Building a comprehensive report on Azure AD admin role assignments in Powershell
Keeping an eye on azure ad administrative role assignments is crucial for tenant security and compliance. forget about the built-in pim report in the azure ad portal - take reporting to the next level and build your own report with graph, kql and powershell..
Unassigning inactive roles, verifying that all role holders have registered MFA and are active users, auditing service principals, role-assignable groups and guests with roles, move users from active to eligible roles in PIM ( Privileged Identity Management ), and making sure that no synchronized users have privileged roles are just a few ideas for why you should be reporting on this topic.
In this blogpost I will showcase how to gather data from various sources and compile it all into an actionable status report. Since different tenants have different needs and ways of working, I’m providing examples so that you can write your own custom-tailored script.
The report will list the following records:
- Users with eligible or active Azure AD admin roles - including details on last role activation date, role assignment and expiration dates, MFA status and last sign-in date, admin owner account status etc.
- Service Principals / Applications and Managed Identities with active Azure AD admin roles - including details on last authentication date, tenant ownership, etc.
- Role-assignable groups with eligible or active Azure AD admin roles
Note : Role-assignable groups granted one or more Azure AD admin roles will be listed in the report but users with active or eligible membership to such groups will currently not be listed.
See the Report examples chapter for details.

Prerequisites
Connecting to graph and log analytics, mfa registration details, role assignments, principal last sign-in date, eligible role last activation date, default mfa method and capability, admin account owner, service principal owner organization, report examples, example script.
These Powershell modules are required:
- Graph Powershell SDK
- Azure Powershell
Other prerequisites:
- Global Reader role (or other AAD roles granting enough read-access)
- Admin consent to any required non-consented Graph scopes (read-only) in Graph Powershell SDK.
- Reader-role on the Log Analytics workspace where the Azure AD Sign-in and Audit logs are exported.
Connect to Graph with the Graph Powershell SDK using the required read-only scopes, and select the beta endpoint as required by some of the cmdlets:
Then connect to Azure with the Azure Powershell module, for running KQL queries on the Log Analytics workspace data. Read my Query Azure AD logs with KQL from Powershell blogpost for more information on running KQL queries in Powershell. Update the various parameters according to your environment.
Extracting data
We need to extract data from various sources using Microsoft Graph and KQL queries in Log Analytics.
To report on MFA registration details for Azure AD admin role holders it is likely most efficient to extract all registration details and create a hashtable for quick lookup, depending on the number of users in the tenant.
Assigned roles are active role assignments. This query will also return eligible role assignments which are currently activated through PIM, so we’ll filter those out as they will just be duplicates in the report as they are also listed as eligible roles.
Eligible roles are role assignments requiring activation in PIM.
Then we combine the two assignment types into one array. Use the Select-Object cmdlet to pick out a few records while developing and testing the script.
Now we have all the assignment objects we need in the $allRoleAssignments array, and will process each of those objects in a foreach loop to fetch other necessary data. In the following examples I’ve populated the $roleObject variable with one object from the $allRoleAssignments array.
Since the $allRoleAssignments array may contain both users and Service Principals with active or eligible role assignments, the $roleObject.Principal.AdditionalProperties.'@odata.type property will tell which principal type the current object is - either '#microsoft.graph.user or #microsoft.graph.servicePrincipal . And for Service Principals we can differentiate on types in the $roleObject.Principal.AdditionalProperties.servicePrincipalType property - which is either Application or ManagedIdentity .
The quickest way to get an Azure AD user’s last sign-in date is to query Graph for the user and selecting signInActivity .
For Service Principals we need to query the Azure AD logs in Log Analytics with KQL to fetch the date when the Service Principal last signed in.
KQL query for Service Principal of type Application :
KQL query for Service Principals of type ManagedIdentity :
We also need to fetch the latest date of eligible role activations for users. If $roleObject.AssignmentType equals null and the principal is a user, the following KQL query can help out:
Users with administrative roles and no registered MFA method can be a security risk, depending on tenant configuration and conditional access policies. It’s best to avoid it - while also report on the default type of MFA methods active role assignees have. We already have the $mfaRegistrationDetailsHashmap hashtable and can query it for each processed role where the principal is a user.
If you’re following Microsoft best-practises and separating normal user accounts from administrative roles, you should be having a separate admin account for each user who requires privileged roles and access.
When having separate admin accounts it’s also important to check account status of the admin account owners if possible - to make sure that all admin accounts of terminated employees have been disabled and/or deleted. This query will depend on how you identify admin account owners in your tenant, the following example extracts the owner’s accountName from the UPN and queries Graph for any user with that onPremisesSamAccountName + employeeId .
Service Principals of multi-tenant app registrations can be owned by other Azure AD tenants and consented to in your tenant. It’s important to know about these and understand why they have privileged roles.
If $roleObject.Principal.AdditionalProperties.appOwnerOrganizationId is not null , query Graph for the tenant properties of the owner organization.
$spOwnerOrg.displayName will contain the tenant organization name, and $spOwnerOrg.defaultDomainName the tenant’s default domain’, which can provide a better clue of what the Service Principal is used for and by whom.
Note : Know 100% what you’re doing before removing any privileged roles from Service Principals, especially from Microsoft-owned apps which likely have the roles for a very good reason.
That’s about it, we now have the data necessary to compile an actionable status report on all active and eligible Azure AD role assignments.
Compiling the report
We can now construct a PSCustomObject per role assignment with the collected data.
User with eligible role assignment:
User with active role assignment and owner account details:
Service Principal with role assignment:
Managed Identity with role assignment:
Role-assignable group with role assignment:
In case you need more tips on creating a reporting powershell script for this report, take a look at the example script I’ve published on GitHub .
Thanks for reading!
Be sure to provide any feedback on Twitter or LinkedIn .
- ← Previous Post
- Next Post →

- Do-It-Yourself
- Microsoft 365
- Virtualization
- Photography
- Places, Events
- Privacy Policy
- Terms of Use
- Google News
- Forgot Password
Azure Active Directory: Role Changes (ie. Global Administrators) (Auditing and Splunk)
Auditing Role Changes
I had recently been asked to figure out a way to audit Azure Active Directory (AAD, AzAD) Role changes — such as the Global Administrator — using a SIEM (security information and event management). The Azure portal only provides 1 month’s Role Management history, and being able to query a SIEM, such as Splunk, would allow a security professional to go back further during the course of his or her investigation and auditing.
There are two immediate ways to audit role changes that do not require coding skills:
- Azure AD Portal
Microsoft 365 Compliance Center
“ Eligible ” vs “ Permanent ” Roles: ” If a user has been made eligible for a role, that means they can activate the role when they need to perform privileged tasks. There’s no difference in the access given to someone with a permanent versus an eligible role assignment. The only difference is that some people don’t need that access all the time.” [Source: Privileged Identity Management (PIM)]
Note on Audit Log
During the course of writing this article, I found that when a Role membership was modified, the Core Directory service would log that action with the correct timestamp. The PIM service may later also trigger an alert if said operation was done outside of its domain — generally within about 2 minutes. However, I had recently come across a severely DELAYED alert by the PIM service that could cause unnecessary panic for auditors and the security team. The below screenshot is an example of such alert occurring nearly 9 HOURS after role changes were made:
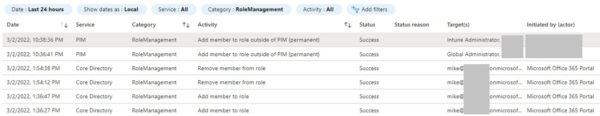
Role Change Audit Log – PIM Alert (Azure AD Portal)
There also was this odd alert that occurred 30 hours later:
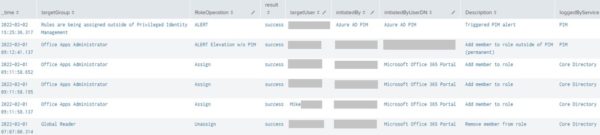
Role Change Audit Log – PIM Alert after 30 Hours (Splunk)
Why would a delayed alert be a problem?
Potentially false alarm and unnecessary escalation. Let’s look at the below screenshot as an example:

Role Change Audit Log – PIM Alert (Splunk)
The Core Directory service correctly notified an auditor that the “Global Administrator” role had its membership modified at 1:36pm ( Assign – Role granted) and 1:54pm ( Unassign – Role removed), but PIM followed up with an alert of its own 9 HOURS later at 10:36pm ( Alert ). The auditor may subsequently panic late that evening that a “Global Administrator” had been assigned and escalate the situation. The security team looked at the “Global Administrator” role and found that user “mike” did not possess that access (it was removed at 1:54pm). Also notice there was only one ( success -ful) alert entry from PIM at 10:36pm for a member having been added outside of its service. There was no additional one about the role having been removed . Perhaps PIM only cares if access was granted?
I have not yet found the reason for why PIM would alert so late after an action was taken. Maybe Azure AD was overwhelmed with log synchronization at that time? Seems like a misstep on Microsoft’s part to not prioritize IAM-related alerts. If you know why, please share in the Comments!
Azure Active Directory Portal
To view Role changes in the AzureAD Portal, go to Azure Active Directory > Monitoring > Audit Logs . From there, change the Category to “ Role Management “. Below is a sample output. Azure will not allow you to change the Date range past the last 1 month .
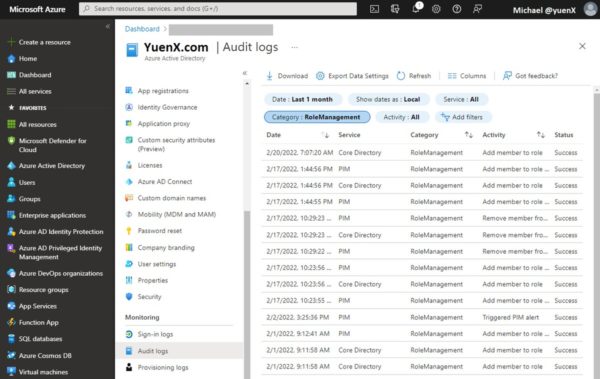
Audit Role Changes (Azure AD Portal)
To view Role changes in the M365/O365 Compliance Center, go to Microsoft 365 Compliance > Solutions > Audit . Under Activities, type “role” and select “ Added member to Role ” and “ Removed a user from a directory role “. Unlike the Azure AD Portal, you can have the date go back further than the last 1 month. The Audit search will take some time to complete and so feel free to go grab yourself a cup of coffee.
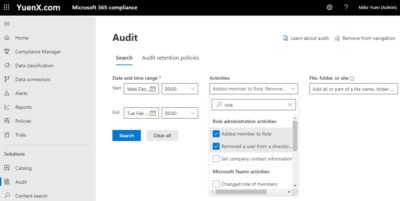
Splunk (SIEM)
Here is the query I formulated to audit role changes. It was interesting to see what happens on the Azure AD backend when a user is added to or removed from a given Role, and how the request is processed by PIM or the Core Directory service. Furthermore, the event logs were not presented in a consistent way, requiring the query to account for some variations I had come across.
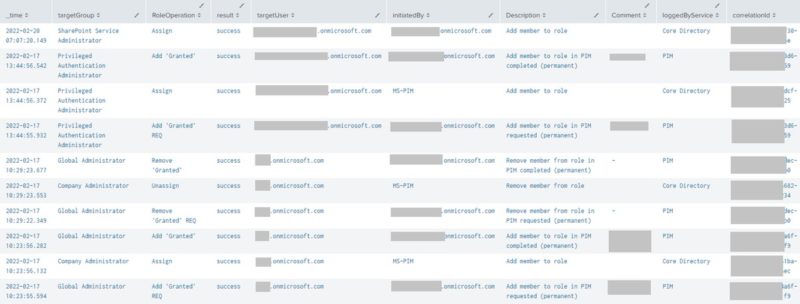
Audit Role Changes (Splunk)
Use the below query to locate any additional (or all) Role Management Operation Types that had surfaced in your Splunk environment for a time period you specify:
Other Categories and SourceTypes
To find other available Categories to audit on, use: index=YuenX_Azure sourcetype=”azure:aad: audit ” | stats count by category
Some interesting ones:
- sourcetype=”azure:aad: audit ” category= UserManagement
- sourcetype=”azure:aad: audit ” category= GroupManagement
Scheduled Alerts
You may want to set up a Splunk Alert to notify the Security and Azure administration teams of any changes within a specific time period so any unauthorized activity could be looked at.
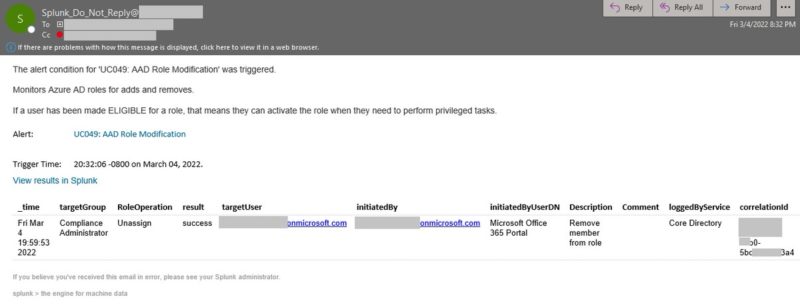
Role Change – Splunk Email Alert
- A cron job of every 45 minutes with a search of the last 46 mins worked best for my environment
- Example: An event occurred at 9:00am. Azure AD produces the log at 9:05am, gets ingested into Splunk at 9:07am, indexed at 9:10am, and scheduled search runs at 9:12am. At the time of schedule execution (9:12am), it looks back at the last 11 minutes — that includes any event from 9:01am on. Because the event had occurred at 9:00am, it was not in scope of the scheduled search and the alert was not triggered. In this example, setting the search window to 16 minutes instead would catch any event that occurred since 8:56am
- Azure AD has a tendency to not produce a log entry for as late as 20-30 minutes. You may have to adjust your scheduled search window to go beyond the last 30 minutes. Be sure to properly test in your environment. Be mindful of the time it takes for Splunk to finish indexing the logs
- M365 Audit Log in Compliance Center / Azure AD Audit Activities
- Azure AD Logs / Azure AD Audit Data
Related Posts
- Visualize Account Lockouts with Splunk Dashboards
- Find Account Lockout Sources and Modifications
- Group and Membership Changes
- Successful Logins from Unknown Users
- Cannot Add Microsoft Account, “Work or School Email Address”
Share this Post
About the author: michael yuen @yuenx.
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Azure built-in roles
- 50 contributors
Azure role-based access control (Azure RBAC) has several Azure built-in roles that you can assign to users, groups, service principals, and managed identities. Role assignments are the way you control access to Azure resources. If the built-in roles don't meet the specific needs of your organization, you can create your own Azure custom roles . For information about how to assign roles, see Steps to assign an Azure role .
This article lists the Azure built-in roles. If you are looking for administrator roles for Microsoft Entra ID, see Microsoft Entra built-in roles .
The following table provides a brief description of each built-in role. Click the role name to see the list of Actions , NotActions , DataActions , and NotDataActions for each role. For information about what these actions mean and how they apply to the control and data planes, see Understand Azure role definitions .
Web and Mobile
Ai + machine learning, internet of things, mixed reality, integration, management and governance, hybrid + multicloud.
- Assign Azure roles using the Azure portal
- Azure custom roles
- Permissions in Microsoft Defender for Cloud
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback .
Submit and view feedback for
Additional resources
Azure Active Directory Identity Blog articles
https://techcommunity.microsoft.com/t5/azure-active-directory-identity/bg-p/Identity
Easily Manage Privileged Role Assignments in Microsoft Entra ID Using Audit Logs
Published Monday, January 8, 2024

One of the best practices for securing your organization's data is to follow the principle of least privilege, which means granting users the minimum level of permissions they need to perform their tasks. Microsoft Entra ID helps you apply this principle by offering a wide range of built-in roles as well as allowing you to create custom roles and assign them to users or groups based on their responsibilities and access needs. You can also use Entra ID to review and revoke any role assignments that are no longer needed or appropriate.
It can be easy to lose track of role assignments if admin activities are not carefully audited and monitored. Routine checks of role assignments and generating alerts on new role assignments are one way to track and manage privileged role assignment.
Chances are that when a user with privileged roles is approached, they’ll say they need the role. This may be true; however, many times users will unknowingly say they need those permissions to carry out certain tasks when they could be assigned a role with lower permissions. For example, a user will be able to reset user passwords as a Global Administrator, but that does not mean they can’t do that with another role with far less permissions.
Defining privileged permissions
Privileged permissions in Entra ID can be defined as “permissions that can be used to delegate management of directory resources to other users, modify credentials, authentication or authorization policies, or access restricted data.” Entra ID roles each have a list of permissions defined to them. When an identity is granted the role, the identity also inherits the permissions defined in the role.
It’s important to check the permissions of these roles. The permissions defined in all built-in roles can be found here . For example, there are a few permissions that are different for the Privileged Authentication Administrator role than the Authentication Administrator role, giving the former more permissions in Entra ID. The differences between the authentication roles can be viewed here .
Another example of having differences between similar roles is for the end user administration roles. The differences and nuances between these roles are outlined in detail here .
Auditing activity
To decide if a user really needs a role, it’s crucial to monitor their activities and find the role with the least privilege that allows them to carry out their work. You’ll need Entra ID audit logs for this. Entra ID audit logs can either be sent to a Log Analytics Workspace or connected to a Sentinel instance.
There are two methods that can be used to get the events of carried out by admin accounts. The first will make use of the IdentityInfo table, which is only available in Sentinel after enabling User and Entity Behavior Analytics ( UEBA ). If you aren’t using UEBA in Sentinel or if you’re querying a Log Analytics Workspace, then you'll need to use the second method in the next heading.
Using Microsoft Sentinel
To ingest Entra ID audit logs into Microsoft Sentinel, the Microsoft Entra ID data connector must be enabled, and the Audit Logs must be ticked as seen below.
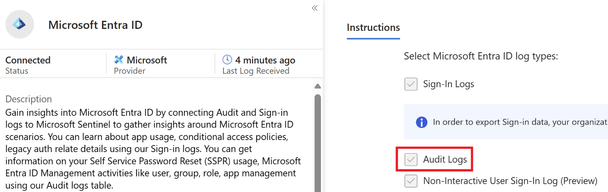
Figure 1 Entra ID data connector in Sentinel with Audit logs enabled
The IdentityInfo table stores user information gathered by UEBA. Therefore, it also includes the Entra ID roles a user has been assigned. This makes it very simple to get a list of accounts that have been assigned privileged roles.
The query below will give a unique list of activities an account has taken, as well as which roles the account has been assigned:
This will give results for all accounts that carried out tasks in Entra ID and may generate too many operations that were not privileged. To filter for specific Entra ID roles, the following query can be run where the roles are defined in a list. Three roles have been added as examples, but this list can and should be expanded to include more roles:
Once the query is run, the results will give insights into the activities performed in your Entra ID tenant and what roles those accounts have. In the example below, the top two results don’t pose any problems. However, the third row contains a user that has the Global Administrator role and has created a service principal. The permissions needed to create a service principal can be found in roles less privileged than the Global Administrator role. Therefore, this user can be given a less privileged role. To find out which role can be granted, check this list , which contains the least privileged role required to carry out specific tasks in Entra ID.

Figure 2 Actions taken by users in Entra ID
Using Log Analytics Workspace

Figure 3 Configuring the forwarding of Entra ID Audit logs to a Log Analytics Workspace
To ingest Entra ID audit logs into a Log Analytics Workspace follow these steps .
Because there is no table that contains the roles an identity has been granted, you’ll need to add the list of users to the query and filter them. There are multiple ways to get a list of users who have been assigned a specific Entra ID role. A quick way to do this is to go to Entra ID and then select Roles and administrators. From there, select the role and export the identities that have been assigned to it. It’s important to have the User Principal Names (UPNs) of the privileged users. You’ll need to add these UPNs, along with the roles the user has, to the query. Some examples have been given in the query itself. If the user has more than one role, then all roles must be added to the query.
Once you run the query, the results will give insights into the activities performed in your Entra ID tenant by the users you have filtered for. In the example below, the top two results can cause problems. Both have the Global Administrator role, but their operations don’t necessitate to have that role. The permissions needed for these operations can be found in roles less privileged than the Global Administrator role. Therefore, these users can be given a less privileged role. To find out which role can be granted, check this list , which contains the least privileged role required to carry out specific tasks in Entra ID.
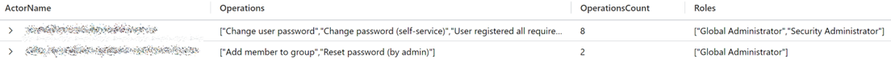
Figure 4 Actions taken by users in Entra ID
If this user still requires the Global Administrator role then the Security Administrator role will become redundant as the Global Administrator contains more permissions than the Security Administrator role.
Keeping accounts with privileges that are not required is keeping your attack surface greater than it needs to be. By ingesting Entra ID Audit logs, you can query and identify users who have unnecessary and over-privileged roles. You can then find a suitable alternative role for them.
Timur Engin
LinkedIn Twitter
Learn more about Microsoft Entra:
- See recent Microsoft Entra blogs
- Dive into Microsoft Entra technical documentation
- Learn more at Azure Active Directory (Azure AD) rename to Microsoft Entra ID
- Join the conversation on the Microsoft Entra discussion space and Twitter
- Learn more about Microsoft Security
More from Azure Active Directory Identity Blog articles

What's new in Microsoft Entra

Important update: Azure AD Graph API retirement

Important update: Deprecation of Azure AD PowerShe ...

Microsoft Entra resilience update: workload identi ...

Microsoft Entra Internet Access: Unify Security Se ...

Microsoft Entra: Top content creators to follow

Upgrade your tenant restrictions to v2

Act now: Turn on or customize Microsoft-managed Co ...
Cross-tenant access settings - Notes from the fiel ...

Microsoft Entra adds identity skills to Copilot fo ...
Related Posts
- DevOps Lifecycle
- DevOps Roadmap
- Docker Tutorial
- Kubernetes Tutorials
- Amazon Web Services [AWS] Tutorial
- AZURE Tutorials
- GCP Tutorials
- Docker Cheat sheet
- Kubernetes cheat sheet
- AWS interview questions
- Docker Interview Questions
- Ansible Interview Questions
- Jenkins Interview Questions
- Microsoft Azure Tutorial

Introduction
- Introduction to Microsoft Azure | A cloud computing service
- Microsoft Azure - High-Level Overview of Architecture Center
- How Microsoft Azure Works?
- Microsoft Azure - Using the Azure Quickstart Centre
- Microsoft Azure - Getting Free Trial with Azure Quickstart Center
- Microsoft Azure - Storage Accounts
- Microsoft Azure - Storage in Azure Cloud Shell
- Microsoft Azure - Mounting Azure Storage in a Container App
- Microsoft Azure - Concept of Blob Versioning in Azure Storage
- Microsoft Azure - Using Blob Versioning
- Microsoft Azure - Automatically Manage Azure Blobs Lifecycles
- Microsoft Azure - Add Storage Blob Owner Role Assignment For Azure AD User
- Microsoft Azure- Disk Storage in Microsoft Azure
- How to Setup a Azure Storage Account For Data Archive?
- Microsoft Azure - Hosting a Static Website with Azure Storage
- Microsoft Azure - Azure Managed Disk State Details using PowerShell
- Microsoft Azure - Mount Azure Storage in Container App In App Service
- Microsoft Azure - Delete Orphaned Disks using PowerShell Script
- What Are Azure Data Security Features?
- Microsoft Azure - Virtual Network
- Microsoft Azure - Find Orphaned Network Interface Cards(NICs)
- What is Microsoft Azure Network Watcher?
- Microsoft Azure - Finding the Right Load Balancing Service
- Microsoft Azure - Application Security with Azure Active Directory
- Microsoft Azure - Find and Delete Orphaned Public IP addresses in Azure Portal
- Microsoft Azure - Protecting Hybrid Cloud Workloads using Azure Defender
Compute Virtual Machines
- What are Azure Virtual Machines?
- Microsoft Azure - Introduction to Azure VM Extension
- Microsoft Azure - Simpler Management of Virtual Machine
- Microsoft Azure - Managing Multiple Virtual Machines
- Create Free Windows Virtual Machine in Azure
- Microsoft Azure - Pre-built Azure VMs
- Microsoft Azure - Archive Azure VM to Azure Storage Account
- How to Reset a Azure VM Password?
- Microsoft Azure - Improvements in Linux Virtual Machine
- Microsoft Azure - Connecting Linux VM using SSH
- Microsoft Azure - Connecting Windows VM using RDP
- Microsoft Azure - Azure VM Disk Space in Percentage using Azure KQL
- Microsoft Azure - Creating an OS Disk Snapshot of a Azure VM
- Microsoft Azure - Reduce Cost Using Virtual Machine
- Microsoft Azure - Resize a Azure Virtual Machine for Windows or Linux Servers
- Microsoft Azure - Resizing Virtual Machine Using PowerShell Script
- Microsoft Azure - Configuring Backup For Azure App Services
- Microsoft Azure - Getting Started With Azure Backup For Protecting an IaaS VM
- Defense in Depth Strategy in Microsoft Azure
- Microsoft Azure - Enable IIS Logs for Monitoring
- Microsoft Azure - Using Azure Monitor Workbooks
- Microsoft Azure - Enable Azure Monitor VM Insights Agent For Azure VM
- Microsoft Azure - Introduction to Spot Virtual Machines
- Azure Virtual Machine for Machine Learning
- Microsoft Azure - Tracking Memory Utilization of Azure VM using KQL Log Query
- Microsoft Azure - Track CPU Utilization of a Azure Virtual Machines using KQL Log Query
- Microsoft Azure - Heartbeat KQL Log Monitoring Query
- Microsoft Azure - Firewall Network Flow Logs with TimeGenerated using KQL
- Microsoft Azure - Setting up a Auto Shutdown For Azure Virtual Machine
- Microsoft Azure - Get CPU Utilization Data of a Azure VM in Azure Portal
- Microsoft Azure - CPU and Memory Utilization of Azure VMs in a Single Table Chart
- Microsoft Azure - Retrieve Azure Virtual Machine Admin User Name
- Microsoft Azure - Enable Boot Diagnostics For a VM in Azure
- Microsoft Azure - Disable Boot Diagnostics For a VM in Azure
- Microsoft Azure - Setup Auto Startup and Shutdown of an Azure VM
- 7 Tips to Reduce Cost with Azure Virtual Machines
- Microsoft Azure - Assigning Tags to a Azure VM
- Microsoft Azure - Check Virtual Machine Creation Date and Time
- Microsoft Azure - VMs Patch Update Summary by Installation Status
- Microsoft Azure - Graph Query to Get Properties of Azure VM Resource
- Microsoft Azure - Check for Apache Log4J Vulnerability in Azure VMs
- Microsoft Azure - Get Azure VM Properties using Azure PowerShell
- Microsoft Azure - Manage Azure VMs using Azure PowerShell Commands
- Microsoft Azure - Check Status of Azure VM using Azure PowerShell
- Microsoft Azure - Azure CLI Commands to Manage Azure VMs
- Microsoft Azure - KQL Query to Get the VM Computer Properties
- Microsoft Azure - Create SHH Key to Manage Azure Linux VMs
- Microsoft Azure - VM CPU Utilisation Across Subscriptions with Range
- Microsoft Azure - Common Virtual Machine Issues
- Microsoft Azure - Manage Virtual Machine via Azure Mobile App
- Microsoft Azure - Increase Processors & Memory Size of Windows Virtual Machine
- Microsoft Azure - Troubleshoot Azure VM Inbound and Outbound Connections
- Microsoft Azure - Deletion of Snapshots using PowerShell Script
- Microsoft Azure - Connect to a Storage Account using Private Link
- Microsoft Azure - Accessing Virtual Machines using Bastion
- Microsoft Azure - Getting VMComputer Records Properties
Compute Functions
- Microsoft Azure - Monitoring Azure Functions
- Microsoft Azure - Creating Azure Functions From VS Code
- Microsoft Azure - Debugging Azure Functions using VS Code
- Microsoft Azure - Deploy Azure Functions using VS Code
- Microsoft Azure - Renaming an Azure Functions
- Microsoft Azure - Simple way to Create a Function App
- Microsoft Azure - New Features in Azure Functions
- Microsoft Azure - Using VS Code for Azure Function Projects
- Microsoft Azure - Custom Handlers for Azure Functions
Compute Monitoring
- Microsoft Azure - Enable Windows Performance Counters in Azure for Monitoring
- Microsoft Azure - Enable Linux Performance Counters in Azure for Monitoring
- Microsoft Azure - Enable Windows Event Logs in Azure for Monitoring
- Microsoft Azure - Enable Linux System Logs in Azure for Monitoring
Azure Services
- Microsoft Azure - Introduction to Quickstart Center
- Microsoft Azure- Add Extensions in Azure App Service
- Microsoft Azure - Working with App Service Domains
- Microsoft Azure - Create Web Apps in Azure
- Microsoft Azure - Creating an App Service Plan
- Microsoft Azure - Creating a Logic App of Consumption Type
- Microsoft Azure - Azure App Service Managed Certificates
- Microsoft Azure - Deploy a Static Web App
- Microsoft Azure - Removing Unused Services From Azure
- What is Microsoft Azure Functions?
- Microsoft Azure - RDP to Azure Virtual Machines using Azure Bastion
- Microsoft Azure - Getting started with Azure Static Web Apps
- Microsoft Azure - Cloning Web Apps using Azure App Services
- Microsoft Azure - Enable Local Cache on Azure App
- Microsoft Azure - Exploring the Azure Mobile App Home Screen
- Microsoft Azure - Container Registration for App Deployment
- Microsoft Azure - Roll Back Versions of Azure Logic Apps
- Microsoft Azure - Modifying API Connections With Logic Apps
- Microsoft Azure - Azure Media Service
- Microsoft Azure - Using Github Action in Azure App Service
- Microsoft Azure - Using JSON with Azure Logic Apps
- Microsoft Azure - Configuring Log Analytics Data Retention
- Microsoft Azure - Creating JSON Snippet For Policy Initiative Creation using CSV File
- Microsoft Azure - Working with Files in Azure App Service
- Microsoft Azure - Using Power Apps in VS Code
- Microsoft Azure - Preventing Changes to Resources in Azure App Services
- Microsoft Azure- Writing Queries and Creating Dashboards using Azure Resource Graph
- Microsoft Azure - Enabling Resource Providers for Azure Subscription
- Microsoft Azure - Find Orphaned Disks
- Microsoft Azure - Handling Orphaned NSGs
- Microsoft Azure - Configuring an Alert Rule with Azure Monitor
- Microsoft Azure - Count of Azure Resources using Resource Graph Query
- Microsoft Azure - Create Alert For Conditional Access Policy Changes
- Microsoft Azure - Create Pie Charts For Orphaned Resources using KQL
- Microsoft Azure - Patch Management Update Summary Status
- Microsoft Azure - Check Resource Owner in Azure using KQL
- Microsoft Azure - Check Enabled and Disabled Diagnostics for Azure Resources
- Microsoft Azure - Azure Firewall Flow Logs From Select Source IP
- Microsoft Azure - Resource Tagging and Best Practices
- Microsoft Azure - Using the Azure Activity Log
- Microsoft Azure - Scaling Inventory Resources
- Microsoft Azure - Moving Resources Among Groups
Cognitive Services
- Build a Text Translator Web App using Flask and Azure Cognitive Services
- Microsoft Azure - Introduction to Metric Advisor
- Microsoft Azure - Cognitive Service Text Analytics in Web App Containers
- Microsoft Azure - Opinion Mining with Azure Cognitive Services
- Microsoft Azure - Customizing Charts on Azure Dashboard
- Microsoft Azure - Customizing Azure Dashboard Tiles
- Microsoft Azure - Auto Refreshing Dashboards
- Microsoft Azure - Pinning to Portal Dashboard
- Microsoft Azure - Database Availability and Consistency For Azure SQL
- Microsoft Azure SQL Database
- Microsoft Azure - Security in Azure SQL
- Microsoft Azure - Identifying & Accessing Management for Azure SQL
- Microsoft Azure - Security Capabilities and Tasks of Azure SQL
- Microsoft Azure - Configure Azure SQL with Azure CLI
- Microsoft Azure - Configure Auditing for Azure SQL Database
- Microsoft Azure - Azure SQL Managed Instance Deployment Options
- Microsoft Azure - Azure SQL Managed Instance
- Microsoft Azure - PaaS vs. IaaS in Azure SQL
- Microsoft Azure - Management Interfaces for Azure SQL
- Microsoft Azure - Opportunities in the Cloud with Azure SQL
- Microsoft Azure - Create Azure SQL Database
- Microsoft Azure - Introduction to Azure Database For MySQL
- Microsoft SQL Server Active Directory Authentication on Linux Machine
- Introduction to Azure Cosmos DB
- Microsoft Azure - Notebooks in Cosmos DB
- Microsoft Azure - Using C# in CosmoDB
- Microsoft Azure - Choosing a Partition Key in Cosmos DB
- Microsoft Azure - Introduction to Azure Data Factory
- Microsoft Azure - Migrating From MySQL to Cloud
- Microsoft Azure - Advanced Threat Protection for Azure SQL Database
- Microsoft Azure - Using Flexible Server in Azure Database for PostrgeSQL
- Microsoft Azure - Accelerating Cloud Migration & Datacenter Discovery
- Azure DevOps: An Introduction, Services, Projects, Benefits, Drawbacks
- Microsoft Azure - Availability Zones For Kubernetes Cluster
- Microsoft Azure - Zone Redundancy and SLA of Azure SQL
- Microsoft Azure - Create Project in Azure Devops using Basic Process
- Microsoft Azure – Create Project in Azure Devops using Agile Process
- Microsoft Azure - Starting & Stopping a Azure Kubernetes Service Cluster
- Microsoft Azure - Introduction to Azure Kung Fu Toolkit
- Microsoft Azure - Introduction to Kubernetes Diagnostics
- How to Create Backlog and Sprint in Agile Process?
- Microsoft Azure - Running an App inside a Docker Container Image
- How to Push a Container Image to a Docker Repository?
- Microsoft Azure - Manage and Export Azure Policies with GitHub Integration
- Microsoft Azure Arc Enabled Kubernetes
- Microsoft Azure - Introduction to Azure Arc
- Microsoft Azure - Deploying Web Applications Using GitHub Actions
- Microsoft Azure - Messaging with Azure Web PubSub
- Microsoft Azure - Testing in Production Sites Feature using PowerShell
- Microsoft Azure - Build and Deploy App with Azure SDK For Java
Machine Learning and IoT
- Microsoft Azure - Introduction to Azure Sentinel
- Machine Learning with Microsoft Azure ML Studio Without Code
- What is the Best Azure IoT Service for You?
- Microsoft Azure - Key IoT Products
- Microsoft Azure - Using Azure Form Recognizer
Miscellaneous
- Microsoft Azure - Productivity Tips For Azure portal
- Microsoft Azure - Get Azure Policies Definitions and Policy Initiatives Definitions
- Microsoft Azure - Create a Custom Policy Initiative in Azure
- Technical Overview of Microsoft Mesh
- Microsoft Azure - Working with Azure Health Bot
- Microsoft Azure - Introduction to Azure Digital Twins
- Microsoft Azure - Working with Themes in Azure
- Microsoft Azure - Understanding Azure KeyBoard Shortcuts
- Microsoft Azure - Using Table Parameter in Azure CLI
- Microsoft Azure - Add Azure Cloud Shell to VS Code
- Microsoft Azure - Accessing Cloud Shell from Microsoft Docs
- Microsoft Azure - Azure App Servers Routing using PowerShell
- Microsoft Azure - Introduction to SMART
- Microsoft Azure - Lift & Shift Approach for Infrastructure Migration
- Microsoft Azure - Configure Diagnostic Settings For Azure Subscription
- Microsoft Azure - Checking your Access on Azure Subscription
- Microsoft Azure - Enabling Logs for Troubleshooting the Azure Firewall Rules
- Microsoft Azure - Rebooting an Application Gateway
- Microsoft Azure - PAL Tagging in Azure
- Microsoft Azure - Using Cost Management in Azure Portal
- Microsoft Azure - View Delegated Roles in Azure Lighthouse
- Microsoft Azure - Using the Global Search
- Microsoft Azure - Quick Copy & Paste on Portal
- Microsoft Azure - Alerts as Notifications on Phone
- Microsoft Azure - Developing ARM Templates using Azure Bicep
Microsoft Azure – Using the Azure Activity Log
In the given article we will get introduced to Azure activity logs. In this article, we will go through the activity log and let you know how to access it and what you can use it for. The activity log is really great to tell the who, what, and when for operations in your Azure resources.
Implementation:
There’s a range of data that you can look at in your activity log from Azure Resource Manager operation logs to updates in your service health events. So, there are different ways where you can get to the activity log. One is by going to all services over here. And then you can find the activity log, favorite it, and it’ll show up in your navigation bar.

You can also go to monitor and select the activity log from the table of contents on the left.

Or you could simply go to a resource, such as this VM right here, where you will also find an activity log in your table of contents. And the advantage of going to a resource and then clicking on the activity log is that all your filters will already be prefiltered down to that particular resource.

So, you can see here subscription, resource group, and the resource name are already set to this particular VM. If you wanted to change these filters, you can easily edit what’s already here or click on add filter, and then select a filter type that you would like, such as operation, and then you can select a particular operation.

Let’s create a role assignment in this case. Click it, select, and then it will filter down to only show create role assignment events. If you would like to see everything at a quick glance, you could click on the quick insights button, which will open a panel of premade filters that are filtered by things like errors, alerts fired, or role assignments. It will show you the number of everything that happened in the past 24 hours.

You can see here on these particular logs, you have an arrow to the left of this. This means that these logs are grouped together by correlation ID and then sorted in chronological order. You can also get some more information out of your logs by editing the columns of this table, which you can do in the top left button, and then by selecting whatever columns you would like to see or would like not to see.

Another way you can see more information is by clicking on a particular log, which will open the more info panel. And this will show you a lot more detail about your log and will even allow you to drill down into the JSON where you can see everything at the most granular level.

From this more info panel, you can also add an activity log alert or create a new support request. So, the activity log is really great because it enables you to see your events happening on every resource that you have.
So, you are in a VM right now, but you could just as easily be in a web app where you can see activity log here as well. Or, you could also be in a storage account where, again, you can find an activity log in the same place.

Not only that, but you can also click on the container that these resources are contained in, and this container itself will also have activity logs in its ToC, so, in the left-most panel on the table of contents. And here, instead of having the filters being filtered down to the most granular resource level, you will only be filtered down to the resource group.

So, you will see all the events that are happening in that resource group to those resources in there as well. It’s always the second item in every resource type on Azure. So, that functionality’s available throughout the entire platform.
Please Login to comment...
- Cloud-Computing
- Geeks-Premier-League-2022
- Geeks Premier League
- Microsoft Azure
- How to Delete Whatsapp Business Account?
- Discord vs Zoom: Select The Efficienct One for Virtual Meetings?
- Otter AI vs Dragon Speech Recognition: Which is the best AI Transcription Tool?
- Google Messages To Let You Send Multiple Photos
- 30 OOPs Interview Questions and Answers (2024)
Improve your Coding Skills with Practice
What kind of Experience do you want to share?
Our DevOps Solution
- Application Performance Optimization
- Apps / Web User Experience Boosting
- Microservice Management Enhancement
- Database Performance Optimization
- DevSecOps Implementation
- Centralized Log Management
- Multicloud Monitoring
- DevOps team Collaboration
What's DevOps?
Understand how you can optimize DevOps practices to boost your company’s competitiveness.
COMMUNITY & ARTICLES
- Application Performance Monitoring
- Datadog Overview
- Infrastructure Monitoring
- Integration Tools
- Real User Monitoring

GCP: Monitor IAM role assignments via Log Alerts in GCP
By Kishore Jagannath .Jul 7, 2022
GCP IAM enables Organization and Project administrators to manage role based access to users on specific resources. Typically enterprises using Google cloud want to enforce strict controls on roles and permissions granted to individual users, groups or service accounts. Enterprises would want to enforce best practices of granting roles to user groups alone instead of individual users or service accounts.
In this article I will be presenting on of the methodologies to monitor the IAM role access within the GCP Cloud organisation through Cloud Log Alerts . As an example use case lets consider an example on how to configure log alerts when roles are assigned to users directly instead of user groups.
In The GCP Logging Page lets filter based on Audit Logs to view all the changes that has happened on GCP resources.

Refine the Log filter to filter the audit logs and extract logs relevant to IAM Policy and role assignments.
logName=(“projects/<PROJECT_ID>/logs/cloudaudit.googleapis.com%2Factivity” ) AND protoPayload.methodName= “SetIamPolicy”
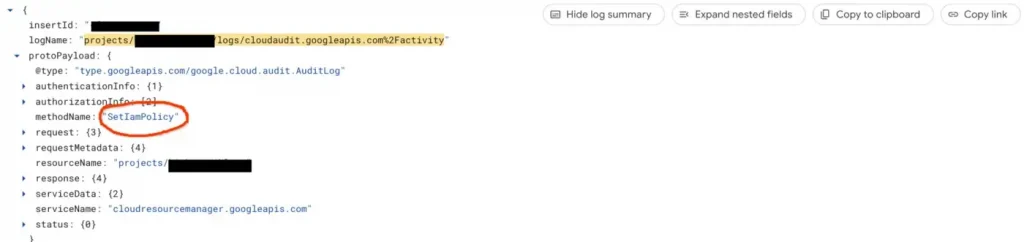
GCP Audit Log for IAM Role Assignments
Refine the log filter to filter audit logs for IAM role assignments when “users have been assigned to roles”
logName=(“projects/<<PROJECT_ID>>/logs/cloudaudit.googleapis.com%2Factivity” ) AND protoPayload.methodName= “SetIamPolicy” AND (protoPayload.serviceData.policyDelta.bindingDeltas.member: “user:”)
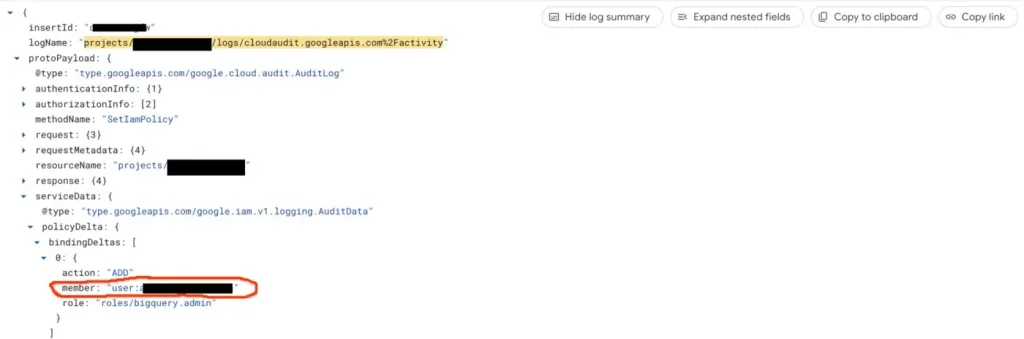
GCP Audit Log when roles are assigned to users
Create a log alert based on Log occurrence. With this configuration an alert will be triggered on the specified notification channel whenever an IAM policy is assigned to a user.
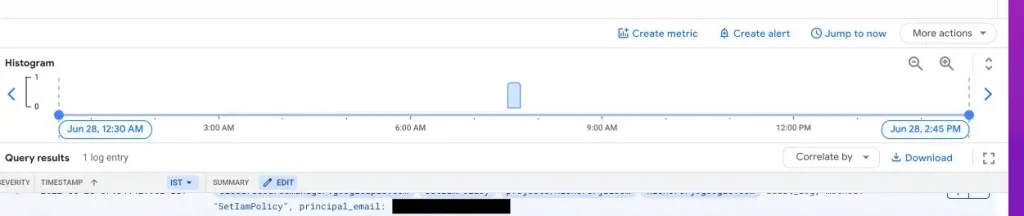
We showcased how to create Log alerts in GCP to track specific IAM role assignments. You can utilise this feature to get automatic alerts when non recommended practices like assigning roles to users directly or when roles are assigned to service accounts.
The original article published on Medium .
- Tags: IAM role , identity and access management (IAM) , Log Alert
Related Posts
Custom intercom domain using gcp.
By Adrian Trzeciak.Jul 8, 2022 This short article describes how to add a custom domain to Intercom behind SSL certificate managed by Google. The currently
Cloud Connectivity | GCP and Azure
By Dolly Sharma.Dec 4, 2022 In this blog post, let’s walk through the detailed steps of configuring the connectivity between Google Cloud Platform (GCP) and
How to: Dataform in Google Cloud-Part 1
Why should you consider using Dataform?
- [email protected]
- Building 5, Dubai Media City, Dubai, UAE.
- Privacy Policy
community posts
- DevOps Introduction
- What's Devops
- Apps/Web UX Boosting
- Multi-cloud Environment Monitoring
- DevOps Team Collaboration
- Getting Started with Oracle Enterprise Performance Management Cloud for Administrators
- Securing EPM Cloud
- Understanding EPM Cloud Security Compliance Features
Audit Reports, Login Reports, and Audit Logs in EPM Cloud on OCI (Gen 2)
Multiple reports are available in Oracle Enterprise Performance Management Cloud on OCI (Gen 2) to audit user, role, and group modifications.
- The roleAssignmentAuditReport EPM Automate command.
- The Role Assignment Audit Report for OCI REST API.
- The groupAssignmentAuditReport EPM Automate command.
- The Group Assignment Audit Report REST API.
- The userAuditReport EPM Automate command.
- The User Audit Report REST API.
- The User Login Report in Access Control .
- The invalidLoginReport EPM Automate command.
- The Invalid Login Report for OCI REST API.
In addition, Identity Cloud Service provides you audit and login reports such as the following:
- Audit log containing information on successful and failed logins, and user management actions: user creation, update, and deletion
- Application Role Privileges Report, which can be used as an audit report for all predefined role modifications
- Successful Login Attempts Report
- Unsuccessful Login Attempts Report
- Dormant Users Report
For information on these reports, see Audit and User Reports in Identity Cloud Service (OCI Gen 2 only) .

Easily Manage Privileged Role Assignments in Microsoft Entra ID Using Audit Logs
Defining privileged permissions, auditing activity, using microsoft sentinel, using log analytics workspace.
One of the best practices for securing your organization's data is to follow the principle of least privilege, which means granting users the minimum level of permissions they need to perform their tasks. Microsoft Entra ID helps you apply this principle by offering a wide range of built-in roles as well as allowing you to create custom roles and assign them to users or groups based on their responsibilities and access needs. You can also use Entra ID to review and revoke any role assignments that are no longer needed or appropriate.
It can be easy to lose track of role assignments if admin activities are not carefully audited and monitored. Routine checks of role assignments and generating alerts on new role assignments are one way to track and manage privileged role assignment.
Chances are that when a user with privileged roles is approached, they'll say they need the role. This may be true; however, many times users will unknowingly say they need those permissions to carry out certain tasks when they could be assigned a role with lower permissions. For example, a user will be able to reset user passwords as a Global Administrator, but that does not mean they can't do that with another role with far less permissions.
Privileged permissions in Entra ID can be defined as “permissions that can be used to delegate management of directory resources to other users, modify credentials, authentication or authorization policies, or access restricted data.” Entra ID roles each have a list of permissions defined to them. When an identity is granted the role, the identity also inherits the permissions defined in the role.
It's important to check the permissions of these roles. The permissions defined in all built-in roles can be found here . For example, there are a few permissions that are different for the Privileged Authentication Administrator role than the Authentication Administrator role, giving the former more permissions in Entra ID. The differences between the authentication roles can be viewed here .
Another example of having differences between similar roles is for the end user administration roles. The differences and nuances between these roles are outlined in detail here .
To decide if a user really needs a role, it's crucial to monitor their activities and find the role with the least privilege that allows them to carry out their work. You'll need Entra ID audit logs for this. Entra ID audit logs can either be sent to a Log Analytics Workspace or connected to a Sentinel instance.
There are two methods that can be used to get the events of carried out by admin accounts. The first will make use of the IdentityInfo table, which is only available in Sentinel after enabling User and Entity Behavior Analytics ( UEBA ). If you aren't using UEBA in Sentinel or if you're querying a Log Analytics Workspace, then you'll need to use the second method in the next heading.
To ingest Entra ID audit logs into Microsoft Sentinel, the Microsoft Entra ID data connector must be enabled, and the Audit Logs must be ticked as seen below.

Figure 1 Entra ID data connector in Sentinel with Audit logs enabled
The IdentityInfo table stores user information gathered by UEBA. Therefore, it also includes the Entra ID roles a user has been assigned. This makes it very simple to get a list of accounts that have been assigned privileged roles.
The query below will give a unique list of activities an account has taken, as well as which roles the account has been assigned:
This will give results for all accounts that carried out tasks in Entra ID and may generate too many operations that were not privileged. To filter for specific Entra ID roles, the following query can be run where the roles are defined in a list. Three roles have been added as examples, but this list can and should be expanded to include more roles:
Once the query is run, the results will give insights into the activities performed in your Entra ID tenant and what roles those accounts have. In the example below, the top two results don't pose any problems. However, the third row contains a user that has the Global Administrator role and has created a service principal. The permissions needed to create a service principal can be found in roles less privileged than the Global Administrator role. Therefore, this user can be given a less privileged role. To find out which role can be granted, check this list , which contains the least privileged role required to carry out specific tasks in Entra ID.

Figure 2 Actions taken by users in Entra ID

Figure 3 Configuring the forwarding of Entra ID Audit logs to a Log Analytics Workspace
To ingest Entra ID audit logs into a Log Analytics Workspace follow these steps .
Because there is no table that contains the roles an identity has been granted, you'll need to add the list of users to the query and filter them. There are multiple ways to get a list of users who have been assigned a specific Entra ID role. A quick way to do this is to go to Entra ID and then select Roles and administrators. From there, select the role and export the identities that have been assigned to it. It's important to have the User Principal Names (UPNs) of the privileged users. You'll need to add these UPNs, along with the roles the user has, to the query. Some examples have been given in the query itself. If the user has more than one role, then all roles must be added to the query.
Once you run the query, the results will give insights into the activities performed in your Entra ID tenant by the users you have filtered for. In the example below, the top two results can cause problems. Both have the Global Administrator role, but their operations don't necessitate to have that role. The permissions needed for these operations can be found in roles less privileged than the Global Administrator role. Therefore, these users can be given a less privileged role. To find out which role can be granted, check this list , which contains the least privileged role required to carry out specific tasks in Entra ID.

Figure 4 Actions taken by users in Entra ID
If this user still requires the Global Administrator role then the Security Administrator role will become redundant as the Global Administrator contains more permissions than the Security Administrator role.
Keeping accounts with privileges that are not required is keeping your attack surface greater than it needs to be. By ingesting Entra ID Audit logs, you can query and identify users who have unnecessary and over-privileged roles. You can then find a suitable alternative role for them.
Timur Engin
LinkedIn Twitter
Learn more about Microsoft Entra:
This article was originally published by Microsoft's Entra (Azure AD) Blog . You can find the original article here .
Related Posts
- Wipro’s new IMC tool automates app migration to Azure AD
- Volt Typhoon targets US critical infrastructure with living-off-the-land techniques
- Using Microsoft 365 Defender to protect against Solorigate
- US Government sets forth Zero Trust architecture strategy and requirements
- Top 5 Common Deployment Tips for US Government Agencies

COMMENTS
Here are the Azure RBAC-related operations that are logged in Activity Log: Create role assignment; Delete role assignment; Create or update custom role definition; Delete custom role definition; Azure portal. The easiest way to get started is to view the activity logs with the Azure portal. The following screenshot shows an example of role ...
Role assignments enable you to grant a principal (such as a user, a group, a managed identity, or a service principal) access to a specific Azure resource. This article describes the details of role assignments. Role assignment. Access to Azure resources is granted by creating a role assignment, and access is revoked by removing a role assignment.
Keeping an eye on Azure AD administrative role assignments is crucial for tenant security and compliance. Forget about the built-in PIM report in the Azure AD portal - take reporting to the next level and build your own report with Graph, KQL and Powershell. Unassigning inactive roles, verifying that all role holders have registered MFA and are ...
It also logs Azure role assignments (the operation to assign resource permissions to identities) There is consistent logging irrespective of the management tool being used (Azure Portal, Azure CLI, Azure PowerShell, SDKs or Direct API calls) because of Azure singular management layer — Azure Resource Manager — ARM (Figure 1.1). ...
Auditing Role Changes. I had recently been asked to figure out a way to audit Azure Active Directory (AAD, AzAD) Role changes — such as the Global Administrator — using a SIEM (security information and event management). The Azure portal only provides 1 month's Role Management history, and being able to query a SIEM, such as Splunk, would allow a security professional to go back further ...
You would just go into the PIM in azure, click azure ad roles, click manage roles, choose the global admin role, Click role settings, and you will see options like this. If you don't have PIM, then it becomes quite a bit more complicated but could probably be less complicated than your example, you could set up log analytics to ingest azure ad ...
Next, you'll want to ensure you (or the user or service principal who will be authenticating to Azure AD) are in the appropriate Azure role in the in the Log Analytics workspace, either the Log Analytics Reader role, or the Log Analytics Contributor role. Azure portal - Log Analytics role assignments . You can set this role assignment in the ...
GCP Audit Log for IAM Role Assignments. Step 3: Refine the log filter to filter audit logs for IAM role assignments when "users have been assigned to roles"
Azure role-based access control (Azure RBAC) has several Azure built-in roles that you can assign to users, groups, service principals, and managed identities. Role assignments are the way you control access to Azure resources. If the built-in roles don't meet the specific needs of your organization, you can create your own Azure custom roles.
Routine checks of role assignments and generating alerts on new role assignments are one way to track and manage privileged role assignment. Chances are that when a user with privileged roles is approached, they'll say they need the role. ... Figure 3 Configuring the forwarding of Entra ID Audit logs to a Log Analytics Workspace .
The activity log is really great to tell the who, what, and when for operations in your Azure resources. ... or role assignments. It will show you the number of everything that happened in the past 24 hours. You can see here on these particular logs, you have an arrow to the left of this. This means that these logs are grouped together by ...
Step1: In The GCP Logging Page lets filter based on Audit Logs to view all the changes that has happened on GCP resources. Step 2: Refine the Log filter to filter the audit logs and extract logs relevant to IAM Policy and role assignments.
Audit Reports, Login Reports, and Audit Logs in EPM Cloud on OCI (Gen 2) Multiple reports are available in Oracle Enterprise Performance Management Cloud on OCI (Gen 2) to audit user, role, and group modifications. Role Assignment Audit Report - Audits the changes made to predefined and application role assignments. Available via:
Is there a way to hook Log Analytics or Azure Monitor into Role Assignments in order to capture when a new user/service principal/group is added to a Role for any resource within a tenant? I'm looking for a log to tie alerts to. Something with a human readable DisplayName for both the user/sp/group and the resource its applied to. Example:
Routine checks of role assignments and generating alerts on new role assignments are one way to track and manage privileged role assignment. Chances are that when a user with privileged roles is approached, they'll say they need the role. ... Figure 3 Configuring the forwarding of Entra ID Audit logs to a Log Analytics Workspace.
2. As far as I understand from my investigation, if you want to do it using Azure Built-in roles, you need the following three roles at the very least: Reader role assignment scoped to the AKS cluster to be able to discover the cluster. Azure Kubernetes Service Cluster User Role role assignment scoped to the AKS cluster as mentioned in the note ...