the Democrats by nearly two-to-one (66% to 34% Republican or lean GOP); majorities of older voters (those in their mid-60s and older) identify as Republicans or lean Republican. While there have been wide age divides in American politics over the last two decades, this wasn’t always the case; in the 1990s there were only very modest age differences in partisanship. (Explore this further in Chapter 4 .)
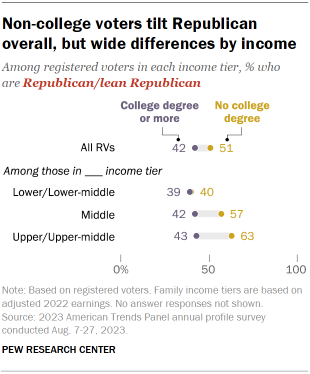
Education and family income: Voters without a college degree differ substantially by income in their party affiliation. Those with middle, upper-middle and upper family incomes tend to align with the GOP. A majority with lower and lower-middle incomes identify as Democrats or lean Democratic. There are no meaningful differences in partisanship among voters with at least a four-year bachelor’s degree; across income categories, majorities of college graduate voters align with the Democratic Party. (Explore this further in Chapter 6 .)
Rural voters move toward the GOP, while the suburbs remain divided: In 2008, when Barack Obama sought his first term as president, voters in rural counties were evenly split in their partisan loyalties. Today, Republicans hold a 25 percentage point advantage among rural residents (60% to 35%). There has been less change among voters in urban counties, who are mostly Democratic by a nearly identical margin (60% to 37%). The suburbs – perennially a political battleground – remain about evenly divided. (Explore this further in Chapter 7 . )
Growing differences among religious groups: Mirroring movement in the population overall, the share of voters who are religiously unaffiliated has grown dramatically over the past 15 years. These voters, who have long aligned with the Democratic Party, have become even more Democratic over time: Today 70% identify as Democrats or lean Democratic. In contrast, Republicans have made gains among several groups of religiously affiliated voters, particularly White Catholics and White evangelical Protestants. White evangelical Protestants now align with the Republican Party by about a 70-point margin (85% to 14%). (Explore this further in Chapter 5 .)
What this report tells us – and what it doesn’t
In most cases, the partisan allegiances of voters do not change a great deal from year to year. Yet as this study shows, the long-term shifts in party identification are substantial and say a great deal about how the country – and its political parties – have changed since the 1990s.

The steadily growing alignment between demographics and partisanship reveals an important aspect of steadily growing partisan polarization. Republicans and Democrats do not just hold different beliefs and opinions about major issues , they are much more different racially, ethnically, geographically and in educational attainment than they used to be.
Yet over this period, there have been only modest shifts in overall partisan identification. Voters remain evenly divided, even as the two parties have grown further apart. The continuing close division in partisan identification among voters is consistent with the relatively narrow margins in the popular votes in most national elections over the past three decades.
Partisan identification provides a broad portrait of voters’ affinities and loyalties. But while it is indicative of voters’ preferences, it does not perfectly predict how people intend to vote in elections, or whether they will vote. In the coming months, Pew Research Center will release reports analyzing voters’ preferences in the presidential election, their engagement with the election and the factors behind candidate support.
Next year, we will release a detailed study of the 2024 election, based on validated voters from the Center’s American Trends Panel. It will examine the demographic composition and vote choices of the 2024 electorate and will provide comparisons to the 2020 and 2016 validated voter studies.
The partisan identification study is based on annual totals from surveys conducted on the Center’s American Trends Panel from 2019 to 2023 and telephone surveys conducted from 1994 to 2018. The survey data was adjusted to account for differences in how the surveys were conducted. For more information, refer to Appendix A .
Previous Pew Research Center analyses of voters’ party identification relied on telephone survey data. This report, for the first time, combines data collected in telephone surveys with data from online surveys conducted on the Center’s nationally representative American Trends Panel.
Directly comparing answers from online and telephone surveys is complex because there are differences in how questions are asked of respondents and in how respondents answer those questions. Together these differences are known as “mode effects.”
As a result of mode effects, it was necessary to adjust telephone trends for leaned party identification in order to allow for direct comparisons over time.
In this report, telephone survey data from 1994 to 2018 is adjusted to align it with online survey responses. In 2014, Pew Research Center randomly assigned respondents to answer a survey by telephone or online. The party identification data from this survey was used to calculate an adjustment for differences between survey mode, which is applied to all telephone survey data in this report.
Please refer to Appendix A for more details.
Sign up for our Politics newsletter
Sent weekly on Wednesday
Report Materials
Table of contents, behind biden’s 2020 victory, a voter data resource: detailed demographic tables about verified voters in 2016, 2018, what the 2020 electorate looks like by party, race and ethnicity, age, education and religion, interactive map: the changing racial and ethnic makeup of the u.s. electorate, in changing u.s. electorate, race and education remain stark dividing lines, most popular.
About Pew Research Center Pew Research Center is a nonpartisan fact tank that informs the public about the issues, attitudes and trends shaping the world. It conducts public opinion polling, demographic research, media content analysis and other empirical social science research. Pew Research Center does not take policy positions. It is a subsidiary of The Pew Charitable Trusts .

IMAGES
VIDEO
COMMENTS
Clients receive 24/7 access to proven management and technology research, expert advice, benchmarks, diagnostics and more. Fill out the form to connect with a representative and learn more. Or give us a call . jsbacContact jsbacContact 8 a.m. - 7 p.m. ET 8 a.m. - 5 p.m. GMT Monday through Friday
IT must adopt an Exponential IT mindset and define its own transformation journey to evolve into organization leaders in a rapidly changing technology landscape. This blueprint will help IT leaders build a roadmap of Exponential IT initiatives using Info-Tech's actionable IT transformation framework. SECURITY.
New research on information technology from Harvard Business School faculty on issues including the HealthCare.gov fiasco, online privacy concerns, and the civic benefits of technologies that utilize citizen-created data. Page 1 of 59 Results →. 12 Mar 2024. HBS Case.
Information technology articles from across Nature Portfolio. Information technology is the design and implementation of computer networks for data processing and communication. This includes ...
The Journal of Information Technology (JIT) is a top-ranked journal, focused on new research addressing information, management, and communications technologies as applied to the digital worlds of business, government and non-governmental enterprises. View full journal description. This journal is a member of the Committee on Publication Ethics ...
Microsoft News Center | Feb 13, 2024. View more news and awards. Explore research at Microsoft, a site featuring the impact of research along with publications, products, downloads, and research careers.
Plan in real time - Let AI run ongoing resource allocation. Trust, but verify - Enable true accountability. Learn More. Visit our IT Cost Optimization Center. Over 100 analysts waiting to take your call right now: 1-519-432-3550 x2019. Info-Tech's strategic and actionable principles to enable IT leaders to extract the value from ...
Computer science is the study and development of the protocols required for automated processing and manipulation of data. This includes, for example, creating algorithms for efficiently searching ...
4. Expanded trust boundaries Key tech trends. It was estimated that almost 100 percent of biometrics-capable devices (such as smartphones) will be using biometrics for transactions by 2022. 22 "Usage of biometric technology in transactions with mobile devices worldwide 2016-2022", Statista Research Department, June 13, 2022. The effectiveness of these technologies has advanced ...
One research paper started it all. The research we do today becomes the Google of the future. Google itself began with a research paper, published in 1998, and was the foundation of Google Search. Our ongoing research over the past 25 years has transformed not only the company, but how people are able to interact with the world and its information.
Overview. Advancing the state-of-the-art in IT in such applications as cyber security and biometrics, NIST accelerates the development and deployment of systems that are reliable, usable, interoperable, and secure; advances measurement science through innovations in mathematics, statistics, and computer science; and conducts research to develop ...
In the world of technology, research is a compass that helps us navigate its convoluted evolutions. For instance, Information Technology (IT) research has been conducted in computer science, software engineering, data analytics, and cybersecurity. IT research involves systematic inquiry to advance knowledge, problem-solving, and innovation.
SIGITE is a society of IT educators who organize the Research in Information Technology (RIIT) conference to showcase and promote IT research. The conference aims to identify and support IT research that is unique, hands-on, and industry-driven, and to provide an online repository for IT researchers to share their work.
Access 160+ million publications and connect with 25+ million researchers. Join for free and gain visibility by uploading your research.
130 Information Technology Research Topics And Quick Writing Prompts. The field of information technology is one of the most recent developments of the 21st century. Scholars argue that we are living in a technological age. Despite this buzz, however, many students still find it challenging to compose an information technology research topic.
Research IT will not be holding our regular office hours during the week of Spring Break, 3/25 - 3/29. Please get in touch with us at [email protected] for any help in the meantime. Savio HPC services are back online: Tues, 3/26. The Savio HPC services are back online. Taking this opportunity, we have another exciting news to share.
Enterprises are adopting GenAI as well. In fact, 85% of enterprises believe that investment in GenAI technology in the next 24 months is important or critical (from the ISG 2023 Future Workplace Study). And the recently completed ISG Buyer Behavior research on AI shows enterprises are experiencing positive outcomes from their AI investments.
The building will also accommodate 50 computing research groups, which correspond to the number of new faculty the college is hiring — 25 in core computing positions and 25 in shared positions with departments at MIT. These groups bring together a mix of new and existing teams in related research areas spanning floors four through seven of ...
Abstractspiepr Abs1. Every day people do research as they gather information to learn about something of interest. In the scientific world, however, research means something different than simply gathering information. Scientific research is characterized by its careful planning and observing, by its relentless efforts to understand and explain ...
21. Honeybees and the Internet. Honeybee intelligence can be used to improve the speed and efficiency of Internet servers by up to 25%, according to Georgia Institute of Technology researchers ...
Research is defined as a meticulous and systematic inquiry process designed to explore and unravel specific subjects or issues with precision. This methodical approach encompasses the thorough collection, rigorous analysis, and insightful interpretation of information, aiming to delve deep into the nuances of a chosen field of study.
Research is the careful consideration of study regarding a particular concern or research problem using scientific methods. According to the American sociologist Earl Robert Babbie, "research is a systematic inquiry to describe, explain, predict, and control the observed phenomenon. It involves inductive and deductive methods.".
Research IT is now part of a bigger and unified Research Technology team led by Dr. Todd Ferris. Research IT is renamed to Research Technology Engineering Services. The REDCap team, previously part of Research IT, is now part of Research Technology Application Solutions. The Research Technology team also includes Data Services (fka Research ...
Free Online Educational Resources. CT Learning Hub is your destination for universal access to curated tools and resources anytime, anywhere. The CT Learning Hub puts resources in the hands of CT families, students and educators. The Hub is a free and interactive web page of digital resources to support online and offline learning.
NAWI is a research program and public-private partnership supported by the United States Department of Energy in partnership with the California Department of Water Resources and the California State Water Resources Control Board. NAWI brings together a world-class team of industry and academic partners to examine the critical technical ...
SK hynix Inc. announced Wednesday (April 3) that it plans to invest close to $4 billion to build an advanced packaging fabrication and RD facility for AI products in the Purdue Research Park. The development of a critical link in the U.S. semiconductor supply chain in West Lafayette marks a giant leap forward in the industry and the state.
The Office of the Vice President for Research (OVPR) works closely with faculty, staff and students from across the three U-M campuses to catalyze, support and safeguard research and creative practice in ways that serve the public and advance the university's vital mission. This individual will serve as a key member of the OVPR Leadership Team.
Seven studies from researchers at the prestigious Dana-Farber Cancer Institute have been retracted over the last two months after a scientist blogger alleged that images used in them had been ...
Research into new pharmaceuticals has produced an unanticipated by-product: Petunias that glow in the dark
Pew Research Center's comprehensive analysis of party identification among registered voters - based on hundreds of thousands of interviews conducted over the past three decades - tracks the changes in the country and the parties since 1994. Among the major findings: The partisan coalitions are increasingly different.