Academia.edu no longer supports Internet Explorer.
To browse Academia.edu and the wider internet faster and more securely, please take a few seconds to upgrade your browser .
Enter the email address you signed up with and we'll email you a reset link.
- We're Hiring!
- Help Center


Cyber Security Awareness, Knowledge and Behavior: A Comparative Study

2020, Journal of Computer Information Systems
Cyber-attacks represent a potential threat to information security. As rates of data usage and internet consumption continue to increase, cyber awareness turned to be increasingly urgent. This study focuses on the relationships between cyber security awareness, knowledge and behavior with protection tools among individuals in general and across four countries: Israel, Slovenia, Poland and Turkey in particular. Results show that internet users possess adequate cyber threat awareness but apply only minimal protective measures usually relatively common and simple ones. The study findings also show that higher cyber knowledge is connected to the level of cyber awareness, beyond the differences in respondent country or gender. In addition, awareness is also connected to protection tools, but not to information they were willing to disclose. Lastly, findings exhibit differences between the explored countries that affect the interaction between awareness, knowledge, and behaviors. Results, implications, and recommendations for effective based cyber security training programs are presented and discussed.
Related Papers
Issues In Information Systems
Dusan Lesjak
IEEE Access
Ana Kovacevic
BROU PATRICK ERVIN BENIE
International Journal of Commerce, IT & Management, Vol. 3 (8), 2013
Semiu Akanmu
Nazar Elfadil
Cybersecurity plays an important role in reliance on digital equipment and programs to manage daily lives chores including the transmission and storage of personal information. Therefore, it is a global issue in our growing society, and it becomes increasingly important to measure and analyze the awareness of it. In this paper, a questionnaire has been designed to measure the current level of cybersecurity awareness (CSA) among Saudi university students. Cybersecurity students' awareness level questionnaire has been adapted from few other previous cybersecurity awareness campaigns. In this questionnaire, a total of 136 students have participated in the survey. The questionnaire was collected to measure the cybersecurity students’ awareness level through their knowledge, culture, and surrounding environment or through students’ behavior by thee affected factors. These are: gender, location, and study department of the students. The study findings reveal that the students’ awarene...
European Scientific Journal ESJ
Abdalmonem Tamtam
The abundance of information available through the Internet, mobile applications, and cloud computing has made it convenient for users to access a wide range of information. However, this convenience comes with a cost as this information is constantly at risk of being compromised by cybercriminals and hackers. While the recognition of the potential dangers of information security is increasing in developed countries, in regions like Libya in North Africa, the level of protection for this information is insufficient. The purpose of this study is to examine the various factors that may influence or affect the users’ practice and awareness at home. The investigated factors are policy, behavior, training, knowledge of IT and education. In order to accomplish the goals of this study, a quantitative methodology was implemented. Specifically, a survey was created to assess the correlation between key factors and security awareness and practices in the home environment. The survey attracted...
Research Trend
Mahdi Alhaji Musa
The emergence of the internet and also the use of various online applications and the exposure to the social platforms that are evolving day by day have positioned students to online risk. Online fraud, cyber-bully, phishing are among those risks students are exposed to in their daily activities. To find a solution to that, cybersecurity awareness can prepare them to protect themself against such risk. This research aims to investigate the students' awareness of basic knowledge of cybersecurity. A quantitative approach was used for data collection using a set of designed questionnaires, this method was used to investigate the students' cybersecurity knowledge and observe their behavior toward using the internet, from the survey a total of 201 Computer Science students in the Department of Computer Science at Yobe State University, Nigeria participated in the study. The research has encountered moderate responses from the students as all universities are close at this period due to the COVID 19 pandemic, only students living in urban were able to reach out in the study. The result obtained from the experiment were analyzed and it shows the University students' cybersecurity awareness is at a satisfactory level and more than average of the students are not well aware of how to protect their data. The research contribution is, there is no active cybersecurity awareness program in place, and also females' students are more likely to be the victim of cyber-attack. Besides that, the survey alsoindicated a high enthusiasm for students to learn more about cybersecurity.
Mimi Zazira Hashim
Studies shows that training is good alternative to deliver cybersecurity knowledge to kids. This paper reports on the finding of the study after conducting an awareness training program. The ultimate goal of the program is to help children and kids to understand issues related to cybersecurity and instill the cybersecurity awareness. Children are now discovering computers, smartphones or tablets at an early age. Even though Internet connected computers and mobile devices can be useful for learning, enhance social relations and keep young users connected to their parent, it can also be a source of danger and concern for parents. Safer browsing habits need to be cultivated as much as earlier among them. Cybersecurity awareness training was conducted to deliver the content to the target group. The objectives of this study are to examine cybersecurity awareness after the participant go through the training, to suggest several measures to improve a better understanding on cybersecurity a...
Journal of Cybersecurity and Privacy
Knowledge of possible cyber threats as well as awareness of appropriate security measures plays a crucial role in the ability of individuals to not only discriminate between an innocuous versus a dangerous cyber event, but more importantly to initiate appropriate cybersecurity behaviors. The purpose of this study was to construct a Cybersecurity Awareness INventory (CAIN) to be used as an instrument to assess users’ cybersecurity knowledge by providing a proficiency score that could be correlated with cyber security behaviors. A scale consisting of 46 items was derived from ISO/IEC 27032. The questionnaire was administered to a sample of college students (N = 277). Based on cybersecurity behaviors reported to the research team by the college’s IT department, each participant was divided into three groups according to the risk reports they received in the past nine months (no risk, low risk, and medium risk). The ANOVA results showed a statistically significant difference in CAIN sco...
Fariza Khalid
The emergence of various online applications and abundance of exposure to the use of social media nowadays had put users in higher potential to online related risks. Racial abuse, cyber-bullying, online fraud, addiction towards gaming and gambling and pornography are among the risks that online users may be exposed to in their daily life. To protect oneself from these risks, it has to come from self-awareness. This research aims to investigate university students' awareness of cybersecurity. Research data was collected usi ng a set of questionnaire to 142 second-year students in the faculty of education in one of the universities in Malaysia. Descriptive data analysis was done using an SPSS software. The result of this study showed that even though these university students demonstrated a hi gh level of awareness on certain elements in cyber security such as cyber bully, personal information, and internet banking, there are still lacking appropriate knowledge on the aspect of cyber-sex and self-protection. This paper also discusses the role of all level of community in educating children and young adults in this matter.
RELATED PAPERS
Beytulhikme An International Journal of Philosophy
Murat Bahadır
Gerrit De Waal
International Journal of Knowledge-Based Development
Robert B Mellor
Health Security
Tanko Ishaya
SPE Drilling & Completion
Ryan Graham
Political Science and Politics
Thomas Heilke
Beatriz Rivero
Cryobiology
Dariusz Kulus
László Ferenczi
Joice Waani
Revista Avances en Sistemas e Informática
mauricio alberto quiroz castro
Archives of Pharmacal Research
Toxicology Letters
John Snawder
Pablo Cobreros
International Journal of Public Health Science (IJPHS)
adi mamahit
De Gruyter eBooks
Cecilia Panti
Journal of Architecture and Urbanism
Jonas Jakaitis
SMU毕业证文凭圣玛丽大学学院本科毕业证书 英国学历学位认证如何办理
Luca Cioccolanti
Molecular Biology Reports
didem tecimel
European Journal of Immunology
Aranzazu Cruz-Adalia
Elide Alinovi
Revista Chilena de Antropología
Nicole Fuenzalida
Revista Venezolana De Computacion
J. Germán Juárez Rodríguez
RELATED TOPICS
- We're Hiring!
- Help Center
- Find new research papers in:
- Health Sciences
- Earth Sciences
- Cognitive Science
- Mathematics
- Computer Science
- Academia ©2024

LIACS Thesis Repository

These webpages contain theses and reports by students affiliated with the various bachelor and master programmes offered at the Leiden Institute of Advanced Computer Science ( LIACS ), the computer science and artificial intelligence department of Leiden University . Note: this thesis repository might be incomplete for certain programmes.
Master ICT in Business and the Public Sector
The following thesis was written by a student in the 2020-2021 class of the Master ICT in Business and the Public Sector programme at Leiden University.
Thesis details
Citation details
Touhami, Mounaim Ben, Quantifying the Effectiveness of Cyber Security Awareness on Human Behavior , Thesis Master ICT in Business and the Public Sector, LIACS, Leiden University, 2021.
Cyber-Security awareness and its contribution towards sustainable human development: insights from the Zimbabwean context
Cybersicherheits-Awareness und ihr Beitrag zu einer nachhaltigen gesellschaftlichen Entwicklung: Erkenntnisse aus Zimbabwe
- Original Paper
- Published: 29 April 2024
Cite this article

- Colletor Tendeukai Chipfumbu 1 ,
- Theo Tsokota ORCID: orcid.org/0000-0002-7347-515X 2 &
- Tendayi Marovah 3
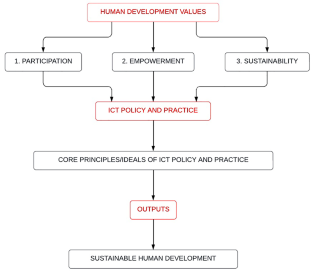
Focusing on citizens’ awareness of cyber-security, this paper contributes to debates on ICTs and their contribution towards human development. The paper philosophically argues for the importance of cyber-security and cybercrime awareness in fostering sustainable human development through the responsible and meaningful use of ICT. Using the overarching values of the human development framework (empowerment, participation and sustainability), the paper assesses government ICT policy documents and subsequent initiatives such as the establishment of community information centres and integration of ICT in the education sector. This was done to establish the extent to which citizens have been provided with prerequisite knowledge and skills to deal with cyber-crime. It emerged from the study that regardless of the effort by the Government of Zimbabwe (GoZ) to enforce a law which encourage a cyber-security culture, awareness about cyber-security remains far below what can be expected in a cyber-world. As a result, if citizens’ lack cyber knowledge their freedom to be and do what they reasonably value on the Internet is continually threatened. The paper, thus, suggests the introduction of rigorous citizens’ awareness campaigns on cyber-crime and security to enable them to deal with unfounded fears and experiences that potentially limit their ability to deliberate, transact or act to be and freely do what they reasonably value.
This is a preview of subscription content, log in via an institution to check access.
Access this article
Price includes VAT (Russian Federation)
Instant access to the full article PDF.
Rent this article via DeepDyve
Institutional subscriptions
Data availability
The datasets generated during and/or analyzed during the current study are available from the corresponding author on reasonable request.
Abawajy J (2014) User preference of cyber security awareness delivery methods. Behav Inf Technol 33(3):237–248
Article MathSciNet Google Scholar
Aspray W, Doty P (2023) Does technology really outpace policy, and does it matter? A primer for technical experts and others. Asso for Info Science & Tech 74(8):885–904
Article Google Scholar
Bada M, Sasse A (2014) Cyber Security Awareness Campaigns: Why Do They Fail to Change Behaviour? . Retrieved from. http://discovery.ucl.ac.uk/1468954
Carvalho J, Francisco R, Relvas AP (2015) Family functioning and information and communication technologies: How do they relate? A literature review. Comput Human Behav 45:99–108
Chikakano J (2019) Zimbabwe’s proposed cyberspace regulatory framework and its likely effects on FOE and A2l. In MISA Zimbabwe Commentaries on The Cyber crime and Cyber Security Bill—2017. Media: 22–37 (Insitute of Sourthern Africa Zimbabwe Chapter)
Chirwa DM, Ncube CB (eds) (2023) The internet, development, human rights and the law in Africa. Taylor & Francis
Google Scholar
Choi M, Levy Y, Hovav A (2013) The role of user computer self-efficacy, cybersecurity countermeasures awareness, and cybersecurity skills influence on computer misuse. Proceedings of the Pre-International Conference of. Inf Syst 14(2013) ((ICIS) SIGSEC—Workshop on Information Security and Privacy (WISP), Milano)
Chuma W (2018) The politics of media policy making in a contested transition: The case of Zimbabwe’s government of national unity. Int J Commun 12(19):2009–2013
Cone BD, Irvine CE, Thompson MF, Nguyen TD (2007) A video game for cyber security training and awareness. Computers and Security 26(1):63–72
Cornish P, Hughes R, Livingstone D (2009a) Cyberspace and the National Security of the. Threats and Responses. Chatham House, London, United Kingdom
Cornish P, Hughes R, Livingstone D (2009b) Cyberspace and the national security of the United. Kingdom threats Responses Chatham House London 1(1):1–46
Demirer V (2016) Information and Communication Technologies. In Instructional Process and Concepts in Theory and Practice. Springer, pp 493–523
Dutt, V., Ahn, Y.-S., & Gonzalez, C. (2013). Cyber situation awareness: modeling detection of cyber attacks with instance-based learning theory. Human Factors, 55(3), 605–618.
Frank, I., & Odunayo, E. (2013). Approach to cyber security issues in Nigeria: challenges and solution. International Journal of Cognitive Research in science, engineering and education, 1(1), 100–110.
Grobler M, Gaire R, Nepal S (2021) User, usage and usability: Redefining human centric cyber security. Front Big Data 4:1–18
Hadlington L, Murphy K (2018) Is media multitasking good for cybersecurity? exploring the relationship between media multitasking and everyday cognitive failures on self-reported risky cybersecurity behaviors. Cyberpsychology, Behavior, and Social Networking 21(3):168–172
Humayun M, Niazi M, Jhanjhi N, Alshayeb M, Mahmood S (2020) Cyber security threats and vulnerabilities: a systematic mapping study. Arab J Sci Eng 45:3171–3189
Hungwe B (2019) Disserting the Cyber crime and Cyber Security Bill—2017. In MISA Zimbabwe Commentaries on The Cyber crime and Cyber Security Bill—2017. Media: 38–51 (Insitute of Southern Africa)
Ibrahim S (2014) Introduction. The Capability Approach: From Theory to Practice: Rationale, Review and. Reflections (In S. Ibrahim & M. Tiwari (Eds.), In The Capability Approach: From Theory to Practice. Palgrave Macmillan)
Imhonopi D, Urim U (2015) Information and communication technology. Ict) Gov Niger Challenges Prospect journal Humanit Soc Sci Creat Arts 6(2):1–14
Kortjan N, von Solms R (2014) A conceptual framework for cyber-security awareness and education in SA. South African Comput J 52(1):29–41
Kritzinger E, von Solms SH (2010) Cyber security for home users: A new way of protection through awareness enforcement. Comput Secur 29(8):840–847
Magidi M (2024) De-industrialisation, Urban Governance Challenges and Deteriorating Urban Infrastructure in Norton, Zimbabwe: Is the Town Ruralising? In Secondary Cities and Local Governance in Southern. Africa: 255–269 (Springer)
Makeri YA (2017) Cyber security issues in Nigeria and challenges. Int J 7(4)
Marovah T (2013) Citizenship education and human capabilities: lynchpin for sustainable learning environment and social justice. TD. J Transdiscipl Res South Africa 9(3):593–607
Marovah T (2020) Using the capability approach to assess the value of Ubuntu: Comprehensive citizenship in Zimbabwean higher education. In Teaching and Learning for Comprehensive Citizenship. Routledge, pp 95–113
Mazango E (2017) Media games and shifting of spaces for political communication in Zimbabwe. Westminster papers in communication and. culture, vol 2, pp 33–55
McCowan T, Unterhalter E (2013) Education, Citizenship and Deliberative Democracy: Sen’s Capability Perspective: Tristan McCowan and Elaine Unterhalter. In Education for Civic and Political Participation. Routledge, pp 142–161
Mhiripiri, N. A., & Ureke, O. (2018). Theoretical paradoxes of representation and the problems of media representations of Zimbabwe in crisis. Critical Arts, 32(5-6), 87–103.
(2020) MISA. Cybersecurity (and Data Protection Bill entrenches surveillance: MISA Zimbabwe analysis of the Cybersecurity and Data Protection Bill 2019. M. Zimbabwe)
Motlanthe K (2018) Report of the Commission of. Inquiry (into the 1st of August 2018 Post-Election Violence. G. o. Zimbabwe)
Mpofu M (2023) Media Policies and Practices in Zimbabwe’s ‘New Dispensation’. In Making Politics in Zimbabwe’s Second Republic: The Formative Project by Emmerson Mnangagwa. Springer, pp 87–104
Mpofu S, Mutsvairo B, Matsilele T (2023) Uncovering the Power of Whistleblowing as a New Form of Citizen Journalism in Non-democratic Countries. In Different Global Journalisms: Cultures and. Contexts: 85–106 (Springer)
Msongelwa-Njini JB, Dube SS (2013) Computer ethical challenges facing professionals in Zimbabwe. International Conference on ICT for. Africa: 20–23 (Harare, Zimbabwe)
Mushunje M (2020) Customer Perceptions of Community. Information (Centres in Zimbabwe University of Pretoria)
Mutsvairo B, Columbus S (2012) Emerging patterns and trends in citizen journalism in Africa: The case of Zimbabwe. Cent Eur J Commun 1(5):121–135
Mwase T, Marovah T (2023) Decolonising the Zimbabwean ordinary level Food Technology and Design curriculum. Cogent Educ 10(1):1–15
Ncube T, Murray U, Dennehy D (2023) Digitalising Social Protection Systems for Achieving the Sustainable Development Goals: Insights from Zimbabwe. CAIS 53(1):138–161
Ndawana E (2023) The Potential Role of Social Media in Peacebuilding in Zimbabwe. J Peacebuilding Dev 18(1):53–67
Ndubueze PN (2020) Cybercrime and Legislation in an African Context. The. Palgrave, Handbook of International Cybercrime and Cyberdeviance, pp 345–364
Nicholls G (2014) Professional development in higher education: New dimensions and directions. Routledge
Book Google Scholar
Nussbaum MC (2011) Capabilities, entitlements, rights: Supplementation and critique. J Human Dev Capabil 12(1):23–37
Pretorius A, Blaauw D (2015) Getting to know the Amakwerre-kwerre: the socio-economic circumstances of Zimbabwean day labourers in South Africa. Ethn Racial Stud 38(5):808–823
Saidi U (2022) Against the Grain: The Tragedy of Zimbabwe in the Context of 4 IR. Africa and the Fourth Industrial Revolution: Curse or Cure? Advances: 67–90 (in African Economic, Social and Political Development. Springer, Cham)
Saki O (2019) Omnibus Laws in Zimbabwe. In MISA Zimbabwe Commentaries on The Cyber crime and Cyber Security. Bill, vol 2017. Media Insitute of Southern Africa Zimbabwe Chapter, pp 4–21
Sarkar G, Singh H, Kumar S, Shukla SK (2023) Tactics, techniques and procedures of cybercrime: A methodology and tool for cybercrime investigation process. Proceedings (18th International Conference on Availability, Reliability and Security)
Schmid R, Petko D (2019) Does the use of educational technology in personalized learning environments correlate with self-reported digital skills and beliefs of secondary-school students? Comput Educ 136:75–86
Sen A (1999) Development as Freedom. Knopf, Oxford: Oxford University Press
Senol M, Karacuha E (2020) Creating and implementing an effective and deterrent national cyber security strategy. J Eng 20:1–19
Sharma R (2012) Study of latest emerging trends on cyber security and its challenges to society. Int J Sci Eng Res 3(6):1–4
MathSciNet Google Scholar
Sibanda MN, Ndlovu M (2023) An Alternative Arena for “Communities of Resistance”? Podcasting, Democratic Spaces, and Counterpublics in Zimbabwe. In Converged Radio, Youth and Urbanity in Africa: Emerging trends and perspectives. Springer, pp 37–53
Snyder H (2019) Literature review as a research methodology: An overview and guidelines. J Bus Res 104:333–339
Tshabangu T, Salawu A (2024) Alternative media, repression and the crisis state: Towards a political economy of alternative media in post-Mugabe Zimbabwe. J Asian Afr Stud 59(1):172–186
Tsokota T, von Solms R, van Greunen D (2014) Towards a strategy for ICT integration in the tourism sector in Zimbabwe. The 6th Annual International Conference on ICT for. Africa 2014:
UNDP (2022) The 2021. Hum Dev 202(2) (Report, Uncertain times, unsettled lives Shaping our future in a transforming world. UNDP, New York)
UNESCO. (2012a). Exploring Sustainable Development: A Multiple-Perspective Approach S. a. C. O. United Nations Educational. https://sustainabledevelopment.un.org/content/documents/732unesco.pdf
UNESCO. (2012b). Shaping the Education of Tomorrow: 2012 Full-length Report on the UN Decade of Education for Sustainable Development United Nations Decade of Education for Sustainable Development (2005–2014), Issue. S. a. C. O. United Nations Educational.
Veletsianos G, Kimmons R (2016) Scholars in an increasingly open and digital world: How do education professors and students use Twitter? Internet High Educ 30:1–10
von Solms R, van Niekerk J (2013) From information security to cyber security. Comput Secur 38:97–102
Walker M (2012) A capital or capabilities education narrative in a world of staggering inequalities? Int J Educ Dev 32(3):384–393
World Bank. (2024). World Bank Data. World Bank. Retrieved 27 March 2024 from https://data.worldbank.org/country/zimbabwe
Yu W, Xu G, Chen Z, Moulema P (2013) A cloud computing based architecture for cyber security situation awareness. In, vol 2013. IEEE, IEEE conference on communications and network security (cNS), pp 488–492
Zeldin W (2012) UN Human Rights Council: First Resolution on Internet Free Speech. Library (of Congress. Global Legal Monitor)
Download references
Acknowledgements
I thank the anonymous reviewers for their helpful comments.
Author information
Authors and affiliations.
Department of Information and Marketing Sciences, Midlands State University, P. Bag 9055, Gweru, Zimbabwe
Colletor Tendeukai Chipfumbu
Theo Tsokota
Dept. of Humanities, Business Development & Arts Education, Midlands State University, P. Bag 9055, Gweru, Zimbabwe
Tendayi Marovah
You can also search for this author in PubMed Google Scholar
Contributions
The Author contributed to the whole process of the preparation of thevmanuscript. All authors read and approved the final manuscript.
Corresponding author
Correspondence to Theo Tsokota .

Ethics declarations
Conflict of interest.
C.T. Chipfumbu, T. Tsokota and T. Marovah declare that they have no competing interests. Informed Consent All procedures required by the were followed prior to carrying out research permission. All the relevant information was provided.
Additional information
Publisher’s note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
Reprints and permissions
About this article
Chipfumbu, C.T., Tsokota, T. & Marovah, T. Cyber-Security awareness and its contribution towards sustainable human development: insights from the Zimbabwean context. Int. Cybersecur. Law Rev. (2024). https://doi.org/10.1365/s43439-024-00120-6
Download citation
Received : 27 February 2024
Accepted : 04 April 2024
Published : 29 April 2024
DOI : https://doi.org/10.1365/s43439-024-00120-6
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Citizenship
- Cyber-security
- Human development
- Sustainable development
- Find a journal
- Publish with us
- Track your research
Google Custom Search
Wir verwenden Google für unsere Suche. Mit Klick auf „Suche aktivieren“ aktivieren Sie das Suchfeld und akzeptieren die Nutzungsbedingungen.
Hinweise zum Einsatz der Google Suche
- Professorship of Cyber Trust
- TUM School of Computation, Information and Technology
- Technical University of Munich
Teaching at the Professorship of Cyber Trust
Theses and student projects.
We offer motivated students interested in our research projects the opportunity to write their Thesis (Bachelor or Master) or to conduct Guided Research Projects.
Application
Please send your application to one of our chair members via email, including your motivation (i.e. why you are interested in our research), a short CV and your current Examination Report (TUMonline → Studies → Transcripts → Print Examination Report). Please do not hesitate to contact us for further information.
Open Student Projects
This list is not comprehensive. Please browse through our researchers' websites if you are looking for different topics you may be interested to work on.
Assigned Student Projects
Completed student projects.
- Bibliography
- More Referencing guides Blog Automated transliteration Relevant bibliographies by topics
- Automated transliteration
- Relevant bibliographies by topics
- Referencing guides
Dissertations / Theses on the topic 'Information security awareness'
Create a spot-on reference in apa, mla, chicago, harvard, and other styles.
Consult the top 50 dissertations / theses for your research on the topic 'Information security awareness.'
Next to every source in the list of references, there is an 'Add to bibliography' button. Press on it, and we will generate automatically the bibliographic reference to the chosen work in the citation style you need: APA, MLA, Harvard, Chicago, Vancouver, etc.
You can also download the full text of the academic publication as pdf and read online its abstract whenever available in the metadata.
Browse dissertations / theses on a wide variety of disciplines and organise your bibliography correctly.
Lund, Per. "Information Security Awareness amongst students : A study about information security awareness at universities." Thesis, Luleå tekniska universitet, Institutionen för system- och rymdteknik, 2018. http://urn.kb.se/resolve?urn=urn:nbn:se:ltu:diva-70873.
Toussaint, Gregory W. "Executive security awareness primer." Thesis, Utica College, 2015. http://pqdtopen.proquest.com/#viewpdf?dispub=1586318.
The purpose of this paper was to create a primer for a security awareness program to educate senior level executives on the key aspects of cyber security. This is due to the gap area that was discovered in the lack of both executive security awareness programs, and the lack of executives that fully abide by their company's security policies. This, coupled with research showing that executives are highly targeted by attackers, was the impetus behind this project. It was determined that the content of an executive security awareness program should be similar to that of a security awareness program for all other employees, with the differences being in the delivery and time frame of each segment. Due to this, literature was reviewed on the various topics of security awareness. Research revealed the importance of capturing an executive's attention, in order to keep their interest in the program. It was recommended that individuals charged with creating an executive security awareness program begin by having one on one meetings with the executives in their company. These meetings will help assess the time constraints of their company executives as well as their current knowledge of the various security awareness topics. This will help with tailoring the program specifically to their company executives. This primer may be used by any company or organization in the beginning stages of creating their own security awareness program for executives. Keywords: Cybersecurity, Professor Albert Orbinati, Executive Security Awareness, Internet Safety.
Korovessis, Peter. "Establishing an information security awareness and culture." Thesis, University of Plymouth, 2015. http://hdl.handle.net/10026.1/3836.
Puhakainen, P. (Petri). "A design theory for information security awareness." Doctoral thesis, University of Oulu, 2006. http://urn.fi/urn:isbn:9514281144.
Talib, Shuhaili. "Personalising information security education." Thesis, University of Plymouth, 2014. http://hdl.handle.net/10026.1/2896.
Turesson, Michael, Vadim Koroliov, and Ola Brolin. "What is your password? : Assessing information security awareness among employees in an organisation." Thesis, Jönköping University, JIBS, Business Informatics, 2009. http://urn.kb.se/resolve?urn=urn:nbn:se:hj:diva-9655.
The development of Information and Communication Technologies has opened up a large pool of possibilities for any and every business actor. These possibilities have brought up new vulnerabilities as well. Information security has become an inherent part of any organization. Companies and organizations invest significant amount of resources in IT security solutions, usually omitting the weakest link of the defense - the people.
The research intended to study and evaluate the information security awareness level of employees in a public organization which preferred to remain anonymous. This study is based on a mixed-methods approach. A survey was built up and performed, basing on the interview of the employees and the IT Security Chief. The interview intended to give a general picture of the attitude, knowledge and behavior the employees towards information security and its constituent aspects.
The results of the survey show that the information security awareness at this particular organization has an average performance based on the grading scale determined by the management of the company. Generally speaking, half of the information security focus areas show underdeveloped sense of awareness among employees, whereas the other focus areas are close to perfect. In terms of information security, the research indicates that there is a gap between the employees' theoretical condition and their day to day be-havior. In other words, the theoretical and practical preparation of the employees does not provide an appropriate information security awareness behavior. Some of the reasons for unsecure behavior were complex and sophisticated security designs including passwords; another problem was inherent in the work design which imposed the use of multiple systems and applications in the daily work.
In the end, the research suggests some recommendations for improvement, as well as practices to sustain a desirable level of information security awareness level. The overall information security awareness program required immediate improvements in order to boost the positive attitude and behavior of employees towards information security, as well as enrich the knowledge of information security in general.
Spandonidis, Bladimiros. "Linking Information Security Awareness to Information Security Management Strategy.A Study in an IT Company." Thesis, Linnéuniversitetet, Institutionen för informatik (IK), 2015. http://urn.kb.se/resolve?urn=urn:nbn:se:lnu:diva-45894.
Harris, Mark. "THE SHAPING OF MANAGERS’ SECURITY OBJECTIVES THROUGH INFORMATION SECURITY AWARENESS TRAINING." VCU Scholars Compass, 2010. http://scholarscompass.vcu.edu/etd/2208.
Mauwa, Hope. "Information security awareness: generic content, tools and techniques." Thesis, Nelson Mandela Metropolitan University, 2007. http://hdl.handle.net/10948/560.
Ashenden, D. M. "Information security awareness : improving current research and practice." Thesis, University College London (University of London), 2015. http://discovery.ucl.ac.uk/1469598/.
Hanus, Bartlomiej T. "The Impact of Information Security Awareness on Compliance with Information Security Policies: a Phishing Perspective." Thesis, University of North Texas, 2014. https://digital.library.unt.edu/ark:/67531/metadc699974/.
Almualla, Mohammed Humaid. "Collaborative cyber security situational awareness." Thesis, Brunel University, 2017. http://bura.brunel.ac.uk/handle/2438/16206.
Casmir, Respickius. "A Dynamic and Adaptive Information Security Awareness (DAISA) Approach." Doctoral thesis, Kista : Department of Computer & Systems Sciences, Stockholm University [Institutionen för data- och systemvetenskap, Stockholms universitet], 2005. http://urn.kb.se/resolve?urn=urn:nbn:se:su:diva-743.
Bauer, Stefan, Edward Bernroider, and Katharina Chudzikowski. "Prevention is better than cure! Designing information security awareness programs to overcome users' non-compliance with information security policies in banks." Elsevier, 2017. http://dx.doi.org/10.1016/j.cose.2017.04.009.
Edwards, Keith. "Examining the Security Awareness, Information Privacy, and the Security Behaviors of Home Computer Users." NSUWorks, 2015. http://nsuworks.nova.edu/gscis_etd/947.
Grant, Gordon J. "Ascertaining the Relationship between Security Awareness and the Security Behavior of Individuals." NSUWorks, 2010. http://nsuworks.nova.edu/gscis_etd/167.
Uffen, Jörg [Verfasser]. "Information security management and employees' security awareness : an analysis of behavioral determinants / Jörg Uffen." Hannover : Technische Informationsbibliothek und Universitätsbibliothek Hannover (TIB), 2014. http://d-nb.info/1051037875/34.
Alkahtani, Hend K. "Raising the information security awareness level in Saudi Arabian organizations through an effective, culturally aware information security framework." Thesis, Loughborough University, 2018. https://dspace.lboro.ac.uk/2134/28120.
Al, Salek Aous. "INFORMATION SECURITY AWARENESS TRAINING FOR END-USER : A Survey on the Perspective of Nordic Municipalities." Thesis, Högskolan i Skövde, Institutionen för informationsteknologi, 2021. http://urn.kb.se/resolve?urn=urn:nbn:se:his:diva-20163.
Bulgurcu, Burcu. "The antecedents of information security policy compliance." Thesis, University of British Columbia, 2008. http://hdl.handle.net/2429/1121.
Lambe, Erik. "Information Security Culture and Threat Perception : Comprehension and awareness of latent threats in organisational settings concerned with information security." Thesis, Uppsala universitet, Statsvetenskapliga institutionen, 2018. http://urn.kb.se/resolve?urn=urn:nbn:se:uu:diva-352263.
Rydefelt, Calatayud Leonor. "A holistic model to create organizational information security awareness programs – iSAP." Thesis, KTH, Skolan för informations- och kommunikationsteknik (ICT), 2011. http://urn.kb.se/resolve?urn=urn:nbn:se:kth:diva-48050.
Banerjea-Brodeur, Nicolas Paul. "Advance passenger information passenger name record : privacy rights and security awareness." Thesis, McGill University, 2003. http://digitool.Library.McGill.CA:80/R/?func=dbin-jump-full&object_id=80909.
Ashaju, Oluwafemi. "Investigating the Effects of Information Security Awareness in the Third Sector." Thesis, Luleå tekniska universitet, Digitala tjänster och system, 2020. http://urn.kb.se/resolve?urn=urn:nbn:se:ltu:diva-79531.
Ojala, Burman Emma. "Impact of demographic factors on information security awareness : a study on professionals and students in Sweden." Thesis, Högskolan i Skövde, Institutionen för informationsteknologi, 2021. http://urn.kb.se/resolve?urn=urn:nbn:se:his:diva-20151.
Donaldson, Jacob. "Empathy in Security: The Effect of Personalized Awareness and Training Initiatives on Information Security Attitude and Behavioral Intention." Ohio University Honors Tutorial College / OhioLINK, 2021. http://rave.ohiolink.edu/etdc/view?acc_num=ouhonors1618497031421455.
Bukelwa, Ngoqo. "The establishment of a mobile phone information security culture: linking student awareness and behavioural intent." Thesis, University of Fort Hare, 2014. http://hdl.handle.net/10353/657.
Scrimgeour, Juan-Marc. "A method for implementing an information security awareness campaign within an organisation." Master's thesis, Faculty of Commerce, 2019. https://hdl.handle.net/11427/31786.
Waddell, Stanie Adolphus. "A Study of the Effect of Information Security Policies on Information Security Breaches in Higher Education Institutions." NSUWorks, 2013. http://nsuworks.nova.edu/gscis_etd/331.
Gundu, Tapiwa. "Towards an information security awareness process for engineering SMEs in emerging economies." Thesis, University of Fort Hare, 2013. http://hdl.handle.net/10353/d1007179.
Waly, Nesren Saleh. "Organisational information security management : the impact of training and awareness : evaluating the socio-technical impact on organisational information security policy management." Thesis, University of Bradford, 2013. http://hdl.handle.net/10454/5666.
McDaniel, Christopher R. Tardy Matthew L. "Role-based access control for coalition partners in maritime domain awareness /." Monterey, Calif. : Springfield, Va. : Naval Postgraduate School ; Available from National Technical Information Service, 2005. http://library.nps.navy.mil/uhtbin/hyperion/05Jun%5FMcDaniel.pdf.
Ball, Albert. "A Comparison of Users' Personal Information Sharing Awareness, Habits, and Practices in Social Networking Sites and E-Learning Systems." NSUWorks, 2012. http://nsuworks.nova.edu/gscis_etd/84.
Agrianidis, Anastasios. "Information Security Training and Serious Games." Thesis, Luleå tekniska universitet, Institutionen för system- och rymdteknik, 2021. http://urn.kb.se/resolve?urn=urn:nbn:se:ltu:diva-85460.
Cone, Benjamin D. "A CYBERCIEGE campaign fulfilling Navy information assurance training and awareness requirements." Thesis, Monterey, Calif. : Springfield, Va. : Naval Postgraduate School ; Available from National Technical Information Service, 2006. http://library.nps.navy.mil/uhtbin/hyperion/06Mar%5FCone.pdf.
Hammarstrand, Johanna, and Tommy Fu. "Information security awareness and behaviour: of trained and untrained home users in Sweden." Thesis, Högskolan i Borås, Akademin för bibliotek, information, pedagogik och IT, 2015. http://urn.kb.se/resolve?urn=urn:nbn:se:hb:diva-10457.
Tesfazion, Henok. "The use of instant messaging applications among swedish students and their security awareness." Thesis, Högskolan i Skövde, Institutionen för informationsteknologi, 2020. http://urn.kb.se/resolve?urn=urn:nbn:se:his:diva-18941.
Smith, Stephen J. C. School of Information Systems Technology And Management UNSW. "An empirical study of information systems security, understanding and awareness in E-government." Awarded by:University of New South Wales. School of Information Systems, Technology And Management, 2005. http://handle.unsw.edu.au/1959.4/23969.
Quesinberry, Malora. "An Analysis of Faculty and Staff's Identification of Malware Threats." Digital Commons @ East Tennessee State University, 2016. https://dc.etsu.edu/etd/3088.
Ntwali, Blaise. "Investigating the Relationship between Learning Styles and Delivery Methods in Information Security Awareness Programs." Master's thesis, Faculty of Commerce, 2021. http://hdl.handle.net/11427/33943.
Malis, Johanna, and Josette Falck. "Informationssäkerhetspolicy och Säkerhetsmedvetenhet : En undersökning av kommunala förvaltningars praktiska arbete med att uppnå informationsäkerhet." Thesis, Högskolan i Halmstad, 2016. http://urn.kb.se/resolve?urn=urn:nbn:se:hh:diva-31863.
Al-Hamar, Aisha. "Enhancing information security in organisations in Qatar." Thesis, Loughborough University, 2018. https://dspace.lboro.ac.uk/2134/33541.
Gamagedara, Arachchilage Nalin Asanka. "Security awareness of computer users : a game based learning approach." Thesis, Brunel University, 2012. http://bura.brunel.ac.uk/handle/2438/7620.
Dawson, Alan Robert. "Exploring Strategies for Implementing Information Security Training and Employee Compliance Practices." ScholarWorks, 2019. https://scholarworks.waldenu.edu/dissertations/7794.
Tardy, Matthew L. "Role-based access control for coalition partners in maritime domain awareness." Thesis, Monterey, California. Naval Postgraduate School, 2005. http://hdl.handle.net/10945/1925.
Alageel, Sami M. "Development of an information security awareness training program for the Royal Saudi Naval Forces (RSNF)." Thesis, Monterey, Calif. : Springfield, Va. : Naval Postgraduate School ; Available from National Technical Information Service, 2003. http://library.nps.navy.mil/uhtbin/hyperion-image/03Jun%5FAlageel.pdf.
Björneskog, Amanda, and Shoshtari Nima Goniband. "Comparison of Security and Risk awareness between different age groups." Thesis, Blekinge Tekniska Högskola, Institutionen för programvaruteknik, 2017. http://urn.kb.se/resolve?urn=urn:nbn:se:bth-14552.
Harper, Allen A. "The impact of consumer security awareness on adopting the Internet of Things| A correlational study." Thesis, Capella University, 2016. http://pqdtopen.proquest.com/#viewpdf?dispub=10196140.
The research topic of this study is the impact of consumer security awareness on the adoption of the Internet of Things. The Internet of Things (IoT) is the emerging network of Internet connected smart devices. Several authors have predicted that adoption of the IoT will be hindered if security issues are not addressed. Other authors have noted that users often trade security and privacy for convenience. To better understand these two points of view, the main research question of this study is: to what extent does consumer security awareness impact adoption of the Internet of Things. To address the competing factors impacting adoption, the unified theory of acceptance and use of technology (UTAUT) will be used as the base model of this study and was extended to account for the construct of security awareness. A quantitative non-experimental correlational study was designed to measure the impact. The population of this study is U.S. adult consumers of Internet connected smart devices. The sample frame was selected from the SurveyMonkey™ voluntary audience panel. Multiple regression was used as the statistical analysis to perform hypothesis testing and attempt to answer the research questions. The findings of the study showed that although there is a statistically significant impact of security awareness on adoption of the IoT, it is not the dominant factor. Other factors, such as performance expectation and effort expectation prove to be better indicators of adoption of the IoT at this time. Several recommendations are given to improve future studies in this area. The results of this study provide business managers, IoT device manufacturers and service providers with valuable information on the relation between awareness of security risks and adoption of the IoT.
Curran, Theresa. "Standardizing Instructional Definition and Content Supporting Information Security Compliance Requirements." Diss., NSUWorks, 2018. https://nsuworks.nova.edu/gscis_etd/1038.
Skärgård, Marie. "Mikroträning som utbildningsmetod inom informationssäkerhet." Thesis, Högskolan i Skövde, Institutionen för informationsteknologi, 2017. http://urn.kb.se/resolve?urn=urn:nbn:se:his:diva-13716.

- Resources / Blog
Understanding the Importance of Cybersecurity Awareness Training

The Vital Importance of Cybersecurity Awareness Training in the Digital Age
When a company falls victim to a malicious cybersecurity attack, there is far more on the line than the subsequent PR nightmare. Yes, a security breach can damage your organization's reputation and trust, but that's just the tip of the iceberg. Identity theft, financial fraud, and disruptions to your business can all occur due to an attack on your company. The truth about cybersecurity in 2023 is that it is about far more than firewalls and endpoint protection. Security is everyone's responsibility, not just IT. If you need proof, consider that this year, 74% of data breaches were caused by human error.
Security experts know your company is only as safe as its least informed employee. However, shockingly, many organizations don't require their staff to complete cybersecurity awareness training.
On this page:
What is Cybersecurity Awareness Training?
Benefits of Cybersecurity Awareness Training
Why cybersecurity awareness training is important, the purpose of cybersecurity awareness training, security case studies.
Like any other type of corporate training, security awareness is about education and giving your employees new skills. It helps your people understand, identify, and avoid cyber threats, which, in turn, helps prevent or mitigate harm to organizations and stakeholders. Cybersecurity awareness is about creating a knowledgeable workforce where each teammate understands their role in maintaining cybersecurity by recognizing and preventing potential breaches.
More companies are undergoing digital transformation and embracing remote work to create a more flexible environment for their employees. As they do, the IT infrastructure grows ever more complicated and vulnerable as a result. A good corporate training program will offer modules on all the most important cybersecurity threats and best practices for responding to them.
Here are the essential topics to include in your organization's training efforts:
Phishing: This attack involves using fraudulent emails or messages to trick recipients into revealing sensitive information, such as login credentials or financial data. Phishing is responsible for one in three successful data breaches and often precedes large-scale exposure. If an attacker obtains an employee's access credentials, they can gain entry to broader systems or networks, compromising a larger pool of sensitive data.
Email Security: Just one deceptive email is all it takes to breach your company's defenses. Training employees to identify and respond appropriately to suspicious emails is step one to building your human firewall.
Password Security: Weak passwords are among the most common ways malicious actors infiltrate your network. Cybersecurity training should always teach employees how to create strong passwords and manage them effectively. Safe passwords should have at least eight characters and include a mix of letters, numbers, and special symbols.
Safe Internet Browsing: We all invariably find ourselves surging the web at some point during the day, which is why you need to teach your team how to do it safely. It may seem like second nature, but all kinds of threats are hiding on the Internet that even seasoned pros can miss. Make sure your team knows to update their browsers regularly and can recognize secure websites and risky online behaviors.
Mobile Device Security: Mobile devices often contain sensitive information, including personal data, corporate emails, and business documents, which means a robust training program must include best practices for securing them.
Network Security: Nearly a third of workers in the U.S. work remotely, at least part-time, commonly using less secure home networks or public Wi-Fi. The safe use of public networks, secure authentication methods, and remote access to the company's Virtual Private Networks (VPNs) are all helpful topics to include.
Data Protection: What data is most important? How should your company guard the vast amount of sensitive and private information it collects from customers, employees, and research and development? A good cybersecurity training program should teach employees to safely handle this sensitive information.
Privacy Laws: With more data privacy laws passing in jurisdictions across the globe, every employee is responsible for adhering to these regulations.
Malware and Ransomware Awareness: Most businesses experienced ransomware and malware attacks in 2023, which are malicious software programs that allow criminals to steal sensitive data from individuals and organizations.
Cybersecurity awareness training equips your staff with the knowledge and skills to identify and respond to threats online, reducing the risk of a successful attack. Training creates a culture that values and practices security within the organization where every employee understands their role in your company’s security posture.
We should also note that tailoring your cybersecurity training to different roles is crucial because each department faces unique risks. For instance, the finance department should receive training focused on financial fraud and invoice scams, while the IT department might need more in-depth training on network security and intrusion detection. Customizing the training ensures that each employee gets the relevant information and skills for their roles and responsibilities.
The average cost of a data breach in 2022 was a historic high of approximately $4.35 million . Look no further than this eye-popping stat to understand why introducing cybersecurity training to your organization is so important. Anything you can do to bring that number down and mitigate the financial blows that typically accompany a successful cyber attack is worthwhile.
The benefits are multifaceted:
- Empowering Employees : Well-informed employees are less vulnerable and less likely to fall prey to attacks. One of the major benefits of security training is that it enhances the first line of defense and lowers the risk of data breaches and cyberattacks significantly.
- Risk Mitigation : Risk mitigation involves creating security policies and processes to reduce the overall risk or impact of a cybersecurity threat. Unless you include employee learning and development modules on risk prevention, detection, and remediation, your security policies will never be successful.
- Compliance and Legal Implications : Meeting regulatory requirements and ensuring compliance with various data protection and privacy laws reduces the likelihood of incurring penalties, as many regulations require staff to be trained in cybersecurity best practices
- Building a Resilient Organizational Culture: Fostering a culture of vigilance and proactive cybersecurity behavior, empowering employees to take charge of their digital security.
In today's digital age, cybersecurity training is more crucial than ever. Here are three things that demonstrate the importance of cyber security awareness training:
The Human Factor
Employees are often the weakest line of defense against cyber attacks, so why wouldn’t you want to help them? Without proper training, they can unknowingly make it easy for attackers to infiltrate the organization's network. Training ensures they remain vigilant, recognize potential hazards, and know the appropriate steps to mitigate them.
Adaptation to Evolving Threats :
As with most things in the digital age, nothing remains the same for long. Rather, the threat landscape is continuously evolving and becoming more sophisticated.
Let’s consider some real-world examples of how cybersecurity awareness education can benefit an organization:
Example 1: Spearfishing
We’ve already covered phishing, the most common type of attack. Spear phishing is the next evolution, where criminals use highly targeted and personalized emails or messages to trick individuals into revealing sensitive information. They will customize the messages to a specific individual or organization to the point where they can include details about the target's role, relationships, work projects, or recent activities. Moreover, the attacker may use email addresses and logos to impersonate a trusted colleague, supervisor, or service provider.
Ideally, your training program would teach employees to use email filtering and to recognize a phishing attempt so they can report the attack and prevent a significant data breach. Encouraging a good, healthy skepticism of unexpected or unusual emails can go a long way toward thwarting spearfishing attempts.
Example 2: Malicious Insiders
Did you know sometimes employees or contractors will misuse their access and privileges to intentionally harm an organization? These people are known as insider threats and will often try to steal sensitive data, such as customer information, intellectual property, or trade secrets, and sell or use it for personal gain. By conducting regular training sessions, you can enable staff to identify a malicious insider, safeguarding sensitive company information from being stolen.
More and more companies prioritize training employees in cybersecurity awareness, but there is still a long way to go. Not only are there more attacks than ever, but the tactics of cybercriminals are becoming increasingly advanced. Cybercriminals will relentlessly target your security gaps, such as weak passwords and unsecured networks. So, consider this a call to action for all organizations: It's time to prioritize and invest in cybersecurity awareness training to educate employees about risks and best practices to mitigate them.
- Expand/Collapse Microsoft Office 38 RSS
- Expand/Collapse Training Trends 107 RSS
- Expand/Collapse CyberSecurity 59 RSS
- Expand/Collapse DevOps 2 RSS
- Expand/Collapse Modern Workplace 37 RSS
- Expand/Collapse Cloud 15 RSS
- Expand/Collapse Programming 10 RSS
- Expand/Collapse Artificial Intelligence (AI) 5 RSS
- Expand/Collapse ITIL 17 RSS
- Expand/Collapse Data & Analytics 24 RSS
- Expand/Collapse Business Analyst 12 RSS
- Expand/Collapse Training By Job Role 1 RSS
- Expand/Collapse Leadership and Professional Development 14 RSS
- Expand/Collapse Managed Learning Services 3 RSS
- Expand/Collapse Design & Multi-Media 1 RSS
- Study Guides
- Homework Questions
Proposal Classical Argument Thesis Outline Assignment (1)

IMAGES
VIDEO
COMMENTS
(CIO), chief information security officer (CISO), and IT directors in Hampton Roads, Virginia, who have implemented cybersecurity awareness and training strategies within their organization. Implications for positive social change include the potential improvement to awareness and training programs that contribute to better cybersecurity
In the dynamic realm of cybersecurity, awareness training is crucial for strengthening defenses against cyber threats. This survey examines a spectrum of cybersecurity awareness training methods ...
Cetin & Hamdullah Nejat Basim (2020): Cyber Security Awareness, Knowledge and Behavior: A Comparative Study, Journal of Computer Information Systems, DOI: 10.1080/08874417.2020.1712269
errors, cyber security awareness training is conducted to improve user awareness. Cyber security awareness training that is engaging, fun, and motivating is required to ensure that the awareness message gets through to users. Gamification is one such method by which cyber security awareness training can be made fun, engaging, and motivating.
Walden University. College of Management and Technology This is to certify that the doctoral dissertation by Jermaine Jewel Jean-Pierre has been found to be complete and satisfactory in all respects,
However, increasing levels of awareness can only transpire if cyber awareness itself is fully understood, a thesis already made in 2015 by Letho: "[While] the world grows more connected through the cyber world, the most efficient plan to increase cyber security awareness is the improvement of the know-how of the citizens and actors of the ...
This study uses a digital learning platform to examine the cyber security awareness among UiTM Terengganu Faculty of Computer and Mathematical Sciences students. The study is significant to focus on the weakness and to educate the students about being cyber victims. The data was collected using a set of questionnaires among 110 students.
Cyber Security Awareness Among College Students. Abbas Moallem1,2(&) UX Experts, LLC, Cupertino, CA, USA. San Jose State University, San Jose, CA, USA. [email protected]. Abstract. This study reports the early results of a study aimed to investigate student awareness and attitudes toward cyber security and the resulting risks in the most ...
The work in proposed a conceptual framework for the design and implementation of cyber security games to improve, using game-based approaches, cyber security education, and pedagogical effectiveness. Various data and statistical measure were used to assess the mindset of internet users for preparing a cybersecurity awareness framework [ 50 ].
Note: this thesis repository might be incomplete for certain programmes. ... Touhami, Mounaim Ben, Quantifying the Effectiveness of Cyber Security Awareness on Human Behavior , Thesis Master ICT in Business and the Public Sector, LIACS, Leiden University, 2021. ...
This thesis will lay out the importance of connectivity in our society - from the individual user to national security and the military. I will examine the vulnerabilities, cite case studies, and look at the consequences the cyberattacks have or could have on society. To best frame my research, I will include recent cyber events and examine the
Cyber Security Awareness in Higher Education. T. Hunt. Published 2016. Computer Science, Education. TLDR. The purpose of this research paper is to discuss the security challenges that are associated with the digital age and point out the importance of cyber security awareness and protection. Expand.
(Q1) What factors do security awareness practitioners use to motivate cybersecurity awareness. 1.2 Delimitation The purpose of this study is exploring the perspective and the view of the security awareness practitioner, with the aim of addressing the research question identified in section 1.1 above.
A Systematic Literature Review on the Cyber Security. 1 Dr.Yusuf Perwej, 2 Prof. (Dr.) Syed Qamar Abbas, 3 Jai Pratap Dixit, 4 Dr. Nikhat Akhtar, 5Anurag. Kumar Jaiswal. 1 Professor, Department of ...
A survey of cyber-security awareness in Saudi Arabia. In Proceedings of the 2016 11th International Conference for Internet Technology and Secured Transactions (ICITST), Barcelona, Spain, 5-7 December 2016. [Google Scholar] Senthilkumar, K.; Easwaramoorthy, S. A Survey on Cyber Security awareness among college students in Tamil Nadu.
internship mentors, Michael Cassell, Yeecong Yang, Nancy Dam, Mario Perez, and Lorenzo. Ocampo for educating me in all aspects of the security realm, and for inspiring me to pursue a. thesis project in the field of cybersecurity. Lastly, I would like to thank my family for supporting me throughout my education and.
egies to enhance cyber security awareness. The thesis discusses the back-ground and context of cyber security in the maritime industry, highlighting the growing interconnectivity and reliance on digital systems. It identifies the prob-lem statement as the need to enhance the cyber security awareness to safe-
Focusing on citizens' awareness of cyber-security, this paper contributes to debates on ICTs and their contribution towards human development. The paper philosophically argues for the importance of cyber-security and cybercrime awareness in fostering sustainable human development through the responsible and meaningful use of ICT. Using the overarching values of the human development ...
Dissertations / Theses on the topic 'Cyber-security awareness' To see the other types of publications on this topic, follow the link: Cyber-security awareness. Author: Grafiati. Published: 4 June 2021 Last updated: 16 February 2022 Create a spot-on reference in APA, MLA, Chicago, Harvard, and other styles ...
Consult the top 47 dissertations / theses for your research on the topic 'Computer security ; cybersecurity.'. Next to every source in the list of references, there is an 'Add to bibliography' button. Press on it, and we will generate automatically the bibliographic reference to the chosen work in the citation style you need: APA, MLA, Harvard ...
A graduate-level information security project should make a timely, original contribution to an ongoing problem or debate in the field. The best cybersecurity thesis topics will therefore explore issues of current importance to the broader infosec community, ideally with some degree of both academic and practical utility.
End User Awareness of IoT Device Users in the domain of smart homes - A survey study: Bachelor: 2020: Show Don't Tell: Improving user perception and understanding of privacy or anti-tracking tools: Master: 2020: Analysis of process mining in the context of cyber security with the example of identity and access management: Master: 2020
There is a strong case to be made for effective Collaborative Cyber-Security Situational Awareness (CCSA) that is designed to protect valuable assets, making them more resilient to cybersecurity threats. ... "The use of instant messaging applications among swedish students and their security awareness." Thesis, Högskolan i Skövde ...
The Vital Importance of Cybersecurity Awareness Training in the Digital Age When a company falls victim to a malicious cybersecurity attack, there is far more on the line than the subsequent PR nightmare. Yes, a security breach can damage your organization's reputation and trust, but that's just the tip of the iceberg. Identity theft, financial fraud, and disruptions to your business can all ...
A. An important part of improving cyber defenses is raising public awareness. 1. By acquiring knowledge about cyber security threats and best practices, individuals can impede cybercriminals' ability to access sensitive personal information (Lessig 2021). B. Cyber threat education in schools helps bring attention to the issue among the general ...