- skip navigation
- Data Protection
- Accessibility
- search search
- Campusplan Campus Map

KIT Graduate School Cyber Security

Welcome to the KIT Graduate School Cyber Security
In virtually all areas of information technology today, cyber security is of the utmost importance. In a highly digitalized world with highly digitalized economies, protection against increasingly dangerous cyber attacks is crucial. In recent years, the news have been littered with reports on attacks on individuals, businesses, hospitals, local administrations, government institutions, and critical infrastructures. These events illustrate that demand for cutting-edge expertise in cyber security is at an all-time high.
The KIT Graduate School Cyber Security provides doctoral researchers with state-of-the-art technical, scientific, and interdisciplinary skills, enabling them to respond effectively to present and future security challenges. As a nexus in a multifaceted field, the school brings together the different security disciplines at KIT. It organizes regular networking events and serves as a platform for interdisciplinary work and the exchange of ideas among doctoral, post-doctoral, and senior researchers.

On 18 June 2024, the next Cyber Sec Seminar slot will be filled by a hands-on workshop on voice and speaking for early career researchers at Triangel Studio.

Two CyberSec members, Patricia Guerra-Balboa and Àlex Miranda-Pascual, won the 2023 Community Congress Poster Award with their poster titled "Differentially Private Trajectory Data". We congratulate them on this great success!
- Tools and Resources
- Customer Services
- Conflict Studies
- Development
- Environment
- Foreign Policy
- Human Rights
- International Law
- Organization
- International Relations Theory
- Political Communication
- Political Economy
- Political Geography
- Political Sociology
- Politics and Sexuality and Gender
- Qualitative Political Methodology
- Quantitative Political Methodology
- Security Studies
- Share This Facebook LinkedIn Twitter
Article contents
Critical theory, security, and emancipation.
- K.M. Fierke K.M. Fierke School of International Relations, University of St Andrews
- https://doi.org/10.1093/acrefore/9780190846626.013.138
- Published in print: 01 March 2010
- Published online: 30 November 2017
Critical theory in International Relations originated from the Marxist tradition which, during the mid- to late Cold War, formed the basis of dependency and world systems theory. In the years before and after the Cold War, critical theory became part of a larger post-positivist challenge to the discipline and to the development of critical security studies. At the heart of contestation within the broader arena of critical security is the concept of emancipation, developed by members of the Frankfurt School such as Theodor W. Adorno and Max Horkheimer. Several key debates have been at the center of critical security studies relating to the construction of threats, identity and difference, human security, and emancipation. In particular, critical security analysts have addressed the question of how, given the range of threats or risks that exist in the world, some threats come to have priority over others and become the focus of discourses of security. Also, some scholars have disputed the idea that identity is dependent on difference. The concept of human security shifts attention away from states to individuals, emphasizing human rights, safety from violence, and sustainable development. In the case of emancipation, critical theorists have expressed concern that the concept is too closely linked with modernity, meta-narratives, especially Marxism and liberalism, and the Enlightenment belief that humanity is progressing toward a more perfect future. What is needed is not to avoid emancipation per se, but to pay close attention to its underlying assumptions.
- critical theory
- Frankfurt School
- critical security studies
- emancipation
- human security
Introduction
Critical theory in International Relations can mean several things. Critical theory refers to a body of thought growing out of the Marxist tradition, which, during the mid- to late Cold War informed dependency and world systems theory. In the decade prior to and following the end of the Cold War, critical theory, informed by Gramsci and the Frankfurt School, both of which have a Marxist lineage, became part of a larger post-positivist challenge to the discipline and to the development of critical security studies. In this context, the word critical was also used in relation to a much broader array of approaches, including postmodern, feminist, and postcolonial accounts. At the heart of this widespread critique was a concern for those outside established structures of power, who had been excluded from accounts of international relations, or, more specifically, discussions of security. In this respect, the attempt to dismantle the dominant state and Eurocentric assumptions of international relations and security studies was part of an attempt to allow a space for the voices of the marginalized and the suffering to be heard within a discipline and a subfield that had prioritized questions relating to the threat and use of force by states. For critical theory, and critical security studies as its offshoot, theory and practice are closely intertwined. The theorist does not observe the world objectively, but rather is always situated in a historical context and responding to a set of historically specific circumstances. In this respect, the critical developments within international relations have to be understood against the backdrop of critical social movements in the world. Emancipation is a specific concept, developed by members of the Frankfurt School, such as Adorno and Horkheimer, which has been at the heart of contestation within the broader arena of critical security studies.
Classical and Older Literatures
The discussion of classical literatures of critical theory has to be distinguished from the discussion of classical literatures of security in so far as the two did not merge until the 1990s, with the development of critical security studies. Up to this point in time, development, a central concern of critical theory, and security, largely informed by realist thought, were separate areas of study and practice. Marxist and neo-Marxist international relations theories, which emerged during the Cold War, focused their critique primarily on dominant realist and liberal views of the international system. Like the Marxist tradition from which they derived, critical theories emphasized questions of hierarchy. Development studies addressed questions of inequality and poverty, while security studies focused on conflict and war. The latter was, during the first two decades of the Cold War, more often referred to as strategic or national security studies.
The critical Marxist literature presented a critique of the more liberal model of development, which assumed that societies in the South could replicate social and economic changes experienced by the North since the eighteenth century . The liberal model located the lack of development within individual states, ignoring the embeddedness of these states in historical, more global relationships. By contrast, the critical Marxist literature was premised on the idea that globalization is not a new phenomenon. The underdevelopment of the South went hand in hand with the development of the North in a capitalist world economy. Critics of European imperialism in the early part of the twentieth century , and not least Lenin ( 1939 / 1988 ), argued that capitalism was fueled by the need to expand in search of profit. Imperialism was a manifestation of this global expansion in pursuit of wealth. In the period following decolonization, these arguments were adapted to explain less formal structures of control. Immanuel Wallerstein’s ( 1974 ) world systems theory provided a framework for understanding the relationship between the development of the industrial core, the underdevelopment of a periphery, which provided raw materials, and a semi-periphery, which produced luxury goods and provided a buffer against revolutionary transformation. Dependency theorists further examined how links between elites in North and South reproduced a relationship of Southern dependence and underdevelopment (Cardoso and Faletto 1979 ).
From the 1950s to the 1970s, a critical discourse of development became popular in areas of the periphery that had been historically exploited. This critical framework, like critical theory, placed the backwardness of the economies of the former colonies in a larger global context, in which the formal imperial relationship had, since decolonization, been replaced by less formal processes of exploitation. For instance, Northern companies purchased raw materials and labor power in the South below their true cost. Cheap labor and cheap Southern raw materials were transformed into manufactured goods in the North. In this critical discourse, the exploitative relationship was simply a new expression of the hierarchy that had constituted the capitalist world economy for centuries. It wasn’t that the South was undeveloped, but rather that it had been deliberately underdeveloped within a global relationship. Poverty was a direct consequence of how wealth was produced. This provided a global structural argument about the cause of poverty and legitimized practices on the part of Southern governments to intervene in the economy in order to lead the development process. At the time, many third world states joined together in calling for a New International Economic Order, or a reorganization of the global economy so that they would no longer be disadvantaged.
Critical Theory and Security
The 1980s saw the emergence of a neoliberal free market agenda, which pushed the critical arguments about underdevelopment into the background. At the same time, other offshoots of critical theory began to assume a place within International Relations, a development which was not unrelated to events in the world of Cold War security relations. US President Reagan’s rhetoric about limited nuclear war and demonstration shots over Europe revived fears of nuclear war, which spawned a political debate over the meaning of security, particularly in Europe. While NATO argued that nuclear weapons had blessed Europe with an unprecedented period of peace, peace and disarmament movements mobilized around arguments that the increasing likelihood of nuclear war made these weapons a source of insecurity rather than security. Reagan’s early policy, in the name of nuclear deterrence and mutually assured destruction, was one inspiration for this fear. However, against the background of these debates, in 1983 , he introduced the Strategic Defense Initiative (SDI), or “Star Wars,” followed, in subsequent years, by arguments that SDI would replace deterrence and make the “world sleep more secure.” After Soviet Premier Gorbachev came to power in 1985 , he also entered into the debate, arguing the need for New Thinking, to conceive of security in political terms, and to emphasize the importance of common security. Against this background, the two superpowers began to engage in a peace competition that led to face-to-face talks in Reykjavik and discussions, for the first time during the Cold War, of disarmament and not merely arms control. In 1989 , “velvet” revolutions shook Eastern Europe, and the Soviet Union watched as the communist regimes were dissolved, not by force but by popular demand.
The Cold War was declared over with the dismantling of the Berlin Wall, well before the dissolution of the Soviet Union in 1991 . Almost no one, and least of all the practitioners of security studies, saw the end of the Cold War coming. They were shocked both by the rapid course of events and by the fact that these changes did not fit with the realist assumptions of security studies. Not disarmament, nor velvet revolutions, nor a state relinquishing its sovereignty could be explained within a framework that defined security in terms of the threat and use of force by states. The sudden lack of a security problem, in addition to the apparent declining utility of military force, stimulated reflection and critical evaluation within the academy on the meaning of security.
These dramatic changes in the political world added momentum to the critique of international relations theory more generally, and security studies more specifically, which had been under way in the academy. In the post–World War II period, security studies, as well as conflict analysis, had been preoccupied with the attempt to develop the scientific status of the field, with a focus on deductive formal modeling, particularly of nuclear strategy (see, for instance, Schelling 1966 ), or the creation of empirical databases, such as the Correlates of War project, respectively. This emphasis on science in the academy, or, in the political world, on force structure, planning, and other technical problems related to nuclear and conventional weapons (Crawford 1991 :289), went hand in hand with a distancing from the more political aspects of security. This demise of the political was also evident in the prominence of neo-realism by the 1980s. Neo-realists, such as Waltz ( 1979 ), criticized earlier realisms for being reductionist, that is, for reducing the problem of insecurity to the level of the individual or the state instead of the system of anarchy. In the search for elegance and parsimony, neo-realism removed any traces of the human, the political, or the cultural from international relations and provided instead a general theory of international relations, and a set of categories for formulating causal hypotheses that could then be tested against the world.
While the preoccupation with force structures, neo-realism, and social science created distance from the politics of security, this was also the point at which it began to be reintroduced. The period leading up to the end of the Cold War gave rise to a more fundamental attack on the scientific pretensions of the field, which was related to a larger Third Debate between positivists and post-positivists in international relations theory. One early expression of this emerging debate was Robert Cox’s ( 1981 ) distinction between problem solving and critical theory, which questioned the politics of power that underpins dominant theories. Cox argued that problem solving theory takes the world as it is, and attempts to find solutions to problems within it; critical theory, by contrast, raises questions about the historical location of both the theorist and his or her theory. As he famously stated, “Theory is always for some one and for some purpose” ( 1981 :128). Around the same time, Barry Buzan ( 1983/1991 ) introduced the idea that security is an “essentially contested concept.” Somewhat later, post-structuralists, such as Richard Ashley ( 1984 ) and R.B.J. Walker ( 1987 ) exposed the absence of the political in international theory, the scientific pretensions of neorealism and the disciplining effect of the discourse of sovereignty. Constructivists, such as Nicholas Onuf ( 1989 ) and Alexander Wendt ( 1992 ) questioned the static view of anarchy, arguing that the world of international politics is not given but always in the process of being made. Analysts of gender, such as Cynthia Enloe ( 1989 ), Ann Tickner ( 1993 ), and Spike Peterson ( 1992 ), began to uncover the gendered assumptions embedded in the theories, concepts, and practices of international security. The application of security to a range of new and different threats, and the analysis of how threats are constructed, gave rise to a burgeoning literature on critical security studies.
Critical analysts of security were often accused of lacking either empirical pretensions or ability. Yet security studies had been plagued by this problem from the beginning. As Nye and Lynne-Jones ( 1988 :13) pointed out: “In the fortunate absence of empirical data on nuclear exchanges, the field [of security studies] encourages non-empirical analyses.” Given the dramatic changes in international politics, the questions raised by critical security studies, and the attempts to develop new approaches and answers, arguably were more in tune with a changing world than their counterparts in the mainstream. As Krause and Williams ( 1997 ) document, critical security studies gave rise to a large number of studies within a fairly short period of time. The main problem was that these scholars did not define “empirical” in a way that fits with the research program of the mainstream. The difference regards a question of how scholars might know the world they are analyzing.
While rationalists treat the identities of actors – as self-interest maximizers – as given, critical analysts argued that identities, threats, and interests are constructed in historically specific circumstances. The shift to an understanding of security as a social and political construction expands the potential for formulating questions relating specifically to processes of change, including how enemies transform their relationship into one of friendship, how threats are defined and how the use of force is constructed. These questions were more empirically relevant to the changing contexts of the post–Cold War world than general theory that assumes the sameness of security across time.
Changing Debates
Critical security studies is distinguished from a longer tradition of security studies by the adoption of a critical approach. However, the meaning of critical has itself been at the heart of the evolving debate. Since Cox formulated the distinction between critical and problem solving theory in 1981 , critical theorists, such as Ken Booth ( 1991 ; 2005 ) and Richard Wyn Jones ( 1999 ) have identified critical security studies (CSS) with Marxist traditions of critical theory, such as the Frankfurt School or Gramsci. Keith Krause and Michael Williams ( 1997 ) have argued that CSS is a useful way to categorize a range of approaches that have challenged the narrow metatheoretical assumptions of traditional security studies. Reinforcing the multiplicity of critical approaches, Fierke ( 2007 ) analyzed a range of concepts and debates that have defined critical security studies, and their relevance to real world problems. While the Copenhagen School does not claim to be critical, its important work on the securitization of threats (Buzan et al. 1998 ) or discourse analysis (Hansen 2006 ), has an important place in this literature. Critical security studies has grown in leaps and bounds over the last decade, and the arguments are often complex, drawing on a range of philosophical traditions, including, in addition to the Frankfurt School and Gramsci, Wittgenstein, Schmitt, Bourdieu, Foucault, and Derrida. The following explores a few key debates that have been at the center of critical security studies relating to the construction of threats, identity and difference, human security, and emancipation.
The Construction of Threats
Traditional security studies asked a question about how to respond to objective threats. Critical security analysts have begun with a different question about how, given the range of threats or risks that exist in the world, from the destruction of the environment to nuclear weapons to terrorism or human rights, some threats come to have priority over others and become the focus of discourses of security. The question can be asked more broadly in terms of how specific objects or phenomena come to be constituted as one type or another, that is, as “threats” (Wæver 1995 ), “crises” (Weldes 1996 ), “problems” (Dalby 2002 ) or “risks” (Beck 2003 ). These ascriptions of meaning are not always self-evident and any one has consequences for how actions or policy responses are constituted. Critics often confuse the issue by assuming that social construction of any of these is equivalent to fabrication, that is, if threats are constructed they don’t really exist. However, to call a threat a social construction is not, for instance, to deny that nuclear weapons exist or that they can maim or kill millions. The question, as posed by Weldes et al. ( 1999 :12) is rather one of “how one gets from here to such widely shared propositions as these: that the U.S. is threatened by Russian, but not British nuclear weapons; that Third World states are more likely to use nuclear weapons than Western countries; that Iraq’s nuclear potential is more threatening than the U.S. nuclear arsenal; and the U.S. is safer with nuclear weapons than without them.” The focus is the process by which objects embedded in one set of relationships are given meaning as threatening, while in another they are understood to be benign.
Conventional approaches to security start with an objective threat, which is assumed to exist independent of the routines, procedures, discourses and knowledge brought to bear by security agencies (Huysmans et al. 2006 :44). More critical approaches emphasize that threats are a product of a politics of representation. Far from being a purely external phenomenon, to which security agencies merely react, a potential threat is transformed into a security question through the active intervention of security agencies. Measurements of the scope and seriousness of threats are shaped by social, cultural, and political processes that produce some phenomena as “security” threats while largely ignoring others. In the process of reification, a human-made object or situation comes to be understood as a factual given that exists externally and independently of the agencies that produced it. It is not that weapons or threats of one kind or another have been made up but rather that the meaning attached to them, and the subsequent practice, has been molded in discourses. In this way, the actors and insecurities taken for granted in conventional security studies are called into question, thereby denaturalizing the state and its insecurities, demonstrating how both are culturally produced (Weldes et al. 1999 :10).
Critical scholars of security (Campbell 1998 ; Weldes et al. 1999 ; Huysmans et al. 2006 ) focus on the background assumptions and discourses belonging to a culture from which threats are defined. Their intent is to denaturalize what has come to be assumed in order to open a space for alternatives. The Copenhagen School has distinguished itself from the broader category of critical security studies, which it identifies with critical theorists and post-structuralists. While the latter through a process of denaturalization attempt to show that change is possible, the Copenhagen School emphasizes that social constructions often become sedimented and relatively stable practices. Thus the task is not only to criticize this sedimentation but also to understand how the dynamics of security work and thus to change them (Buzan et al. 1998 :35). The Copenhagen School brings greater nuance to the constructivist argument that security is not an objective condition but an outcome of a specific kind of social process, an argument which tends to grow out of a critique of the realist focus on state security. Ole Wæver ( 1995 ) embraces the latter but for a different reason. Security, he argues, is a concept with a history and connotations that can’t be escaped. The core of this concept is defense of the state. The alternative to denaturalizing related discourses of security, as is characteristic of critical security studies, is to take the realist concept seriously and to examine its dynamics. Broadening the concept of security raises an unanswerable question of where to stop, that is, security potentially relates to everything that is potentially threatened. The alternative is to examine how security is used , that is, to examine it as a field of practices and how it typically works.
Security is typically about survival and about an existential threat to a particular object, which legitimizes the use of extraordinary measures. It opens the way for the state to justify the taking of special powers to handle the threat. The problem of security arises from an emergency condition, which establishes the right to use whatever means are necessary to block a threatening development. In and of itself, there is nothing in this depiction of security that is contrary to the realist picture, which focuses on the state; rather, it represents how security typically works for states. The concept of securitization highlights the dynamics by which some threats as opposed to others come to be understood under the rubric of security and the significance of this naming as an act of construction.
The Copenhagen School argues that security is a speech act. The speech act, which was elaborated by John Austin ( 1962/1975 ), begins with the idea that saying something is doing something. Saying “I do” in the context of a wedding is not mere language or description. It is an act that brings a marriage into being. Promising or threatening are not labels that refer to objects in the world, but rather acts that involve an exchange in relation to others which, to be meaningful, must rest on certain shared understandings and some degree of credibility. The credibility of a threat will cease in the absence of a consistent pattern of following through on threats. Because the shared understanding attached to security is one of existential threat, uttering the word security is an act that constitutes a threat as existential. Threats that are securitized have been identified as existential threats that require an emergency response and the suspension of normal politics.
For instance, before September 11, 2001 , terrorism was a category of criminal activity, and remains so for many international actors. However, after September 11, terrorism became an existential threat to the United States. The threat was existential insofar as the survival of America and American identity was seen to be at stake, and thus the threat had absolute priority. Use of the word security and the language of war constituted an emergency condition, where elites claimed the right to use whatever means are necessary to block the threat, including a policy of preemption against states that harbor terrorists. In so doing, they broke free of the rules that would normally constrain their actions. Since September 11, increasing surveillance and powers of arrest have been justified in the name of security. In the argument of the Copenhagen School, securitization is different from “normal” politics. The politicization of an issue brings it into the open and makes it a matter of public choice and something to be decided upon, that is, a part of the normal politics of public deliberation in a democracy. The securitization of an issue, by contrast, removes it from the political haggling of normal politics and justifies its prioritization over other issues, as well as decisive action by leaders. This may work to silence opposition, as leaders exploit threats for domestic purposes and act without democratic control or constraint. In this respect, security becomes a negative term that points to the removal of an issue from the realm of politics.
The Copenhagen School distinguishes itself from more critical security studies by its acceptance of certain realist themes, including attention to the processes by which state security practices are sedimented. Other critical analysts go beyond the Copenhagen School’s claim that securitization represents the suspension of normal politics to explore the role of securitization as a continual technique of governance, its role in the suspension of the political, such that the “state of exception becomes the norm” (Muller 2004 ; Shapiro 2004 ; Bigo 2006 ; Dillon 2007 ).
Michel Foucault ( 1976 ) argued that in modernity the legal authority of the state, accompanied by a view of individuals as citizens, represents a form of biopolitics. Biopolitics is the transformation of state power from the power of death to the management of populations and power over life. This reduces the citizen to what Giorgio Agamben ( 1998 ) refers to as “bare life.” The citizen of “normal politics,” derived, for instance, from Aristotle’s conception, engages in political debate and decision making. In Foucault’s argument, sovereign power revolves around the governance of populations and biological life rather than political life. The subject of politics is no longer the potential agency of the citizen, but the management of life itself. In this respect, the founding political image of the West has shifted from “Athens to Auschwitz” (Agamben 2004 :169).
Auschwitz is a symbol of depoliticization, where survival is elevated over questions about the nature and continuation of a specific form of political life. The suspension of normal politics, as discussed by the Copenhagen School, becomes, in this view, a permanent “state of exception” (Agamben 2005 ). In the state of exception the sovereign becomes both the law and outside the law, insofar as it has the power to suspend the law, imposing extrajudicial exceptional powers or a permanent state of emergency, which becomes an important technology of government control. The state of emergency need not always be openly declared in a technical sense, yet statutory amendments and changes in the background speak directly to the permanence of the state of exception. The suspension of conventional legislative and judicial powers and the concentration of power in the hands of the core executive constitute the state of exception.
While the initial questions about the meaning of security were often situated within arguments about the need to expand the concept to cover new areas, such as the environment or poverty, the Copenhagen School argued that we cannot so easily escape a history of meaning and use in which security is associated with states and military power (Wæver 1995 ). What is important, in this argument, is the analysis of how a concept of security is put to use in the construction of threats. Post-structuralists go a step further to examine a more structural process by which insecurity is reproduced. The dilemma, according to Anthony Burke ( 2002 :20) is that “security is bound into a dependent relation with ‘insecurity,’ it can never escape it: it must continue to produce images of ‘insecurity’ in order to retain its meaning.” While both rely on some notion of the “exceptional,” the Copenhagen School presents the exception as a deviation from “normal” deliberative and democratic politics, which are suspended in the face of a threat; by contrast, post-structuralists implicate liberal governance in the production of a long-term or permanent “state of exception.” All of these approaches depart from the assumption of traditional security studies that threats exist as objective phenomena separate from processes of making meaning.
Identity and Difference
The critical literature on threats goes beyond the assumption of traditional security studies that threats exist as objective phenomena in the world to examine how threats are constructed. Threats thus do not exist in a static field and their construction presumes a corresponding definition of the subject and object of threats. Thus, not only threats but identity are problematized by critical security analysts. In neo-realist accounts, states are assumed to be unitary and rational actors and thus identity is not an issue. The concept of identity, by contrast, opens up the possibility of multiple identities, and change between them. According to Goff and Dunn ( 2004 ), identity has four dimensions: alterity, fluidity, constructedness, and multiplicity. Discussions of identity within the literature on critical security studies have revolved around several aspects of identity. The first point, upon which critical analysts generally agree, is that identity exists in a relationship, an idea that is often captured in the concept of alterity. Identity is a social category that expresses not only the meaning any one actor attributes to the self; rather self-definitions are related to definitions that the self gives to others and others to the self. Categories are thus intersubjective and defining of a particular community of identity and practice; they are not purely in the minds of individuals.
The discussion of identity as a relationship suggests that it is to some degree constituted in difference. As William Connolly ( 1991 :64) argues, identity, whether of an individual, a state, or some other social group, is always “established in relation to a series of differences that have become socially recognized. These differences are essential to its being. If they did not coexist as difference, it would not exist in its distinctness and solidity.” Critical scholars inspired by Foucault and Derrida, among others, have highlighted several dimensions of the identity–difference relationship. The first is the role of identity and difference in constituting “insides” and “outsides” of states (Walker 1993 ; Campbell 1998 ). Notions of order, progress, democracy, and ethics have been presumed to be only possible “inside” the state, while the “outside” is a realm characterized by anarchy, war, and the primacy of power. David Campbell ( 1998 ) takes this logic a step further to demonstrate how US identity has been dependent on the production of danger from evil others outside. Another theme is the role of difference in constructing hierarchy and the legitimacy of intervention. Roxanne Lynn Doty ( 1996 ) explored practices of representation by Northern elites that constituted the “imperial encounter.” She analyzes the role of binary oppositions, characterized by reason/rationality, passion/emotion, parent/child, and good/evil, and the construction of regions such as the “South” or the “third world,” or more narrowly Kenya or the Philippines, in relation to the “North,” the United States or Britain. Doty argues that hierarchical representations legitimized intervention in these regions. Gender is also a site where identity is constructed in hierarchical difference. Gender discourse provides a system of meanings and a way of thinking that shapes how men and women experience, understand, and represent themselves, which also shapes many other aspects of human life and culture (Cohn, in Cooke and Woollacott 1993 :228–9). This discourse rests on dichotomies that construct mutually exclusive oppositions, including mind to body, culture to nature, thought to feeling, logic to intuition, objectivity to subjectivity, etc.
Whether deconstructing the “othering” of enemies or subordinates, all of these scholars emphasize the power inherent in constructions of knowledge based on difference. Most of them build on the Foucauldian idea that discourse not only contains linguistic expressions, to be judged in terms of the accuracy of representation, but also generates modes of power and exclusion. As Michael Shapiro (Der Derian and Shapiro 1989 :75) comments: “In deploying identities for actors and producing the overall meaning frame within which they operate, [discourses] constitute and reproduce prevailing systems of power and authority in general and direct the actions flowing from these systems to the particular.” The purpose of critical analysis, in this school of thought is to deconstruct the binary oppositions upon which power and exclusionary processes rest.
Some scholars have disputed the idea that identity is dependent on difference. Ole Wæver ( 1996 :122) points to contemporary Europe as an example that raises questions about this claim. Rather than constructing clear and dangerous others, post–Cold War Europe has, he argues, been “a pole of attraction with graduated membership so that Europe fades out but is not constituted against an external enemy.” Critical theorists in the tradition of Habermas, such as Linklater ( 1998 ), have argued that dialogue can be a path to some kind of universal consent against the background of particular differences. Linklater ( 1996 :85–7) claims that discourse ethics seeks to critique all forms of systematic inequality that prevent active participation in dialogue. Nonetheless, critical scholars who emphasize identity and difference have problematized the goal of universal consent. First, the goal of expanding the values of the polis to the international sphere is in conflict with the search for consent within sovereign states, insofar as democratic consent within sets the stage for practices of exclusion of others outside. While these critical scholars also seek dialogue that crosses lines of difference, they resist totalization in any form, including a totalized universal agreement. It is difference itself that is to be celebrated. Freedom is about speaking, listening, and being heard, and not being excluded from communication and conversation (Ashley and Walker 1990 :395). An ethical relationship between self and other requires contestation and negotiation. All ethics arises from a relationship to otherness, which entails a permanent critique of totalization and a struggle on behalf of difference rather than attempts to eliminate it.
In practice, processes of dialogue have been defined less by the search for universal agreement than the attempt to move beyond the stark identity–difference relationship, which is the foundation of conflict, toward some kind of common identity and language that would make talk – as distinct from fighting – possible. Before the end of the Cold War, the European dialogue between disarmament campaigns in the West and human rights initiatives in the Eastern Bloc constituted “citizens of a Europe whole and free,” in contrast to bifurcated Cold War identities of a divided Europe (Fierke 1998 ). Divided societies moving out of conflict have also often sought some kind of common identity. In South Africa, the notion that all citizens are South Africans provided a foundation of common identity for the truth and reconciliation process. In Northern Ireland, a common identity of this kind is by definition more problematic, given the conflict has been defined by allegiance to either the United Kingdom or Ireland. As a result, distinctions within the peace process between “men of violence” and those who had renounced violence played a larger role.
The shift within critical security studies to a focus on identity went hand in hand with a methodological shift away from the attempt, common within the social sciences, to fix the meaning of terms in order to test them against the world, to forms of discourse analysis. Given the fluidity of identity from one context to another or its changeability, it is imperative that the analyst examine how identities are formed in context and in relationship to other identities. The extent to which discourse analysis should be viewed as a “method” has been a subject of debate. As Jennifer Milliken (in Fierke and Jorgensen 2001 :136) points out, some discourse analysts within international relations avoid questions of rigor and systematic method given their association with positivism and an objective world “out there.” Others, such as Hansen ( 2006 ), have argued that it is imperative for discourse analysts to be clear in stating their assumptions and presenting their methods. The fact that discourse analysis rests on a more constitutive model of analysis, as distinct from a causal one, does not make it less rigorous by definition (Hansen 2006 :28).
The debate over identity and difference also flows over into debates over discourse analysis. While most who identify themselves with post-structuralism would focus analysis on the deconstruction of hierarchical oppositions, others conceive of discourse analysis as useful for a range of tasks. First, it may be useful for analyzing the multiple discourses for giving meaning to identities in a context undergoing change. For instance, in the aftermath of the Cold War, against the backdrop of conflict in the former Yugoslavia, and particularly Bosnia, Western observers placed the identities of the antagonists in several different frameworks of meaning, drawing on analogies to World War I, World War II, Vietnam, etc., each of which shaped a different understanding of the conflict and conclusions about the type of action to be taken (Fierke 1996 ; Hansen 2006 ). A second approach focuses on the distinct contours of different worlds across time. The subjects, objects, and practices that constituted the world of sixteenth century witch-hunts or eighteenth century slave-trading or twenty-first century terrorism are historically and culturally specific. Discourse analysis may be used to map the transition between worlds. Neta Crawford ( 2002 ) adopts a form of argument analysis to map the transition from a world in which slavery was legitimate to one in which it became an illegitimate practice. A third angle explores how meanings, shaped in one historical encounter, may carry over into future interactions, to be transformed within a new discourse. For instance, the concept of a safe haven, situated during the 1990s in a discourse of protecting refugees and civilians in war, has been transported, in the context of the War on Terrorism, into a discourse of terrorism (Fierke 2007 ). Despite changes in the discourse over time, the core of the safe haven, since it was defined in the 1949 Geneva Convention, has been the protection of vulnerable people. By contrast, in the National Military Strategic Plan for the War on Terrorism , published by the Chairman of the Joint Chiefs of Staff ( 2006 ), the safe haven is “one of the most important resources of extremists” ( 2006 :15). While this is not the first time that the term has been used in relation to nefarious activities, such as money laundering and fraud, there is an overlap between the use of safe haven in this context and the protection discourses of the 1990s. Both are embedded in a world of “failed states”; what changes is the identity of the subject, from that of “victim” to be protected to “terrorist” who is a source of fear.
Human Security
Global inequality was a theme of the early Marxist literature of international relations. This theme reemerged in the 1990s, in a somewhat different form, as “failed states,” many of which were a product of decolonization and bloody intrastate war, began to proliferate. The old concept of security, focusing on conflict between states, was of minimal use for understanding this phenomenon. Two developments in the mid-1990s provided an alternative point of departure. The first was a concept of human security, articulated in the 1994 UN Human Development Program report. Human security shifts attention away from states to individuals, emphasizing human rights, safety from violence, and sustainable development. The second was a rethinking of the relationship between security and development, previously two separate areas of analysis. This rethinking gave rise to a conclusion that underdevelopment is dangerous insofar as it correlates and coexists with violent conflict (Duffield 2001 ; Hampson et al. 2001 ). Achieving human security, in this argument, would require the transformation of entire societies into liberal democracies. These developments reinforced the idea that the international community, and the United States more specifically, had a responsibility to spread democracy to other areas of the world.
Human security was first popularized by the UN Development Program and was a response to an observation after the end of the Cold War that in today’s conflicts civilians are often the victims and even the primary targets of violence. Human security builds on the idea that people’s rights are at least as important as those of states. It had relevance in a context where, since the end of the Cold War, the majority of casualties in war had been civilian, where more than 30 million people had been displaced from their homes, where large numbers of child soldiers had been recruited or forced into violent conflict, and where rape had become a standard practice of warfare. The concept emerged from the fusion of several other concepts (Hampson et al. 2001 :152). The first, which was introduced by the Brundtland Commission in 1987 , was sustainable development. The Commission’s report argued that environmental protection was a necessary condition for the long-term survival of humanity and, subsequently, of any long-term development strategy (World Commission on the Environment and Development 1987 ). The second, introduced by the first development report of the UN Development Program in 1990 , was human development. The report stated that “people must be at the center of all development [and] […] that while growth in national production (GDP) is absolutely necessary to meet all essential human objectives, what is important is to study how this growth translates – or fails to translate – into human development” (UNDP 1990 :iii). In the fifth Human Development Report in 1994 human development was merged with a significantly broadened security agenda to produce human security (Hampson et al. 2001 :153).
The core concern underpinning the human security concept is the inextricable interrelationship between freedom from want and freedom from fear (Thomas 2004 :353). This rests on a holistic understanding in which the vulnerability of individuals poses a threat to – and thus the safety of individuals is key to – global security (Hampson 2004 :350). One major focus of the human security agenda was a treaty that banned landmines, which are often left scattered around a landscape after war, and can be a source of harm to people going about their daily business. Other issues on the agenda include protecting civilians in armed conflict; reforming sanction regimes to mitigate some of the more negative effects on civilians; the rights of women; humanitarian intervention to protect against future Rwandas or Srebrenicas; and the demobilization and rehabilitation of combatants, and particularly child soldiers. The International Criminal Court has also been an important item on the human security agenda, as has the “responsibility to protect,” a proposal of the International Commission on Intervention and State Sovereignty (ICISS) which incorporates a concept of human security over more narrow definitions of national security. The ICISS proposal represents a rethinking of the conflictual relationship between sovereignty and non-interference, on the one hand, and human rights on the other. Sovereignty comes with an obligation of the state to provide protection to its population. When the latter is not forthcoming or the state becomes a source of harm, the responsibility to protect transfers to the international community.
Human security is a critical concept in so far as it raises questions about the focus and assumptions of realist security studies. Scholars have, however, complained about the existence of over thirty definitions of human security (Alkire 2004 :359). The lack of clear boundaries has been useful for political actors who seek to organize as broad a coalition as possible behind the concept, and for anthropologists who seek to uncover how it is used in different contexts. Scholars of human security have, on the one hand, sought a more precise category in order to improve its analytic strength, and, on the other hand, have been troubled by the difficulty of fixing the definition of human security. Kyle Grayson ( 2004 ) raises a concern about the politics of conceptualizing human security. He asks who, what, and where is marginalized when “experts” provide a precise/scientific definition that is of practical use, and argues that the focus of attention should be the power–knowledge nexus that the concept constitutes.
The methodological issue points to questions about the concept’s critical potential in practice. On the one hand, despite its distance from liberal notions of possessive individualism, as noted by Thomas ( 2000 :xi), human security does have links to a liberal model of development. In this respect, many of its assumptions are in conflict with more critical theories of development. On the other hand, the concept has been used to present a critical challenge to current practice. Human security has been a key concept of NGOs and others who are interested in actually transforming global economic structures. As Thomas ( 2000 :9) notes, “the shift to human security […] highlights the importance of scrutinizing global processes that may impact on, even jeopardize security and the global governance structures which drive these processes.” Whether human security is understood to be part of a new regime of power or a challenge to existing regimes, the concept rests on a recognition that the traditional means of providing safety and security to civilians, that is, the nation-state, is no longer – if it ever was – effective in many parts of the world.
Liberal discourses of development and democracy have focused on individual states, ignoring the embeddedness of these states in historical relations that are global. This focus has been maintained in the merging of development and security discourses. Mark Duffield ( 2001 ) provides a critical analysis of the relationship between security and development, which, he argues, has increasingly been addressed within a liberal governance model. Since the mid-1990s there has been a change of policy based on the conclusion that underdevelopment is dangerous and is a source of conflict. In this respect, “want” perpetuates “fear.” This conclusion, which is an extension of the liberal model, does not locate underdevelopment or “failed states” in an unjust global system, which emerged along with a capitalist world economy and a history of imperialism, but instead internalizes the causes of conflict and political instability. Conflict is a result of underdeveloped and dysfunctional war-torn societies. The solution to underdevelopment is to be found in the transformation of individual societies rather than the global system in this liberal logic. The policy of international organizations has thus shifted from humanitarian assistance and aid, per se, to the process of reconstructing post-conflict societies along liberal lines (Duffield 2001 :11). As a result, an increasingly complex array of UN agencies, donor governments, NGOs, and military establishments work together to bring about a change in societies so that problems of the past don’t reemerge. Their practice rests on an argument that development is impossible without stability and that security isn’t sustainable without development (Duffield 2001 :16).
Duffield examines human security as part of a Foucauldian strategy of biopolitics, whereby a strategic complex of global actors and governing agencies, through a newly formed public–private relationship, shapes and controls civil populations. He argues that the nature of power and authority has changed radically. This new power, expressed in the globalized structures of liberal peace, differs from old imperial structures. Rather than the brute imposition of power, or the direct control of territory, we see partnership and participation, which implies a mutual acceptance of shared normative understandings. Inclusion in global structures means buying into the norms that underpin these structures. This development is a response to the demise of political alternatives in the South, since the end of the Cold War and the demise of the socialist project. On the part of the West, it is an attempt to stem refugee flows and to transform entire societies, replacing indigenous values and modes of organization with liberal ones.
The marriage of development and security discourses reinforced a liberal agenda of transforming entire societies into liberal democracies. This agenda is problematic for two reasons. First, as already discussed, it represents a new regime of power, albeit “softer” than the old imperialist regime. Marxists view human security as a repackaging of liberal humanitarianism, with its routine failure to address underlying social causes (Thomas 2004 :353). Second, the discourse failed to problematize the role of historical global relations in the production of “failed states” and, subsequently, in the production of fear and want. The discourse localizes agency in the “international community” and some Western states, which have taken on the role of “fixing” the problem of human insecurity. The resulting practices have the potential to reproduce historical relationships of power.
On the one hand, human security embodies a number of liberal assumptions and has reinforced a liberal agenda. On the other hand, it contains a potential for questioning and rethinking these assumptions. Liberal approaches ask how security is to be provided to the individual, given the failure of states. More critical analyses look to the global historical context, and the assumptions underpinning it, to the processes by which “failed” states, and subsequently human insecurity are produced and reproduced.
Critical Theory and Emancipation
The Frankfurt School originated in 1930s Germany with Theodor Adorno and Max Horkheimer , who articulated a technique of immanent critique and the concept of emancipation. Immanent critique begins with the idea that the critical theorist stands within time and within a historical context, rather than outside time as an objective observer, as assumed by problem solving theories. The critical theorist creates a critical distance from his or her historical context in order to explore its origins, development, institutions, and potential for change (Booth 2005 :11). Critical theory presents a more three-dimensional world containing not only the powerful but others as well. Immanent critique relies on a clear link between theory and practice and, as Richard Wyn Jones ( 1999 :6, 56) argued, “critical theory stands or falls by its ability to illuminate the possibilities for emancipatory transformation.” If problem solving theory reinforces the position of the powers that be, critical theory and immanent critique make suffering humanity the prism through which problems are viewed. This means focusing on the men, women, and communities for whom the present order is a cause of insecurity. If all theory is theory for someone, then critical theory, or critical security studies, is for the voiceless, the unrepresented, the powerless, and its purpose is their emancipation (Wyn Jones 1999 :159). Edward Said ( 1994 :84) further suggests that critical intellectuals “are always tied to and ought to remain an organic part of an ongoing experience in society: of the poor, the disadvantaged, the voiceless, the unrepresented, the powerless.” Consistent with a Gramscian argument, intellectuals are the agents of critique, who engage specialist information and expertise to the end of challenging prevailing hegemonic discourses (Wyn Jones 1999 :160).
In everyday language, emancipation is associated with struggles for freedom from domination, such as the emancipation of American slaves or the emancipation of women. The word is derived from the Latin emancipare , meaning the action of setting free from slavery or tutelage ( Wyn Jones , in Booth 2005 :216). The theoretical roots of the concept are found in Marxist theory. In his “Theses on Feuerbach,” Marx claimed that the point is to change the world, not merely to interpret it. While originally equating emancipation with the need to be freed from the vicissitudes of nature, Adorno and Horkheimer later rethought the problem as they struggled to make sense of the barbarism of the Holocaust, arguing that it represented the deification of instrumental reasoning, which had been essential to nature’s domination. They instead envisioned emancipation as a “reconciliation” with nature, suggesting a more non-instrumental relationship with it. Several decades later, Habermas ( 1984 ; 1987 ) discussed emancipation in relation to interaction and community, and identified emancipation with the potential to be freed from those institutions and practices that stand in the way of unconstrained communication.
Within international relations, Andrew Linklater ( 1998 ) adapted the discourse ethics of Habermas to an argument about the potential for global dialogue as a path to more universal agreement and thus a more universal culture and identity. Ken Booth ( 1991 ) further identified two elements of the relationship between security and emancipation, defining security as the absence of threats, and presenting emancipation as freeing people from the physical and human constraints that stop them from carrying out what they freely choose to do. War and the threat of war are constraints, as are poverty, poor education, and oppression. He later ( 1999 :41–2) defined what emancipation is not. In his argument, it is not a universal, timeless concept, nor can it be gained at the expense of others. Emancipation is not synonymous with westernization. These arguments point to a larger concern, expressed by other critical theorists, that the concept of emancipation is too closely linked with modernity, meta-narratives, especially Marxism and liberalism, and the Enlightenment belief that humanity is progressing toward a more perfect future.
Protagonists in this debate fear that the codification of positive alternatives, based on the search for universal consensus, as suggested by Habermas or Linklater, will only buttress new regimes of power, as was the case with Marxist communism in the former Eastern Bloc. They point to Western discourses of universalism that are implicated in the production of a particular conception of politics and society. In this conception, negative representations of non-European peoples contribute to the construction of Western identity as the highest civilization, and legitimize its project of global domination (Linklater 1998 :47). From this perspective, the critique of universalist concepts, including emancipation, is fundamental to eradicating hegemonic representations of the non-Western world that have been part of the construction of Western power. One related argument is that the agents of emancipation are invariably from the West, whether in the form of Western-dominated international institutions, a Western-led global civil society, or the “ethical foreign policies” of leading Western powers (Barkawi and Laffey 2006 : 350). Even when the concrete agents of emancipation are not themselves Westerners, they are conceived as the bearers of Western ideas. This does not mean that emancipation needs to be avoided per se, only that, like any other phenomenon in international relations, critical attention to its underlying assumptions is required.
Emancipation begins with critique and is primarily about the act of freeing, whether from the assumptions that blind us to alternatives or from the structures of power that constrain human potential. Wyn Jones (in Booth 2005 :216) argues that some concept of emancipation is a necessary element of any form of analysis that attempts to problematize and criticize the status quo. Hayward Alker (also in Booth 2005 :200) discusses the need to include multiple Western and non-Western perspectives on freedom without “giving up the distinctive and attractive appeal to human improvement and emancipatory development that is so central to the ethical/global concerns of the critical security studies project.” Even Jacques Derrida ( 1996 :82) has expressed a commitment to the “great classical discourse of emancipation,” while avoiding inscription of the discourse into “a teleology, a metaphysics, an eschatology.” He goes so far as to state that there “is no ethico-political decision or gesture without […] a ‘yes’ to emancipation.” Emancipation is a process rather than an end point, a direction rather than a destination. Immanent critique is one step in this process and the point of departure for identifying the emancipatory potential of a context. Emancipation can more generally be understood in relation to the critical imperative of freeing security studies from those assumptions that blind scholars to concerns outside its narrow definition, which focuses on statecraft and force, thereby opening a space to consider alternatives. Emancipation further refers to freeing those outside established structures of power from the constraints that hold them back from realizing their potential.
- Agamben, G. (1998) Homer Sacer: Sovereign Power and Bare Life . Stanford: Stanford University Press.
- Agamben, G. (2004) Bodies without Words: Against the Biopolitical Tatoo. German Law Journal 5 (2), 168–9.
- Agamben, G. (2005) State of Exception . Chicago: University of Chicago Press.
- Alkire, S. (2004) What Is Human Security? Security Dialogue 35 (3), 359–60.
- Ashley, R. (1984) The Poverty of Neorealism. International Organization 38 (2), 225–49.
- Ashley, R. , and Walker, R.B.J. (1990) Reading Dissidence/Writing the Discipline: Crisis and the Question of Sovereignty in International Relations. International Studies Quarterly 34 (3), 367–416.
- Austin, J.L . (1975) How to Do Things with Words , 2nd edn. Oxford: Oxford University Press. Originally published 1962.
- Barkawi, T. , and Laffey, M. (eds.) (2006) The Post-Colonial Moment in Security Studies. Review of International Studies 32 (2), 329–52.
- Beck, U. (2003) The Silence of Words: On Terror and War. Security Dialogue 34 (3), 255–67.
- Bigo, D. (2006) Security, Exception, Ban and Surveillance. In D. Lyon (ed.) Theorizing Surveilliance: The Panopticon and Beyond . Cullompton: Willan, pp. 46–68.
- Booth, K. (1991) Security and Emancipation. Review of International Studies 17 (14), 313–26.
- Booth, K. (ed.) (1999) Three Tyrannies. In T. Dunne and N.J. Wheeler (eds.) Human Rights in Global Politics . Cambridge: Cambridge University Press, pp. 31–70.
- Booth, K. (ed.) (2005) Critical Security Studies and World Politics . Boulder: Lynne Rienner.
- Burke, A. (2002) Aporias of Security. Alternatives 27, 1–27.
- Buzan, B . (1991) People, States and Fear: An Agenda for International Security Studies in the Post-Cold War Era . London: Harvester Wheatsheaf. Originally published 1983.
- Buzan, B. , Wæver, O. , and Wilde, J. de (1998) Security: A New Framework of Analysis . Boulder: Lynne Rienner.
- Campbell, D. (1998) Writing Security: United States Foreign Policy and the Politics of Identity , 2nd edn. Minneapolis: University of Minnesota Press.
- Cardoso, F.H. , and Faletto, E. (1979) Dependency and Development in Latin America . Berkeley: University of California Press.
- Chairman of the Joint Chiefs of Staff (2006) National Military Strategic Plan for the War on Terrorism (Feb. 1). At www.jcs.mil , accessed Jun. 15, 2009.
- Connolly, W. (1991) Identity/Difference: Democratic Negotiations of Political Paradox . Ithaca: Cornell University Press.
- Cooke, M. , and Woollacott, A. (eds.) (1993) Gendering War Talk . Princeton: Princeton University Press.
- Cox, R.W. (1981) Social Forces, States and World Orders: Beyond International Relations Theory. Millennium 10 (1), 126–55.
- Crawford, N. (1991) Once and Future Security Studies. Security Studies 1 (2), 283–316.
- Crawford, N. (2002) Argument and Change in World Politics: Ethics, Decolonization and Humanitarian Intervention . Cambridge: Cambridge University Press.
- Dalby, S. (2002) Environmental Security . Minneapolis: University of Minnesota Press.
- Der Derian, J. , and Shapiro, M. (eds.) (1989) International/Intertextual Relations: Post-Modern Readings in International Relations . Lexington: Lexington Books.
- Derrida, J. (1996) Remarks on Deconstruction and Pragmatism, trans. S. Critchley. In C. Mouffe (ed.) Deconstruction and Pragmatism . London: Routledge, pp. 77–88.
- Dillon, M. (2007) Governing Terror: The State of Emergency of Biopolitical Governance. International Political Sociology 1, 7–28.
- Doty, R.L. (1996) Imperial Encounters: The Politics of Representation in North/South Relations . Minneapolis: University of Minnesota Press.
- Duffield, M. (2001) Global Governance and the New Wars: The Merging of Development and Security . London: Zed Books.
- Enloe, C. (1989) Bananas, Beaches and Bases: Making Feminist Sense of International Politics . Berkeley: University of California Press.
- Fierke, K.M. (1996) Multiple Identities, Interfacing Games: The Social Construction of Western Action in Bosnia. European Journal of International Relations 2 (4), 467–98.
- Fierke, K.M. (1998) Changing Games, Changing Strategies: Critical Investigations in Security . Manchester: University of Manchester Press.
- Fierke, K.M. (2007) Critical Approaches to International Security . Cambridge: Polity.
- Fierke, K.M. , and Jorgensen, K.E. (2001) Constructing International Relations: The Next Generation . Armonk: M.E. Sharpe.
- Foucault, M. (1976) The Will to Knowledge: The History of Sexuality . London: Penguin.
- Goff, P.M. , and Dunn, K.C. (2004) Identity and Global Politics: Theoretical and Empirical Elaborations . Basingstoke: Palgrave.
- Grayson, K. (2004) What Is Human Security? A Challenge to the Power over Knowledge of Traditional Security Studies. Security Dialogue 35 (3), 356–7.
- Habermas, J. (1984) Theory of Communicative Action . Vol. 1: Reason and the Rationalization of Society , trans. T. McCarthy . London: Heinemann.
- Habermas, J. (1987) Theory of Communicative Action . Vol. 2: Lifeworld and System: A Critique of Functionalist Reason , trans. T. McCarthy . London: Heinemann.
- Hampson, F.O. , Daudelin, J. , Hay, J. , Reid, H. , and Martin, T. (2001) Madness in the Multitude: Human Security and World Disorder . Oxford: Oxford University Press.
- Hampson, F.O. (2004) What Is Human Security? A Concept in Need of a Global Policy Response. Security Dialogue 35 (3), 349–50.
- Hansen, L. (2006) Security as Practice: Discourse Analysis and the Bosnian War . London: Routledge.
- Huysmans, J. , Dobson, A. , and Prokhovnik, R. (eds.) (2006) The Politics of Protection: Sites of Insecurity and Political Agency . London: Routledge.
- Krause, K. , and Williams, M. (eds.) (1997) Critical Security Studies . Minneapolis: University of Minnesota Press.
- Lenin, V.I . (1988) Imperialism: The Highest Stage of Capitalism . New York: International. Originally published 1939.
- Linklater, A. (1996) Citizenship and Sovereignty in the Post-Westphalian State. European Journal of International Relations 2 (1), 77–103.
- Linklater, A. (1998) The Transformation of Political Community: Ethical Foundations of the Post-Westphalian Era . Cambridge: Polity.
- Muller, B. (2004) (Dis)qualified Bodies: Securitization, Citizenship and Identity Management. Citizenship Studies 8, 279–94.
- Nye, J. , and Lynn-Jones, S. (1988) International Security Studies: A Report of a Conference on the State of the Field. International Security 12 (4), 5–27.
- Onuf, N. (1989) World of Our Making: Rules and Rule in Social Theory and International Relations . Columbia: University of South Carolina Press.
- Peterson, V.S. (ed.) (1992) Gendered States: Feminist (Re)Visions of International Relations Theory . Boulder: Lynne Rienner.
- Said, S. (1994) Culture and Imperialism . New York: Vintage.
- Schelling, T. (1966) Arms and Influence . New Haven: Yale University Press.
- Shapiro, M.J. (2004) Methods and Nations: Cultural Governance and the Indigenous Subject . London: Routledge.
- Thomas, C. (2000) Global Governance, Development and Human Security . London: Pluto.
- Thomas, C. (2004) What Is Human Security? A Bridge between the Interconnected Challenges Confronting the World. Security Dialogue 35 (3), 353–4.
- Tickner, J.A. (1993) Gender and International Relations: Feminist Perspectives on Achieving International Security . New York: Columbia University Press.
- United Nations Development Program (UNDP) (1990) Human Development Report, 1990 . New York: UNDP.
- Wæver, O. (1995) Securitization and Desecuritization. In R.D. Lipschutz (ed.) On Security . New York: Columbia University Press, pp. 46–86.
- Wæver, O. (1996) European Security Identities. Journal of Common Market Studies 34 (1), 103–32.
- Walker, R.B.J. (1987) Realism, Change and International Political Theory. International Studies Quarterly 31 (1), 65–86.
- Walker, R.B.J. (1993) Inside/Outside: International Relations as Political Theory . Cambridge: Cambridge University Press.
- Wallerstein, I. (1974) The Rise and Future Demise of the World Capitalist System: Concepts of Comparative Analysis. Comparative Studies in Society and History , 16 (4), 390–2, 399–406.
- Waltz, K. (1979) Theory of International Politics . Reading: Addison Wesley.
- Weldes, J. (1996) Constructing the National Interest. European Journal of International Relations 2 (3), 275–318.
- Weldes, J. , Laffey, L. , Gusterson, H. , and Duvall, R. (eds.) (1999) Cultures of Insecurity . Minneapolis: University of Minnesota Press.
- Wendt, A. (1992) Anarchy Is What States Make of It: The Social Construction of Power Politics. International Organization 46 (2), 391–425.
- World Commission on the Environment and Development (1987) Our Common Future, Brundtland Commission. At www.are.admin.ch/are/en/nachaltig/international_uno/unterseite023301 , accessed 24 June 2006.
- Wyn Jones, R. (1999) Security, Strategy and Critical Theory . Boulder: Lynne Rienner.
Links to Digital Materials
The Responsibility to Protect, Report of the International Commission on International and State Sovereignty, 2001. At www.dfait-maeci.gc.ca/iciss-ciise/report-en.asp , accessed Jul. 2009.
Acknowledgments
This essay is heavily indebted to my book Critical Approaches to International Security ( 2007 ). Readers wishing a more detailed treatment of this topic are encouraged to consult this source.
Printed from Oxford Research Encyclopedias, International Studies. Under the terms of the licence agreement, an individual user may print out a single article for personal use (for details see Privacy Policy and Legal Notice).
date: 24 May 2024
- Cookie Policy
- Privacy Policy
- Legal Notice
- Accessibility
- [66.249.64.20|81.177.182.159]
- 81.177.182.159
Character limit 500 /500
- skip navigation
- Privacy Policy
- Accessibility
- search search

Welcome at the Chair of Privacy and Security

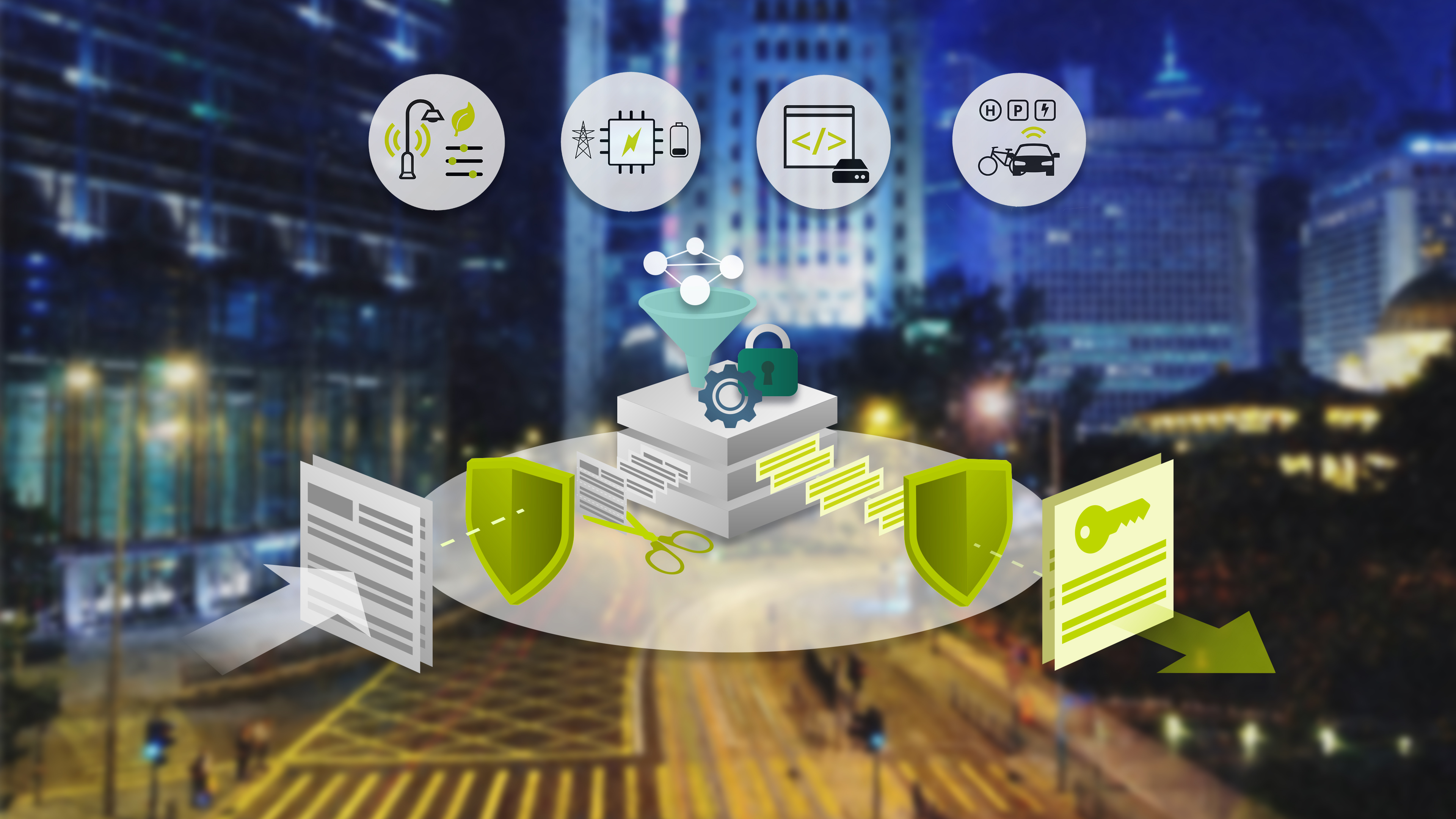
We work on all aspects of technical data protection and network and IT security. We are primarily interested in privacy, i.e. the protection of individuals against the misuse of their data.
Over the past decades, digital technologies have developed rapidly. The advent of digital transformation and the interconnectivity of all areas of life opens up a wealth of new possibilities. Autonomous networked vehicles, cloud computing, industry 4.0, virtual reality with haptic feedback, online banking or social networks are just a few keywords that are changing the way and quality of life. However, this development also brings with it a number of challenges that people often do not immediately grasp, but which may well conflict with their interests. Our research group is engaged in the development and analysis of security concepts that protect from all types of potential attackers on such systems. We are also interested in the development of technologies that promote data protection in order to protect privacy in the digital world. Finally, we develop protocols and algorithms to secure the underlying infrastructures for communication and computation.
We are part of the KASTEL Security Research Labs, as well as the excellence cluster CeTI , the Centre for Tactile Internet with Human-in-the-Loop.
The papers Fantômas: Understanding Face Anonymization Reversibility (Julian Todt, Simon Hanisch, Thorsten Strufe) and Provable Security for the Onion Routing and Mix Network Packet Format Sphinx (Philip Scherer, Christiane Weis, Thorsten Strufe) have been accepted at PETS 2024. The preprints are available at arXiv: Fantômas & Provable Sphinx Security .
Congratulations!

It has been a pleasure to have study visitors from the Brazilian Universidade Federal de Campina Grande (UFCG) here in Karlsruhe. The visit was part of the German Academic Exchange Service (DAAD) and has brought us many interesting discussions!
The paper Pirates: Anonymous Group Calls Over Fully Untrusted Infrastructure (Christoph Coijanovic, Akim Stark, Daniel Schadt, Thorsten Strufe) has been accepted at ACISP 2024!
In this paper the scientists construct a system which allows anonymous group voice calls – even over infrastructure which might be malicious. Their system is the first one to meet the recommendation of a sub-400 millisecond latency.

On April 12, 2024, our researcher Patricia Guerra Balboa has participated in the FameLab competition for science communication with her presentation about Differential Privacy and the anonymization of trajectories. She was awarded the silver medal and the audience price, which earns her an invitation to the national finals in Bielefeld. Congratulations!
(Picture: FameLab Germany: Karlsruhe 2024 © Wissenschaftsbüro Karlsruhe, Foto: Netzoptimisten)

Presentations made painless
- Get Premium
127 Cyber Security Essay Topic Ideas & Examples
Inside This Article
With the increasing reliance on technology, cyber security has become a critical concern for individuals, organizations, and governments worldwide. As cyber threats continue to evolve and become more sophisticated, it is essential to stay informed about the latest trends and issues in this field. If you are tasked with writing an essay on cyber security, here are 127 topic ideas and examples to get your creative juices flowing.
The role of artificial intelligence in enhancing cyber security.
The impact of cyber attacks on critical infrastructure.
The ethical considerations of cyber warfare.
The legal frameworks governing cyber security.
The challenges of securing the Internet of Things (IoT) devices.
The role of encryption in protecting sensitive information.
The effectiveness of password policies in preventing cyber attacks.
The psychology behind social engineering attacks.
The impact of cyber attacks on the global economy.
The future of biometrics in cyber security.
The role of cyber insurance in mitigating cyber risks.
The ethics of hacking for the greater good.
The impact of cyber attacks on healthcare systems.
The role of education in raising cyber security awareness.
The challenges of securing cloud computing environments.
The implications of quantum computing on cyber security.
The importance of international cooperation in combating cyber crime.
The role of cyber security in protecting intellectual property.
The impact of cyber attacks on national security.
The challenges of securing critical data in the cloud.
The role of cybersecurity audits in identifying vulnerabilities.
The impact of cyber attacks on the banking and financial sector.
The ethical implications of government surveillance for cyber security purposes.
The role of cybersecurity professionals in addressing the skills gap.
The challenges of securing personal information in the digital age.
The impact of cyber attacks on elections and democratic processes.
The role of user awareness training in preventing cyber attacks.
The implications of data breaches for consumer trust.
The challenges of securing mobile devices in the workplace.
The role of cyber security in protecting personal privacy.
The impact of cyber attacks on small businesses.
The role of cyber security in safeguarding intellectual property in academia.
The challenges of securing critical infrastructure in developing countries.
The ethical considerations of vulnerability disclosure.
The impact of cyber attacks on the transportation sector.
The role of cyber security in protecting children online.
The challenges of securing Internet of Things (IoT) in smart homes.
The implications of cyber attacks on the aviation industry.
The role of cyber security in protecting against ransomware attacks.
The impact of cyber attacks on the entertainment industry.
The challenges of securing e-commerce platforms.
The role of cyber security in preventing identity theft.
The implications of cyber attacks on the energy sector.
The ethical considerations of government backdoor access to encrypted data.
The impact of cyber attacks on the hospitality and tourism industry.
The role of cyber security in protecting sensitive government information.
The challenges of securing online gaming platforms.
The implications of cyber attacks on the media and journalism.
The role of cyber security in protecting against social media threats.
The impact of cyber attacks on the transportation and logistics industry.
The challenges of securing online banking and financial transactions.
The role of cyber security in protecting against insider threats.
The implications of cyber attacks on the education sector.
The ethical considerations of using cyber weapons in warfare.
The impact of cyber attacks on the retail industry.
The role of cyber security in protecting against insider trading.
The challenges of securing online voting systems.
The implications of cyber attacks on the gaming industry.
The role of cyber security in protecting against intellectual property theft.
The impact of cyber attacks on the healthcare and pharmaceutical industry.
The challenges of securing social media platforms.
The ethical considerations of cyber security in autonomous vehicles.
The implications of cyber attacks on the hospitality industry.
The role of cyber security in protecting against credit card fraud.
The impact of cyber attacks on the manufacturing industry.
The challenges of securing online dating platforms.
The implications of cyber attacks on the insurance industry.
The role of cyber security in protecting against corporate espionage.
The impact of cyber attacks on the food and beverage industry.
The challenges of securing online marketplaces.
The implications of cyber attacks on the pharmaceutical industry.
The role of cyber security in protecting against intellectual property infringement.
The impact of cyber attacks on the nonprofit sector.
The challenges of securing online streaming platforms.
The ethical considerations of cyber security in wearable technology.
The implications of cyber attacks on the real estate industry.
The role of cyber security in protecting against medical identity theft.
The impact of cyber attacks on the telecommunications industry.
The challenges of securing online job portals.
The implications of cyber attacks on the automotive industry.
The role of cyber security in protecting against data breaches in the legal sector.
The impact of cyber attacks on the music industry.
The challenges of securing online auction platforms.
The implications of cyber attacks on the construction industry.
The role of cyber security in protecting against online harassment.
The impact of cyber attacks on the advertising and marketing industry.
The challenges of securing online learning platforms.
The implications of cyber attacks on the fashion industry.
The role of cyber security in protecting against online stalking.
The impact of cyber attacks on the sports industry.
The challenges of securing online travel booking platforms.
The implications of cyber attacks on the beauty and cosmetics industry.
The role of cyber security in protecting against online scams.
The impact of cyber attacks on the hospitality and catering industry.
The challenges of securing online dating applications.
The implications of cyber attacks on the healthcare and wellness industry.
The role of cyber security in protecting against online bullying.
The impact of cyber attacks on the entertainment and events industry.
The challenges of securing online food delivery platforms.
The implications of cyber attacks on the fitness and wellness industry.
The role of cyber security in protecting against online fraud.
The impact of cyber attacks on the home services industry.
The challenges of securing online social networking platforms.
The implications of cyber attacks on the pet care industry.
The role of cyber security in protecting against online piracy.
The impact of cyber attacks on the restaurant industry.
The challenges of securing online fashion retail platforms.
The implications of cyber attacks on the healthcare and fitness industry.
The role of cyber security in protecting against online hate speech.
The impact of cyber attacks on the wedding and event planning industry.
The challenges of securing online grocery delivery platforms.
The implications of cyber attacks on the gaming and entertainment industry.
The impact of cyber attacks on the music and entertainment industry.
The challenges of securing online travel and tourism platforms.
The implications of cyber attacks on the beauty and wellness industry.
The role of cyber security in protecting against online identity theft.
The impact of cyber attacks on the fashion and retail industry.
The challenges of securing online health and wellness platforms.
The implications of cyber attacks on the food and beverage industry.
These essay topic ideas cover a broad range of industries and sectors, highlighting the pervasive nature of cyber security threats. Whether you choose to explore the implications of cyber attacks on a specific industry, examine the challenges of securing a particular platform, or discuss the ethical considerations of cyber security, there are endless possibilities for research and analysis in this field. Remember to choose a topic that interests you and aligns with your objectives, ensuring a rewarding and engaging essay-writing experience.
Want to create a presentation now?
Instantly Create A Deck
Let PitchGrade do this for me
Hassle Free
We will create your text and designs for you. Sit back and relax while we do the work.
Explore More Content
- Privacy Policy
- Terms of Service
© 2023 Pitchgrade
Beyond Intractability

The Hyper-Polarization Challenge to the Conflict Resolution Field: A Joint BI/CRQ Discussion BI and the Conflict Resolution Quarterly invite you to participate in an online exploration of what those with conflict and peacebuilding expertise can do to help defend liberal democracies and encourage them live up to their ideals.
Follow BI and the Hyper-Polarization Discussion on BI's New Substack Newsletter .
Hyper-Polarization, COVID, Racism, and the Constructive Conflict Initiative Read about (and contribute to) the Constructive Conflict Initiative and its associated Blog —our effort to assemble what we collectively know about how to move beyond our hyperpolarized politics and start solving society's problems.
By Omario Kanji
October 2003
In the context of conflict resolution, the definition of "security" depends on one's perspective. At the simplest level, security may be defined as "the quality or state of being secure," "freedom from danger," or "freedom from fear or anxiety." Of the many other levels on which one can analyze security, the most relevant here are individual, group, regional, national, and global. Our task is then relatively simple; we consider how security is defined at these different levels. What emerges is a framework upon which security agreements are constructed and implemented.
Individual Security
On the individual level, security is most often understood as safety. This safety includes freedom from harm, whether physical or psychological. Threats to an individual's security can produce the fear or anxiety mentioned above. The United Nations Universal Declaration of Human Rights states that all people are entitled to "security of person." This declaration reinforces the concept of freedom from physical and psychological harm. Yet, what measures will be taken to protect an individual from harm? The most common forms of protection are legal structures that protect individuals from threats to their security. These include, but are not limited to, laws against murder, sex crimes, bodily harm, theft, and psychological harm such as coercion. The state assumes responsibility for constructing and implementing these legal regulations. In addition, security can be related to one's ability to attain the fundamental physical needs of a home, food, and socio-economic needs such as a job. The concept of individual security can therefore be linked to an individual's perception of her or his standard of living. The individual may thus equate security with a high standard of living.
Group Security
Discussing regional security requires us to first define the extent of the "region." Since we have placed the regional beneath the national level in this hierarchy, we are speaking of a physical area within a nation, which could be a collection of provinces, cities, or states. If there were certain religious, national, or ethnic groups that dominated a region, we would still speak of their security at the group level. What is regional security, then?
The simplest concept of security at the regional level could be economic, implying protection of regional interests. Perhaps a regional association with, or ownership of, a valued resource could provoke desires for security, and the responsibility for protecting that security would rest on the region. For example, labor or trade unions perform this function. Other notions of security at this level could be to maintain a certain standard of living. In this realm, members of a regional group might want to protect themselves from mass immigration, which could occur due to the region's coveted resources. The region might seek to ensure its security by campaigning against this immigration. Threats to security are often cited here, usually connected to issues of lowered living standards. On a more subtle level, religious, national, or ethnic groups may shrewdly promote their interests under the guise of regional security, and may elevate their group security to a regional priority level.
National Security
The definition of security at the group level shares many similarities with the definition of individual security; as the individual expects to have security of person, so does the group. But at the group level, an important aspect of security is freedom from discrimination . While an individual certainly can be mistreated for her or his affiliation with a religious, national, or ethnic group, this mistreatment is more obvious and perhaps more successfully prevented when an entire group is subject to the same mistreatment. We can define the group, i.e., why that group IS a group. Is it due to the similar nationality of its members? Are they a group because they share similar religious beliefs? Whatever the reason, group security may be interpreted as safety from threats to the group's identity . As with ensuring individual security, laws help ensure group security, although laws can also be discriminatory, which is actually one source of intractable conflict.
Regional Security
The national level of security is probably the most often examined and contentious definition of security. The nation-state often assumes the role of guarantor for individual security, group security, and perhaps regional security; for example, agricultural subsidies or steel tariffs are one way in which a nation-state protects a region within its boundaries from a foreign threat.
After ensuring individual, group, and regional security, how does the state define its own security? Lasso and Gonzalez state that "the entirety of conditions -- political, economic, military, social, and cultural -- necessary to guarantee the sovereignty, independence, and promotion of national interest..."[1] defines security. We can then ask what threatens those five conditions. Security from the military viewpoint is highly visible, and a nation will act when it is threatened militarily. Economic threats can also be simply defined, although domestic protectionism can often clash with international trade agreements signed by the same nation. A nation's claim that its protectionism helps ensure national economic security can cause international uproar. (For example, see the essay on Development and Conflict .)
Tension is introduced when a nation defines what in particular guarantees its political, socio-economic, and cultural security. For example, actions undertaken to protect cultures can easily be interpreted as discriminatory or racist. Cultural security is especially difficult to define and protect in heterogeneous, democratic societies such as the United States.
Socio-economic security can also assume controversial definitions and interpretations. Surely a rapidly aging population can threaten socio-economic security. A further question is what measures the state will undertake to solve the problem. Tension can again be introduced if the state or the society chooses to blame a specific group for the threat to socio-economic security. Here, security definitions are at odds since the state is protecting its own security by threatening a group's security.
Perhaps the most ambiguous aspect of security is that of political security, which may be very broadly defined. Often, a nation will react to threats to its political philosophies, as well as threats to its culture, society, or economy. The term "national security" has recently been used to justify "security" procedures within the United States as well as military action outside its borders. This widens the parameters for national security definitions, and implies a wide range of actions available to a nation.
Global Security
Global security is a relatively new concept, and conjures up images of organizations such as the United Nations. Global security, however, may be undermined by national security concerns; if one nation feels threatened by another, then global security cannot exist since members of the world are in disagreement. Global security is also undermined by negative judgment by one nation of another's philosophy of government. If nation A decides that nation B's governing methods are wrong, nation A will not submit to a global authority that allows nation B's methods to continue. Global security is thus a weak concept, since it assumes a supranational entity to whose judgment nations would yield in matters of disagreement. This is obviously a far-fetched goal, which is unlikely to be realized in the near future. As resources such as land, water, and oil are increasingly coveted by nations, global security has little chance to emerge as a durable concept in international relations.[2]
The Security Dilemma
At the national and global level, providing security creates a dilemma. It is generally thought that security is provided with a strong military that can deter attack. Yet, the development of military strength can be seen as a threat by the other side, which then increases its own military investment. This, then, actually decreases both sides' security, rather than increasing it. Security is actually a positive-feedback system. The more security I feel, the more secure my opponent(s) will feel, because I won't have to arm myself against them. But the less secure I feel, the more I will arm, and the less secure my opponent will feel as well. This security dilemma is what fueled the Cold War, the nuclear arms race, and indeed, it is much of what is fueling the conflict between Israel and the Palestinians, Indians and Pakistanis and North and South Korea. (There are other factors in all of those conflicts as well, but security is a big issue.)[3]
The concept of security, on all levels, is related to basic concepts of human psychology. If threatened, people will react and take necessary defensive measures. At the individual level, one can sometimes ward off threats by exercising caution in his or her daily life. He or she may arrange additional security measures, such as alarm systems, weapons, or perhaps changing residences. This same type of reaction may occur on the group or regional level. On the national and global levels, more formal structures of defense and security agreements exist. Nations might activate defense systems to react to overt threats, but this can threaten the other side, thereby reducing security, rather than increasing it. Furthermore, they might cooperate to create security agreements such as NATO, which foster cooperation and collaborative defense and security measures in the face of a perceived threat.
[1] L.H. Lasso, G. Gonzalez, in B.M. Bagley, S.A. Quezada, Eds. Mexico in Search of Security, (University of Miami Press, 1993), 4. < http://www.amazon.com/Mexico-Security-Bruce-M-Bagley/dp/1560006862 >; see also Brian J. Bow, and Arturo Santa Cruz, The State and Security in Mexico: Transformation and Crisis in Regional Perspective (Routledge, 2012). < http://books.google.com/books?id=Am9r_7ftVdoC >.
[2]. For further discussion of global security, including applications to the War in Iraq, Hurricane Katrina, and Weapons of Mass Destruction (WMDs), see: Peter Hough, Understanding Global Security , (Routledge, 2008). < http://books.google.com/books?id=c_B-qty22m8C >.
[3] This paragraph was added by Heidi Burgess. It was not part of the author's original essay, but as editor, I took the liberty of adding it.
Use the following to cite this article: Kanji, Omario. "Security." Beyond Intractability . Eds. Guy Burgess and Heidi Burgess. Conflict Information Consortium, University of Colorado, Boulder. Posted: October 2003 < http://www.beyondintractability.org/essay/security >.
Additional Resources
The intractable conflict challenge.

Our inability to constructively handle intractable conflict is the most serious, and the most neglected, problem facing humanity. Solving today's tough problems depends upon finding better ways of dealing with these conflicts. More...
Selected Recent BI Posts Including Hyper-Polarization Posts

- Massively Parallel Peace and Democracy Building Links for the Week of May 19, 2024 -- Another in our weekly set of links from readers, our colleagues, and others with important ideas for our field.
- Crisis, Contradiction, Certainty, and Contempt -- Columbia Professor Peter Coleman, an expert on intractable conflict, reflects on the intractable conflict occurring on his own campus, suggesting "ways out" that would be better for everyone.
- Massively Parallel Peace and Democracy Building Links for the Week of April 28, 2024 -- New suggested readings from colleagues and the Burgesses.
Get the Newsletter Check Out Our Quick Start Guide
Educators Consider a low-cost BI-based custom text .
Constructive Conflict Initiative

Join Us in calling for a dramatic expansion of efforts to limit the destructiveness of intractable conflict.
Things You Can Do to Help Ideas
Practical things we can all do to limit the destructive conflicts threatening our future.
Conflict Frontiers
A free, open, online seminar exploring new approaches for addressing difficult and intractable conflicts. Major topic areas include:
Scale, Complexity, & Intractability
Massively Parallel Peacebuilding
Authoritarian Populism
Constructive Confrontation
Conflict Fundamentals
An look at to the fundamental building blocks of the peace and conflict field covering both “tractable” and intractable conflict.
Beyond Intractability / CRInfo Knowledge Base

Home / Browse | Essays | Search | About
BI in Context
Links to thought-provoking articles exploring the larger, societal dimension of intractability.
Colleague Activities
Information about interesting conflict and peacebuilding efforts.
Disclaimer: All opinions expressed are those of the authors and do not necessarily reflect those of Beyond Intractability or the Conflict Information Consortium.
Beyond Intractability
Unless otherwise noted on individual pages, all content is... Copyright © 2003-2022 The Beyond Intractability Project c/o the Conflict Information Consortium All rights reserved. Content may not be reproduced without prior written permission.
Guidelines for Using Beyond Intractability resources.
Citing Beyond Intractability resources.
Photo Credits for Homepage, Sidebars, and Landing Pages
Contact Beyond Intractability Privacy Policy The Beyond Intractability Knowledge Base Project Guy Burgess and Heidi Burgess , Co-Directors and Editors c/o Conflict Information Consortium Mailing Address: Beyond Intractability, #1188, 1601 29th St. Suite 1292, Boulder CO 80301, USA Contact Form
Powered by Drupal
production_1
Cybersecurity: The Matter of National Security Essay
Cybersecurity has been an evergreen subject recently. According to Daniele Irandoost, cyberspace has had many benefits in almost every important country’s sector (Irandoost, 2018). The initial intention for developing cyberspace was to open avenues for people to communicate unlimitedly and promote efficiency in operations. Equally, cyberspace has been a safe harbor for criminals to plan and execute operations that can be catastrophic to humanity. A report by the US intelligence indicates technology as the immediate threat to national security. Such a report raises the question of whether the threat of cyberspace outweighs its benefits (Irandoost, 2018). However, if the security of cyberspace is critically evaluated and all the risks eliminated, cyberspace can be an asset that will continue to transform the world (Irandoost, 2018). Consequently, cybersecurity is vital for national security and could cause a disaster unprecedented in the world if it is at risk.
One of the controversial points concerning ethics in this article is a breach of personal data. It is unethical to use someone else’s information without their consent. Most of the crimes committed on the internet involve gaining access to someone’s information and using it for manipulation, intimidation, and blackmailing for financial or political gain. This unethical behavior amounts to fraud and has often been employed on innocent people. Cyberspace has also been the center of spreading false information, causing it to influence public opinion towards an individual or a particular policy, causing great suffering to the victims.
I side with the idea that cyberspace poses a significant threat to national security. My stance is based on the various instances where the internet has been used to cause significant damage to a particular sector. There have been increased hacking cases and bypassing security measures where criminals have gained access to sensitive information. This instance indicates how cyberspace has brought our enemies close than we never imagined. Consequently, a major disaster will strike that will affect the entire nation if cybersecurity is not treated with the sensitivity it deserves.
Irandoost, D. (2018). Cybersecurity: A National Security Issue? . E-International Relations. Web.
- Social Engineering as Internet Threat
- Chemco Crisis Resolution and Public Relations
- Cybersecurity Workforce in Emergent Nations
- Cybersecurity Advancements in Electric Power Systems
- Cybersecurity Dangers and Their Analysis
- The US and Apple Relationship in the Field of Cybersecurity
- Content Analysis of Cyber Insurance Policies
- Cybercrime Effects on UAE Educational Institutions
- Chicago (A-D)
- Chicago (N-B)
IvyPanda. (2023, February 24). Cybersecurity: The Matter of National Security. https://ivypanda.com/essays/cybersecurity-the-matter-of-national-security/
"Cybersecurity: The Matter of National Security." IvyPanda , 24 Feb. 2023, ivypanda.com/essays/cybersecurity-the-matter-of-national-security/.
IvyPanda . (2023) 'Cybersecurity: The Matter of National Security'. 24 February.
IvyPanda . 2023. "Cybersecurity: The Matter of National Security." February 24, 2023. https://ivypanda.com/essays/cybersecurity-the-matter-of-national-security/.
1. IvyPanda . "Cybersecurity: The Matter of National Security." February 24, 2023. https://ivypanda.com/essays/cybersecurity-the-matter-of-national-security/.
Bibliography
IvyPanda . "Cybersecurity: The Matter of National Security." February 24, 2023. https://ivypanda.com/essays/cybersecurity-the-matter-of-national-security/.
Artificial Intelligence and Security
Welcome to the website of the Artificial Intelligence and Security research group at KIT.
Our research group combines machine learning (or AI in the broader scope) and computer security. In particular, we develop methods in system security and application security, for instance, approaches for attack detection or vulnerability discovery in software. Moreover, we research the robustness of machine learning against attacks striving for "secure AI." In this context, we are particularly interested in the security of "Explainable AI" (XAI).
We are part of Karlsruhe Institute of Technology (KIT) and the KASTEL Security Research Labs .

Cyber Security Essay for Students and Children
Cyber security essay.
Cybersecurity means protecting data, networks, programs and other information from unauthorized or unattended access, destruction or change. In today’s world, cybersecurity is very important because of some security threats and cyber-attacks. For data protection, many companies develop software. This software protects the data. Cybersecurity is important because not only it helps to secure information but also our system from virus attack. After the U.S.A. and China, India has the highest number of internet users.

Cyber Threats
It can be further classified into 2 types. Cybercrime – against individuals, corporates, etc.and Cyberwarfare – against a state.
Cyber Crime
Use of cyberspace, i.e. computer, internet, cellphone, other technical devices, etc., to commit a crime by an individual or organized group is called cyber-crime. Cyber attackers use numerous software and codes in cyberspace to commit cybercrime. They exploit the weaknesses in the software and hardware design through the use of malware. Hacking is a common way of piercing the defenses of protected computer systems and interfering with their functioning. Identity theft is also common.
Cybercrimes may occur directly i.e, targeting the computers directly by spreading computer viruses. Other forms include DoS attack. It is an attempt to make a machine or network resource unavailable to its intended users. It suspends services of a host connected to the internet which may be temporary or permanent.
Malware is a software used to disrupt computer operation, gather sensitive information, or gain access to private computer systems. It usually appears in the form of code, scripts, active content, and other software. ‘Malware’ refers to a variety of forms of hostile or intrusive software, for example, Trojan Horses, rootkits, worms, adware, etc.
Another way of committing cybercrime is independent of the Computer Network or Device. It includes Economic frauds. It is done to destabilize the economy of a country, attack on banking security and transaction system, extract money through fraud, acquisition of credit/debit card data, financial theft, etc.
Hinder the operations of a website or service through data alteration, data destruction. Others include using obscene content to humiliate girls and harm their reputation, Spreading pornography, threatening e-mail, assuming a fake identity, virtual impersonation. Nowadays misuse of social media in creating intolerance, instigating communal violence and inciting riots is happening a lot.
Get the huge list of more than 500 Essay Topics and Ideas
Cyber Warfare
Snowden revelations have shown that Cyberspace could become the theatre of warfare in the 21st century. Future wars will not be like traditional wars which are fought on land, water or air. when any state initiates the use of internet-based invisible force as an instrument of state policy to fight against another nation, it is called cyberwar’.
It includes hacking of vital information, important webpages, strategic controls, and intelligence. In December 2014 the cyberattack a six-month-long cyberattack on the German parliament for which the Sofacy Group is suspected. Another example 2008 cyberattack on US Military computers. Since these cyber-attacks, the issue of cyber warfare has assumed urgency in the global media.
Inexpensive Cybersecurity Measures
- The simplest thing you can do to up your security and rest easy at night knowing your data is safe is to change your passwords.
- You should use a password manager tool like LastPass, Dashlane, or Sticky Password to keep track of everything for you. These applications help you to use unique, secure passwords for every site you need while also keeping track of all of them for you.
- An easy way for an attacker to gain access to your network is to use old credentials that have fallen by the wayside. Hence delete unused accounts.
- Enabling two-factor authentication to add some extra security to your logins. An extra layer of security that makes it harder for an attacker to get into your accounts.
- Keep your Softwares up to date.
Today due to high internet penetration, cybersecurity is one of the biggest need of the world as cybersecurity threats are very dangerous to the country’s security. Not only the government but also the citizens should spread awareness among the people to always update your system and network security settings and to the use proper anti-virus so that your system and network security settings stay virus and malware-free.
Customize your course in 30 seconds
Which class are you in.

- Travelling Essay
- Picnic Essay
- Our Country Essay
- My Parents Essay
- Essay on Favourite Personality
- Essay on Memorable Day of My Life
- Essay on Knowledge is Power
- Essay on Gurpurab
- Essay on My Favourite Season
- Essay on Types of Sports
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Download the App

SafeHome.org may receive compensation from some providers listed on this page. Learn More
We may receive compensation from some providers listed on this page. Learn More
Home Security Systems: Your Options for 2024
What we've learned from more than 1,000 hours of research...

Home Security Systems
A list of security systems reviewed in 2024
Security System Finder
Get matched with the perfect security system.
Compare Security Systems
Have a few brands in mind? Compare them.
Security Cameras
A list of 2024's top rated home security cameras.

Getting to Know Home Security Systems
Your home is undoubtedly one of the most important places or spaces in your life. It’s where you sleep at night. It’s where you create memories with your family. It’s where you should feel most safe and secure.
Unfortunately, the sanctity of this safety is violated with frightening frequency. According to the FBI, approximately 2.5 million homes are burglarized every year. 1 That doesn’t mean you have to sit back and wait to be a victim, though. There are proactive measures you can take to protect your family and your property.
For many people, that means installing a high-quality home security system . There’s really no better way to prevent burglars and thieves from snooping around where they shouldn’t, and you can’t beat the peace of mind that comes from knowing you can summon help in seconds (or at least minutes) during an emergency situation.
That said, selecting which security system is right for you can be a little daunting. And we get why. You might have questions about installation: do you need to have someone out to install it, or are you handy enough to do it yourself? Questions about features: what’s better, battery-powered or hardwired cameras? And don’t forget questions about money: how much does it all cost? It can be tricky to know where to start.
Don’t worry. We’re here to help.

SimpliSafe Equipment
To say that shopping for a home security system can be daunting is a profound understatement. There is a lot to consider, but don’t worry — we’ve spent countless hours testing security systems in our home. After reading this guide you’ll be up to speed on everything you need to know about home security, and it will hopefully make your purchasing decisions a lot more clear.
This guide covers absolutely everything you need to know about home security systems. We get into features and accessories, costs and contracts, and even touch on a few factors you might never have considered. But let’s not keep beating around the bush. Let’s get to it.

What are Home Security Systems?
Let’s start with the basics: just what is a home security system. Probably the best definition of a home security system is a network of connected sensors and other equipment that work cooperatively to protect your home. All of these devices are designed to let you know when there’s a problem – a fire, a flood, a break-in – so you can contact emergency personnel.
Another way of defining a home security system is to talk about its various components. There are a lot of choices.
- Entryway sensors
- Motion sensors
- Base stations
- Security cameras
- Video doorbells
- Home automation devices such as smart locks and thermostats
Floodlights
- Panic buttons
- Glass break sensors
- Keychain fobs
- Smart smoke detectors
- Smart carbon monoxide detectors
- Water leak detectors
In fact, probably the best way to understand home security systems is to focus on each one of these pieces of equipment in turn, so you get an idea of how a system can protect you.

Entryway Sensors

Vivint Door and Window Sensor
- Core Function — Also called door and window sensors, they are the backbone of a home security system. They sound the alarm when a door or window is open (and the alarm is set). This deters criminals and alerts the homeowner of a security breach.
- How it Works — Entry sensors come in two parts, a magnet and a sensor. The two components form a magnetic field when in close contact with each other. However, when the door or window they are attached to opens, the magnetic field is disturbed and the sensor signals the base station to sound the siren.
- Key Features & Tech — Once upon a time entry sensors had to be bolted to doors and windows, and you might still find that with some professionally installed security systems. DIY systems have grown more and more popular though, and these typically offer easy adhesive or velcro installation that you can do yourself, no tools required. In either case, when a sensor is triggered, the system sends you a mobile alert.
- Add-ons and Integrations — Some systems allow users to automate IoT devices based on the entry sensor’s status. For example, when a door opens, the base station can signal smart lights to turn on. We recommend installing an entry sensor on every possible first-floor entry into your home and on any accessible second-floor windows. However, you can purchase entry sensors to protect every door and window in your home.
Motion Sensors

Cove Motion Detector
- Core Function — Motion sensors sound the alarm and/or trigger mobile alerts when motion is detected inside of the home. They are meant to be used as an added layer of protection.
- How it Works — These devices emit an invisible light/laser, which when disturbed sounds the alarm. Some motion detectors (like the one pictured below) use infrared technology that can sense body heat. The simplest of these sensors, called PIR (passive infrared) sensors help avoid false alarms by triggering only when a moving object emits body heat. That mean s leaves blowing by or a passing car won’t set them off. More sophisticated “active infrared” sensors can distinguish between different types of objects, which helps to prevent pets from setting off alarms.
- Key Features & Tech — Motion detectors can be integrated into other types of equipment. A motion detector might be connected to a floodlight, for instance, so that movement triggers it to come on. Attaching a motion detector to a security cameras allows for even more features, such as video capture and even facial recognition.
- Add-ons and Integrations — As with entry sensors, most motion sensors can be connected to smart home ecosystems and configured to perform interconnected actions.

Lorex cameras
- Core Function — Security cameras are mounted inside and outside of the home to keep a constant watch for safety. Many cameras record continuously and notify the homeowner when activity occurs. Just the presence of a camera is sometimes enough to deter a criminal.
- How it Works — Today’s cameras offer continuous recording or motion-activated recording. Either way, they record video and often send real-time alerts. You’re the first to know if it is the pizza guy or a porch pirate on your property.
- Key Features & Tech — The best cameras deliver HD image quality, mobile access with live-streaming, two-way voice, pan and tilt, and more.
- Add-ons and Integrations — Many cameras integrate with existing home automation platforms like Nest, HomeKit, etc. You can configure your cameras with various rules, such as setting it to record every day at 3 p.m. when your kids get home from school.
Video Doorbells

Ring Video Doorbell 3
- Core Function — A first line of defense, video doorbells help to protect your home from package thieves and burglars. Many doorbell cams let you see and talk with front-stoop friends and visitors from virtually anywhere. Homeowners and neighbors have even used them to identify car thieves. With car theft on the rise, these cameras are a welcome tool for many.
- How it Works — The easy DIY video doorbells replace your existing doorbell. They sport a small camera that either records video activity or takes still shots. In the simplest setups, you can access images yourself so you know what’s happening in and around your home. Some systems, though, allow you record footage you can then turn over to the police. Oh, and of course, it works like a doorbell, too.
- Key Features & Tech — Mobile access, monitoring, and control via mobile app is perhaps the best feature to look for in a doorbell camera. Other features include HD image quality, cloud storage, night vision, two-way talk, and more.
- Add-ons and Integrations — Similar to home security cameras, some doorbell video cameras can be integrated into home automation ecosystems for more convenient (and smart!) controls.
Home Automation Controls

Vivint App Package Notification
- Core Function — Home automation streamlines everyday tasks to make our lives easier and more efficient. Smart controls allow users to remotely control and automate everything from lights and thermostats, to garage doors, cameras, and even coffee makers. Home automation also enables families to ensure the safety and security of extended family members — like older loved ones who are aging in place .
- How it Works — Depending on the platform, smart home automation controls work via mobile commands (smartphone or tablet), voice commands, or both. You set the rules, and the house reacts accordingly. Turn down the lights!
- Key Features & Tech — The features and tech range from simple commands (like turning on a reading light) to powerful AI-driven surveillance technology. It’s up to the user to decide how futuristic they want their home. The sky’s the limit with smart home automation controls.
- Add-ons and Integrations — Many platforms can support literally hundreds of smart devices. This means users can customize their systems to their heart’s content. Most hubs work with devices that use Z-Wave , Zigbee , IFTTT , and more. A lot of them also work with voice assistants like Alexa and Google Assistant to allow for hands-free voice control.

Ring Floodlight
- Core Function — Floodlights’ primary purpose is to shine a light on suspicious activity. After all, the perimeters of many homes can be dark, thus making them especially vulnerable to intruders. They also help with visibility at night for guests entering and exiting, especially seniors who don’t see as well.
- How it Works — These motion-activated devices “flood” a yard or driveway with a bright light. Criminals prefer the cover of darkness, and floodlights completely eliminate the dark and expose the bad guys.
- Key Features & Tech — Many floodlights can be mounted in just minutes. Most boast ultra-bright LEDs, and some have a built-in siren that sounds when motion is triggered. Today’s best floodlights double as security cameras.
- Add-ons and Integrations — Depending on your platform, you can set customizable motion zones, custom scheduling, fully integrate into a smart home ecosystem with mobile controls, and the list goes on.
Panic Buttons

Vivint Smart Hub Settings
- Core Function — These wall-mounted devices have a built-in help button. The life-saving button is pressed in the event of a medical emergency or home invasion. They summon help immediately.
- How it Works — Many control panels have a built-in panic button that works via landline, Wi-Fi, or cellular to send a signal to the monitoring center (if the user has professional monitoring). In a time of crisis, simply press the panic button and rest assured that help is on its way.
- Key Features & Tech — These devices are fairly simple. And simple is exactly what you want when precious seconds could save a life. Some control panels with panic buttons have two-way voice so you can talk directly with responders.
- Add-ons and Integrations — N/A
Glass-Break Sensors

SimpliSafe – Glassbreak Detector
- Core Function — As the name suggests, glass-break sensors detect glass breaking. The moment a security breach is detected, the alarm sounds and alerts are sent. These sensors are often sold separately, but they’re highly effective and work well alongside of magnetic window sensors.
- How it Works — Mount them near a window, as the sensors have tiny microphones that detect the high-frequency sound of glass breaking. When glass breaks, the sensor triggers the alarm and alerts, hopefully making the burglar tuck tail and run.
- Key Features & Tech — N/A
Keychain Fobs

abode Key Fob
- Core Function — Keychain fobs allow users to remotely arm and disarm their system. Many keychain touchpads also include a panic button, which offers peace of mind when coming and going in the dark.
- How it Works — Hook the small device to your keychain, or keep it in your pocket or purse. If you forget to arm your system when you leave your home, just take out your keychain fob and you’re back in business. These devices are powered by batteries, and are helpful if your system doesn’t offer mobile access.
- Key Features & Tech — The best keychain fobs have a long battery life and are small enough to not be a bother. While most have remote arm/disarm buttons, not all include a panic button.
Smart Smoke Detectors

SimpliSafe – Smoke Detector
- Core Function — Fires often happen when the homeowner is away, rendering the traditional smoke detector useless. But a smart smoke detector not only sounds the alarm, it also sends real-time alerts to your smartphone.
- How it Works — The device is app-based, so you can be up and running within minutes. You can access and control the smoke detector just by opening the app, then monitoring any potential situations.
- Key Features & Tech — Smart smoke detectors often send low-battery notifications straight to your smartphone, integrate with IFTTT and other smart platforms, offer helpful voice instructions when smoke is detected, and more.
- Add-ons and Integrations — Most smoke detectors offer seamless integration with third-party platforms. Also consider CO detectors and water leak sensors (mentioned below).

Smart Carbon Monoxide Detectors

Vivint Smart CO/Smoke Detectors
- Core Function — These life-saving devices send real-time alerts and notifications to your mobile device. That way, you’ll never walk into a home with a CO leak and risk a potentially fatal outcome.
- How it Works — Similar to the smart smoke detectors, these devices come pre-configured and ready to go. Just plug it in and follow the easy setup instructions in the companion app. Anytime it senses CO, the alarm will sound and you will get an instant alert(s). Note that many companies have begun offering devices that offer both smoke and CO detection. See the Vivint detector in the picture above.
- Key Features & Tech — Users should look for long battery life and a sleek companion app with convenient mobile access and controls.
- Add-ons and Integrations — Connect a smart CO detector into a home automation system to access everything on one user-friendly dashboard.
Water Leak Detectors
- Core Function — This device is worth its weight in gold, as water damage can be devastating. If your home springs a leak while you’re away, don’t worry, a water leak detector will notify you, allowing you to call the plumber asap.
- How it Works — Put the sensor near faucets and other appliances/fixtures that have the potential to leak. If (or when!) a leak occurs, the sensor will sound an alarm and send you a mobile alert.
- Key Features & Tech — Some water leak detectors communicate with smart water valves to shut off your water at the source (if needed), thereby limiting or even eliminating water damage. Smart! Some water leak sensors also have built-in freeze, flood, and humidity sensors, too.
- Add-ons and Integrations — Same as smoke and CO detectors listed above.
In other words, a home security system is a network of electronic devices that protect and secure your home or apartment from criminal activity such as burglars, thieves, and home intruders.
Pro Tip: While an increasing number of companies are offering DIY installation, some still require professional installation. Keep in mind, though, having your system professionally installed will likely cost you north of $100.
How Do Home Security Systems Work?

Cove Installation Steps 1-2
The most basic home security systems will primarily use door and window sensors that communicate with a central hub. When the system is active and a door or window opens, the sensor will notify the hub which will send out an alert or sound an alarm. Some systems will even alert the authorities if you have professional monitoring set up. From there, your system can get more complex by adding on sensors, security cameras, and other pieces of equipment, but we’ll get into that more later.
Now, if the security system is set up with professional monitoring, the control panel will immediately notify the monitoring station. Once the monitoring station personnel are notified of the security breach, they will take necessary action, which usually begins with a call to the homeowner. However, in some cases, they can communicate with the homeowner directly through the system’s control panel (if the system has a neat feature called 2-way talk, which we will discuss later).
Thankfully, a lot of the time alarms are false. This can be for any number of reasons — maybe you forgot the alarm was set and opened a window; maybe your dog set off the motion detector — but regardless of the reason, your monitoring staff will still reach out to you. If it is a false alarm, you can let them know what’s going on. If you don’t respond, though, most will then escalate action and alert authorities.
Keep in mind that we’re always testing home security systems to see how they perform. To check out our results on the most responsive security companies, read our guide to home security company response times .
Security systems that aren’t linked to professional monitoring centers are referred to as non-monitored or self-monitored systems. As these names suggest, the task of monitoring and responding to alerts falls entirely on the shoulders of the homeowner. They have to be ready for alerts, they have to be willing to check the system and see what’s happening, and, if there is an emergency, they’re the ones who must call in emergency personnel.
There are loads of great do-it-yourself security systems that secure the home in that way, and one feature they all share in common is the ability to notify homeowners remotely, which helps the homeowner to take immediate action.
The majority of self-monitored systems rely on text-based alerts that are sent to your smartphone via push notifications. Depending on how detailed they are, you might get a message saying “hallway motion sensor activated” or “there is a person at your gate.” If you have cameras in place, you might also be able to see what’s going on. Some folks feel this is enough protection, but others might feel more secure if a professional was also alerted.

There’s yet one more way security systems work that’s worth mentioning: simply having one can be an effective deterrent to anyone who might be thinking about breaking in. Video doorbells and outdoor cameras can alert would-be home invaders that you’re keeping a close watch on your property, but truthfully all you need to do this is put your security company’s sign in your yard. Even the idea of a security system scares most burglars. It’s another good reason to display signs and stickers where they’re obvious.

Deep Sentinel Yard Sign in our yard
How does your home measure up when it comes to security? Take this quiz to see how you score, and get recommendation to protect your home.
Benefits of Owning a Security System for Your Home
There are tons of benefits to outfitting your home with a security system. For one, it can cut down the chances you’ll fall victim to a burglary or a home invasion .
While that alone would be enough to convince most people to invest in a security system, here are the top 5 that you should consider:
- Benefit #1 – Protect your family. You and your family can remain safe and secure. The peace of mind families get from home protection is profound.
- Benefit #2 – Protect your home and valuables. Remember, most criminals won’t even bother if they see you have an alarm system in place. Others might try, but they are often scared off at the sound of the alarm. This means your home and valuables are protected from damage and theft.
- Benefit #3 – Detect potentially fatal dangers. This goes beyond burglary — security systems can detect in-home hazards such as smoke, fires, carbon monoxide, etc. Many security systems will automatically detect these dangers and immediately notify the monitoring station. Early detection keeps everyone (and everything!) much safer.
- Benefit #4 – Control your home remotely. Many of the advanced systems allow the homeowner to remotely control everything from door locks to security cameras, lights, heating, air, entertainment, and of course, the alarm itself. This allows the owner of the system to enjoy a more convenient and novel lifestyle, and at the push of a button.
- Benefit #5 – Get home insurance discounts. This is a great benefit that helps where it matters… right in the pocketbook. Insurance companies view homes equipped with home security systems as less of a risk or liability. Therefore, they will often discount your home insurance premium (sometimes up to 20%) if you can prove you have a system in place.

Police Officer Sent to Our House from Cove Monitoring
Is a Home Security System Right for Me?
The long and short of it is this — your home security should be thought of just like any other system in your home. You wouldn’t really go without an HVAC or an electrical system, and your security — we feel — is even more important. Even more so now, given how accessible and affordable these systems are .
But how do you really know if a security system is right for you, and not just another thing to purchase in hopes of easing paranoid delusions? Well, if you find yourself nodding “yes” to any of the following, then a home security system is absolutely right for you.
- You live in a high-crime area, with reported home break-ins
- You live in a low-crime area (any home can become a target)
- Your home has been broken into in the past
- You travel frequently or are out-of-town often
- You are a senior who lives alone (or have older parents who live alone)
- You have small children at home and want to feel protected
- You enjoy easy-to-use technology that makes life a little easier
- You have valuable possessions or keepsakes in your home
- You’ve noticed ‘unsavory’ characters roaming your neighborhood
- You live in a region that experiences natural disasters (i.e. fires, flooding)
Most households will find at least some benefits to owning a home security system. Also, it’s worth noting that many systems do not require a long-term contract. So if you’re truly on-the-fence about getting home security, then perhaps try an easy-to-install DIY kit with no monthly fees or contracts. That way, if you find it isn’t right for you, you can rest easy knowing you haven’t invested too much.
List of Home Security Companies
- AT&T Digital Life
- Cox Homelife
- CPI Security
- Deep Sentinel
- Link Interactive
- Protection One
Home Security Companies by Subscribers

Source: https://www.sdmmag.com/2019-SDM-100-Rankings
Note that some of the largest companies, such as ADT and Brinks Home Security, are not ranked because such detailed information was not publicly available or they did not report it to SDM. Companies that reported fewer than 1,000 residential subscribers are not included in this ranking.
Perhaps most interesting about our list above is the diversity of home security companies represented. Each company takes a different approach to home protection. Each company has a particular target demographic, a specific philosophy, value proposition, company culture, etc.
And while no company is a great fit for everyone , every company is a great fit for someone . So it just takes a little homework to find the company and system that’s right for you and your home.
The good news is, you don’t have to do that homework yourself. That’s what we’re here for. We spend all our time–more than a thousand hours a year, in fact—putting security systems through their paces. We find out what it takes to trip a SimpliSafe motion sensor, just how loud a Ring Chime is, and how much you’ll pay to add a camera to your ADT system. Then we condense it all and write it up in clear, easy-to-understand language so all you have to do is read through guides like this one.
How Much Do Home Security Systems Cost?
We’ll share a cost-comparison chart in just a bit. But first, it’s important to understand the different pricing structures typical of home security systems. The last thing you want is to be taken for a ride and find yourself upside-down in your security system. So here’s what to look out for…
While finding the right home security system to fit your needs should be your main focus, the cost will likely be a major consideration. When assessing costs, it’s important to determine how much you’ll really be paying. Don’t just take the pricing the company advertises at face value.
Here’s why: Many security companies like to offer monitoring services “starting at” a particular price. They may also advertise “as low as.” But more often than not, the “as low as” price is lower than what you’ll end up forking out for your monitoring system. So remember, there’s more to the total cost than the initial, advertised price.
An additional piece of advice: be on the lookout for sales. Many home security companies offer seasonal discounts. For example, at the time of this writing, SimpliSafe was offering a 50 percent discount for any new system.
Pro Tip: Home security systems are great, but to get true peace of mind at home, don’t forget to keep a list of resources handy in case you need immediate help or are concerned about your family’s safety. Check out our in-depth safety and security resource guide for more.
When searching for a security system, typically the only price you’ll see upfront is the monthly fee. However, most security systems also have installation fees, activation fees, and sometimes even equipment fees, as well as taxes and surcharges to add on. Don’t let this scare you away, but do keep it in mind.
5 Common Home Security Fees to Consider

You’ll want to compare the upfront costs to the long-term costs of each security system. You might find your $20 a month advertised bargain monitoring contract ending up costing you, say, $45 a month after you add on all the fees and other charges.
Look at the overall costs of the different systems and options, add it up, and compare the costs between the various security companies you’re considering. You might be surprised at what you find. For instance, a company advertising “free installation and activation” may have a high monthly fee, making it more expensive than a system that does charge an installation fee but waives the monthly fee.
There’s one last thing to consider when it comes to pricing. Some home security providers rent out equipment rather than sell it outright. This means your initial cost will be lower, but you’re going to be paying a higher monthly fee, and you can’t take your equipment with you when you go. Some people prefer one over the other, but it’s really a matter of preference and budget.
On the other hand, it could end up costing you more than if you had rented the equipment and paid a higher monthly fee, but with a much lower upfront price. Here’s the point: Look at the overall costs, do the simple math, average out the numbers, and find the best deal . You’ll be glad you did.
Here’s a side-by-side cost comparison of some of the best home security systems:
Did you notice the pricing comparison chart (above) lists the four different cost breakdowns? Now notice how none of these companies charges only a monthly monitoring fee. They each have other costs to factor in – from installation and activation costs, to equipment costs. This is typical of most home security companies. So keep it in mind while shopping around to find the best value on home protection.
Do You Own or Rent Your Home? This Helps to Determine Which Security System is Right for You.
Now consider your personal living situation. Do you own your home, or are you renting? This matters greatly, as it will influence the type of system you choose and the money you will spend.
When you own a home, you have different factors to consider when choosing a security system. Homeowners typically stay in place for longer than renters, so they often choose a system with longevity in mind. This allows them to spread the costs over a longer period of time. Also, homeowners can make major changes or modifications to their home, so this might influence their decision.

SimpliSafe Base Station Closeup
Renters , on the other hand, may need to seek a landlord’s permission to make changes to the home. They may also be hesitant about spending a lot of money to purchase a system they may not be able to take with them when they move.
Also, there are contracts to consider. A renter must be careful not to lock themselves into a contract they might not be able to get out of. If you rent, consider contract lengths for rental or purchase/rental options that allow you to keep the system and take it with you when you move.
Now, this isn’t to say that home security options for renters are thin pickings. Quite the contrary – more and more companies are offering fantastic security systems for renters at affordable prices.
FYI: Thinking of taking your home on the road? Learn about some easy security options for recreational vehicles in our thorough buyers guide to RV security systems .
Buying Home Security Equipment vs Leasing
If you’re renting, consider how long you plan to stay at your current location. If you’re only staying for a couple of years, then look into a security system with do-it-yourself (DIY) installation and purchased equipment, rather than something that’s leased.
Now we get that this might seem counterintuitive, but the reason is that most security companies that lease out their equipment will require professional installation and a mandatory long-term contract. That’s a pretty big commitment for a renter, and usually a waste of money. If you decide to leave, you still have to pay to cancel the contract. Note though, that some providers will allow you to transfer your system to a new property, but that usually comes with contract renegotiations.
If you purchase a DIY system, it moves with you when you go. It takes minimal effort to take down and set up most DIY systems, and some companies will even send you a care package of fresh adhesives for your sensors and other installation must-haves if you tell them you’re moving.
If you own your home, and are planning to stay awhile, you may want to choose a more permanent solution with a lower upfront cost but longer contractual obligations. If you’re renting (or are a homeowner but plan to move in the near future) consider going with a company that has a higher upfront cost, but that gives you ownership of the equipment. This way, you’ll see lower monthly costs and the benefit of being able to take the equipment with you when you move.
Did You Know? Amazon is pretty generous on doling out home security systems deals and discounts on Prime Day. To find some great savings, head over to our rundown of The Best Amazon Prime Day Deals on Home Security Systems .
Another benefit of owning the security equipment is that you can source extra sensors (and other options) from commercial retailers, rather than having to buy direct from the company. Full service companies typically charge premium fees for their equipment. Looking elsewhere is yet another way to save money.
If you prefer to lease equipment rather than purchase, the upfront cost will definitely be lower, but in reality you’re still paying for that equipment over time, most likely in your monthly service fees. So again, consider the overall cost. Additionally, if you want extra sensors or fancy options or add-ons, the cost of that monthly subscription may rise.

Alder Security Equipment
Or… you may simply be told that you cannot get the options you want. Sometimes the company won’t have what you’re looking for, doesn’t offer it to customers in your area, or has compatibility issues that were not considered. You’ll want to think about the scalability of the system you sign up for, especially if you want to upgrade or make changes to your system down the line.
What to Look For in a Home Security System
Home compatibility.
Here’s another big factor to consider. It’s important that your monitoring system is compatible with your home. Overly sensitive alarms leading to false alarms can cause a nuisance, while on the other hand, you do not want an alarm that doesn’t sound when it should.
Note that some systems are better for certain areas and living conditions. For instance, some systems are well suited for rural areas, while others can be used pretty much anywhere.
With this in mind, there are three connectivity types that will power your system, and these are:
Let’s take a closer look at what these options are all about, and to see which is right for you.
Today, most modern security systems rely on broadband, which means they need a Wi-Fi connection to function properly. Wi-Fi is best for home automation systems. Although the availability of broadband connectivity has dramatically increased in recent years, not every house has this type of connection, especially in rural areas. Or, such areas may have broadband connectivity, but poor or unreliable coverage due to the location. Obviously, this presents a problem, as you need a security system that offers reliable 24-hour service for peace of mind.
If broadband or Wi-Fi is an issue, you may want to consider a security system that utilizes a landline. Landline monitoring is the least expensive option, but it’s not always the most secure. If a criminal wants access to your home, they could easily cut the wires and disable the entire system. While this is always a possibility (and therefore a concern), it’s actually not too common.
Cellular is least susceptible when it comes to tampering, but it also tends to be the most expensive of the connectivity options. If you do go with cellular, you must ensure your area has good cellular coverage. If it doesn’t, you won’t be able to reliably access your security system remotely to check on alerts or to view security camera live-feeds.
You also need good coverage so that your security equipment can communicate with the monitoring station and work with compatible devices and sensors. Think of it in the same way your computer wirelessly connects to your printer and interacts over the same network. If you have a security system with remote sensors and a smartphone app, all of this technology needs to properly interact in order to make your system truly safe and secure.

Closeup of Deep Sentinel Camera, mounted Outside
Home Automation Options
Our homes also differ in terms of intelligence. Whether you have a brilliant smart home now, or you have plans to make yours smarter in the near future, it’s important to consider whether the home security system you purchase is going to play well with it. In our increasingly connected world, it’s not always a given that devices will work with specific platforms. When you start thinking about smart devices like toasters, refrigerators, and televisions, it can get even more confusing. Good home security systems are compatible with all the top smart platforms, including Alexa, Google Home, and Apple HomeKit.
You’re particularly savvy, though, so you’ll also want to consider what kind of contol your system provides through your smart platform. Will you be able to unlock your door remotely using your phone, control the AC and turn on your lights with just your voice?

Person Detection on the Vivint Smart Hub
You’ll find that some equipment is compatible with almost everything, while other equipment is only compatible with specific systems or devices from the same company/brand. For instance, you may find it hard to search for a security system that works with smart thermostats from Google Nest, even though they’re some of the most popular smart thermostats today. That’s because the Nest Thermostat doesn’t support Z-Wave, which is what most security systems use today for inter-brand communication.
Additionally, getting each and every device to communicate properly, and to maintain this functionality, can be frustrating and difficult. However, the more compatible a security system is with other smart technology in the home, the fewer problems you’ll have with the system and its components.
So be sure to look into the platforms that your system works with.
Common Features Found in Home Security Systems
For many, the features of a home security system are incredibly important and top the list of things to consider when it comes time to buy. However, you need to strike a balance between the features you want and how much the system costs. Also, you wouldn’t want to pay for features you don’t need and won’t use, which can happen when you purchase standard home security bundles.
Don’t fall into this trap. Instead, save money by choosing a system that meets your needs perfectly, and only pay for what you are going to use. For instance, why pay for a security bundle with ten window sensors when you only have six windows? That’s money down the drain.
So write down exactly what you want monitored in your home or apartment, and then make sure the system that you’re considering checks all of the boxes (equipment, devices, add-ons, etc.) to meet your needs.
However, it’s generally better to have too many features than it is to have too few features, so be sure to do your homework. Also, it’s important to note that almost all major security companies will customize a system that works specifically for your home and budget.
Here’s a comparison of some of the most common features available from a few of the top rated security companies:
Now, here are the most common options and features to look for when shopping for a security system:
- Control Panel – A control panel monitors the security equipment, has a siren or other alarm, and can communicate with emergency dispatchers. Some control panels have a simple digital display, while others may feature a full-color touchscreen for managing the system. But it’s the 21st century after all – so the majority of people are controlling their systems from their smartphones. This is why a sophisticated touchscreen digital display is becoming less and less of a selling point.
- Remote Control – Most home security systems now offer remote controllers that fit onto keychains. These typically have a convenient button that can arm and disarm the security system, and can alert the monitoring station if there’s an emergency or break-in. These remote controls are a quick and easy way to access your system, and they work very much like the key fob that comes with many new cars on the market.
- Motion Sensors – These sensors are generally placed at entryways and in large rooms. As the name suggests, motion sensors send an alert (or alarm) whenever they detect motion, and they often work hand-in-hand with security cameras (they activate the cameras to record the motion). This way, you’ll be able to see the perpetrator (or the plant that fell from the counter) and even keep a recording of it for evidence or what have you.
- Door and Window Sensors – These are similar to motion sensors, but they only detect if the window or door they are attached to is opened. These can be great for doors and windows that are on the other side of your house, or the rooms you visit less frequently.
- Freeze Sensors – These sensors will alert you about very low temperatures that could potentially freeze pipes. This allows you to wrap the pipes or take other preventative measures to keep pipes from freezing and breaking.
- Heat Sensors – Different from smoke alarms, these sensors are set off by rapidly rising temperatures indicative of fire. They do not need to detect smoke to be activated, so if there isn’t much smoke present (or the smoke is blowing the other direction) these sensors will still work to help keep you and your home safe and secure from a potentially catastrophic house fire.
- Flood Sensor – Most useful in flood-prone areas with basements, Flood Sensors alert you when water levels are detected so that you can take the necessary action to prevent further damage to your home.
- Glass Break Sensors – These sensors are set off by the high frequency sound of glass breaking, alerting you of vandals or burglars. Needless to say, if someone breaks your window to gain access to your home and valuables, you’ll be the first to know.
- Security Cameras – Security cameras can provide video recordings and a live view of your house and surroundings. Motion sensor security cameras can detect the slightest movement and begin recording immediately. You can also monitor your property remotely using your smartphone if your particular system allows for it. This feature is especially important if you travel or work long hours. They can even help protect your pets! To find your perfect fit, see our favorite security systems with cameras .
- Home Automation – Installing a security system in your home is a convenient occasion to add home automation. Home security companies provide mobile apps that can control home lighting, thermostats, surveillance cameras, and more. But be sure to carefully check equipment compatibility. To help you on your way, here’s a list of our favorite home security systems with automation .
- Carbon Monoxide Detectors – These detectors will alert you if and when the carbon monoxide in your home reaches life-threatening levels. As you likely know, carbon monoxide is colorless and odorless, so you may not realize there’s a leak until it’s too late. But with a quality carbon monoxide detector, you can rest easy knowing you’re covered.
- Smoke Alarms – Smoke alarms alert you of high levels of smoke, signaling a potential fire. Although they are often purchased with a battery and used separately from your system, having a smoke detector wired into your house and into your alarm system is a smart choice for most homes. This solution is safer and can reduce the risk of loss when it comes to life and property.
- Two-Way Voice – Another nifty feature, two-way voice allows you to speak directly with the call center of your security system monitoring service. You can two-way talk either through the control panel in your home, or remotely with another device such as a smartphone (if your system allows for it). You can let the monitoring station know if it’s a false alarm, or if there’s a serious problem like a medical emergency or security breach.
- Mobile & App Support – Mobile access for home security systems enables you to monitor and control your home remotely, from anywhere in the world. A smartphone, tablet, or desktop computer can be used for arming a system, viewing live security video, controlling lights, unlocking and locking the door, and even controlling the air conditioning.
- Guarantees and Warranties – Many companies offer warranties for their equipment that covers equipment failure within a given time frame. They may also provide relocation guarantees with discounted or free installation services, in the event you move while still under contract. Not all companies offer guarantees or warranties, so go over the contract with a fine-toothed comb before you sign it.
- Cellular Monitoring – Many alarm system control panels use cellular signals to communicate with emergency operators. Others use landlines or broadband internet connections as mentioned previously. Cellular systems are generally the least vulnerable to tampering, but they are also the most expensive. Be sure to learn which type of connection the company offers before signing up for an alarm system.
- Landline Monitoring – Landline monitoring provides the most stable connection when a reliable cellular or Wi-Fi network isn’t available. Traditionally, landline home security was the least expensive, but cellular networks today are becoming more affordable. Also, as we discussed, a landline connection carries a certain risk. That is, a burglar can cut the wires to disable your system. While this isn’t common, it’s something to keep in mind.
- Flood Lights – Often combined with motion sensors, flood lights can be used to light up a large area so you can see who is on your property and scare them off.
Home Security Installation Methods

Installing Vivint Outdoor Camera Pro
Installing home security systems can be overwhelming, so for some people it’s best left to the professionals. However, if you count yourself among the DIY crowd, there are many systems that can be easily installed by homeowners and renters; this can also save you a lot of money. With that said, there are benefits and drawbacks of both installation methods. So let’s have a closer look.
Professional vs DIY Installation
Professional installation ensures that everything is up and running properly. And the installation professional can give you a walkthrough of the system so that you can familiarize yourself with the different features and how to use them. This option is best for those who will be living in their current home for a long time. However, if you think you’re going to move relatively soon, then a system with DIY installation may be the best choice for you. It will certainly save you money.
So ask yourself an important question: “What type of person am I?” Professional installations are best for busy adults, non-tech-savvy people, and those who aren’t good with tools (although many DIY systems only require a single screwdriver for setup). The elderly may also benefit from getting professional installation, rather than over-burdening themselves with a DIY option.

Frontpoint Door Sensor vs Ring Sensor
But if you have the time and the skills, DIY installation is a smart choice. Many companies that offer DIY installation have comprehensive manuals – and even video tutorials – on how to set everything up. Also, companies now provide easy-to-use apps that will guide you through the connectivity between devices and the control panel.
One of the main issues with a DIY system is that if problems arise during the setup, it’s going to be between you and the customer service team to figure them out. What seemed like a quick setup could turn into hours of troubleshooting and headaches trying to describe what’s going on to folks who aren’t there looking at it. These problems aren’t the norm, but if you don’t have the troubleshooting skills — or time, or patience — it’s something to consider.
Finally, it’s also worth noting that wireless systems usually do not need professional installation. Such systems are virtually plug-and-play, with no wires to run through walls, and user-friendly connectivity processes. These wireless systems allow for easy-install with basic tools and minimal skills.

abode Gateway
Let’s look at some of the pros and cons of both types of installations:
Professional Installation
- It can be a major time saver – Unless your home security IQ is especially high, DIY installation can take a good bit of time. The more high-tech your system, the more time. It’s not just about unboxing, running lines, and connecting equipment to hubs and smart devices either. You have to know exactly where to place your equipment if you want to actually improve your home’s security. With professional installation, you don’t have to spend hours toiling over what goes where, getting everything drilled and screwed in, then realizing it doesn’t work right and you have to troubleshoot to find where you went wrong, and then having to redo it all again. The professional knows exactly how to set up the system.
- It will have a professional appearance – The professional will install everything flawlessly, so that all the cameras, sensors, and the control panel are level and properly secured. DIY installations can get sloppy if not done properly.
- You’ll get an experienced walkthrough – At the end of the installation, the installer will walk you through how to use the system and how to take full advantage of all the features. If you do it yourself, you may never come across certain features.
- There may be a bundled discount – Sometimes professional installations come with extra equipment, or even discounts on the monthly plans. This can offset some of the cost of the professional installation and make it more economically attractive. Check with your system provider to see if they offer any such discounts.

Don, our Smart Home Professional from Vivint
- Higher upfront costs – Some providers may advertise professional installation as free, but really the cost is built into a higher monthly fee or higher equipment costs. Generally, the costs for a professional installation can range from as low as $99 for a basic system, up to $1,500 or more. Often this cost depends on what features you want and how big your house is. As mentioned, you should compare the upfront costs, along with the total cost of the monitoring service over the course of the contract, to see if the “free” installation is worth it.
- Appointment scheduling can be a hassle – Let’s face it, if you need work from a company done during business hours, it’s going to interfere with…well, your business hours. If you’re only home in the evenings, scheduling an appointment can be a pain. To add to this pain, many home security companies require installation windows of up to eight hours. You can’t just leave a key under the mat: you have to be there all that time to wait for them. It’s not unusual to have to take a day off for a complex security system installation. We don’t all have that kind of work flexibility.
- Your system may not be fully customizable – While the professional installer sets everything up nicely, they tend to follow a strict install routine, which may not be exactly to your specs. Also, you might want additions and upgrades later, but these may not be compatible with your system setup. So remember to consider scalability, especially if you’re particular about what you want.

Don, our Vivint technician, installing the Vivint Window Sensor
DIY Installation
- You have full control – Professional installers tend to follow a strict routine when it comes to how to install and set up a security system. When you do it yourself, you can fully customize where the devices go. You can then add on any additional devices, or change out old ones, whenever you want. DIY installation offers the freedom to really make your home security system your own.
- Lower costs – Doing it yourself eliminates the need to pay an expert to do it. You can easily save hundreds of dollars this way, possibly more, as many companies that offer DIY install have cheaper monthly plans. Some companies, such as ADT, even offer cheaper systems when you’re self-installing, for even more savings.
- No appointments to keep – Here’s the thing: professional installation works on the company’s and the installer’s schedules. Depending on where you live, you could be waiting several days for an installer to show up. In the meantime, your home remains unprotected. You can install DIY systems whenever you want. It’s sort of right there in the name. You also won’t need to contact an installer if something in your setup should change.
- Get a great sense of satisfaction – Anyone who has finished a DIY project knows the satisfaction that comes with it. There’s nothing else like seeing your own handiwork come to fruition. And if something goes wrong down the road, you’ll feel empowered to fix it on your own, rather than feeling helpless and needing to call an expert. You’ll know all about your security system by the time it’s operating, and you can feel confident about using and maintaining the system well into the future.

Installing the Reolink Argus 3
- DIY installations can be tough and time consuming – DIY can be time consuming, especially if things don’t go smoothly. If you’re busy and have a hectic schedule, DIY install might become a much bigger hassle than you bargained for. You have to weigh the low price of the DIY installation against the value of your time (and patience!).
- There may be troubleshooting issues – When things don’t go as planned, you may have to spend hours figuring out the issue, possibly seeking help through the company’s customer support. Even then, you may not fully solve the issue. Not all customer support personnel are helpful, and it can be difficult to explain and understand the issue if you’re not exactly sure what’s wrong.
- High upfront equipment costs – You may have to buy the equipment yourself to install it, which only adds to the upfront cost. With professional installations, you’ll likely be renting the equipment, with the costs built into the monthly subscription fee. If you don’t mind paying more upfront, you could save money over time by going the DIY route.
- You won’t get a professional walkthrough – With no walkthrough, there’s a chance you might not fully comprehend your new security system, and you might miss out on some neat features or pro tips. Control panels and apps can have a lot of hidden functions you may not discover on your own, or even see mentioned in the user’s manual.
Comparing Home Security Systems by Company
If you’ve been paying attention, you should have a pretty good idea of what to look for when it comes to features, technology, and functions. These days, though, you have to consider who’s producing your system as well. You can’t afford to put your family’s safety in the hands of a company you don’t absolutely trust.
So, what do you look for in a home security company? And how do you compare home security system companies to one another ?
Here are a handful of important things to consider when choosing a home security company. While there might be other considerations, these are the main factors that can (and will!) impact your service:
- Does the company serve your area? You wouldn’t want to fall in love with a company that only serves, say, the state of Florida when you live way up in Minnesota. This happens, so be sure you understand the service area.
- How fast is the response time? The reliability of a home security company is easily measured — and it’s measured in ‘average response time.’ If a system has 24/7 professional monitoring (many do), then the response time is how long it takes for the monitoring center personnel to reach out to the homeowner after a security breach. The faster, the better. Some companies have this down to 15 seconds. Steer clear of companies that take longer than 30-45 seconds.
- What is the customer service like? Most people don’t even think to consider customer service, until it’s too late. We’ll say it again, though, for those of you in the back: you’re researching security systems. Your security is at stake. You want a company that you can trust to be reliable, responsive, and helpful in a crisis. Some security companies don’t exactly have the best track-record of satisfying customers when it matters the most. While others get outstanding marks across the board. A home invasion is not a time to discover that you can’t get someone on the phone. So be sure to find a company with A+ service before you invest; you’ll be glad you did.
- Do they require contracts? While contracts aren’t all bad (as we’ll discuss), be wary of companies that require long-term contracts on all of their plans. If you’re a homeowner and plan to stay put for several years, a contract isn’t a deal-breaker. But if you rent, for instance, and plan on moving around, it’s best to find a company that doesn’t require you to mortgage your security system, if you will.
- Do they offer a money-back guarantee? A money-back guarantee (and other customer-friendly policies) is the security company’s way of standing behind their products and services. Look for a generous money-back guarantee, because you just never know. Many companies offer 30-day, 60-day, and even 90-day money-back guarantees. This is a great way to take the risk off your shoulders.
- Does the company offer ‘scalable’ systems? Some security companies only offer ultra-basic home security systems that do not accommodate additional devices or integrate with home automation platforms. So be sure to find out if the company offers add-ons and options, as well as systems that are compatible with third-party platforms. These are all important factors to consider.
- Does the company offer DIY installation? Some companies actually require professional installation. While this is great for some people, it simply doesn’t work for others. So it’s nice to at least have the option of DIY install. When comparing home security companies, be sure you understand their installation methods.
- Count the cost. We really dig into this important consideration in our ‘Cost of Home Security’ section below. But get a good feeling of the average price-points when comparing security companies. And don’t forget to look past the advertised pricing — as there’s always more to the story.

Deep Sentinel Equipment
Reading Security Company Reviews
It’s the digital age, so security system company reviews are easy enough to find. They can also be extremely helpful in narrowing down your choices and digging deeper into a particular system. In fact, you can learn pretty much everything about a security company and their offerings by reading an in-depth review.
A really solid review will share the pros and cons, the ups and downs, and pretty much everything you should know before you pull out your wallet. It’s entirely possible (and encouraged) to fully understand each system you have your eye on – the features and tech, the contracts, warranties, everything.
But unfortunately, not all home security company reviews are created equal. There are lots of websites that are just trying to push products, making their reviews completely unbiased and downright misleading.
So here’s what you want to look for in a review:
- The company/reviewer is a true authority. If the reviewer isn’t a home security expert, keep searching. There are enough quality sources out there that really know home security, so it’s silly to waste time reading the opinions of amateurs. The one exception is the consumer who owns the actual system they’re reviewing. These reviews are typically not in-depth or detailed, but they give you a sense of customer satisfaction.
- They share the pros AND cons. If a review is 100% glowing and has nothing negative to say about a security system, then it’s probably a fake review. By fake review we mean unbiased and not trustworthy. No security system is perfect. So look for reviews that tell the whole story about your potential purchase.
- They test the security systems. Ideally you want to read a review written by someone who has tested the system. This way, they can share specifics about how it functions. Taking the thing out of the box and actually testing it is the best way to get a full picture of the product.
- They score the security systems. It’s nice to see an easy-reference chart that scores the different categories. This score chart helps you to see how a particular offer stacks up against other similar security systems.
- They are very thorough. Too much information is better than too little information. Look for reviews that are easy-to-navigate from section to section, with each section detailing everything you need to know, and nothing you don’t.
- They are helpful. You should get a sense that the review is actually helping you to make a wise decision on your home security purchase.

SimpliSafe Wireless Keypad Menu Options
Final Words
Choosing a home security system can seem intimidating at first, especially when you’re trying to decide which one best fits your lifestyle and living arrangement. But the more understanding you have of the different options, the better off you’ll be when it comes to finding the one that makes sense for you. Hopefully, this guide has helped you to get a better grasp on the options and what to look for so that you can make the right choice.
The good news is that there are plenty of options. From features and technology, to the different installation methods, monitored vs. self-monitored, warranties, guarantees, customer service, and more. No two companies are exactly alike, and each one has something new and unique to bring to the table. This means that you’re sure to find a system that suits your needs — and your budget!
The Zebra. (2023, January 31). Burglary Statistics. https://www.thezebra.com/resources/research/burglary-statistics/

Rob Gabriele
As a home security expert and Managing Editor for SafeHome.org, Rob Gabriele has written and edited over 1,000 articles related to home security. His expertise is in smart home protection with thousands of hours of testing and research under his belt. Formerly a reporter and producer for the USAToday network, Rob has been a writer and editor for over 10 years. He holds a Master’s of Science with an emphasis on writing from the University of Montana, and he currently lives in Indianapolis, IN.


Stark Industries Solutions: An Iron Hammer in the Cloud
The homepage of Stark Industries Solutions.
Two weeks before Russia invaded Ukraine in February 2022, a large, mysterious new Internet hosting firm called Stark Industries Solutions materialized and quickly became the epicenter of massive distributed denial-of-service (DDoS) attacks on government and commercial targets in Ukraine and Europe. An investigation into Stark Industries reveals it is being used as a global proxy network that conceals the true source of cyberattacks and disinformation campaigns against enemies of Russia.
At least a dozen patriotic Russian hacking groups have been launching DDoS attacks since the start of the war at a variety of targets seen as opposed to Moscow. But by all accounts, few attacks from those gangs have come close to the amount of firepower wielded by a pro-Russia group calling itself “ NoName057(16) .”
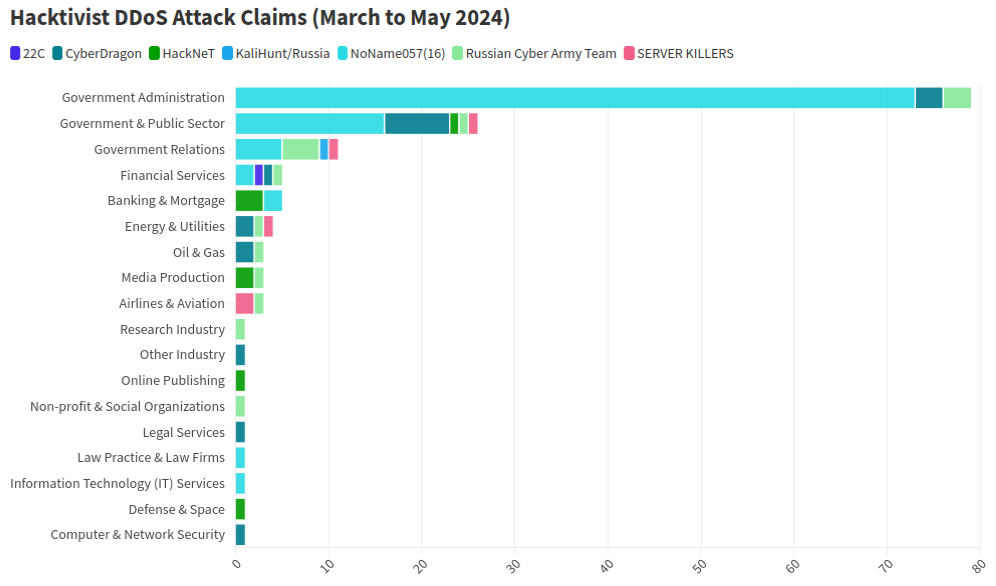
This graphic comes from a recent report from Arbor NETSCOUT about DDoS attacks from Russian hacktivist groups.
As detailed by researchers at Radware , NoName has effectively gamified DDoS attacks, recruiting hacktivists via its Telegram channel and offering to pay people who agree to install a piece of software called DDoSia . That program allows NoName to commandeer the host computers and their Internet connections in coordinated DDoS campaigns, and DDoSia users with the most attacks can win cash prizes.
The NoName DDoS group advertising on Telegram. Image: SentinelOne.com.
A report from the security firm Team Cymru found the DDoS attack infrastructure used in NoName campaigns is assigned to two interlinked hosting providers: MIRhosting and Stark Industries . MIRhosting is a hosting provider founded in The Netherlands in 2004. But Stark Industries Solutions Ltd was incorporated on February 10, 2022, just two weeks before the Russian invasion of Ukraine.
Security experts say that not long after the war started, Stark began hosting dozens of proxy services and free virtual private networking (VPN) services, which are designed to help users shield their Internet usage and location from prying eyes.
Proxy providers allow users to route their Internet and Web browsing traffic through someone else’s computer. From a website’s perspective, the traffic from a proxy network user appears to originate from the rented IP address, not from the proxy service customer.

These services can be used in a legitimate manner for several business purposes — such as price comparisons or sales intelligence — but they are also massively abused for hiding cybercrime activity because they can make it difficult to trace malicious traffic to its original source.
What’s more, many proxy services do not disclose how they obtain access to the proxies they are renting out, and in many cases the access is obtained through the dissemination of malicious software that turns the infected system in a traffic relay — usually unbeknownst to the legitimate owner of the Internet connection. Other proxy services will allow users to make money by renting out their Internet connection to anyone.
Spur.us is a company that tracks VPNs and proxy services worldwide. Spur finds that Stark Industries (AS44477) currently is home to at least 74 VPN services, and 40 different proxy services. As we’ll see in the final section of this story, just one of those proxy networks has over a million Internet addresses worldwide available for rent worldwide.
Raymond Dijkxhoorn operates a hosting firm in The Netherlands called Prolocation . He also co-runs SURBL , an anti-abuse service that flags domains and Internet address ranges that are strongly associated with spam and cybercrime activity, including DDoS.
Dijkxhoorn said last year SURBL heard from multiple people who said they operated VPN services whose web resources were included in SURBL’s block lists.
“We had people doing delistings at SURBL for domain names that were suspended by the registrars,” Dijkhoorn told KrebsOnSecurity. “And at least two of them explained that Stark offered them free VPN services that they were reselling.”
Dijkxhoorn added that Stark Industries also sponsored activist groups from Ukraine.
“How valuable would it be for Russia to know the real IPs from Ukraine’s tech warriors?” he observed. Continue reading →

Why Your Wi-Fi Router Doubles as an Apple AirTag

Image: Shutterstock.
Apple and the satellite-based broadband service Starlink each recently took steps to address new research into the potential security and privacy implications of how their services geo-locate devices. Researchers from the University of Maryland say they relied on publicly available data from Apple to track the location of billions of devices globally — including non-Apple devices like Starlink systems — and found they could use this data to monitor the destruction of Gaza, as well as the movements and in many cases identities of Russian and Ukrainian troops.
At issue is the way that Apple collects and publicly shares information about the precise location of all Wi-Fi access points seen by its devices. Apple collects this location data to give Apple devices a crowdsourced, low-power alternative to constantly requesting global positioning system (GPS) coordinates.
Both Apple and Google operate their own Wi-Fi-based Positioning Systems (WPS) that obtain certain hardware identifiers from all wireless access points that come within range of their mobile devices. Both record the Media Access Control (MAC) address that a Wi-FI access point uses, known as a Basic Service Set Identifier or BSSID .
Periodically, Apple and Google mobile devices will forward their locations — by querying GPS and/or by using cellular towers as landmarks — along with any nearby BSSIDs. This combination of data allows Apple and Google devices to figure out where they are within a few feet or meters, and it’s what allows your mobile phone to continue displaying your planned route even when the device can’t get a fix on GPS.
With Google’s WPS, a wireless device submits a list of nearby Wi-Fi access point BSSIDs and their signal strengths — via an application programming interface (API) request to Google — whose WPS responds with the device’s computed position. Google’s WPS requires at least two BSSIDs to calculate a device’s approximate position.
Apple’s WPS also accepts a list of nearby BSSIDs, but instead of computing the device’s location based off the set of observed access points and their received signal strengths and then reporting that result to the user, Apple’s API will return the geolocations of up to 400 hundred more BSSIDs that are nearby the one requested . It then uses approximately eight of those BSSIDs to work out the user’s location based on known landmarks.
In essence, Google’s WPS computes the user’s location and shares it with the device. Apple’s WPS gives its devices a large enough amount of data about the location of known access points in the area that the devices can do that estimation on their own.
That’s according to two researchers at the University of Maryland, who theorized they could use the verbosity of Apple’s API to map the movement of individual devices into and out of virtually any defined area of the world. The UMD pair said they spent a month early in their research continuously querying the API, asking it for the location of more than a billion BSSIDs generated at random.
They learned that while only about three million of those randomly generated BSSIDs were known to Apple’s Wi-Fi geolocation API, Apple also returned an additional 488 million BSSID locations already stored in its WPS from other lookups .
UMD Associate Professor David Levin and Ph.D student Erik Rye found they could mostly avoid requesting unallocated BSSIDs by consulting the list of BSSID ranges assigned to specific device manufacturers. That list is maintained by the Institute of Electrical and Electronics Engineers (IEEE), which is also sponsoring the privacy and security conference where Rye is slated to present the UMD research later today.
Plotting the locations returned by Apple’s WPS between November 2022 and November 2023, Levin and Rye saw they had a near global view of the locations tied to more than two billion Wi-Fi access points. The map showed geolocated access points in nearly every corner of the globe, apart from almost the entirety of China, vast stretches of desert wilderness in central Australia and Africa, and deep in the rainforests of South America.
A “heatmap” of BSSIDs the UMD team said they discovered by guessing randomly at BSSIDs.
The researchers said that by zeroing in on or “geofencing” other smaller regions indexed by Apple’s location API, they could monitor how Wi-Fi access points moved over time. Why might that be a big deal? They found that by geofencing active conflict zones in Ukraine, they were able to determine the location and movement of Starlink devices used by both Ukrainian and Russian forces.
The reason they were able to do that is that each Starlink terminal — the dish and associated hardware that allows a Starlink customer to receive Internet service from a constellation of orbiting Starlink satellites — includes its own Wi-Fi access point, whose location is going to be automatically indexed by any nearby Apple devices that have location services enabled.
A heatmap of Starlink routers in Ukraine. Image: UMD.
The University of Maryland team geo-fenced various conflict zones in Ukraine, and identified at least 3,722 Starlink terminals geolocated in Ukraine.
“We find what appear to be personal devices being brought by military personnel into war zones, exposing pre-deployment sites and military positions,” the researchers wrote. “Our results also show individuals who have left Ukraine to a wide range of countries, validating public reports of where Ukrainian refugees have resettled.”
In an interview with KrebsOnSecurity, the UMD team said they found that in addition to exposing Russian troop pre-deployment sites, the location data made it easy to see where devices in contested regions originated from.
“This includes residential addresses throughout the world,” Levin said. “We even believe we can identify people who have joined the Ukraine Foreign Legion.”
A simplified map of where BSSIDs that enter the Donbas and Crimea regions of Ukraine originate. Image: UMD.
Levin and Rye said they shared their findings with Starlink in March 2024, and that Starlink told them the company began shipping software updates in 2023 that force Starlink access points to randomize their BSSIDs. Continue reading →
Patch Tuesday, May 2024 Edition
Microsoft today released updates to fix more than 60 security holes in Windows computers and supported software, including two “zero-day” vulnerabilities in Windows that are already being exploited in active attacks. There are also important security patches available for macOS and Adobe users, and for the Chrome Web browser, which just patched its own zero-day flaw.

First, the zero-days. CVE-2024-30051 is an “elevation of privilege” bug in a core Windows library. Satnam Narang at Tenable said this flaw is being used as part of post-compromise activity to elevate privileges as a local attacker.
“CVE-2024-30051 is used to gain initial access into a target environment and requires the use of social engineering tactics via email, social media or instant messaging to convince a target to open a specially crafted document file,” Narang said. “Once exploited, the attacker can bypass OLE mitigations in Microsoft 365 and Microsoft Office, which are security features designed to protect end users from malicious files.”
Kaspersky Lab , one of two companies credited with reporting exploitation of CVE-2024-30051 to Microsoft, has published a fascinating writeup on how they discovered the exploit in a file shared with Virustotal.com.
Kaspersky said it has since seen the exploit used together with QakBot and other malware. Emerging in 2007 as a banking trojan, QakBot (a.k.a. Qbot and Pinkslipbot ) has morphed into an advanced malware strain now used by multiple cybercriminal groups to prepare newly compromised networks for ransomware infestations.
CVE-2024-30040 is a security feature bypass in MSHTML , a component that is deeply tied to the default Web browser on Windows systems. Microsoft’s advisory on this flaw is fairly sparse, but Kevin Breen from Immersive Labs said this vulnerability also affects Office 365 and Microsoft Office applications.
“Very little information is provided and the short description is painfully obtuse,” Breen said of Microsoft’s advisory on CVE-2024-30040.
Continue reading →
How Did Authorities Identify the Alleged Lockbit Boss?
Last week, the United States joined the U.K. and Australia in sanctioning and charging a Russian man named Dmitry Yuryevich Khoroshev as the leader of the infamous LockBit ransomware group. LockBit’s leader “ LockBitSupp ” claims the feds named the wrong guy, saying the charges don’t explain how they connected him to Khoroshev. This post examines the activities of Khoroshev’s many alter egos on the cybercrime forums, and tracks the career of a gifted malware author who has written and sold malicious code for the past 14 years.

Dmitry Yuryevich Khoroshev. Image: treasury.gov.
On May 7, the U.S. Department of Justice indicted Khoroshev on 26 criminal counts, including extortion, wire fraud, and conspiracy. The government alleges Khoroshev created, sold and used the LockBit ransomware strain to personally extort more than $100 million from hundreds of victim organizations, and that LockBit as a group extorted roughly half a billion dollars over four years.
Federal investigators say Khoroshev ran LockBit as a “ ransomware-as-a-service ” operation, wherein he kept 20 percent of any ransom amount paid by a victim organization infected with his code, with the remaining 80 percent of the payment going to LockBit affiliates responsible for spreading the malware.
Financial sanctions levied against Khoroshev by the U.S. Department of the Treasury listed his known email and street address (in Voronezh, in southwest Russia), passport number, and even his tax ID number (hello, Russian tax authorities). The Treasury filing says Khoroshev used the emails [email protected] , and [email protected] .
According to DomainTools.com , the address [email protected] was used to register at least six domains, including a Russian business registered in Khoroshev’s name called tkaner.com , which is a blog about clothing and fabrics.
A search at the breach-tracking service Constella Intelligence on the phone number in Tkaner’s registration records — 7.9521020220 — brings up multiple official Russian government documents listing the number’s owner as Dmitri Yurievich Khoroshev.
Another domain registered to that phone number was stairwell[.]ru , which at one point advertised the sale of wooden staircases. Constella finds that the email addresses [email protected] and [email protected] used the password 225948 .
DomainTools reports that stairwell.ru for several years included the registrant’s name as “ Dmitrij Ju Horoshev ,” and the email address [email protected] . According to Constella, this email address was used in 2010 to register an account for a Dmitry Yurievich Khoroshev from Voronezh, Russia at the hosting provider firstvds.ru .
Cyber intelligence firm Intel 471 finds that [email protected] was used by a Russian-speaking member called Pin on the English-language cybercrime forum Opensc. Pin was active on Opensc around March 2012, and authored 13 posts that mostly concerned data encryption issues, or how to fix bugs in code.
Other posts concerned custom code Pin claimed to have written that would bypass memory protections on Windows XP and Windows 7 systems, and inject malware into memory space normally allocated to trusted applications on a Windows machine.
Pin also was active at that same time on the Russian-language security forum Antichat , where they told fellow forum members to contact them at the ICQ instant messenger number 669316 .
A search on the ICQ number 669316 at Intel 471 shows that in April 2011, a user by the name NeroWolfe joined the Russian cybercrime forum Zloy using the email address [email protected] , and from an Internet address in Voronezh, RU.
Constella finds the same password tied to [email protected] (225948) was used by the email address [email protected] , which Intel 471 says was registered to more than a dozen NeroWolfe accounts across just as many Russian cybercrime forums between 2011 and 2015.
NeroWolfe’s introductory post to the forum Verified in Oct. 2011 said he was a system administrator and C++ coder.
“Installing SpyEYE, ZeuS, any DDoS and spam admin panels,” NeroWolfe wrote. This user said they specialize in developing malware, creating computer worms, and crafting new ways to hijack Web browsers.

“I can provide my portfolio on request,” NeroWolfe wrote. “P.S. I don’t modify someone else’s code or work with someone else’s frameworks.”
In April 2013, NeroWolfe wrote in a private message to another Verified forum user that he was selling a malware “loader” program that could bypass all of the security protections on Windows XP and Windows 7.
“The access to the network is slightly restricted,” NeroWolfe said of the loader, which he was selling for $5,000. “You won’t manage to bind a port. However, it’s quite possible to send data. The code is written in C.”
In an October 2013 discussion on the cybercrime forum Exploit , NeroWolfe weighed in on the karmic ramifications of ransomware. At the time, ransomware-as-a-service didn’t exist yet, and many members of Exploit were still making good money from “lockers,” relatively crude programs that locked the user out of their system until they agreed to make a small payment (usually a few hundred dollars via prepaid Green Dot cards).
Lockers, which presaged the coming ransomware scourge, were generally viewed by the Russian-speaking cybercrime forums as harmless moneymaking opportunities, because they usually didn’t seek to harm the host computer or endanger files on the system. Also, there were still plenty of locker programs that aspiring cybercriminals could either buy or rent to make a steady income.
NeroWolfe reminded forum denizens that they were just as vulnerable to ransomware attacks as their would-be victims, and that what goes around comes around.
“Guys, do you have a conscience?,” NeroWolfe wrote. “Okay, lockers, network gopstop aka business in Russian. The last thing was always squeezed out of the suckers. But encoders, no one is protected from them, including the local audience.” Continue reading →
Why Your VPN May Not Be As Secure As It Claims
Virtual private networking (VPN) companies market their services as a way to prevent anyone from snooping on your Internet usage. But new research suggests this is a dangerous assumption when connecting to a VPN via an untrusted network, because attackers on the same network could force a target’s traffic off of the protection provided by their VPN without triggering any alerts to the user.

When a device initially tries to connect to a network, it broadcasts a message to the entire local network stating that it is requesting an Internet address. Normally, the only system on the network that notices this request and replies is the router responsible for managing the network to which the user is trying to connect.
The machine on a network responsible for fielding these requests is called a Dynamic Host Configuration Protocol (DHCP) server, which will issue time-based leases for IP addresses. The DHCP server also takes care of setting a specific local address — known as an Internet gateway — that all connecting systems will use as a primary route to the Web.
VPNs work by creating a virtual network interface that serves as an encrypted tunnel for communications. But researchers at Leviathan Security say they’ve discovered it’s possible to abuse an obscure feature built into the DHCP standard so that other users on the local network are forced to connect to a rogue DHCP server.
“Our technique is to run a DHCP server on the same network as a targeted VPN user and to also set our DHCP configuration to use itself as a gateway,” Leviathan researchers Lizzie Moratti and Dani Cronce wrote. “When the traffic hits our gateway, we use traffic forwarding rules on the DHCP server to pass traffic through to a legitimate gateway while we snoop on it.”
The feature being abused here is known as DHCP option 121 , and it allows a DHCP server to set a route on the VPN user’s system that is more specific than those used by most VPNs. Abusing this option, Leviathan found, effectively gives an attacker on the local network the ability to set up routing rules that have a higher priority than the routes for the virtual network interface that the target’s VPN creates.
“Pushing a route also means that the network traffic will be sent over the same interface as the DHCP server instead of the virtual network interface,” the Leviathan researchers said. “This is intended functionality that isn’t clearly stated in the RFC [standard]. Therefore, for the routes we push, it is never encrypted by the VPN’s virtual interface but instead transmitted by the network interface that is talking to the DHCP server. As an attacker, we can select which IP addresses go over the tunnel and which addresses go over the network interface talking to our DHCP server.”
Leviathan found they could force VPNs on the local network that already had a connection to arbitrarily request a new one. In this well-documented tactic, known as a DHCP starvation attack , an attacker floods the DHCP server with requests that consume all available IP addresses that can be allocated. Once the network’s legitimate DHCP server is completely tied up, the attacker can then have their rogue DHCP server respond to all pending requests.
“This technique can also be used against an already established VPN connection once the VPN user’s host needs to renew a lease from our DHCP server,” the researchers wrote. “We can artificially create that scenario by setting a short lease time in the DHCP lease, so the user updates their routing table more frequently. In addition, the VPN control channel is still intact because it already uses the physical interface for its communication. In our testing, the VPN always continued to report as connected, and the kill switch was never engaged to drop our VPN connection.”
The researchers say their methods could be used by an attacker who compromises a DHCP server or wireless access point, or by a rogue network administrator who owns the infrastructure themselves and maliciously configures it. Alternatively, an attacker could set up an “ evil twin ” wireless hotspot that mimics the signal broadcast by a legitimate provider.
Bill Woodcock is executive director at Packet Clearing House , a nonprofit based in San Francisco. Woodcock said Option 121 has been included in the DHCP standard since 2002, which means the attack described by Leviathan has technically been possible for the last 22 years.
“They’re realizing now that this can be used to circumvent a VPN in a way that’s really problematic, and they’re right,” Woodcock said.
Woodcock said anyone who might be a target of spear phishing attacks should be very concerned about using VPNs on an untrusted network.
“Anyone who is in a position of authority or maybe even someone who is just a high net worth individual, those are all very reasonable targets of this attack,” he said. “If I were trying to do an attack against someone at a relatively high security company and I knew where they typically get their coffee or sandwich at twice a week, this is a very effective tool in that toolbox. I’d be a little surprised if it wasn’t already being exploited in that way, because again this isn’t rocket science. It’s just thinking a little outside the box.” Continue reading →
Man Who Mass-Extorted Psychotherapy Patients Gets Six Years
A 26-year-old Finnish man was sentenced to more than six years in prison today after being convicted of hacking into an online psychotherapy clinic, leaking tens of thousands of patient therapy records, and attempting to extort the clinic and patients.
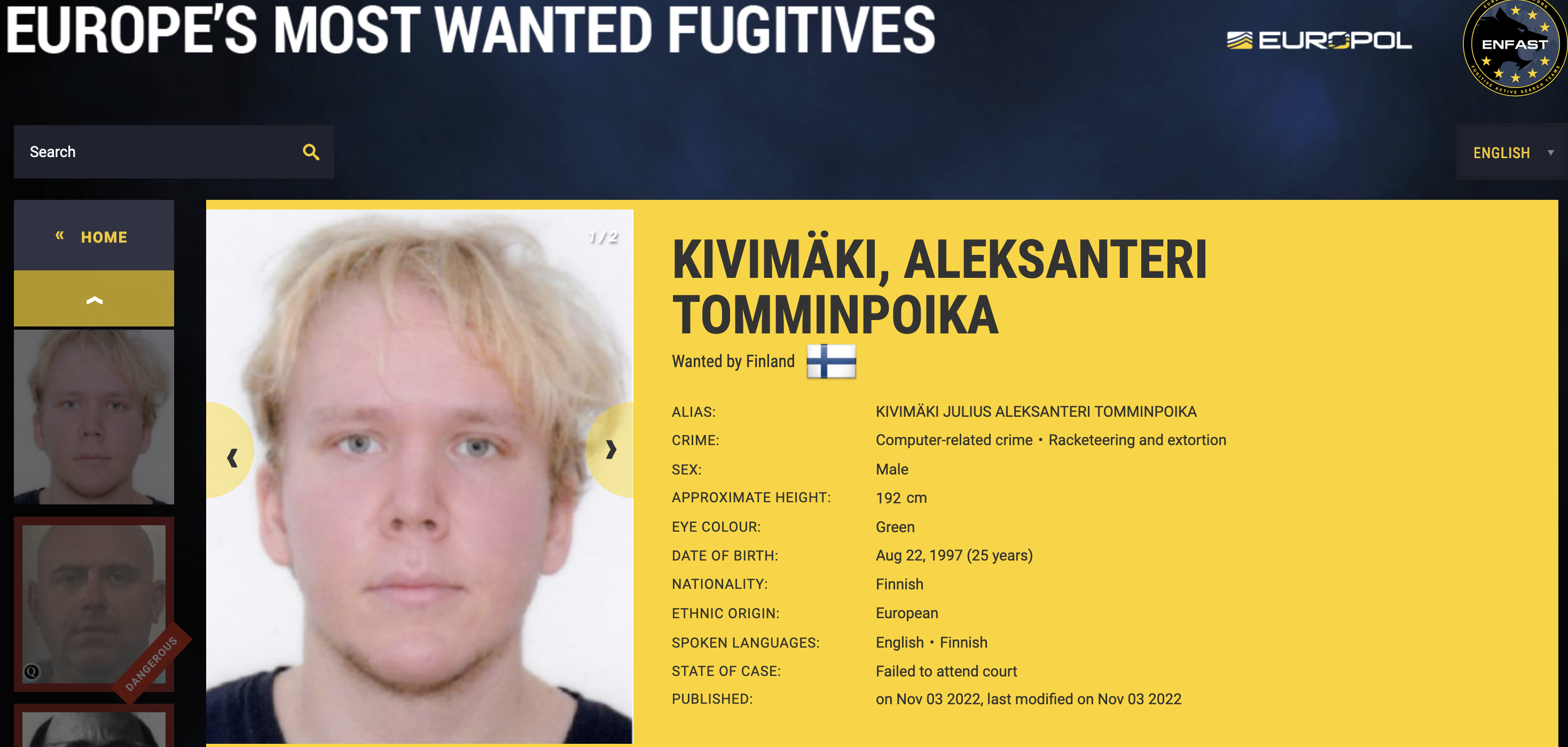
On October 21, 2020, the Vastaamo Psychotherapy Center in Finland became the target of blackmail when a tormentor identified as “ransom_man” demanded payment of 40 bitcoins (~450,000 euros at the time) in return for a promise not to publish highly sensitive therapy session notes Vastaamo had exposed online.
Ransom_man announced on the dark web that he would start publishing 100 patient profiles every 24 hours. When Vastaamo declined to pay, ransom_man shifted to extorting individual patients. According to Finnish police, some 22,000 victims reported extortion attempts targeting them personally, targeted emails that threatened to publish their therapy notes online unless paid a 500 euro ransom.
Finnish prosecutors quickly zeroed in on a suspect: Julius “Zeekill” Kivimäki , a notorious criminal hacker convicted of committing tens of thousands of cybercrimes before he became an adult. After being charged with the attack in October 2022, Kivimäki fled the country. He was arrested four months later in France , hiding out under an assumed name and passport.
Antti Kurittu is a former criminal investigator who worked on an investigation involving Kivimäki’s use of the Zbot botnet, among other activities Kivimäki engaged in as a member of the hacker group Hack the Planet (HTP).
Kurittu said the prosecution had demanded at least seven years in jail, and that the sentence handed down was six years and three months. Kurittu said prosecutors knocked a few months off of Kivimäki’s sentence because he agreed to pay compensation to his victims, and that Kivimäki will remain in prison during any appeal process.
“I think the sentencing was as expected, knowing the Finnish judicial system,” Kurittu told KrebsOnSecurity. “As Kivimäki has not been sentenced to a non-suspended prison sentence during the last five years, he will be treated as a first-timer, his previous convictions notwithstanding.”
But because juvenile convictions in Finland don’t count towards determining whether somebody is a first-time offender, Kivimäki will end up serving approximately half of his sentence.
“This seems like a short sentence when taking into account the gravity of his actions and the life-altering consequences to thousands of people, but it’s almost the maximum the law allows for,” Kurittu said. Continue reading →
FCC Fines Major U.S. Wireless Carriers for Selling Customer Location Data
The U.S. Federal Communications Commission (FCC) today levied fines totaling nearly $200 million against the four major carriers — including AT&T , Sprint , T-Mobile and Verizon — for illegally sharing access to customers’ location information without consent.
The fines mark the culmination of a more than four-year investigation into the actions of the major carriers. In February 2020, the FCC put all four wireless providers on notice that their practices of sharing access to customer location data were likely violating the law.
The FCC said it found the carriers each sold access to its customers’ location information to ‘aggregators,’ who then resold access to the information to third-party location-based service providers.
“In doing so, each carrier attempted to offload its obligations to obtain customer consent onto downstream recipients of location information, which in many instances meant that no valid customer consent was obtained,” an FCC statement on the action reads. “This initial failure was compounded when, after becoming aware that their safeguards were ineffective, the carriers continued to sell access to location information without taking reasonable measures to protect it from unauthorized access.”
The FCC’s findings against AT&T , for example, show that AT&T sold customer location data directly or indirectly to at least 88 third-party entities. The FCC found Verizon sold access to customer location data (indirectly or directly) to 67 third-party entities. Location data for Sprint customers found its way to 86 third-party entities, and to 75 third-parties in the case of T-Mobile customers.
The commission said it took action after Sen. Ron Wyden (D-Ore.) sent a letter to the FCC detailing how a company called Securus Technologies had been selling location data on customers of virtually any major mobile provider to law enforcement officials.
That same month, KrebsOnSecurity broke the news that LocationSmart — a data aggregation firm working with the major wireless carriers — had a free, unsecured demo of its service online that anyone could abuse to find the near-exact location of virtually any mobile phone in North America. Continue reading →
Russian FSB Counterintelligence Chief Gets 9 Years in Cybercrime Bribery Scheme
The head of counterintelligence for a division of the Russian Federal Security Service (FSB) was sentenced last week to nine years in a penal colony for accepting a USD $1.7 million bribe to ignore the activities of a prolific Russian cybercrime group that hacked thousands of e-commerce websites. The protection scheme was exposed in 2022 when Russian authorities arrested six members of the group, which sold millions of stolen payment cards at flashy online shops like Trump’s Dumps .

A now-defunct carding shop that sold stolen credit cards and invoked 45’s likeness and name.
As reported by The Record , a Russian court last week sentenced former FSB officer Grigory Tsaregorodtsev for taking a $1.7 million bribe from a cybercriminal group that was seeking a “roof,” a well-placed, corrupt law enforcement official who could be counted on to both disregard their illegal hacking activities and run interference with authorities in the event of their arrest.
Tsaregorodtsev was head of the counterintelligence department for a division of the FSB based in Perm, Russia. In February 2022, Russian authorities arrested six men in the Perm region accused of selling stolen payment card data. They also seized multiple carding shops run by the gang, including Ferum Shop , Sky-Fraud , and Trump’s Dumps , a popular fraud store that invoked the 45th president’s likeness and promised to “make credit card fraud great again.”
All of the domains seized in that raid were registered by an IT consulting company in Perm called Get-net LLC , which was owned in part by Artem Zaitsev — one of the six men arrested. Zaitsev reportedly was a well-known programmer whose company supplied services and leasing to the local FSB field office. Continue reading →
Who Stole 3.6M Tax Records from South Carolina?

For nearly a dozen years, residents of South Carolina have been kept in the dark by state and federal investigators over who was responsible for hacking into the state’s revenue department in 2012 and stealing tax and bank account information for 3.6 million people. The answer may no longer be a mystery: KrebsOnSecurity found compelling clues suggesting the intrusion was carried out by the same Russian hacking crew that stole of millions of payment card records from big box retailers like Home Depot and Target in the years that followed.
Questions about who stole tax and financial data on roughly three quarters of all South Carolina residents came to the fore last week at the confirmation hearing of Mark Keel , who was appointed in 2011 by Gov. Nikki Haley to head the state’s law enforcement division. If approved, this would be Keel’s third six-year term in that role.
The Associated Press reports that Keel was careful not to release many details about the breach at his hearing, telling lawmakers he knows who did it but that he wasn’t ready to name anyone.
“I think the fact that we didn’t come up with a whole lot of people’s information that got breached is a testament to the work that people have done on this case,” Keel asserted.
A ten-year retrospective published in 2022 by The Post and Courier in Columbia, S.C. said investigators determined the breach began on Aug. 13, 2012, after a state IT contractor clicked a malicious link in an email. State officials said they found out about the hack from federal law enforcement on October 10, 2012.
KrebsOnSecurity examined posts across dozens of cybercrime forums around that time, and found only one instance of someone selling large volumes of tax data in the year surrounding the breach date.
On Oct. 7, 2012 — three days before South Carolina officials say they first learned of the intrusion — a notorious cybercriminal who goes by the handle “ Rescator ” advertised the sale of “a database of the tax department of one of the states.”
“Bank account information, SSN and all other information,” Rescator’s sales thread on the Russian-language crime forum Embargo read. “If you purchase the entire database, I will give you access to it.”
A week later, Rescator posted a similar offer on the exclusive Russian forum Mazafaka , saying he was selling information from a U.S. state tax database, without naming the state. Rescator said the data exposed included Social Security Number (SSN), employer, name, address, phone, taxable income, tax refund amount, and bank account number.
“There is a lot of information, I am ready to sell the entire database, with access to the database, and in parts,” Rescator told Mazafaka members. “There is also information on corporate taxpayers.” Continue reading →
- Next ›

- Share full article
Advertisement
Supported by
Guest Essay
It Is Inexcusable How Judge Cannon Is Delaying the Trump Documents Case

By Brian Greer
Mr. Greer was a lawyer in the Central Intelligence Agency’s Office of General Counsel from 2010 to 2018.
The task before Judge Aileen Cannon, who is presiding over the classified documents case of Donald Trump, is not easy. She must protect Mr. Trump’s constitutional rights while also ensuring the prompt and fair administration of justice.
Still, it is inexcusable that she is utterly failing to keep the case moving along in a fair but timely manner. And unfortunately, there isn’t much that the special counsel in the case, Jack Smith, can do about it.
While working as an attorney in the C.I.A.’s Office of General Counsel, I developed an expertise in Espionage Act prosecutions similar to the one pending against Mr. Trump, who is accused of illegally taking classified state documents from the White House after he left office and then obstructing the government’s repeated efforts to retrieve them. I know firsthand that cases like this can be quite complicated and lengthy.
But outside of the unique issues raised by Mr. Trump’s status as a former president (for example, immunity and the Presidential Records Act), the prosecution against him is actually not particularly complex. The volume of classified records subject to discovery is not outside the norm, and if the defendant were not Donald Trump, this would be a relatively routine Espionage Act prosecution for unlawful retention of classified records.
With a competent and determined judge, Mr. Trump’s due process rights could have been well protected and the trial could have reasonably been set for this summer. However, this is not the first time Judge Cannon — a Trump appointee — has granted delay after delay, and thanks to a recent scheduling order , it’s now all but certain that the case will not go to trial until after Election Day.
If Mr. Trump wins the election, the case will be effectively over. The Trump Justice Department would almost certainly dismiss the indictment at his behest when the clock strikes noon on Jan. 20, 2025.
One way of taking a measure of how Judge Cannon has failed is by looking at the progress of pretrial litigation, which started soon after Mr. Trump was indicted in June 2023. In a criminal trial, the purpose of pretrial litigation is threefold: to ensure the defense gets access to all discoverable material; to resolve “dispositive” motions that could result in dismissal of the case if granted, like Mr. Trump’s presidential immunity assertion; and to determine what the trial will look like. The latter is an especially important task here given that Mr. Trump is charged with illegally mishandling some of our most closely guarded secrets, which could be further compromised depending on how they are used at a public trial.
Measured against these goals, Judge Cannon has made almost no progress over the past 11 months. That is shocking and indefensible.
On the scope of discovery, Judge Cannon has failed to rule on Mr. Trump’s motion — filed four months ago — to compel additional discovery from the government. Under her new schedule, she may not rule on it until July. A ruling granting Mr. Trump’s motion could result in months of additional delays.
The discovery and use of classified information is one of the thornier issues in cases of this nature. Here, too, the judge has made almost no progress, and her inexperience is showing. She has ruled on just one substantive motion with respect to Mr. Trump, which was filed by the government in December and applied to only a sliver of the classified information at issue in the case. Under her new scheduling order, the next phase of litigation involving classified information won’t begin until mid-June. Judge Cannon won’t even begin to address the difficult questions about how classified information will be used and disclosed at trial until August at the earliest, even though Mr. Trump’s team has had access to over 90 percent of the classified discovery since last fall.
On efforts to dismiss the case, in February, Mr. Trump made seven such motions, and so far Judge Cannon has ruled on only two. Some of them are plainly frivolous, but she has insisted on extensive hearings for each one, some of which have not been held yet.
Finally, Judge Cannon has not yet addressed a single substantive issue that will determine what the trial looks like. The most difficult issues she needs to address lie ahead, including those involving presidential immunity, attorney-client privilege and, most important, how this highly classified information will be used and protected at trial. She won’t even start resolving these issues until August at the earliest — over 14 months after Mr. Trump was indicted.
At the same time, Judge Cannon has displayed an extremely high tolerance for delay tactics from Mr. Trump’s defense team — or shenanigans, as we called them when I worked on such cases. For instance, she has wasted two months addressing Mr. Trump’s efforts to publicly expose witness information in his court filings. Most federal judges would quickly shut down these tactics, but this judge seems to invite them, and the delays they cause.
It is thus impossible to conclude that Judge Cannon is diligently moving the case forward as she has claimed. While some minor delays have been warranted to protect Mr. Trump’s rights, especially in light of his other pending prosecutions, the overall speed of the case remains glacial — seemingly by design.
Outside of the unwarranted delays, Judge Cannon has shown a repeated willingness to entertain extreme arguments from the Trump legal team. For instance, she seriously considered adopting the position, via a jury instruction, that Mr. Trump had unreviewable authority to designate highly classified government documents as his own “personal” records under the Presidential Records Act. Rather than squarely rejecting this absurd argument, she instead refused to rule on it until closer to trial, leaving prosecutors in a lurch.
Despite these issues, Mr. Smith, the special counsel, will not be able to seek the judge’s removal from the case anytime soon, if ever. There is a very high bar for removal, and scheduling delays alone are insufficient reason. Still, the more significant issues to be decided lie ahead, and it’s possible that one or more frivolous rulings from Judge Cannon could cause Mr. Smith to seek her removal on appeal.
However, the time necessary to resolve such an appeal will almost certainly push a trial past the November election.
The rule of law depends in part on fair, impartial judges. When judges put their finger on the scale, as Judge Cannon appears to have done, it undermines public confidence in our justice system. Moreover, failing to hold Mr. Trump accountable will have the compound effect of undermining our credibility on national security matters — by sending the message that a former president can knowingly compromise the trusted secrets of our foreign allies with impunity.
The world is watching, and Judge Cannon is proving that she is not fit for this moment.
Brian Greer ( @secretsandlaws ) was a lawyer in the Central Intelligence Agency’s Office of General Counsel from 2010 to 2018.
The Times is committed to publishing a diversity of letters to the editor. We’d like to hear what you think about this or any of our articles. Here are some tips . And here’s our email: [email protected] .
Follow the New York Times Opinion section on Facebook , Instagram , TikTok , WhatsApp , X and Threads .
- Skip to main content
- Keyboard shortcuts for audio player
Liam and Olivia are still the most popular baby names in the U.S.—but Mateo is rising

Scott Horsley

Olivia and Liam were the most popular names for girls and boys in 2023, just as they have been in each of the last five years. Meg Oliphant/Getty Images for Rock 'n' Roll M hide caption
Olivia and Liam were the most popular names for girls and boys in 2023, just as they have been in each of the last five years.
For all the upheaval of recent years, one thing has stayed the same: Liam and Olivia are still the most popular baby names in the U.S. for the fifth year in a row.
An annual tally by the Social Security Administration — released just in time for Mother's Day — shows 20,802 baby boys were named Liam last year, while 15,270 baby girls were named Olivia. Also for the fifth year running, Noah and Emma were the runners up.

Baby Names Are Overwhelming. Here's How To Narrow Your List
Almost all the most popular names have remained remarkably consistent from year to year. "Mateo" was the only new entry to crack the top ten list for either boy's or girl's names in 2023.
Chozen, Kaeli, and Alitzel making buzz
While some names gained newfound buzz last year — Izael and Chozen for boys, Kaeli and Alitzel for girls — they remain far behind trusted standbys like Oliver and Charlotte.
More than one out of 100 baby boys was named Liam last year, while Olivia was attached to just under one in 100 baby girls.
"Everyone thinks they're choosing a name that's just so special for their child," University of Chicago professor Eric Oliver told Freakanomics Radio back in 2013. "It's only when they get to the playground and there are half a dozen other Ellas there that they realize, 'Oh, maybe I'm part of a social trend.'"
(Ella was the 13th most popular girl's name in 2013. By last year it had dropped to 32d place. )
Pop cultural influence may give a lift to some previously obscure names. Social Security researchers note that Chozen, the second fastest-growing boy's name, is a character on the Netflix show Cobra Kai . The rise of Kaeli as a girl's name may have been sparked by TikTok star Kaeli McEwen.
Correction May 11, 2024
An earlier version of this story misspelled the Netflix show's name Cobra Kai as Corbra Kai.
- Social Security Administration
Search msd.govt.nz
- What we can do for:
- Work programmes
- Child Youth and Wellbeing
- News and media
- Research and insights
- Long-term Insights Briefings
- Corporate publications
- Consultations
- Planning and Strategy
- Research archive
- Official Information Act
- Evaluation reports
- Monitoring reports
- Literature Reviews
- Working Papers
- Regulatory Impact Statements
- Funding Contracting Service Guidelines
- Reports to the Minister for Social Development and Employment
- Reports to the Associate Minister for Social Development and Employment
- Reports to the Minister for Disability Issues
- Reports to the Minister for Seniors
- Reports to the Minister for Youth
- Careers at MSD

Social Security (Childcare Subsidy) Amendment Regulations 2024
22 May 2024.
The paper seeks agreement to amendments to the Social Security Regulations 2018 to allow parents and caregivers access to the Childcare Subsidy to pay for top-up payments required by home-based educators for 20 Hours ECE from 3 June 2024.
Word format
What we can do for.
- Individuals
- Young adults
- Disabled people
About us and our work
- Publications and resources
- Other MSD websites
- Privacy, copyright and disclaimer
- Accessibility
- About this site


AMD Infinity Guard¹
Enabling IT ecosystem security for a data-driven world

Data Generation is Skyrocketing
The exponential growth of data sharing – propelled by IoT, digitization, and cloud computing – is further intensifying through rapid adoption of machine learning, AI, social media, and collaborative applications. The increased global emphasis on privacy regulations and severe penalties for breaches underscores data’s unparalleled value amid rising security risks.
Threats to Data Security are Growing – and Evolving
Vigilance against evolving threats is crucial given the heightened vulnerabilities of the expanding data landscape. Alongside the complex risks of AI democratization and surging cloud adoption, enterprise data protection requires dependable support from CSPs to enable and enhance confidential computing.

The AMD EPYC Approach to Security
With the modern “ZEN” architecture, AMD EPYC processors are designed with security in mind from the ground up to be highly resistant to today’s sophisticated attacks, helping protect your sensitive data, avoid downtime, and reduce resource drain. In addition, AMD Infinity Guard provides a unique and robust set of security features that help complement industry ecosystem partners at the software and system levels.
AMD Infinity Guard
Built-in at the silicon level, AMD Infinity Guard offers the advanced capabilities required to help defend against internal and external threats and keep your data safe.
Foundational Security with Continuous Improvement
- AMD Secure Boot²
Transparent Secure Memory Encryption (TSME)
Amd shadow stack, secure encrypted virtualization (sev), sev encrypted state (sev-es), sev secure nested paging (sev-snp), amd secure boot 2.
AMD Secure Boot defends against firmware threats, extending the silicon root of trust to help protect BIOS, enhancing security against malware and attacks in virtualized environments.

Help safeguard against internal security threats with encrypted data protection, including defense against certain cold-boot attacks. Integrated high-performance encryption engines in memory channels enable optimal performance without the need for application software modifications.
AMD Shadow Stack 3 offers hardware-enforced stack protection, mitigating malware attacks like return oriented programming (ROP). It maintains return addresses for integrity checks and supports Microsoft® hardware enforced stack protection.

Encrypt and protect each VM's memory space from the hypervisor and other VMs using individual keys, with support for up to 1006 keys 4 . Enjoy limitless encrypted memory capacity, with added support for CXL memory expansion.
Protects the contents of the registers when the Virtual Machine is offline.

SEV-SNP 3 provides VM integrity and confidentiality against malicious hypervisors, it enhances cloud security across diverse workloads, with optional defenses against malicious interrupt injection, specific speculative side channel attacks, and TCB rollback attacks.

Confidential Computing
Confidential computing helps keep data protected while it is being processed—designed to make data inaccessible to even the cloud service provider. Leverage a growing ecosystem using AMD Infinity Guard to address the special security concerns about migrating sensitive applications and data to the cloud.

Customer Success Stories
See how datacenters are improving performance, security, and cost-savings with AMD EPYC™ processors.
SEV Developer Resources
Access SEV whitepapers, specifications, and tools for developers.
AMD EPYC White Papers Solution Briefs
Find AMD and partner documentation on deploying AMD EPYC powered solutions.

Newsletter and Request Contact
Subscribe to data center insights from amd, request contact from an amd epyc™ sales expert.
- GD-183A: AMD Infinity Guard features vary by EPYC™ Processor generations and/or series. Infinity Guard security features must be enabled by server OEMs and/or Cloud Service Providers to operate. Check with your OEM or provider to confirm support of these features. Learn more about Infinity Guard at http://www.amd.com/en/products/processors/server/epyc/infinity-guard.html .
- An OEM who has enabled the AMD Secure Boot feature grants permission for their cryptographically signed BIOS code to run only on their platforms using an AMD secure boot enabled motherboard. One-time-programmable fuses in the processor bind the processor to the OEM’s firmware code signing key. From that point on, that processor can only be used with motherboards that use the same code signing key.
- Available in 3rd Gen and newer AMD EPYC processors.
- 4th Gen AMD EPYC 8004 and 9004 processors. 3 rd generation AMD EPYC processors support up to 506 keys.
Main Navigation
- Contact NeurIPS
- Code of Ethics
- Code of Conduct
- Create Profile
- Journal To Conference Track
- Diversity & Inclusion
- Proceedings
- Future Meetings
- Exhibitor Information
- Privacy Policy
NeurIPS 2024
Conference Dates: (In person) 9 December - 15 December, 2024
Homepage: https://neurips.cc/Conferences/2024/
Call For Papers
Abstract submission deadline: May 15, 2024
Author notification: Sep 25, 2024
Camera-ready, poster, and video submission: Oct 30, 2024 AOE
Submit at: https://openreview.net/group?id=NeurIPS.cc/2024/Conference
The site will start accepting submissions on Apr 22, 2024
Subscribe to these and other dates on the 2024 dates page .
The Thirty-Eighth Annual Conference on Neural Information Processing Systems (NeurIPS 2024) is an interdisciplinary conference that brings together researchers in machine learning, neuroscience, statistics, optimization, computer vision, natural language processing, life sciences, natural sciences, social sciences, and other adjacent fields. We invite submissions presenting new and original research on topics including but not limited to the following:
- Applications (e.g., vision, language, speech and audio, Creative AI)
- Deep learning (e.g., architectures, generative models, optimization for deep networks, foundation models, LLMs)
- Evaluation (e.g., methodology, meta studies, replicability and validity, human-in-the-loop)
- General machine learning (supervised, unsupervised, online, active, etc.)
- Infrastructure (e.g., libraries, improved implementation and scalability, distributed solutions)
- Machine learning for sciences (e.g. climate, health, life sciences, physics, social sciences)
- Neuroscience and cognitive science (e.g., neural coding, brain-computer interfaces)
- Optimization (e.g., convex and non-convex, stochastic, robust)
- Probabilistic methods (e.g., variational inference, causal inference, Gaussian processes)
- Reinforcement learning (e.g., decision and control, planning, hierarchical RL, robotics)
- Social and economic aspects of machine learning (e.g., fairness, interpretability, human-AI interaction, privacy, safety, strategic behavior)
- Theory (e.g., control theory, learning theory, algorithmic game theory)
Machine learning is a rapidly evolving field, and so we welcome interdisciplinary submissions that do not fit neatly into existing categories.
Authors are asked to confirm that their submissions accord with the NeurIPS code of conduct .
Formatting instructions: All submissions must be in PDF format, and in a single PDF file include, in this order:
- The submitted paper
- Technical appendices that support the paper with additional proofs, derivations, or results
- The NeurIPS paper checklist
Other supplementary materials such as data and code can be uploaded as a ZIP file
The main text of a submitted paper is limited to nine content pages , including all figures and tables. Additional pages containing references don’t count as content pages. If your submission is accepted, you will be allowed an additional content page for the camera-ready version.
The main text and references may be followed by technical appendices, for which there is no page limit.
The maximum file size for a full submission, which includes technical appendices, is 50MB.
Authors are encouraged to submit a separate ZIP file that contains further supplementary material like data or source code, when applicable.
You must format your submission using the NeurIPS 2024 LaTeX style file which includes a “preprint” option for non-anonymous preprints posted online. Submissions that violate the NeurIPS style (e.g., by decreasing margins or font sizes) or page limits may be rejected without further review. Papers may be rejected without consideration of their merits if they fail to meet the submission requirements, as described in this document.
Paper checklist: In order to improve the rigor and transparency of research submitted to and published at NeurIPS, authors are required to complete a paper checklist . The paper checklist is intended to help authors reflect on a wide variety of issues relating to responsible machine learning research, including reproducibility, transparency, research ethics, and societal impact. The checklist forms part of the paper submission, but does not count towards the page limit.
Please join the NeurIPS 2024 Checklist Assistant Study that will provide you with free verification of your checklist performed by an LLM here . Please see details in our blog
Supplementary material: While all technical appendices should be included as part of the main paper submission PDF, authors may submit up to 100MB of supplementary material, such as data, or source code in a ZIP format. Supplementary material should be material created by the authors that directly supports the submission content. Like submissions, supplementary material must be anonymized. Looking at supplementary material is at the discretion of the reviewers.
We encourage authors to upload their code and data as part of their supplementary material in order to help reviewers assess the quality of the work. Check the policy as well as code submission guidelines and templates for further details.
Use of Large Language Models (LLMs): We welcome authors to use any tool that is suitable for preparing high-quality papers and research. However, we ask authors to keep in mind two important criteria. First, we expect papers to fully describe their methodology, and any tool that is important to that methodology, including the use of LLMs, should be described also. For example, authors should mention tools (including LLMs) that were used for data processing or filtering, visualization, facilitating or running experiments, and proving theorems. It may also be advisable to describe the use of LLMs in implementing the method (if this corresponds to an important, original, or non-standard component of the approach). Second, authors are responsible for the entire content of the paper, including all text and figures, so while authors are welcome to use any tool they wish for writing the paper, they must ensure that all text is correct and original.
Double-blind reviewing: All submissions must be anonymized and may not contain any identifying information that may violate the double-blind reviewing policy. This policy applies to any supplementary or linked material as well, including code. If you are including links to any external material, it is your responsibility to guarantee anonymous browsing. Please do not include acknowledgements at submission time. If you need to cite one of your own papers, you should do so with adequate anonymization to preserve double-blind reviewing. For instance, write “In the previous work of Smith et al. [1]…” rather than “In our previous work [1]...”). If you need to cite one of your own papers that is in submission to NeurIPS and not available as a non-anonymous preprint, then include a copy of the cited anonymized submission in the supplementary material and write “Anonymous et al. [1] concurrently show...”). Any papers found to be violating this policy will be rejected.
OpenReview: We are using OpenReview to manage submissions. The reviews and author responses will not be public initially (but may be made public later, see below). As in previous years, submissions under review will be visible only to their assigned program committee. We will not be soliciting comments from the general public during the reviewing process. Anyone who plans to submit a paper as an author or a co-author will need to create (or update) their OpenReview profile by the full paper submission deadline. Your OpenReview profile can be edited by logging in and clicking on your name in https://openreview.net/ . This takes you to a URL "https://openreview.net/profile?id=~[Firstname]_[Lastname][n]" where the last part is your profile name, e.g., ~Wei_Zhang1. The OpenReview profiles must be up to date, with all publications by the authors, and their current affiliations. The easiest way to import publications is through DBLP but it is not required, see FAQ . Submissions without updated OpenReview profiles will be desk rejected. The information entered in the profile is critical for ensuring that conflicts of interest and reviewer matching are handled properly. Because of the rapid growth of NeurIPS, we request that all authors help with reviewing papers, if asked to do so. We need everyone’s help in maintaining the high scientific quality of NeurIPS.
Please be aware that OpenReview has a moderation policy for newly created profiles: New profiles created without an institutional email will go through a moderation process that can take up to two weeks. New profiles created with an institutional email will be activated automatically.
Venue home page: https://openreview.net/group?id=NeurIPS.cc/2024/Conference
If you have any questions, please refer to the FAQ: https://openreview.net/faq
Abstract Submission: There is a mandatory abstract submission deadline on May 15, 2024, six days before full paper submissions are due. While it will be possible to edit the title and abstract until the full paper submission deadline, submissions with “placeholder” abstracts that are rewritten for the full submission risk being removed without consideration. This includes titles and abstracts that either provide little or no semantic information (e.g., "We provide a new semi-supervised learning method.") or describe a substantively different claimed contribution. The author list cannot be changed after the abstract deadline. After that, authors may be reordered, but any additions or removals must be justified in writing and approved on a case-by-case basis by the program chairs only in exceptional circumstances.
Ethics review: Reviewers and ACs may flag submissions for ethics review . Flagged submissions will be sent to an ethics review committee for comments. Comments from ethics reviewers will be considered by the primary reviewers and AC as part of their deliberation. They will also be visible to authors, who will have an opportunity to respond. Ethics reviewers do not have the authority to reject papers, but in extreme cases papers may be rejected by the program chairs on ethical grounds, regardless of scientific quality or contribution.
Preprints: The existence of non-anonymous preprints (on arXiv or other online repositories, personal websites, social media) will not result in rejection. If you choose to use the NeurIPS style for the preprint version, you must use the “preprint” option rather than the “final” option. Reviewers will be instructed not to actively look for such preprints, but encountering them will not constitute a conflict of interest. Authors may submit anonymized work to NeurIPS that is already available as a preprint (e.g., on arXiv) without citing it. Note that public versions of the submission should not say "Under review at NeurIPS" or similar.
Dual submissions: Submissions that are substantially similar to papers that the authors have previously published or submitted in parallel to other peer-reviewed venues with proceedings or journals may not be submitted to NeurIPS. Papers previously presented at workshops are permitted, so long as they did not appear in a conference proceedings (e.g., CVPRW proceedings), a journal or a book. NeurIPS coordinates with other conferences to identify dual submissions. The NeurIPS policy on dual submissions applies for the entire duration of the reviewing process. Slicing contributions too thinly is discouraged. The reviewing process will treat any other submission by an overlapping set of authors as prior work. If publishing one would render the other too incremental, both may be rejected.
Anti-collusion: NeurIPS does not tolerate any collusion whereby authors secretly cooperate with reviewers, ACs or SACs to obtain favorable reviews.
Author responses: Authors will have one week to view and respond to initial reviews. Author responses may not contain any identifying information that may violate the double-blind reviewing policy. Authors may not submit revisions of their paper or supplemental material, but may post their responses as a discussion in OpenReview. This is to reduce the burden on authors to have to revise their paper in a rush during the short rebuttal period.
After the initial response period, authors will be able to respond to any further reviewer/AC questions and comments by posting on the submission’s forum page. The program chairs reserve the right to solicit additional reviews after the initial author response period. These reviews will become visible to the authors as they are added to OpenReview, and authors will have a chance to respond to them.
After the notification deadline, accepted and opted-in rejected papers will be made public and open for non-anonymous public commenting. Their anonymous reviews, meta-reviews, author responses and reviewer responses will also be made public. Authors of rejected papers will have two weeks after the notification deadline to opt in to make their deanonymized rejected papers public in OpenReview. These papers are not counted as NeurIPS publications and will be shown as rejected in OpenReview.
Publication of accepted submissions: Reviews, meta-reviews, and any discussion with the authors will be made public for accepted papers (but reviewer, area chair, and senior area chair identities will remain anonymous). Camera-ready papers will be due in advance of the conference. All camera-ready papers must include a funding disclosure . We strongly encourage accompanying code and data to be submitted with accepted papers when appropriate, as per the code submission policy . Authors will be allowed to make minor changes for a short period of time after the conference.
Contemporaneous Work: For the purpose of the reviewing process, papers that appeared online within two months of a submission will generally be considered "contemporaneous" in the sense that the submission will not be rejected on the basis of the comparison to contemporaneous work. Authors are still expected to cite and discuss contemporaneous work and perform empirical comparisons to the degree feasible. Any paper that influenced the submission is considered prior work and must be cited and discussed as such. Submissions that are very similar to contemporaneous work will undergo additional scrutiny to prevent cases of plagiarism and missing credit to prior work.
Plagiarism is prohibited by the NeurIPS Code of Conduct .
Other Tracks: Similarly to earlier years, we will host multiple tracks, such as datasets, competitions, tutorials as well as workshops, in addition to the main track for which this call for papers is intended. See the conference homepage for updates and calls for participation in these tracks.
Experiments: As in past years, the program chairs will be measuring the quality and effectiveness of the review process via randomized controlled experiments. All experiments are independently reviewed and approved by an Institutional Review Board (IRB).
Financial Aid: Each paper may designate up to one (1) NeurIPS.cc account email address of a corresponding student author who confirms that they would need the support to attend the conference, and agrees to volunteer if they get selected. To be considered for Financial the student will also need to fill out the Financial Aid application when it becomes available.
Social Security
Disability starter kits.
Disability Home
The Disability Starter Kit will help you get ready for your disability interview or online application. Kits are available for adults and for children under age 18.
The starter kits provide information about the specific documents and the information that we will request from you. We will ask for more details during your interview.
The kits also provide general information about the disability programs and our decision-making process that can help take some of the mystery out of applying for disability benefits.

COMMENTS
Securing Military Gear Essay. Decent Essays. 5060 Words. 21 Pages. Open Document. Importance of Securing Items The definition of sensitive items is anything that considered classified or a mission essential item. They range anywhere from protective wear, maps, patrol routes, nods (night vision goggles) or simply your weapon.
Accountability of Sensitive Items. 1026 words 5 pages. Show More. This essay will be about the importance of keeping the accountability of sensitive items and how the accountability of sensitive items affects the unit. AR 710-2 and AR 735-5 both cover the Army policy for property accountability. Some sensitive items are your weapon, military ID ...
Essay On Military Equipment. It is important to maintain our equipment because without our equipment or non-efficient equipment, our mission success or readiness goes down. This is especially important in the military because of the seriousness of our jobs. It is in the Army values "I will always maintain my arms, my equipment, and myself."
Welcome to the KIT Graduate School Cyber Security. In virtually all areas of information technology today, cyber security is of the utmost importance. In a highly digitalized world with highly digitalized economies, protection against increasingly dangerous cyber attacks is crucial. In recent years, the news have been littered with reports on ...
military hardware for the Iraqi security forces. For example, according to the report, the military could not account for 12,712 out of 13,508 weapons, including pistols, assault rifles, rocket propelled grenade launchers and machine guns. So as you see it affects not only the military but the United States in general.
Cybersecurity refers to a range of approaches for preventing illegal exposure to systems software and information. The paper focuses on the various definitions of cybersecurity and the dimensions and principles to protect against the data on the hardware and software from unauthorized access, harm, or misuse. The three….
Critical theory refers to a body of thought growing out of the Marxist tradition, which, during the mid- to late Cold War informed dependency and world systems theory. In the decade prior to and following the end of the Cold War, critical theory, informed by Gramsci and the Frankfurt School, both of which have a Marxist lineage, became part of ...
Version 1.4, 24 June 2021 DoD Chief Information Officer Cybersecurity Risk Management 1. This document provides an outline and high-level guidance on the expectations for the Cybersecurity Strategy (CSS), previously identified as the Information Assurance Strategy, primarily included as an appendix to a system's Program Protection Plan, as required by the Clinger-Cohen Act (40 U.S.C ...
Papers accepted at PETS 2024. The papers Fantômas: Understanding Face Anonymization Reversibility (Julian Todt, Simon Hanisch, Thorsten Strufe) and Provable Security for the Onion Routing and Mix Network Packet Format Sphinx (Philip Scherer, Christiane Weis, Thorsten Strufe) have been accepted at PETS 2024. The preprints are available at arXiv: Fantômas & Provable Sphinx Security.
Cybersecurity Necessity and Benefits. Second, the exploration of human factors in the framework of cyber-security can assist in resolving the issues of understanding a defender's cognitive state, possibilities for automation, and an attacker's subjective traits. Cybersecurity Incident Response and Risk Minimization.
Published: Jan 16, 2024. Inside This Article. 127 Cyber Security Essay Topic Ideas & Examples. With the increasing reliance on technology, cyber security has become a critical concern for individuals, organizations, and governments worldwide. As cyber threats continue to evolve and become more sophisticated, it is essential to stay informed ...
October 2003. In the context of conflict resolution, the definition of "security" depends on one's perspective. At the simplest level, security may be defined as "the quality or state of being secure," "freedom from danger," or "freedom from fear or anxiety." Of the many other levels on which one can analyze security, the most relevant here are ...
Cybersecurity has been an evergreen subject recently. According to Daniele Irandoost, cyberspace has had many benefits in almost every important country's sector (Irandoost, 2018). The initial intention for developing cyberspace was to open avenues for people to communicate unlimitedly and promote efficiency in operations.
Welcome to the website of the Artificial Intelligence and Security research group at KIT. Our research group combines machine learning (or AI in the broader scope) and computer security. In particular, we develop methods in system security and application security, for instance, approaches for attack detection or vulnerability discovery in ...
Two reasons - the first one is obvious, but the other one perhaps not so often considered. 1. Secure Workforce. The stronger your security culture is, the more likely your workforce will exhibit secure behaviors, and as a result your organization will be far more secure. This is critical in today's environment.
Cybersecurity means protecting data, networks, programs and other information from unauthorized or unattended access, destruction or change. In today's world, cybersecurity is very important because of some security threats and cyber-attacks. For data protection, many companies develop software. This software protects the data.
The Government of Canada has requested to buy an additional six hundred ninety (690) KMU-572 Joint Direct Attack Munition (JDAM) tail kits; seventy-five (75) KMU-556 JDAM tail kits; and twenty-five (25) KMU-557 JDAM tail kits that will be added to a previously implemented case whose value was under the congressional notification threshold.
The importance of securing sensitive items comes down to maintaining accountability for operation security‚ mission success and a soldiers over all readiness. The habits of exercising security and accountability of a soldiers items allow the soldier and their team to operate to the highest standards or have items be accessed. Premium.
Iran's relationship with nuclear technology has always been ambiguous, even ambivalent. Both during the regime of the pro-western Shah Mohammed Reza Pahlavi in the 1960s and 1970s and the anti ...
Only a few hours later, the employee watched as the hacker remotely accessed the supervisory control and data acquisition (SCADA) system to raise the amount of sodium hydroxide to 11,100 parts per million, up from 100 parts per million.Such an increase would make the drinking water caustic.
They test the security systems. Ideally you want to read a review written by someone who has tested the system. This way, they can share specifics about how it functions. Taking the thing out of the box and actually testing it is the best way to get a full picture of the product. They score the security systems.
CVE-2024-30040 is a security feature bypass in MSHTML, a component that is deeply tied to the default Web browser on Windows systems. Microsoft's advisory on this flaw is fairly sparse, but ...
The task before Judge Aileen Cannon, who is presiding over the classified documents case of Donald Trump, is not easy. She must protect Mr. Trump's constitutional rights while also ensuring the ...
Kickstart your AI journey with the Copilot adoption kit . If you're ready to train your users on how to make the most of AI at work, use the customizable resources in the Copilot adoption kit. Available in nine languages, this kit includes ready-made resources such as a training presentation, company-wide communications, tip sheets, and more.
Olivia and Liam are the most popular baby names in the U.S. for the fifth consecutive year, according to an annual tally by the Social Security Administration.
Social Security (Childcare Subsidy) Amendment Regulations 2024. 22 May 2024. The paper seeks agreement to amendments to the Social Security Regulations 2018 to allow parents and caregivers access to the Childcare Subsidy to pay for top-up payments required by home-based educators for 20 Hours ECE from 3 June 2024.
AMD Infinity Guard offers advanced modern security features to help defend against threats, keeping your data centers' data safe & secure. Learn More! ... Evaluation Boards & Kits. Evaluation Boards; Boards & Kits Accessories; Software, Tools, & Apps . ... AMD EPYC White Papers Solution Briefs Find AMD and partner documentation on deploying AMD ...
Camera-ready papers will be due in advance of the conference. All camera-ready papers must include a funding disclosure. We strongly encourage accompanying code and data to be submitted with accepted papers when appropriate, as per the code submission policy. Authors will be allowed to make minor changes for a short period of time after the ...
The Disability Starter Kit will help you get ready for your disability interview or online application. Kits are available for adults and for children under age 18. The starter kits provide information about the specific documents and the information that we will request from you. We will ask for more details during your interview.